Challenges and Potential Improvements for Passkey Adoption—A Literature Review with a User-Centric Perspective
Abstract
1. Introduction
1.1. Scope and Research Questions
- RQ1
- What are the main challenges that hinder passkey adoption for end users?
- RQ2
- What are the main potential improvements to enhance passkey adoption among end users?
- RQ3
- Is it possible to derive a relative number regarding the adoption of passkeys among end users for online authentication, and if so, what is the adoption rate?
1.2. Key Contribution
1.3. Outline
2. Comparison with Existing Surveys
- Literature survey: Is the respective work performing a literature survey?
- Passkey focus: Is the respective work focusing specifically on passkeys? Not covering this aspect means that it covers passkeys but not as the primary content.
- Technical focus: Does it have a focus on the technical aspects of passkeys?
- Protocol focus: Does it have a focus on the protocol aspects of passkeys?
- Usability focus: Does it have a focus on usability aspects of passkeys?
3. Background
3.1. Authentication
- Something you know (e.g., password).
- Something you have (e.g,. a phone or security key).
- Something you are (e.g., face, fingerprint, iris, etc.).
3.2. Conventional Authentication Methods
3.3. FIDO
3.3.1. UAF
3.3.2. U2F
3.3.3. WebAuthn
3.3.4. Passkeys
3.3.5. CTAP2
3.4. User Experience
3.5. Current Challenges with Conventional Authentication Methods
3.5.1. Social Engineering
3.5.2. Phishing
3.5.3. Adoption of New Security Measures and Technologies
3.5.4. Human Aspect on Security
4. Methodology and Search Strategy
4.1. Search Strategy
4.2. Inclusion Criteria
- The paper’s content is related to the literature topic, i.e., related to passkeys with a focus on a user-centric topic.
- The paper’s content is fully accessible through open access or covered by a DTU license.
- The paper is written in English, Danish, or German.
4.3. Snowball Process
- The scope of the paper is closely related to the scope of this literature review.
- The paper is either also a literature review or covers a key aspect from the perspective of this survey, like, for example, covering user challenges with passkeys, etc.
4.4. Filtering Process
- The found item is a book, which is not a scientific medium.
- The paper has an unclear methodology, or the methodology is not described in detail.
- The paper contains too few references or too many claims without proof.
5. General Overview of Passkey Literature
5.1. Table of Challenges
5.2. Table of Improvements
6. Limitations and Challenges in Passkeys
6.1. Challenges
6.1.1. Technical Challenges
6.1.2. Usability Challenges
- Account revocation [83];
Lack of User Awareness
Setup Complexity
Lack of Portability and Platform Dependency Concerns
Account Delegation
Account Recovery
Account Revocation
Adoption in Enterprise Environments
6.1.3. Perception Challenges
6.2. Improvements
6.2.1. Technical Improvements
6.2.2. Usability Improvements
6.2.3. Perception Improvements
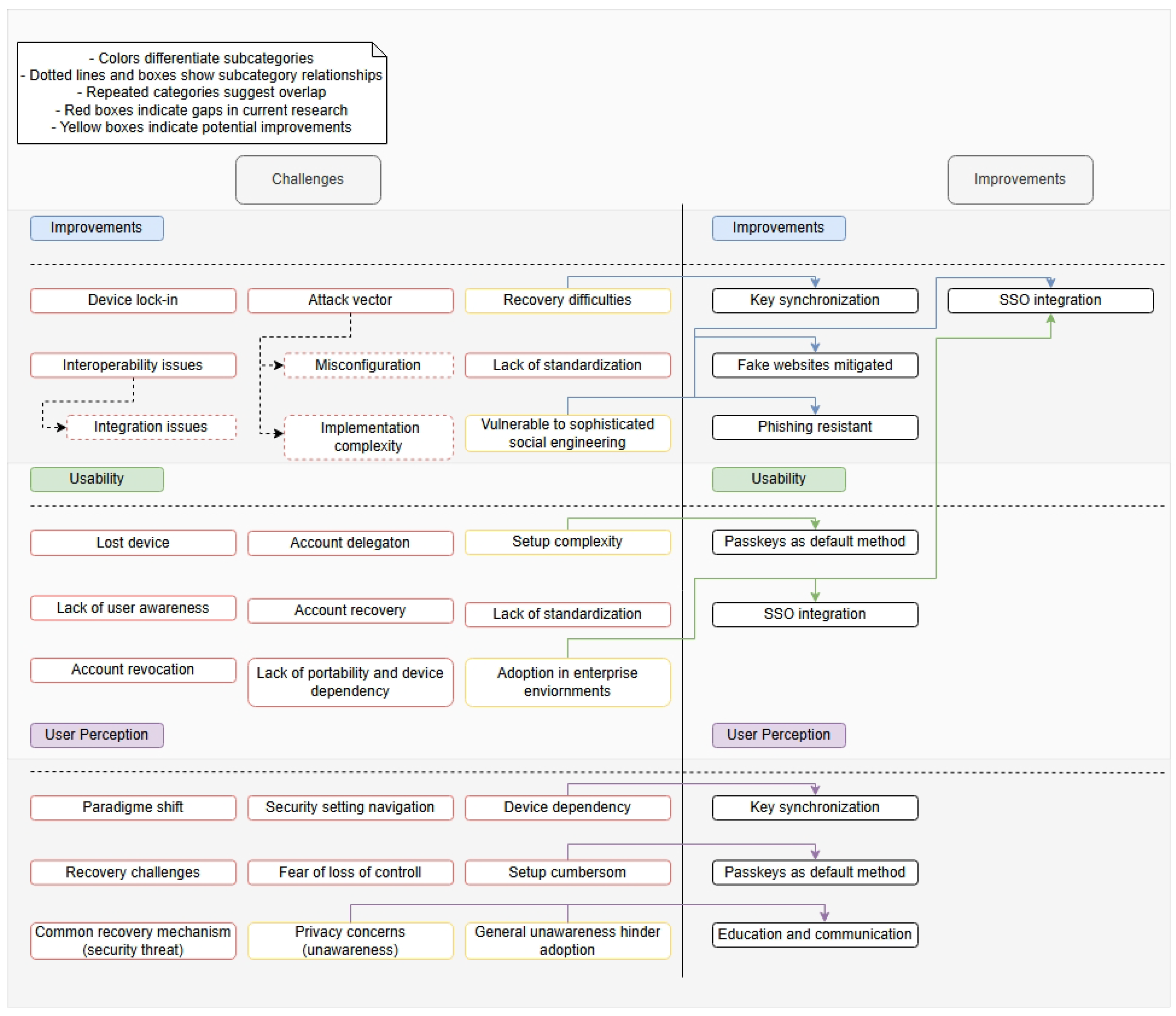
6.3. Mapping of Challenges and Improvements
7. Lessons Learned and Discussion
- Account sharing. Currently, only a few solutions allow for the sharing of passkeys among multiple people. Usually, they are either very technical and rely on a specific protocol implementation, like in [92], or require a more complex password manager setup and usage of all involved people of the respective password manager or the sharing of a hardware key, which also gives access to other accounts. Especially in the context of enterprises, where account sharing and delegation are crucial for day-to-day business, these issues need to be solved to achieve a higher adoption rate of passkeys. We, furthermore, note that resolving this issue needs to be achieved in a way that does not weaken the high protection of passkeys against phishing attacks.
- Passkey recovery. Despite this being tied to the high-security guarantees of passkeys, research suggests that many people fear losing their passkey(s), and therefore, losing access to their accounts. While this is not directly solvable by changing the passkeys themselves, it can be achieved by building standardized and secure ways of synchronizing passkeys among different devices, potentially allowing for restoring passkeys to a new device. We note that recent research has already started to propose solutions for this, like in [31] or [72], and standards like [104] have been released, focusing on setting secure guidelines. Additionally, we note that it is important to solve this problem while keeping the next point in mind.
- Transferability. Related to the previous point, another key challenge is the transferability of passkeys. While it is good from a security perspective that passkeys are often tied directly to a hardware key or the device, this is not practical for many end users, as they can lose or damage devices, lose keys, or want to transfer their passkeys easily to their new device or service. Therefore, there needs to be an easy, standardized, and secure way of exporting or transferring passkeys to another device or system. Similar to the account sharing challenge. This must be achieved without weakening the protection against phishing attacks.
8. Future Research Directions
9. Conclusions
- RQ1: What are the main challenges that hinder passkey adoption for end users?The main challenges we see from the current academic research are, firstly, the user perception of passkeys. The passkey technology itself cannot directly address this; instead, it must be improved by improving user awareness and knowledge of the passkey technology. Secondly, despite significant improvements, current academia suggests there are key technical challenges regarding the account recovery, sharing, delegation, and transferability of passkeys. These challenges are especially relevant to the business adoption of passkeys and also negatively impact usability. Lastly, another aspect that can contribute to hindering passkey adoption is the lack of standardization, which can make it more troubling to implement passkeys from a technical perspective, and for users whose cognitive load associated with learning different user interface paradigms from multiple providers is further overwhelmed.
- RQ2: What are the main potential improvements to enhance passkey adoption among end users?Despite the challenges, we see clear improvements in passkeys that can enhance adoption. Passkeys offer superior technical security over existing authentication methods, like passwords, while achieving high usability. Furthermore, through numerous research studies in the usability domain, passkeys have already made significant progress and improved their setup and usability during authentication processes. These aspects are critical for the user-centric considerations of the adoption of passkeys.
- RQ3: Is it possible to derive a relative number regarding the adoption of passkeys among end users for online authentication, and if so, what is the adoption rate?The first part of this research question can be answered with a tendency towards no. While some academic research tries to estimate the adoption rate among end users, we conclude that they do not provide enough evidence of being statistically significant. Other community-driven resources give at least an idea of the possibility of adopting passkeys from a user perspective, highlighting that more and more companies are offering support for this form of authentication.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| CTAP | Client to Authenticator Protocol |
| CISO | Chief Information Security Officer |
| DAA | Direct Anonymous Attestation |
| DTU | Technical University of Denmark |
| FIDO | Fast Identity Online |
| FIDO2 | Fast Identity Online 2 |
| IAM | Identity and Access Management |
| LDA | Latent Dirichlet Allocation |
| OSINT | Open-Source Intelligence |
| OTP | One Time Password |
| PAKE | Password-Authenticated Key Agreement |
| SSO | Single Sign-On |
| TEE | Trusted Execution Environment |
| TOTP | Time based One Time Passwords |
| TPM | Trusted Platform Module |
| U2F | Universal 2nd Factor |
| UFA | Universal Authentication Framework |
| UX | User Experience |
| W3C | World Wide Web Consortium |
Appendix A
Overview of the Search Terms
| No. | Search Keyword(s) |
|---|---|
| 1 | Passkeys |
| 2 | Passkeys AND user |
| 3 | Passkeys AND user AND challenges |
| 4 | Passkeys AND user AND difficulties |
| 5 | Passkeys AND user AND improvements |
| 6 | Passkeys AND effects |
| 7 | Passkeys AND security |
| 8 | Passkeys AND security AND effect |
| 9 | Passkeys AND security improvements |
| 10 | Passkeys AND secrecy |
| 11 | Passkeys AND implications |
| 12 | Passwords AND user AND challenges |
| 13 | Passwords AND user AND difficulties |
| 14 | Passwords AND user AND improvements |
| 15 | Passkeys vs. Passwords |
| 16 | passkeys AND end-user AND business end-user |
| 17 | passkeys AND challenges AND ecosystem lock-in AND portability |
| 18 | passkeys AND security constraints |
| 19 | passkeys AND security constraints AND adoptability |
| 20 | passkeys AND adoptability |
| 21 | passkeys AND awareness AND understanding |
| 22 | passkeys AND security effects AND phishing mitigation AND authentication methods |
| 23 | passkeys AND cross-service implications AND password leaking |
| 24 | passkeys AND enrollment AND passwords |
| 25 | passkeys AND recovery AND backup |
| 26 | passkeys AND adoptions AND google AND apple |
| 27 | passkeys AND integration AND authentication methods |
| 28 | passkeys AND end-user |
| 29 | passkeys AND business end-user |
| 30 | passkeys AND improvements |
| 31 | passkeys AND passwords |
| 32 | passkeys AND challenges AND ecosystem lock-in |
| 33 | passkeys AND challenges AND portability |
| 34 | passkeys AND security constraints AND adoptability |
| 35 | passkeys AND awareness |
| 36 | passkeys AND understanding |
| 37 | passkeys AND security effects AND phishing mitigation |
| 38 | passkeys AND cross-service implications AND password leaking |
| 39 | passkeys AND enrollment |
| 40 | passkeys AND recovery |
| 41 | passkeys AND backup |
| 42 | passkeys AND adoptions AND google |
| 43 | passkeys AND adoptions AND apple |
| 44 | passkeys AND integration AND authentication methods |
References
- Papathanasaki, M.; Maglaras, L.; Ayres, N. Modern Authentication Methods: A Comprehensive Survey. AI Comput. Sci. Robot. Technol. 2022, 2022, 1–24. [Google Scholar] [CrossRef]
- Pearman, S.; Thomas, J.; Naeini, P.E.; Habib, H.; Bauer, L.; Christin, N.; Cranor, L.F.; Egelman, S.; Forget, A. Let us Go in for a Closer Look: Observing Passwords in Their Natural Habitat. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, CCS ’17, Dallas, TX, USA, 30 October–3 November 2017; pp. 295–310. [Google Scholar] [CrossRef]
- Herley, C.; van Oorschot, P.C.; Patrick, A.S. Passwords: If We’re So Smart, Why Are We Still Using Them? In Proceedings of the Financial Cryptography and Data Security; Dingledine, R., Golle, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 230–237. [Google Scholar] [CrossRef]
- Bosnjak, L.; Brumen, B. Rejecting the Death of Passwords: Advice for the Future. Comput. Sci. Inf. Syst. 2019, 16, 313–332. [Google Scholar] [CrossRef]
- Wash, R.; Rader, E.; Berman, R.; Wellmer, Z. Understanding Password Choices: How Frequently Entered Passwords Are Re-used across Websites. In Proceedings of the Twelfth Symposium on Usable Privacy and Security (SOUPS 2016), Denver, CO, USA, 22–24 June 2016; pp. 175–188. [Google Scholar]
- George, D.A.S. The Dawn of Passkeys: Evaluating a Passwordless Future. Partners Univers. Innov. Res. Publ. 2024, 2, 202–220. [Google Scholar] [CrossRef]
- Ghorbani Lyastani, S.; Schilling, M.; Neumayr, M.; Backes, M.; Bugiel, S. Is FIDO2 the Kingslayer of User Authentication? A Comparative Usability Study of FIDO2 Passwordless Authentication. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 268–285. [Google Scholar] [CrossRef]
- Angelogianni, A.; Politis, I.; Xenakis, C. How Many FIDO Protocols Are Needed? Analysing the Technology, Security and Compliance. ACM Comput. Surv. 2024, 56, 1–51. [Google Scholar] [CrossRef]
- Younis Mostafa, E.; Mohammed, S.J. THE LANDSCAPE OF AUTHENTICATION SYSTEMS: A COMPREHENSIVE SURVEY. MINAR Int. J. Appl. Sci. Technol. 2023, 5, 1–16. [Google Scholar] [CrossRef]
- Bicakci, K.; Uzunay, Y. Is FIDO2 Passwordless Authentication a Hype or for Real?: A Position Pape. In Proceedings of the 2022 15th International Conference on Information Security and Cryptography (ISCTURKEY), Ankara, Turkey, 19–20 October 2022; pp. 68–73. [Google Scholar] [CrossRef]
- Keil, M.; Markert, P.; Dürmuth, M. “It’s Just a Lot of Prerequisites”: A User Perception and Usability Analysis of the German ID Card as a FIDO2 Authenticator. In Proceedings of the 2022 European Symposium on Usable Security (EuroUSEC ’22), Karlsruhe, Germany, 29–30 September 2022; pp. 172–188. [Google Scholar] [CrossRef]
- Prasad, A. A Comparative Study of Passwordless Authentication. TechRxiv 2024. [Google Scholar] [CrossRef]
- Chaudhari, A.; Pawar, A.; Pawar, A.; Pawar, A.; Pawar, G. A Comprehensive Study on Authentication Systems. In Proceedings of the 2023 7th International Conference On Computing, Communication, Control Furthermore, Automation (ICCUBEA), Pune, India, 18–19 August 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Arabo, A.; Oduguwa, T. A Review of Password-less User Authentication Schemes. Authorea 2023. [Google Scholar] [CrossRef]
- Putz, F.; Schön, S.; Hollick, M. Future-Proof Web Authentication: Bring Your Own FIDO2 Extensions. In Proceedings of the Emerging Technologies for Authorization and Authentication; Saracino, A., Mori, P., Eds.; Springer: Cham, Switzerland, 2021; pp. 17–32. [Google Scholar] [CrossRef]
- Kuchhal, D.; Saad, M.; Oest, A.; Li, F. Evaluating the Security Posture of Real-World FIDO2 Deployments. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; pp. 2381–2395. [Google Scholar] [CrossRef]
- Reynolds, J.; Smith, T.; Reese, K.; Dickinson, L.; Ruoti, S.; Seamons, K. A Tale of Two Studies: The Best and Worst of YubiKey Usability. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 872–888. [Google Scholar] [CrossRef]
- Al Kabir, M.A.; Elmedany, W. An Overview of the Present and Future of User Authentication. In Proceedings of the 2022 4th IEEE Middle East and North Africa COMMunications Conference (MENACOMM), Amman, Jordan, 6–8 December 2022; pp. 10–17. [Google Scholar] [CrossRef]
- Kizza, J.M. Authentication. In Guide to Computer Network Security; Kizza, J.M., Ed.; Springer International Publishing: Cham, Switzerland, 2024; pp. 215–238. [Google Scholar] [CrossRef]
- Newhouse, W.; Bartock, M.; Cichonski, J.; Ferraiolo, H.; Souppaya, M.; Brown, C.; Dog, S.E.; Prince, S.; Sexton, J. Derived Personal Identity Verification (PIV) Credentials: Includes Executive Summary (A); Approach, Architecture, and Security Characteristics (B); and How-to Guides (C); Technical Report NIST SP 1800-12; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019. [CrossRef]
- EUR-Lex-02018R0389-20230912-EN-EUR-Lex. Available online: https://eur-lex.europa.eu/eli/reg_del/2018/389/2023-09-12 (accessed on 1 March 2025).
- Boopathy, D.; Sundaresan, M. Framework Model and Algorithm of Request Based One Time Passkey (ROTP) Mechanism to Authenticate Cloud Users in Secured Way. In Proceedings of the 10th Indiacom—2016 3rd International Conference on Computing for Sustainable Global Development, New Delhi, India, 16–18 March 2016; Hoda, M.N., Ed.; pp. 3898–3903. [Google Scholar]
- Biggio, B.; Akhtar, Z.; Fumera, G.; Marcialis, G.; Roli, F. Security Evaluation of Biometric Authentication Systems under Real Spoofing Attacks. IET Biom. 2012, 1, 11–24. [Google Scholar] [CrossRef]
- Ryu, R.; Yeom, S.; Herbert, D.; Dermoudy, J. The Design and Evaluation of Adaptive Biometric Authentication Systems: Current Status, Challenges and Future Direction. ICT Express 2023, 9, 1183–1197. [Google Scholar] [CrossRef]
- Pagnin, E.; Mitrokotsa, A. Privacy-Preserving Biometric Authentication: Challenges and Directions. Secur. Commun. Netw. 2017, 2017, 1–9. [Google Scholar] [CrossRef]
- Arora, S.S.; Badrinarayanan, S.; Raghuraman, S.; Shirvanian, M.; Wagner, K.; Watson, G. Avoiding Lock Outs: Proactive FIDO Account Recovery Using Managerless Group Signatures. 2022. Available online: https://eprint.iacr.org/2022/1555 (accessed on 1 March 2025).
- Das, S.; Dingman, A.; Camp, L.J. Why Johnny Doesn’t Use Two Factor A Two-Phase Usability Study of the FIDO U2F Security Key. In Proceedings of the Financial Cryptography and Data Security; Meiklejohn, S., Sako, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2018; pp. 160–179. [Google Scholar] [CrossRef]
- Ciolino, S.; Parkin, S.; Dunphy, P. Of Two Minds about Two-Factor: Understanding Everyday FIDO U2F Usability through Device Comparison and Experience Sampling. In Proceedings of the Fifteenth USENIX Conference on Usable Privacy and Security (SOUPS’19), Santa Clara, CA, USA, 11–13 August 2019; pp. 339–356. [Google Scholar]
- Kepkowski, M.; Hanzlik, L.; Wood, I.; Kaafar, M.A. How Not to Handle Keys: Timing Attacks on FIDO Authenticator Privacy. arXiv 2022. [Google Scholar] [CrossRef]
- Kim, D.; Kim, S.; Ryu, G.; Choi, D. Session Replication Attack Through QR Code Sniffing in Passkey CTAP Registration. In Proceedings of the ICT Systems Security and Privacy Protection; Pitropakis, N., Katsikas, S., Furnell, S., Markantonakis, K., Eds.; Springer: Cham, Switzerland, 2024; pp. 294–307. [Google Scholar] [CrossRef]
- Mitra, A.; Ghosh, A.; Sethuraman, S.C. TUSH-Key: Transferable User Secrets on Hardware Key. arXiv 2023. [Google Scholar] [CrossRef]
- Lyastani, S.G.; Backes, M.; Bugiel, S. A Systematic Study of the Consistency of Two-Factor Authentication User Journeys on Top-Ranked Websites. In Proceedings of the Proceedings 2023 Network and Distributed System Security Symposium, San Diego, CA, USA, 27 February–3 March 2023. [Google Scholar] [CrossRef]
- ISO-9241-11:2018; Ergonomics of Human-System Interaction. ISO: Geneva, Switzerland, 2018.
- Abraham, S.; Chengalur-Smith, I. An Overview of Social Engineering Malware: Trends, Tactics, and Implications. Technol. Soc. 2010, 32, 183–196. [Google Scholar] [CrossRef]
- Daza, D.R.M.; Tabuco, F.C.A.; Naval, P.C. Phishing Detection Using Ensemble of Classifiers. In Recent Challenges in Intelligent Information and Database Systems; Nguyen, N.T., Chbeir, R., Manolopoulos, Y., Fujita, H., Hong, T.P., Nguyen, L.M., Wojtkiewicz, K., Eds.; Springer Nature: Singapore, 2024; Volume 2144, pp. 39–50. [Google Scholar] [CrossRef]
- CFCS (Authority). The Cyber Threat from Phishing Mails. 2020. Available online: https://www.cfcs.dk/en/cybertruslen/threat-assessments/phishing/ (accessed on 1 March 2025).
- Thomopoulos, G.A.; Lyras, D.P.; Fidas, C.A. A Systematic Review and Research Challenges on Phishing Cyberattacks from an Electroencephalography and Gaze-Based Perspective. Pers. Ubiquitous Comput. 2024, 28, 449–470. [Google Scholar] [CrossRef]
- Peng, P.; Xu, C.; Quinn, L.; Hu, H.; Viswanath, B.; Wang, G. What Happens After You Leak Your Password: Understanding Credential Sharing on Phishing Sites. In Proceedings of the 2019 ACM Asia Conference on Computer and Communications Security (Asia CCS ’19), Auckland New, Zealand, 9–12 July 2019; pp. 181–192. [Google Scholar] [CrossRef]
- Bock, M. Measuring Adoption of Phishing-Resistant Authentication Methods on the Web. 2023. Available online: https://hdms.bsz-bw.de/frontdoor/index/index/docId/7038 (accessed on 1 March 2025).
- Qualys SSL Labs-SSL Pulse. Available online: https://www.ssllabs.com/ssl-pulse/ (accessed on 1 March 2025).
- Baier, E. The Evolution of SSL and TLS|DigiCert.Com. 2015. Available online: https://www.digicert.com/blog/evolution-of-ssl (accessed on 1 March 2025).
- Furuberg, I.L.; Øseth, M. From Password to Passwordless: Exploring User Experience Obstacles to the Adoption of FIDO2 Authentication. Master’s Thesis, NTNU, Ålesund, Norway, 2023. [Google Scholar]
- Ometov, A.; Bezzateev, S.; Mäkitalo, N.; Andreev, S.; Mikkonen, T.; Koucheryavy, Y. Multi-Factor Authentication: A Survey. Cryptography 2018, 2, 1. [Google Scholar] [CrossRef]
- Arthur, W.; Challener, D.; Goldman, K. A Practical Guide to TPM 2.0: Using the New Trusted Platform Module in the New Age of Security; Springer Nature: Singapore, 2015. [Google Scholar] [CrossRef]
- Das, S.; Russo, G.; Dingman, A.C.; Dev, J.; Kenny, O.; Camp, L.J. A Qualitative Study on Usability and Acceptability of Yubico Security Key. In Proceedings of the 7th Workshop on Socio-Technical Aspects in Security and Trust (STAST ’17), Orlando, FL, USA, 5 December 2017; pp. 28–39. [Google Scholar] [CrossRef]
- Frykholm, N.; Juels, A. Error-Tolerant Password Recovery. In Proceedings of the 8th ACM Conference on Computer and Communications Security (CCS ’01), Philadelphia, PA, USA, 5–8 November 2001; pp. 1–9. [Google Scholar] [CrossRef]
- Forget, A.; Chiasson, S.; van Oorschot, P.C.; Biddle, R. Improving Text Passwords through Persuasion. In Proceedings of the 4th Symposium on Usable Privacy and Security (SOUPS ’08), Pittsburgh, PA, USA, 23–25 July 2008; pp. 1–12. [Google Scholar] [CrossRef]
- Owens, K.; Anise, O.; Krauss, A.; Ur, B. User Perceptions of the Usability and Security of Smartphones as FIDO2 Roaming Authenticators. In Proceedings of the Seventeenth USENIX Conference on Usable Privacy and Security (SOUPS’21), Virtual Event, 9–10 August 2021; pp. 57–76. [Google Scholar]
- Tam, L.; Glassman, M.; Vandenwauver, M. The Psychology of Password Management: A Tradeoff between Security and Convenience. Behav. Inf. Technol. 2010, 29, 233–244. [Google Scholar] [CrossRef]
- Kim, B.C.; Park, Y.W. Security versus Convenience? An Experimental Study of User Misperceptions of Wireless Internet Service Quality. Decis. Support Syst. 2012, 53, 1–11. [Google Scholar] [CrossRef]
- Walia, K.S.; Shenoy, S.; Cheng, Y. An Empirical Analysis on the Usability and Security of Passwords. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science (IRI), Las Vegas, NV, USA, 11–13 August 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Seitz, T.; Hartmann, M.; Pfab, J.; Souque, S. Do Differences in Password Policies Prevent Password Reuse? In Proceedings of the 2017 CHI Conference Extended Abstracts on Human Factors in Computing Systems, Denver, CO, USA, 6–11 May 2017; pp. 2056–2063. [Google Scholar] [CrossRef]
- Uzonyi, D.G.; Pitropakis, N.; McKeown, S.; Politis, I. OPSEC VS Leaked Credentials: Password Reuse in Large-Scale Data Leaks. In Proceedings of the 2023 IEEE 28th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Edinburgh, UK, 6–8 November 2023; pp. 74–79. [Google Scholar] [CrossRef]
- Zimmermann, V.; Marky, K.; Renaud, K. Hybrid Password Meters for More Secure Passwords—a Comprehensive Study of Password Meters Including Nudges and Password Information. Behav. Inf. Technol. 2023, 42, 700–743. [Google Scholar] [CrossRef]
- Umejiaku, A.P.; Dhakal, P.; Sheng, V.S. Balancing Password Security and User Convenience: Exploring the Potential of Prompt Models for Password Generation. Electronics 2023, 12, 2159. [Google Scholar] [CrossRef]
- Fernando, W.P.K.; Dissanayake, D.A.N.P.; Dushmantha, S.G.V.D.; Liyanage, D.L.C.P.; Karunatilake, C. Challenges and Opportunities in Password Management: A Review of Current Solutions. Sri Lanka J. Soc. Sci. Humanit. 2023, 3, 9–20. [Google Scholar] [CrossRef]
- Hall, R.C.; Hoppa, M.A.; Hu, Y.H. An Empirical Study of Password Policy Compliance. J. Colloq. Inf. Syst. Secur. Educ. 2023, 10, 8. [Google Scholar] [CrossRef]
- Arias-Cabarcos, P.; Marin, A.; Palacios, D.; Almenarez, F.; Diaz-Sanchez, D. Comparing Password Management Software: Toward Usable and Secure Enterprise Authentication. IT Prof. 2016, 18, 34–40. [Google Scholar] [CrossRef]
- Hien, T.N.T.; Sangsongfa, A.; Amm-Dee, N. Discovering Personal Data Security Issues: Insights from “Have I Been Pwned”. In Advances in Computing and Data Sciences; Singh, M., Tyagi, V., Gupta, P.K., Flusser, J., Ören, T., Cherif, A.R., Tomar, R., Eds.; Springer Nature: Cham, Switzerland, 2025; Volume 2194, pp. 259–269. [Google Scholar] [CrossRef]
- Rahman, T.; Rohan, R.; Pal, D.; Kanthamanon, P. Human Factors in Cybersecurity: A Scoping Review. In Proceedings of the 12th International Conference on Advances in Information Technology, Bangkok, Thailand, 29 June–1 July 2021; pp. 1–11. [Google Scholar] [CrossRef]
- Naqvi, B.; Perova, K.; Farooq, A.; Makhdoom, I.; Oyedeji, S.; Porras, J. Mitigation Strategies against the Phishing Attacks: A Systematic Literature Review. Comput. Secur. 2023, 132, 103387. [Google Scholar] [CrossRef]
- Chowdhury, N.H.; Adam, M.T.P.; Skinner, G. The Impact of Time Pressure on Cybersecurity Behaviour: A Systematic Literature Review. Behav. Inf. Technol. 2019, 38, 1290–1308. [Google Scholar] [CrossRef]
- Grobler, M.; Gaire, R.; Nepal, S. User, Usage and Usability: Redefining Human Centric Cyber Security. Front. Big Data 2021, 4, 583723. [Google Scholar] [CrossRef]
- Petersen, K.; Vakkalanka, S.; Kuzniarz, L. Guidelines for Conducting Systematic Mapping Studies in Software Engineering: An Update. Inf. Softw. Technol. 2015, 64, 1–18. [Google Scholar] [CrossRef]
- Webster, J.; Watson, R. Analyzing the Past to Prepare for the Future: Writing a Literature Review. MIS Q. 2002, 26, xiii–xxiii. [Google Scholar]
- Wohlin, C. Guidelines for Snowballing in Systematic Literature Studies and a Replication in Software Engineering. In Proceedings of the 18th International Conference on Evaluation and Assessment in Software Engineering, London, UK, 13–14 May 2014; pp. 1–10. [Google Scholar] [CrossRef]
- Tay, A. How to Write a Superb Literature Review. Nature 2020, d41586-020-03422-x. [Google Scholar] [CrossRef]
- Stanton, J.M.; Stam, K.R.; Mastrangelo, P.; Jolton, J. Analysis of End User Security Behaviors. Comput. Secur. 2005, 24, 124–133. [Google Scholar] [CrossRef]
- Rahman, B. Conflicts Between Passkeys and European E-ID Scheme. 2024. Available online: https://urn.fi/URN:NBN:fi-fe2024083067275 (accessed on 1 March 2025).
- Corella, F. Overcoming the UX Challenges Faced by FIDO Credentials in the Consumer Space. In Proceedings of the HCI for Cybersecurity, Privacy and Trust; Moallem, A., Ed.; Springer: Cham, Switzerland, 2023; pp. 447–466. [Google Scholar] [CrossRef]
- Alqubaisi, F.; Wazan, A.S.; Ahmad, L.; Chadwick, D.W. Should We Rush to Implement Password-less Single Factor FIDO2 Based Authentication? In Proceedings of the 2020 12th Annual Undergraduate Research Conference on Applied Computing (URC), Dubai, United Arab Emirates, 15–16 April 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Shiraishi, M.; Shinagawa, T. Toward Cloud-Based FIDO Authentication with Secure Credentials Recovery. Available online: https://www.os.is.s.u-tokyo.ac.jp/papers/posters/2023-acsac-shiraishi-abstract.pdf (accessed on 1 March 2025).
- Lassak, L.; Pan, E.; Ur, B.; Golla, M. Why Aren’t We Using Passkeys? Obstacles Companies Face Deploying {FIDO2} Passwordless Authentication. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, PA, USA, 14–16 August 2024; pp. 7231–7248. [Google Scholar]
- Blei, D.; Ng, A.; Jordan, M. Latent Dirichlet Allocation. In Proceedings of the Advances in Neural Information Processing Systems; MIT Press: Cambridge, MA, USA, 2001; Volume 14. [Google Scholar]
- Hoffman, M.D.; Blei, D.M.; Bach, F. Online learning for Latent Dirichlet Allocation. In Proceedings of the 24th International Conference on Neural Information Processing Systems (NIPS’10), Red Hook, NY, USA, 6–9 December 2010; Volume 1, pp. 856–864. [Google Scholar]
- Chuang, J.; Manning, C.D.; Heer, J. Termite: Visualization Techniques for Assessing Textual Topic Models. Adv. Vis. Interfaces 2012, 74–77. [Google Scholar] [CrossRef]
- Chen, P. Vulnerability Testing for WebAuthn. Ph.D. Thesis, University of Twente, Enschede, The Netherlands, 2024. [Google Scholar]
- Domingues, P.; Frade, M.; Negrao, M. Digital Forensic Artifacts of FIDO2 Passkeys in Windows 11. In Proceedings of the 19th International Conference on Availability, Reliability and Security (ARES ’24), Vienna, Austria, 30 July–2 August 2024; pp. 1–10. [Google Scholar] [CrossRef]
- Georgiadis, E. FIDO2 Overview, Use Cases, and Security Considerations. Ph.D. Thesis, School of Information Sciences and Technology Department of Informatics, Athens, Greece, 2023. [Google Scholar] [CrossRef]
- Guirat, I.B.; Halpin, H. Formal Verification of the W3C Web Authentication Protocol. In Proceedings of the 5th Annual Symposium and Bootcamp on Hot Topics in the Science of Security, Raleigh, NC, USA, 10–11 April 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Schrempp, L. Formal Verification of FIDO2 with Human Interaction. Master’s Thesis, Information Security Group, Swiss Federal Institute of Technology (ETH) Zurich, Zurich, Switzerland, 2023; 91p. [Google Scholar] [CrossRef]
- Ulqinaku, E.; Assal, H.; Abdou, A.; Chiasson, S.; Čapkun, S. Is Real-time Phishing Eliminated with FIDO? Social Engineering Downgrade Attacks Against FIDO Protocols. 2020. Available online: https://eprint.iacr.org/2020/1298 (accessed on 1 March 2025).
- Blessing, J.; Hugenroth, D.; Anderson, R.J.; Beresford, A.R. SoK: Web Authentication in the Age of End-to-End Encryption. arXiv 2024. [Google Scholar] [CrossRef]
- Farke, F.M.; Lorenz, L.; Schnitzler, T.; Markert, P.; Dürmuth, M. {“You} Still Use the Password after {all”}—Exploring {FIDO2} Security Keys in a Small Company. In Proceedings of the Sixteenth Symposium on Usable Privacy and Security (SOUPS 2020), Online, 7–11 August 2020; pp. 19–35. [Google Scholar]
- Kepkowski, M.; Machulak, M.; Wood, I.; Kaafar, D. Challenges with Passwordless FIDO2 in an Enterprise Setting: A Usability Study. In Proceedings of the 2023 IEEE Secure Development Conference (SecDev), Atlanta, GA, USA, 18–20 October 2023; pp. 37–48. [Google Scholar] [CrossRef]
- Marky, K.; Ragozin, K.; Chernyshov, G.; Matviienko, A.; Schmitz, M.; Mühlhäuser, M.; Eghtebas, C.; Kunze, K. “Nah, It’s Just Annoying!” A Deep Dive into User Perceptions of Two-Factor Authentication. ACM Trans. Comput.-Hum. Interact. 2022, 29, 1–32. [Google Scholar] [CrossRef]
- Reese, K.; Smith, T.; Dutson, J.; Armknecht, J.; Cameron, J.; Seamons, K. A Usability Study of Five Two-Factor Authentication Methods. In Proceedings of the Fifteenth USENIX Conference on Usable Privacy and Security (SOUPS’19), Santa Clara, CA, USA, 11–13 August 2019; pp. 357–370. [Google Scholar]
- Würsching, L.; Putz, F.; Haesler, S.; Hollick, M. FIDO2 the Rescue? Platform vs. Roaming Authentication on Smartphones. In Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems (CHI ’23), Hamburg Germany, 23–28 April 2023; pp. 1–16. [Google Scholar] [CrossRef]
- Esberg, L. Exploring How UX Design Can Influence Users to Behave More Securely. 2024. Available online: https://www.divaportal.org/smash/record.jsf?pid=diva2%3A1867602&dswid=2574 (accessed on 1 March 2025).
- Lassak, L.; Hildebrandt, A.; Golla, M.; Ur, B. “It’s Stored, Hopefully, on an Encrypted Server”: Mitigating Users’ Misconceptions About {FIDO2} Biometric {WebAuthn}. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Virtual Event, 11–13 August 2021; pp. 91–108. [Google Scholar]
- Bandre, S.R. Design and Implementation of Smartphone Authentication System Based on Color-Code. In Proceedings of the 2015 International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Luke, K.; Kondo, T.; Kai, S.; Mayes, K.; Tezuka, S. Using Secret Sharing to Improve FIDO Attack Resistance for Multi-Device Credentials. In Proceedings of the 2023 8th International Conference on Information and Network Technologies (ICINT), Tokyo, Japan, 19–21 May 2023; pp. 49–56. [Google Scholar] [CrossRef]
- Nishith, D.; Samanta, I. Intelligent Authentication Gateway: Bridging the Gap Between Traditional and FIDO2 Security Through AI/ML Enhancement. Available online: https://engrxiv.org/preprint/download/3699/6576/5295 (accessed on 1 March 2025).
- Amft, S.M. On the Usability of Authentication Security Communication. Doctoral Thesis, Institutionelles Repositorium der Leibniz Universität Hannover, Hannover, Germany, 2024. [Google Scholar] [CrossRef]
- Venkatesh, V. Determinants of Perceived Ease of Use: Integrating Control, Intrinsic Motivation, and Emotion into the Technology Acceptance Model. Inf. Syst. Res. 2000, 11, 342–365. [Google Scholar] [CrossRef]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User Acceptance of Information Technology: Toward a Unified View. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef]
- Ghinea, D.; Kaczmarczyck, F.; Pullman, J.; Cretin, J.; Kölbl, S.; Misoczki, R.; Picod, J.M.; Invernizzi, L.; Bursztein, E. Hybrid Post-Quantum Signatures in Hardware Security Keys. In Applied Cryptography and Network Security Workshops; Springer: Cham, Switzerland, 2023. [Google Scholar]
- Bonneau, J.; Herley, C.; van Oorschot, P.C.; Stajano, F. The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012; pp. 553–567. [Google Scholar] [CrossRef]
- Itoh, K.; Kanaoka, A. Survey of Services That Store Passwords in a Recoverable Manner. In Proceedings of the HCI for Cybersecurity, Privacy and Trust; Moallem, A., Ed.; Springer: Cham, Switzerland, 2023; pp. 68–77. [Google Scholar] [CrossRef]
- Hao, F.; Ryan, P.Y.A. Password Authenticated Key Exchange by Juggling. In Proceedings of the Security Protocols XVI; Christianson, B., Malcolm, J.A., Matyas, V., Roe, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 159–171. [Google Scholar] [CrossRef]
- Jarecki, S.; Krawczyk, H.; Xu, J. OPAQUE: An Asymmetric PAKE Protocol Secure Against Pre-computation Attacks. In Advances in Cryptology— EUROCRYPT 2018; Nielsen, J.B., Rijmen, V., Eds.; Springer International Publishing: Cham, Switzerland, 2018; Volume 10822, pp. 456–486. [Google Scholar] [CrossRef]
- Lancrenon, J. On Password-Authenticated Key Exchange Security Modeling. In Technology and Practice of Passwords; Stajano, F., Mjølsnes, S.F., Jenkinson, G., Thorsheim, P., Eds.; Springer International Publishing: Cham, Switzerland, 2016; Volume 9551, pp. 120–143. [Google Scholar] [CrossRef]
- Lassak, L.; Markert, P.; Golla, M.; Stobert, E.; Dürmuth, M. A Comparative Long-Term Study of Fallback Authentication Schemes. In Proceedings of the CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 11–16 May 2024; pp. 1–19. [Google Scholar] [CrossRef]
- Regenscheid, A.; Temoshok, D.; LaSalle, C. Incorporating Syncable Authenticators into NIST SP 800-63B: Digital Identity Guidelines—Authentication and Lifecycle Management; Technical Report NIST SP 800-63Bsup1; National Institute of Standards and Technology (U.S.): Gaithersburg, MD, USA, 2024. [CrossRef]




| Literature | Literature Survey | Passkey Focus | Technical Focus | Protocol Focus | Usability Focus |
|---|---|---|---|---|---|
| [1] | x | ||||
| [9] | x | ||||
| [12] | x | ||||
| [13] | x | x | x | ||
| [14] | x | x | x | ||
| [15] | x | ||||
| [8] | x | x | x | x | |
| [16] | x | ||||
| [7] | x | x | |||
| [17] | x | ||||
| [18] | x | ||||
| Our work | x | x | x | x | x |
| No. | Citation |
|---|---|
| 7 | [71] |
| 8 | [6] |
| 9 | [72] |
| 10 | [73] |
| Category | References |
|---|---|
| Technical | [6,13,15,26,29,30,71,73,77,78,79,80,81,82] |
| Usability | [6,8,11,12,13,17,27,28,42,45,48,69,71,79,82,83,84,85,86,87,88] |
| User Perception | [7,11,16,27,42,48,73,79,80,82,84,86,88,89,90] |
| Category | References |
|---|---|
| Technical | [8,16,26,31,39,72,77,91,92,93] |
| Usability | [10,27,45,70,94] |
| User Perception | [7,14,89] |
| Category | Improvement | Challenges |
|---|---|---|
| Technical | 3 | 2 |
| Usability | 3 | 1 |
| User Perception | 1 | 3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Matzen, A.; Rüffer, A.; Byllemos, M.; Heine, O.; Papaioannou, M.; Choudhary, G.; Dragoni, N. Challenges and Potential Improvements for Passkey Adoption—A Literature Review with a User-Centric Perspective. Appl. Sci. 2025, 15, 4414. https://doi.org/10.3390/app15084414
Matzen A, Rüffer A, Byllemos M, Heine O, Papaioannou M, Choudhary G, Dragoni N. Challenges and Potential Improvements for Passkey Adoption—A Literature Review with a User-Centric Perspective. Applied Sciences. 2025; 15(8):4414. https://doi.org/10.3390/app15084414
Chicago/Turabian StyleMatzen, Alexander, Artur Rüffer, Marcus Byllemos, Oliver Heine, Maria Papaioannou, Gaurav Choudhary, and Nicola Dragoni. 2025. "Challenges and Potential Improvements for Passkey Adoption—A Literature Review with a User-Centric Perspective" Applied Sciences 15, no. 8: 4414. https://doi.org/10.3390/app15084414
APA StyleMatzen, A., Rüffer, A., Byllemos, M., Heine, O., Papaioannou, M., Choudhary, G., & Dragoni, N. (2025). Challenges and Potential Improvements for Passkey Adoption—A Literature Review with a User-Centric Perspective. Applied Sciences, 15(8), 4414. https://doi.org/10.3390/app15084414










