1. Introduction
Driven by the rapid development of big data, artificial intelligence and other technologies, human society has entered the era of digital economy, and data have become a basic strategic resource and an important factor of production related to the political, economic, military, social and cultural development of the country. With the continuous generation and aggregation of data, the asset attributes of data are becoming more and more prominent, and are gradually becoming a new type of asset [
1,
2].
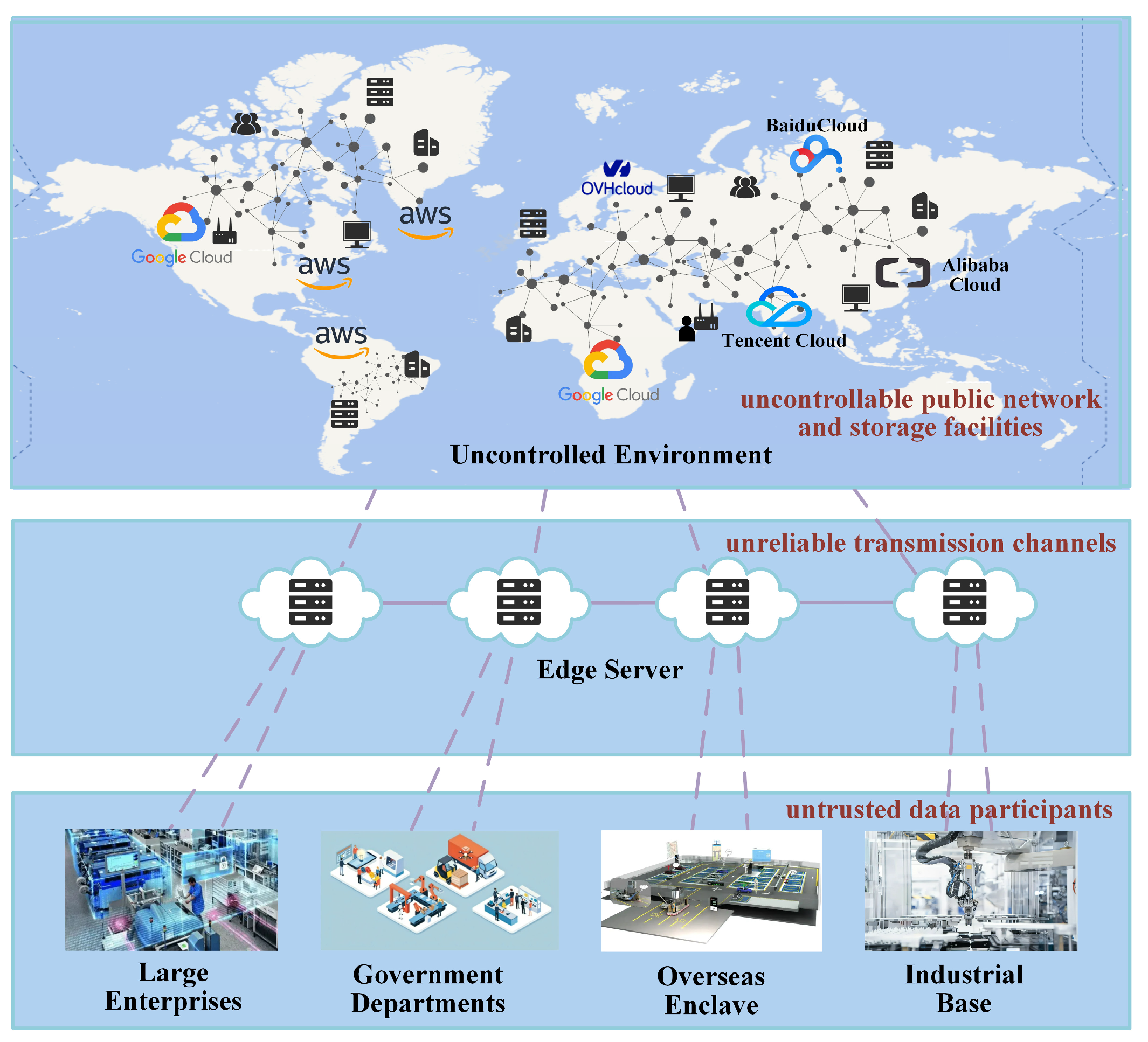
From the asset point of view, the value of data statically stored locally is very limited, and the asset value of the data is reflected in the use of the data. Furthermore, the asset value of data is not only in aggregation and analysis, but also in sharing and circulation. However, when data assets are shared and circulated across borders and domains, they are usually in an uncontrolled environment (such as third-party data storage platforms, data outsourcing service companies, public transmission networks, etc.), as shown in
Figure 1. With the continuous enrichment of network attack means, the life cycle security risks of data asset production, storage, exchange, processing, return and destruction are aggravated due to the uncontrollable public network and storage facilities, untrusted data participants and unreliable transmission channels in the process of cross-border cross-domain sharing and circulation of data assets. The security operation ability of data assets has increasingly become an important part of the core competence of enterprises.
Faced with massive highly sensitive and high-value data assets, there are many problems in current security protection methods [
3]. First, the security risks faced by data asset protection are more complex and diverse than traditional information system security, the existing technical means mainly solve a single problem, through the deployment of security protection measures to ensure the security of the business system, thus forming a number of security protection islands, which not only increase the difficulty of security management, but also lack a systematic security protection ability. Second, the sharing and circulation of data assets is a difficulty and key link of security protection. It is necessary to ensure that there is no disclosure, as well as privacy and compliance in the process of circulation. At the same time, once there are security issues such as data leakage and privacy disclosure, we must be able to trace back to the risk points and those responsible. In addition, it is necessary to ensure that the ownership, right to use and control of data and data assets are clearly defined and confirmed, but it is difficult for the security protection ability of the existing technology to ensure prior supervision and solid verification in the matter and traceability after the event. Third, the security protection of massive data itself is a kind of high-density complex calculation, which necessitates greater requirements for the performance of security means. Although conventional security means can be extended by stacking, they bring the performance burden to the protected business system and increase its running costs.
Based on the above analysis, this paper focuses on the security risks faced by the sharing and circulation of data assets in an uncontrolled environment, and on the security requirements of four key scenarios: outsourcing storage, multi-party sharing, trusted operation and cross-domain return. This paper establishes a security protection model of data assets throughout their life cycle, with cryptography technology as the core, and designs a security technical framework that runs through each link of data asset sharing and circulation. In addition, an architecture design scheme of data asset security sharing and a circulation system based on cryptography service technology is proposed.
The main contributions of this paper are as follows.
A security protection model for the whole life cycle of data assets is established, which is closely adapted to flexible and complex business scenarios, and provides a theoretical basis for the design of data asset sharing and circulation security technology framework and system architecture.
A security technical framework covering the whole life cycle of data asset sharing and circulation is designed, which covers all the links of data asset production, storage, exchange, processing, return and destruction, and provides omni-directional technical protection for the secure sharing and circulation of data assets.
An architecture design scheme of data asset security sharing and circulation system based on cryptography service technology is proposed, based on the design ideas of refactoring, modularization, scalability and high availability. Micro-service and container technology are introduced to split the security protection function of data assets, which can quickly realize on-demand deployment, flexible access and dynamic adjustment.
The remaining chapters of this paper are composed as follows.
Section 2 discusses the progress of the relevant research work in detail.
Section 3 focuses on the security requirements of data assets in four key scenarios: outsourcing storage, multi-party sharing, trusted operation and cross-domain return. This section also establishes the security protection model of data assets in the whole life cycle.
Section 4 introduces in detail the security technology system of data asset sharing and circulation based on a password.
Section 5 introduces in detail the architecture design of data asset security sharing and circulation system based on cryptography service technology.
Section 6 describes the implementation results of the system and compares them with the functions proposed in other related papers.
Section 7 summarizes the work of the full text.
2. Related Works
In recent years, data asset protection technology has attracted the attention of a large number of scientific research institutions and enterprises. Researchers have carried out relevant research and made some progress in the confirmation of data assets, outsourcing storage, operation trusted management and security return.
Regarding the aspect of confirming the right of data assets, the access control and authentication method based on attributes is mainly used to solve the problems of unclear boundary of ownership, authority management lacking in detail and difficult-to-trace operation behavior in the process of data asset circulation in uncontrolled environments. The Technical Committee on Network Security of the European Telecommunications Standards Institute has developed an attribute-based access control scheme [
4]. Yao et al. proposed a novel framework that combines federated learning and blockchain by Shapley value (FLBS) to achieve a good trade-off between privacy and fairness [
5].
Regarding the aspect of data asset security outsourcing storage, aiming at the risk of leakage, tampering and damage of data asset outsourcing cloud storage processes in uncontrolled environments, the data storage method of an encryption model and the cleaning and weight removal method oriented to data characteristics are mainly adopted. Large foreign companies such as IBM use data security storage systems based on encryption models [
6]. In order to solve the problem that it is difficult to provide high confidentiality protection for users’ outsourced data in a cloud storage environment, Song et al. proposed a scheme of hierarchical encryption and de-gravity of data from the point of view of data confidentiality itself [
7]. This scheme realizes the hierarchical encryption of data without introducing any third party and does not need online assistance of users, but the efficiency and security and reliability of data outsourcing encryption storage still need to be improved.
Regarding the aspect of trusted management of data asset operation, aiming at the requirements of compliance judgment, traceability and audit of data operation, the compliance judgment method based on blockchain is mainly adopted. He et al. [
8] summarized the existing Ethereum smart contract security audit methods and compare several mainstream audit tools from various perspectives. Zhang et al. [
9] proposed a blockchain-based dynamic data auditing scheme with strong timeliness to ensure that data stored in outsourcing storage systems remain intact, but the fragmentation identification ability of data assets and the fineness of secure operation management still need to be improved.
Regarding the aspect of data asset security return, for cross-border, cross-domain data transmission that can be easily monitored, blocked, intercepted and traced back to the source and other security threats, the main methods are covert communication and the use of public networks for information-hiding transmission [
10,
11]. Some scholars have carried out research into the aspects of information-hiding capacity measurement, anti-file lossy processing information hiding schemes, single-layer encryption and single-hop forwarding, multi-layer encryption and multi-hop forwarding channel construction, and so on [
12,
13], and have realized the construction of high-rate and high-security hidden channels, but the deployment complexity and flexibility of the hidden channel construction method still need to be improved.
Generally speaking, data asset protection in the current uncontrolled environment lacks an overall solution, which is mainly aimed at a link in the process of the secure circulation of highly sensitive and high-value data assets, and cannot protect the whole life cycle of data asset circulation. In view of the basic scientific problems of data asset protection in uncontrolled environments, it is urgently required to strengthen the systematic research on data asset protection systems, fine confirmation rights, secure outsourcing storage and operation trusted management, and to secure returns in uncontrolled environments.
3. Security Model
Because the cost of data replication is very low relative to the cost of production, the data can easily be copied and disseminated, which results in damage to the rights and interests of the owners of data assets. Therefore, it is necessary to ensure that the ownership, right to use and control of data and data assets are clearly defined and confirmed in the full business chain and life cycle of data asset sharing and circulation, and are effectively guaranteed by technical means and management system.
3.1. Full Life Cycle Model
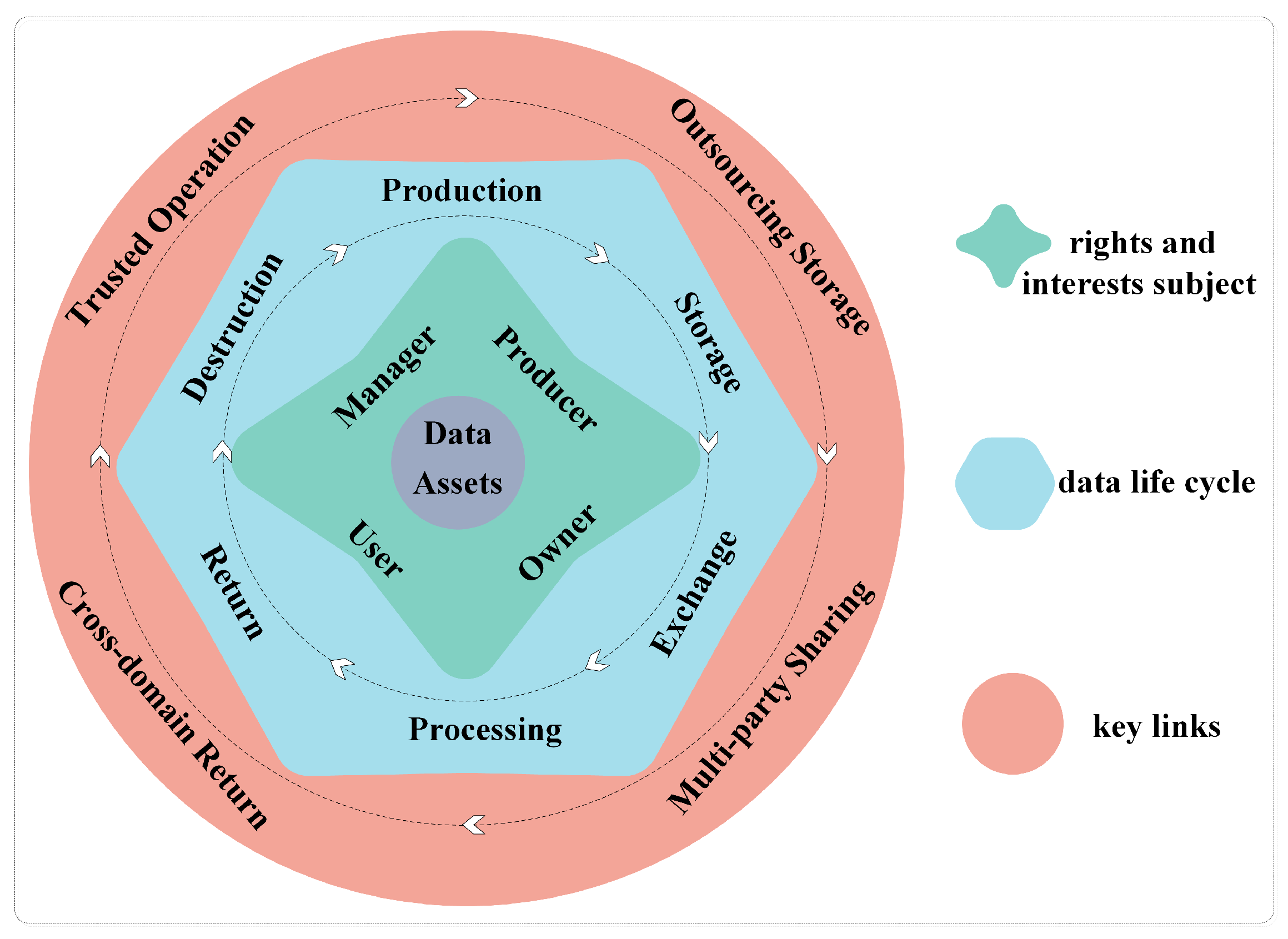
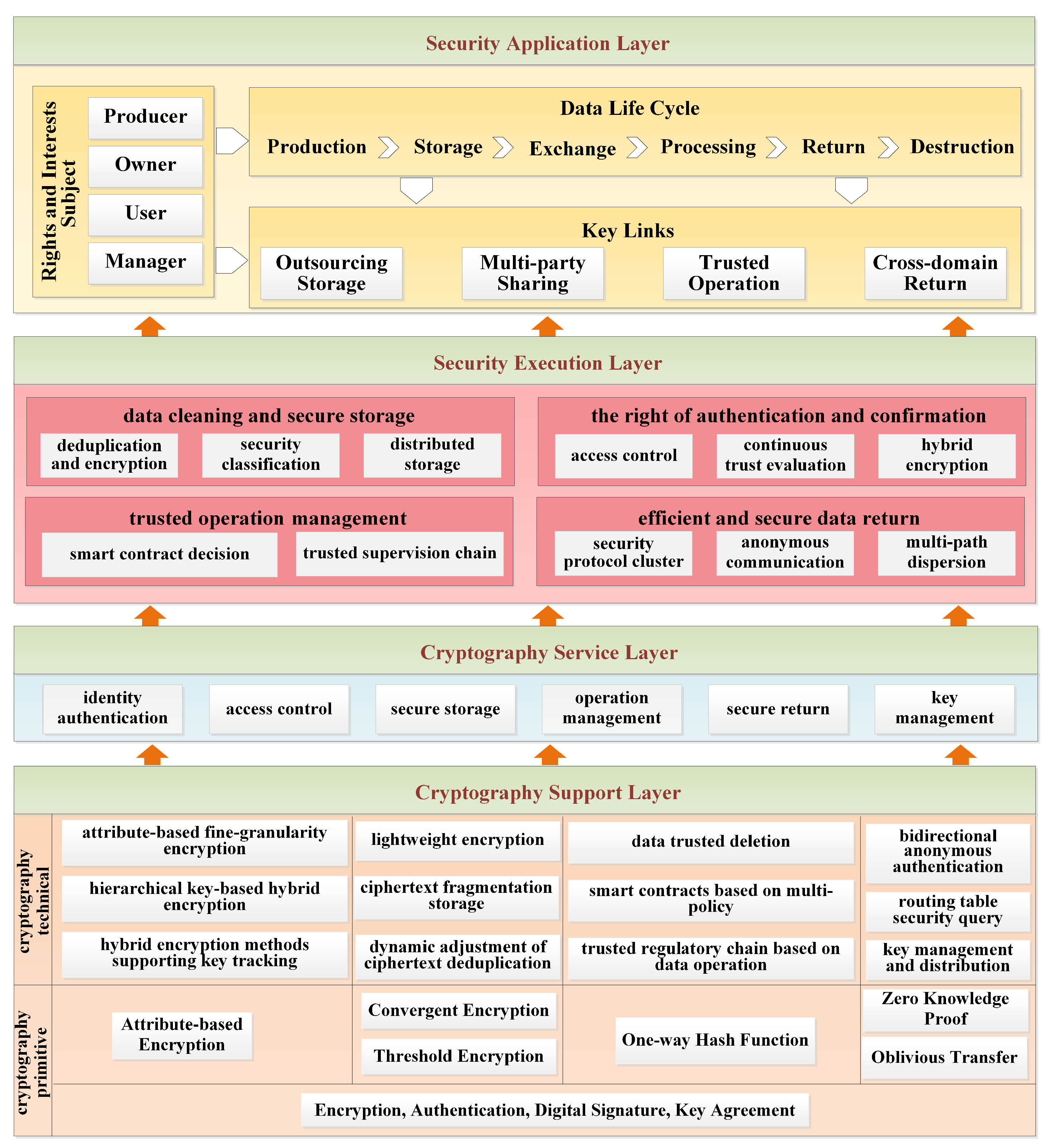
At present, with regard to the definition of the whole life cycle model of data assets, most scholars simply consider the whole life cycle of the data, that is, only consider data acquisition, transmission, storage, use, sharing, destruction and so on. As a special asset, the whole life cycle of data sharing and circulation is determined by multiple dimensions and factors. Therefore, this paper proposes a whole life cycle model of data assets from three dimensions: the rights and interests subject, data life cycle and key links, as shown in
Figure 2.
The subject of rights and interests is involved in the process of the sharing and circulation of data assets. In the whole life cycle of data assets, four kinds of roles are mainly involved: producer, owner, user and manager. A producer refers to the provider of data, which can be a person, system, or equipment, etc. The owner refers to the organization or individual who owns or actually controls the data assets, and may transfer, lease, outsource the data assets, etc. A user refers to an organization or individual who uses the data, who can apply for the data, download data, analyze data, and so on. A manager refers to the organization or individual authorized by the owner to carry out data asset management, but who does not necessarily have ownership of data assets, such as data outsourcing service providers, cloud storage service companies and so on.
The whole life cycle of data involved in the process of data asset sharing and circulation covers the whole life process of data asset production, storage, exchange, processing, return, destruction and so on.
The key links involved in the process of data asset sharing and circulation mainly involve four typical scenarios: outsourcing storage, multi-party sharing, trusted operation and cross-domain return. Outsourcing storage refers to the practice of data asset owners entrusting all or part of the data to third-party service providers for storage, such as cloud storage services, AI training services, and so on. Multi-party sharing refers to the interaction of data between different data asset owners to achieve benefit sharing. Trusted operation means that the data asset has a complete record and deterministic execution result on data deletion, outgoing, copy and modification in the process of circulation. Cross-domain return refers to the return of data distributed in different regions to the data asset center or elsewhere through a transmission channel.
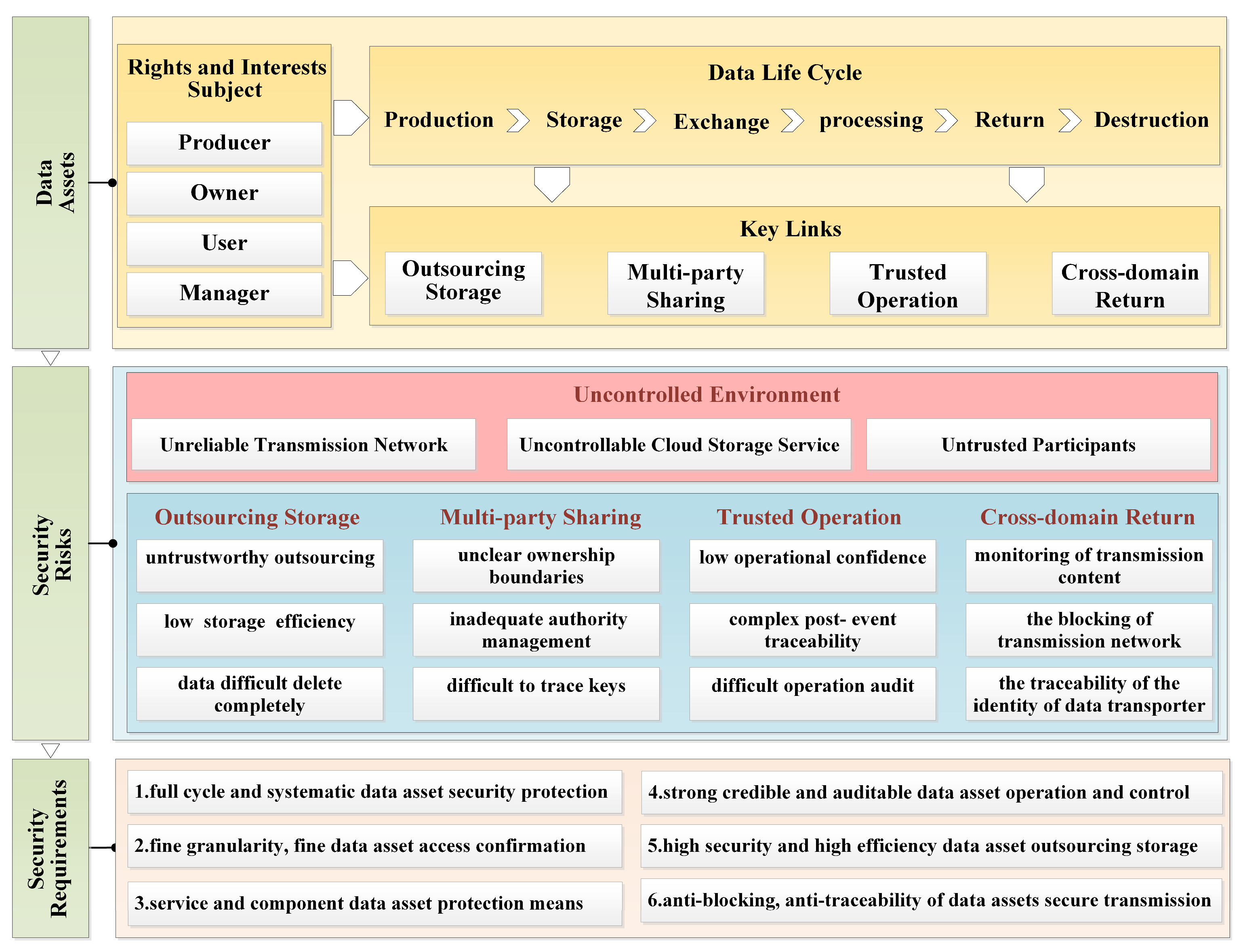
3.2. Security Risks
As shown in
Figure 3, this paper argues that the main security risks in the whole process of data asset sharing and circulation in uncontrolled environments include three levels: unreliable transmission network, uncontrollable cloud storage service and untrusted participants, which can be summarized as follows:
There are many uncontrolled factors and strong countermeasures.
The means of protection are scattered and difficult to implement.
Cloud storage is untrustworthy, and the security is poor.
The storage capacity is limited, and the efficiency is low.
The management means are extensive, and the granularity is coarse.
The confidence level of control is low, and the audit is difficult.
The monitoring and control can easily be blocked, and the risk is high.
The transmission scale is massive, and the rate is low.
Specifically, when data assets are outsourced, they face some security risks, such as untrustworthy outsourcing service providers, low efficiency of outsourced storage, and the difficulty of completely deleting external data. When multi-party sharing is involved, they face security risks such as unclear ownership boundaries of data assets, inadequate authority management, difficult-to-trace keys, etc. When trusted operations are involved, they face security risks such as low operational confidence, complex post- event traceability, difficult operation audit, etc. When transmitting back across domains, they face some security risks, such as the monitoring of transmission content, the blocking of transmission network, the traceability of the identity of the data transporter, and so on.
Therefore, by analyzing the security risks faced by data assets in uncontrolled environments, the new security requirements can be summarized as follows.
Full cycle and systematic data asset security protection.
Fine granularity and fine data asset access confirmation.
Strong credible and auditable data asset operation and control.
Service and component data asset protection means.
High security and high efficiency data asset outsourcing storage.
Anti-blocking, anti-traceability of data assets secure transmission.
Therefore, it is urgently required to establish a security protection model that can protect the different stages of the whole life cycle of data assets, and provide multi-mode and all-rounded systematic protection for the security risks faced by different stages of the whole life cycle of data assets and different operating scenarios.
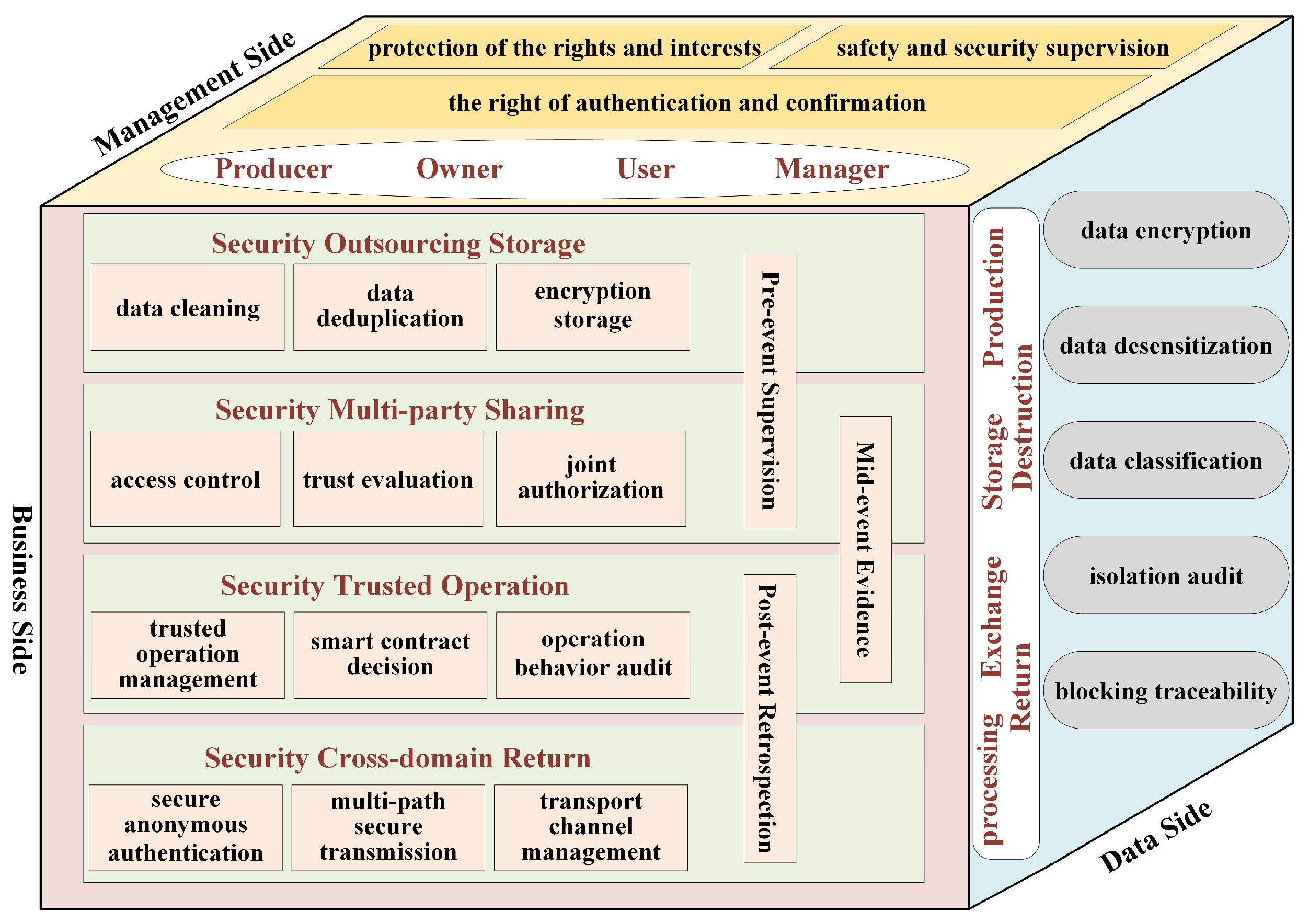
3.3. Security Protection Model
By analyzing the logical loopholes, defense weaknesses and security requirements of data assets in transaction circulation, outsourcing storage, cross-border transmission and so on, this paper aims at covering the protection of rights and interests, circulation control, outsourcing storage, operation trusted management and security return from three dimensions: data asset participation object, whole life cycle stage and key links of operation. The data asset sharing and circulation protection model in an uncontrolled environment is constructed, and the comprehensive security protection ability of data surface, management surface and business surface is formed, as shown in
Figure 4.
On the data side, data protection is an important line of defense of data asset protection system, and it is the basis of the data asset protection model. Combined with the concept of data life cycle, data asset security can be fully guaranteed, and the data asset protection ability can be formed by means of data desensitization, data encryption, data classification, isolation audit, blocking traceability and so on.
On the management side, in the process of the cross-border circulation of data assets, the protection of the rights and interests of producers, owners, users and managers of data assets is fully considered, their respective powers are clear, and the right of authentication is particularly important. At the same time, it is necessary to carry out safety supervision in the process of operation and provide targeted security control means.
On the business side, data asset sharing circulation, that is, data cross-subject circulation, is a difficulty and key link of security protection, which is very important. In the whole process of sharing circulation, we must not only abide to the following rules, “do not leak, no privacy, not exceed limits, comply with the protocol”, but also ensure that upon data leakage, privacy disclosure and other issues, we must have a data traceability mechanism to find the risk point and responsible person to achieve pre-event supervision, mid-event evidence, and post-event retrospection. Specifically, data cleaning, encryption storage, access control, trust evaluation, operation behavior audit, intelligent contract, multi-path secure transmission, secure anonymous authentication and other technical means can be used to realize outsourcing storage security, multi-party sharing security, trusted operation security and cross-domain return security in the whole process of data asset sharing and circulation.
4. Security Technical Framework
Cryptography technology is one of the most effective, reliable and economical key technologies to protect the secure sharing and circulation of data assets. Based on the protection model covering the main security risks and overall requirements of data assets in the whole life cycle, this paper designs a security technical framework that runs through the production, storage, exchange, processing, return and destruction of data assets, as shown in
Figure 5. The security technical framework takes cryptography technology as the core, considering four aspects: cryptography support, cryptography service, security execution and security application. It realizes the protection coverage of transaction circulation, outsourcing storage and cross-border transmission of data assets, and ensures the security of data assets in the process of dynamic sharing and circulation in uncontrolled environments.
4.1. Cryptography Support Layer
Encryption, authentication, digital signature, key agreement and other primitive cryptography methods provide attribute-based fine-granularity encryption, hierarchical key-based hybrid encryption, hybrid encryption methods supporting key tracking, lightweight encryption, ciphertext fragmentation storage, dynamic adjustment of ciphertext deduplication, data trusted deletion, smart contracts based on multi-policies, trusted regulatory chains based on data operation, bidirectional anonymous authentication, routing table security query, key management and distribution, etc. These provide basic cryptography technical support for the whole life cycle security protection of data assets in an uncontrolled environment.
4.2. Cryptography Service Layer
Through the mechanism of micro-service and containerization based on cryptography functions, six basic cryptography services are provided, such as identity authentication, access control, secure storage, operation management, secure return and key management, so as to ensure the whole life cycle security of data assets in uncontrolled environments. In addition, the function of a cryptography service can be adjusted and continuously expanded according to the changes of security protection requirements in the process of data sharing and circulation. In addition to data encryption, it can also provide support for data authentication, data transmission, data storage, data traceability, sharing and utilization.
4.3. Security Execution Layer
Cross-convergence of multiple technologies: In the process of data cleaning and secure storage, clear text cleaning, dense state weight removal, fragmentation storage and other technologies are used to preprocess the file based on data sensitivity, and to improve the dynamic efficiency under different security levels to achieve the balance and optimization of security efficiency. In the precise determination of data assets, attribute-based access control, continuous trust evaluation, hybrid encryption and other technologies are adopted to reduce the correlation between ciphertext and complex policies, improve the accuracy of ownership boundary division, and realize the dynamic binding of attribute permissions. In the trusted management of data operation, the trusted supervision chain of data operation is constructed by using the technology of intelligent contract and blockchain, through reliable contract rule design and efficient contract rule optimization. In the process of efficient and secure data return, anonymous communication and multi-path dispersion technology are adopted, and a high-security protocol cluster is designed to realize the multi-dimensional security protection of traffic characteristics, connection relationship, network topology, information content and user identity in the process of data return transmission. At the same time, the software of secure routing and covert channel construction technology, for rapid deployment, resources on-demand reconstruction of the transmission channel to achieve anti-traceability and tracking of data efficient and secure return.
4.4. Security Application Layer
Through the application of security protection technology to the whole process of the production, storage, exchange, processing, return and destruction of data assets, the systematic protection ability of data asset sharing circulation outsourcing storage, multi-party sharing, trusted operation, cross-domain return and other key links is formed. The protection of each link is related to each other, which is more systematic and has higher protection performance than the stacking of a single technology.
5. System Architecture
At present, there are many problems in the construction mode of cryptography security systems [
14]. Because of the complex application scenario and many security requirements, different types and a large number of cryptography devices and cryptography technologies are introduced to connect various security application services. The direct consequences of the construction mode of this cryptography security system are as follows.
Decentralized deployment of equipment, difficult to manage;
A wide variety of technologies and heavy management workload;
Complex integration of cryptography security applications with existing systems;
Lack of intensive use and scheduling of cryptography security resources;
Lack of cloud computing and edge computing environment;
Lack of quantification of cryptography security services and lack of supervision of applications.
Therefore, it is difficult to meet the requirements of security protection in the process of cross-border cross-domain sharing and circulation of massive data assets.
Based on the above analysis, an architecture design scheme of data asset security sharing and circulation system based on cryptography service technology is proposed. A set of comprehensive security service platform software systems is formed by aggregating and integrating a variety of new cryptography and data security technologies, and a flexible multi-mode service aggregation capability is adopted by way of edge computing, micro-service and capacity deployment. This provides unified management and convenient service for the safe sharing and circulation of data assets in uncontrolled scenarios.
5.1. Architecture Design
Under an uncontrolled environment, the secure sharing and circulation system of data assets needs to establish the basic ability of the dimensions of secure transaction circulation, secure outsourcing storage, secure cross-border transmission and so on, covering all aspects of the whole life cycle of data assets. In addition, factors such as complex and varied usage scenarios, large volume data asset protection, and interaction with business systems should also be taken into account [
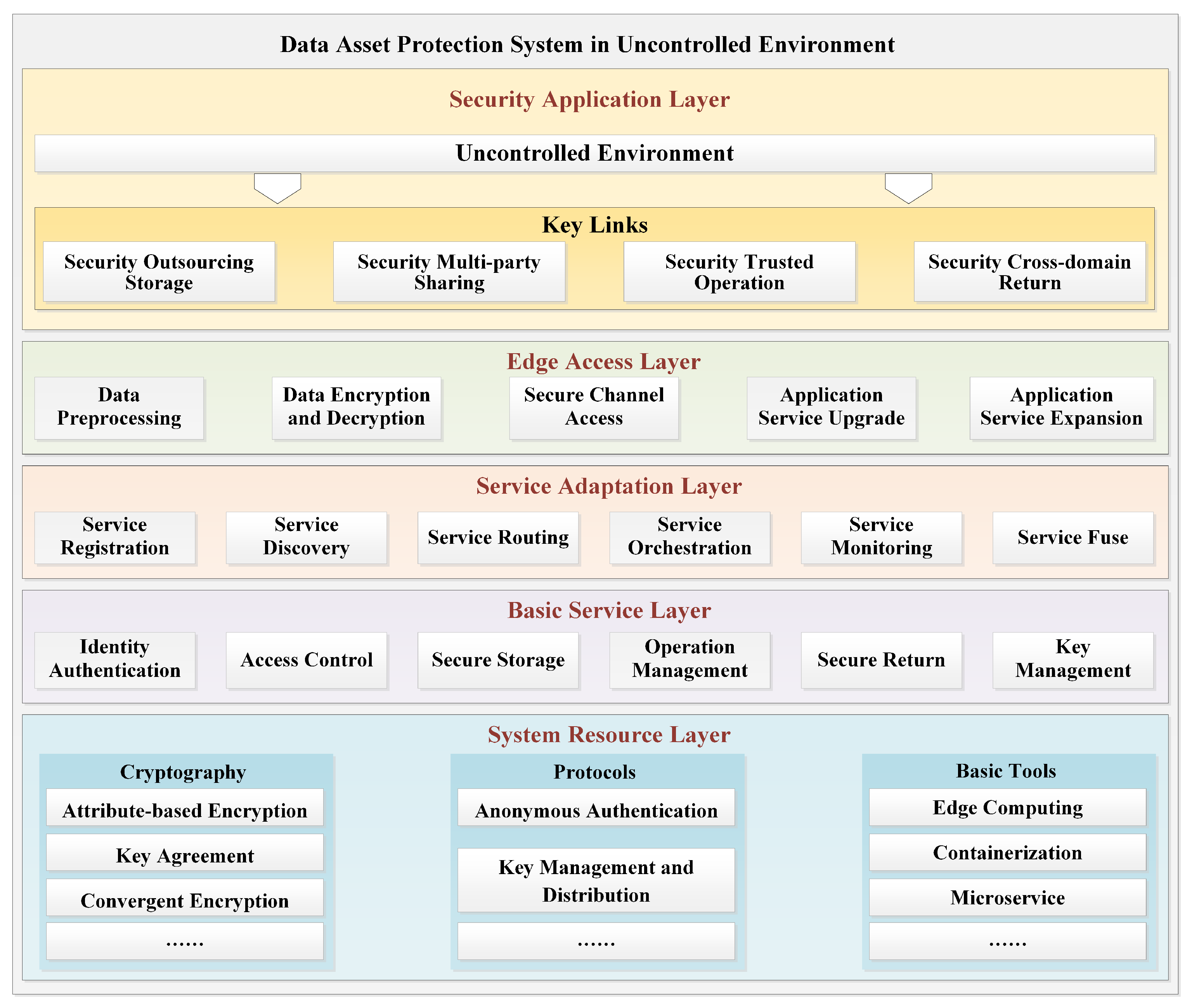
15]. The system proposed in this paper is based on the mechanism of micro-service and containerization of cryptography function, and adopts the cloud edge collaborative deployment mode to form an open system with continuous evolution ability and continuous improvement, which can efficiently connect the business system.
As shown in
Figure 6, the secure data asset sharing and circulation system in an uncontrolled environment is constructed based on micro-service and cloud edge framework. Through the integrated central management and control terminal, the whole process of data assets can be traced and is always in a monitored state. The data transmission channel security, data control security, data storage security and data operation security are realized by means of data security reinforcement. The automatic allocation of equipment is carried out by using the shared circulation task of data assets to realize the security of task control. Personnel-authorized control is used to isolate user rights and manage data, implementing data asset security management. The system platform adopts a hierarchical logic architecture, including an edge access layer, a service adaptation layer, a basic service layer and a system resource layer. The edge access layer is deployed in cluster mode to realize data cleaning, data encryption and decryption, secure channel access, application service upgrade, application service expansion and so on. Based on the construction technology of cryptography security service platform for uncontrolled environments, the service adaptation layer is mainly responsible for the arrangement and scheduling of all kinds of security services, including service registration, service discovery, service routing, service orchestration, service monitoring and so on. The basic service layer provides key data security services, including identity authentication, access control, secure storage, operation management, secure return, key management and other cryptography service modules. The system resource layer is mainly responsible for the centralized management of all kinds of security resource libraries on the platform, as well as unified access to the security algorithm library and security protocol library through the construction of resource management services.
5.2. Service Applications
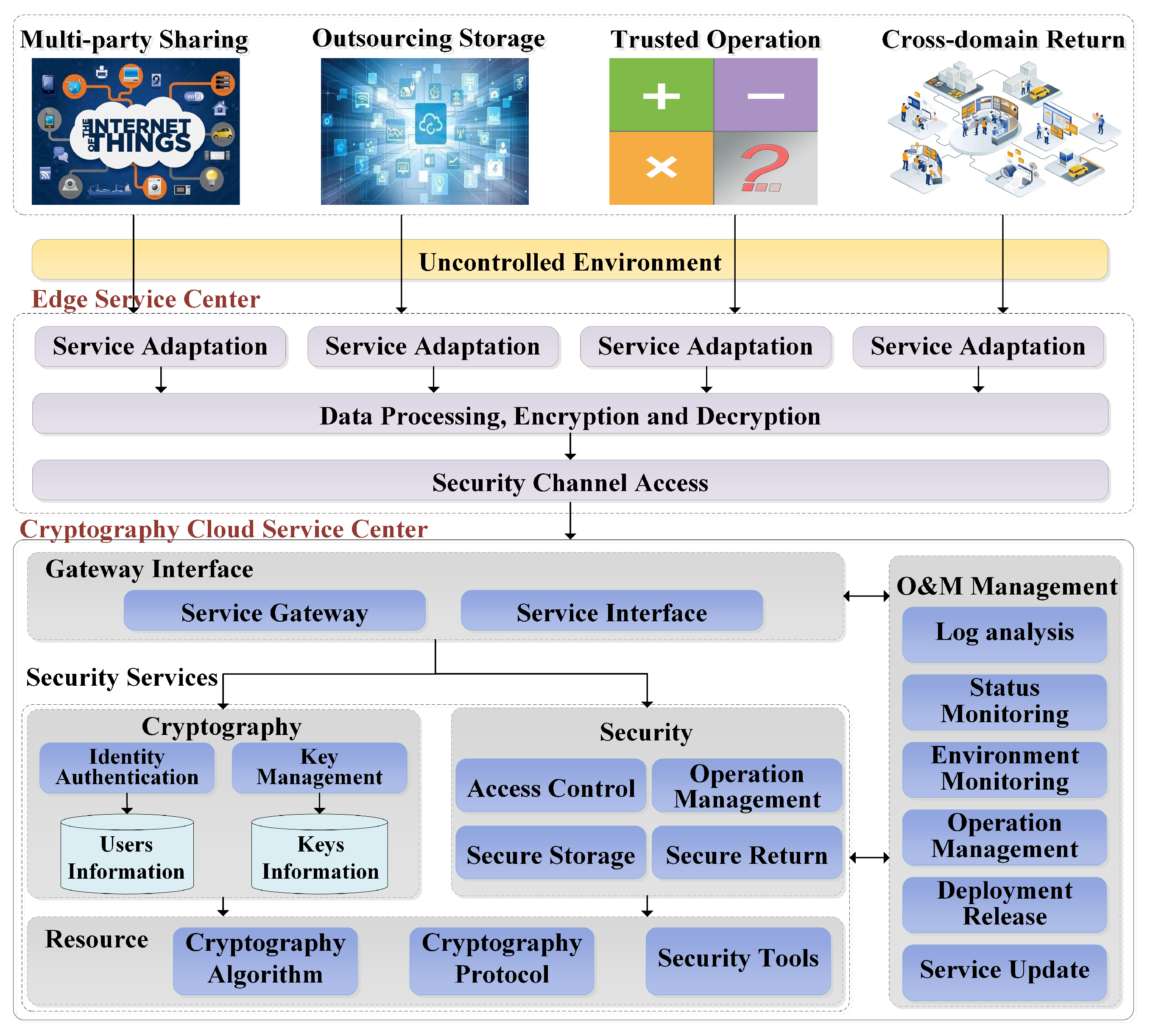
In an uncontrolled environment, the secure data asset sharing and circulation system provides multi-class cryptography services to the external application business system by deploying the edge server. As shown in
Figure 7, based on the service-oriented architecture, the cryptography cloud service center is constructed, and the security service components such as cryptography are provided to realize the unified management of security control service. Based on security API and other technologies, a unified security API is constructed to realize the security authorization and standardized management of security service requirements. Based on the dynamic refactoring architecture, the edge security gateway is constructed to realize load balancing, on-demand configuration and secure stealth edge security control. Based on the edge computing mode, the new edge service is constructed to realize the fast adaptation between the protection system and the protected business system.
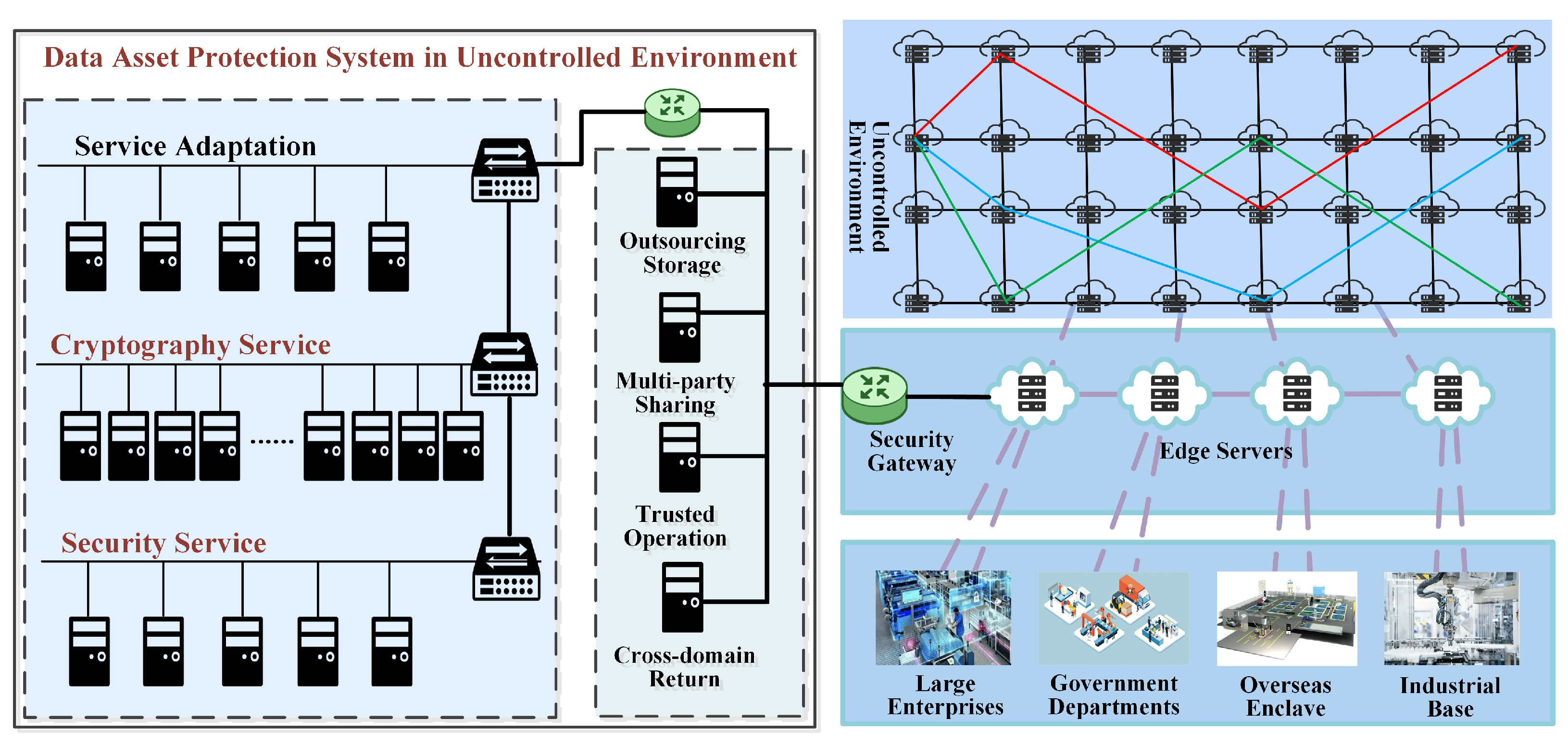
5.3. System Deployment
The secure data asset sharing and circulation system is generally deployed according to cloud-edge-end architecture. As shown in
Figure 8, the cryptography service cloud center deployed in the cloud provides security protection business functions in the form of service, including identity authentication, access control, secure storage, operation management, security return, key management and other cryptography services, which are called directly by users according to the interface rules of RESTful API. The service center deployed at the edge is connected with the cryptography cloud service center and the protected data asset business system through the security gateway, and provides security services such as outsourcing storage, flow control, trusted operation, cross-domain return and so on in the process of data asset sharing and circulation. The security gateway deployed on the end side is connected with the cloud and edge control services through the built-in agent to realize the security requirement response and security service installation of the protected data asset business system.
6. System Implementation
The data asset security sharing and circulation system designed in this paper uses Java as the main program development tool, MySQL as the main database tool, and Amap as the system visualization base map. By designing a security-outsourcing storage module, a security multi-party-sharing module, a security trusted operation module and a security cross-domain return module, the security protection and visual analysis of data assets in the process of transaction circulation, outsourcing storage and cross-border transmission are realized.
6.1. Security Outsourcing Storage Module
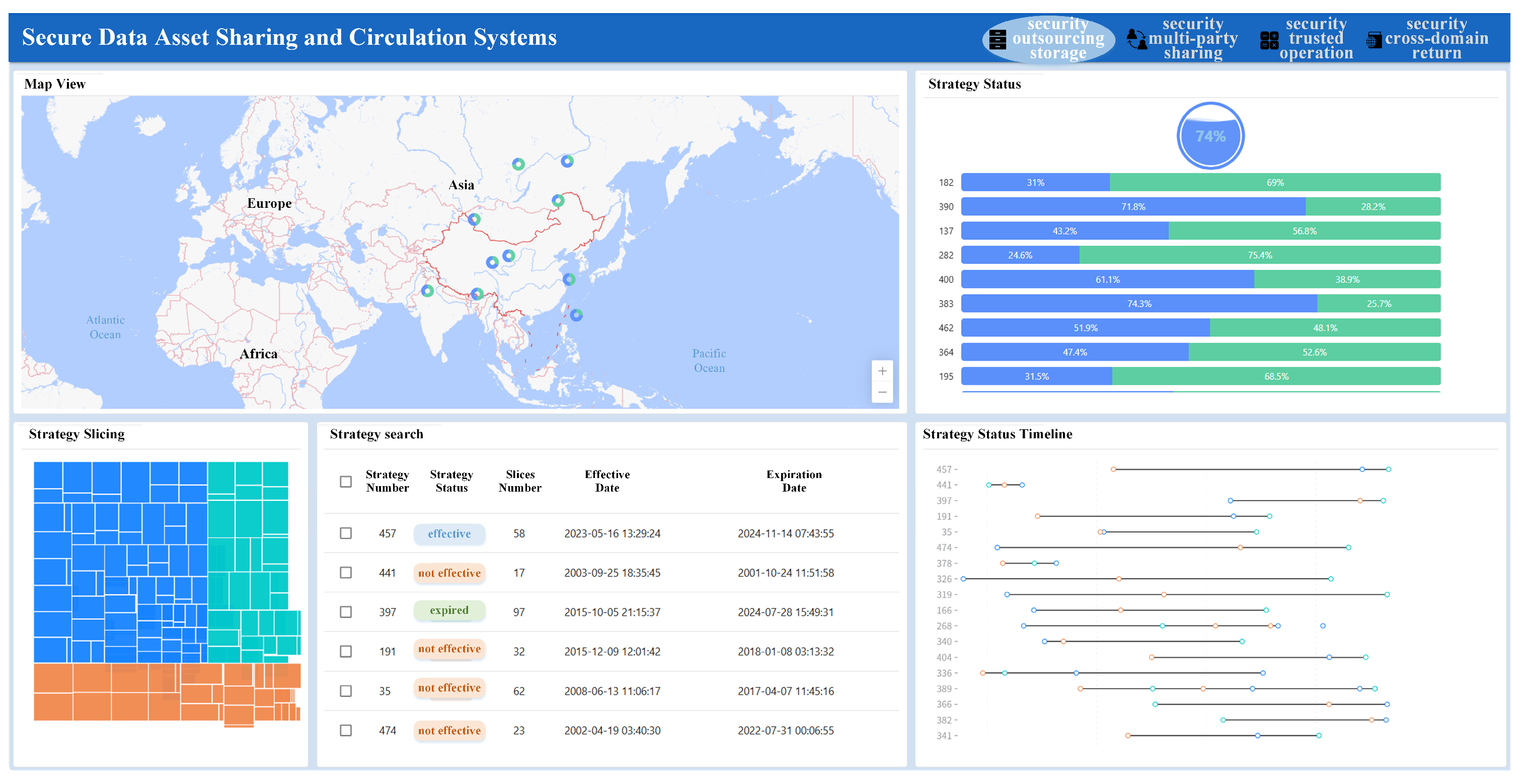
In the security outsourcing storage function module, the visual presentation and analysis of the security protection status of data assets in the outsourced storage process are realized through components such as Amap, water wave dashboard, percentage bar chart, tree chart, data search view and scattered Gantt chart, as shown in
Figure 9.
The Amap shows the distribution of data asset storage nodes. When hovering over a node, a pop-up window containing detailed information such as storage device number, storage status, IP address, security configuration policy, data throughput, etc., is displayed. When a node is clicked, the water wave dashboard dynamically updates the currently selected node to visually display the device storage usage rate and security policy status. Through the water wave dashboard, managers can monitor the changing trend of equipment storage utilization rate in real time. When the storage utilization rate is close to the alert line, managers can expand the storage capacity or clean data in time by observing the water wave height. In addition, by comparing the storage usage rate at different time points, we can analyze the storage growth pattern, predict the future storage demand, and provide decision support for capacity planning and security configuration strategy adjustment. The percentage bar chart shows the longitudinal comparison information of the throughput of data inflow and outflow of storage devices, reflecting the overall change in data throughput. Through the percentage bar chart, managers can quickly identify storage devices with abnormal network traffic and adjust security protection policies in time. For example, when the proportion of inbound or outbound traffic of a device deviates significantly from the normal range, it may indicate network attacks or equipment failures. At this time, the corresponding security configuration policies will be re-issued and modified. The tree chart shows the distribution of security configuration policies of storage devices. The storage devices configured with the same policy are divided into groups, and each group is distinguished by different colors. Different devices in the same group are presented in slices. Through tree diagram, managers can quickly locate problem devices. For example, by analyzing the number of slices and redundancy under different policies, they can evaluate the fault tolerance of security protection. In a scatter Gantt chart, the life cycle of a secure storage policy is displayed on a time axis, including creation time, effective time, and expiration time. In the data search interface, the table displays the policy number, status, number of slices and other conditions for filtering. Through scatter Gantt chart, managers can find the rules and problems of strategy formulation by observing the time distribution of strategy creation, effectiveness and invalidation. For example, finding that a large number of policies fail in a short period of time may indicate that there is a problem in the formulation of security configuration policies, which need to be modified in time.
6.2. Security Multi-Party Sharing Module
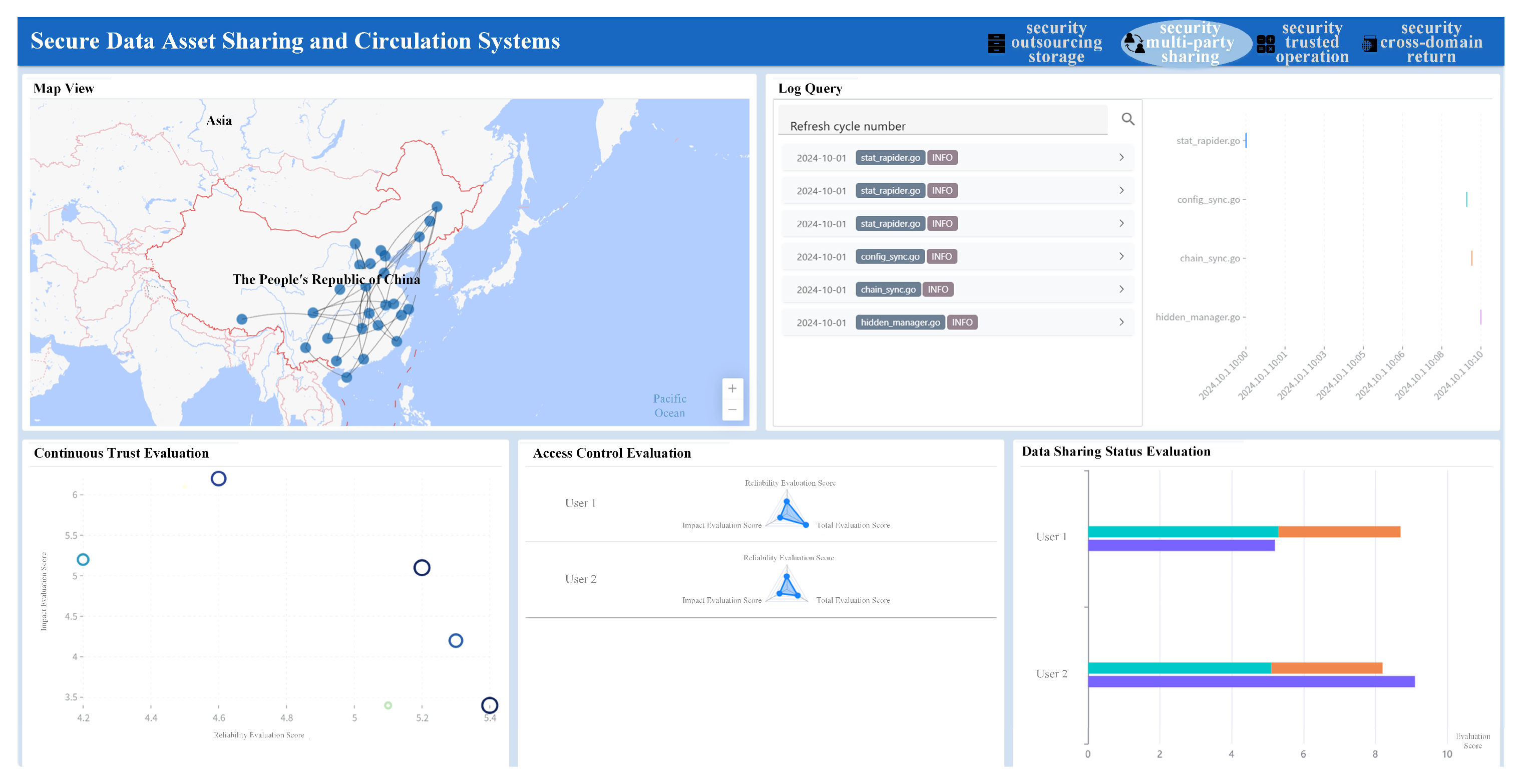
In the security multi-party sharing function module, the security situation of data assets in the multi-party sharing process is visually presented and analyzed through components such as Amap, log distribution maps, scattered circle maps, multi-dimensional radar maps, and statistical maps, so as to facilitate timely discovery of security risks and adjustment or modification of security protection strategies, as shown in
Figure 10.
The node information that is undergoing data sharing is displayed in Amap. The connection between nodes intuitively reflects the network connection relationship of data sharing participants, and can intuitively perceive the whole process of data sharing. In the data sharing log search interface, managers can quickly filter target logs by entering keywords, selecting component types, setting security levels or adjusting time ranges and other multi-dimensional conditions. At the same time, real time synchronously presents the time distribution diagram of matching logs on the right side of the interface, and clearly shows the distribution density of logs in different time periods based on the timeline. In the process of data sharing, it records according to the preset log template, and through statistical analysis of the selected logs, the change trend of key indicators such as the number of logs and risk level in time series is intuitively presented by a line chart and bar chart, and the analysis results are given in three aspects: continuous trust evaluation, access control evaluation and data sharing status evaluation. In the continuous trust evaluation view, the scatter circle diagram is used to display the overall information of all data sharing events recorded in the log. Each scatter represents a data sharing event. Through the attributes such as the position, color and size of the scatter, the type, trust level and influence scope of the event are visually presented. In the access control evaluation view, the access control policy of each data sharing participant is evaluated using a multi-dimensional radar chart, which helps managers discover risks in real time and adjust access control policies in time. In the data sharing status evaluation view, combining the continuous trust evaluation results and the access control evaluation results, the comprehensive trust results of each data sharing participant are given, which helps managers quickly lock high-risk data sharing participants and data sharing things.
6.3. Security Trusted Operation Module
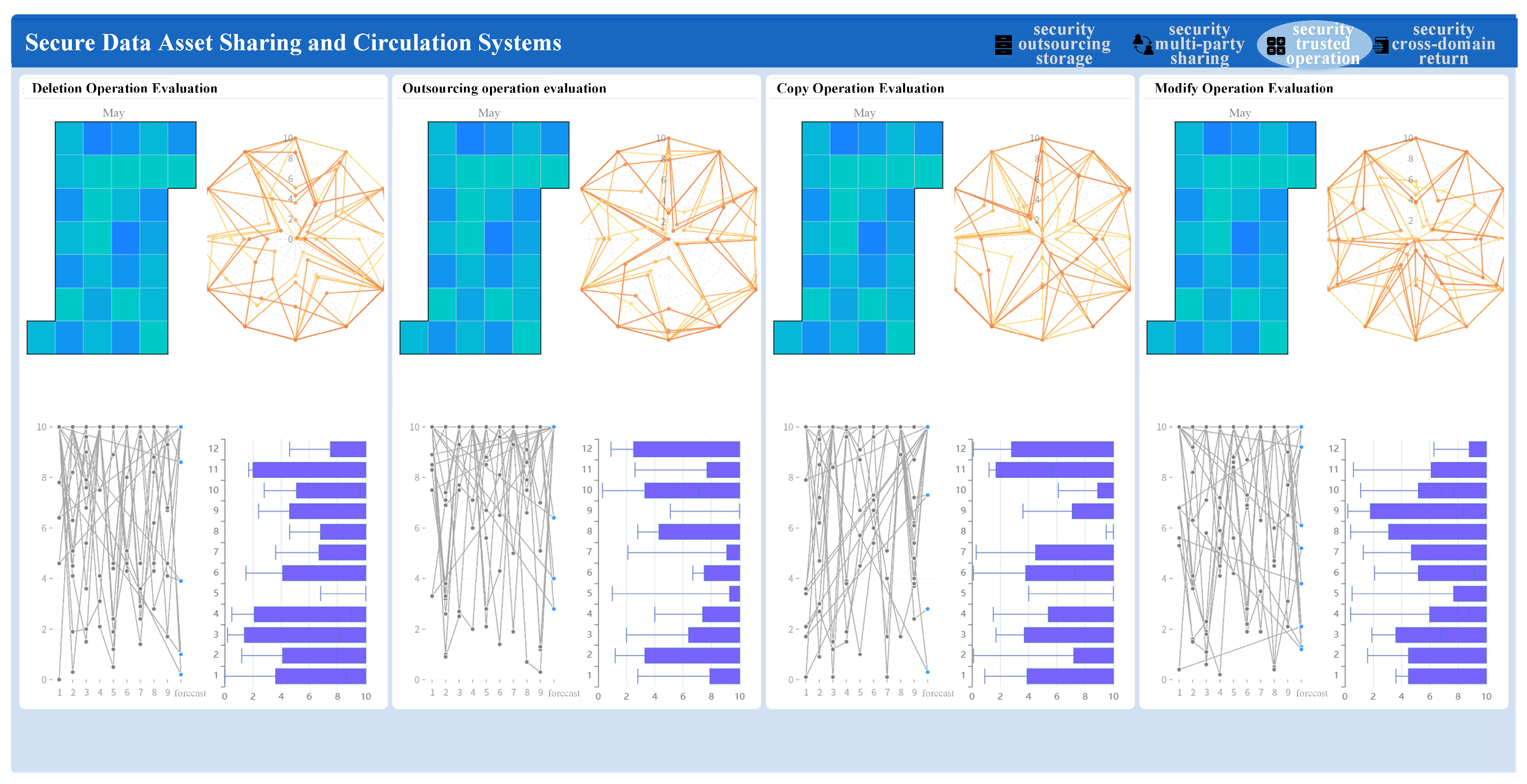
In the security trusted operation function module, the operation processes such as data deletion, outsourcing, copy and modify are visually presented and analyzed through components such as thermal calendar chart, radar chart, line chart and box chart, as shown in
Figure 11.
After selecting the operation that needs supervision, the security trusted operation function module immediately starts the multi-dimensional operating status calculation mechanism based on risk analysis, abnormal behavior detection and event extraction, which can quickly judge the credibility of data operation and identify potential abnormal operation or network attack risk.
Taking copy operation management as an example, by analyzing the log file of each operation, a quantitative evaluation model is established, and the risk degree of each operation is visually presented in the form of a thermal calendar diagram. In the calendar chart, different color gradients correspond to different risk levels. The red area represents high risk, and the green area represents low risk. Managers can quickly identify high-risk periods. When managers select a certain date on the thermal calendar chart, the interface triggers the intelligent linkage mechanism and automatically jumps to the radar chart interface. This radar chart is centered on the selected date and covers the 10-day data cycle before and after, building a three-dimensional operation management index evaluation system. In this way, managers can fully perceive the real time status and historical trend of the operation event. In the line chart interface, the system takes time as the horizontal axis and dynamically displays the changes in the number of times of this operation in the form of curves. Through an analysis of the curve trend, managers can clearly observe the fluctuations of indicators at different time nodes. The box chart clearly shows the concentration trend and dispersion degree of the number of operations through statistics such as median, quartile, minimum and maximum. The length of the box reflects the distribution interval of the number of operations, the dotted line defines the normal fluctuation range of the data, and the abnormal values are separately marked in the form of discrete points. In this way, potential abnormal operations or network attack risks can be quickly identified.
6.4. Security Cross-Domain Return Module
In the security cross-domain return function module, multi-dimensional data such as geographic information, performance indicators, network topology and operation logs are called and integrated through various interfaces, and components such as Amap, smart table, network topology diagram, data flow diagram and data search view are used to realize multi-view presentation and analysis in the whole process of cross-domain return of data assets, so as to timely discover potential security risks through real time monitoring, anomaly detection and status analysis, as shown in
Figure 12.
In the Amap, the CPU, memory and disk load of each transmission node are displayed through a ring diagram. Managers can quickly identify nodes with abnormal load and intuitively perceive the overall running status of the data asset backhaul process through node size and color changes. In addition, through the spatial distribution characteristics of the map, the geographical distribution law of each node deployment can be analyzed, and potential regional failure risks and network attack risks can be found. The radar chart design embedded in the smart table makes the comparison of multi-dimensional performance indicators (CPU load, memory load, disk load) more intuitive. Managers can quickly identify abnormal nodes through the shape changes of the radar chart, and conduct in-depth analysis through the sorting and filtering functions of the table. In addition, through real-time monitoring of indicators such as online status and network speed, network anomalies and offline nodes can be found in time. The connection relationship between transmission nodes is shown in the network topology diagram. Through the Dagre layout algorithm, managers can clearly observe the hierarchical relationship and connection pattern between nodes, and then identify key nodes and potential single point failure risks. At the same time, through node dragging and layout adjustment, the network structure can be optimized and the reliability and performance of data asset transmission can be improved. In the data flow diagram, the relevant data flow directions of all data with different characteristics are displayed, including key information such as operation stage (issued configuration/unissued configuration/information synchronization), operation module, operation type and operation IP. Through the visualization effect of data flow view, managers can analyze the data flow in different operation stages and identify bottlenecks and anomalies in the process of configuration delivery and synchronization. The data search view provides functions such as data filtering, status filtering and resetting. By adding data filtering conditions, dynamic filtering and filtering of data are realized. Using multi-condition combination queries, managers can quickly locate specific types of operation records, analyze operation modes and abnormal situations and identify high-frequency operations and potential operational risks according to the statistical display of the number of operations.
6.5. System Function Comparison
This scheme integrates various cutting-edge security technologies with cryptography as the core, achieving comprehensive security protection for data assets throughout their entire lifecycle. The specific technical capabilities at each stage are as follows.
6.5.1. Multi-Party Sharing
Data access control, authentication, and authorization are critical for precise management of data asset ownership and usage rights. Existing solutions often rely on traditional cryptographic methods to ensure confidentiality but struggle to support flexible changes in permission rules. To address this, a novel method for the precise management of data assets in uncontrolled environments is proposed to ensure secure data exchange and sharing. Based on attribute sets of different data assets and data users, attribute-based encryption is employed to achieve fine-grained access control based on attributes such as time and location. By analyzing multidimensional trust evaluation factors for data assets and users, a continuous dynamic trust evaluation method is established to enable the dynamic authentication of data. Additionally, precise control over the distribution and revocation of keys for data users ensures fine-grained dynamic authorization during data asset circulation. From the comparison of security features provided in
Table 1, it can be seen that this approach balances the efficiency of rights determination and control for data assets in uncontrolled environments, reduces the correlation between ciphertexts and complex access control policies, and enhances the precision of defining data asset ownership boundaries, overcoming the limitations of static, passive and inefficient control mechanisms.
6.5.2. Outsourcing Storage
Cloud storage services in uncontrolled environments face challenges such as uncontrollability and high risks of data leakage. Existing data cleansing methods have coarse granularity and poor practicality, while current storage methods incur high computational overhead and low efficiency. To address these issues, a novel method for cloud data cleansing and secure storage based on multi-dimensional equilibrium is proposed. For multi-source heterogeneous data, an efficient data transformation process and mapping rules are designed. By combining data attributes, the sensitivity of data is quantitatively assessed, and different weights are assigned to data sensitivity based on data categories. A combination of coarse-grained filtering and fine-grained control is used to achieve data deduplication. Based on data adaptive partitioning and lightweight encryption, a fragmented encryption storage scheme is designed to dynamically adjust the redundancy, dispersion, and security of data storage for different security levels. By constructing efficient retrieval and rapid recovery/reconstruction mechanisms for fragmented data using distributed multi-hash techniques, fast and reliable recovery and reconstruction of cloud data are achieved. From the comparison of security features provided in
Table 2, it can be seen that the proposed approach optimally balances data storage security and efficiency, improving the extraction efficiency and recovery reliability of distributed secure storage in uncontrolled scenarios while ensuring data security.
6.5.3. Trustworthy Operations
In uncontrolled environments, there is a need to accurately identify, dynamically manage and evaluate the trustworthiness of data operations by different users, applications, and at different times. A new method for fine-grained trustworthy management of data operations is proposed. By conducting fine-grained identification of data assets, operation subjects, and operation environments, and performing comprehensive rule-based evaluations, a mapping relationship between multi-policy rules and smart contracts is established. A trustworthy supervision chain is constructed to ensure the reliable execution of rules and the traceability of operations. From the comparison of security features provided in
Table 3, it can be seen that the proposed approach uses smart contracts and blockchain technology to enable trustworthy recording of data operation behaviors by different data providers. Trustworthiness metrics are derived from these records, and trust values are combined with access control methods to provide the basis for data access authorization and rights determination. This achieves fine-grained control over data operations, evidence preservation during operations, and traceability after operations.
6.5.4. Secure Transmission
In uncontrolled environments with strong adversarial conditions, massive data return transmission faces security threats such as eavesdropping, tracking, traceability, and blocking. To address these challenges, a novel data transmission channel resistant to traceability, tracking, and analysis is designed, based on advanced cryptographic techniques such as zero-knowledge proofs and oblivious transfer, combined with anonymous communication technology. This ensures data transmission security across dimensions such as traffic characteristics, communication relationships, network topology, information content, and user identities, while resisting colluding attacks. By leveraging intelligent operation and maintenance management technology, a secure data transmission channel is constructed that supports rapid deployment and resource reconstruction according to demand. From the comparison of security features provided in
Table 4, it can be seen that the proposed approach provides comprehensive traceless capabilities across five dimensions: traffic characteristics, communication relationships, network topology, user identities, and information content. This ensures transmission security even when some nodes act maliciously and supports the construction of customized transmission channels within minutes, enabling parallel scheduling of thousands of data streams.