Abstract
The low power wide area networks (LPWANs) based on the LoRaWAN standard are suitable for Internet of Things (IoT) applications that involve a large number of low-power devices distributed over large areas. The LoRaWAN standard imposes some limitations on end-device configuration, such as the medium access strategies to be adopted, which depend on the region in which the network operates. In particular, in Europe, according to the ETSI regulations, a LoRaWAN end-device can use either a pure ALOHA medium access control (MAC) protocol or a polite medium access technique based on Listen Before Talk (LBT) Adaptive Frequency Agility (AFA). The aim of this work is to investigate the combined use of the two MAC protocols in the same LoRaWAN network. In particular, the work presents a simulative assessment of a LoRaWAN network that combines the use of Pure ALOHA and LBT AFA in realistic scenarios, under different workloads, when they work in compliance with the ETSI regulations. The work provides quantitative information that can help the network designer choose which protocol is more suitable for achieving the desired performance.
1. Introduction
The Internet of Things (IoT) paradigm is spreading across several sectors, providing connectivity between people, smart sensors, computing devices, robots, digital machines, etc. [1,2,3,4]. In particular, IoT applications can be found in several domains, including smart cities and smart homes [5,6,7,8], smart monitoring [9,10,11,12], healthcare [13,14], and factory automation [15,16,17,18,19]. Since IoT scenarios are highly heterogeneous and the number of IoT applications [20,21] is steadily growing, the selection of wireless technologies capable of meeting their needs is wide, spanning low-power short-range technologies, such as RFID and Bluetooth Low Energy [22,23,24], high-power technologies, such as cellular networks [25], and some amendments to the IEEE 802.15.4 and IEEE 802.11 standards for Industrial IoT [26,27,28,29,30].
As a complement of the aforementioned technologies, low power wide area networks (LPWANs) offer connectivity solutions for IoT applications that require low throughput, low power consumption, and wide coverage range using low-cost devices [31]. A very popular LPWAN standard is the Long Range Wide Area Network (LoRaWAN) [32]. LoRaWAN works on top of Long Range (LoRa) modulation [33] and defines a system architecture and protocol standards that aim to satisfy multiple key IoT requirements, such as low cost, low power, mobility support and easy network reconfiguration [34,35].
According to the LoRaWAN regional parameters [36], different rules are defined for both the medium access strategy and the parameter configuration, depending on the region in which the LoRaWAN devices operate. In particular, in Europe, two different uncoordinated channel access strategies [37] can be adopted, i.e., based on Pure ALOHA or on a polite spectrum access technique involving a clear channel assessment (CCA) prior to transmission. In fact, the norms imposed by the European Telecommunications Standards Institute (ETSI) allow the usage of either a duty-cycle limitation or a transmission management based on Listen Before Talk (LBT) Adaptive Frequency Agility (AFA). As discussed in [37], Pure ALOHA and LBT AFA differ in multiple aspects. As Pure ALOHA does not use any CCA mechanism, it works in an energy-efficient way under low workloads, but it may suffer from a significant number of collisions under high network traffic. In contrast, by running the CCA before starting a transmission, LBT AFA can mitigate the message loss due to overlapping transmissions, at the expense of increasing the energy consumption.
Some works in the literature compared the medium access control (MAC) protocols supported by LoRaWAN [38,39]. However, to our knowledge, none of them evaluated the performance obtained by combining Pure ALOHA and LBT AFA on the same LoRaWAN network when they work in accordance with the ETSI regulations [40,41]. In contrast, this paper presents a performance assessment of a LoRaWAN network that combines the use of the two supported MAC protocols when they work in compliance with the ETSI regulations, with the aim of providing the network designer with useful information to choose the most suitable protocol to reach the desired performance metrics. The assessment is performed through simulations in realistic scenarios under different workload conditions.
The structure of this paper is the following. Section 2 recaps the relevant literature. Section 3 outlines the main features of LoRaWAN, while Section 4 presents the MAC protocols supported by LoRaWAN. Section 5 describes the envisaged network configuration scenarios, while Section 6 addresses the performance evaluation and discusses the results obtained. Finally, Section 7 concludes the paper and outlines further research threads.
2. Related Work
LPWANs are capable of connecting a large number of devices distributed in wide areas and, for this reason, represent a promising option to replace or complement traditional cellular and short-range wireless technologies [42,43,44]. Among LPWANs, the LoRaWAN standard is emerging thanks to its interesting features that offer wide communication ranges with a low-cost network infrastructure that includes low-power devices.
LoRaWAN supports single-hop LoRa-based transmissions. Consequently, LoRaWAN cannot, at the same time, achieve a wide coverage range and a relatively high bit rate by setting the LoRa modulation parameters. For this reason, several works propose novel medium access strategies and routing protocols for LoRa-based networks [45,46,47,48,49]. Among them, the proposals in [48,49] exploit the Software-Defined Networking (SDN) paradigm to implement priority-based traffic management mechanisms and load balancing algorithms [50,51,52,53].
Furthermore, LoRaWAN only supports random MAC protocols, and therefore cannot provide real-time flows with bounded delays. For this reason, several works in the literature deal with the proposal and evaluation of alternative MAC protocols to LoRaWAN ones. For example, the works in [54,55,56] propose centralized MAC protocols for LoRa-based networks that are capable of supporting real-time communications through a Time Division Multiple Access (TDMA) channel access method.
The previously described works introduce multiple extensions to the LoRaWAN standard and often build directly on the LoRa physical layer. As a result, they require custom software implementation on LoRaWAN commercial-off-the-shelf (COTS) devices.
LoRaWAN supports uncoordinated channel access strategies based on Pure ALOHA or LBT AFA. Several state-of-the-art works deal with simple random MAC protocols (similar to standard ones) for LoRaWAN, such as Slotted ALOHA [57,58] or other protocols based on LBT [59,60], providing comparisons [61].
The work in [38] summarizes the restrictions that the ETSI norms impose on some timing parameters and presents a comparative performance evaluation of Pure ALOHA and LBT AFA. The aim of [38] is to compare the packet-loss ratio obtained by each protocol through different simulations on the same network. Conversely, this work investigates the combined use of the two MAC protocols in the same LoRaWAN network, that is, in the simulation, some of the end-devices adopt Pure ALOHA and the others adopt LBT AFA. The aim here is to provide quantitative information on which protocol an end-device shall use to meet the requirements of its traffic flows. Furthermore, differently from the work in [38], here, we evaluate multiple performance metrics, i.e., the packet loss ratio, the packet discard ratio, the end-to-end delay, and the energy consumption ratio per transmission.
A performance evaluation of a LoRaWAN network in which both protocols, i.e., the Pure ALOHA and LBT, are adopted is addressed in [39,62]. However, none of them takes into account the limitations imposed by the ETSI norms defined in [40,41]. On the contrary, this paper addresses a performance assessment of a LoRaWAN network in which both the devices that use ALOHA-based and the devices that use LBT-based MAC protocols work in accordance with the ETSI norms. In particular, this paper discusses the results obtained through simulations in realistic scenarios under different workloads and provides useful information about the performance of the two MAC protocols. In this way, the network designer can choose the MAC protocol that is more suitable to achieve the desired performance.
3. LoRaWAN Background
LoRaWAN defines a system architecture to wirelessly connect battery-operated devices distributed over a large area. The LoRaWAN specification [32] also includes a protocol stack optimized to provide support for low-cost, mobile, and bidirectional communications for IoT applications.
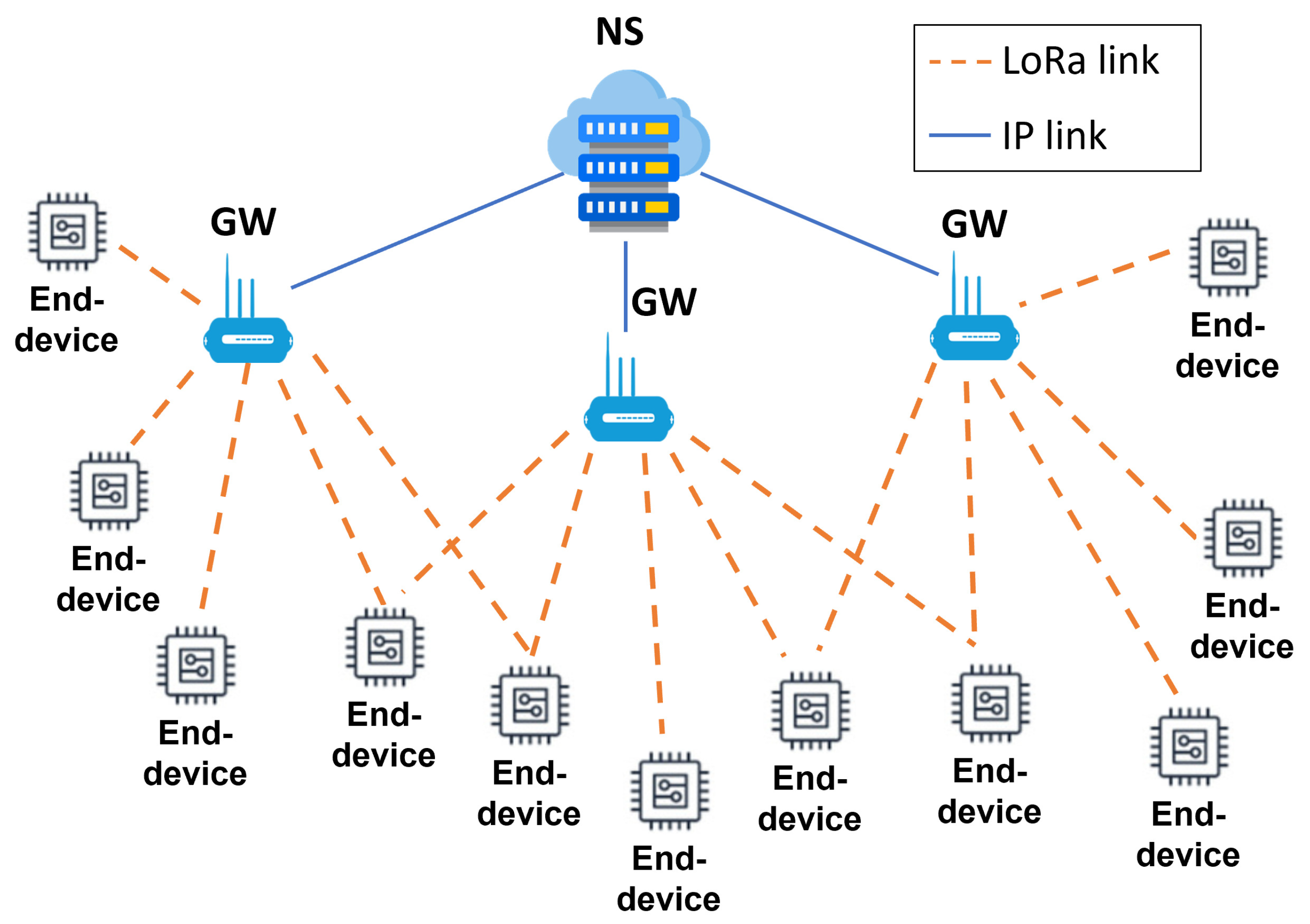
The LoRaWAN topology, shown in Figure 1, consists of a star-of-stars that includes several LoRaWAN end-devices, some gateways (GWs), and a network server (NS).
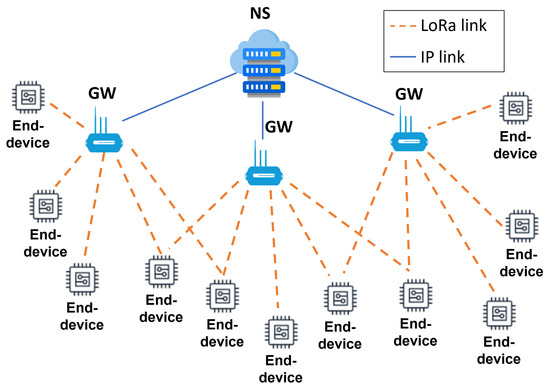
Figure 1.
The LoRaWAN topology.
Communication between the end-devices and the NS is bidirectional and goes through the GWs. In particular, the end-devices exchange messages with the GWs through single-hop LoRa transmissions, while each GW communicates with the NS via an IP connection. GWs relay messages from the end-devices to the NS (uplink) and vice versa (downlink). Note that a given uplink (UL) message is sent by an end-device to the NS through one or more GWs. Conversely, a downlink (DL) message is sent by the NS to a single end-device through only one GW.
LoRaWAN builds on LoRa [33], a spread spectrum modulation technique derived from Chirp Spread Spectrum (CSS) technology. The LoRa modulation allows the configuration of multiple parameters [63] that have an impact on communication performance in terms of bit rate, coverage, energy consumption, and robustness to interference or noise. The main LoRa parameters are the carrier frequency (CF), bandwidth (BW), spreading factor (SF), coding rate (CR), and transmission power (TP). In a LoRaWAN network, the time required by a message transmission using specific LoRa parameters is called the time on air (ToA) and is calculated through the Equation (1) provided in [64],
where
- NP: number of preamble symbols.
- SW: the length of the synchronization word.
- PL: the size of the physical payload in bytes.
- CRC: a Boolean flag relevant to the presence of the cyclic redundancy check (CRC).
- IH: a Boolean flag relevant to the presence of the physical header.
- DE: a Boolean flag relevant to the data rate optimization status.
- : the value of the parameter in formula .
LoRa parameters can assume multiple values based on the region in which the LoRaWAN devices operate, according to [36]. By configuring these parameters, it is possible to tune the bit rate, coverage, and energy consumption. For example, as discussed in [65,66], increasing SF expands coverage but reduces the bit rate by approximately half, thus almost doubling ToA and energy consumption.
According to [67,68] the SFs are quasi-orthogonal, and therefore, simultaneous transmissions that use different SFs on the same channel are not totally immune to each other. However, in case the signal-to-interference ratio (SIR) of the received messages exceeds the isolation threshold specified in [67], the messages can be correctly decoded.
The LoRaWAN Adaptive Data Rate (ADR) algorithm [69] allows the use of the highest possible bit rate to prolong the battery life of the end-device. In this way, each end-device can individually set its bit rate and TP. If ADR is enabled, the NS is in charge of managing the bit rate and TP of the end-devices using defined LoRaWAN MAC commands; otherwise, each end-device individually manages its bit rate and TP. Note that the mobile end-devices commonly disable the ADR mechanism, especially when the radio channel attenuation varies quickly, as the NS would not be able to efficiently handle the runtime configuration of their bit rate and TP.
In LoRaWAN, three different classes of end-devices, i.e., Class A, B and C, are defined.
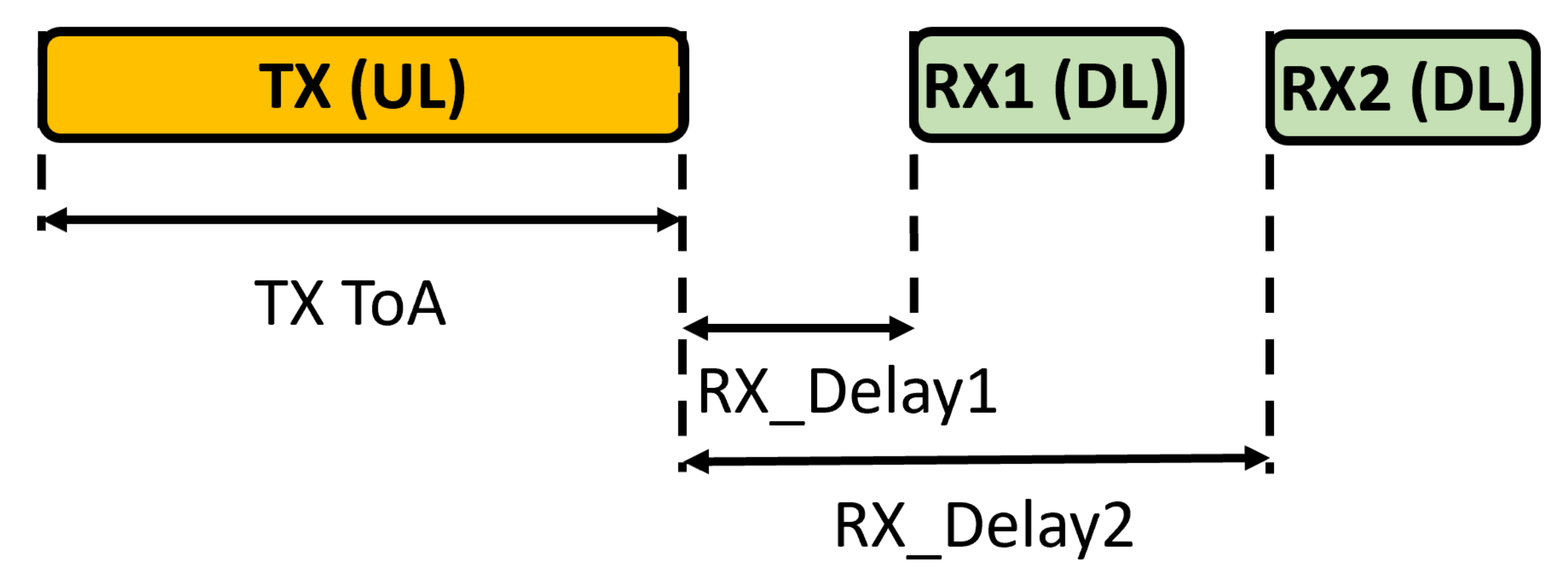
Class A (All) end-devices enable bidirectional communications while maintaining low energy consumption. In particular, Class A end-devices strongly favor UL communications, which are based on the communication needs of the end-device, while the transmission of DL messages is allowed only after the end-device has successfully sent an UL message, following the scheme shown in Figure 2.
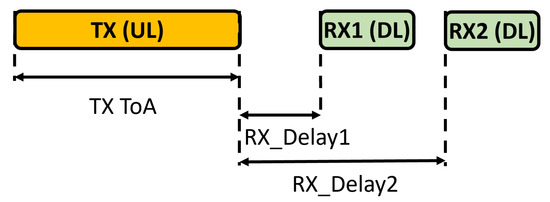
Figure 2.
Receiving window timings for Class A end-devices.
Once an UL transmission is completed, the end-device opens two receiving windows. The first window (RX1 in Figure 2) begins seconds (+/−20 s) after the end of the UL transmission, while the second one (RX2) begins seconds (+/−20 s) after the end of the UL transmission. The minimum duration of a receiving window is equal to the time required by the end-device’s radio transceiver to recognize the preamble of the DL message. When a preamble is detected during a receiving window, the receiver remains active until the DL message is demodulated. If an end-device correctly demodulates a DL message during RX1 and it is the destination of the DL message, RX2 will not start. Note that the NS can send DL messages to specific end-devices at the start of each receiving window. After UL transmission, the end-device can only send a new message after receiving a DL message (in RX1 or RX2) or once RX2 has expired. Class B (Beaconing) end-devices support bidirectional communications with scheduled receiving windows. In fact, in addition to the Class A receiving windows, Class B end-devices open extra receiving windows at scheduled times. To implement this operational mode, the GWs periodically send a beacon to synchronize the end-devices. This way, the NS knows when the end-devices are listening. Class B end-devices realize a trade-off between energy consumption and latency of DL communication.
Class C (Continuously listening) end-devices support bidirectional communications with maximal receiving windows. This class of end-devices provides almost permanently open receiving windows, except for when they are transmitting. Class C end-devices are typically mains powered, as they consume more energy than the Class A and Class B ones, and guarantee the lowest latency to DL communications.
Since all LoRaWAN COTS devices must support Class A features, this paper explores the use of Class A end-devices.
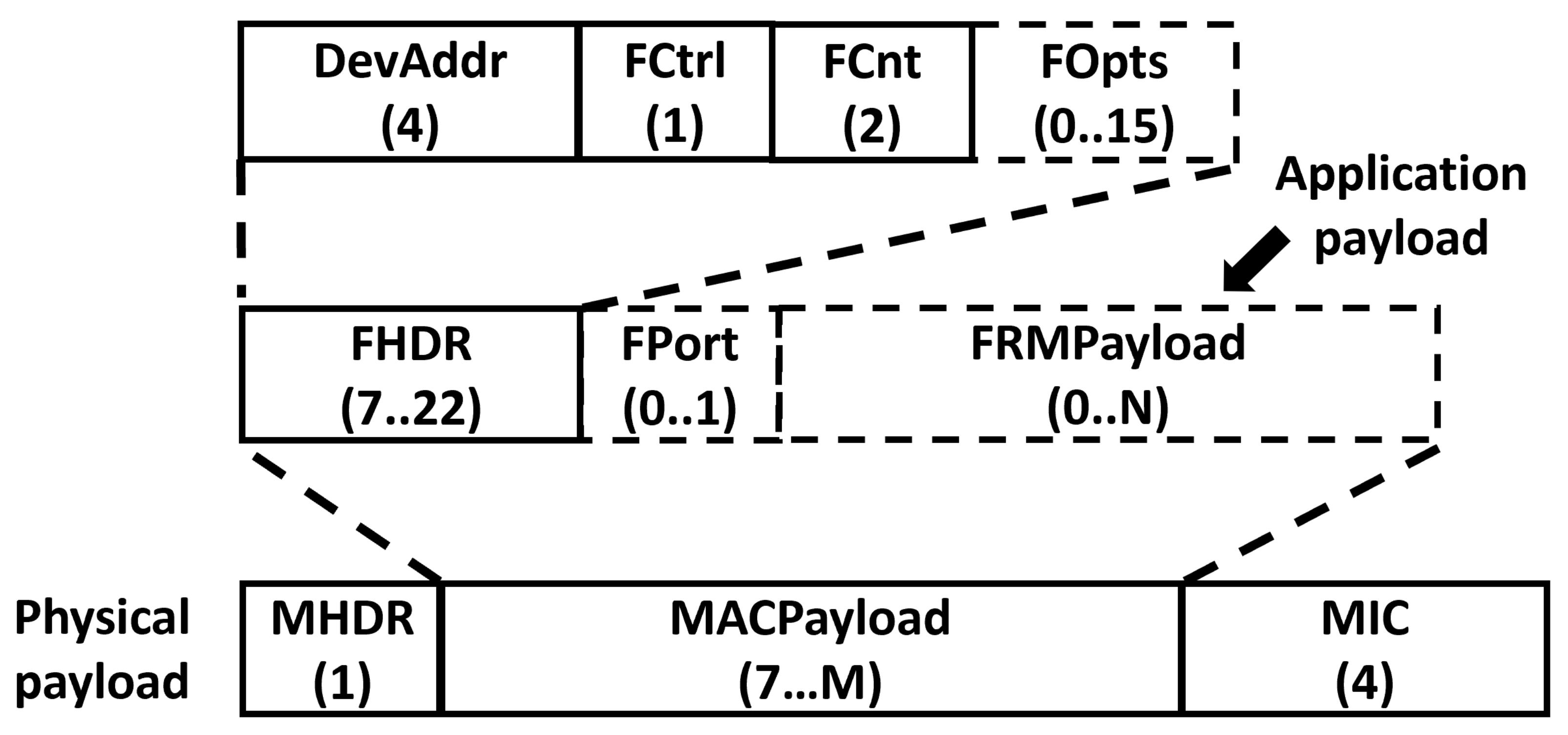
As shown in Figure 3, in a LoRaWAN network, the application payload is encapsulated in the FRMPayload field of a LoRaWAN frame (MACPayload in Figure 3). The MACPayload also contains a frame header (FHDR) and an optional FPort field. In turn, the physical payload consists of a single-octet MAC header (MHDR) followed by the MACPayload and ending with a 4-octet message integrity code (MIC).
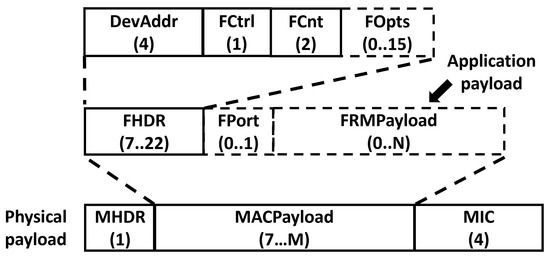
Figure 3.
LoRaWAN message format.
Figure 3 shows below each field the corresponding length in bytes. The maximum lengths of the FRMPayload (N) and MACPayload fields (M) are region-specific [36]. Note that for the LoRaWAN data messages (i.e., the ones with an nonempty FRMPayload field), the FPort field is mandatory. As a result, an overhead of 12 bytes is introduced in each LoRaWAN data message.
4. LoRaWAN Medium Access Control Protocols
The LoRaWAN regional parameters document [36] describes several aspects of LoRaWAN communication, such as the permitted transmission management strategies and some details on the channel frequencies that can be used. The document also suggests to refer to the specific norms of the region in which the LoRaWAN end-devices operate to obtain authoritative information.
For instance, in Europe, operation in the 868 MHz region is regulated by the ETSI norms EN 300 220 [40,41], in the sub-bands specified in the ERC Recommendation 70-03. As far as the channel access strategy is concerned, the ETSI regulations allow the choice of using either a Pure ALOHA MAC protocol with duty-cycle limitation or a polite spectrum access based on LBT AFA. These uncoordinated MAC protocols cannot support real-time traffic, as they do not enforce predictability and do not provide any time or frequency reservation mechanism. Consequently, an end-to-end delay bound cannot be calculated exactly or stochastically [70,71,72,73].
4.1. Pure ALOHA
The Pure ALOHA MAC protocol is a random medium access strategy that allows an end-device to transmit at any time, i.e., whenever it has a message to be transmitted.
Each end-device using Pure ALOHA-based medium access strategies must comply with duty cycle constraints () and maximum transmission power, where is defined as the maximum percent of time per hour that an end-device can transmit in a sub-band. For example, with a equal to 5%, an end-device can transmit 180 s per hour.
Table 1 shows the duty cycle constraints () and maximum transmission power () in the EU863-870MHz ISM band relevant to the sub-bands that match the ERC Recommendation 70-03.

Table 1.
Duty-cycle limitations of the sub-bands of the EU863-870MHz ISM band that match the ERC Recommendation 70-03.
Since the ETSI limitations apply to the sub-bands, in the case that a number of 125 kHz-channels higher than one is available for transmission in a given sub-band, the transmission times on these channels must be jointly considered.
The current LoRaWAN specification exclusively uses transmissions with limited duty cycle to conform to the ETSI regulation [36].
4.2. Polite Spectrum Access
A polite medium access requires that the end-devices listen to the channel to sense if it is busy or not by running a CCA before transmitting. In particular, if the mean signal level detected at the CCA interval () is below the CCA threshold, the end-device will start to send the message; otherwise, applying the AFA technique, the end-device switches to another channel and restarts the CCA before trying to transmit.
If the transmitter detects that all channels are busy, the transmission is delayed for a deferral interval (), i.e., the backoff delay. In this way, message collisions are prevented. Note that an end-device is not allowed to try to access the same channel before a random time interval (longer than a specific value) expires.
Table 2 [40] shows the restrictions that the ETSI regulations impose on the usage of the MAC protocol based on LBT AFA.

Table 2.
Timing parameters of polite medium access based on LBT AFA.
As shown in Table 2, the minimum CCA interval () shall be 160 s. If the target channel is busy, shall be larger than or equal to a specific value, i.e., that corresponds to the CCA length. The minimum time between two consecutive deferral intervals, here called , is declared by the manufacturer. Once the CCA is performed, the end-devices must start the message transmission within a value declared by the manufacturer, which is lower than or equal to 5 ms. A single transmission shall last less than or equal to a , i.e., 1 s. The maximum duration of a sequence of messages, called a transmission dialogue, shall end within . According to the ETSI regulations, this value is equal to 4 s. Moreover, after each message transmission, an end-device shall be silent for a time interval, here called , higher than or equal to 100 ms.
Finally, each end-device is allowed to transmit up to 100 s per hour over a 200 kHz spectrum. As a result, the duty cycle per 200 kHz spectrum () is equal to approximately 2.78%.
5. Network Configuration and Performance Metrics
In this paper, we investigate how to take advantage of using, on the same network, both the MAC protocols available for LoRaWAN when they work in accordance with the ETSI norms. In our model, a group of end-devices uses Pure ALOHA while the other group adopts LBT AFA. To combine the use of the two protocols, we envisaged two possible approaches. The first one does not impose any constraint on how the two protocols are configured, while in the second case, channel separation is adopted.
The first approach, here called the SHC (SHared Channels) scenario, involves a LoRaWAN network in which the end-devices that use Pure ALOHA and those that use LBT AFA work on the same channels. In the second approach, here called the SPC (SPlit Channels) scenario, the channels available for transmissions are split into two different sets. This way, in the same LoRaWAN network, the group of end-devices that use the Pure ALOHA MAC protocol exploits a set of channels, while the other group of end-devices runs LBT AFA on the other set of channels. In particular, for the SPC scenario, we consider two configurations of channels (here called Configuration A and Configuration B) that differ for the number of channels used by the two considered MAC protocols.
In the SHC scenario, all the end-devices operate on the same set of channels, as shown in Table 3.

Table 3.
SHC scenario—channel configuration.
From Table 3 it is possible to obtain the overall duty cycle of each end-device that uses Pure ALOHA or LBT AFA (i.e., 12.1% and about 19.46%, respectively) as the sum of the duty cycle values of each used channel.
Table 4 and Table 5 show the channels used by the end-devices in the configurations A and B of the SPC scenario according to the MAC protocol used.

Table 4.
SPC scenario—Configuration A.

Table 5.
SPC scenario—Configuration B.
In particular, in Configuration A (shown in Table 4), each end-device that adopts Pure ALOHA operates on four channels and can achieve an overall duty cycle of 11%, while each end-device that uses LBT AFA works on three channels and can reach a duty cycle up to about 8.34%.
In Configuration B of the SPC scenario (shown in Table 5), the end-devices that use Pure ALOHA exploit three channels and can achieve an overall duty cycle of 11%, while those that adopt LBT AFA work on four channels and can reach a duty cycle of about 11.12%.
In this work, the above-mentioned scenarios and configurations are evaluated against the performance metrics that are defined in the following subsection.
Performance Metrics
The performance metrics used in this work to assess LoRaWAN are the packet loss ratio (PLR), the packet discard ratio (PDR), the end-to-end delay (e2eDelay), and the energy consumption ratio per transmission ().
The PLR represents the ratio between lost and transmitted messages, measured at the application layer and expressed as a percentage, according to Equation (2):
where , , and are the number of messages transmitted, correctly received, and lost, respectively, measured by each end-device. This parameter is assessed for both protocols under consideration.
The PDR represents the ratio of the number of messages discarded by the MAC layer after performing the maximum number of backoffs to the number of messages received by the MAC layer from the application layer, measured by each end-device and expressed as a percentage, according to Equation (3),
where and are the number of messages received from the application layer and discarded by the MAC layer after performing the maximum number of backoffs, respectively, measured by each end-device. Note that the PDR is meaningful only for the end-devices that use LBT AFA. In fact, for the end-devices that adopt Pure ALOHA, the PDR is always equal to zero, as all the messages are sent without performing any channel assessment or backoff algorithm.
The e2eDelay is the time interval between message generation at the source node () and reception at the destination node (), measured at the application level, calculated as in Equation (4):
In the simulated scenarios, the source node is an end-device, while the destination node is the NS. To evaluate the delay on the LoRa link only, we assume that the delay introduced by the communication between the GW and the NS is equal to 0.
Finally, is defined as the ratio between the average energy consumed per transmission by an end-device that adopts LBT AFA () and the one consumed by an end-device that uses Pure ALOHA (), expressed as a percentage, according to Equation (5),
The following section describes how the simulation was performed and discusses the results obtained in the aforementioned scenarios, using different configurations and under different workload conditions.
6. Performance Evaluation
Here, an assessment of a LoRaWAN network is presented in which end-devices that use Pure ALOHA and other ones that adopt LBT AFA operate in the same area. Evaluation is performed through simulations using the OMNeT++ simulation environment [74,75]. In particular, we use the Framework for LoRa (FLoRa) [76], which in turn adopts components of the Internet Networking (INET) framework [77] to simulate the main features of the LoRaWAN class A end-devices, the LoRa physical layer, and the wireless channel. We developed the LBT AFA medium access scheme from scratch.
The imperfect orthogonality of the LoRa SFs is implemented as suggested in [67]. Moreover, a duty cycle check function is performed by the end-devices before each message transmission to ensure that the ETSI limitations are met.
The assessment is performed in a scenario that refers to a realistic industrial use case and is similar to the one adopted in [78]. The simulated network includes 200 end-devices (e.g., sensors) distributed over a sensing area of 1000 m × 1000 m, an NS, and a GW. As discussed in Section 5, a group of end-devices uses Pure ALOHA while the other set of end-devices adopts LBT AFA.
The NS and the GW are positioned in the middle of the sensing area. Some end-devices are stationary, and the others are mobile. The stationary end-devices are distributed in the sensing area so that the number of end-devices that use the same SF is always the same for all SFs. The mobile end-devices traverse the sensing area with an average speed of 0.3 m/s following the ChiangMobility model as in [38,47,79].
In the simulations, the LoRa Path Loss Oulu model [76] provided by FLoRa and the parameters experimentally found in a suburban environment in the work [80] are adopted.
The application layers of the end-devices are not synchronized with each other. Consequently, multiple end-devices can generate messages or attempt to transmit at the same time and message collisions may occur, especially in the Pure ALOHA MAC protocol case.
Each end-device that uses the LBT AFA MAC protocol reacts to an unsuccessful transmission attempt, i.e., to the case in which a channel is sensed as busy, with the adoption of the AFA technique. As a result, the end-device switches to another channel and restarts the CCA before trying to send. If all the channels available for transmission are busy, the message transmission is delayed, i.e., the end-device waits for a backoff delay before retrying transmission. In particular, the end-devices use an exponential backoff algorithm, and the maximum number of backoffs before dropping a message, here called , is set to 5. In the simulated scenarios, for every transmission attempt, the end-devices that use LBT AFA perform a CCA of 160 s, i.e., the minimum CCA interval according to [40] (see Table 2).
We consider end-devices that generate and transmit messages with an application payload of 20 bytes, as in [78]. No retransmission mechanism is adopted.
For each scenario and channel configuration, we simulate three different message generation patterns, i.e., Case L, Case M and Case H, which correspond to low, medium, and high traffic loads, respectively. In particular, stationary and mobile end-devices generate messages following an exponential distribution (ED) that defines the time interval between the generation of two consecutive messages. The message generation patterns in the three cases are shown in Table 6.

Table 6.
Message generation patterns.
To better assess the performance of the two MAC protocols, we reduce the DL communications by using unconfirmed messages and disabling the ADR mechanism in all the end-devices. This way, there are no message losses due to the GW switching from receiving to transmitting states to transmit acknowledgments or ADR commands. Furthermore, as discussed in Section 3, the ADR mechanism should be disabled on the mobile end-devices, as generally it is not able to efficiently handle the LoRa runtime configuration. In this case, each end-device must individually manage its LoRa parameters. For this reason, we implement a custom algorithm that runs on each end-device instead of the ADR algorithm. The custom algorithm works as follows. During the configuration phase, a test application runs on a mobile end-device. This end-device moves in the sensing area and calculates the parameters that guarantee a message delivery ratio higher than a configurable threshold (e.g., 96% in our simulations) at multiple points, which correspond to multiple distances from the GW. For example, in the simulations we evaluated distances from the GW in steps of 10 m (a configurable value in the simulator). Based on the findings of the algorithm described above, the network designer configures the mobile end-devices to switch their LoRa configuration according to the distance from the GW.
The simulation time is 43,200 s, i.e., 12 h, to gather a significant amount of data. Moreover, each simulation is repeated ten times, varying the seed for random number generation to obtain statistically significant results.
Table 7 shows the simulation parameters.

Table 7.
Simulation parameters.
In the following, we show and discuss the results of the evaluated scenarios.
In particular, Section 6.1 presents the evaluation of a LoRaWAN network with 100 end-devices that use Pure ALOHA and 100 end-devices that adopt LBT AFA. Among the end-devices, 50% are stationary, while the other 50% are mobile. In the assessment in Section 6.1, we consider both the scenarios discussed above (i.e., SHC and SPC) and the channel configurations (A and B) under different traffic loads.
The SHC scenario is the most challenging one, because the end-devices that use Pure ALOHA and those that use LBT AFA compete for the same channels. Furthermore, differently from the SPC scenario, the SHC one does not require to split in two different sets the channels that can be used by each of the two protocols, thus allowing the end-devices to use all the available channels. For this reason, both Section 6.2 and Section 6.3 focus on the performance of the two protocols in the SHC scenario. In particular, Section 6.2 evaluates a LoRaWAN network with an equal number of stationary and mobile end-devices with varying percentages of end-devices that use Pure ALOHA and LBT AFA, respectively. Section 6.3 instead evaluates a LoRaWAN network with an equal number of end-devices that use ALOHA and LBT AFA with varying percentages of stationary and mobile end-devices, respectively. Finally, Section 6.4 summarizes the results obtained.
6.1. Assessment in Different Scenarios and Channel Configurations
Table 8 shows the average PLR of both stationary and mobile end-devices in all scenarios and configurations evaluated.

Table 8.
Average PLR under different traffic conditions.
As expected, the PLR values increase with the traffic load, and the highest PLR values are experienced in Case H.
Furthermore, the results in Table 8 show that in the simulated scenarios, the PLR values obtained by LBT AFA are better than those achieved by Pure ALOHA. In particular, the difference increases with the workload. In fact, when the channels are sensed as busy multiple times, LBT AFA reduces the PLR by leveraging the AFA technique and also the exponential backoff algorithm if all the available channels are sensed as busy, before retrying to transmit.
In the SPC scenario, the end-devices that use LBT AFA perform better in Configuration B than in Configuration A, because in Configuration B they use four channels, instead of three. The PLR values obtained in the SPC scenarios are lower than those relevant to the SHC scenario, in which the end-devices that use LBT AFA work on seven channels, because the SHC scenario does not split the set of available channels. Consequently, the end-devices that adopt the LBT AFA have to compete for the channel access also with the end-devices that use Pure ALOHA.
Table 8 shows that no significant differences were found in PLR values between stationary and mobile end-devices. The slightly lower average PLR of the mobile nodes is because most of them transit over an area covered by low SFs. As a result, their transmissions require a low ToA; therefore, their message collision probability is also low because it is less likely that other end-devices will be using the same channel during the transmission of the messages.
Table 9 shows the average PDR measured by the end-devices that use LBT AFA.

Table 9.
Average PDR under different traffic conditions (LBT AFA only).
The results in Table 9 show that in the evaluated scenarios, the end-devices that adopt the LBT AFA MAC protocol discard some messages after performing the maximum number of backoffs. In particular, the PDR increases under a high workload, as in this case, the channels are often sensed as busy, and therefore, both the AFA technique and the backoff algorithm are used multiple times. In some cases, a message transmission attempt reaches the maximum number of backoffs without succeeding, and the message is discarded. The PDR values can be reduced by increasing the parameter at the expense of increasing the energy consumption.
Finally, the stationary and mobile end-devices obtain similar PDR values.
The average and maximum e2eDelays of the stationary and mobile end-devices obtained in all the scenarios and configurations evaluated are shown in Table 10.

Table 10.
Average and maximum e2eDelay under different traffic conditions.
As shown in Table 10, the Pure ALOHA MAC protocol significantly outperforms LBT AFA in terms of average and maximum e2eDelay. This is because the end-devices that use Pure ALOHA can transmit at any time if they have messages to send. In fact, Pure ALOHA end-devices do not perform any channel assessment before transmitting and do not adopt a backoff algorithm, and therefore, they do not delay their message transmission.
As it was expected, the highest maximum e2eDelay values are experienced in Case H, i.e., when the end-devices generate the highest number of messages. In fact, in this case, for both the MAC protocols under consideration, multiple messages can be enqueued in the MAC layer queue, and therefore, the e2eDelay also includes the time spent by the message in the MAC layer queue waiting for being transmitted. Moreover, in Case H, the probability that the channels are found to be busy with LBT AFA is higher than in the other cases. As a result, sometimes, the end-devices reach the maximum allowed number of backoffs before a successful transmission, and therefore, they experience the highest maximum e2eDelay values.
Finally, Table 11 shows the energy-consumption ratio per transmission in all the scenarios assessed.

Table 11.
Average under different traffic conditions.
As expected, the energy consumption of the end-devices that use LBT AFA is higher than that of the end-devices that use Pure ALOHA, as LBT AFA involves one or more CCAs before transmission. Furthermore, the highest values are obtained in Case H, i.e., under the highest workload. In fact, in this case, the end-devices that adopt LBT AFA run a higher number of CCAs due to multiple (unsuccessful) transmission attempts on busy channels.
As shown in Table 11, the values obtained in the SHC scenario are higher than those obtained in the two configurations of the SPC scenario. This is because in the SHC scenario, LBT AFA can use all the available channels, and therefore, a higher number of CCAs can be run before performing a backoff. However, the end-devices that use Pure ALOHA and those that use LBT AFA compete for the same channels. Consequently, the channels are sensed as busy multiple times, and therefore, the higher number of CCAs implies a higher energy consumption.
6.2. Impact of the Percentage of End-Devices That Use Pure ALOHA and LBT AFA
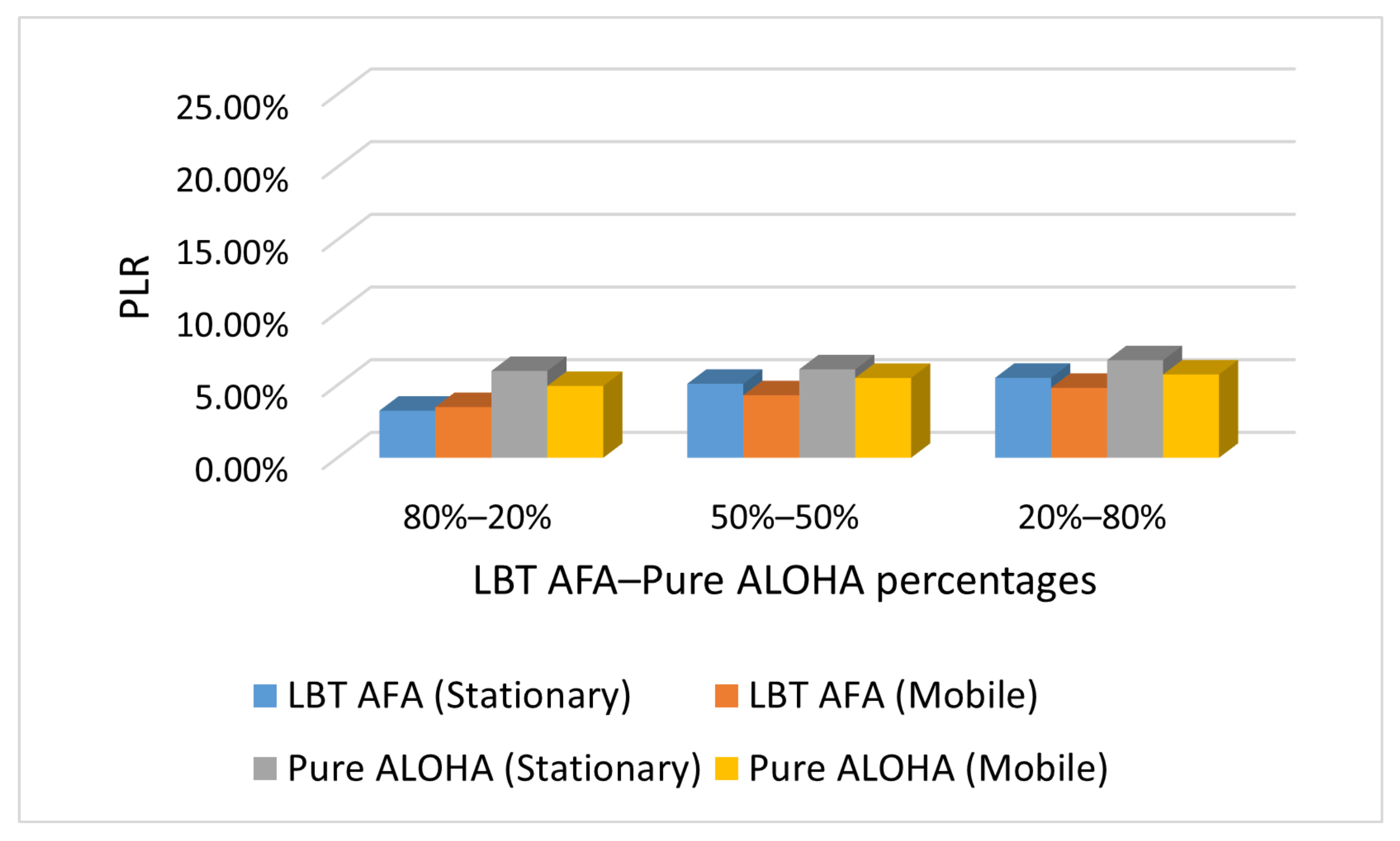
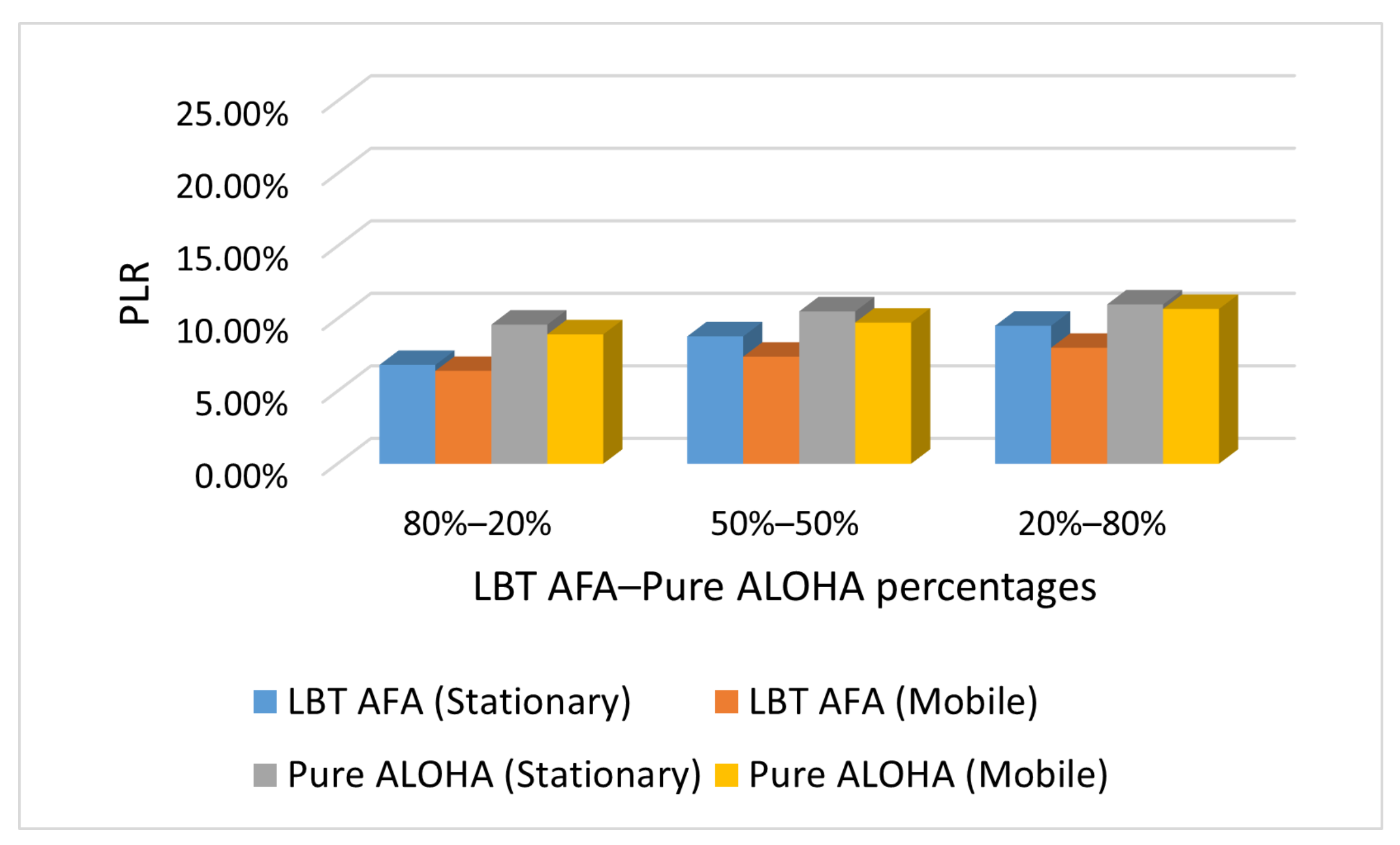
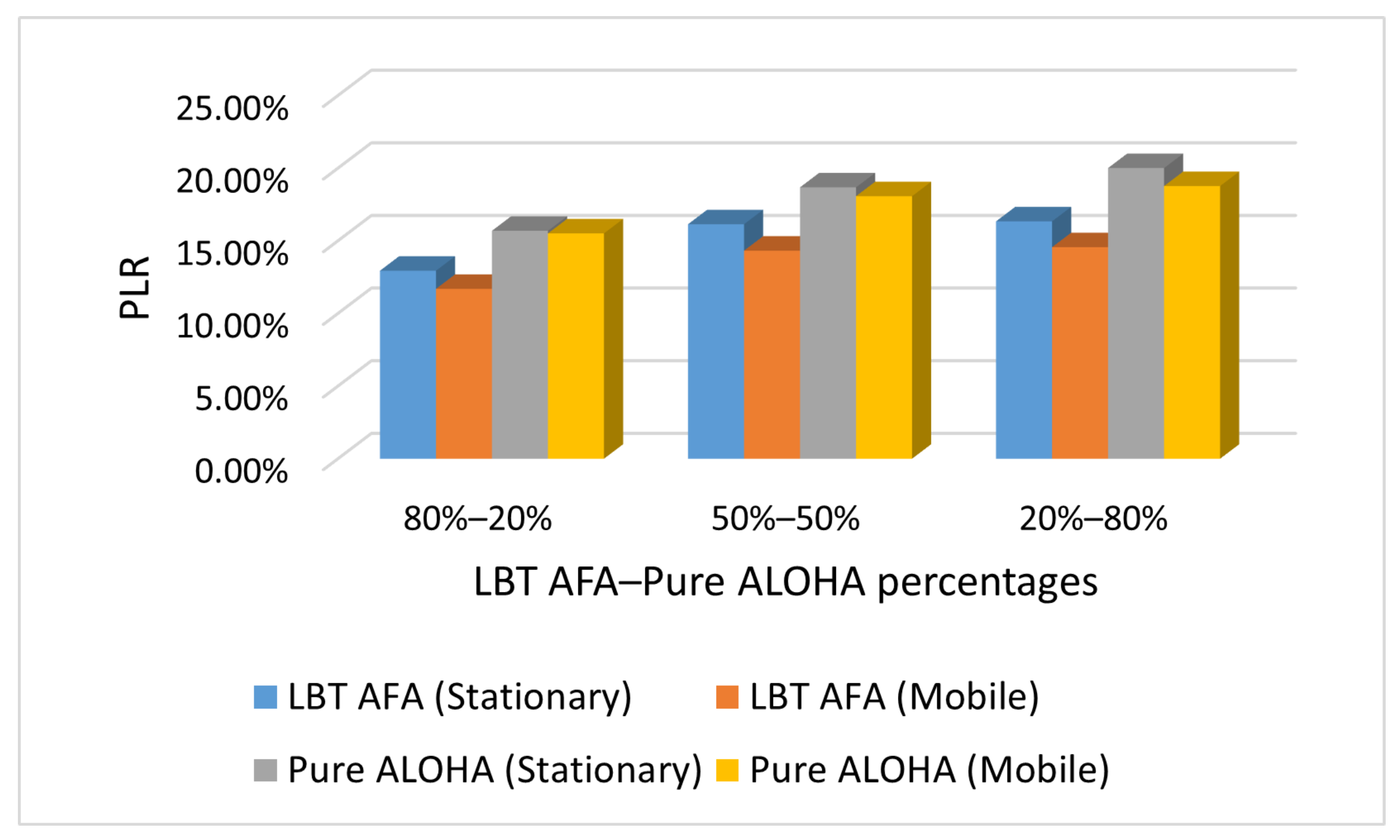
Figure 4, Figure 5 and Figure 6 show the impact on PLR of the percentage of end-devices that use Pure ALOHA and LBT AFA in the SHC scenario under different traffic conditions (i.e., Case L, M and H). In this evaluation, the number of stationary and mobile end-devices is the same (i.e., 100).
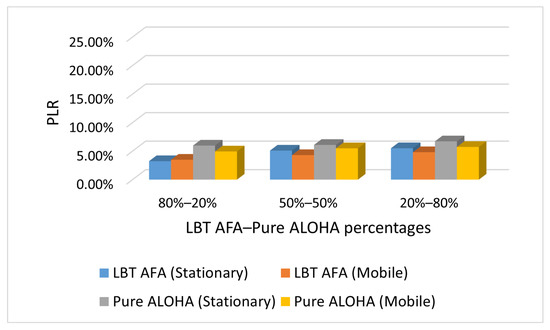
Figure 4.
Case L: PLR with varying percentages of end-devices that use Pure ALOHA and LBT AFA.
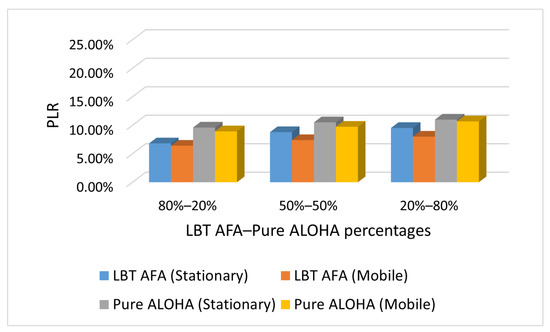
Figure 5.
Case M: PLR with varying percentages of end-devices that use Pure ALOHA and LBT AFA.
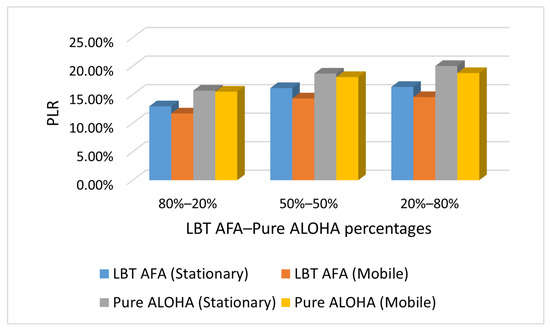
Figure 6.
Case H: PLR with varying percentages of end-devices that use Pure ALOHA and LBT AFA.
From Figure 4, Figure 5 and Figure 6, it can be seen that in all cases, the PLR increases with the number of end-devices that use Pure ALOHA. This is because with Pure ALOHA, a high number of collisions occurs, as end-devices transmit without performing any CCA. The graphs in Figure 4, Figure 5 and Figure 6 show similar trends. As the PLR values increase with traffic load, the maximum values are obtained in case H.
Table 12 shows the average e2eDelays of stationary and mobile end-devices obtained in the SHC scenario with varying percentages of end-devices that use Pure ALOHA and LBT AFA under different traffic conditions (i.e., Case L, M and H).

Table 12.
Average e2eDelay with varying percentages of end-devices that use Pure ALOHA and LBT AFA.
The results show that there are no significant differences in terms of average e2eDelay with varying percentages of end-devices that use Pure ALOHA and LBT AFA. In all the cases, Pure ALOHA outperforms LBT AFA because Pure ALOHA end-devices do not delay their transmissions applying a backoff algorithm, but transmit right away whenever they have messages to send.
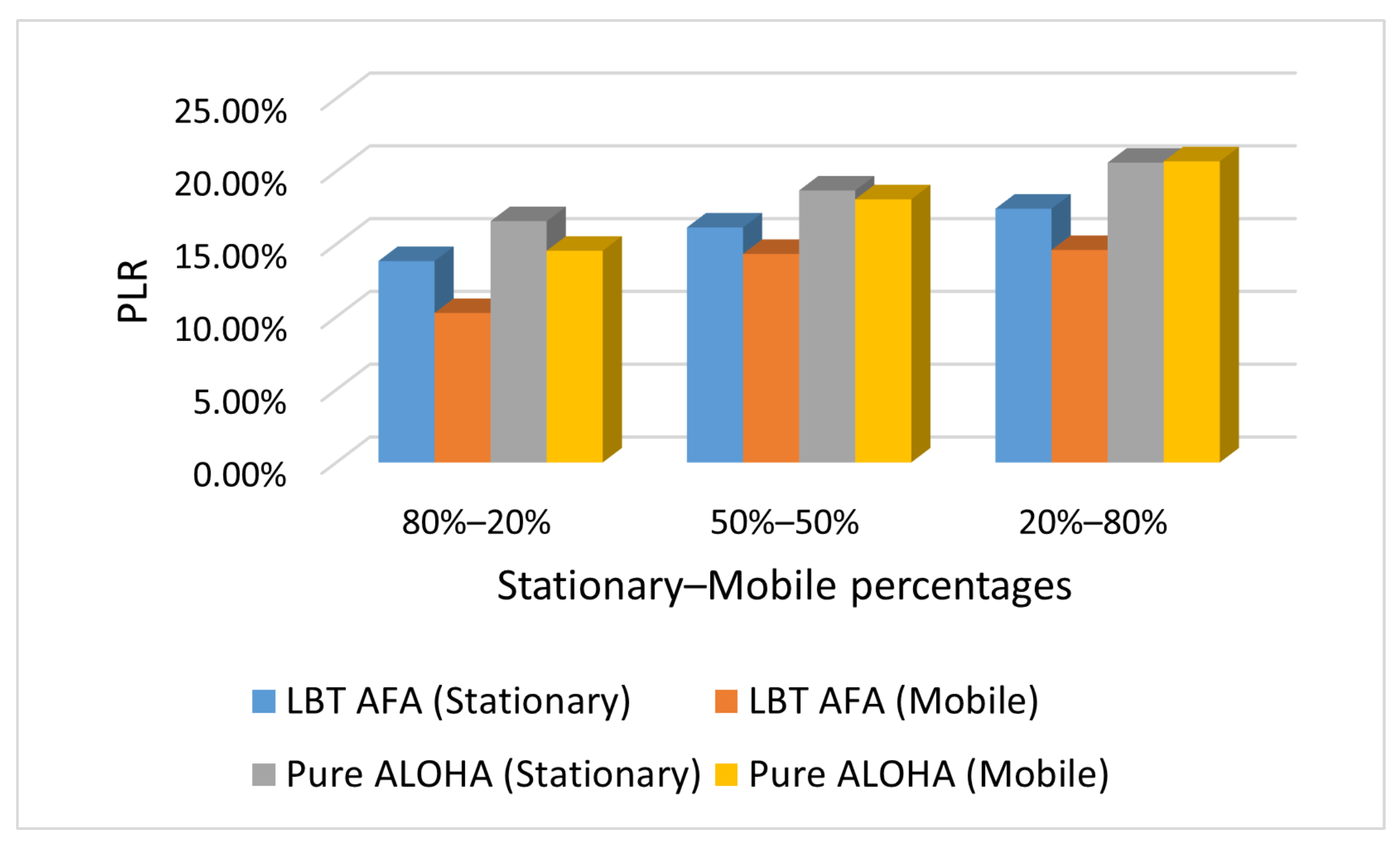
6.3. Impact of the Percentages of Stationary and Mobile End-Devices
This subsection presents the results obtained in the SHC scenario with varying percentages of stationary and mobile end-devices, respectively. In this evaluation, the number of end-devices that use Pure ALOHA and LBT AFA is the same (i.e., 100).
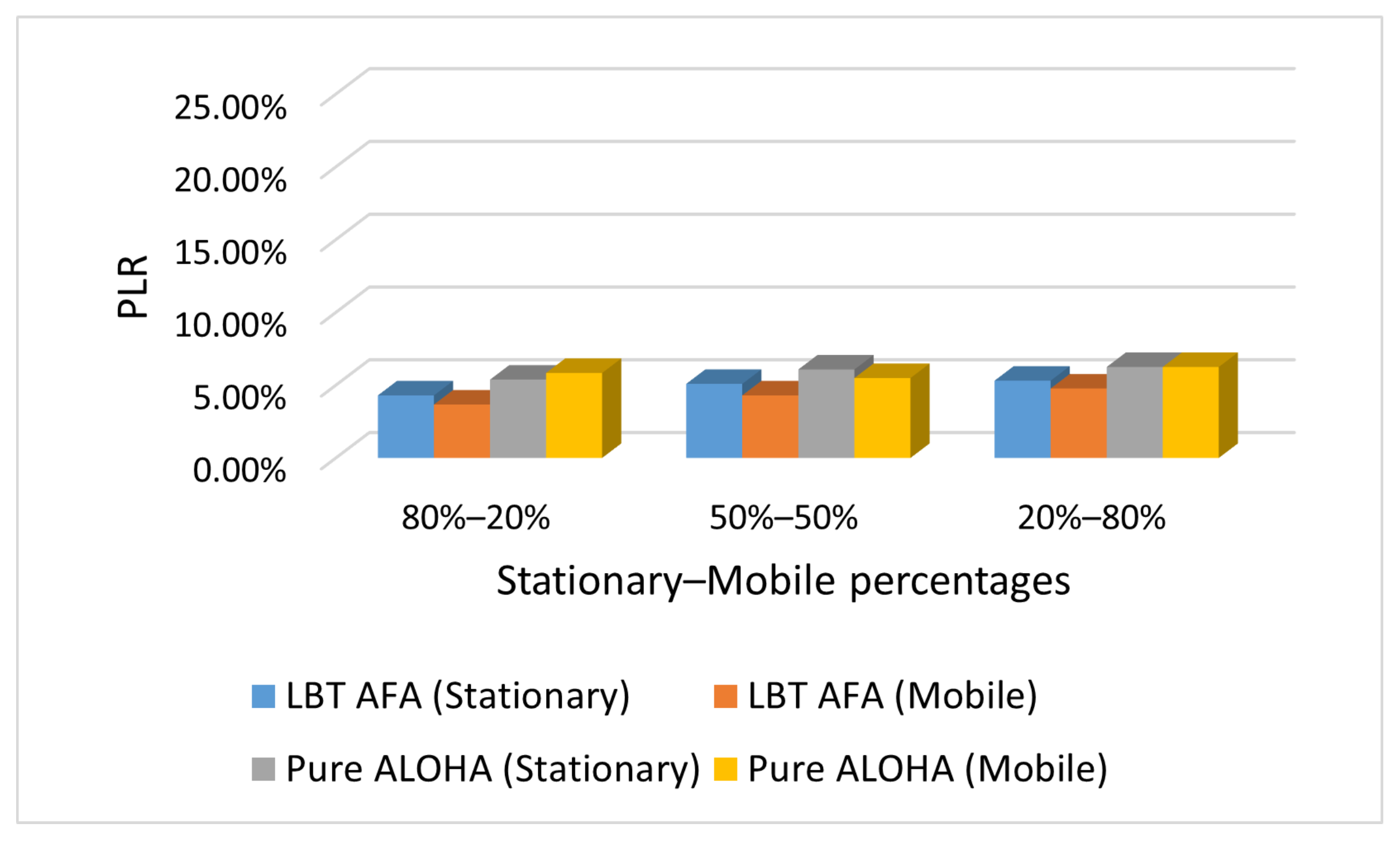
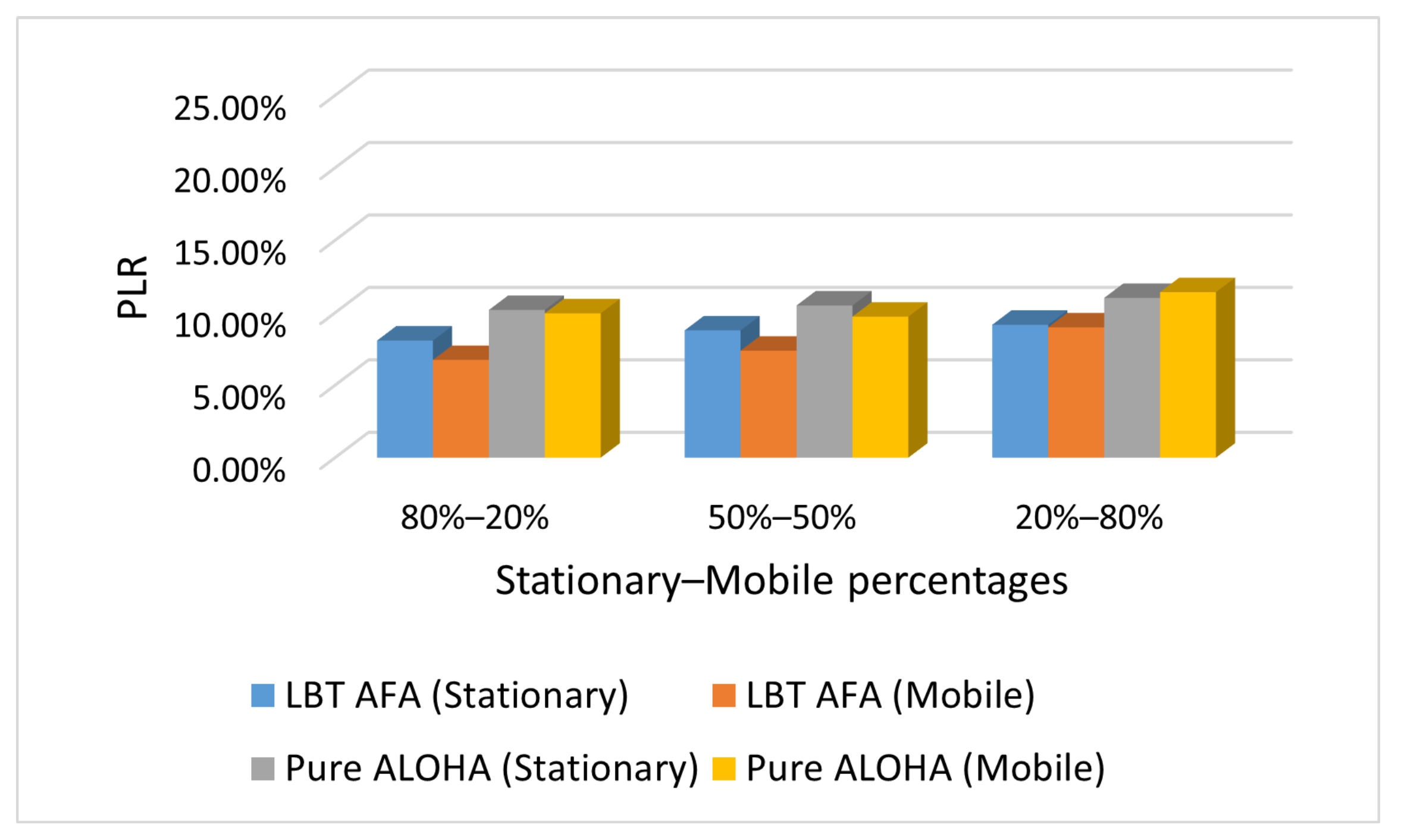
Figure 7, Figure 8 and Figure 9 show the PLR under different traffic conditions (i.e., Case L, M and H).
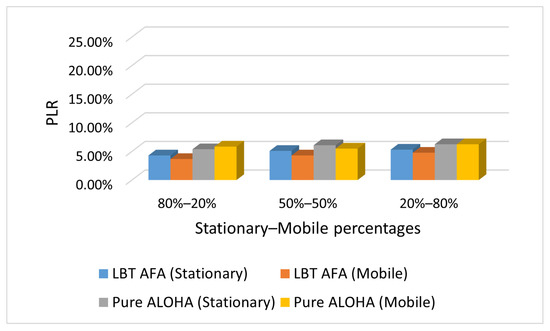
Figure 7.
Case L: PLR with varying percentages of stationary and mobile end-devices.
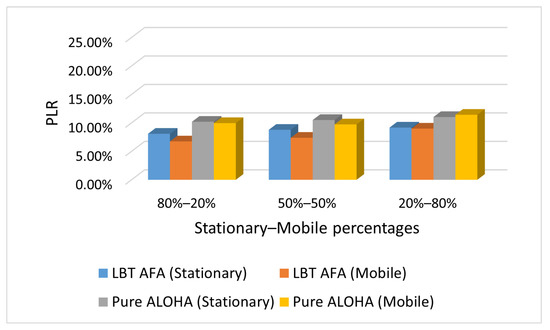
Figure 8.
Case M: PLR with varying percentages of stationary and mobile end-devices.
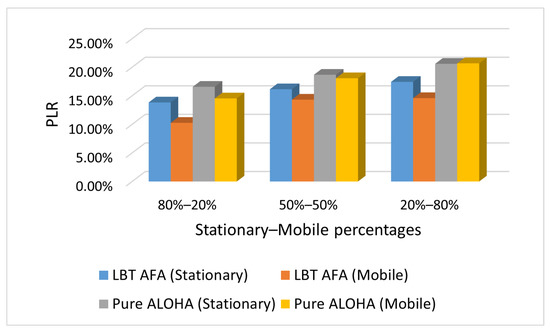
Figure 9.
Case H: PLR with varying percentages of stationary and mobile end-devices.
As expected, the PLR values increase with the percentage of mobile end-devices because in our scenario, they send messages more frequently than stationary ones. Consequently, a higher number of mobile end-devices generates a higher network traffic, and this increases the PLR.
Table 13 presents the average e2eDelay values obtained with varying percentages of stationary and mobile end-devices under different traffic conditions.

Table 13.
Average e2eDelay with varying percentages of stationary and mobile end-devices.
As can be seen, in this scenario, the percentage of stationary and mobile end-devices does not have a significant impact on the average e2eDelay.
6.4. Discussion
The simulation results show that the PLR values obtained by LBT AFA are lower than those of Pure ALOHA. In particular, the difference increases with the traffic load. The reason for this result is that with Pure ALOHA, the end-devices transmit without performing any CCA; therefore, they may incur a high number of collisions. On the contrary, LBT AFA runs CCA before starting a transmission and uses AFA (and may resort to backoff) whenever the channel is found to be busy. Consequently, with LBT AFA, the packet loss decreases, but the CCA increases the energy consumption. Pure ALOHA outperforms LBT AFA in terms of average e2eDelay, as the end-devices that use Pure ALOHA do not adopt a backoff algorithm; therefore, they do not delay their transmissions.
The PLR increases with the number of end-devices that use Pure ALOHA because the end-devices transmit right away whenever they have messages to send (without running CCA). Our results show that the PLR increases with the percentage of mobile end-devices because in our scenario, they generate a higher network traffic than stationary ones. Furthermore, in our scenarios, neither the percentage of stationary and mobile end-devices nor the percentage of end-devices using Pure ALOHA and LBT AFA significantly impact the average e2eDelay.
When the messages to be transmitted are of equal importance, LBT AFA can be a good option, as it reduces collisions. However, in some scenarios, e.g., in the industrial communications, different end-devices typically transmit traffic flows with different criticality levels (e.g., alarms, and best-effort traffic). In these cases, the choice of the MAC protocol to be used by each end-device can help to meet the requirements of the relevant traffic flow. For example, the end-devices that can generate high-priority messages that have to be delivered as soon as possible (e.g., alarms) should prefer Pure ALOHA.
7. Conclusions
This paper proposed a simulative performance assessment in different scenarios and configurations of a LoRaWAN network that combines the use of the two MAC protocols supported by LoRaWAN, Pure ALOHA and LBT AFA, working in compliance with the ETSI regulations.
Summarizing, the results obtained show that in the assessed scenarios, LBT AFA obtains lower PLR values than Pure ALOHA. In particular, the benefits offered by LBT AFA become more evident as the workload increases.
However, end-devices that adopt LBT AFA experience a PDR that increases with the traffic load. This value represents the number of messages that are discarded because the maximum number of backoffs is reached. To reduce the number of messages discarded, it is possible to increase the parameter. In this way, the probability of a message being sent increases, as a higher number of transmission attempts will be run before discarding it. However, on average, as each end-device will run a higher number of CCAs, the energy consumption will also increase.
As the results show, in the scenarios assessed, Pure ALOHA consumes slightly less energy per transmission than LBT AFA because it does not perform any CCA. Furthermore, pure ALOHA experiences lower e2eDelays than LBT AFA because message transmissions are not delayed.
Based on the findings of this assessment, the network designer can determine which MAC protocol to use on each end-device depending on the desired performance target (i.e., PLR, PDR, e2eDelay, or energy consumption).
In particular, to achieve low PLR values, the LBT AFA MAC protocol is the preferred choice and setting a high value can be an option to obtain low PDR values. On the contrary, if the primary target is to reduce the maximum message e2eDelay, the network designer can adopt Pure ALOHA, which is also able to offer low PLR under low and medium workloads.
Future work will deal with a priority-based traffic classification algorithm that runs on the LoRaWAN end-devices and allows the network designer to choose, for each traffic flow, the MAC protocol that best matches the flow requirements. Furthermore, we will also explore the use of the SDN paradigm to dynamically select LoRa parameters in mobile end-devices.
Author Contributions
Conceptualization, L.L.; methodology, L.L., L.L.B. and G.P.; investigation, L.L., L.L.B., G.P., A.P. and M.P.; software, L.L., A.P. and M.P., writing—original draft preparation, L.L., L.L.B. and G.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research was partially funded by the Project “Soluzioni innovative per la connettività wired e wireless nell’industria 4.0 a supporto dell’efficienza e resilienza della fabbrica”, within the action IV.4—“Dottorati e contratti di ricerca su tematiche dell’innovazione del nuovo Asse IV del PON Ricerca e Innovazione 2014-2020 Istruzione e ricerca per il recupero—REACT-EU”.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data underlying this article will be shared on reasonable request from the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
Abbreviations
The following abbreviations are used in this manuscript:
| ADR | Adaptive Data Rate |
| AFA | Adaptive Frequency Agility |
| BW | Bandwidth |
| CF | Carrier Frequency |
| CCA | Clear Channel Assessment |
| COTS | Commercial-off-the-shelf |
| CR | Coding Rate |
| CRC | Cyclic Redundancy Check |
| CSS | Chirp Spread Spectrum |
| DC | Duty cycle |
| DL | Downlink |
| e2eDelay | End-to-end delay |
| Energy consumption ratio per transmission | |
| ED | Exponential distribution |
| ETSI | European Telecommunications Standards Institute |
| FLoRa | Framework for LoRa |
| GW | Gateway |
| INET | Internet Networking |
| LBT | Listen Before Talk |
| LoRa | Long Range |
| LoRaWAN | Long Range Wide Area Network |
| LPWAN | Low Power Wide Area Network |
| MAC | Medium Access Control |
| MDPI | Multidisciplinary Digital Publishing Institute |
| NS | Network server |
| OMNeT++ | Objective Modular Network Testbed in C++ |
| PDR | Packet Discard Ratio |
| PLR | Packet Loss Ratio |
| SDN | Software-Defined Networking |
| SF | Spreading Factor |
| SIR | Signal-to-interference ratio |
| TDMA | Time Division Multiple Access |
| ToA | Time on Air |
| TP | Transmission Power |
| UL | Uplink |
References
- Asghari, P.; Rahmani, A.M.; Javadi, H.H.S. Internet of Things applications: A systematic review. Comput. Netw. 2019, 148, 241–261. [Google Scholar] [CrossRef]
- Battaglia, F.; Iannizzotto, G.; Lo Bello, L. A person authentication system based on RFID tags and a cascade of face recognition algorithms. IEEE Trans. Circuits Syst. Video Technol. 2017, 27, 1676–1690. [Google Scholar] [CrossRef]
- Sepasgozar, S.; Karimi, R.; Farahzadi, L.; Moezzi, F.; Shirowzhan, S.; Ebrahimzadeh, S.M.; Hui, F.; Aye, L. A Systematic Content Review of Artificial Intelligence and the Internet of Things Applications in Smart Home. Appl. Sci. 2020, 10, 3074. [Google Scholar] [CrossRef]
- Patti, G.; Leonardi, L.; Lo Bello, L. A Novel MAC Protocol for Low Datarate Cooperative Mobile Robot Teams. Electronics 2020, 9, 235. [Google Scholar] [CrossRef]
- Razmjoo, A.; Gandomi, A.; Mahlooji, M.; Astiaso Garcia, D.; Mirjalili, S.; Rezvani, A.; Ahmadzadeh, S.; Memon, S. An Investigation of the Policies and Crucial Sectors of Smart Cities Based on IoT Application. Appl. Sci. 2022, 12, 2672. [Google Scholar] [CrossRef]
- Kim, K.; Li, S.; Heydariaan, M.; Smaoui, N.; Gnawali, O.; Suh, W.; Suh, M.J.; Kim, J.I. Feasibility of LoRa for Smart Home Indoor Localization. Appl. Sci. 2021, 11, 415. [Google Scholar] [CrossRef]
- Iannizzotto, G.; Lo Bello, L.; Nucita, A.; Grasso, G.M. A Vision and Speech Enabled, Customizable, Virtual Assistant for Smart Environments. In Proceedings of the 2018 11th International Conference on Human System Interaction (HSI), Gdansk, Poland, 4–6 July 2018; pp. 50–56. [Google Scholar] [CrossRef]
- Syed, A.S.; Sierra-Sosa, D.; Kumar, A.; Elmaghraby, A. IoT in smart cities: A survey of technologies, practices and challenges. Smart Cities 2021, 4, 429–475. [Google Scholar] [CrossRef]
- Miao, H.Y.; Yang, C.T.; Kristiani, E.; Fathoni, H.; Lin, Y.S.; Chen, C.Y. On Construction of a Campus Outdoor Air and Water Quality Monitoring System Using LoRaWAN. Appl. Sci. 2022, 12, 5018. [Google Scholar] [CrossRef]
- Leonardi, L.; Patti, G.; Battaglia, F.; Lo Bello, L. Simulative assessments of the IEEE 802.15.4 CSMA/CA with Priority Channel Access in Structural Health Monitoring scenarios. In Proceedings of the IEEE 15th International Conference on Industrial Informatics (INDIN), Emden, Germany, 24–26 July 2017. [Google Scholar] [CrossRef]
- Ullo, S.L.; Sinha, G.R. Advances in smart environment monitoring systems using IoT and sensors. Sensors 2020, 20, 3113. [Google Scholar] [CrossRef]
- Iannizzotto, G.; Lo Bello, L.; Patti, G. Personal Protection Equipment detection system for embedded devices based on DNN and Fuzzy Logic. Expert Syst. Appl. 2021, 184, 115447. [Google Scholar] [CrossRef]
- Kim, B.; Kim, S.; Lee, M.; Chang, H.; Park, E.; Han, T. Application of an Internet of Medical Things (IoMT) to Communications in a Hospital Environment. Appl. Sci. 2022, 12, 12042. [Google Scholar] [CrossRef]
- Leonardi, L.; Lo Bello, L.; Patti, G.; Ragusa, O. A Network Architecture and Routing Protocol for the MEDIcal WARNing System. J. Sens. Actuator Netw. 2021, 10, 44. [Google Scholar] [CrossRef]
- Soldatos, J.; Gusmeroli, S.; Malo, P.; Di Orio, G. Internet of things applications in future manufacturing. In Digitising the Industry Internet of Things Connecting the Physical, Digital and VirtualWorlds; River Publishers: Aalborg, Denmark, 2022; pp. 153–183. [Google Scholar]
- Carpenzano, A.; Caponetto, R.; Lo Bello, L.; Mirabella, O. Fuzzy traffic smoothing: An approach for real-time communication over Ethernet networks. In Proceedings of the 4th IEEE International Workshop on Factory Communication Systems (WFCS 2002), Vasteras, Sweden, 28–30 August 2002; pp. 241–248. [Google Scholar] [CrossRef]
- Fedullo, T.; Morato, A.; Peserico, G.; Trevisan, L.; Tramarin, F.; Vitturi, S.; Rovati, L. An IoT Measurement System Based on LoRaWAN for Additive Manufacturing. Sensors 2022, 22, 5466. [Google Scholar] [CrossRef] [PubMed]
- Toscano, E.; Lo Bello, L. Cross-channel interference in IEEE 802.15. 4 networks. In Proceedings of the 2008 IEEE International Workshop on Factory Communication Systems (WFCS 2008), Dresden, Germany, 21–23 May 2008; pp. 139–148. [Google Scholar] [CrossRef]
- Ferrero, R.; Collotta, M.; Bueno-Delgado, M.V.; Chen, H.C. Smart management energy systems in industry 4.0. Energies 2020, 13, 382. [Google Scholar] [CrossRef]
- Iannizzotto, G.; La Rosa, F.; Lo Bello, L. A wireless sensor network for distributed autonomous traffic monitoring. In Proceedings of the 3rd International Conference on Human System Interaction, Rzeszow, Poland, 13–15 May 2010; pp. 612–619. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zeadally, S.; Azad, M.A.K. Emerging wireless technologies for Internet of Things applications: Opportunities and challenges. Encycl. Wirel. Netw. 2020, 390–400. [Google Scholar] [CrossRef]
- Abdulkawi, W.M.; Nizam-Uddin, N.; Sheta, A.F.A.; Elshafiey, I.; Al-Shaalan, A.M. Towards an Efficient Chipless RFID System for Modern Applications in IoT Networks. Appl. Sci. 2021, 11, 8948. [Google Scholar] [CrossRef]
- Iannizzotto, G.; Milici, M.; Nucita, A.; Lo Bello, L. A Perspective on Passive Human Sensing with Bluetooth. Sensors 2022, 22, 3523. [Google Scholar] [CrossRef]
- Jeon, K.E.; She, J.; Soonsawad, P.; Ng, P.C. BLE Beacons for Internet of Things Applications: Survey, Challenges, and Opportunities. IEEE Internet Things J. 2018, 5, 811–828. [Google Scholar] [CrossRef]
- Ogbodo, E.U.; Abu-Mahfouz, A.M.; Kurien, A.M. A Survey on 5G and LPWAN-IoT for improved smart cities and remote area applications: From the aspect of architecture and security. Sensors 2022, 22, 6313. [Google Scholar] [CrossRef]
- Battaglia, F.; Collotta, M.; Leonardi, L.; Lo Bello, L.; Patti, G. Novel Extensions to Enhance Scalability and Reliability of the IEEE 802.15. 4-DSME Protocol. Electronics 2020, 9, 126. [Google Scholar] [CrossRef]
- Patti, G.; Lo Bello, L. A priority-aware multichannel adaptive framework for the IEEE 802.15. 4e-LLDN. IEEE Trans. Ind. Electron. 2016, 63, 6360–6370. [Google Scholar] [CrossRef]
- Tian, L.; Santi, S.; Seferagić, A.; Lan, J.; Famaey, J. Wi-Fi HaLow for the Internet of Things: An up-to-date survey on IEEE 802.11ah research. J. Netw. Comput. Appl. 2021, 182, 103036. [Google Scholar] [CrossRef]
- Battaglia, F.; Collotta, M.; Leonardi, L.; Lo Bello, L.; Patti, G. A scalable approach for periodic traffic scheduling in IEEE 802.15. 4-DSME networks. In Proceedings of the IEEE 17th International Conference on Industrial Informatics (INDIN 2019), Helsinki-Espoo, Finland, 22–25 July 2019; Volume 1, pp. 1747–1750. [Google Scholar] [CrossRef]
- Patti, G.; Alderisi, G.; Lo Bello, L. Introducing multi-level communication in the IEEE 802.15. 4e protocol: The MultiChannel-LLDN. In Proceedings of the 2014 IEEE Emerging Technology and Factory Automation (ETFA 2014), Barcelona, Spain, 16–19 September 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Bembe, M.; Abu-Mahfouz, A.; Masonta, M.; Ngqondi, T. A survey on low-power wide area networks for IoT applications. Telecommun. Syst. 2019, 71, 249–274. [Google Scholar] [CrossRef]
- LoRa Alliance Technical Committee. LoRaWAN™ 1.0.4 Specification; LoRa Alliance: Fremont, CA, USA, 2020. [Google Scholar]
- Semtech Corporation Wireless Sensing and Timing Products Division. LoRa™ Modulation Basics; Semtech: Camarillo, CA, USA, 2015. [Google Scholar]
- Luvisotto, M.; Tramarin, F.; Vangelista, L.; Vitturi, S. On the use of LoRaWAN for indoor industrial IoT applications. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef]
- Toscano, E.; Lo Bello, L. A topology management protocol with bounded delay for Wireless Sensor Networks. In Proceedings of the 2008 IEEE International Conference on Emerging Technologies and Factory Automation, Hamburg, Germany, 15–18 September 2008; pp. 942–951. [Google Scholar] [CrossRef]
- LoRa Alliance Technical Committee Regional Parameters Workgroup. RP002-1.0.0 LoRaWAN Regional Parameters; LoRa Alliance: Fremont, CA, USA, 2019. [Google Scholar]
- Zucchetto, D.; Zanella, A. Uncoordinated access schemes for the IoT: Approaches, regulations, and performance. IEEE Commun. Mag. 2017, 55, 48–54. [Google Scholar] [CrossRef]
- Leonardi, L.; Lo Bello, L.; Battaglia, F.; Patti, G. Comparative Assessment of the LoRaWAN Medium Access Control Protocols for IoT: Does Listen before Talk Perform Better than ALOHA? Electronics 2020, 9, 553. [Google Scholar] [CrossRef]
- Ortín, J.; Cesana, M.; Redondi, A. How do ALOHA and Listen Before Talk Coexist in LoRaWAN? In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; pp. 1–7. [Google Scholar] [CrossRef]
- ETSI. Short Range Devices (SRD) Operating in the Frequency Range 25 MHz to 1000 MHz; Part 1: Technical Characteristics and Methods of Measurement; ETSI: Sophia Antipolis, France, 2017. [Google Scholar]
- ETSI. Short Range Devices (SRD) Operating in the Frequency Range 25 MHz to 1000 MHz; Part 2: Harmonised Standard for Access to Radio Spectrum for Non Specific Radio Equipment; ETSI: Sophia Antipolis, France, 2018. [Google Scholar]
- Leonardi, L.; Lo Bello, L.; Patti, G. LoRa support for long-range real-time inter-cluster communications over Bluetooth Low Energy industrial networks. Comput. Commun. 2022, 192, 57–65. [Google Scholar] [CrossRef]
- Sisinni, E.; Mahmood, A. Wireless Communications for Industrial Internet of Things: The LPWAN Solutions. In Wireless Networks and Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2021; pp. 79–103. [Google Scholar]
- Peruzzi, G.; Pozzebon, A. Combining LoRaWAN and NB-IoT for Edge-to-Cloud Low Power Connectivity Leveraging on Fog Computing. Appl. Sci. 2022, 12, 1497. [Google Scholar] [CrossRef]
- Dias, J.; Grilo, A. LoRaWAN multi-hop uplink extension. Procedia Comput. Sci. 2018, 130, 424–431. [Google Scholar] [CrossRef]
- Álamos, J.; Kietzmann, P.; Schmidt, T.C.; Wählisch, M. DSME-LoRa: Seamless Long Range Communication Between Arbitrary Nodes in the Constrained IoT. ACM Trans. Sens. Netw. (TOSN) 2022, 18, 1–43. [Google Scholar] [CrossRef]
- Leonardi, L.; Lo Bello, L.; Patti, G. MRT-LoRa: A multi-hop real-time communication protocol for industrial IoT applications over LoRa networks. Comput. Commun. 2022, 199, 72–86. [Google Scholar] [CrossRef]
- Farooq, M.O. Multi-hop communication protocol for LoRa with software-defined networking extension. Internet Things 2021, 14, 100379. [Google Scholar] [CrossRef]
- Lalle, Y.; Fourati, M.; Fourati, L.C.; Barraca, J.P. Routing Strategies for LoRaWAN Multi-Hop Networks: A Survey and an SDN-Based Solution for Smart Water Grid. IEEE Access 2021, 9, 168624–168647. [Google Scholar] [CrossRef]
- Leonardi, L.; Lo Bello, L.; Aglianò, S. Priority-based bandwidth management in virtualized software-defined networks. Electronics 2020, 9, 1009. [Google Scholar] [CrossRef]
- Muthanna, M.S.A.; Wang, P.; Wei, M.; Ateya, A.A.; Muthanna, A. Toward an ultra-low latency and energy efficient LoRaWAN. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems; Springer: Berlin/Heidelberg, Germany, 2019; pp. 233–242. [Google Scholar]
- Leonardi, L.; Ashjaei, M.; Fotouhi, H.; Lo Bello, L. A proposal towards software-defined management of heterogeneous virtualized industrial networks. In Proceedings of the 2019 IEEE 17th International Conference on Industrial Informatics (INDIN), Helsinki-Espoo, Finland, 22–25 July 2019; Volume 1, pp. 1741–1746. [Google Scholar] [CrossRef]
- Hussain, M.; Shah, N.; Amin, R.; Alshamrani, S.S.; Alotaibi, A.; Raza, S.M. Software-defined networking: Categories, analysis, and future directions. Sensors 2022, 22, 5551. [Google Scholar] [CrossRef]
- Leonardi, L.; Battaglia, F.; Lo Bello, L. RT-LoRa: A Medium Access Strategy to Support Real-Time Flows Over LoRa-Based Networks for Industrial IoT Applications. IEEE Internet Things J. 2019, 6, 10812–10823. [Google Scholar] [CrossRef]
- Rizzi, M.; Ferrari, P.; Flammini, A.; Sisinni, E.; Gidlund, M. Using LoRa for industrial wireless networks. In Proceedings of the IEEE 13th International Workshop on Factory Communication Systems (WFCS), Trondheim, Norway, 31 May–2 June 2017; pp. 1–4. [Google Scholar]
- Leonardi, L.; Battaglia, F.; Patti, G.; Lo Bello, L. Industrial LoRa: A Novel Medium Access Strategy for LoRa in Industry 4.0 Applications. In Proceedings of the 44nd Annual Conference of IEEE Industrial Electronics Society (IECON 2018), Washington, DC, USA, 21–23 October 2018. [Google Scholar] [CrossRef]
- Polonelli, T.; Brunelli, D.; Marzocchi, A.; Benini, L. Slotted aloha on lorawan-design, analysis, and deployment. Sensors 2019, 19, 838. [Google Scholar] [CrossRef]
- Polonelli, T.; Brunelli, D.; Benini, L. Slotted aloha overlay on lorawan-a distributed synchronization approach. In Proceedings of the 2018 IEEE 16th international conference on embedded and ubiquitous computing (EUC), Bucharest, Romania, 29–31 October 2018; pp. 129–132. [Google Scholar]
- Beltramelli, L.; Mahmood, A.; Österberg, P.; Gidlund, M. LoRa beyond ALOHA: An investigation of alternative random access protocols. IEEE Trans. Ind. Inform. 2020, 17, 3544–3554. [Google Scholar] [CrossRef]
- Gamage, A.; Liando, J.C.; Gu, C.; Tan, R.; Li, M. Lmac: Efficient carrier-sense multiple access for çoRa. In Proceedings of the 26th Annual International Conference on Mobile Computing and Networking, London, UK, 21–25 September 2020; pp. 1–13. [Google Scholar]
- Loh, F.; Mehling, N.; Hoßfeld, T. Towards LoRaWAN without Data Loss: Studying the Performance of Different Channel Access Approaches. Sensors 2022, 22, 691. [Google Scholar] [CrossRef]
- Ortín, J.; Cesana, M.; Redondi, A. Augmenting LoRaWAN Performance With Listen Before Talk. IEEE Trans. Wirel. Commun. 2019, 18, 3113–3128. [Google Scholar] [CrossRef]
- Bor, M.; Roedig, U. LoRa Transmission Parameter Selection. In Proceedings of the 2017 13th International Conference on Distributed Computing in Sensor Systems (DCOSS), Ottawa, ON, Canada, 5–7 June 2017; pp. 27–34. [Google Scholar] [CrossRef]
- Mikhaylov, K.; Petaejaejaervi, J.; Haenninen, T. Analysis of capacity and scalability of the LoRa low power wide area network technology. In Proceedings of the European Wireless; 22th European Wireless Conference, Oulu, Finland, 18–20 May 2016; pp. 1–6. [Google Scholar]
- Bor, M.C.; Roedig, U.; Voigt, T.; Alonso, J.M. Do LoRa low-power wide-area networks scale? In Proceedings of the 19th ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Malta, 13–17 November 2016; pp. 59–67. [Google Scholar]
- Augustin, A.; Yi, J.; Clausen, T.; Townsley, W.M. A Study of LoRa: Long Range & Low Power Networks for the Internet of Things. Sensors 2016, 16, 1466. [Google Scholar] [CrossRef] [PubMed]
- Croce, D.; Gucciardo, M.; Mangione, S.; Santaromita, G.; Tinnirello, I. Impact of LoRa imperfect orthogonality: Analysis of link-level performance. IEEE Commun. Lett. 2018, 22, 796–799. [Google Scholar] [CrossRef]
- Benkhelifa, F.; Bouazizi, Y.; McCann, J.A. How Orthogonal is LoRa Modulation? IEEE Internet Things J. 2022, 9, 19928–19944. [Google Scholar] [CrossRef]
- Semtech Corporation. LoRaWAN—Simple Rate Adaptation Recommended Algorithm; Semtech: Camarillo, CA, USA, 2016. [Google Scholar]
- Kaczynski, G.A.; Lo Bello, L.; Nolte, T. Deriving exact stochastic response times of periodic tasks in hybrid priority-driven soft real-time systems. In Proceedings of the 2007 IEEE Conference on Emerging Technologies and Factory Automation (EFTA 2007), Patras, Greece, 25–28 September 2007; pp. 101–110. [Google Scholar] [CrossRef]
- Fontanelli, D.; Greco, L.; Palopoli, L. Optimal resource allocation for stochastic systems performance optimisation of control tasks undergoing stochastic execution times. Int. J. Control. 2022, 95, 461–472. [Google Scholar] [CrossRef]
- Lo Bello, L.; Ashjaei, M.; Patti, G.; Behnam, M. Schedulability analysis of Time-Sensitive Networks with scheduled traffic and preemption support. J. Parallel Distrib. Comput. 2020, 144, 153–171. [Google Scholar] [CrossRef]
- Diaz, J.; Lopez, J.; Garcia, M.; Campos, A.; Kim, K.; Lo Bello, L. Pessimism in the stochastic analysis of real-time systems: Concept and applications. In Proceedings of the 25th IEEE International Real-Time Systems Symposium (RTSS 2004), Lisbon, Portugal, 5–8 December 2004; pp. 197–207. [Google Scholar] [CrossRef]
- OMNeT++ Discrete Event Simulator. Available online: http://www.omnetpp.org (accessed on 4 January 2023).
- Varga, A. A practical introduction to the OMNeT++ simulation framework. In Recent Advances in Network Simulation; Springer: Berlin/Heidelberg, Germany, 2019; pp. 3–51. [Google Scholar]
- Slabicki, M.; Premsankar, G.; Di Francesco, M. Adaptive configuration of LoRa networks for dense IoT deployments. In Proceedings of the IEEE/IFIP Network Operations and Management Symposium (NOMS), Taipei, Taiwan, 23–27 April 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Mészáros, L.; Varga, A.; Kirsche, M. INET Framework. In Recent Advances in Network Simulation; Springer: Berlin/Heidelberg, Germany, 2019; pp. 55–106. [Google Scholar]
- Haxhibeqiri, J.; Karaagac, A.; Van den Abeele, F.; Joseph, W.; Moerman, I.; Hoebeke, J. LoRa indoor coverage and performance in an industrial environment: Case study. In Proceedings of the 2017 22nd IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Limassol, Cyprus, 12–15 September 2017; pp. 1–8. [Google Scholar]
- Vieira, L.F.M.; Cunha, A.V.d.S. Performance of greedy forwarding in geographic routing for the internet of drones. Internet Technol. Lett. 2018, 1, e47. [Google Scholar] [CrossRef]
- Petajajarvi, J.; Mikhaylov, K.; Roivainen, A.; Hanninen, T.; Pettissalo, M. On the coverage of LPWANs: Range evaluation and channel attenuation model for LoRa technology. In Proceedings of the 2015 14th International Conference on ITS Telecommunications (ITST), Copenhagen, Denmark, 2–4 December 2015; pp. 55–59. [Google Scholar]
- Camp, T.; Boleng, J.; Davies, V. A survey of mobility models for ad hoc network research. Wirel. Commun. Mob. Comput. 2002, 2, 483–502. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).