Verifiable Key-Aggregate Searchable Encryption Scheme for Fog-Based Internet of Autonomous Vehicles
Abstract
1. Introduction
- We utilize smart contracts , oblivious search inquiries, and key search encryption (KSE) to develop a Multi-Key Access (MKA) scheme. The aggregation of secure keys and the generation of trapdoors for permitted data retrieval (denoted as ) can be accomplished by integrating KSE with an . The leakage of k information related to is effectively mitigated through the use of oblivious search requests.
- A dual-verifiable technique is also developed by our team, which utilizes two homomorphic hash functions and their properties. This approach enables the effective verification of the overall search outcome. Additionally, this method notably decreases the communication and computational costs through collaborative confirmation. Additionally, bilinear pairing is not employed in the dual-verifiable algorithm.
- We validate the suggested system and perform a thorough security study, showcasing its strong security features. Additionally, we conduct comprehensive testing to assess its performance, demonstrating its effectiveness in terms of processing and transmission expenses.
2. Related Work
3. Preliminaries
3.1. Cryptographic Assumptions
3.2. Dual-Verifiable Encryption
- Key Enter the files amounts (n) for n files , and generate key using homomorphic hash .
- AggKey : This algorithm generates the aggregate key () after receiving as inputs the amount of files (n) and key .
- Encrypt . This algorithm generates n ciphertexts () and an aggregated ciphertext (), obtaining n files () and two homomorphic hashes ( and ).
- Verify : Initially, this method determines if . Environmental data ciphertexts () are accurate if this equation is true. Then, it decrypts using key , yielding decrypted data (). Additionally, it determines whether . This equation indicates that several files have not been altered if it is correct. It returns the original data () at the end.
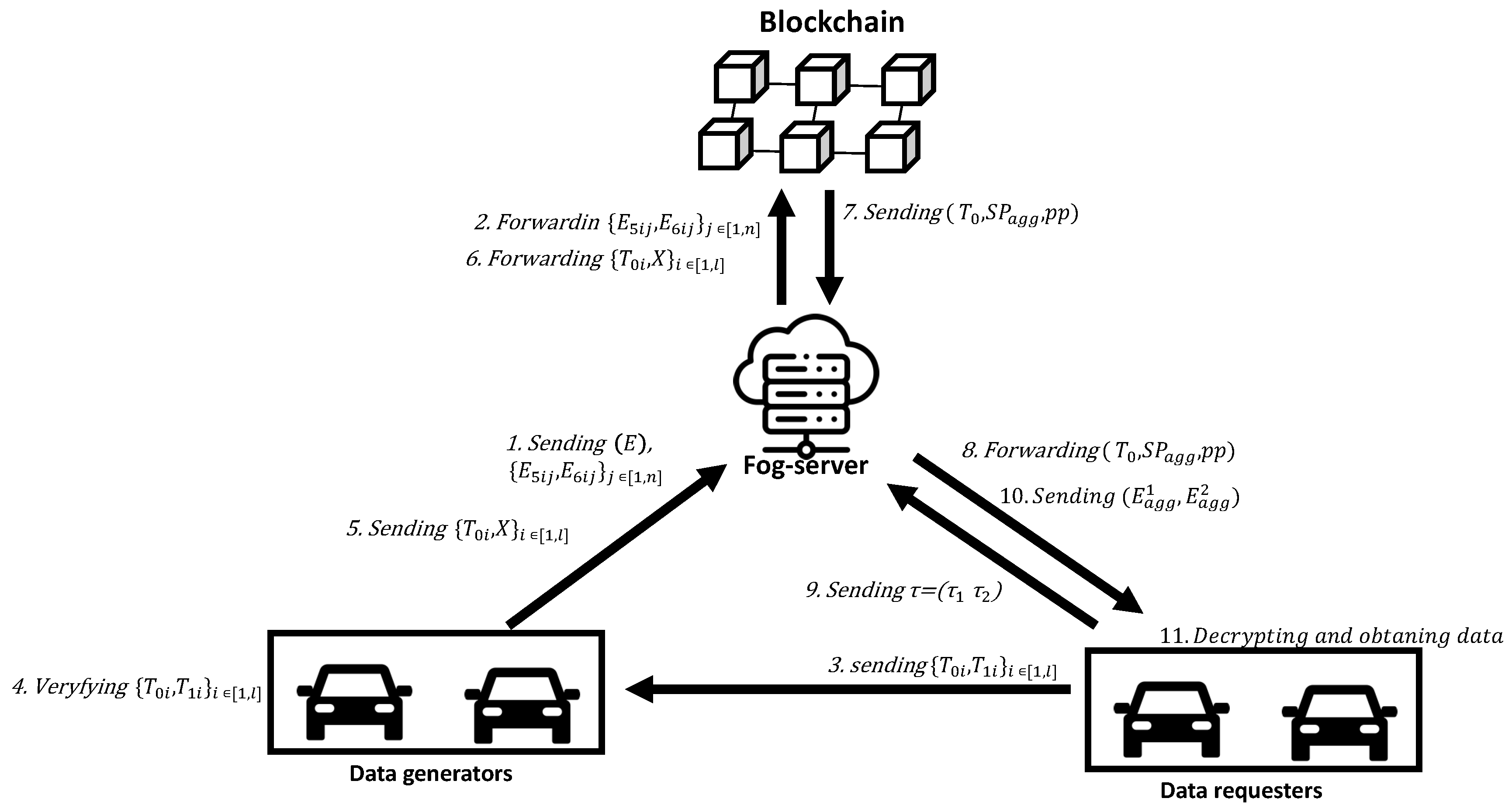
3.3. System Model
- Data generators () are conceptualized as entities that interact with sensors to produce environmental sensing data. To generate environmental data ciphertexts and k ciphertexts, encrypts various types of environmental data using distinct keys and their associated k. Subsequently, the FS receives these ciphertexts to share environmental information with . Additionally, the keyword-encrypted data are added to the blockchain for future processing.
- Vehicle insurance companies are among the entities requesting access to environmental data on automobiles. While maintaining the confidentiality of the search term, the requester transmits search requests to the data guardian, along with a token and supporting evidence. The data guardians are provided with proof to verify that the k is part of the approved k set. Once the proof is successfully verified, the data guardians transmit permission to the blockchain. To conduct searches for the desired terms, the requester can utilize the blockchain to access a search trapdoor. Additionally, the requester can confirm the accuracy of the decrypted environmental data and the precision of the encrypted environmental data retrieved from the file system.
- The responsibility of maintaining encrypted environmental data and the corresponding k ciphertexts transmitted by lies with the fog server (FS). Additionally, it is accountable for providing search services.
- Smart contracts are implemented using blockchain technology. The Aggregate Smart Contract (ASC) refers to the blockchain . The ASC performs three primary functions: creating a search trapdoor for approved s, combining the various keys from s, and collecting keys from environmental data.
3.4. Security Threats
3.5. Security Goals
4. Proposed Scheme
4.1. Overview
4.2. Details of the Proposed Scheme
- A bilinear pairing mapping and an additive group () are chosen so that . A multiplicative group is represented by . Keep in mind that the order number (q) is the same for .
- A point generator () and the number (n) of secret keys () are selected to compute for , where n is the maximum limit of stored files.
- Two homomorphic hash algorithms ( and ) and a collision-resistant hash algorithm () are selected.
- n keywords are generated ().
Registration
- Data generators registration. Each generates its key pair, where is a public key and is a private key.
- Data requester registration. Each generates its key pair, where is a public key and is a private key.
5. Security Analysis
5.1. Secure Search
5.2. Accountability
5.3. Decryption
5.4. Access Control
5.5. Requester Privacy
6. Performance Evaluation
6.1. Comparison of Security Properties
6.2. Communication Overhead
6.3. Computational Cost
6.4. Smart Contract Time Consumption
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Basudan, S.; Lin, X.; Sankaranarayanan, K. A privacy-preserving vehicular crowdsensing-based road surface condition monitoring system using fog computing. IEEE Internet Things J. 2017, 4, 772–782. [Google Scholar] [CrossRef]
- Al-Jaburi, L.R.; Fadare, O.A.; Al-Turjman, F. Integrated AI Architecture and Fog Computing for Cyber-Physical Systems Autonomous Vehicles. In Smart Infrastructures in the IoT Era; Springer: Berlin, Germany, 2025; pp. 969–983. [Google Scholar]
- Li, C.; Dong, M.; Xin, X.; Li, J.; Chen, X.B.; Ota, K. Efficient privacy-preserving in IoMT with blockchain and lightweight secret sharing. IEEE Internet Things J. 2023, 10, 22051–22064. [Google Scholar] [CrossRef]
- Biswas, A.; Wang, H.C. Autonomous vehicles enabled by the integration of IoT, edge intelligence, 5G, and blockchain. Sensors 2023, 23, 1963. [Google Scholar] [CrossRef] [PubMed]
- Yin, H.; Zhang, W.; Deng, H.; Qin, Z.; Li, K. An attribute-based searchable encryption scheme for cloud-assisted IIoT. IEEE Internet Things J. 2023, 10, 11014–11023. [Google Scholar] [CrossRef]
- Srirama, S.N. A decade of research in fog computing: Relevance, challenges, and future directions. Softw. Pract. Exp. 2024, 54, 3–23. [Google Scholar] [CrossRef]
- Lee, J.; Kim, M.; Oh, J.; Park, Y.; Park, K.; Noh, S. A secure key aggregate searchable encryption with multi delegation in cloud data sharing service. Appl. Sci. 2021, 11, 8841. [Google Scholar] [CrossRef]
- Deng, L.; Wang, T.; Feng, S.; Qu, Y.; Li, S. Secure identity-based designated verifier anonymous aggregate signature scheme suitable for smart grids. IEEE Internet Things J. 2022, 10, 57–65. [Google Scholar] [CrossRef]
- Basudan, S.; Alamer, A. Efficient Privacy-preserving Range Query with Leakage Suppressed for Encrypted Data in Cloud-based Internet of Things. IEEE Access 2024, 12, 187652–187664. [Google Scholar] [CrossRef]
- Basudan, S. IPFS-blockchain-based delegation model for internet of medical robotics things telesurgery system. Connect. Sci. 2024, 36, 2367549. [Google Scholar] [CrossRef]
- Alamer, A.; Basudan, S. A security and privacy-preserving accessing data protocol in vehicular crowdsensing using blockchain. In Proceedings of the Seventh International Congress on Information and Communication Technology: ICICT 2022, London, Volume 2; Springer: Singapore, 2022; pp. 315–327. [Google Scholar]
- Jiang, Z.; Guo, X.; Yu, T.; Zhou, H.; Wen, J.; Wu, Z. Private Set Intersection Based on Lightweight Oblivious Key-Value Storage Structure. Symmetry 2023, 15, 2083. [Google Scholar] [CrossRef]
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
- Liu, J.; Zhao, B.; Qin, J.; Hou, X.; Ma, J. Key-aggregate searchable encryption supporting conjunctive queries for flexible data sharing in the cloud. Inf. Sci. 2023, 645, 119336. [Google Scholar] [CrossRef]
- Wen, J.; Li, H.; Liu, L.; Lan, C. Enhancing Security and Efficiency: A Fine-Grained Searchable Scheme for Encryption of Big Data in Cloud-Based Smart Grids. Mathematics 2024, 12, 1512. [Google Scholar] [CrossRef]
- Pareek, G.; Purushothama, B. A Practical and Efficient Key-Aggregate Cryptosystem for Dynamic Access Control in Cloud Storage. In Proceedings of the International Conference on Distributed Computing and Intelligent Technology; Springer Nature: Cham, Switzerland, 2024; pp. 133–148. [Google Scholar]
- Wang, Y.; Miao, Y.; Li, X.; Leng, T.; Liu, Z.; Liu, X.; Choo, K.K.R.; Deng, R.H. Efficient Homomorphic Encryption-Based Secure Search in Multi-owner Setting for Internet of Things (IoT). IEEE Internet Things J. 2024. Early Access. [Google Scholar] [CrossRef]
- Trivedi, H.S.; Patel, S.J. Key-aggregate searchable encryption with multi-user authorization and keyword untraceability for distributed IoT healthcare systems. Trans. Emerg. Telecommun. Technol. 2023, 34, e4734. [Google Scholar] [CrossRef]
- Liu, J.; Wei, Z.; Qin, J.; Zhao, B.; Ma, J. Verifiable key-aggregate searchable encryption with a designated server in multi-owner setting. IEEE Trans. Serv. Comput. 2023, 16, 4233–4247. [Google Scholar] [CrossRef]
- Yin, H.; Zhao, Y.; Zhang, L.; Qiao, B.; Chen, W.; Wang, H. Attribute-based searchable encryption with decentralized key management for healthcare data sharing. J. Syst. Archit. 2024, 148, 103081. [Google Scholar] [CrossRef]
- Li, J.; Wang, X.; Gan, Q. Verifiable Data Search with Fine-Grained Authorization in Edge Computing. Secur. Commun. Netw. 2022, 2022, 4252466. [Google Scholar] [CrossRef]
- Long, W.; Zeng, J.; Wu, Y.; Gao, Y.; Zhang, H. A Certificateless Verifiable Bilinear Pair-Free Conjunctive Keyword Search Encryption Scheme for IoMT. Electronics 2024, 13, 1449. [Google Scholar] [CrossRef]
- Liu, X.; Yang, X.; Luo, Y.; Zhang, Q. Verifiable multikeyword search encryption scheme with anonymous key generation for medical internet of things. IEEE Internet Things J. 2021, 9, 22315–22326. [Google Scholar] [CrossRef]
- Ali, A.; Almaiah, M.A.; Hajjej, F.; Pasha, M.F.; Fang, O.H.; Khan, R.; Teo, J.; Zakarya, M. An industrial IoT-based blockchain-enabled secure searchable encryption approach for healthcare systems using neural network. Sensors 2022, 22, 572. [Google Scholar] [CrossRef]
- Oh, J.; Lee, J.; Kim, M.; Park, Y.; Park, K.; Noh, S. A secure data sharing based on key aggregate searchable encryption in fog-enabled IoT environment. IEEE Trans. Netw. Sci. Eng. 2022, 9, 4468–4481. [Google Scholar] [CrossRef]
- Wang, H.; Ning, J.; Huang, X.; Wei, G.; Poh, G.S.; Liu, X. Secure fine-grained encrypted keyword search for e-healthcare cloud. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1307–1319. [Google Scholar] [CrossRef]
| Notation | Description |
|---|---|
| The additive group | |
| The multiplicative group | |
| P | The generator of |
| The public system parameter | |
| The data generator | |
| The data requester | |
| The public key for the data generator | |
| The private key for the data generator | |
| E | The environmental data ciphertexts |
| k | Keyword ciphertexts |
| The token generated by the data generator | |
| A keyword proof created by the data generator | |
| The aggregated searchable and symmetric key | |
| The trapdoor created by the aggregation smart contract | |
| The encrypted symmetric key created by the aggregation smart contract |
| Property | Ali et al. [24] | Liu et al. [19] | Haijiang et al. [26] | Jihyeon et al. [25] | Proposed |
|---|---|---|---|---|---|
| Secure search | √ | √ | √ | √ | √ |
| Accountability | × | × | × | × | √ |
| Access control | √ | √ | √ | √ | √ |
| Requester privacy | × | × | × | × | √ |
| Key-leakage resistance | √ | √ | × | √ | √ |
| Dual verifiable search | × | × | × | × | √ |
| Scheme | Aggregate | Trapdoor | Searching | Encryption |
|---|---|---|---|---|
| Liu et al. [19] | ||||
| Jihyeon et al. [25] | ||||
| Proposed scheme |
| Algorithm | Trapdoor | Search | Encryption | Encryption |
|---|---|---|---|---|
| and | 27 | 53 | 5160 | 9 |
| and | 27 | 53 | 5160 | 9 |
| Metric | Key Extract | Key Aggregate | Trapdoor Aggregate |
|---|---|---|---|
| Transaction size (bytes) | 560 | 57 | 27 |
| Execution time (ms) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Basudan, S.; Alamer, A. Verifiable Key-Aggregate Searchable Encryption Scheme for Fog-Based Internet of Autonomous Vehicles. Appl. Sci. 2025, 15, 3081. https://doi.org/10.3390/app15063081
Basudan S, Alamer A. Verifiable Key-Aggregate Searchable Encryption Scheme for Fog-Based Internet of Autonomous Vehicles. Applied Sciences. 2025; 15(6):3081. https://doi.org/10.3390/app15063081
Chicago/Turabian StyleBasudan, Sultan, and Abdulrahman Alamer. 2025. "Verifiable Key-Aggregate Searchable Encryption Scheme for Fog-Based Internet of Autonomous Vehicles" Applied Sciences 15, no. 6: 3081. https://doi.org/10.3390/app15063081
APA StyleBasudan, S., & Alamer, A. (2025). Verifiable Key-Aggregate Searchable Encryption Scheme for Fog-Based Internet of Autonomous Vehicles. Applied Sciences, 15(6), 3081. https://doi.org/10.3390/app15063081







