Research on the Credulity of Spear-Phishing Attacks for Lithuanian Education Institutions’ Employees
Abstract
1. Introduction
2. Related Work
3. Materials and Methods
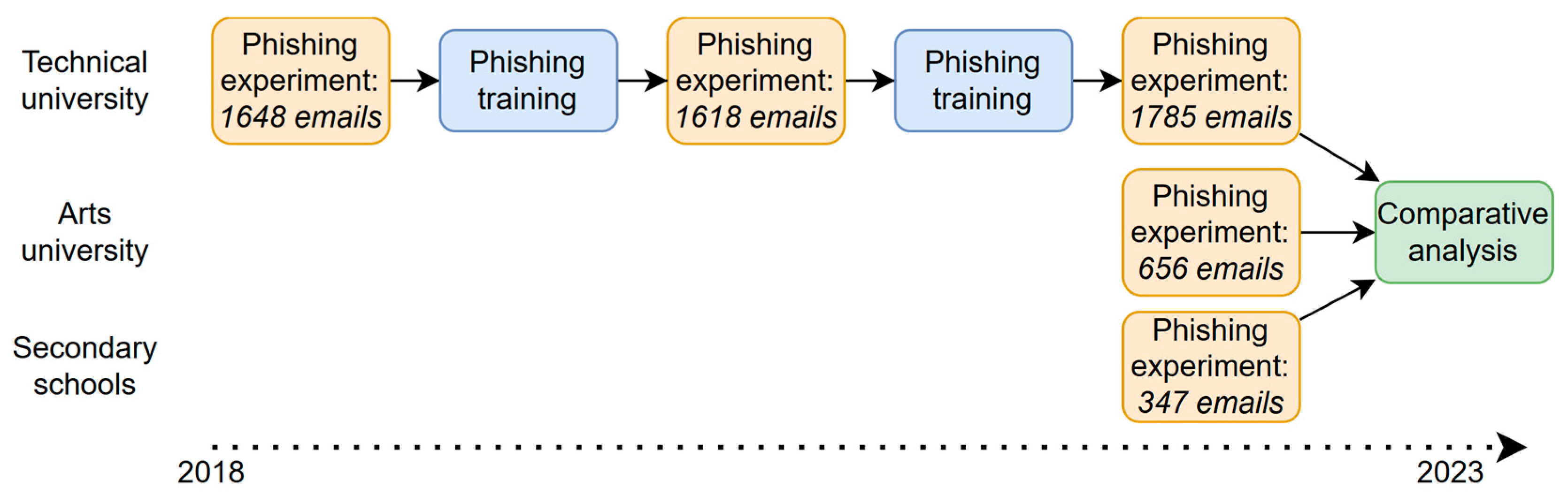
3.1. Scope of the Research
3.2. Design of the Phishing Experiments
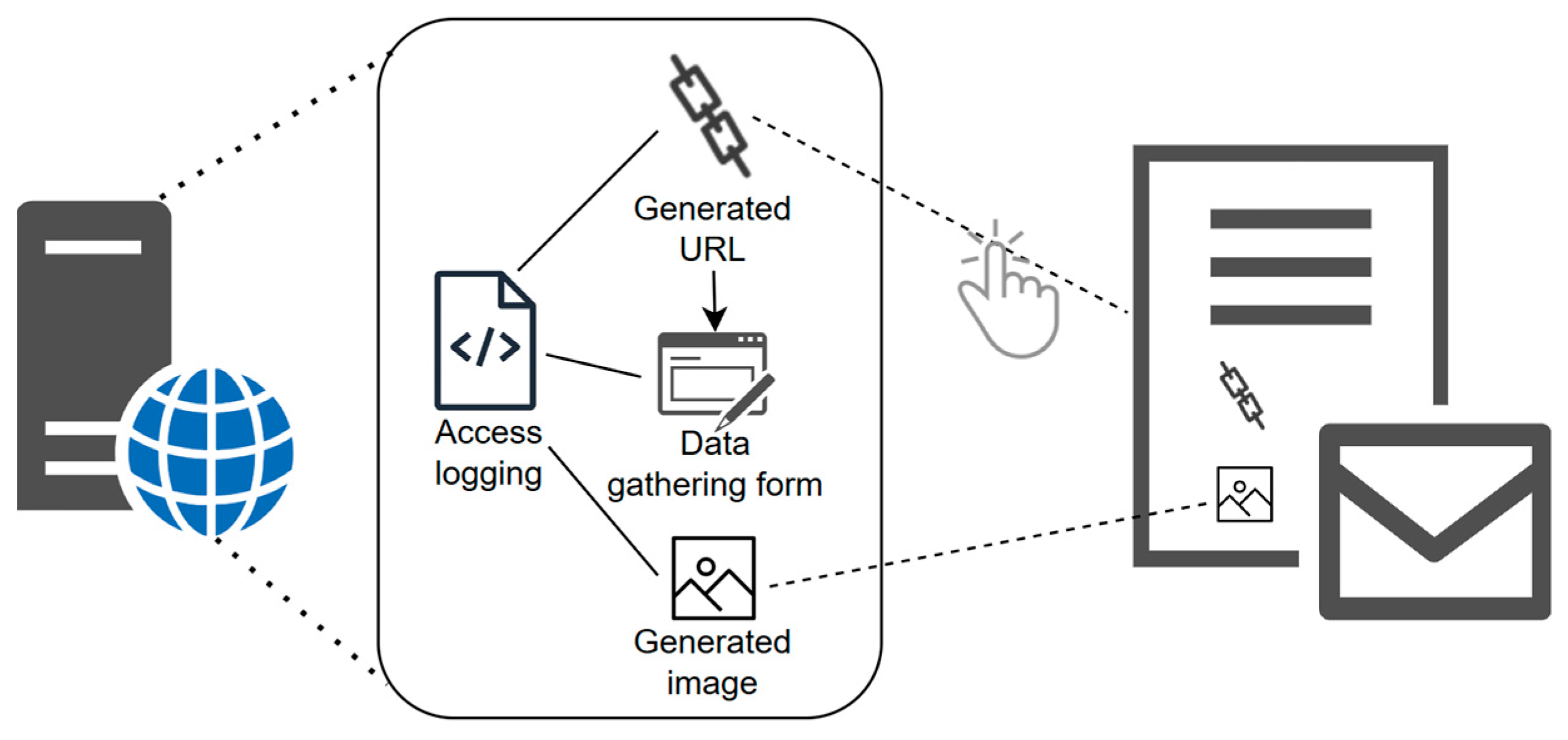
- Generate unique resources for each employee, to ensure traceability.
- For resource request identification and logging, include embedded sources.
- Log all identified user actions with all available data (time, IP address, used device, etc.).
- Assured employee-provided data confidentiality, preventing attack data leakage.
3.3. Analyzed Research Data
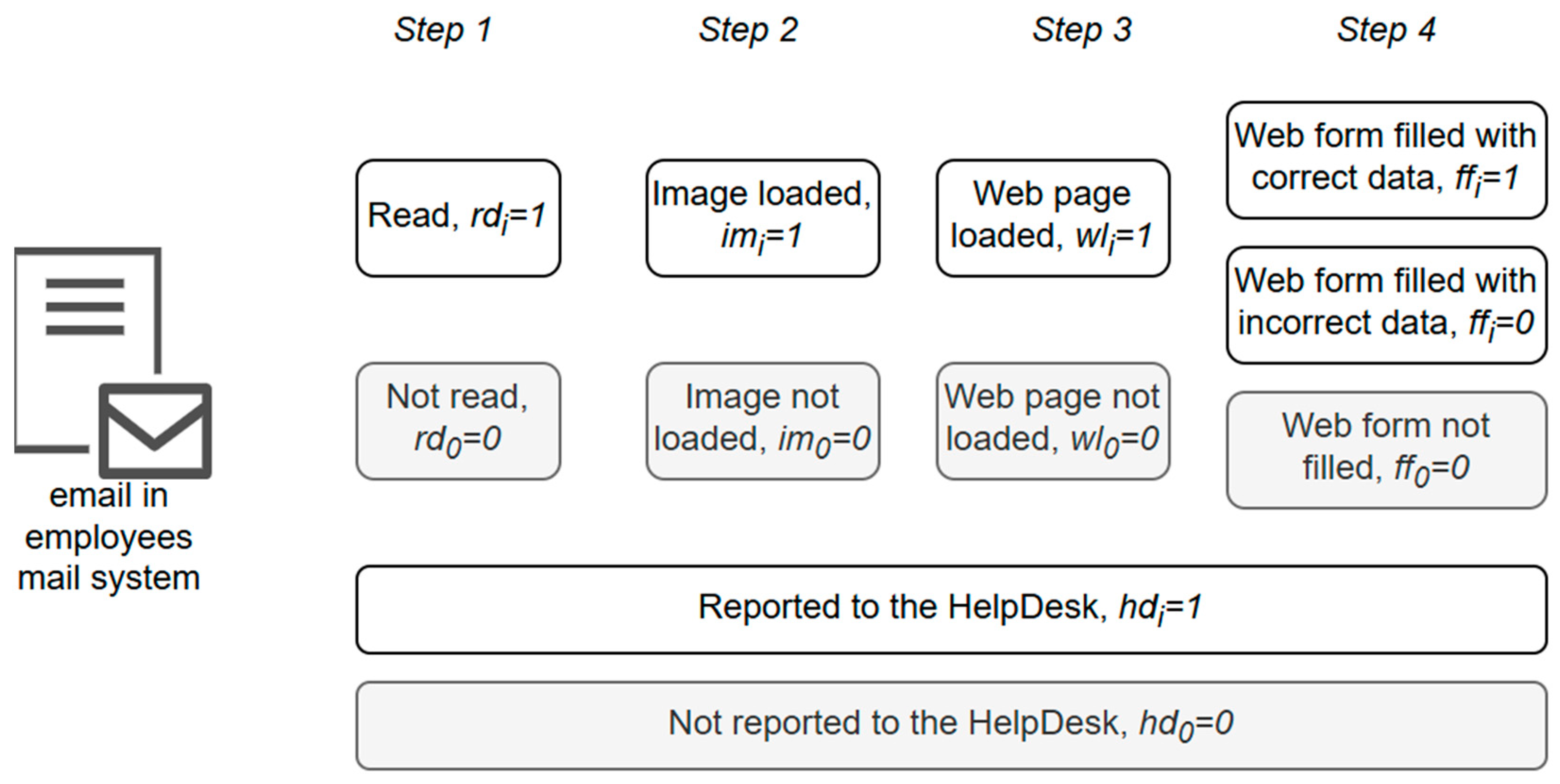
- Time when the email was sent to the user. The email contained unique identifiers dedicated to user action traceability. The time was logged on the email-sending server.
- Time when the user read the email. This was logged every time the user opened the email. Email opening was implemented by integrating an additional external resource, which was automatically loaded. The loading request initiated the creation of an email-opening journal record.
- Time when the user loaded the image embedded in the email. Time logging was implemented based on the same principle, as in the email-opening case.
- Time when the user opened the website, mentioned in the email. The journal record was created on the website.
- Time when the user opened the data entry form. Analog to URL visiting was implemented.
- Time when the user filled in the data. The journal record was saved in the form submission action.
4. Results
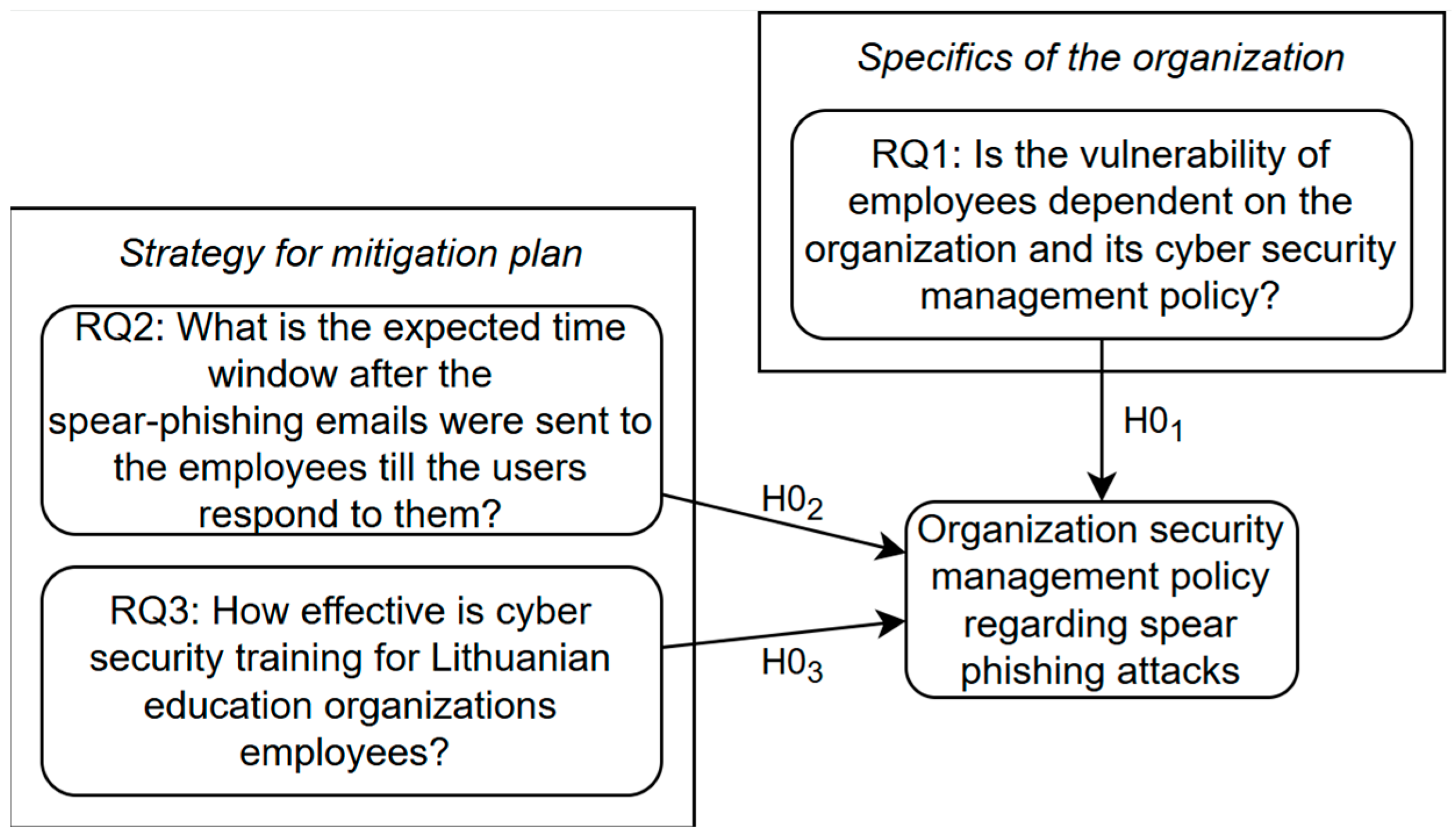
4.1. Is the Vulnerability of Education Organization Employees Dependent on the Organization and Its Cyber Security Management Policy?
4.2. When Will Employees Respond to Spear-Phishing Emails Sent to Them?
4.3. How Effective Is Cyber Security Training for Lithuanian Education Organization Employees?
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wang, Z.; Sun, L.; Zhu, H. Defining social engineering in cybersecurity. IEEE Access 2020, 8, 85094–85115. [Google Scholar]
- APWG: Phishing Activity Trends Reports. Available online: https://apwg.org/trendsreports/ (accessed on 29 May 2023).
- Salahdine, F.; Kaabouch, N. Social engineering attacks: A survey. Future Internet 2019, 11, 89. [Google Scholar] [CrossRef]
- Roy, S.S.; Naragam, K.V.; Nilizadeh, S. Generating Phishing Attacks Using ChatGPT. Available online: https://arxiv.org/abs/2305.05133 (accessed on 29 May 2023).
- Alghenaim, M.F.; Bakar, N.A.A.; Abdul Rahim, F.; Vanduhe, V.Z.; Alkawsi, G. Phishing Attack Types and Mitigation: A Survey. In Proceedings of the International Conference on Data Science and Emerging Technologies, Khulna, Bangladesh, 20–21 December 2022; Springer Nature: Singapore, 2022; pp. 131–153. [Google Scholar]
- Wosah, N.P.; Win, T. Phishing mitigation techniques: A literature survey. arXiv 2021, arXiv:2104.06989. [Google Scholar]
- Wang, Z.; Zhu, H.; Sun, L. Social engineering in cybersecurity: Effect mechanisms, human vulnerabilities and attack methods. IEEE Access 2021, 9, 11895–11910. [Google Scholar]
- Rastenis, J.; Ramanauskaitė, S.; Janulevičius, J.; Čenys, A. Impact of Information Security Training on Recognition of Phishing Attacks: A Case Study of Vilnius Gediminas Technical University. In Proceedings of the Databases and Information Systems: 14th International Baltic Conference, DB&IS 2020, Tallinn, Estonia, 16–19 June 2020; Proceedings 14. Springer International Publishing: Cham, Switzerland, 2020; pp. 311–324. [Google Scholar]
- Shankar, A.; Shetty, R.; Nath, B. A review on phishing attacks. Int. J. Appl. Eng. Res. 2019, 14, 5. [Google Scholar]
- Lakshmi, L.; Reddy, M.P.; Santhaiah, C.; Reddy, U.J. Smart phishing detection in web pages using supervised deep learning classification and optimization technique adam. Wirel. Pers. Commun. 2021, 118, 3549–3564. [Google Scholar] [CrossRef]
- Vijayalakshmi, M.; Mercy Shalinie, S.; Yang, M.H.; U, R.M. Web phishing detection techniques: A survey on the state-of-the-art, taxonomy and future directions. IET Netw. 2020, 9, 235–246. [Google Scholar]
- Do, N.Q.; Selamat, A.; Krejcar, O.; Herrera-Viedma, E.; Fujita, H. Deep learning for phishing detection: Taxonomy, current challenges and future directions. IEEE Access 2022, 10, 36429–36463. [Google Scholar]
- Rashid, J.; Mahmood, T.; Nisar, M.W.; Nazir, T. Phishing detection using machine learning technique. In Proceedings of the 2020 First International Conference of Smart Systems and Emerging Technologies (SMARTTECH), Riyadh, Saudi Arabia, 3–5 November 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 43–46. [Google Scholar]
- Salloum, S.; Gaber, T.; Vadera, S.; Shaalan, K. Phishing email detection using natural language processing techniques: A literature survey. Procedia Comput. Sci. 2021, 189, 19–28. [Google Scholar]
- Tan, C.C.L.; Chiew, K.L.; Yong, K.S.; Sebastian, Y.; Than, J.C.M.; Tiong, W.K. Hybrid phishing detection using joint visual and textual identity. Expert Syst. Appl. 2023, 220, 119723. [Google Scholar]
- Allodi, L.; Chotza, T.; Panina, E.; Zannone, N. The need for new antiphishing measures against spear-phishing attacks. IEEE Secur. Priv. 2019, 18, 23–34. [Google Scholar] [CrossRef]
- Jampen, D.; Gür, G.; Sutter, T.; Tellenbach, B. Don’t click: Towards an effective anti-phishing training. A comparative literature review. Hum.-Centric Comput. Inf. Sci. 2020, 10, 33. [Google Scholar] [CrossRef]
- Mitchell, A. Improving Cybersecurity Behaviors: A Proposal for Analyzing Four Types of Phishing Training. In Proceedings of the WISP 2020, Virtual, 12 December 2020. [Google Scholar]
- Hillman, D.; Harel, Y.; Toch, E. Evaluating Organizational Phishing Awareness Training on an Enterprise Scale. Comput. Secur. 2023, 132, 103364. [Google Scholar]
- Buckley, J.; Lottridge, D.; Murphy, J.G.; Corballis, P.M. Indicators of employee phishing email behaviours: Intuition, elaboration, attention, and email typology. Int. J. Hum.-Comput. Stud. 2023, 172, 102996. [Google Scholar] [CrossRef]
- Shakela, V.; Jazri, H. Assessment of spear phishing user experience and awareness: An evaluation framework model of spear phishing exposure level (spel) in the namibian financial industry. In Proceedings of the 2019 International Conference on Advances in Big Data, Computing and Data Communication Systems (icABCD), Winterton, South Africa, 5–6 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Abroshan, H.; Devos, J.; Poels, G.; Laermans, E. A phishing mitigation solution using human behaviour and emotions that influence the success of phishing attacks. In Proceedings of the 29th ACM Conference on User Modeling, Adaptation and Personalization, Utrecht, The Netherlands, 21–25 June 2021; pp. 345–350. [Google Scholar]
- Zhuo, S.; Biddle, R.; Koh, Y.S.; Lottridge, D.; Russello, G. SoK: Human-centered phishing susceptibility. ACM Trans. Priv. Secur. 2023, 26, 24. [Google Scholar] [CrossRef]
- Xu, T.; Singh, K.; Rajivan, P. Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks. Appl. Ergon. 2023, 108, 103908. [Google Scholar] [CrossRef] [PubMed]
- Frank, M.; Jaeger, L.; Ranft, L.M. Contextual drivers of employees’ phishing susceptibility: Insights from a field study. Decis. Support Syst. 2022, 160, 113818. [Google Scholar] [CrossRef]
- Daengsi, T.; Pornpongtechavanich, P.; Wuttidittachotti, P. Cybersecurity awareness enhancement: A study of the effects of age and gender of Thai employees associated with phishing attacks. Educ. Inf. Technol. 2021, 27, 4729–4752. [Google Scholar] [CrossRef]
- Aleroud, A.; Abu-Shanab, E.; Al-Aiad, A.; Alshboul, Y. An examination of susceptibility to spear phishing cyber attacks in non-English speaking communities. J. Inf. Secur. Appl. 2020, 55, 102614. [Google Scholar] [CrossRef]
- Reinheimer, B.; Aldag, L.; Mayer, P.; Mossano, M.; Duezguen, R.; Lofthouse, B.; Von Landesberger, T.; Volkamer, M. An investigation of phishing awareness and education over time: When and how to best remind users. In Proceedings of the Sixteenth Symposium on Usable Privacy and Security (SOUPS 2020), Online, 10–11 August 2020; pp. 259–284. [Google Scholar]
- Alghenaim, M.F.; Bakar, N.A.A.; Rahim, F.A. Awareness of Phishing Attacks in the Public Sector: Review Types and Technical Approaches. In Proceedings of the International Conference on Emerging Technologies and Intelligent Systems; Springer International Publishing: Cham, Switzerland, 2022; pp. 616–629. [Google Scholar]
- Baki, S.; Verma, R.M. Sixteen Years of Phishing User Studies: What Have We Learned? IEEE Trans. Dependable Secur. Comput. 2022, 20, 1200–1212. [Google Scholar] [CrossRef]
- Sarno, D.M.; Harris, M.W.; Black, J. Which phish is captured in the net? Understanding phishing susceptibility and individual differences. Appl. Cogn. Psychol. 2023, 37, 789–803. [Google Scholar] [CrossRef]
- Lei, W.; Hu, S.; Hsu, C. Uncovering the role of optimism bias in social media phishing: An empirical study on TikTok. Behav. Inf. Technol. 2023, 43, 1827–1841. [Google Scholar] [CrossRef]
- Jerrim, J. Who Responds to Phishing Emails? An International Investigation of 15-Year-Olds Using Pisa Data. Br. J. Educ. Stud. 2023, 71, 701–724. [Google Scholar] [CrossRef]
- Stalans, L.; Chan-Tin, E.; Hart, A.; Moran, M.; Kennison, S. Predicting Phishing Victimization: Comparing Prior Victimization, Cognitive, and Emotional Styles, and Vulnerable or Protective E-mail Strategies. Vict. Offenders 2023, 18, 1216–1235. [Google Scholar] [CrossRef]
- Williams, R.; Morrison, B.W.; Wiggins, M.W.; Bayl-Smith, P. The role of conscientiousness and cue utilisation in the detection of phishing emails in controlled and naturalistic settings. Behav. Inf. Technol. 2023, 43, 1842–1858. [Google Scholar] [CrossRef]
- Frauenstein, E.D.; Flowerday, S.; Mishi, S.; Warkentin, M. Unraveling the behavioral influence of social media on phishing susceptibility: A Personality-Habit-Information Processing model. Inf. Manag. 2023, 60, 103858. [Google Scholar] [CrossRef]
- Burns, A.J.; Johnson, M.E.; Caputo, D.D. Spear phishing in a barrel: Insights from a targeted phishing campaign. J. Organ. Comput. Electron. Commer. 2019, 29, 24–39. [Google Scholar] [CrossRef]
- Tian, C.A.; Jensen, M.L.; Durcikova, A. Phishing susceptibility across industries: The differential impact of influence techniques. Comput. Secur. 2023, 135, 103487. [Google Scholar] [CrossRef]
- Rastenis, J.; Ramanauskaitė, S.; Janulevičius, J.; Čenys, A.; Slotkienė, A.; Pakrijauskas, K. E-mail-based phishing attack taxonomy. Appl. Sci. 2020, 10, 2363. [Google Scholar] [CrossRef]
- Rastenis, J.; Ramanauskaitė, S.; Janulevičius, J.; Čenys, A. Credulity to phishing attacks: A real-world study of personnel with higher education. In Proceedings of the 2019 Open Conference of Electrical, Electronic and Information Sciences (eStream), Vilnius, Lithuania, 25 April 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Alhaddad, M.; Mohd, M.; Qamar, F.; Imam, M. Study of Student Personality Trait on Spear-Phishing Susceptibility Behavior. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 0140571. [Google Scholar] [CrossRef]
- Xu, T.; Rajivan, P. Determining psycholinguistic features of deception in phishing messages. Inf. Comput. Secur. 2023, 31, 199–220. [Google Scholar]
- Vankelecom, L.; Loeys, T.; Moerkerke, B. How to safely reassess variability and adapt sample size? A primer for the independent samples t test. Adv. Methods Pract. Psychol. Sci. 2024, 7, 25152459231212128. [Google Scholar] [CrossRef]
- Asiri, S.; Xiao, Y.; Alzahrani, S.; Li, T. PhishingRTDS: A real-time detection system for phishing attacks using a Deep Learning model. Comput. Secur. 2024, 141, 103843. [Google Scholar]
- Al-Subaiey, A.; Al-Thani, M.; Alam, N.A.; Antora, K.F.; Khandakar, A.; Zaman, S.A.U. Novel interpretable and robust web-based AI platform for phishing email detection. Comput. Electr. Eng. 2024, 120, 109625. [Google Scholar]

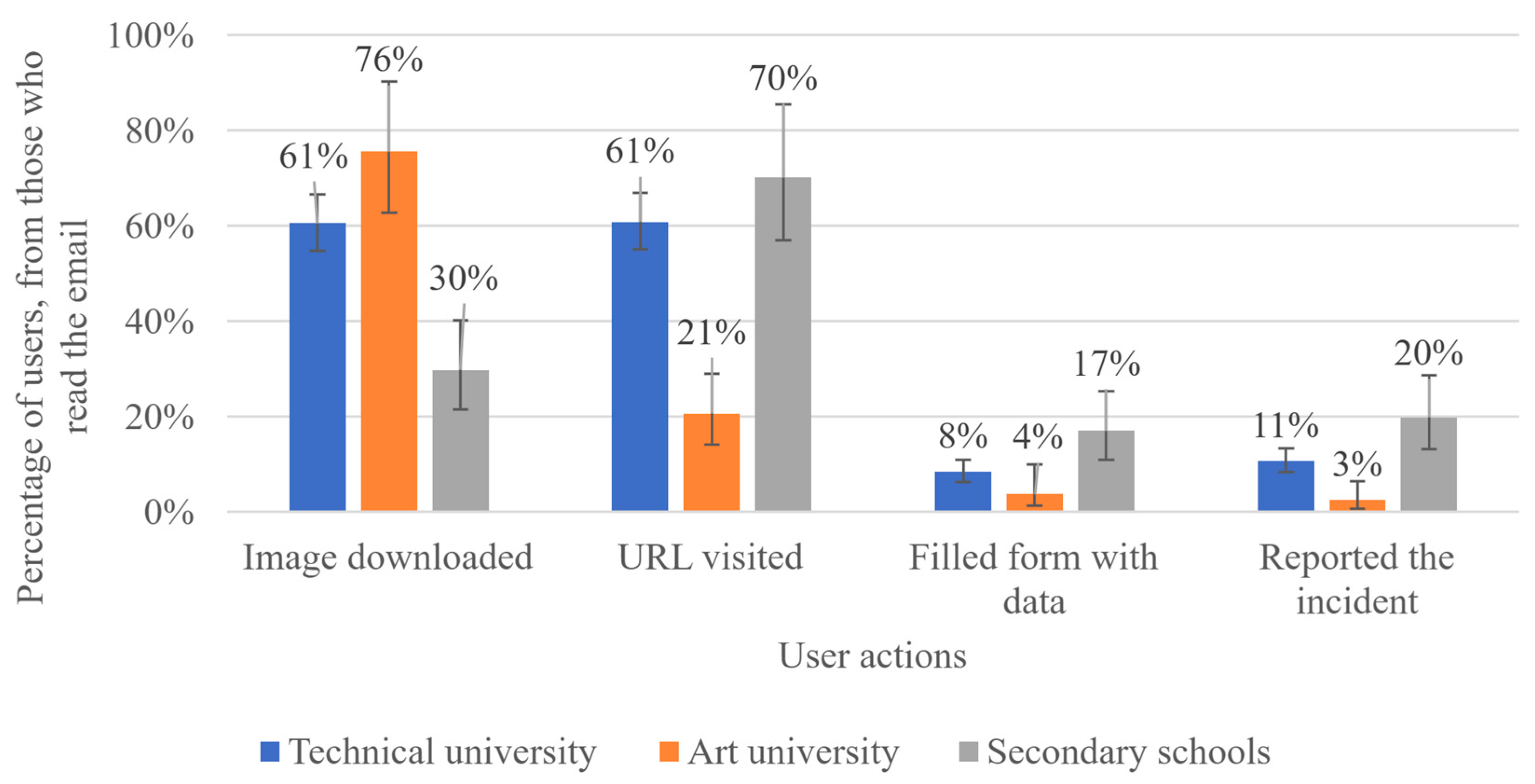
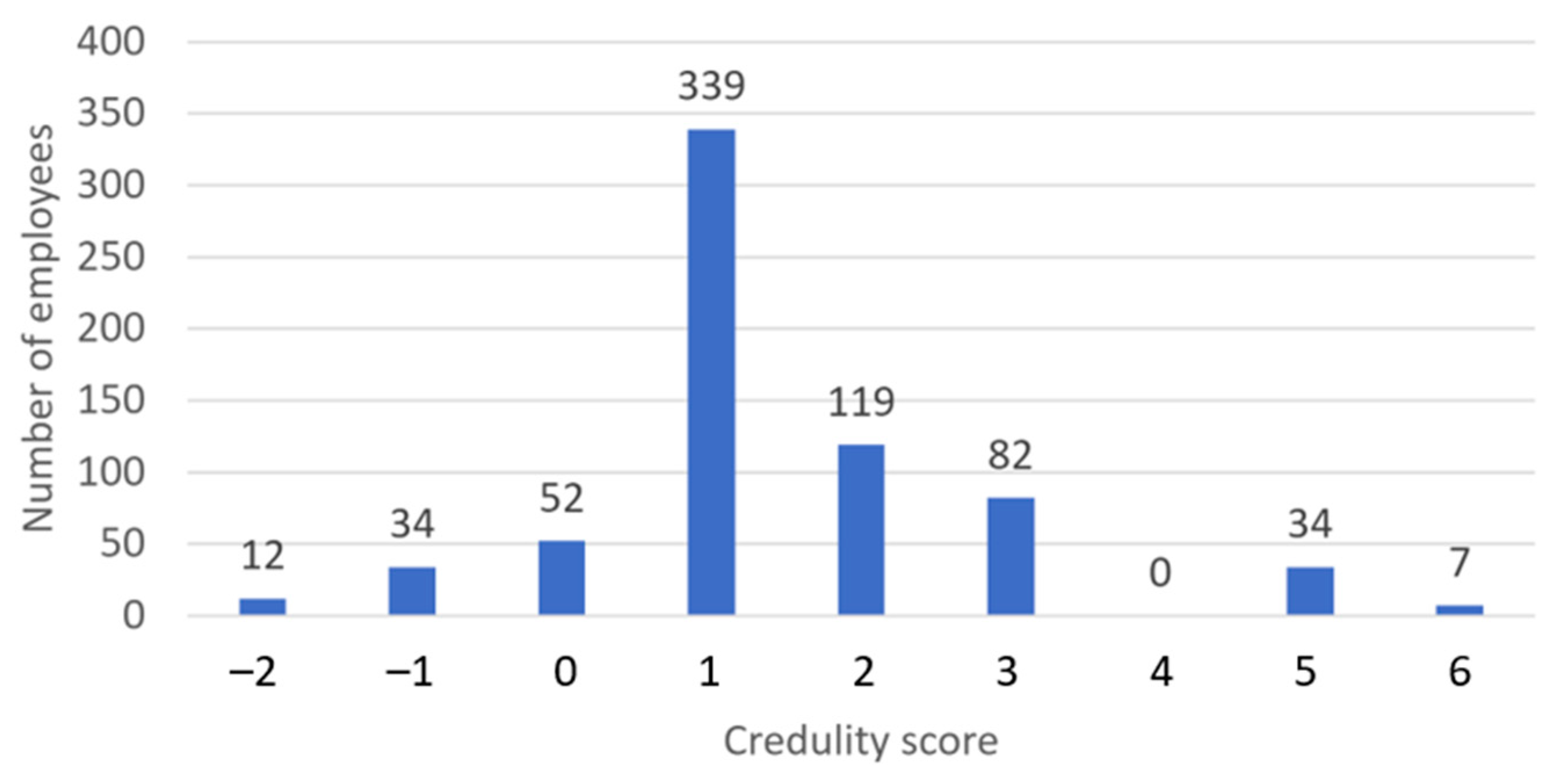
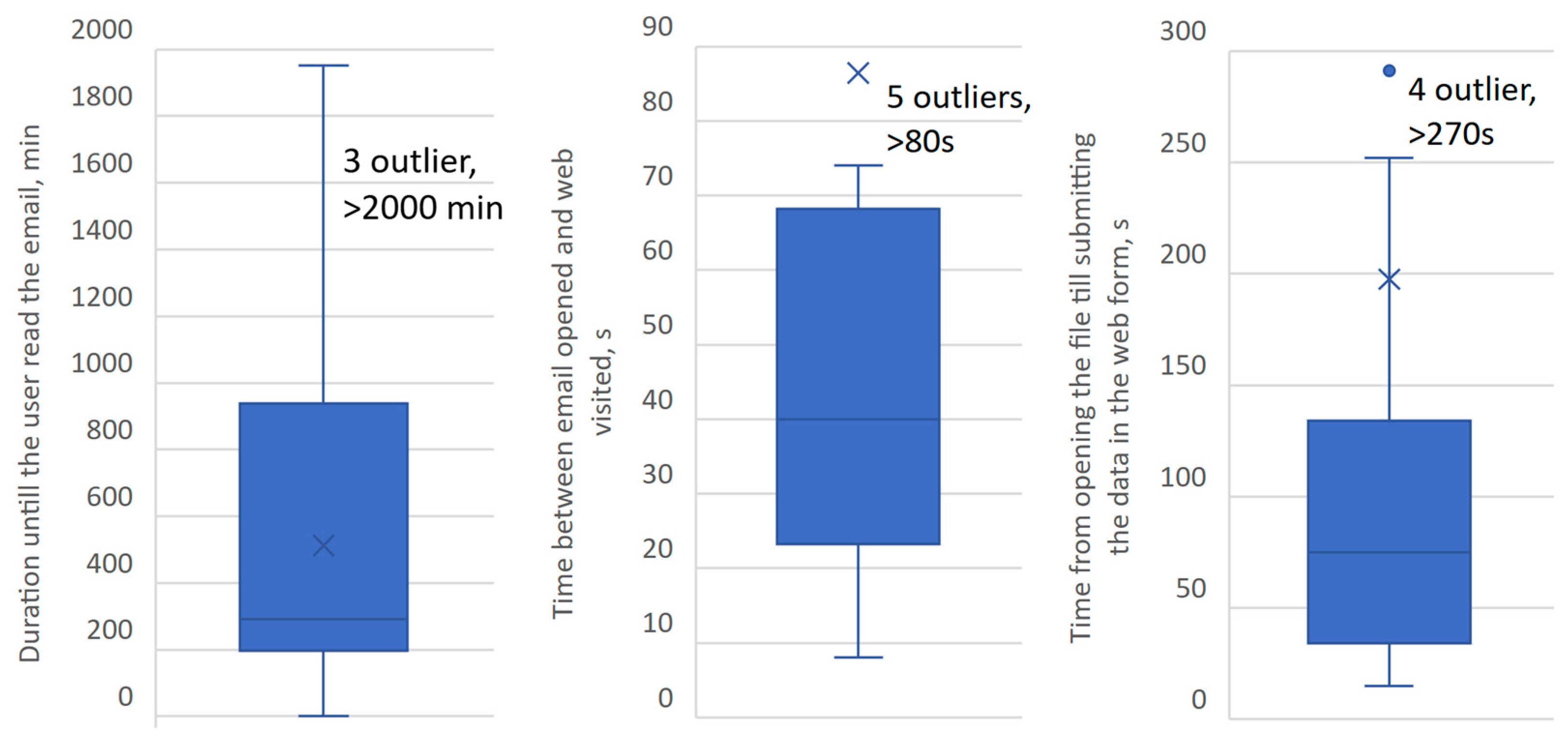

| Employee Actions | Comparison Between Different Types of Education Institution | ||
|---|---|---|---|
| Technical vs. Arts University | Technical University vs. Secondary School | Arts University vs. Secondary School | |
| Emails read | p < 0.0001 | p = 0.4729 | p < 0.0001 |
| Image downloaded | p = 0.0295 | p < 0.0001 | p = 0.0160 |
| URL visited | p < 0.0001 | p = 0.0655 | p < 0.0001 |
| Filled form with data | p = 0.0008 | p = 0.0027 | p < 0.0001 |
| Reported the incident | p < 0.0001 | p = 0.0032 | p < 0.0001 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rastenis, J.; Ramanauskaitė, S.; Čenys, A.; Stefanovič, P.; Radzevičienė, A. Research on the Credulity of Spear-Phishing Attacks for Lithuanian Education Institutions’ Employees. Appl. Sci. 2025, 15, 3431. https://doi.org/10.3390/app15073431
Rastenis J, Ramanauskaitė S, Čenys A, Stefanovič P, Radzevičienė A. Research on the Credulity of Spear-Phishing Attacks for Lithuanian Education Institutions’ Employees. Applied Sciences. 2025; 15(7):3431. https://doi.org/10.3390/app15073431
Chicago/Turabian StyleRastenis, Justinas, Simona Ramanauskaitė, Antanas Čenys, Pavel Stefanovič, and Asta Radzevičienė. 2025. "Research on the Credulity of Spear-Phishing Attacks for Lithuanian Education Institutions’ Employees" Applied Sciences 15, no. 7: 3431. https://doi.org/10.3390/app15073431
APA StyleRastenis, J., Ramanauskaitė, S., Čenys, A., Stefanovič, P., & Radzevičienė, A. (2025). Research on the Credulity of Spear-Phishing Attacks for Lithuanian Education Institutions’ Employees. Applied Sciences, 15(7), 3431. https://doi.org/10.3390/app15073431









