Security Authentication Mechanism of Spatio-Temporal Big Data Based on Blockchain
Abstract
1. Introduction
2. Related Technologies
2.1. Spatio-Temporal Big Data Technology
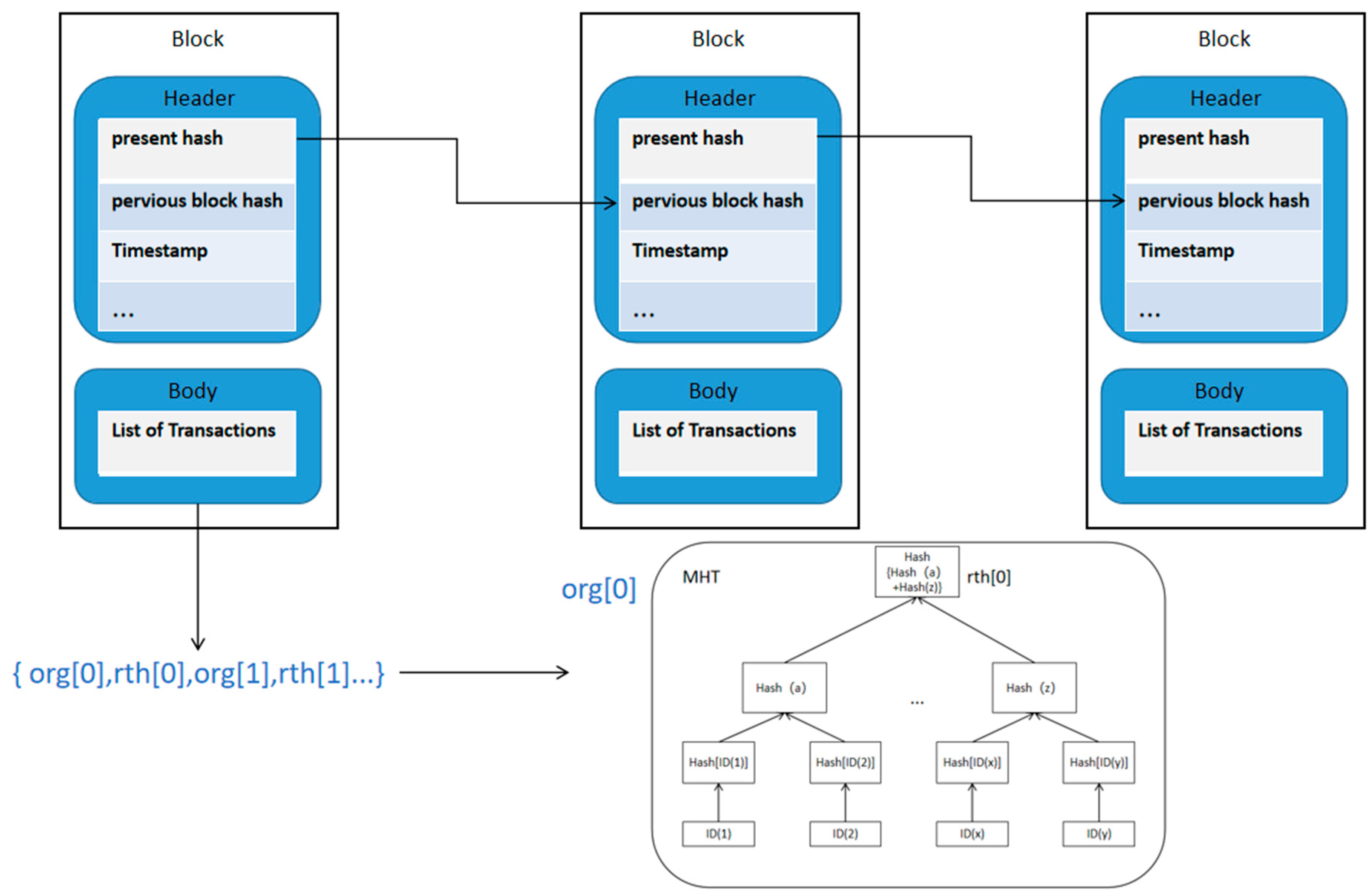
2.2. Blockchain Technology
2.3. Physical Unclonable Technology
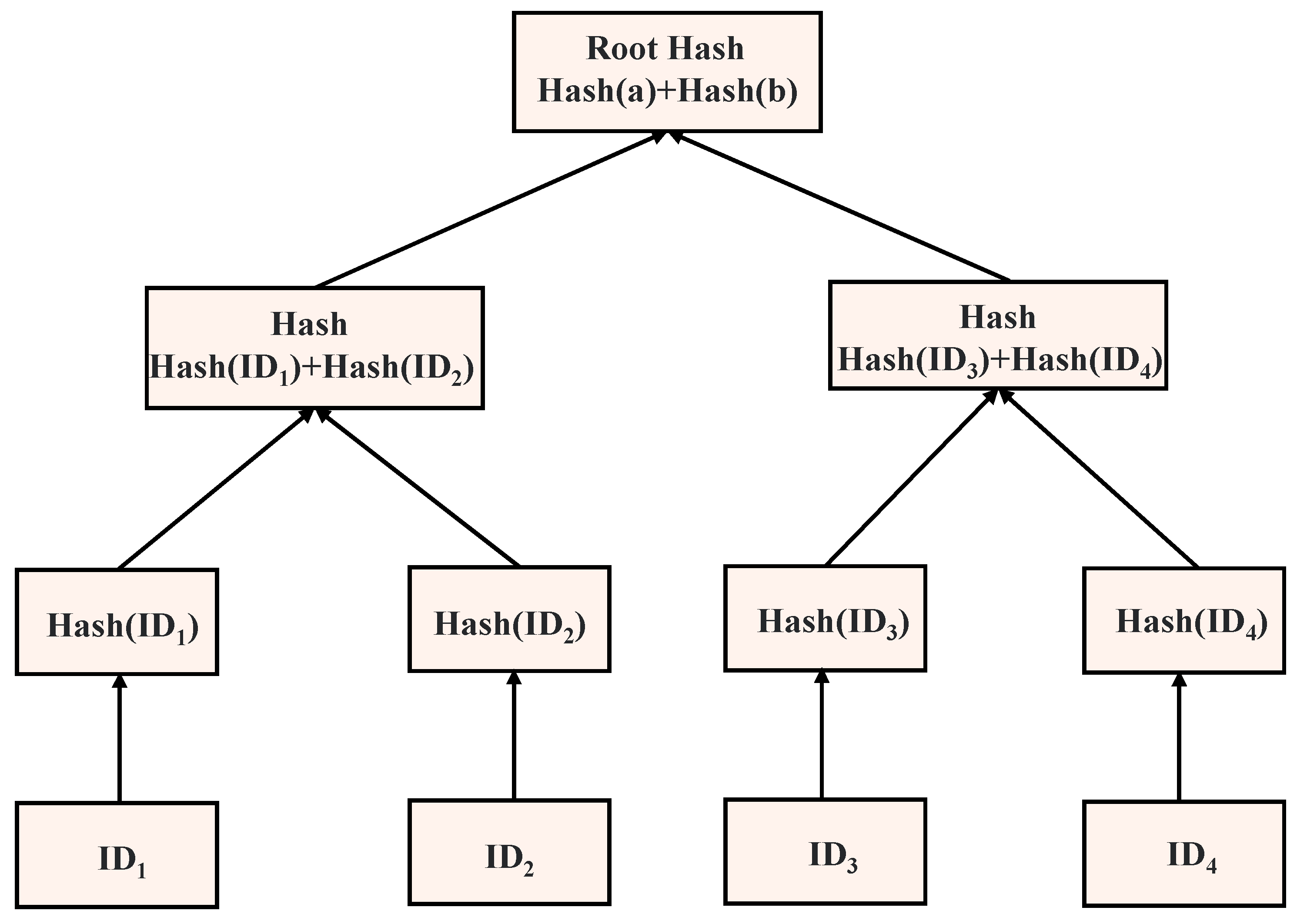
2.4. Merkel Hash Tree
3. Theoretical Analysis of Blockchain Identity Authentication
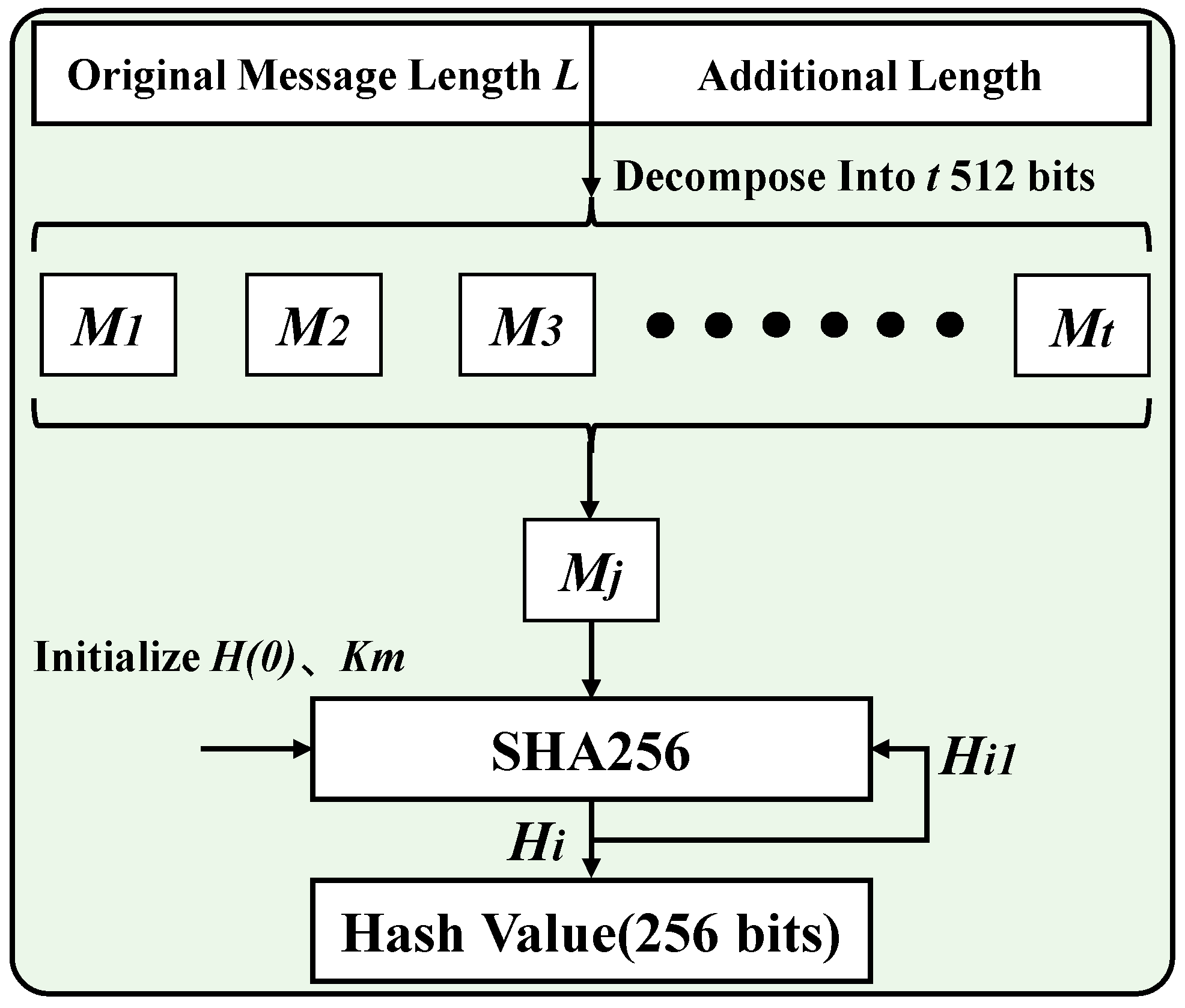
3.1. Principle of SHA256 Algorithm
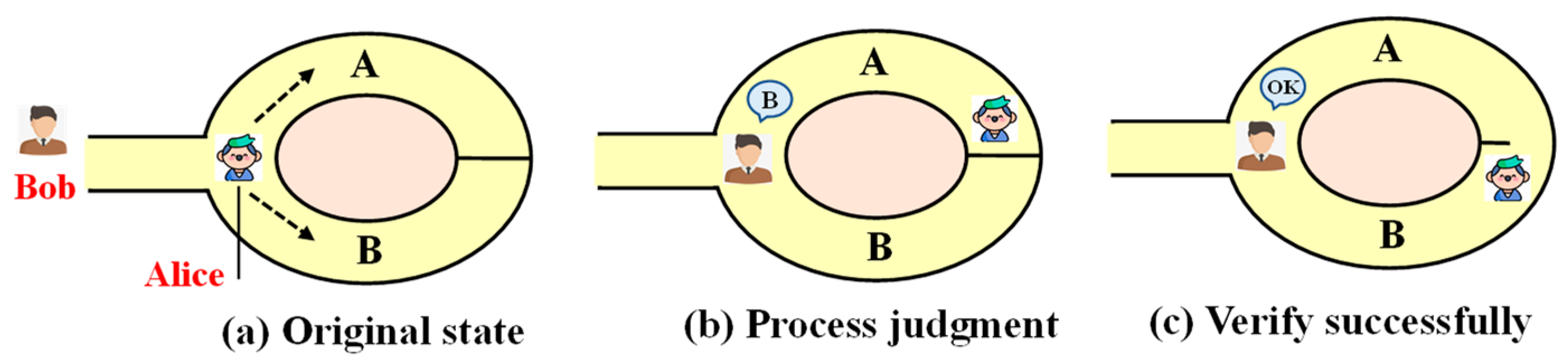
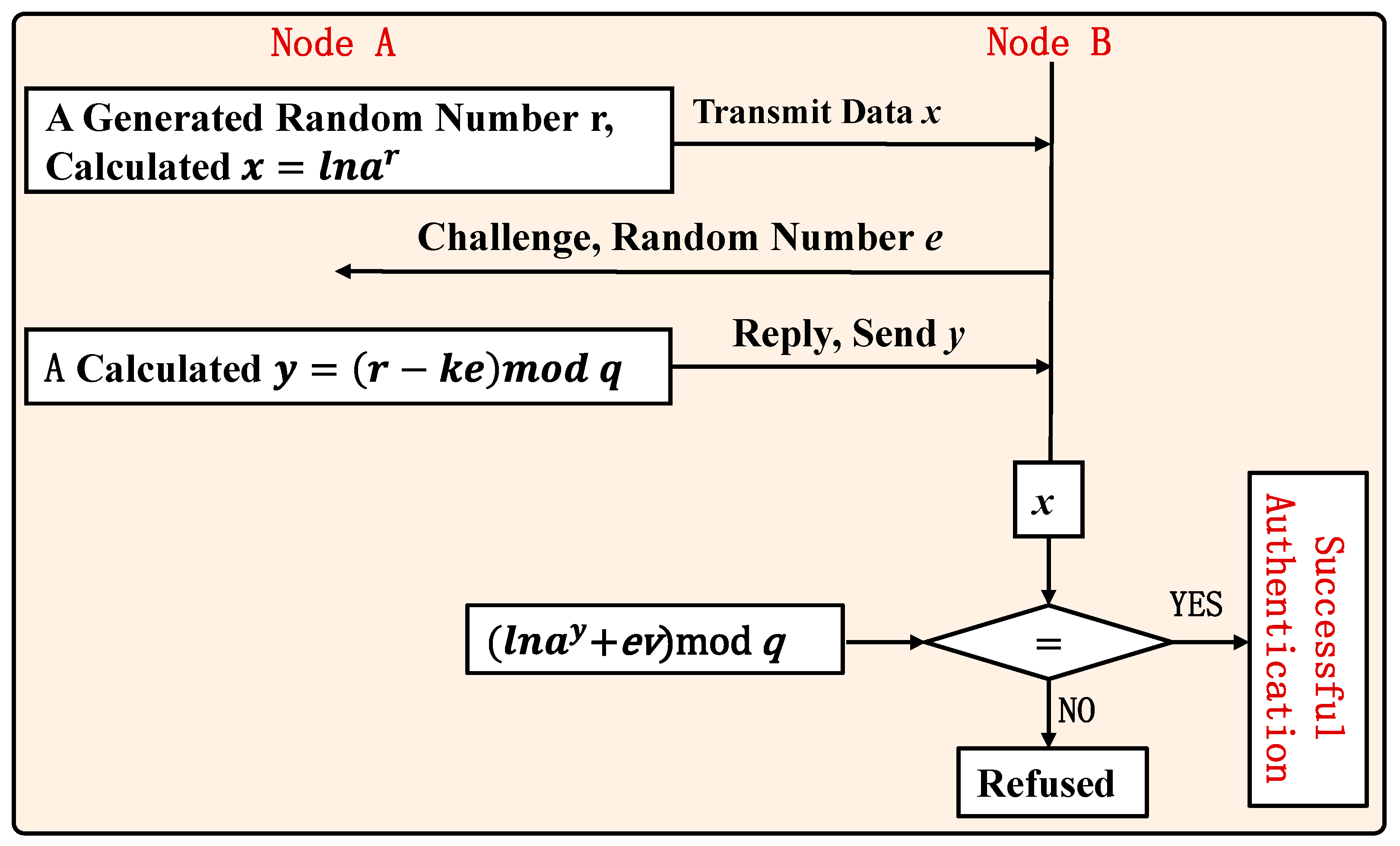
3.2. Identity Authentication Based on Zero-Knowledge Proof
- Step 1:
- Node A requests to join the network, sends its own identity FA, uploads the node to generate a public key v = lna^k mod p (including the private key k = hash (F_A ||K)), and makes v public.
- Step 2:
- Node A selects a random number r smaller than q, calculates it x = lna^r mod p, and makes x public. This process can be completed before both parties authenticate, saving authentication overhead.
- Step 3:
- Suppose node B receives x and initiates a challenge to node A, and sends a random number e smaller than q to node A.
- Step 4:
- Node A calculates y = (r − ke) mod q and sends y to node B.
- Step 5:
- Node B verifies x = lna^y + evmod p and whether it is established. If it is established, the authentication of node A is successful; otherwise, the access of node A is rejected, and an authentication failure message is sent to the client.
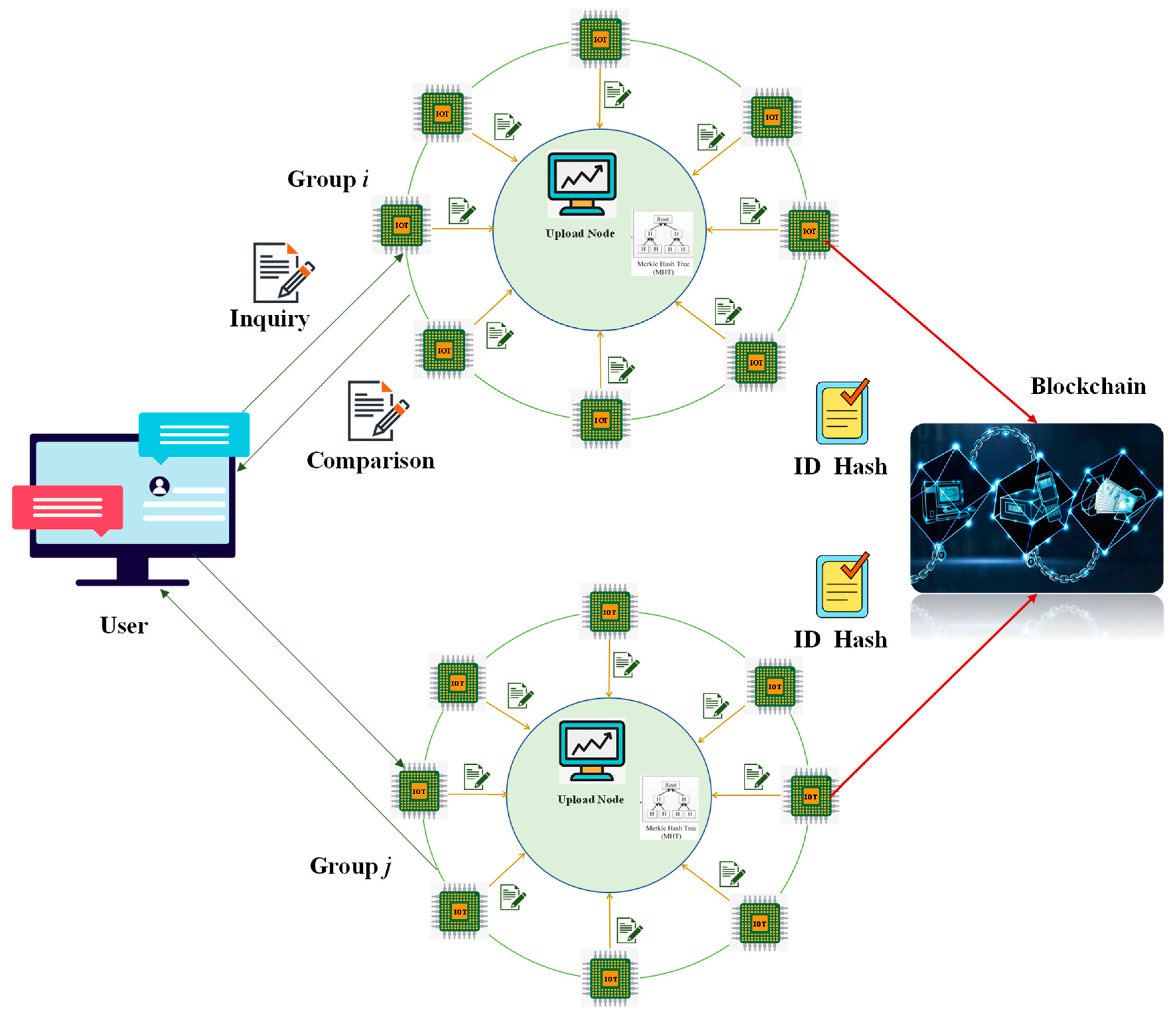
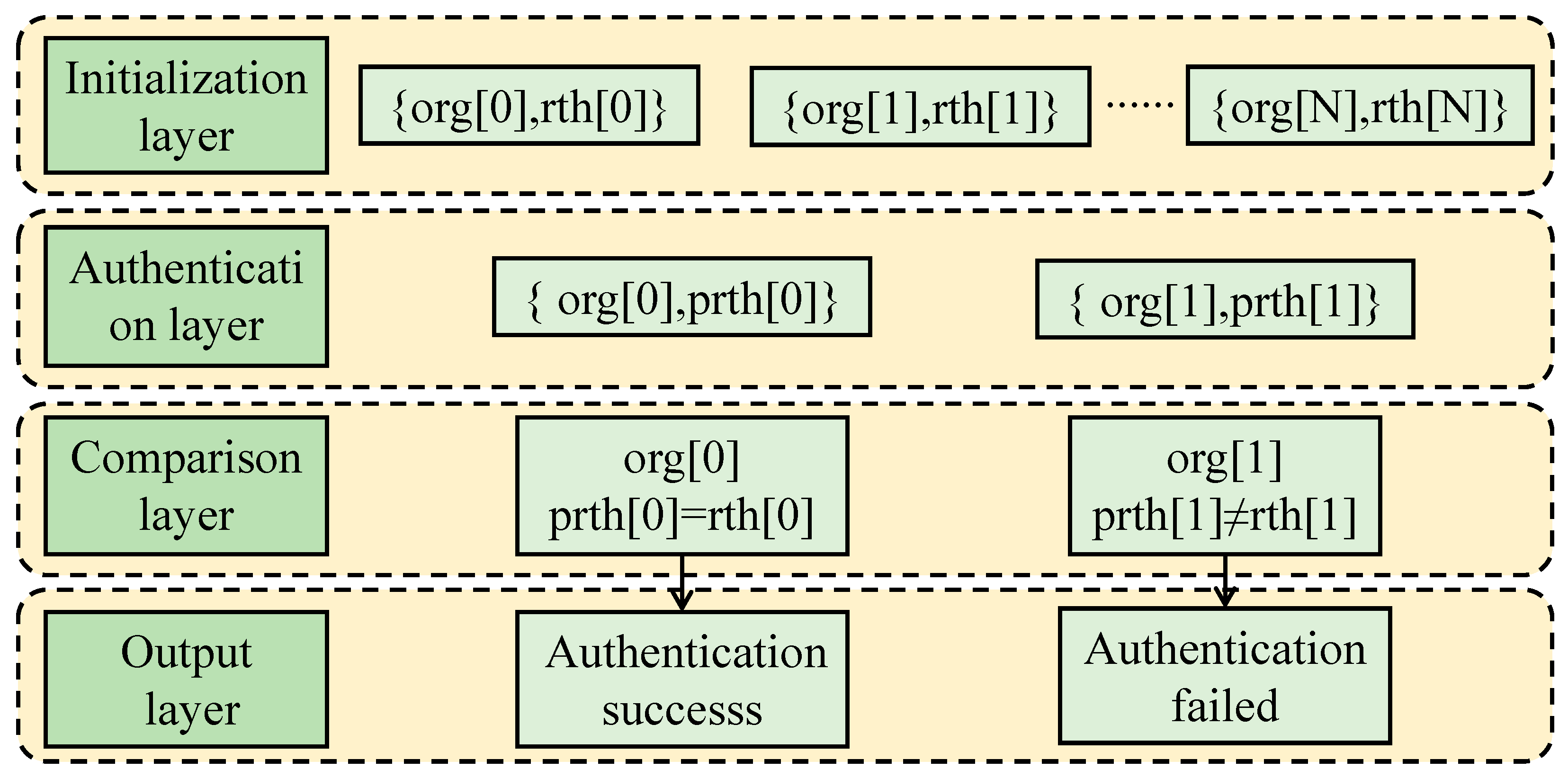
4. Blockchain Group Authentication Scheme
4.1. Group Authentication Principles
- (1)
- Each device’s ID is sufficiently random.
- (2)
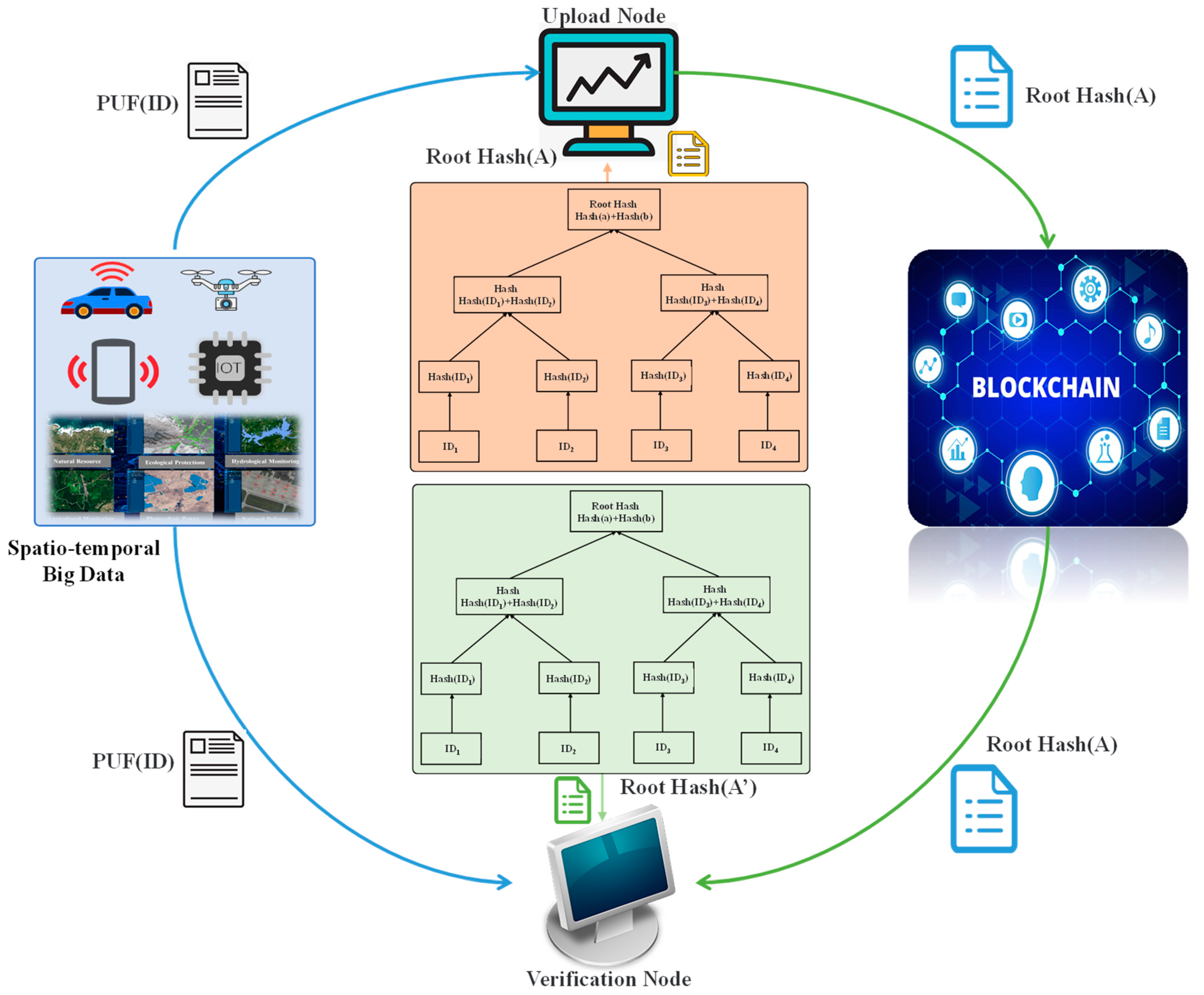
- Group: This is the unit of spatio-temporal big data collection, and the number of devices in each group can be specified by the user. Each group consists of several collection devices and an upload node with strong computing power. The role of the upload node is to receive the ID Hash of the collection device, build the MHT to obtain the Root Hash, and upload the Root Hash to the blockchain.
- (3)
- Blockchain: As a decentralized security storage module, its main function in this system is to store the Root Hash of the group sent by the upload node in the group.
- (4)
- Client: As a user of the system, it issues verification notifications and receives verification results.
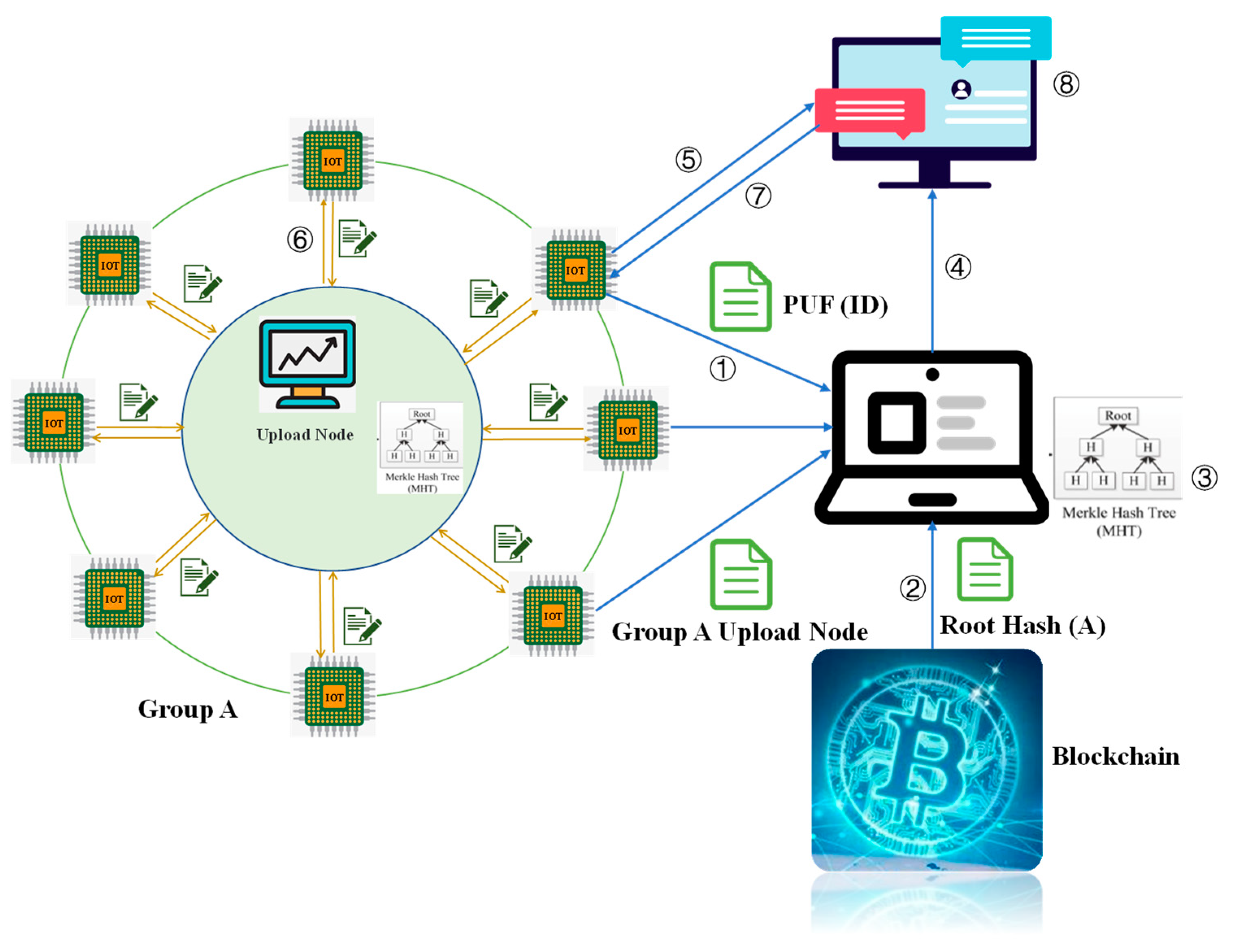
4.2. Initialization Phase
- ①
- The client sends an initialization command to group x.
- ②
- In group x, the device transmits the ID to the upload node, and the upload node performs the MHT algorithm on the ID of the device to the Root Hash value of the group.
- ③
- The upload node saves the Root Hash of its group in the blockchain for preservation.
4.3. Authentication Stage
- ①
- After receiving the verification challenge, all devices of group X use PUF technology to upload their IDs to the verification node (the upload node of group Y is randomly selected).
- ②
- After the verification node receives the ID Hash of the device in group X to be verified, it constructs the MHT to obtain the Root Hash (ROOTHASH(X′)) of the group to be verified.
- ③
- The verification node queries the Root Hash (ROOTHASH(X)) of the group to be verified from the blockchain. Compare ROOTHASH(X) and ROOTHASH(X′). If they are the same, the devices to be verified in this group are legal; if not, it is necessary to verify whether there is any illegal device in group X.
- ④
- Upload the verification result to the client.
- ⑤
- If the verification finds an illegal user, the client sends a challenge to the upload node of group X to be verified.
- ⑥
- The upload node of group X performs zero-knowledge proof identity authentication for the devices in the group.
- ⑦
- The group X upload node uploads the authentication result to the client.
- ⑧
- Based on the information provided by group X, the client finds out the information uploaded by illegal nodes and deletes it.
4.4. System Parameters
4.4.1. Experimental Hardware Parameters
4.4.2. Data Structure Parameter
5. Result Analysis
- (1)
- The Root Hash stored in the blockchain cannot be changed nor tampered with.
- (2)
- As long as there is an inconsistent leaf node in the MHT algorithm, the resulting Root Hash will be completely different. Thus, it is impossible to obtain the same Root Hash as the original ID to complete the authentication, though an attacker can find an ID from the Root Hash in the blockchain to the group to be verified.
5.1. Comparison of Different Authentication Schemes
5.2. Identity Authentication Security Performance Analysis
- (1)
- The hash function has a single irreversible feature, which can ensure that the user’s identity is not leaked.
- (2)
- Due to the intractability of discrete logarithms, even if the attack node intercepts v and a, Eve cannot find k from Formula (2).
- (3)
- The attacking node attempts to obtain r, and then intercepts y and e, so that he can obtain k from Formula (3); however, finding r from Formula (1) is also a problem that is difficult to solve for discrete logarithms. Similarly, the verification node cannot find r and then obtain k.
- (4)
- Replay attack. The scheme is based on the challenge/response method, the authentication process is dynamic and interactive, and the random number sent for each authentication is different. Even if the attacking node obtains all the previously authenticated information, the validating node will not be fooled by outdated information.
- (5)
- The verification node sends the message obtained during the transaction verification process to the attacking node. The verification node can only obtain v and y and judge whether the node is legal, and knows nothing about the relevant information of the private key k. Therefore, the security of the authentication process is guaranteed.
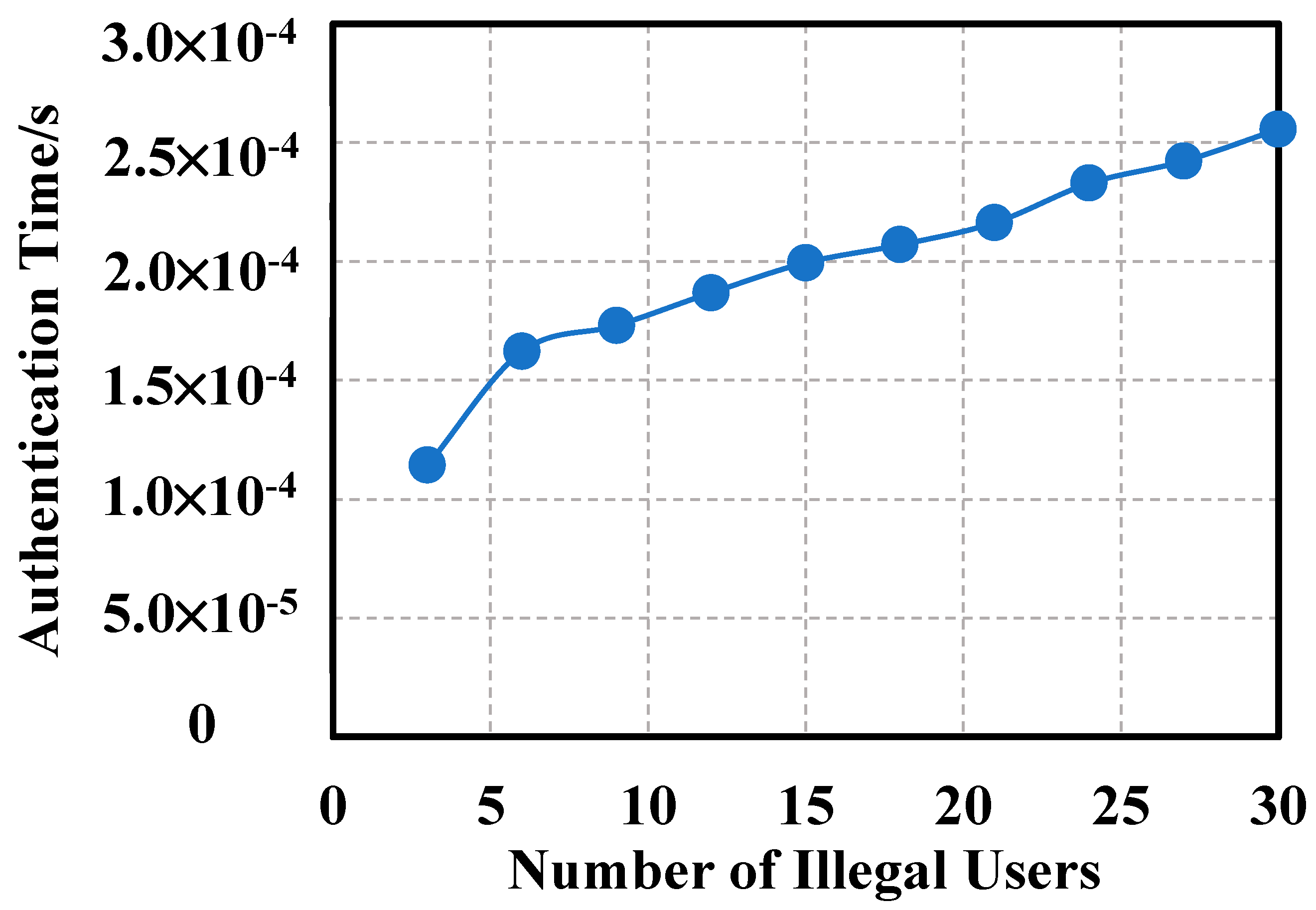
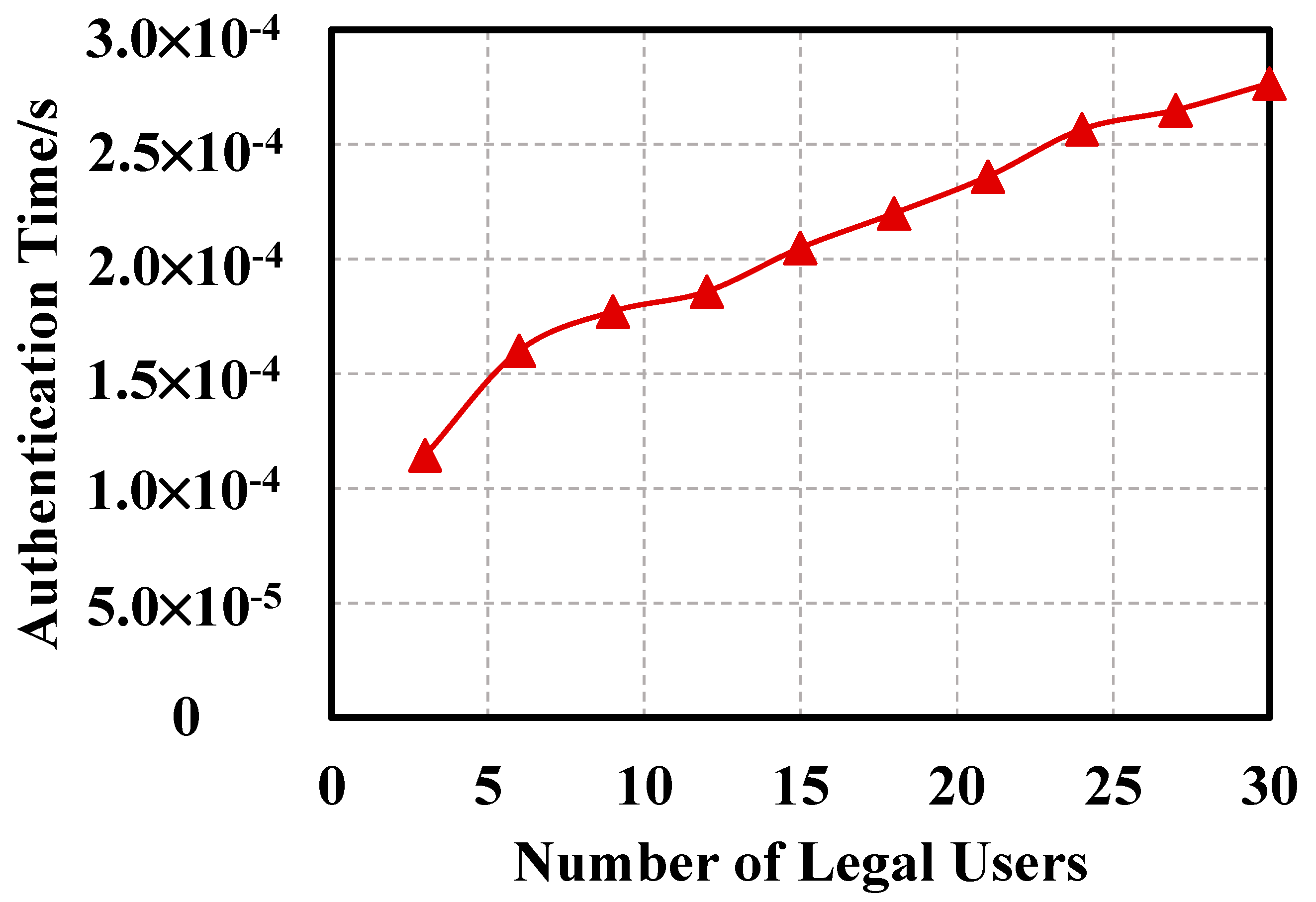
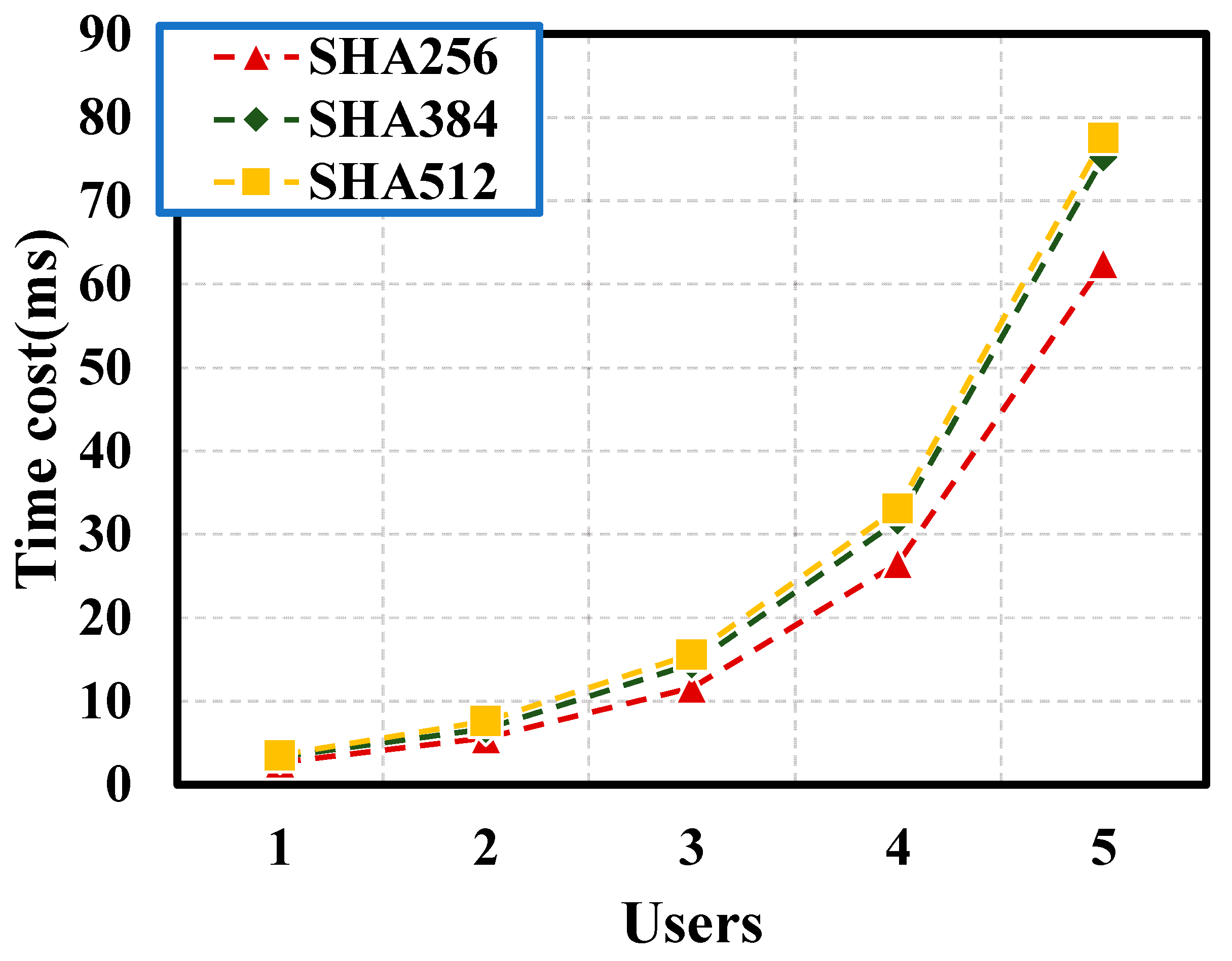
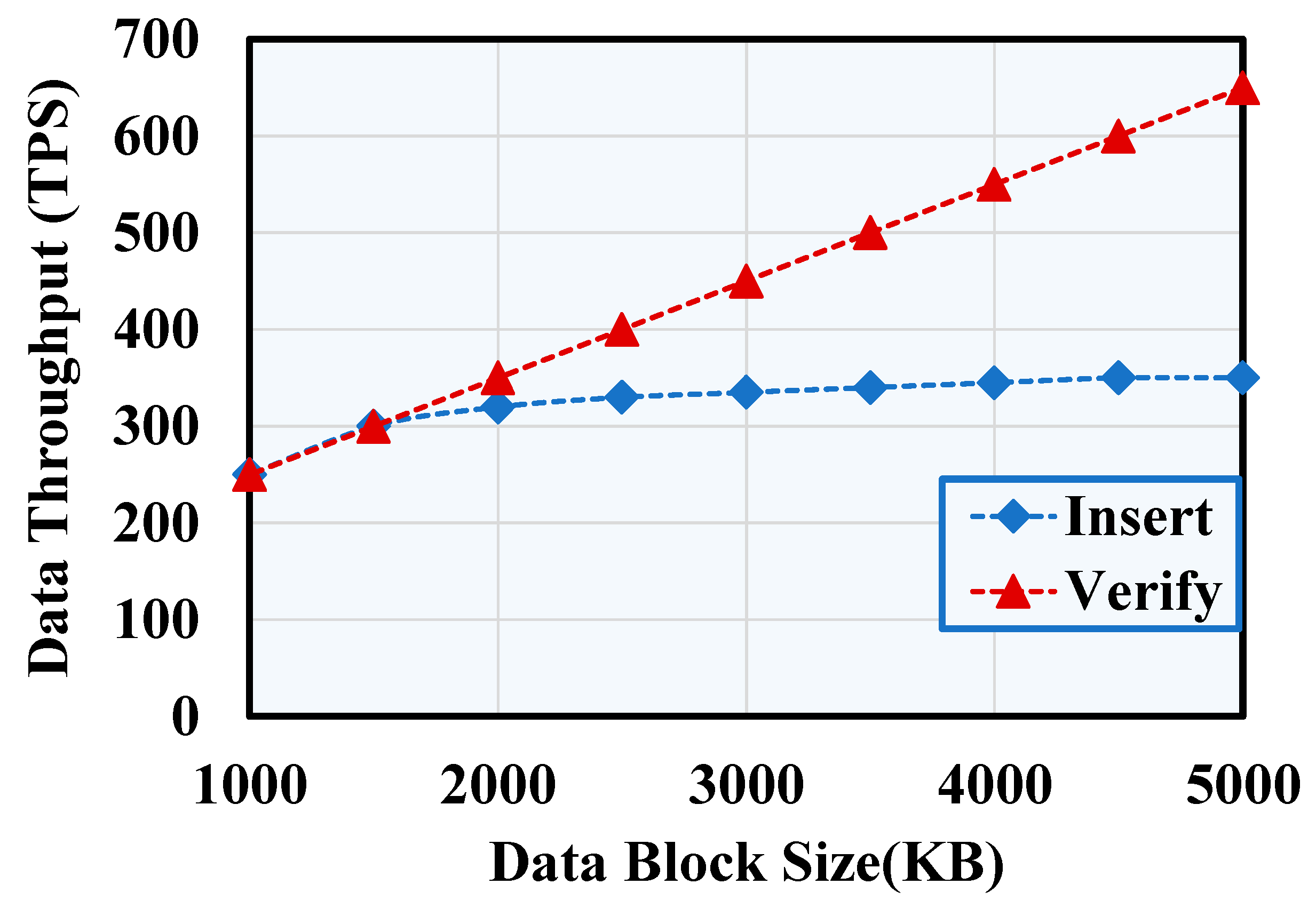
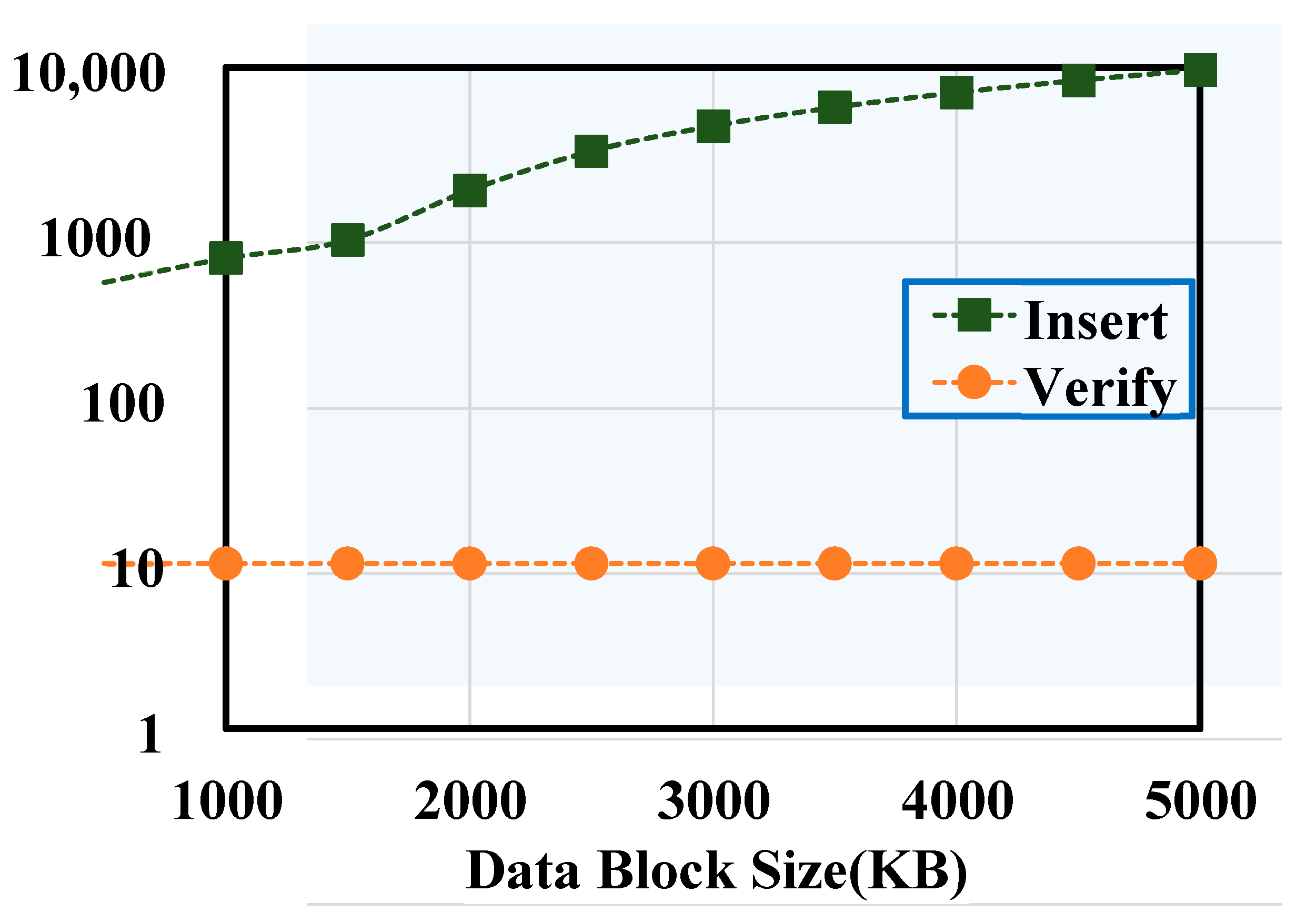
5.3. System Efficiency Analysis
- (1)
- Analysis of the internal efficiency of the system.
- (2)
- System throughput and delay analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ren, Y.; Huang, D.; Wang, W.; Yu, X. BSMD: A blockchain-based secure storage mechanism for big spatio-temporal data. Future Gener. Comput. Syst. 2023, 138, 328–338. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Sangaiah, A.K.; Xu, L.; Kumari, S.; Wu, L.; Shen, J. A lightweight and robust two factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 82, 727–737. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication protocols for internet of things: A comprehensive survey. Secur. Commun. Netw. 2017, 2017, 6562953. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Ahmim, A. Privacy-preservingschemes for ad hoc social networks: A survey. IEEE Commun. Surv. Tutor. 2017, 19, 3015–3045. [Google Scholar] [CrossRef]
- Braeken, A. PUF based authentication protocol for IoT. Symmetry 2018, 10, 352. [Google Scholar] [CrossRef]
- Cui, Z.; Xue, F.; Zhang, S.; Cai, X.; Cao, Y.; Zhang, W.; Chen, J. A hybrid blockchain-based identity authentication scheme for multi-WSN. IEEE Trans. Serv. Comput. 2020, 13, 241–251. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based auth-entication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Kalra, S.; Sood, S.K. Secure authentication scheme for IoT and cloud servers. Pervasive Mob. Comput. 2015, 24, 210–223. [Google Scholar] [CrossRef]
- Yang, H.J.; Li, Y.H. A Blockchain-Based Anonymous Authentication Scheme for Internet of Vehicles. Procedia Comput. Sci. 2022, 201, 413–420. [Google Scholar] [CrossRef]
- Ghosh, B.C.; Bhartia, T.; Addya, S.K.; Chakraborty, S. Leveraging public-private blockchain interoperability for closed consortium interfacing. In Proceedings of the INFOCOM 2021—IEEE Conference on Computer Communications, Vancouver, BC, Canada, 10–13 May 2021; pp. 1–10. [Google Scholar]
- Peng, Z.; Xu, J.; Chu, X.; Gao, S.; Yao, Y.; Gu, R.; Tang, Y. VFChain: Enabling Verifiable and Auditable Federated Learning via Blockchain Systems. IEEE Trans. Netw. Sci. Eng. 2021, 9, 173–186. [Google Scholar] [CrossRef]
- Li, Z.; Gao, S.; Peng, Z.; Guo, S.; Yang, Y.; Xiao, B. B-DNS: A secure and efficient DNS based on the blockchain technology. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1674–1686. [Google Scholar] [CrossRef]
- Ma, Z.; Meng, J.; Wang, J.; Shan, Z. Blockchain-based decentralized authentication modeling scheme in edge and IoT environment. IEEE Internet Things J. 2020, 8, 2116–2123. [Google Scholar]
- Patel, S.; Sahoo, A.; Mohanta, B.K.; Panda, S.S.; Jena, D. DAuth: A decentralized web authentication system using Ethereum based blockchain. In Proceedings of the 2019 International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019; pp. 1–5. [Google Scholar]
- Biswas, S.; Sharif, K.; Li, F.; Nour, B.; Wang, Y. A scalable blockchain framework for secure transact-ions in IoT. IEEE Internet Things J. 2019, 6, 4650–4659. [Google Scholar] [CrossRef]
- Huang, J.; Kong, L.; Chen, G.; Wu, M.Y.; Liu, X.; Zeng, P. To-wards secure industrial IoT: Blockchain system with credit-based consensus mechanism. IEEE Trans. Ind. Inform. 2019, 15, 3680–3689. [Google Scholar] [CrossRef]
- Almadhoun, R.; Kadadha, M.; Alhemeiri, M.; Alshehh, M.; Salah, K. A user authentication scheme of IoT devices using blockchain-enabled fog nodes. In Proceedings of the IEEE/ACS 15th International Conference on Computer Systems and Applications (AICCSA), Aqaba, Jordan, 28 October–1 November 2018. [Google Scholar] [CrossRef]
- Bao, Z.; Shi, W.; He, D.; Chood, K.K.R. IoTChain: A three-tier blockchain-based IoT security architecture. arXiv 2018, arXiv:1806.02008. [Google Scholar]
- Dorri, A.; Jurdak, R.; Gauravaram, P. Blockchain for IoT Security and Privacy: The Case Study of a Smart Home. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 6 April 2023).
- Chatterjee, U.; Chakraborty, R.S.; Mukhopadhyay, D. A PUF-based secure communication protocol for IoT. ACM Trans. Embed. Comput. Syst. 2017, 16, 1–25. [Google Scholar] [CrossRef]
- Merkle, R.C. A certified digital signature. In Advances in Cryptology—CRYPTO’89 Proceedings; Springer: New York, NY, USA, 2001; pp. 218–238. [Google Scholar] [CrossRef]
- Wang, J. Formalization of SHA256 Algorithm for Blockchain. Master’s Thesis, Beijing University of Chemical Industry, Beijing, China, 2022. [Google Scholar] [CrossRef]
- Li, W.H.; Zhang, Z.Y.; Zhou, Z.B.; Deng, Y. A Review of Concise Non-interactive zero-knowledge proof. Acta Cryptologica Sin. 2022, 9, 379–447. [Google Scholar] [CrossRef]
- Zhou, X.C. Research on Authentication Mechanism Based on Zero-Knowledge Proof and Discrete Logarithm. Master’s Thesis, Hefei University of Technology, Hefei, China, 2004. [Google Scholar] [CrossRef]
- Gao, S.; Peng, Z.; Tan, F.; Zheng, Y.; Xiao, B. SymmeProof: Compact zero-knowledge argument for blockchain confidential transactions. IEEE Trans. Dependable Secur. Comput. 2022, 20, 2289–2301. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, X.L.; Ye, Q.; Jiang, H.H. Security Authentication Scheme Based on Zero-knowledge Proof. Comput. Digit. Eng. 2015, 43, 4. [Google Scholar] [CrossRef]
- Sun, X.; Men, S.; Zhao, C.; Zhou, Z. A security authentication scheme in machine-to-machine home network service. Secur. Commun. Netw. 2015, 8, 2678–2686. [Google Scholar] [CrossRef]
- Li, D.; Peng, W.; Deng, W.; Gai, F. A blockchain-based authentication and security mechanism for IoT. In Proceedings of the 27th International Conference on Computer Communication and Networks (ICCCN). In Proceedings of the 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018; pp. 1–6. [Google Scholar]
- Shawky, M.A.; Jabbar, A.; Usman, M.; Imran, M.; Abbasi, Q.H.; Ansari, S.; Taha, A. Efficient Blockchain-based Group Key Distribution for Secure Authentication in VANETs. IEEE Netw. Lett. 2023, 5, 64–68. [Google Scholar] [CrossRef]
| Parameter Name | Parameter Interpretation |
|---|---|
| CE | Client End |
| UN | Upload Node |
| VN | Verification Node |
| BLC | Blockchain |
| INPUT(x) | CE Selects a Group to Be Authenticated(X) |
| RANDOM(x) | Select The UN Of Group(Y) As VN(Random) |
| VERIFY(x) | CE Sent to Group X To Authenticated |
| AUTHORIZE(x,y) | CE Sent Authentication to Node Y |
| PUF(ID,x,y) | ID of a Transmission Group Member |
| QUERY(x) | Query The ROOTHASH(X) Stored in The Blockchain |
| ROOTHASH(x) | ROOTHASH Come From UN |
| ROOTHASH(x′) | ROOTHASH Come From VN |
| MHTupload [ID(x)] = ROOTHASH(x) | UN Obtains ROOTHASH(X) By Building MHT |
| MHTlocal [ID(x)] = ROOTHASH(x′) | VN Obtains ROOTHASH(X′) By Building MHT |
| COMPARE(x,x′) | Compare ROOTHASH(X) With ROOTHASH(X′) |
| PUF(ID) | Use PUF Technology to Encrypt Device’s Ids |
| INTLALIZE(x) | Group X Is Initialized |
| INSERT[ROOTHASH(x)] | Save Group’s Root hash(X) to the Blockchain |
| RETURN (A, B, Y/N) | The Result Message Sent by A To B |
| RETURN (A, B, Y) | The Knot Return Message Sent by A To B |
| ZKPV(x) | Zero-Knowledge Proof Algorithm |
| CE | UN | BLG | |
| IF Y → FINISH IF N → REPEAT | |||
| CE | UN | VN | BL |
| INPUT(x) RANDOM(y) | |||
| MTHlocal[ID(x)] = ROOTHASH(x′) | |||
| IF Y → FINISHIF N → ZKPV(X) | |||
| DELETE(x) INITLALIZE(x) FINISH | |||
| Name | Data |
|---|---|
| CPU | 8 core CPU |
| Memory | 16.00 GB |
| Hard disk | 512 GB |
| Cloud server | Aliyun |
| Number of Group Members | Number of Illegal Members | Number of Trials | Number of Successes | Number of Failures | Verification Success Rate |
|---|---|---|---|---|---|
| 5000 | 0 | 100 | 100 | 0 | 100% |
| 5000 | 5 | 100 | 100 | 0 | 100% |
| 5000 | 20 | 100 | 100 | 0 | 100% |
| 10,000 | 0 | 100 | 100 | 0 | 100% |
| 10,000 | 5 | 100 | 100 | 0 | 100% |
| 10,000 | 20 | 100 | 100 | 0 | 100% |
| Scheme | Single/Group/Mixed Authentication | Decentralization /Centralization | Time Cost | Certification Efficiency |
|---|---|---|---|---|
| Literature [27] | Single | Centralization | O (1) | Poor |
| Literature [28] | Single | Decentralization | O (1) | Poor |
| Literature [14] | Single | Decentralization | O(n2) | Poor |
| Literature [29] | Group | Decentralization | O (n2) | Median |
| This scheme | Mixed | Decentralization | O (logn) | Strong |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, B.; Zhao, J.; Chen, G.; Yin, Y. Security Authentication Mechanism of Spatio-Temporal Big Data Based on Blockchain. Appl. Sci. 2023, 13, 6641. https://doi.org/10.3390/app13116641
Zhou B, Zhao J, Chen G, Yin Y. Security Authentication Mechanism of Spatio-Temporal Big Data Based on Blockchain. Applied Sciences. 2023; 13(11):6641. https://doi.org/10.3390/app13116641
Chicago/Turabian StyleZhou, Bao, Junsan Zhao, Guoping Chen, and Ying Yin. 2023. "Security Authentication Mechanism of Spatio-Temporal Big Data Based on Blockchain" Applied Sciences 13, no. 11: 6641. https://doi.org/10.3390/app13116641
APA StyleZhou, B., Zhao, J., Chen, G., & Yin, Y. (2023). Security Authentication Mechanism of Spatio-Temporal Big Data Based on Blockchain. Applied Sciences, 13(11), 6641. https://doi.org/10.3390/app13116641





