Featured Application
The integrated technological model developed for the Pompeii Archeological Park serves as a pioneering application of IoT/IoE-based systems in the field of cultural heritage management. This approach demonstrates how a large-scale archeological site can be transformed into a smart, data-driven environment capable of ensuring security, safety, enhancing conservation, and improving visitor experience. The framework, which includes real-time monitoring, predictive maintenance, and intelligent risk management, can be adapted and replicated in other heritage contexts worldwide. It provides a scalable and modular reference architecture for the protection and sustainable operation of complex historical environments, especially those exposed to natural degradation and high tourist flows.
Abstract
Pompeii is widely known for its tragic past. In 79 A.D., a massive eruption of Mount Vesuvius buried the city and its inhabitants under volcanic ash. Lost for centuries, it was rediscovered in 1748 when the Bourbon monarchs initiated excavations, marking the beginning of systematic digs. Since then, Pompeii has gained worldwide recognition for its archeological wonders. Despite centuries of looting and damage, it remains a breathtaking site. With millions of visitors annually, the Pompeii Archeological Park is the one most visited site in Italy. Managing such a vast and complex heritage site requires significant effort to ensure both visitor safety and the preservation of its fragile structures. Accessibility is also crucial, particularly for individuals with disabilities and staff responsible for site management. To address these challenges, integrated systems and advanced technologies like the Internet of Things/Everything (IoT/IoE) can provide innovative solutions. These technologies connect people, smart devices (such as mobile terminals, sensors, and wearables), and data to optimize security, safety, and site management. This paper presents a security/safety IoT/IoE-based system for security, safety, management, and visitor services at the Pompeii Archeological Park.
1. Introduction
Managing a cultural heritage site as vast and complex as the Pompeii Archeological Park [1,2,3,4] requires a dedicated commitment to ensuring security, safety, conservation, and accessibility. Special attention must be given to providing equal access for all individuals, particularly those with disabilities, as well as to supporting the personnel responsible for maintaining and overseeing the site’s daily operations. To achieve these objectives, the implementation of integrated technological systems is essential [5,6].
Recent advancements in technology, such as the Internet of Things (IoT) and the Internet of Everything (IoE), have introduced innovative solutions to improve the security, monitoring, and management of heritage sites [7]. These smart systems enable the connection of people, objects (such as mobile devices, intelligent sensors, and wearables), and valuable data, facilitating a more efficient and responsive approach to site maintenance and visitor experience enhancement. To effectively integrate these technologies into a structured security and safety model, the development of an Integrated Multidisciplinary Model for Security and Safety Management (IMMSSM) [8] tailored to the specific needs of Pompeii is fundamental, starting with a proper risk assessment.
To this end, targeted initiatives such as the “Safety & Security for Pompeii Archeological Park” and “Smart@Pompeii” projects have been launched. These interrelated programs focus on implementing intelligent monitoring systems, improving emergency response mechanisms, and optimizing resource allocation for the sustainable preservation of the site. The primary aim of this work is to illustrate the functionalities and benefits of the IoT/IoE integrated system, detailing the methodologies, results, and insights gained from the study and implementation of an innovative communication network designed to support security, safety, and overall site management at the Pompeii Archeological Park. By leveraging cutting-edge technological advancements, Pompeii can continue to thrive as one of the world’s most extraordinary cultural heritage sites while ensuring its long-term preservation for future generations.
In the following sections, a general overview of the work carried out will be presented. Given the extensive number of technological interventions that must be illustrated, it will not be possible to delve into the details beyond a certain level of depth. The description will therefore focus on providing a comprehensive yet high-level summary, highlighting the main innovations, objectives, and outcomes achieved. Detailed technical specifications, implementation procedures, and component-level analyses will be omitted or only briefly mentioned to maintain clarity and ensure that the narrative remains accessible. This approach is necessary to effectively convey the breadth and complexity of the initiatives undertaken without overwhelming the reader with excessive technical minutiae.
Moreover, given the nature of the system, which is designed to ensure the protection and safeguarding of a highly sensitive site, it is essential to adopt a cautious and responsible approach to the dissemination of information. In particular, since this pertains to security, the disclosure of specific technical details—such as the exact configuration of the subsystems, the positioning and capabilities of surveillance devices, the detailed architecture of the communication infrastructure, or the operating logic of control mechanisms—must be strictly avoided. Revealing such information could unintentionally expose the system to vulnerabilities or exploitation attempts, potentially compromising not only the effectiveness of the protective measures in place but also the security of the site as a whole. For this reason, only high-level descriptions and generalized concepts are provided in the documentation, in full compliance with the principles of security by design and confidentiality, which are integral to the overall strategy for managing technological risk and resilience.
2. Pompeii Archeological Park
Pompeii [1,2,3,4] is internationally recognized for its tragic and catastrophic past, as in the year 79 A.D., a violent and devastating eruption of Mount Vesuvius completely buried the city along with its entire population under layers of volcanic ash and pumice. This natural disaster abruptly ended the lives of thousands of people and, at the same time, preserved an extraordinary and unique testimony of Roman civilization frozen in time. Centuries passed before the buried city saw the light again, and it was only in the year 1748 A.D., under the directive of the Bourbon monarchs, that official explorations began, leading to the initial excavations. This marked the beginning of a fascinating and ongoing journey into the past, gradually unveiling the wonders of Pompeii to the world. Pictures of Pompeii Archeological Park are shown in Figure 1, Figure 2, Figure 3 and Figure 4.

Figure 1.
(a) Partial view of the ancient city with the Vesuvius volcano in the back. (b) One of the streets of the ancient city.

Figure 2.
(a) Excavations of Pompeii with the Vesuvius volcano in the back. (b) Real view Map of Pompeii Archeological Park.

Figure 3.
(a) Forum. (b) Interior paintings of the Villa of Mysteries.

Figure 4.
(a) Gymnasium. (b) Interior of a Villa.
From the first stages of excavation, the site’s fame spread across the globe, captivating scholars, artists, and curious travelers alike. The archeological remains of Pompeii offer an unparalleled window into the daily life, customs, and artistic achievements of the ancient Romans. However, despite the immense historical and artistic value of the city, over the centuries, several valuable artifacts have been looted, removed, or subjected to the wear of time. Nevertheless, Pompeii continues to astonish and inspire modern audiences with its remarkable ruins and the gripping story of its tragic demise. Today, the Pompeii Archeological Park attracts millions of visitors every year and stands as one of the most visited cultural sites in Italy.
The uniqueness and sheer size of the archeological site contribute to its extraordinary status, a fact officially recognized by UNESCO in 1997 when Pompeii was included in the World Heritage List. The ruins of the city encompass an extensive variety of structures, including private homes, public buildings, religious temples, intricate mosaics, vibrant frescoes, and a network of well-preserved streets. The overwhelming sense of history and artistry that permeates Pompeii, however, comes with significant challenges. The preservation and management of such an immense site remain an ongoing struggle, as the ruins are constantly exposed to the elements and the inevitable impact of tourism. Natural factors such as material degradation, corrosion caused by atmospheric agents, and the gradual erosion produced by rainfall pose persistent threats to the site’s integrity. Moreover, the high number of visitors walking through the ancient streets and structures increases the risk of wear and tear, making continuous conservation efforts indispensable. If not properly addressed through diligent management and advanced protective measures, these factors could cause significant and irreversible damage to the archeological remains.
The Pompeii Archeological Park extends across approximately 66 ha, with 33 ha open to public visitation. The accessibility of different areas fluctuates depending on the ongoing conservation and restoration activities as well as the flow of tourists. The uncovered area of approximately 44 ha is systematically divided into nine regions and contains an extensive and complex array of structures. Among the site’s components are about 3.2 km of defensive walls, 80 insulae (city blocks), around 1500 domus (private residences), 1200 square meters of floors, 242,000 square meters of masonry surfaces, 20,000 square meters of plasters, 17,777 square meters of decorated surfaces, and 20,000 square meters of roofing structures.
The Pompeii Archeological Park, in addition to its main site, encompasses a collection of smaller archeological locations, commonly referred to as peripheral sites. These sites, while being of lesser extent compared to the central ruins, hold significant historical and cultural value. They are scattered across various locations, sometimes several kilometers away from the main area, and contribute to a broader understanding of the ancient civilization that once thrived in the region. Despite their smaller scale, these peripheral sites provide additional insights into the daily life, architecture, and social organization of the time, making them an essential part of the overall archeological heritage of Pompeii.
Within this vast expanse, visitors can admire some of the most emblematic and well-preserved spaces of ancient Pompeii. Among the most significant locations is the ‘Foro Civile’ (Public Forum), which once represented the social, political, and commercial hub of the city. Another notable site is the Sanctuary of the Public Lares, a sacred place of worship where today some of the casts of the victims of the volcanic disaster are displayed, offering a poignant reminder of the human tragedy that unfolded in 79 A.D. The impressive amphitheater of Pompeii, one of the oldest in the Roman world, could accommodate up to 12,000 spectators gathered to witness gladiatorial combats. Other significant landmarks include the grand theater, the gymnasium, and several luxurious villas adorned with exquisite frescoes and intricate mosaics. Photographs of these remarkable locations, which have been preserved through the centuries, provide valuable insights into the grandeur and sophistication of Roman urban life.
Even today, Pompeii continues to be a vibrant and culturally significant site, hosting extraordinary events, exhibitions, and artistic performances within its historic setting. The evocative nature of Pompeii has left a lasting impression on numerous distinguished artists, writers, and intellectuals who have visited the ruins throughout history. Among them are Wolfgang Amadeus Mozart, Johann Wolfgang von Goethe, and Stendhal, all of whom found inspiration in the city’s remarkable blend of beauty and tragedy. The experience of visiting Pompeii inevitably stirs emotions, immersing visitors in an environment that both fascinates and educates while also provoking reflection on the fragility of human existence in the face of natural forces.
3. Integrated Technology Systems in Cultural Heritage
Integrated technological systems have already been used for security and safety management [5,6], even systems based on IoT/IoE [7].
Moreover, other technologies have been used in cultural heritage sites, including the use of IoT, as illustrated in the following.
For example, three years of continuous environmental monitoring were conducted at The Cloisters, the medieval branch of the Metropolitan Museum of Art in New York. A wireless sensor platform, consisting of over 200 sensors strategically distributed across five galleries, was employed to monitor temperature, airflow, and microclimatic variations. The collected data, analyzed through both physics-based and statistical models, revealed a remarkably stable environment within the galleries. The dense deployment of sensors allowed for the detection of subtle, localized shifts in air quality and highlighted the influence of visitor presence on microclimate dynamics. The high spatial and temporal resolution of the data provides a valuable baseline for understanding the long-term effects of visitor activity and building management practices on the preservation of the art collections [9].
Another similar case is represented by the use of 15 microclimate monitoring stations, developed with open source hardware, within the Mosque-Cathedral of Córdoba—a UNESCO World Heritage Site recognized for its outstanding universal value. The aim was to analyze the behavior of indoor temperature and humidity in relation to external weather conditions, public visitation hours, and the site’s internal layout. Long-term tracking of these variables is crucial for preserving the monument and for optimizing future conservation efforts by reducing associated costs. The monitoring results are presented to highlight the effectiveness and practical benefits of the implemented system [10].
Even distributed smart sensor networks have been deployed at cultural heritage monuments across different areas. The presented system features smart IoT devices, known as Smart Tags, specifically designed to capture environmental measurements in close proximity to the monuments. It also incorporates a middleware layer to facilitate seamless communication between devices and a visualization platform to display the collected data. Particular attention is given to evaluating the NB-IoT connectivity and the power efficiency of the Smart Tags through a series of tests, from which valuable insights are drawn [11].
RFID sensors have been developed and specifically designed to address environmental monitoring challenges. These sensors operate by detecting changes in the properties of an RFID tag that is coupled with a sensitive silver thin film exposed to ambient conditions. The low-cost sensors can be read using a commercial RFID reader, providing information on the environmental corrosivity index and indicating the presence of pollutants. Il particular, they are focused on monitoring hydrogen sulfide (H₂S) pollution within a facility dedicated to the conservation and restoration of archeological and historical wooden artifacts. The findings demonstrate the sensors’ capability to spatially map corrosivity levels within the building, offering valuable insights for preventive conservation strategies [12].
Given the nature of cultural heritage tours at archeological sites, there is a strong need to deliver a large amount of information both effectively and efficiently. From this point of view, smart guide system specifically designed for outdoor archeological environments tend to be very useful. While IoT technology has seen widespread adoption in archeological sites, its applications have been primarily focused on monitoring and preserving the current state of heritage assets. Consequently, research has been largely limited to conservation efforts. To address this gap, the potential of expanding IoT applications into the field of cultural heritage interpretation has been studied. As part of this approach, the cultural value of heritage sites in Yangju, Korea, was analyzed, then assessed the existing methods of heritage guidance at these locations, and proposed a smart guide system leveraging IoT technologies. This system is expected to enhance visitor engagement [13].
Inspired by advancements in the Internet of Things (IoT), Artificial Intelligence (AI), and 5G communications, the concept of the Internet of Cultural Things (IoCT) enables comprehensive interconnectivity between cultural products, services, resources, and platforms. This emerging framework offers individuals a richer humanistic experience, enhances economic returns for the cultural sector, and fosters the growth of cultural heritage preservation and education. Currently, IoCT is attracting significant interest from both industry and academia. From this point of view, it is possible to create proper platform architectures, using IoCT components and core technologies, aimed at linking cultural assets, the Internet, and human interaction [14].
To support the protection and preservation of cultural sites, advanced monitoring systems equipped with sensors are often deployed in close proximity to the assets to gather critical data. This information serves as the foundation for systems and processes dedicated to safeguarding heritage structures. An interesting application is represented by the use of acoustic sensors for the protection of cultural sites situated in both rural and urban settings, utilizing an innovative data flow framework. It was developed and implemented Wireless Acoustic Sensor Networks (WASNs) capable of recording ambient audio signals, which are transmitted to a modular cloud-based platform. There, the data are processed using a highly efficient deep learning algorithm to identify relevant audio sources specific to each site, considering the materials and structural characteristics of the heritage assets. The extracted audio information is then structured through a proper audio signal ontology and integrated with spatiotemporal data using semantic rules, enhancing the interpretability and contextualization of monitoring results such as vandalism, storms, etc. [15].
Artificial Intelligence (AI) and Internet of Things (IoT) technologies, if properly integrated, can transform cultural heritage preservation. While IoT enables real-time air quality and structural health monitoring, AI enhances data analysis, providing predictive insights. The combination of IoT and AI facilitates proactive risk management, ensuring more resilient conservation strategies. Innovative frameworks that leverage Heritage Building Information Modeling (H-BIM) and Digital Twin (DT) for continuous monitoring and predictive maintenance through a multi-step process, beginning with the digitalization of heritage assets using H-BIM, followed by the creation of real-time digital replicas via DT, have been proposed. By integrating advanced technologies, the framework offers a more adaptive and sustainable approach to preserving cultural heritage, addressing both immediate threats and long-term vulnerabilities [16].
The application of computer science techniques, such as artificial intelligence (AI), deep learning (DL), and computer vision (CV), to digital imagery offers significant potential for monitoring and preserving cultural heritage (CH) sites. Various forms of deterioration—such as weathering, mortar loss, joint damage, discoloration, erosion, surface cracking, vegetation growth, seepage, and vandalism—threaten the structural integrity of heritage assets over time. While numerous studies have demonstrated the use of AI for damage detection in modern infrastructures like concrete buildings and bridges, relatively few have applied these methods to quantify defects in cultural heritage structures. Moreover, practical case studies showcasing the real-world application of AI in heritage conservation remain limited. Thus, there is a pressing need to further explore AI-assisted visual inspection approaches for CH sites. These technologies can support inspection professionals by enhancing the accuracy and reliability of damage assessments. Different techniques of image-based damage assessment techniques, with a particular emphasis on the use of deep learning methods for cultural heritage conservation, have been proposed, including several case studies where AI tools complement traditional visual inspections, helping to advance the preservation of historic structures [17].
Video surveillance can be used to realize a vision sensor to implement a dual-service security system for museums. It consists of a system that offers the following two main functions: object monitoring and invisible visual Multiple-Input Multiple-Output (MIMO) communication. For object tracking, a Kalman filter algorithm is employed to predict and monitor the position of items within the surveillance area. To enable covert visual MIMO communication, an Adaptive Row-Column (ARC)-based Least Significant Bit (LSB) substitution technique is combined with the Integer Wavelet Transform (IWT) method. Both services are realized using standard electronic visual displays and existing surveillance cameras, ensuring minimal infrastructure modification. The performance of the object tracking system was assessed by comparing the actual object positions with the estimated ones to determine accuracy. Likewise, the covert visual MIMO system’s performance was evaluated at two stages as follows: imperceptibility was measured by analyzing the differences between cover and stego images on the transmitter side, while reconstruction accuracy was assessed by comparing original and decoded data images at the receiver side. The proposed system achieves enhanced imperceptibility, higher accuracy, and greater robustness compared to existing methods [18].
In recent decades, the need to protect and enhance cultural heritage structures (CHSs) has become increasingly critical, given their unique value and their wide-ranging economic, social, cultural, and environmental impacts. Structural Health Monitoring (SHM) and the effective management of CHS are emerging as essential strategies to assess the current state of conservation and structural integrity. Additionally, the data collected through SHM systems play a crucial role in developing cost-effective and sustainable maintenance plans, aligned with the core principles of historic preservation, such as minimal intervention. However, applying SHM to CHS presents greater challenges compared to modern buildings, due to the uniqueness of each historic structure and the imperative to preserve its architectural and historical authenticity. From this point of view, there are plenty of traditional and advanced SHM techniques applied to cultural heritage structures. They also include the use of fiber optic sensors, smart sensing materials, IoT-based SHM systems, and the integration of Building Information Modeling (BIM) technologies in heritage conservation [19].
Also unmanned aerial vehicles (UAVs) have been used in a cultural heritage context. For example, in utilizing deep learning techniques to detect looting activities at heritage sites using optical imagery captured by UAVs, demonstrating that UAV optical data offer an accessible and effective solution for authorities to monitor heritage sites and showcasing the potential of deep learning to automate the detection of new damage. It also demonstrates the broader implications of applying deep learning for the protection of cultural heritage and explores how the approach could be enhanced with the integration of additional data sources [20].
The use of UAVs also enables the detailed analysis of sites of cultural interest such as the study made on Cala Castle in Huelva, a key medieval fortification rehabilitated between 2003 and 2011 in Spain. A decade after its restoration, UAV-based 3D models and photogrammetric surveys have been created to document both the site and its landscape context. The analysis not only characterized the natural environment but also identified historic structures that shaped the region. As a pilot project, the creation of this visual database aims to support the conservation of heritage sites across the area, contributing to a broader sustainable development strategy at the regional level [21].
Satellite-based monitoring of archeological sites has become common practice, demonstrating its importance for conservation and preservation, especially when used in an integrated way with other technologies [22].
In addition, a lot of other technologies have been applied to cultural heritage to date to also ensure proper risk management [23].
The novelty of this paper is the presentation of a case study of a unique UNESCO heritage site where the intensive use of innovative technology was carried out to create an integrated security/safety IoT/IoE-based system for security, safety, management, and visitor services at the Pompeii Archeological Park.
4. The Framework of the IoT/IoE-Based Integrated Technological System
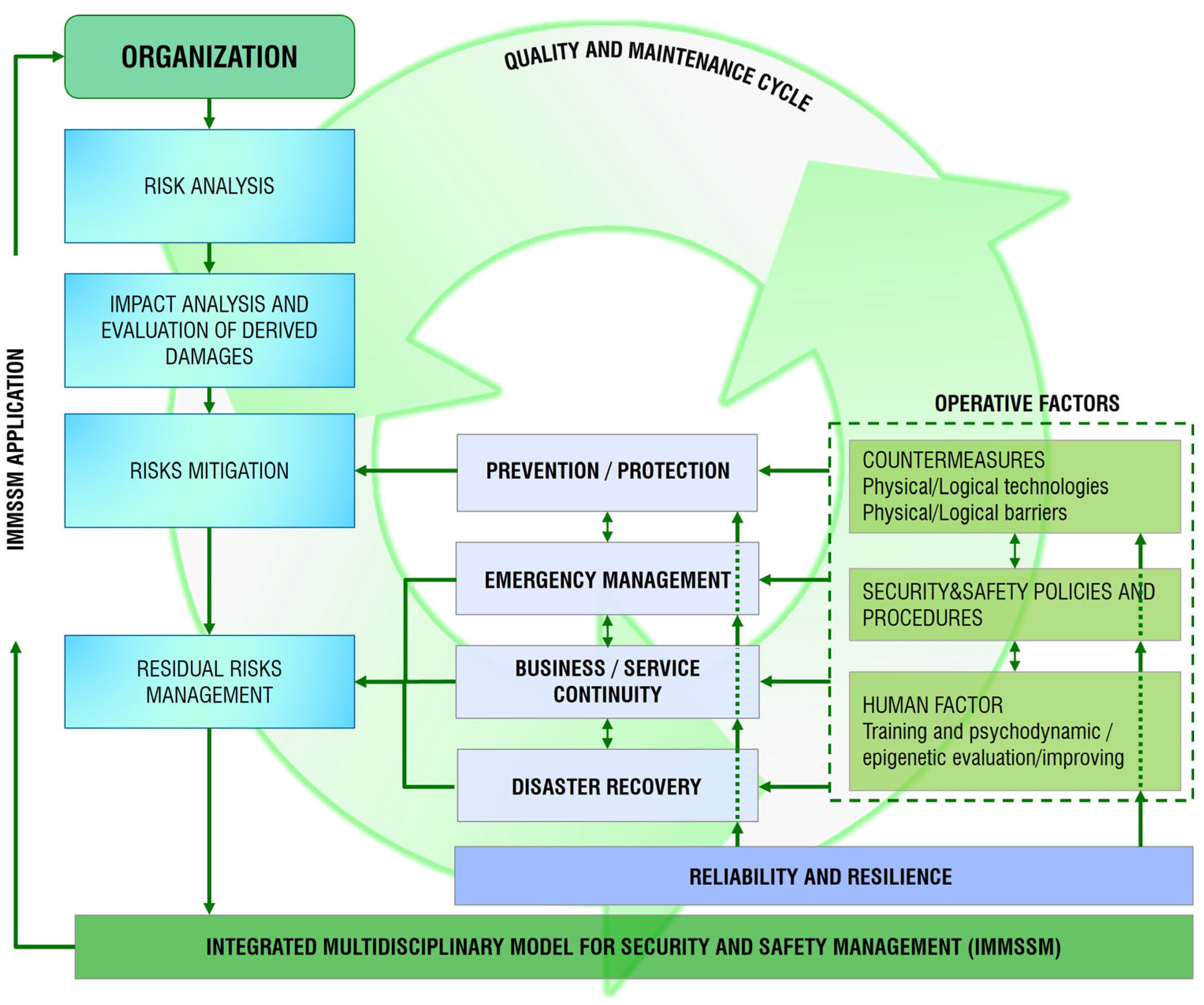
The IoT/IoE Integrated Technological System Framework (IoT/IoE-ITSF) must be capable of implementing and sustaining an Integrated Multidisciplinary Model for Security and Safety Management (IMMSSM) [8] tailored to the unique and irreplaceable Pompeii Archeological Park. This framework is designed to integrate diverse technological, structural, and operational aspects into a cohesive system that ensures the highest standards of security, safety, and general site management. By employing a comprehensive multidisciplinary approach, as illustrated in Figure 5, the IMMSSM guarantees that all essential factors contributing to the proper administration and protection of the site are addressed effectively, also thanks to a suitable risk assessment.
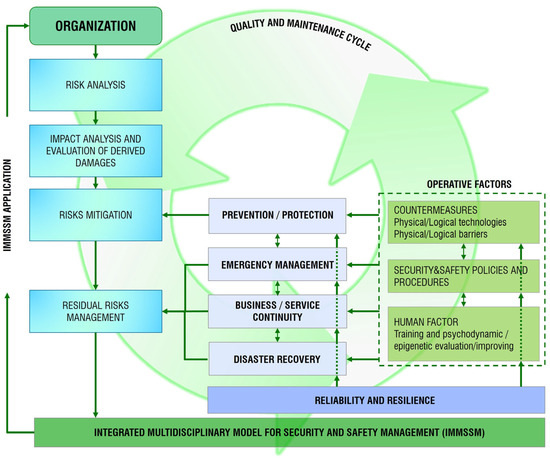
Figure 5.
Diagram of the Integrated Multidisciplinary Model for Security and Safety Management (IMMSSM).
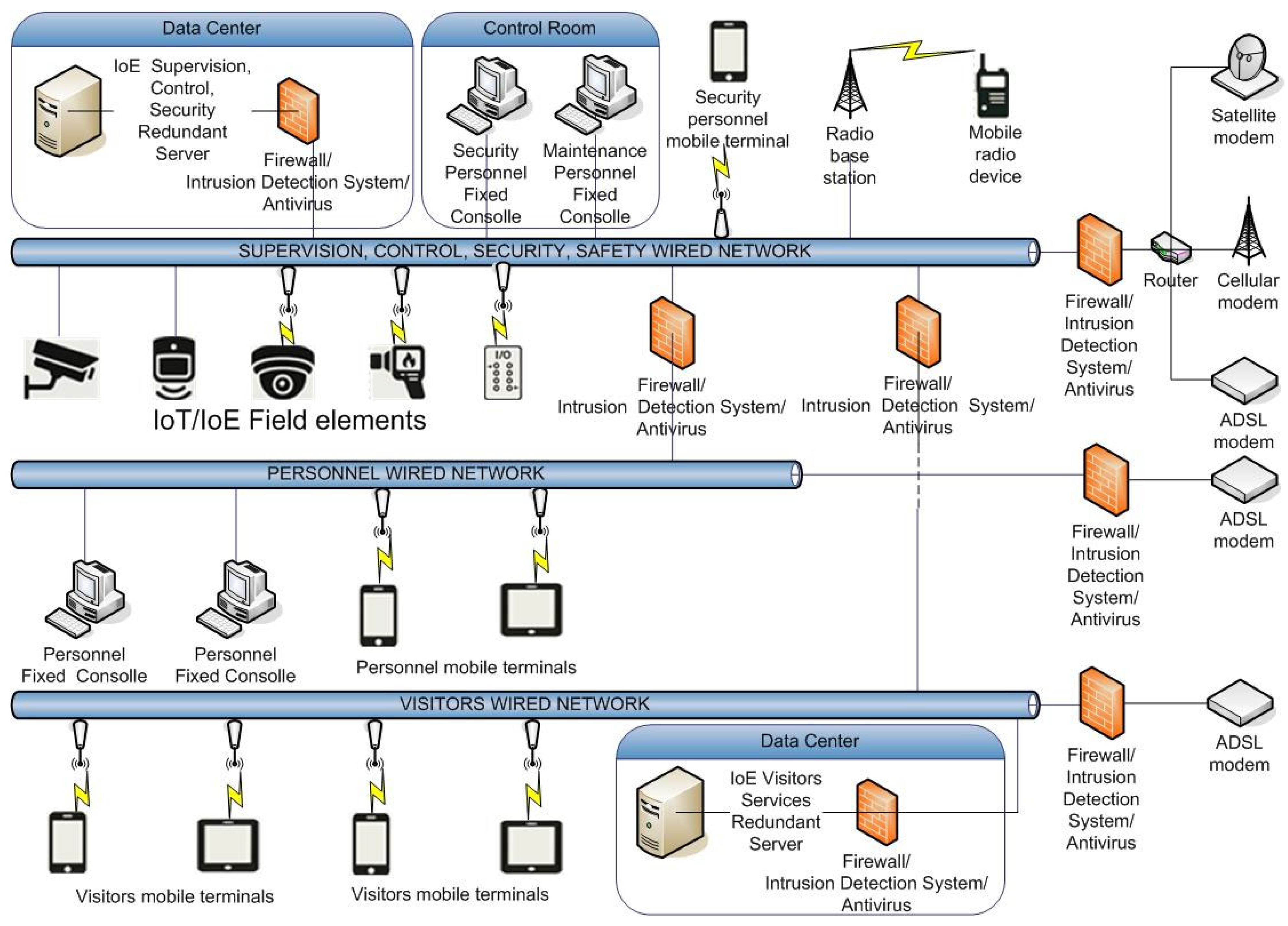
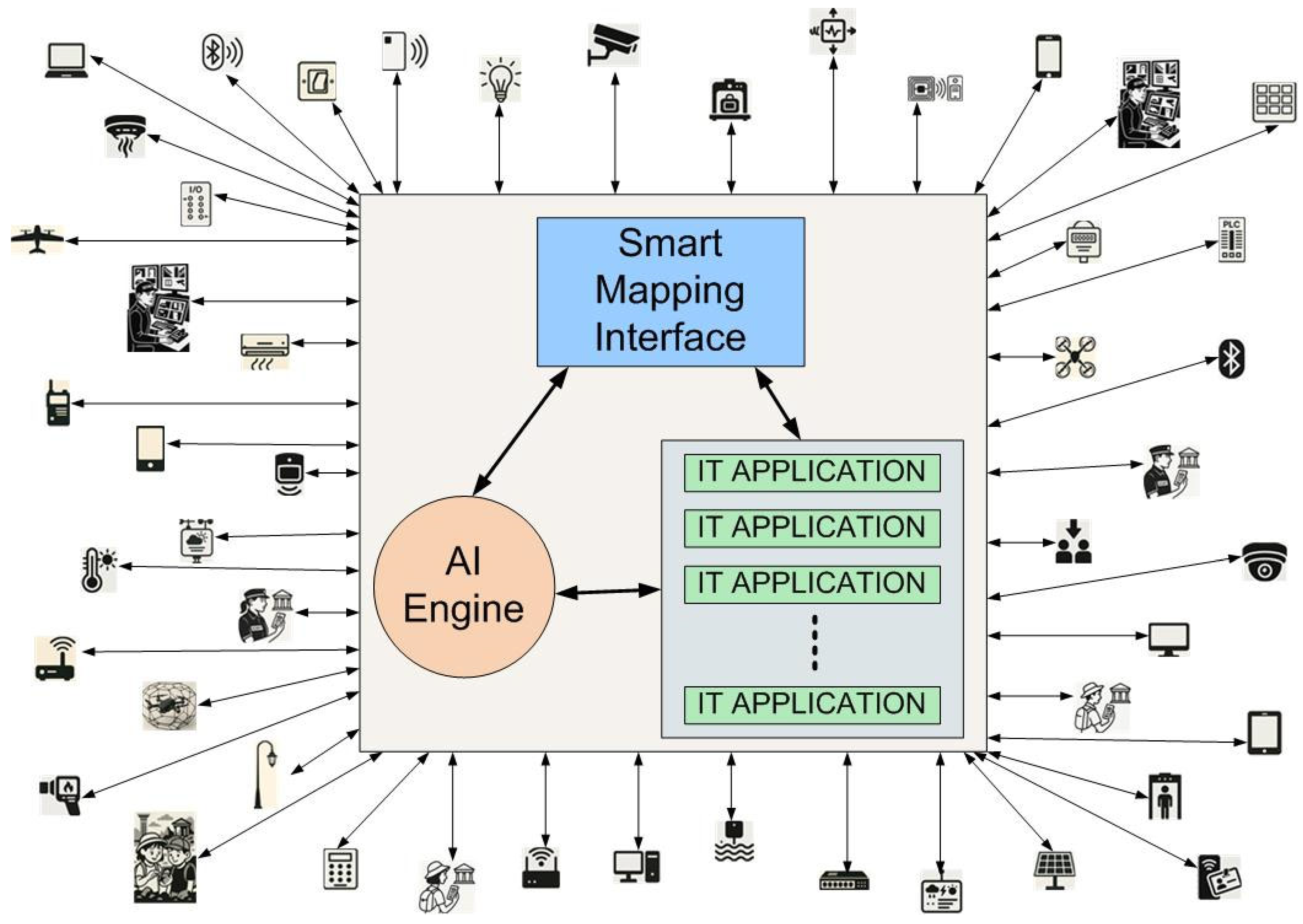
The successful implementation of the IMMSSM relies on the support of a well-designed IoT/IoE-based Integrated Technological System Framework (ITSF), which facilitates all necessary IMMSSM functions while maintaining an optimal balance between flexibility and scalability. This advanced framework enables seamless modifications, ensuring that any required changes in the IMMSSM can be translated into swift and cost-efficient adjustments to the ITSF infrastructure. As a result, the overall efficiency and operational continuity of the security and safety management system remain consistently high. The standard architecture of the IoT/IoE-based ITSF is depicted in Figure 6, offering insights into the structural composition and technological integration that define its functionality.
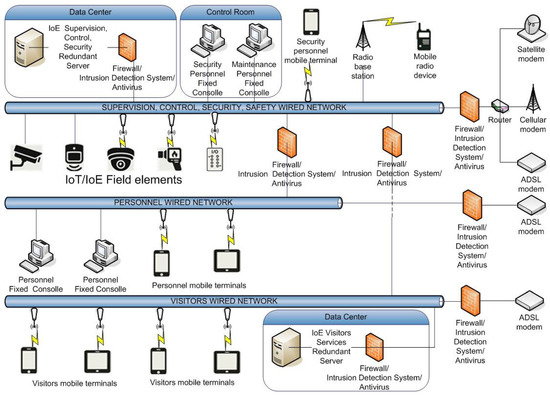
Figure 6.
Framework of the IoT/IoE Integrated Technological System.
Due to the existing architectural constraints, careful planning is required when installing cables, sensors, and related equipment to avoid the interference or disruption of the site’s aesthetic and historical integrity. Given the particular characteristics of the Pompeii Archeological Park and the necessity of ensuring comprehensive security, safety, visitor management, and conservation efforts, a highly reliable and robust IoT/IoE infrastructure has been developed. This infrastructure is designed to function effectively in both routine and critical conditions, providing essential monitoring, communication, and automation capabilities to maintain the safety of the site.
The primary objectives of the IoT/IoE-based ITSF, along with its integrated connections and devices, are as follows:
- Ensure the highest level of security and safety for visitors, site personnel, and both physical and digital assets.
- Maximize ease of use through advanced on-site and remote automated configuration mechanisms.
- Guarantee exceptional reliability, resilience, and adaptability in diverse operational conditions.
- Optimize energy consumption and promote sustainable power management strategies.
- Reduce maintenance costs by implementing self-regulating and low-maintenance components.
- Offer a modular and expandable framework capable of integrating present and future IoT/IoE advancements to streamline site management.
- Provide the capability to seamlessly incorporate additional devices, sensors, or infrastructure elements into the IoT/IoE ITSF whenever needed.
The modular nature of the ITSF allows for continuous scalability, ensuring that new technological advancements can be easily adopted to enhance the system’s effectiveness. This adaptability is crucial in addressing evolving security, safety, conservation, and visitor experience challenges at the archeological park.
The IoT/IoE-based ITSF has been designed through an interdisciplinary approach that considers various human factors and psychological aspects related to security, safety, emergency response, and risk perception among both personnel and visitors. Although the full scope of these considerations cannot be detailed here due to space limitations, they play an integral role in shaping the framework’s design. By integrating both wired and wireless communication technologies, the ITSF connects individuals (security, safety and maintenance personnel, site managers, tourists, etc.), devices (sensors, monitoring equipment, mobile terminals, wearable technology, etc.), and data/information/knowledge-processing systems, fostering a highly responsive and adaptive ecosystem.
Each of these components is treated as an “IoT/IoE object” within the system, allowing for seamless interaction and data exchange. The ITSF is designed to maintain real-time communication with all connected IoT/IoE objects, providing instant alerts to relevant personnel, including control room operators, law enforcement agencies, fire brigades, civil protection units, and medical responders, in the event of hazardous or life-threatening situations. These alerts can be transmitted through multiple communication channels, ensuring rapid response and effective crisis management.
Beyond security and safety, the IoT/IoE-based ITSF supports additional functionalities, such as environmental monitoring, data-driven predictive maintenance, and visitor engagement services. By leveraging advanced data analytics, artificial intelligence, and machine learning algorithms, the system enhances decision-making capabilities, anticipates potential risks, and optimizes resource allocation. For example, automated environmental monitoring can track humidity levels, temperature fluctuations, and pollution exposure, allowing conservation specialists to take proactive measures to protect delicate frescoes, structures, and artifacts from degradation.
Furthermore, the IoT/IoE-based ITSF facilitates seamless integration with innovative technologies such as augmented reality (AR) and virtual reality (VR) applications, enabling immersive educational experiences for visitors. These digital enhancements provide an enriched understanding of the historical and cultural significance of Pompeii while ensuring that security and preservation remain a top priority.
To ensure long-term sustainability, the IoT/IoE-based ITSF has been designed with an emphasis on energy efficiency and eco-friendly operational strategies. This includes incorporating renewable energy sources such as solar-powered sensors, energy-harvesting technologies, and smart grid connectivity to minimize the environmental footprint of the infrastructure. By reducing reliance on conventional power sources and optimizing energy consumption, the system contributes to the sustainable management of the archeological park.
Additionally, the ITSF is fortified with advanced cybersecurity measures to protect against digital threats. A comprehensive suite of security protocols, including firewalls, intrusion detection systems, and anti-virus protection, is strategically implemented within the communication network to safeguard against cyberattacks and unauthorized access. These cybersecurity mechanisms are critical in preserving the integrity and reliability of the ITSF, preventing potential disruptions that could compromise security and operational efficiency.
The continuous evolution of the IoT/IoE-based ITSF ensures that Pompeii’s security, safety, and management infrastructure remain at the forefront of technological innovation. As new advancements emerge, the system’s modularity will allow seamless integration of additional capabilities, further enhancing its ability to protect and sustain one of the world’s most extraordinary archeological heritage sites. Through the intelligent application of IoT/IoE technologies, Pompeii can maintain its status as a globally significant cultural landmark while ensuring the long-term preservation of its invaluable historical treasures for generations to come.
5. The Implemented Technologies and the IoT/IoE-Based Integrated Technological System
The technologies that have been implemented, along with the integrated system based on the Internet of Things (IoT) and the Internet of Everything (IoE), are the result of extensive development and deployment efforts carried out through the following two major and interrelated projects: Smart@Pompeii and Safety&Security of the Archeological Park of Pompeii (PAP). These initiatives were designed not only to introduce digital innovation to one of the world’s most important archeological sites but also to set a benchmark for the application of cutting-edge technologies in the cultural heritage sector.
The Smart@Pompeii project, launched in 2015, marked a turning point in the digital transformation of archeological areas. Its primary objective was to create a “smart” archeological site by integrating advanced technologies with an IoT/IoE-based system capable of monitoring, managing, and enhancing various aspects of the park. This included environmental monitoring, visitor flows, structural health of ruins, and energy efficiency. The ultimate aim was to provide a holistic and data-driven management approach to the Archeological Park of Pompeii (PAP), enabling more efficient operations, better preservation strategies, and an improved experience for visitors. By doing so, Smart@Pompeii positioned itself as the first large-scale implementation of a smart archeological park, blending the ancient world with modern technological innovation in an unprecedented way.
Following and complementing the Smart@Pompeii initiative, the Safety&Security project, initiated in 2018, was conceived with the specific purpose of enhancing the levels of safety and security across the entire archeological area. This project also made use of an integrated IoT/IoE framework, expanding upon the existing infrastructure established by Smart@Pompeii. It introduced a wide array of smart surveillance systems, intelligent access controls, real-time risk monitoring, emergency response solutions, and predictive maintenance systems, all designed to protect both the cultural assets and the visitors of the site. The Safety&Security project addressed new and emerging challenges related to public safety, site protection, and digital risk management in heritage environments.
These two projects are closely interconnected and mutually reinforcing. Smart@Pompeii laid the technological foundation and conceptual framework for a smart, data-centric site management system, while Safety&Security extended this vision into the realm of protection, resilience, and operational continuity. Together, they form a comprehensive and unified digital ecosystem within the PAP; one that is capable of adapting to future challenges and continuously evolving through new technological advancements. Their integration represents a model for future initiatives aiming to apply digital transformation strategies to cultural heritage and archeological preservation on a global scale.
Extensive use was made of components and devices characterized by high reliability, in order to ensure, together with the adoption of robust and resilient system architectures, the high overall reliability of the entire integrated system, as further illustrated in the following section dedicated to the results obtained.
Moreover, all components, devices, subsystems, etc., are powered by independent and autonomous energy sources, separate from the main power grid supply (including the use of green energy sources, as detailed below), in order to ensure the high reliability and resilience of the power supply and, consequently, of the entire integrated system.
6. Development Methodology
The development methodology was structured into the following phases:
- Preliminary analysis, consisting of the following:
- Analysis and definition of the most suitable Integrated Multidisciplinary Model for Security and Safety Management (IMMSSM) for the specific context.
- Risk analysis, aimed at identifying and assessing all present risks.
- Needs analysis, including the identification of desired functionalities and services.
- Analysis, identification, and definition of subsystems and technologies to be adopted in accordance with the outcomes of the previous points.
- Analysis and identification of the most suitable network infrastructure to meet the requirements and needs emerging from the preceding steps.
- Analysis, identification, and definition of security and safety policies and procedures, taking into account the previous points, including the design of a security procedure management system.
- Analysis, identification, and definition of a training program for the involved personnel.
- Analysis and definition of residual risks based on the previous assessments.
- Analysis, identification, and definition of an emergency management system, considering the results of the previous analyses.
- Analysis, identification, and definition of a service continuity system, in line with the outcomes of the previous phases.
- Analysis, identification, and definition of a disaster recovery system, based on the prior evaluations.
- Design phase, consisting of the following:
- Design of the telecommunication infrastructure.
- Design of the subsystems.
- Implementation phase, consisting of the following:
- Implementation of the telecommunication infrastructure.
- Implementation of the subsystems.
- Testing phase, consisting of the following:
- Testing of the telecommunication infrastructure.
- Testing of the subsystems.
- Operation, maintenance, and evolution of the systems, technologies, and the IMMSSM.
As for the implementation phase, the corresponding timeline was carefully designed to account for the specific requirements of the subsystems’ deployment. In this regard, the telecommunications infrastructure—which required considerable time due to the site’s complexity and extent—was organized in such a way that each of its parts could be promptly activated to support the operation of subsystems as they were completed according to varying timelines.
The authors carried out all activities related to the preliminary analysis, developed the design of the system along with all its subsystems and components, supervised and coordinated the implementation phases, conducted system testing, and continue to oversee and coordinate the management, maintenance, and evolution of the systems, technologies, and the IMMSSM, in line with a continuous improvement cycle based on the Plan-Do-Check-Act (PDCA) model.
7. The Telecommunication System
The telecommunication system constitutes the backbone of the entire integrated infrastructure that has been implemented. Since it plays a central and strategic role—serving as the foundation for all other technological components—a dedicated section is provided to describe it before introducing the other elements of the ITSF, also taking into account the challenges of implementing an efficient and distributed telecommunication infrastructure in a unique context such as the Pompeii Archeological Park.
This system has been designed to incorporate both wired and wireless communication modalities, ensuring broad coverage, flexibility, and resilience throughout the Archeological Park.
In regard to the wired network, a redundant dual-fiber optic ring has been implemented for each group of users/functionalities (supervision, control, security, and safety; personnel; and visitors). This high-capacity fiber ring follows multiple independent physical paths along the perimeter of the park, and it is specifically designed to ensure maximum reliability, fault tolerance, and continuous service availability. This ring-based topology significantly enhances the resilience of the fixed communication infrastructure, allowing for the automatic rerouting of data in the event of a failure along one segment of the network.
Single-mode optical fiber was used, as it is capable of ensuring higher transmission speeds compared to multi-mode fiber. In addition, network devices were employed that allow speeds of approximately 10 Gb/s, while the fiber itself can potentially support even higher speeds. This approach ensures that, should bandwidth requirements increase in the future, it will be sufficient to upgrade the network devices, thereby guaranteeing the modularity and expandability of the entire system.
From this fiber-optic backbone, a series of strategically located communication nodes have been deployed. These nodes serve as local hubs, distributing data and connectivity services to nearby devices and subsystems within the park. These include IoT sensors, video surveillance cameras, access points, environmental monitoring systems, and other operational endpoints. Given the inherent complexity of the archeological environment, and the constraints posed by the historical and cultural sensitivity of the site, a custom genetic algorithm [24,25,26] was employed. This algorithm was specifically developed to optimize the positioning of the communication nodes, taking into account both physical constraints and the efficient distribution of electrical power to field devices. Through the use of this evolutionary algorithm, the design team was able to maximize performance and coverage while simultaneously minimizing costs, achieving an excellent cost–benefit ratio in the deployment of the wired infrastructure.
The scheme of the wired telecommunication infrastructures is shown in Figure 7.
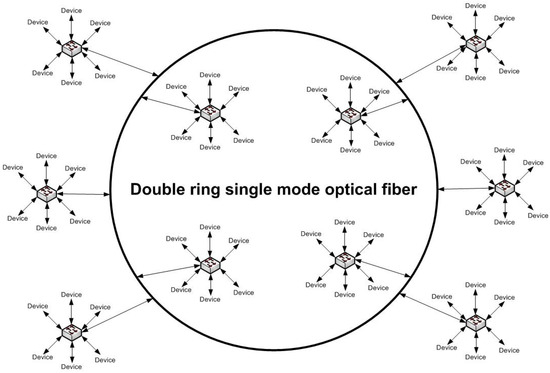
Figure 7.
Scheme of the wired telecommunication infrastructure.
Regarding the wireless communication network, a robust infrastructure based on Digital Mobile Radio (DMR) technology has been deployed. This wireless system not only provides comprehensive coverage within the central archeological area but also extends to the remote peripheral sites that are part of the broader archeological network. Deploying such a system in a historically and architecturally sensitive site posed a number of challenges, including strict limitations on structural modifications, visibility, and environmental impact. To overcome these challenges, another tailored genetic algorithm [6,25,26] was used to identify the optimal locations for the DMR base stations and repeaters. This solution ensured seamless communication coverage and high-quality service, once again optimizing the cost-effectiveness of the deployment.
The DMR system enables all security personnel to remain in constant communication with each other, regardless of their location within the park. It supports the use of smart handheld terminals equipped with interactive displays and processing capabilities, allowing staff to access critical information and system functionalities in real time. This ensures a coordinated, informed, and efficient response to any situation. Furthermore, the DMR network is designed to be interoperable with the regional civil protection and security infrastructure, making it possible to integrate into a unified response network during large-scale emergencies or critical events.
In addition to the wired and DMR-based systems, a dedicated Wi-Fi communication infrastructure has also been established. This network is intended to provide high-speed wireless connectivity not only for internal operational needs but also for visitors and staff, enhancing both user experience and internal communication. As with the other network components, the design and deployment of the Wi-Fi system had to take into consideration the environmental and cultural constraints of the archeological context. To address this, a proper genetic algorithm [7,25,26] was applied to identify optimal access point placement and network configuration. This resulted in an infrastructure that delivers broad and reliable coverage while minimizing visual and structural impact, once again achieving optimal performance and efficiency in terms of cost–benefit.
Overall, the telecommunication infrastructure—composed of the fiber optic backbone, DMR system, and Wi-Fi network—represents a state-of-the-art technological ecosystem, carefully designed and implemented to operate within a highly delicate historical environment. It supports not only daily operational needs and security and safety management but also offers the scalability and flexibility required for future expansion and integration with evolving digital services.
Great attention has been given to service continuity and disaster recovery aspects, both for this component of the project and for all other components.
8. The Video Surveillance and Security Systems
The existing video surveillance system has undergone a significant upgrade and expansion, aimed at enhancing the overall security of both the outer perimeter and various internal zones of the monitored area. This enhancement involved the strategic deployment of a wide range of advanced cameras, selected based on the specific requirements of each surveillance zone, to ensure comprehensive and uninterrupted monitoring under a variety of environmental and operational conditions.
The types of surveillance cameras integrated into the system include the following:
- High-resolution bullet cameras (4K resolution): These are primarily installed to provide detailed and continuous surveillance of the site’s perimeter, the main access roads, and various internal routes and sensitive zones. Their extended range and fixed focus make them ideal for linear coverage and the clear identification of movement across designated boundaries.
- PTZ dome cameras (Pan-Tilt-Zoom): These cameras are designed to rotate horizontally and vertically, as well as zoom in on specific areas or individuals. They are strategically positioned in larger open spaces, at entrance points, and in locations of high tourist or public concentration. Their versatility allows security personnel to dynamically monitor areas that require active scanning and real-time focus.
- Thermal and infrared cameras: Specifically utilized for night-time monitoring or in scenarios where visibility is poor—such as during fog, smoke, or darkness—these cameras are also essential for early fire detection. By identifying heat sources and changes in temperature patterns, they serve as a crucial component for emergency preparedness and incident prevention.
- AI-powered analytical cameras: Equipped with advanced video analytics capabilities, these cameras utilize artificial intelligence algorithms to automatically detect and flag anomalous or suspicious behavior. This includes—but is not limited to—unauthorized intrusions, vandalism, theft, the abandonment of objects, and the formation of unusual gatherings. These features drastically reduce the time required for human operators to identify threats and allow for faster decision making.
- Miniature and covert cameras: Discreetly installed in high-sensitivity areas, these small and visually unobtrusive devices are selected for their ability to blend into the environment while still providing high-quality surveillance. Their design ensures that they do not interfere with the visual or architectural harmony of the monitored zones, especially in culturally or historically sensitive locations.
Due to the unique structural and spatial constraints of the site, a custom genetic algorithm [7,25,26] was used to optimize both the quantity and the spatial distribution of the cameras. This algorithm allows for an ideal balance between surveillance coverage and investment efficiency, ensuring that resources are allocated intelligently to maximize cost–benefit outcomes while maintaining high levels of security performance.
The video surveillance system has been further strengthened by the integration of Unmanned Aerial Vehicles (UAVs), ensuring the constant availability of a remote monitoring capability. This enhancement allows security and safety teams to benefit from rapid, efficient, and highly effective aerial surveillance, significantly improving the overall safety of the monitored area while minimizing potential risks.
UAVs, commonly referred to as drones, provide a unique advantage by offering a flexible and dynamic “eye in the sky” that can be quickly deployed whenever needed. Equipped with high-definition cameras, thermal imaging sensors, and other advanced technologies, UAVs can capture detailed real-time visual and environmental data from a wide range of altitudes and angles. This capability is particularly valuable for covering large, complex, or difficult-to-access areas where fixed surveillance cameras may have blind spots or limitations.
In addition to routine patrol missions, UAVs can be programmed for automated surveillance routes or manually piloted for targeted investigations, such as monitoring sensitive zones, responding to specific security alerts, or inspecting building for signs of damage or intrusion. Their rapid deployment ability ensures that security and safety operators can react almost instantaneously to emerging threats, enhancing response times and reducing the likelihood of escalation.
Moreover, the integration of UAVs into the surveillance supports proactive risk management. By gathering aerial imagery and data, the system enables predictive analysis, early threat detection, and strategic planning for incident prevention. The visual information collected can also be archived and analyzed over time to identify patterns, assess vulnerabilities, and improve long-term security strategies.
The use of UAVs additionally reduces the risks faced by security and safety personnel, allowing hazardous areas to be inspected remotely without exposing staff to potential danger. In critical situations such as emergency evacuations, natural disasters, or security breaches, UAVs can provide immediate situational awareness, guiding both decision-making and operational actions.
In conclusion, the inclusion of UAVs within the video surveillance system represents a transformative advancement, combining technological innovation with operational excellence to deliver a higher level of protection, efficiency, and resilience in security management.
All camera feeds are transmitted through the data communication infrastructure, which channels the video streams to several important destinations as follows: the Control Room, the Data Center, and various Area Security Checkpoints distributed across the monitored area. These key hubs are responsible for real-time monitoring and incident response coordination, and they will be described in more detail in the subsequent sections.
In particular, the video streams directed to the Data Center are securely stored using redundant servers—both on-site and in cloud environments—to ensure data integrity and availability. These video feeds are then processed using a sophisticated AI-driven video analytics system, which continuously scans the footage for indicators of critical or suspicious situations. The system is capable of identifying and alerting staff to events such as thefts, vandalism, aggressive behavior, panic situations, and other emergencies.
Further, proper intrusion detection sensors have been installed in all the necessary areas to be protected by this kind of devices.
Upon the detection of a potential threat, the system immediately notifies security personnel via the central Control Room and the relevant Area Security Checkpoints. This rapid alert mechanism enables swift intervention and ensures that appropriate measures can be taken to manage and neutralize the situation effectively and efficiently, minimizing risk to individuals and property.
9. The Control Room and the Area Security Checkpoints
A brand-new Control Room has been developed and implemented to host and manage all processing and monitoring equipment that comprise the integrated technological infrastructure. These two core facilities serve as the operational and analytical backbone of the entire surveillance and security and safety ecosystem, ensuring that all activities related to monitoring, data management, and response coordination are carried out in an optimized and centralized manner.
The design and construction of these facilities were driven by the imperative to achieve high energy efficiency. Particular attention was paid to minimizing power consumption through the adoption of cutting-edge technologies, smart power management systems, and the integration of alternative energy sources, such as solar and renewable systems, where possible. This approach reflects a strong commitment to sustainability and environmental responsibility while ensuring uninterrupted operation and system resilience.
The Control Room itself is equipped with a sophisticated video wall panel, consisting of multiple high-definition, high-performance monitors arranged to provide operators with a panoramic and detailed real-time view of all surveillance zones. This immersive setup allows security staff to maintain constant visual control over both the central site and all associated peripheral locations. Dedicated operator workstations are ergonomically designed and fully equipped with communication and control interfaces, enabling personnel to perform continuous 24/7 monitoring and response operations throughout the entire year, without interruption.
A dedicated technical section within the Control Room is reserved for system infrastructure technicians. This specialized area is staffed by professionals responsible for overseeing the operation of all IT, network, and hardware components. Their role includes real-time supervision, diagnostics, and the execution of both routine and emergency maintenance tasks. This structural separation of duties ensures that while security operators focus on surveillance and incident response, technical personnel remain fully engaged in preserving the operational integrity and reliability of the system at a deeper level. This dual-layered approach is essential for guaranteeing maximum system availability, fault tolerance, and overall technological resilience.
In addition to the central control infrastructure, a series of Area Security Checkpoints (ASCPs) have also been established, both within the central facility (including all primary access points and internal zones) and across various remote satellite locations. These field-based stations are manned by on-site security personnel who have direct visual access to the video feeds and system alerts relevant to their designated areas. This physical presence in the field empowers them to respond rapidly and efficiently to any emerging critical event, ensuring immediate intervention capabilities. Furthermore, these local operators remain in constant communication with the main Control Room, enabling coordinated action, real-time status updates, and access to supervisory guidance when dealing with complex or escalated situations.
All operations within this advanced environment follow a comprehensive set of standard operating procedures (SOPs), developed under a structured and continuously improving security procedure management system. This system is built upon the PDCA (Plan, Do, Check, Act) methodology, which supports the iterative improvement and strategic refinement of all internal processes. By adhering to this model, the organization ensures that every component of its technological and operational framework operates at maximum efficiency and effectiveness, aligning with best practices in critical infrastructure management and modern security governance.
10. The Data Center and the Artificial Intelligence Engine
To further reinforce the system’s robustness, a state-of-the-art Data Center was constructed as an integral part of the facility. This center was specifically designed to safely host all essential components of the integrated technological ecosystem—including servers, data storage units, networking equipment, and analytical platforms. The infrastructure was engineered to meet rigorous standards of physical and digital security, ensuring data protection and system durability under all operating conditions. The Data Center is continuously monitored by the technical personnel stationed in the Control Room’s infrastructure section, allowing for ongoing performance assessments and proactive maintenance to prevent failures or service interruptions.
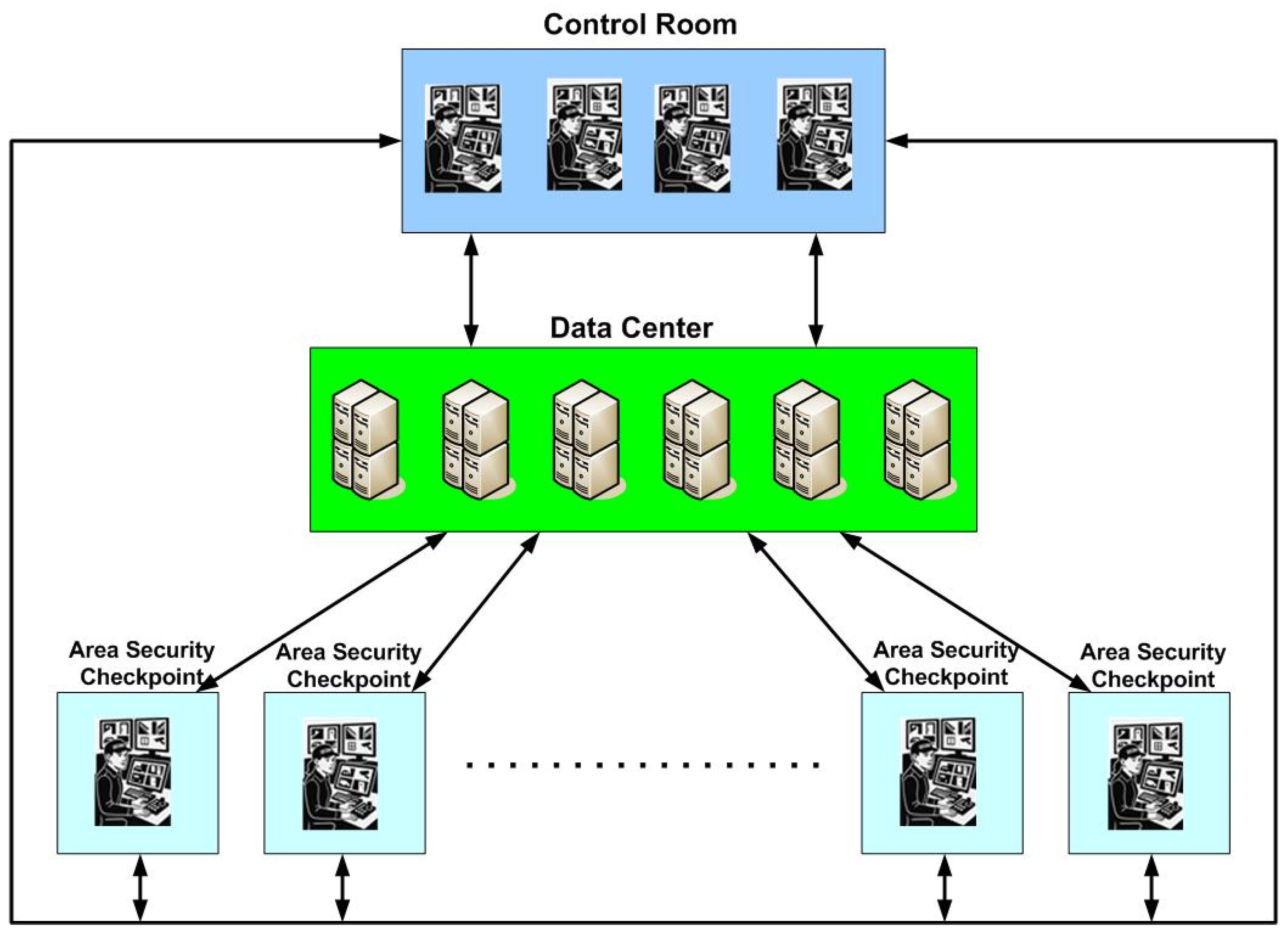
The operative scheme of the Control Room, Data Center, and Area Security Checkpoints is shown in Figure 8.
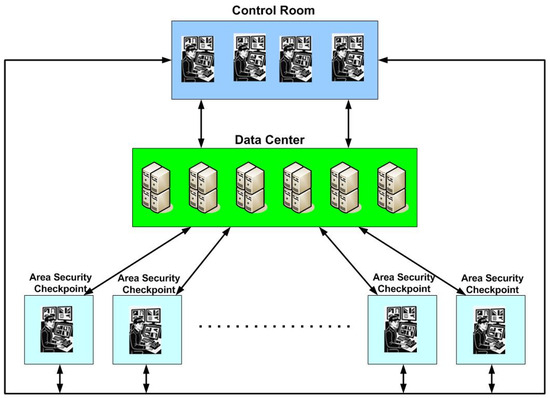
Figure 8.
Operative scheme of the Control Room, Data Center and Area Security Checkpoints.
The computing power of the Data Center plays a pivotal role in enabling and sustaining the high-performance features of the integrated technological system deployed across the archeological site. Among these capabilities, particular emphasis is placed on those that rely on Artificial Intelligence (AI), which require not only considerable processing capacity but also robust, scalable, and resilient infrastructure.
Indeed, the Data Center acts as the central processing hub where all data streams—originating from a vast and heterogeneous network of sensors, monitoring devices, unmanned systems, mobile terminals, and communication platforms—are collected, synchronized, and analyzed in real time. These data sources include environmental and microclimatic sensors, structural health monitoring devices, visitor tracking systems, video surveillance cameras, access control terminals, crowd behavior detectors, etc. The aggregated data volume is substantial, both in velocity and in variety, necessitating a dedicated architecture capable of supporting continuous high-throughput operations.
At the core of this architecture lies a suite of AI modules, which represents the AI engine, specifically designed and optimized to process the incoming data through advanced algorithms such as machine learning, deep learning, pattern recognition, anomaly detection, and predictive analytics. These intelligent components are responsible for translating raw sensor data into actionable insights and automated responses. For example, AI routines continuously evaluate structural integrity indicators to identify early warning signs of damage or degradation. Other models interpret video feeds to detect unusual movements, unauthorized access attempts, or potentially hazardous behaviors.
Furthermore, AI contributes to the overall operational efficiency of the site by managing a wide range of ordinary processes, such as environmental regulation, energy consumption balancing, personnel scheduling, incident reporting, etc. It also plays a crucial role in coordinating emergency procedures by fusing data from multiple inputs and triggering preconfigured security and safety protocols in response to specific conditions or threats.
Thanks to the high-performance computing capabilities of the Data Center, these AI-driven processes can operate with low latency and high reliability, ensuring real-time situational awareness and rapid decision-making support. The system’s modularity and elasticity also allow for the seamless integration of future functionalities and the gradual incorporation of new data sources or analytical tools. Ultimately, this intelligent, data-centric infrastructure serves as the operational backbone for enhancing security and safety, improving conservation strategies, and streamlining the daily management of a complex and dynamic cultural heritage environment.
The project has devoted careful attention to principles of green computing—a set of practices aimed at reducing the environmental impact of IT infrastructure. In this regard, the systems and hardware deployed on site have been selected based on energy efficiency criteria, and the computational facilities—including servers, data processing units, and monitoring terminals—are hosted in structures powered by renewable energy sources. These structures have been engineered to optimize airflow, cooling, and power distribution, minimizing waste and ensuring that energy consumption is kept to a minimum even during peak processing loads.
Green computing does not only refer to hardware or power sources, but it also encompasses software-level optimizations, such as energy-aware algorithms, adaptive computing loads, and the intelligent scheduling of processing tasks during periods of lower environmental stress (e.g., cooler night-time hours). This contributes to a substantial reduction in the overall carbon footprint, aligning with the broader sustainability objectives of the project and complying with national and European environmental directives related to energy use and climate impact.
The data center has been strategically and efficiently integrated with cloud infrastructure to fully leverage the advantages offered by cloud-based operations. This integration enables the execution of all tasks and processes that are technically and operationally suitable for cloud environments, such as scalable computing, automated deployments, and resource optimization. Moreover, the cloud connection ensures a secure and continuous backup of critical data and applications, safeguarding the integrity and availability of essential information. Particular attention has been devoted to implementing high standards of service continuity, so that operations remain stable and uninterrupted even in the event of local system failures or hardware issues. In addition, comprehensive disaster recovery mechanisms have been put in place, including multi-region redundancy, failover procedures, and regular validation of recovery plans, to guarantee the rapid restoration of services with minimal downtime and data loss. This hybrid approach combines the performance and control of on-premises infrastructure with the flexibility, resilience, and scalability of cloud computing, resulting in a robust and future-ready IT environment.
11. The Monitoring Systems
The set of projects that have been developed as part of this comprehensive initiative encompasses a wide array of advanced systems and technologies aimed at the continuous, multi-dimensional monitoring and management of the site and its surrounding environment. These include structural monitoring systems designed to track the integrity and behavior of buildings and archeological structures over time, as well as microclimatic and environmental monitoring networks that collect data on temperature, humidity, air quality, and other critical parameters that influence the preservation of cultural assets.
In addition, the system uses the features of the sophisticated and integrated video surveillance infrastructure, augmented by the strategic deployment of unmanned aerial vehicles (UAVs) and the utilization of high-resolution satellite imagery and remote sensing data. These tools collectively allow for the acquisition of a vast and diverse dataset that encompasses structural, topographic, atmospheric, and human activity-related information. This comprehensive and multi-source data acquisition strategy is essential for capturing both the static and dynamic aspects of the site’s conditions, ensuring the ability to respond not only to long-term trends but also to sudden, critical events in real time.
The collected data, once acquired, is subjected to in-depth analysis using both traditional computational models and real-time data processing algorithms. This enables operators and researchers to gain timely and actionable insights into a wide range of issues, from routine operational management to the handling of emergency situations. Of particular importance is the capacity to monitor and address phenomena related to climate change, such as the increased frequency of extreme weather events, temperature anomalies, rising humidity, and soil instability, all of which can pose significant risks to cultural heritage sites. By effectively integrating all these data sources and analytical tools, the system greatly enhances the risk management capabilities of the considered site, enabling more effective planning, mitigation, and emergency response strategies.
Crucially, this risk management capability is not confined solely to the core archeological site, but it is also extended to encompass a broader geographic scope, including the so-called peripheral sites, as well as the wider surrounding territorial context. This expansion ensures a more holistic approach to site management and conservation, recognizing that environmental, climatic, and anthropogenic pressures do not respect administrative boundaries and must be addressed through integrated, multi-scale strategies.
Within the broader framework of the Smart@Pompeii development initiative, a key element has been the integration of satellite data derived from internationally recognized Earth Observation programs, specifically, the European Copernicus program and Italy’s COSMO-SkyMed satellite constellation. The Copernicus Earth Observation Program, coordinated by the European Commission in collaboration with the European Space Agency (ESA), provides high-quality, timely, and freely accessible data and services. These include land surface monitoring, atmospheric composition analysis, climate change indicators, and emergency management tools. In the context of site preservation, security, and safety, Copernicus delivers accurate insights into land use changes, vegetation health, urban development pressures, and potential natural hazards, supporting informed decision making across a broad spectrum of disciplines.
The COSMO-SkyMed (Constellation of Small Satellites for Mediterranean basin Observation), developed by the Italian Space Agency (ASI) and the Italian Ministry of Defense, is a dual-use (civil and military) satellite system composed of radar imaging satellites capable of capturing high-resolution images under all weather conditions, day and night. In the field of Cultural Heritage, COSMO-SkyMed plays a crucial role by continuously observing monuments, archeological areas, historic buildings, and cultural landscapes in both Italy and around the world. Through repeat satellite passes and interferometric analysis, it is possible to detect and track temporal changes, such as subsidence, structural deformation, unauthorized construction, and environmental degradation, offering early warning capabilities and valuable long-term trend data.
The integration of these satellite data sources into the overarching Smart Mapping Interface (SMI) component—described in detail in the following sections—enables a highly advanced form of spatiotemporal monitoring. With this interface, users can not only visualize but also predict the evolution over time of numerous complex and interrelated phenomena. These include, but are not limited to, the stability of soils and archeological structures, ongoing structural deformations, hydrogeological risks, anthropogenic pressures (such as illegal excavation or unauthorized access), the proliferation of weed vegetation, and the presence and diffusion of airborne or surface-level pollutants, which may negatively impact exposed heritage materials and surfaces.
To support this vast and multi-faceted ecosystem, a powerful artificial intelligence (AI) engine has been developed and deployed. This AI system is underpinned by a variety of advanced technologies and methodologies, including Big Data analysis, video analytics, data mining techniques, and in some cases, blockchain-based data certification and traceability. These tools enable the system to perform predictive analytics across a wide range of parameters and threat vectors. For example, the AI engine can identify patterns that precede environmental deterioration, detect subtle changes in vegetation that signal underground anomalies, or correlate climate data with structural stresses, thereby helping experts anticipate critical situations before they manifest visibly.
In this way, the technological platform not only serves as a real-time monitoring and management system, but it also evolves into a proactive and preventive decision-support tool, contributing to the preservation, security, and sustainable management of one of the world’s most valuable archeological and cultural heritage areas.
12. The New Technologies for Renewable Energies, Lighting, and Communications
As part of the Smart@Pompeii initiative, significant emphasis was placed on the incorporation of renewable energy technologies with the goal of promoting environmental sustainability, energy autonomy, and technological innovation in the context of high historical and cultural value applications. In this way, not only was green energy properly utilized—enhancing the system’s reliability and resilience from this perspective—but innovative components were also introduced, significantly contributing to the IoT/IoE functionalities.
One of the most innovative and symbolic interventions involved the installation of photovoltaic roof tiles, a solution specifically chosen for its ability to seamlessly integrate into the delicate architectural and aesthetic context of the archeological site, particularly during restoration activities on the ancient domus. These specialized photovoltaic elements have been designed to replicate the appearance and texture of traditional Roman roofing materials, ensuring full compatibility with the visual identity of the structures, while also delivering the functionality of modern solar energy generation.
The use of these solar roof tiles made it possible to establish localized energy production systems, effectively creating autonomous “green energy islands” within the archeological site. This decentralized approach to energy generation is particularly advantageous in an environment like Pompeii, where the underground infrastructure cannot be easily or extensively modified, and where the installation of conventional electrical cabling poses logistical challenges as well as potential risks to the integrity of ancient remains. Adopting a micro-grid model, these localized power systems are capable of supplying electricity to specific restoration zones, monitoring stations, and digital infrastructure nodes, without the need for invasive installation methods.
Moreover, the photovoltaic tiles contribute not only to energy production but also to the preservation of the architectural heritage. By serving as protective elements against rain, wind, and UV radiation, they help mitigate the effects of weathering on the reconstructed domus. In this way, the intervention supports a dual objective as follows: fostering environmental sustainability and enhancing the physical protection and conservation of ancient structures.
To complement this sustainable energy strategy, the Smart@Pompeii project also introduced a highly innovative communication infrastructure based on Li-Fi (Light Fidelity) technology. Unlike traditional Wi-Fi systems, which rely on radio waves, Li-Fi employs modulated LED lighting to transmit data at extremely high speeds, enabling ultra-broadband communication through light pulses that are imperceptible to the human eye. This technology has been implemented across various areas of the site and is in the process of further expansion to reach new sections.
Li-Fi offers multiple advantages in the context of a cultural heritage site. Firstly, it allows for the provision of high-speed Internet connectivity in areas where electromagnetic interference needs to be minimized or where the use of radio frequency-based networks is either not feasible or not permitted due to conservation constraints. Secondly, the LED lighting fixtures used in the system have been carefully selected to feature low emission levels in the blue light spectrum, which is known to be particularly harmful to ancient frescoes, pigments, and organic materials. By reducing blue light exposure, the Li-Fi infrastructure not only provides digital connectivity but also contributes to the long-term protection of fragile archeological artworks and surfaces.
In any case, the integrated technological system has been equipped with the advanced functionalities typically found in Building Management Systems (BMS), tailored specifically to support the diverse operational needs of the archeological park. This includes the centralized and automated management of various infrastructure components such as climate control (temperature and humidity), lighting systems adapted to the conservation requirements of archeological artifacts, energy optimization processes to reduce environmental impact, and the monitoring of structural and environmental conditions critical to heritage preservation. The BMS functionalities also enable remote access and real-time diagnostics, allowing facility managers and technical staff to intervene promptly in case of anomalies or emergencies.
Altogether, these interventions—spanning renewable energy generation, energy-efficient communication systems, and sustainable computing infrastructure—represent a forward-thinking model of how advanced technologies can be harmonized with the needs of heritage conservation. They showcase the possibility of transforming an archeological site not only into a place of historical memory and cultural significance but also into a living laboratory for environmental innovation, where the past and the future meet through responsible and intelligent design.
13. The Security Check-In
All entry points to the site have been fully equipped with advanced security technologies, including walk-through metal detectors and X-ray baggage scanning systems, ensuring that every individual and item entering the premises is thoroughly screened. These technological systems are complemented by the presence of trained security personnel, who are responsible for conducting manual inspections when necessary, supervising the screening operations, and maintaining situational awareness at all times.
This comprehensive security setup has been implemented with the primary objective of enhancing the overall security, safety, and protection of the site, particularly in light of the need to safeguard both visitors and staff, as well as the invaluable cultural and historical assets contained within. By integrating human oversight with sophisticated detection technologies, the system significantly reduces the likelihood of unauthorized or dangerous items being brought into the area, including weapons, explosives, or other prohibited materials.
Among the many advantages of this system, there is a notable improvement in incident prevention, allowing potential threats to be identified and neutralized before they can escalate. Additionally, the presence of visible and active security measures serves as a deterrent to malicious behavior, helping to maintain a calm, orderly, and respectful atmosphere within the site.
From a visitor’s perspective, this level of security provides a greater sense of reassurance and peace of mind, encouraging public confidence and allowing guests to enjoy their experience without fear or concern. Furthermore, the efficient and streamlined nature of the screening process ensures that these elevated security and safety standards do not come at the cost of convenience, allowing for smooth entry while maintaining rigorous control protocols.
Overall, the integration of metal detectors, X-ray scanners, and expert security personnel represents a modern, proactive approach to access control, aligning the site with international standards for cultural heritage protection and public security and safety management.
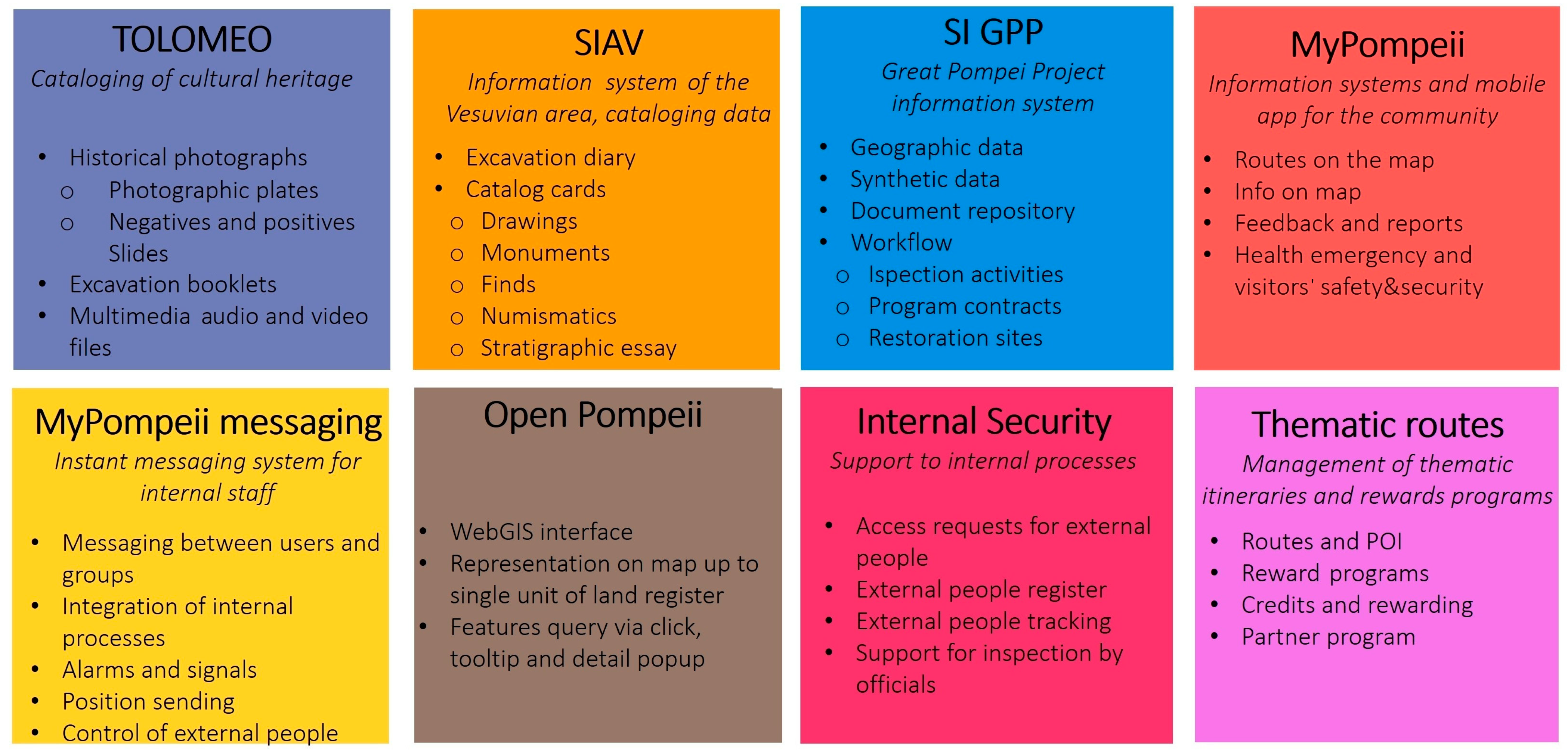
15. The Informative Systems
Various integrated information systems have been developed to offer a wide range of services supporting security, safety, and management—covering both on-site and remote visitor experiences, as well as access to archival resources.
They are represented by the following:
- TOLOMEO, a cataloging system of cultural heritage. Its main features are the following: historical photographs (photographic plates, negative and positive slides, etc.); excavation booklets; multimedia audio and video files.
- SIAV, an information system of the Vesuvian area, cataloging data for the catalog. Its main features are the following: excavation diary; catalog cards (drawings, monuments, finds, numismatics, stratigraphic essay, etc.).
- SI GPP, the great Pompeii project information system. Its main features are as follows: geographic data; synthetic data; document repository; workflow (inspection activities, program contracts, restoration sites, etc.)
- MyPompeii, an information system and mobile app for the community. Its main features are the following: routes on the map; info on the map; feedback and reports; health emergency and visitors’ safety and security; etc.
- My Pompeii Messaging, an instant messaging system for internal staff. Its main features are the following: messaging between users and groups; integration of internal processes; alarms and signals; position sending; control of external people; etc.
- Open Pompeii, a system to access Pompeii information. Its main features are the following: WebGIS interface; representation on map up to a single unit of land register; features query via clicking, tooltip, and detail popup; etc.
- Internal Security, a system to support the internal processes. Its main features are the following: access requests for external people; external people register; external people tracking; support for inspection; etc.
- Thematic Routes, a system for the management of thematic itineraries and reward programs. Its main features are the following: routes and POI (Point of Interest); reward programs; credit and rewarding; partner program.
They are also integrated with the Shared Safeness app and Smart Mapping Interface system that is illustrated in the following.
An overview is provided in Figure 9.
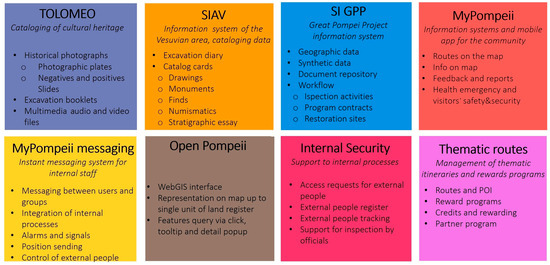
Figure 9.
Scheme of information systems.
As an integral component of the Park’s comprehensive informative system, a wide range of activities has been strategically planned to develop and implement advanced technological solutions aimed at enhancing the protection, management, and preservation of the archeological heritage. These solutions are designed not only to facilitate the regular inspections conducted by technical staff but to also strengthen the ability to monitor and respond to critical situations that may arise due to natural, environmental, or anthropogenic factors.
Among the planned activities is the development of tools to support on-site inspections by trained technicians. These inspections will be aided by mobile technologies, integrated data systems, and digital interfaces, enabling the faster and more precise identification of structural damage, environmental degradation, or other anomalies. In particularly sensitive or high-risk areas, instrumental monitoring is activated to ensure continuous surveillance. This includes the use of sensors, environmental data loggers, and early warning systems that can provide real-time alerts when predefined thresholds are exceeded.
Moreover, as illustrated before, the initiative includes the re-processing and analysis of satellite-derived data, allowing for the remote observation of large areas and the detection of gradual or sudden changes in the terrain or built structures. Complementing this, the use of UAV technology has become a key feature in data acquisition efforts. UAVs are also employed to capture high-resolution aerial imagery of the archeological site. These images then undergo sophisticated post-processing techniques—including photogrammetry, 3D reconstruction, and automated image analysis—to detect even subtle signs of deterioration, deformation, or damage not easily visible during ground inspections.
In addition, diagnostic investigations conducted using techniques such as ground-penetrating radar, infrared thermography, and laser scanning provide critical data about subsurface structures and material conditions. The re-processing of these diagnostic data support the creation of detailed risk maps, highlighting vulnerable zones, structural weaknesses, and areas with high exposure to environmental threats such as humidity, erosion, or seismic activity.
All these activities are part of a broader strategy aimed at identifying and classifying potential risks to the protected archeological assets. This includes not only the physical vulnerability of the artifacts and structures themselves but also their contextual exposure—such as visitor flow, environmental conditions, and proximity to infrastructure. Understanding these risk factors is essential to developing effective, evidence-based conservation and maintenance strategies.
The proposed model for this risk assessment and management process is structured in five sequential stages. The first stage, Knowledge, represents the foundational understanding of the site, much of which has already been established through the previous Great Pompeii Project that began in 2013. This includes detailed documentation, historical research, and baseline condition assessments of the site’s structures and features.
The second stage involves Expeditious Inspections, which refers to systematic surveys of all archeological assets using a comprehensive, site-wide approach. These inspections are designed to be repeated on a semi-annual or annual basis and feed into a centralized damage/defect/criticality database, which forms part of the broader Smart@Pompeii project. The structured and periodic nature of these inspections ensures that the site is regularly monitored and that emerging issues can be addressed promptly.
In the third stage, the focus shifts to the Identification of Potential Risk Classes. Here, different areas, structures, and elements within the site are categorized based on their level of risk, taking into account both their physical condition and their contextual exposure. This classification serves as a critical input for prioritizing interventions and allocating resources efficiently.
The fourth stage emphasizes the Monitoring of the Riskiest Situations, where targeted observation and data collection will be intensified in the areas most susceptible to damage or degradation. This monitoring is expected to be continuous or periodic depending on the severity of the risk and will rely heavily on the technological infrastructure developed under the informative system.
The final stage involves In-Depth Analysis of Specific Situations, where complex or ambiguous cases are examined in greater detail. These analyses will provide essential information to inform the long-term maintenance management plan, ensuring that conservation efforts are both proactive and sustainable.
Ultimately, the results of all these activities and analyses are integrated into the park’s Web-GIS information system. This centralized geospatial platform will allow authorized users to visualize, analyze, and manage spatial data related to the condition and maintenance of the archeological assets. Additionally, the inspection activities are interconnected with the instant messaging system, which enhances coordination among staff, enables real-time communication during fieldwork, and streamlines the overall workflow of site monitoring and management.
16. The Smart Mapping Interface System
One of the most innovative and strategically important components within both the Security & Safety initiatives and the broader spectrum of digital transformation projects at the Archeological Park is the Smart Mapping Interface (SMI). This cutting-edge platform serves not only as a central monitoring hub but also as a comprehensive integration system capable of consolidating data from a wide variety of independent sources and technologies into a unified and interactive environment. The SMI is specifically designed to support real-time decision making, enhance situational awareness, and foster proactive site management across all operational domains.
At the heart of the SMI lies a powerful Digital Twin of the entire Archeological Park, enabling stakeholders—ranging from security and safety operators to cultural heritage managers—to achieve a full-spectrum, geospatial view of every physical and virtual component within the monitored environment. This immersive and detailed 3D visualization allows for complete operational control over all the site’s infrastructures, systems, and ongoing activities, including the real-time tracking and visualization of installed devices (such as sensors, cameras, and control units), as well as the dynamic presence of staff members, maintenance personnel, and visitors moving throughout the park.
Beyond its mapping and visualization capabilities, the SMI is tightly integrated with the park’s overarching digital platform infrastructure, making it capable of processing and aggregating data from a heterogeneous ecosystem of sources. These sources include, but are not limited to the following: video surveillance systems, access control points, intrusion detection devices, seismic activity sensors, hydrogeological monitoring stations, air quality detectors, unmanned aerial vehicles, mobile digital applications used by visitors, etc. Through advanced data fusion techniques, the platform ensures that all collected information is synchronized, contextualized, and made available for real-time analysis.
The user interface of the SMI is engineered according to the principles of Natural User Interface (NUI) design, which ensures that users can interact with the system in a highly intuitive and human-centered way. Through visual, gestural, or touch-based controls, operators can easily navigate the 3D map, access real-time data streams, and receive immediate notifications regarding anomalies, breaches, or emergencies. When certain thresholds are exceeded—whether in temperature, crowd density, air quality, or any other predefined metric—the system automatically generates alerts and alarms, which are clearly displayed on the interface and can also be pushed to relevant personnel for prompt response.
Another unique and forward-looking feature of the Smart Mapping Interface is its built-in Sentiment Analysis module, which serves as a real-time feedback engine based on the collection and intelligent analysis of publicly available social media content. By scanning platforms such as Twitter, Facebook, Instagram, and others, the system is capable of extracting and interpreting user opinions, emotions, and attitudes expressed about the site. These sentiments are then categorized, quantified, and visually represented through dynamically updated graphs, charts, and dashboards, providing immediate insights into public perception. This capability allows management to take data-driven actions in response to emerging trends or negative feedback, improving visitor engagement, service quality, and overall reputation management.
The operative scheme of SMI and other IT applications is shown in Figure 10.
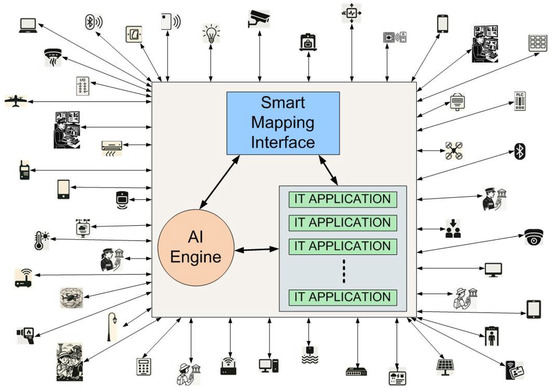
Figure 10.
Operative scheme of SMI and other IT applications.
In addition to digital sentiment gathering, the SMI benefits from physical data collection through the use of crowd sensing technologies strategically deployed throughout the park. Specifically, a network of crowd sensing cells has been installed at all major entrances and other high-traffic areas. These systems gather anonymous metadata from mobile devices—using information derived from SIM cards and network signals—in strict accordance with privacy regulations and data protection laws. Once processed and anonymized, the resulting data provide crucial insights into the number of visitors, their distribution within different zones, as well as aggregated demographic information such as nationality, average age, and gender. These data are not stored in any personally identifiable form, ensuring compliance with GDPR and other relevant privacy frameworks.
Thanks to the seamless integration of these diverse datasets—from environmental monitoring to human sentiment and mobility tracking—the Smart Mapping Interface delivers a high-performance analytical environment. This empowers stakeholders with actionable insights for both proactive safety and security operations and efficient resource management. For instance, by correlating visitor flow data with environmental stress indicators, managers can make informed decisions on where to deploy staff, schedule maintenance, or implement temporary restrictions. In emergency scenarios, the SMI becomes a critical tool for coordinating evacuation strategies, dispatching personnel, and maintaining overall command and control in complex situations.
17. The ISIDE Training Project
In order to significantly enhance the level of expertise, awareness, and operational competence of all individuals involved in the management and implementation of security and safety procedures, a comprehensive and structured training initiative was launched under the name ISIDE. The ISIDE project—ISIS in English—represents a cornerstone of capacity-building efforts within the broader framework of security and safety strategies implemented across the Campania Region.
This program was designed with the explicit goal of ensuring that all staff members working within the Ministry of Culture in the Campania region are equipped with up-to-date knowledge, practical skills, and the ability to respond effectively to a broad spectrum of security and safety challenges that may arise within cultural and archeological sites. The initiative aims to create a shared culture of preparedness, risk awareness, and coordinated response, bridging the gap between heritage protection, visitor security and safety, and national security protocols.
The ISIDE training system is composed of a modular and multi-layered curriculum, structured to address the diverse needs and roles of different stakeholders. It integrates a variety of educational formats to ensure flexibility, accessibility, and maximum learning impact. Specifically, the program includes the following:
- In-person classroom training sessions, which are conducted by subject matter experts and certified professionals in the fields of security, safety, risk assessment, emergency management, technological surveillance, and crowd control. These sessions promote active discussion, case study analysis, and practical exercises in a traditional educational setting.
- Live online training modules, which enable real-time remote participation, allowing geographically dispersed personnel to attend interactive lectures, take part in digital simulations, and engage with trainers through live Q&A sessions. This format supports synchronous learning while minimizing travel and logistical challenges.
- On-demand (deferred) e-learning courses, which are pre-recorded and made accessible through a dedicated online platform. These self-paced modules allow participants to access content anytime and anywhere, thus accommodating different learning schedules and reinforcing key concepts through repetition and review.
- Immersive simulation-based training, which leverages advanced technologies such as virtual reality (VR) headsets, 3D-rendered environments, and interactive control interfaces. Participants are placed within highly realistic risk scenarios—such as natural disasters, terrorist attacks, public health emergencies, or crowd surges—where they must make real-time decisions, apply emergency procedures, and coordinate responses as if in a live situation. These simulations are designed to increase familiarity with crisis dynamics and improve performance under pressure, all within a safe and controlled digital environment.
Through this multifaceted approach, the ISIDE program does not merely deliver theoretical knowledge but also cultivates practical capabilities and reflex-based reactions that are essential in emergency contexts. By combining educational content with experiential learning, the initiative ensures that trainees gain first-hand exposure to realistic security and safety challenges and are prepared to execute their roles with confidence and professionalism.
An additional value of the ISIDE project lies in its ability to foster collaboration across institutions. By training both cultural heritage professionals and police forces within the same framework, it promotes inter-agency coordination, joint strategic planning, and a unified operational language, which are critical for efficient crisis response and the protection of complex sites such as archeological parks.
Ultimately, ISIDE contributes to building a resilient security and safety culture across the Ministry of Culture and regional law enforcement entities, strengthening the overall capacity to prevent, detect, manage, and recover from a wide array of threats—whether they are natural, accidental, or intentional. As a dynamic and scalable platform, ISIDE is also prepared for continuous evolution, incorporating new risks, technologies, and regulatory changes as they emerge, thereby maintaining its relevance and effectiveness over time.
18. Results
The following section presents the values of the main operational parameters of the integrated system, with the aim of providing a comprehensive and quantitative assessment of its performance. This evaluation was conducted by referring to industry standards, guidelines, and benchmarking practices commonly adopted in the security and surveillance technology sector [27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45].
Given the unique nature of the site and the limited availability of the scientific literature addressing comparable integrated systems implemented in cultural heritage environments such as this, it is unfortunately not possible to directly compare the recorded values with those from identical or equivalent systems. Nevertheless, the metrics obtained are in line with, and in several instances even superior to, those observed in partially comparable systems employed in different contexts, as will be further illustrated below [46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77].
To provide structure to the performance analysis, the evaluation criteria have been grouped into two main categories.
The first category includes parameters related to the following:
- Performance benchmarks.
- System latency.
- Reliability metrics.
With regard to performance benchmarks, the following parameters were considered:
- Event processing capacity (e.g., number of analyzed video events and managed alarms per second).
- Average response time to an event (MTTR): time from event occurrence to notification/intervention.
- Maximum supported load (e.g., number of concurrent accesses and video streams).
- Accuracy of intelligent analysis (e.g., percentage of correct recognitions).
In terms of system latency, the following metrics were evaluated:
- Input latency: time between sensor activation and data recording.
- Processing latency: time required to analyze and process an event (e.g., video analysis).
- Notification latency: time from detection to operator notification.
- End-to-end latency: total time between event occurrence and system reaction (alarm, block, log).
- Jitter: variation in latency over time.
Regarding reliability metrics, the following were considered:
- MTBF (Mean Time Between Failures): average time between failures.
- MTTR (Mean Time To Repair): average time to restore system operation.
- Availability = MTBF/(MTBF + MTTR).
- Component error rate: e.g., percentage of video losses, failed access attempts.
The second group of evaluation parameters focuses on system accuracy and detection quality, and it includes the following:
- Accuracy: percentage of correctly classified events. Defined as (TP + TN)/(TP + TN + FP + FN), it provides a global measure of system effectiveness.
- Precision: indicates how reliable the generated alerts are. Defined as TP/(TP + FP), it reflects the system’s ability to minimize false alarms.
- Recall (Sensitivity): measures the ability to detect real threats. Defined as TP/(TP + FN), it reflects the system’s capacity to capture critical events.
- F1-score: harmonic mean of precision and recall. Defined as 2 × (Precision × Recall)/(Precision + Recall), especially useful when events are imbalanced between normal and anomalous.
- False Positive Rate (FPR): percentage of false alarms over non-threatening events. Defined as FP/(FP + TN), measuring how much the system triggers unnecessary alerts.
- False Negative Rate (FNR): percentage of undetected critical events. Defined as FN/(FN + TP), indicating the risk of the system missing actual threats.
- Availability: percentage of time the system is operational. Defined as MTBF/(MTBF + MTTR), reflecting overall system reliability.
Where
- TP = True Positive (correct detection of a real event).
- TN = True Negative (correct rejection of a non-event).
- FP = False Positive (incorrectly signaled event).
- FN = False Negative (missed real event).
The results obtained for the system under analysis are summarized in Table 1, which also includes the minimum and maximum reference values for comparable systems.

Table 1.
Results of performance analysis of the integrated system.
As observed from the presented data, the integrated system exhibits performance levels that are consistent with—and, in several key parameters, superior to—the best benchmark values for similar systems, whether these correspond to upper or lower bounds depending on the performance indicator. This confirms both the efficiency and the effectiveness of the implemented solution in ensuring robust and reliable security management within the site.
19. Conclusions
This work presents the innovative IoT/IoE-based integrated technological system developed for the Pompeii Archeological Park, emphasizing its role in enhancing security, safety, and heritage management within one of the world’s most complex and significant cultural heritage sites. The implementation of the Integrated Multidisciplinary Model for Security and Safety Management (IMMSSM), supported by advanced telecommunications, AI-powered monitoring systems, and sustainable energy solutions, represents a pioneering effort in cultural heritage preservation.
However, despite the achievements, several challenges emerged throughout the development and deployment phases. The historical and architectural sensitivity of the site imposed strict constraints on installation procedures, necessitating customized solutions that balanced technological effectiveness with minimal visual and structural impact. Additionally, the integration of diverse subsystems—ranging from surveillance to environmental monitoring and crowd management—demanded extensive coordination, interdisciplinary expertise, and iterative testing to ensure seamless interoperability.
Looking forward, future research should focus on evaluating the system’s performance over time, particularly in response to evolving threats, environmental conditions, and visitor dynamics. The potential of integrating more adaptive and self-learning AI models, as well as expanding the scope of predictive analytics for security and safety management, structural health monitoring and climate resilience, represents a promising direction. Furthermore, the broader applicability of the IMMSSM and its supporting technologies in other cultural heritage contexts—especially those in less resourced or more vulnerable regions—warrants thorough investigation.
By critically reflecting on both the strengths and limitations of the system, this work contributes to the growing field of intelligent cultural heritage protection and offers valuable insights for future interdisciplinary initiatives aimed at preserving humanity’s shared historical legacy.
Author Contributions
Conceptualization, A.B. and F.G.; Methodology, A.B. and F.G.; Software, A.B. and F.G.; Validation, A.B. and F.G.; Formal analysis, A.B. and F.G.; Investigation, A.B. and F.G.; Resources, A.B. and F.G.; Data curation, A.B. and F.G.; Writing – original draft, F.G.; Writing – review & editing, A.B.; Visualization, A.B. and F.G.; Supervision, A.B. and F.G.; Project administration, A.B.; Funding acquisition, A.B. All authors have read and agreed to the published version of the manuscript.
Funding
The “Safety and Security for Pompeii Archeological Park” project was funded by the National Operative Program “Legalità”—FESR/FSE 2014-2020 of the Ministry of the Interior of Italy, local identifier of operation n. 882. The “ISIDE” project was funded by the National Operative Program “Legalità”—FESR/FSE 2014-2020 of the Ministry of the Interior of Italy, local identifier of operation n. 1213.
Data Availability Statement
The data presented in this study are available upon request from the corresponding author due to privacy reasons.
Acknowledgments
The authors gratefully acknowledge all those who supported, were involved in, or contributed to the design and execution of the projects discussed in this paper.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Berry, J. The Complete Pompeii, 1st ed.; Thames & Hudson: London, UK, 2007. [Google Scholar]
- Beard, M. The Fires of Vesuvius: Pompeii Lost and Found, An Imprint of Harvard, 1st ed.; Belknap Press: Cambridge, MA, USA, 2010. [Google Scholar]
- Wilkinson, P. Pompeii: An Archaeological Guide, 1st ed.; Bloomsbury Academic: London, UK, 2019. [Google Scholar]
- Spina, L. Inside Pompeii, 1st ed.; J. Paul Getty Museum: Los Angeles, CA, USA, 2023. [Google Scholar]
- Garzia, F.; Sammarco, E.; Cusani, R. The integrated security system of the Vatican City State. Int. J. Saf. Secur. Eng. 2011, 1, 1–17. [Google Scholar] [CrossRef]
- Contardi, G.; Garzia, F.; Cusani, R. The integrated security system of the Senate of the Italian Republic. Int. J. Saf. Secur. Eng. 2011, 1, 219–246. [Google Scholar]
- Garzia, F. Implementing an Internet of Everything system in the archaeological area of Quintili’s Villa in the Ancient Appia route park in Rome. WIT Trans. Built Environ. 2017, 174, 261–272. [Google Scholar]
- Garzia, F. An integrated multidisciplinary model for security management and related supporting integrated technological system. In Proceedings of the IEEE International Carnahan Conference on Security Technologies, Orlando, FL, USA, 24 October 2016. [Google Scholar]
- Klein, L.J.; Bermudez, S.A.; Schrott, S.A.; Tsukada, M.; Dionisi-Vici, P.; Kargere, L.; Marianno, F.; Hamann, H.F.; López, V.; Leona, M. Wireless Sensor Platform for Cultural Heritage Monitoring and Modeling System. Sensors 2017, 17, 1998–2019. [Google Scholar] [CrossRef]
- Mesas-Carrascosa, F.J.; Verdú Santano, D.; Meroño de Larriva, J.E.; Ortíz Cordero, R.; Hidalgo Fernández, R.E.; García-Ferrer, A. Monitoring Heritage Buildings with Open Source Hardware Sensors: A Case Study of the Mosque-Cathedral of Córdoba. Sensor 2016, 16, 1620–1634. [Google Scholar] [CrossRef]
- Mitro, N.; Maria Krommyda, M.; Amditis, A. Smart Tags: IoT Sensors for Monitoring the Micro-Climate of Cultural Heritage Monuments. Appl. Sci. 2022, 12, 2315–2334. [Google Scholar] [CrossRef]
- Rioual, S.; Lescop, B.; Pellé, J.; De Alkmim Radicchi, G.; Chaumat, G.; Dominique Bruni, M.D.; Becker, J.; Thierry, D. Monitoring of the Environmental Corrosivity in Museums by RFID Sensors: Application to Pollution Emitted by Archeological Woods. Sustainability 2021, 13, 6158–6168. [Google Scholar] [CrossRef]
- Heesoo, C.; Sangheon, K. Proposal of smart guide system for cultural heritage of archaeological sites using IoT-focusing on Hoeamsa Temple site in Yangju. Korea. Math. Biosci. Eng. 2023, 20, 8745–8765. [Google Scholar]
- Liang, X.; Liu, F.; Wang, L.; Zheng, B.; Sun, Y. Internet of Cultural Things: Current Research, Challenges and Opportunities. Comput. Mater. Contin. 2023, 74, 469–488. [Google Scholar] [CrossRef]
- Kasnesis, P.; Tatlas, N.A.; Mitilineos, S.A.; Patrikakis, C.Z.; Potirakis, S.M. Acoustic Sensor Data Flow for Cultural Heritage Monitoring and Safeguarding. Sensors 2019, 19, 1629–1654. [Google Scholar] [CrossRef]
- Laohaviraphap, N.; Waroonkun, T. Integrating Artificial Intelligence and the Internet of Things in Cultural Heritage Preservation: A Systematic Review of Risk Management and Environmental Monitoring Strategies. Buildings 2024, 14, 3979–4007. [Google Scholar] [CrossRef]
- Mishra, M.; Lourenço, P.B. Artificial intelligence-assisted visual inspection for cultural heritage: State-of-the-art review. J. Cult. Herit. 2024, 66, 536–550. [Google Scholar] [CrossRef]
- Manikandan, C.; Rakesh Kumar, S.; Sai Siva Satwik, K.; Neelamegam, P.; Narasimhan, K.; Raju, N. An Integrated Object Tracking and Covert Visual MIMO Communication Service for Museum Security System Using Single Vision Sensor. Appl. Sci. 2018, 8, 1918–1936. [Google Scholar] [CrossRef]
- Rossi, M.; Bournas, D. Structural Health Monitoring and Management of Cultural Heritage Structures: A State-of-the-Art Review. Appl. Sci. 2023, 13, 6450–6487. [Google Scholar] [CrossRef]
- Altaweel, M.; Khelifi, A.; Shana’ah, M.M. Monitoring Looting at Cultural Heritage Sites: Applying Deep Learning on Optical Unmanned Aerial Vehicles Data as a Solution. Soc. Sci. Comput. Rev. 2024, 42, 480–495. [Google Scholar] [CrossRef]
- Núnez-Camarena, G.M.; Herrera-Limones, R.; López-Escamilla, A. Use of Unmanned Aerial Vehicle Technology in the Protection of Goods of Cultural Interest (GCIs): The Case of the Castle of Cala (Huelva, Spain). Architecture 2024, 4, 247–266. [Google Scholar] [CrossRef]
- Laugier, E.J.; Abdullatif, N.; Glatz, C. Embedding the remote sensing monitoring of archaeological site damage at the local level: Results from the “Archaeological practice and heritage protection in the Kurdistan Region of Iraq” project. PLoS ONE 2022, 17, e0269796. [Google Scholar] [CrossRef]
- Yu, Y.; Abu Raed, A.; Peng, Y.; Pottgiesser, U.; Verbree, E.; van Oosterom, P. How digital technologies have been applied for architectural heritage risk management: A systemic literature review from 2014 to 2024. npj Herit. Sci. 2025, 13, 45–60. [Google Scholar] [CrossRef]
- Bruni, A.; Garzia, F. The New Communication Network for an Internet of Things/Everything Based Security/Safety/General Management/Visitor's Services for the Pompei Archaeological Park, Italy. In Proceedings of the IEEE International Carnahan Conference on Security Technology, Pune, India, 11 October 2023. [Google Scholar]
- Goldberg, D.E. Genetic Algorithms in Search, Optimisation and Machine Learning, 1st ed.; Addison-Wesley: New York, NY, USA, 1989. [Google Scholar]
- Michalewicz, Z. Genetic Algorithms + Data Structures = Evolution Programs, 3rd ed.; Springer: New York, NY, USA, 2013. [Google Scholar]
- ISO/IEC 27001; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. International Organization for Standardization: London, UK, 2022.
- ISO/IEC 27002; Code of Practice for Information Security Controls. International Organization for Standardization: London, UK, 2022.
- ISO/IEC 27005; Information Security, Cybersecurity and Privacy Protection—Guidance on Managing Information Security Risks. International Organization for Standardization: London, UK, 2022.
- IEC 62443-x; Cybersecurity for Industrial Automation and Control Systems. IEC: Geneve, Switzerland, 2018–2024.
- ISO/IEC 25010; Systems and Software Engineering—Systems and Software Quality Requirements and Evaluation (SQuaRE)—System and Software Quality Models. International Organization for Standardization: London, UK, 2011.
- ONVIF Profile T Specification v1.0. 2018. Available online: https://www.onvif.org/wp-content/uploads/2018/09/ONVIF_Profile_T_Specification_v1-0.pdf (accessed on 16 February 2024).
- NIST Special Publication 800-53 Revision 5–Security and Privacy Controls for Information Systems and Organizations. 2020. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r5.pdf (accessed on 22 June 2025).
- EN 50131-x; Intrusion and Hold-Up Alarm Systems. 2006–2020 CENELEC. European Committee for Electrotechnical Standardization: Brussels, Belgium, 2014.
- EN 50132-x; CCTV Systems for Use in Security Applications. iTeh, Inc.: Newark, DE, USA, 2012.
- EN 60839-11; Alarm and Electronic Security Systems–Electronic Access Control Systems. IEC: Geneva, Switzerland, 2023–2015.
- EN 50518; Monitoring and Alarm Receiving Centres. KIWA: Rijswijk, The Netherlands, 2019.
- EN 62676-x; Video Surveillance Systems for Use in Security Applications. iTeh, Inc.: Newark, DE, USA, 2014.
- EN 50136-x; Alarm systems—Alarm transmission systems and equipment. KIWA: Rijswijk, The Netherlands, 2018.
- EN 50134-x; Social alarm systems. iTeh, Inc.: Newark, DE, USA, 2002–2021.
- IEC 61508; Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems. IEC: Geneva, Switzerland, 2010.
- IEC 62443; Security for Industrial Automation and Control Systems. IEC: Geneva, Switzerland, 2009–2024.
- ISO 16484-x; Building Automation and Control Systems (BACS). ISO: Geneva, Switzerland, 2005–2025.
- IEC 61131-3; Programmable Logic Controllers. IEC: Geneva, Switzerland, 2025.
- IEC 62381; Factory Acceptance and Site Acceptance Tests. IEC: Geneva, Switzerland, 2024.
- Recommendation Y.1541; Network Performance Objectives for IP-Based Services. International Telecommunication Union, Telecommunication Standardization Sector: Geneva, Switzerland, 2011.
- Recommendation, Y. Recommendation Y.1564; Ethernet Service Activation Test Methodology. International Telecommunication Union, Telecommunication Standardization Sector: Geneva, Switzerland, 2011.
- Draft Recommendation Y.IMT2020-jg-lsn (Subsequently ITU-T Y.3118); Requirements and Framework for Jitter Bound Guarantee in Large-Scale Networks Including IMT-2020 and Beyond. ITU-T Study Group 13: Geneva, Switzerland, 2022.
- Demichelis, C.; Chimento, P. RFC 3393: IP Packet Delay Variation Metric for IP Performance Metrics (IPPM); Internet Engineering Task Force (IETF): Fremont, CA, USA, 2002. [Google Scholar]
- U.S. Department of Homeland Security, Science and Technology Directorate; National Urban Security Technology Laboratory. Video Security Systems Technology Handbook; U.S. DHS: Washington, DC, USA, 2025. [Google Scholar]
- U.S. Department of Defense. MIL-HDBK-217F Notice 2: Military Handbook–Reliability Prediction of Electronic Equipment; Department of Defense: Washington, DC, USA, 1995. [Google Scholar]
- Stouffer, K.; Pillitteri, V.Y.; Lightman, S.; Abrams, M.; Hahn, A. Guide to Industrial Control Systems (ICS) Security—NIST Special Publication 800-82 Revision 3; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2022. [Google Scholar]
- Fagan, M.; Marron, J.; Olivieri, J.; Davidson, M.J. IoT Device Cybersecurity Capability Core Baseline (Final); NIST IR 8259A; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2020. [Google Scholar]
- National Institute of Standards and Technology (NIST). Cybersecurity Framework 2.0; NIST: Gaithersburg, MD, USA, 2024. [Google Scholar]
- IEC 62439-3:2021; Industrial Communication Networks –High Availability Automation Networks–Part 3: Parallel Redundancy Protocol (PRP) and High-availability Seamless Redundancy (HSR). IEC: Geneva, Switzerland, 2021.
- IEC TR 62380:2004; Reliability Data Handbook–Universal Model for Reliability Prediction of Electronics Components, PCBs and Equipment. IEC: Geneva, Switzerland, 2004.
- IEEE 802.24 TAG; Low Latency Communication White Paper. IEEE Standards Association: Piscataway, NJ, USA, 2023.
- SIA RF-01-2014; On-Premises RF Products–Technical Report–Terminology for Use in Specifying Product Parameters. Security Industry Association: Silver Spring, MD, USA, 2014.
- ANSI/SIA OSIPS-DVI-01:2008; Digital Video Interface Data Model. Security Industry Association: Silver Spring, MD, USA, 2008.
- ANSI/SIA OSIPS-01:2008; Open, Systems Integration and Performance Standards Framework. Security Industry Association: Silver Spring, MD, USA, 2008.
- DC-07-2001.04; Receiver-to-Computer Interface Protocol (Type 2)–for Central Station Equipment Communications. Security Industry Association: Silver Spring, MD, USA, 2001.
- DC-02-1992.02 (R2000.05); Generic Protocols Technical Report. Security Industry Association: Silver Spring, MD, USA, 1992.
- DC-01-1988 (R2001.04); DCS Computer Interface (CIS-1) Technical Report. Security Industry Association: Silver Spring, MD, USA, 1988.
- ANSI/SIA MSD-01-2000; Mobile Security Devices Standard–Monitoring Practices for False Dispatch Prevention. Security Industry Association: Silver Spring, MD, USA, 2000.
- ONVIF. ONVIF Profile S Specification; Version 1.3; ONVIF: San Ramon, CA, USA, 2019. [Google Scholar]
- ONVIF. ONVIF Profile M Specification; Version 1.0; ONVIF: San Ramon, CA, USA, 2021. [Google Scholar]
- ONVIF. ONVIF Profile A Specification; Version 1.0; ONVIF: San Ramon, CA, USA, 2017. [Google Scholar]
- ONVIF. ONVIF Profile C Specification; Version 1.0; ONVIF: San Ramon, CA, USA, 2014. [Google Scholar]
- ONVIF. ONVIF Profile D Specification; Version 1.0; ONVIF: San Ramon, CA, USA, 2021. [Google Scholar]
- ONVIF. ONVIF Core Specification; Version 2.42; ONVIF: San Ramon, CA, USA, 2022. [Google Scholar]
- Smith, J.L.; Doe, A.; Brown, E. Impact of Environmental Stress on Network Latency in Surveillance Systems. J. Security Netw. 2023, 12, 45–60. [Google Scholar]
- Şengönül, E.; Samet, R.; Abu Al-Haija, Q.; Alqahtani, A.; Alturki, B.; Alsulami, A.A. An Analysis of Artificial Intelligence Techniques in Surveillance Video Anomaly Detection: A Comprehensive Survey. Appl. Sci. 2023, 13, 4956. [Google Scholar] [CrossRef]
- Rausand, M. High-Availability System Design, 1st ed.; Springer: London, UK, 2013. [Google Scholar]
- Collier, Z.A.; Panwar, M.; Ganin, A.A.; Kott, A.; Linkov, I. Security Metrics in Industrial Control Systems. In Cyber Security of Industrial Control Systems, Including SCADA Systems; Colbert, E., Kott, A., Eds.; Springer: New York, NY, USA, 2016; pp. 167–185. [Google Scholar]
- Zvereva, A.K.; Kaprielova, M.; Grabovoy, A. AnomLite: Efficient binary and multiclass video anomaly detection. Results Eng. 2025, 25, 1004162. [Google Scholar] [CrossRef]
- Yu, S.; Zhu, Z.; Chen, Y.; Xu, H.; Zhao, P.; Wang, Y.; Padmanabhan, A.; Latapie, H.; Xu, H. VQPy: An Object-Oriented Approach to Modern Video Analytics. In Proceedings of the Machine Learning and Systems (MLSys) 2024; Gibbons, P., Pekhimenko, C., De Sa, C., Eds.; Machine Learning and Systems: Santa Clara, CA, USA, 2024; pp. 279–295. [Google Scholar]
- Smithashree, K.P.; Meghana, M.G.; Shamitha, R.; Suhasini, B.S.; Varsha, M.U. Secure Crowd AI–Crowd Estimation and Surveillance System. Int. Adv. Res. J. Sci. Eng. Technol. 2025, 12, 517–524. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).