SLMAS: A Secure and Light Weight Mutual Authentication Scheme for the Smart Wheelchair
Abstract
1. Introduction
1.1. Key Terms Explanation
1.1.1. XOR Operation
1.1.2. Cryptographic Hash Mechanism
1.1.3. Elliptic Curve Cryptography (ECC)
1.1.4. Symmetric Cryptography
1.1.5. Asymmetric Cryptography
1.1.6. Hajj and Umrah Services
1.2. Adversarial Model
- The communication between two parties occurs via a public channel, and neither endpoint is deemed trustworthy.
- The possesses complete owning authority over the public communication channel.
- The can improve or edit the message being transmitted through the public channel and create a fraudulent message.
- It is impossible to compromise the secret/private key of the trusted authority ()/ central authority ().
1.3. Motivations and Contributions
2. Literature Review
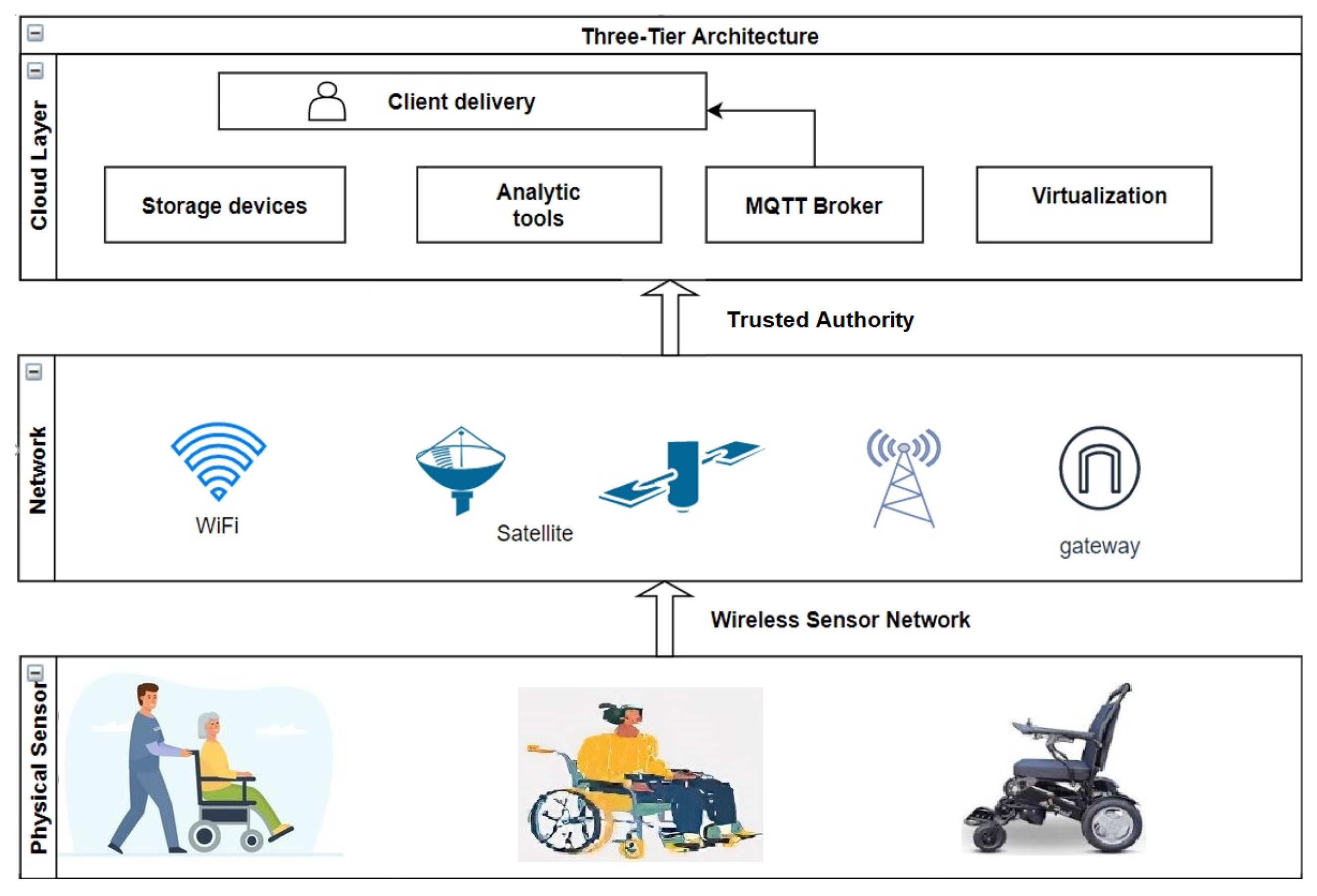
3. Proposed Scheme
3.1. Initialization Process
3.2. Server Registration Process
- Server () picks an identity , and sends it through a protected link to the .
- obtains the registration request from , opts for a random number , a temporary identity , and computes . sends the message that contains to over the trusted channel. further save the parameter in the database.
- Upon receiving the response from , saves the parameters .
3.3. Sensor Node Registration Process
- Sensor Node () catches an identity , and sends it through a protected route to the .
- is contacted by the registration request from , decides a random values , a temporary identity , and computes . communicates the message that contains to over the protected medium. also saves the value in the database.
- Upon receiving the response from , saves the parameters , as presented in Table 7.
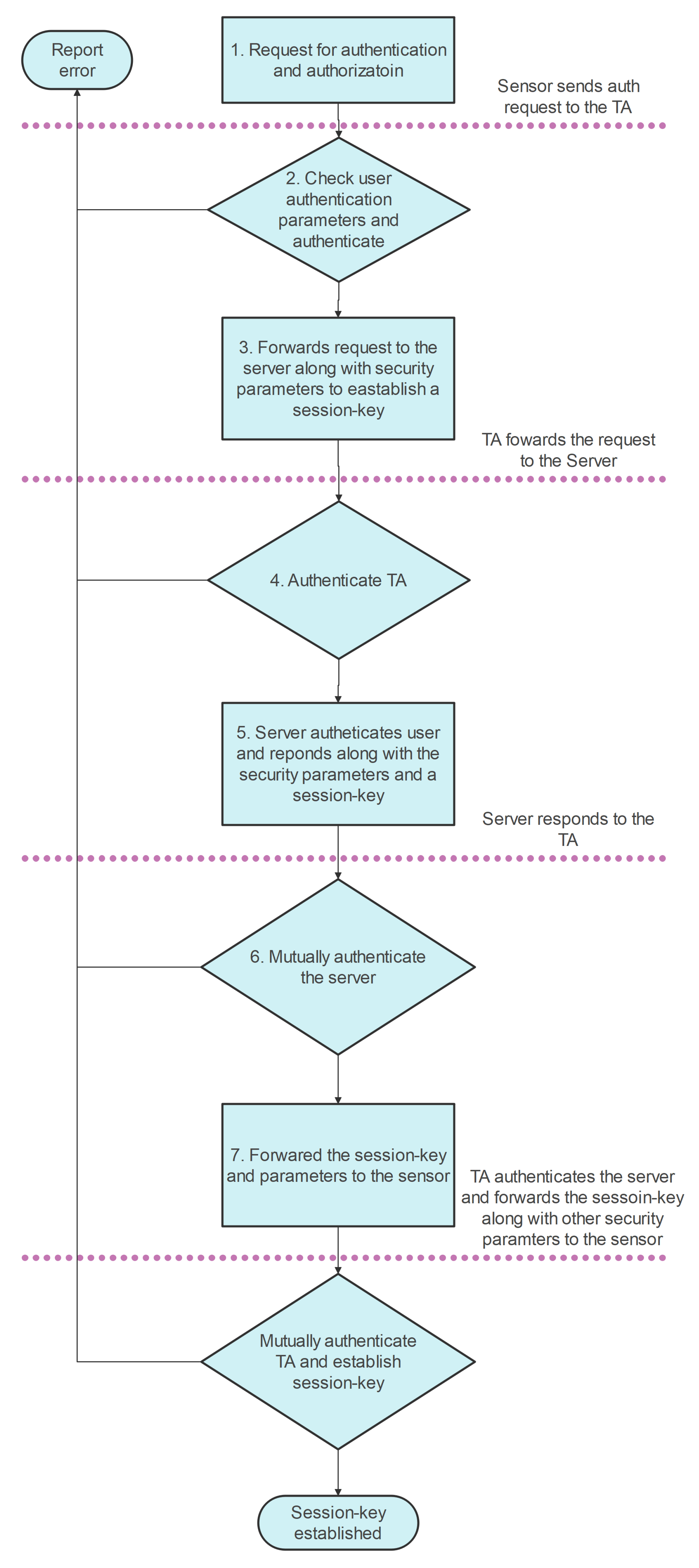
3.4. Authentication and Key-Agreement Process
- selects an arbitrary number and timestamp and computes . Finally, transmits the message to the containing over the public channel.
- Upon obtaining the message from , first verifies the message freshness by examining the condition and check if exists in DB.
- If true, further computes . verifies the authenticity of the by examining the condition
- If true, further computes . picks two arbitrary numbers and further computes . Finally, sends the message containing to the over the insecure channel.
- Upon obtaining the message from , first verifies the messages freshness by examining the condition . Next computes and confirms the legitimacy of the by assessing the scenario .
- If true, picks two arbitrary numbers and presents timestamp , and further computes . Finally, sends the message containing to the via an open channel.
- When the message arrives from to , first assesses the message freshness by validating the condition . If true, further computes pick , and corroborates the validity of the by checking the condition .
- If true , picks a current timestamp and further computes . finally transmits the message containing to the via an open channel.
- Upon the arrival of messages from the , firstly checks the message’s timeliness by inspecting the condition .
- If true, further checks the condition to authenticate the .
- If the condition is validated successfully will compute . If , this key safeguards communication among the and .
4. Security Evaluation of the Proposed Methodology
4.1. Informal Analysis
4.1.1. Mutual Authentication (MA)
4.1.2. Untraceability
4.1.3. Anonymity
4.1.4. Session Key Agreement
4.1.5. Sensor Node Impersonation Attack (IA)
4.1.6. Smart Node Capture Attack
4.1.7. Replay Attack (RA)
4.1.8. Man-in-the-Middle Attack (MITM)
4.1.9. Known Session Key Attack
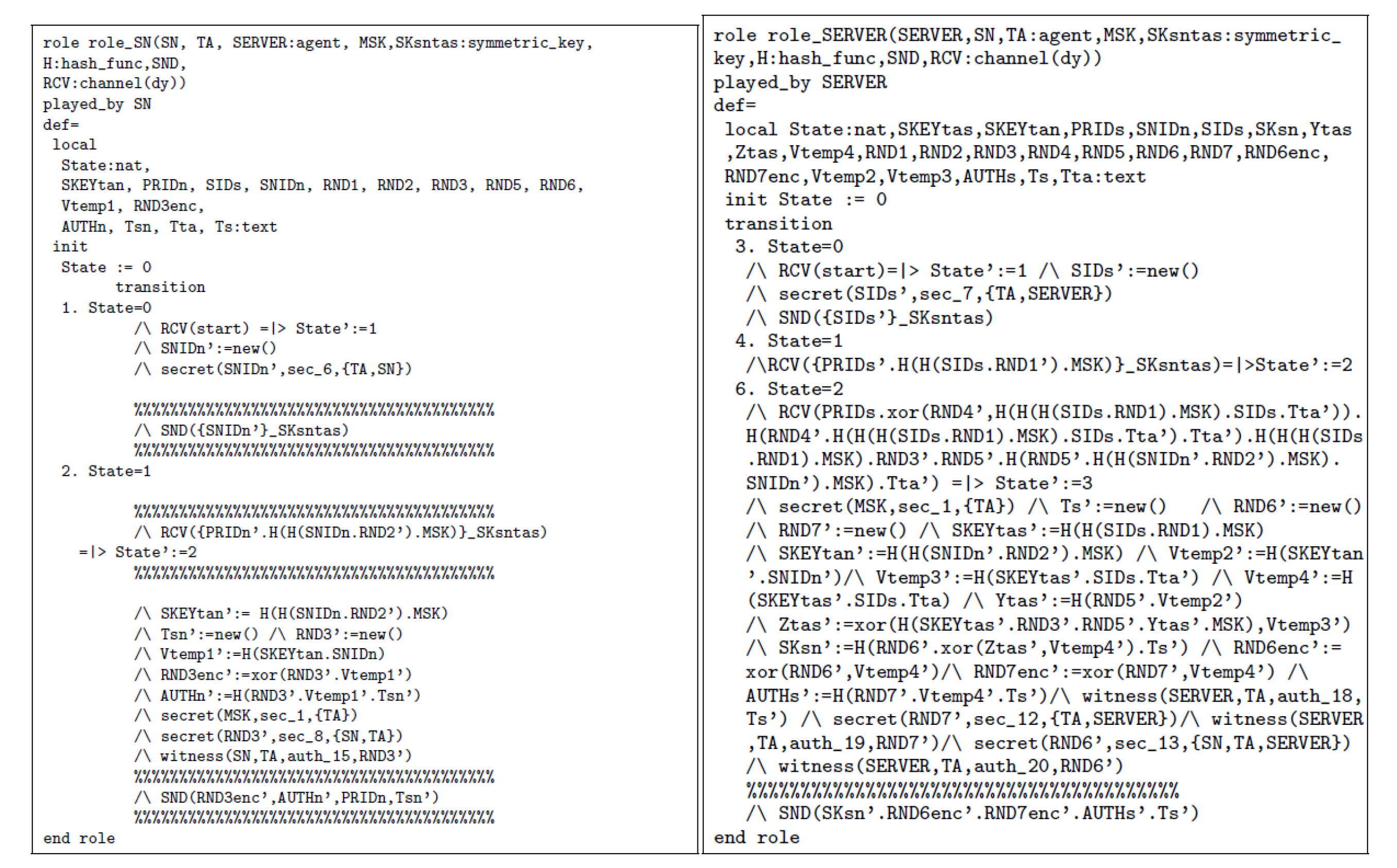
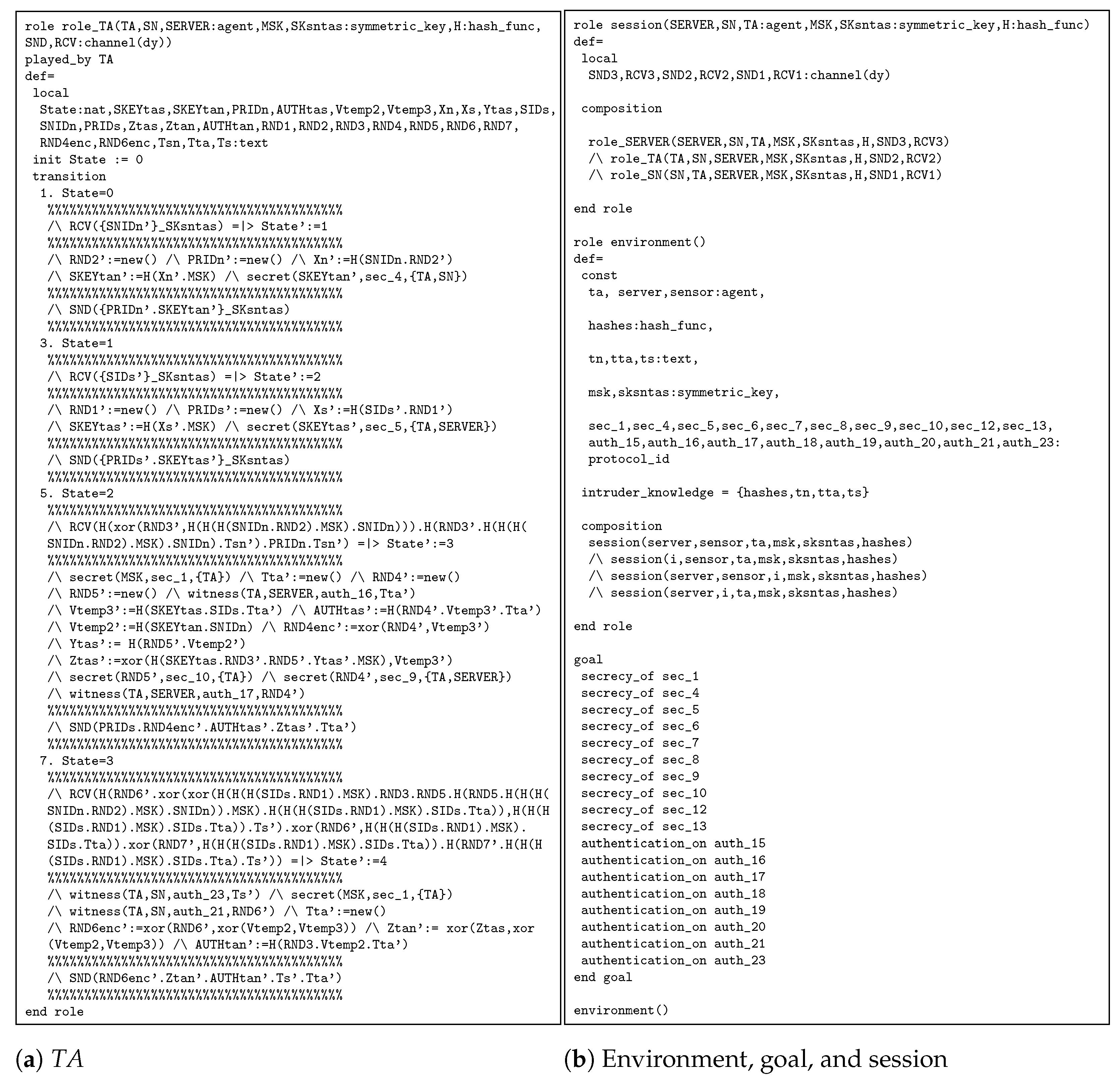
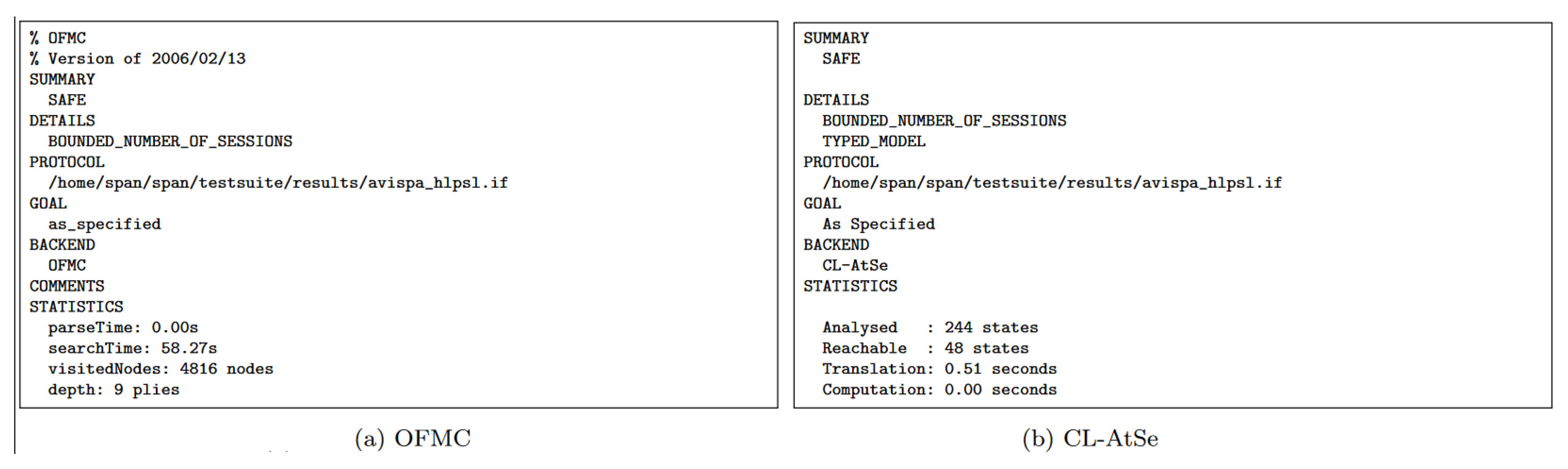
4.2. Automated Security Analysis Performed Formally with the AVISPA Tool
5. Comparative Analysis
5.1. Functionality Comparison
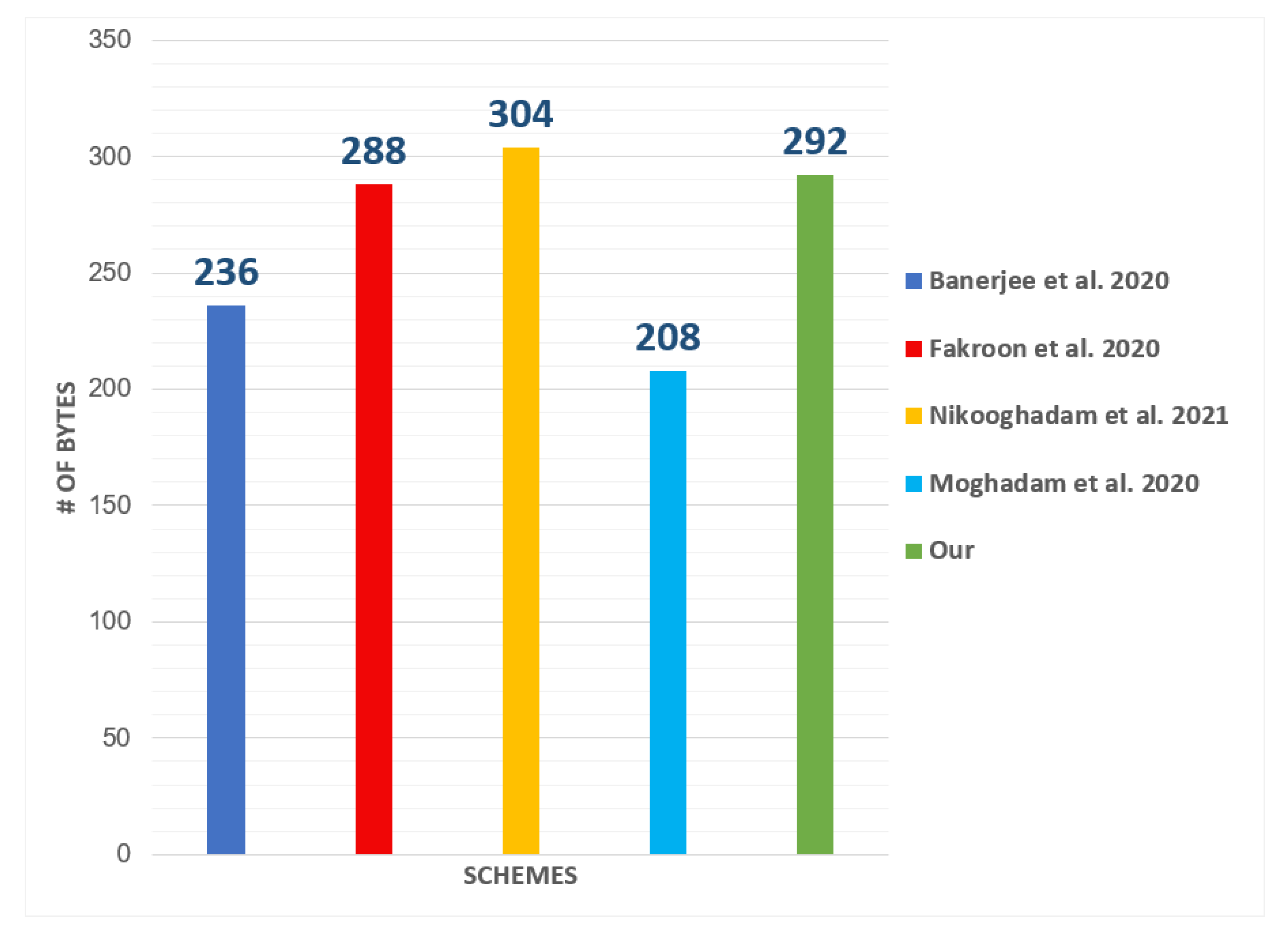
5.2. Communication Analysis
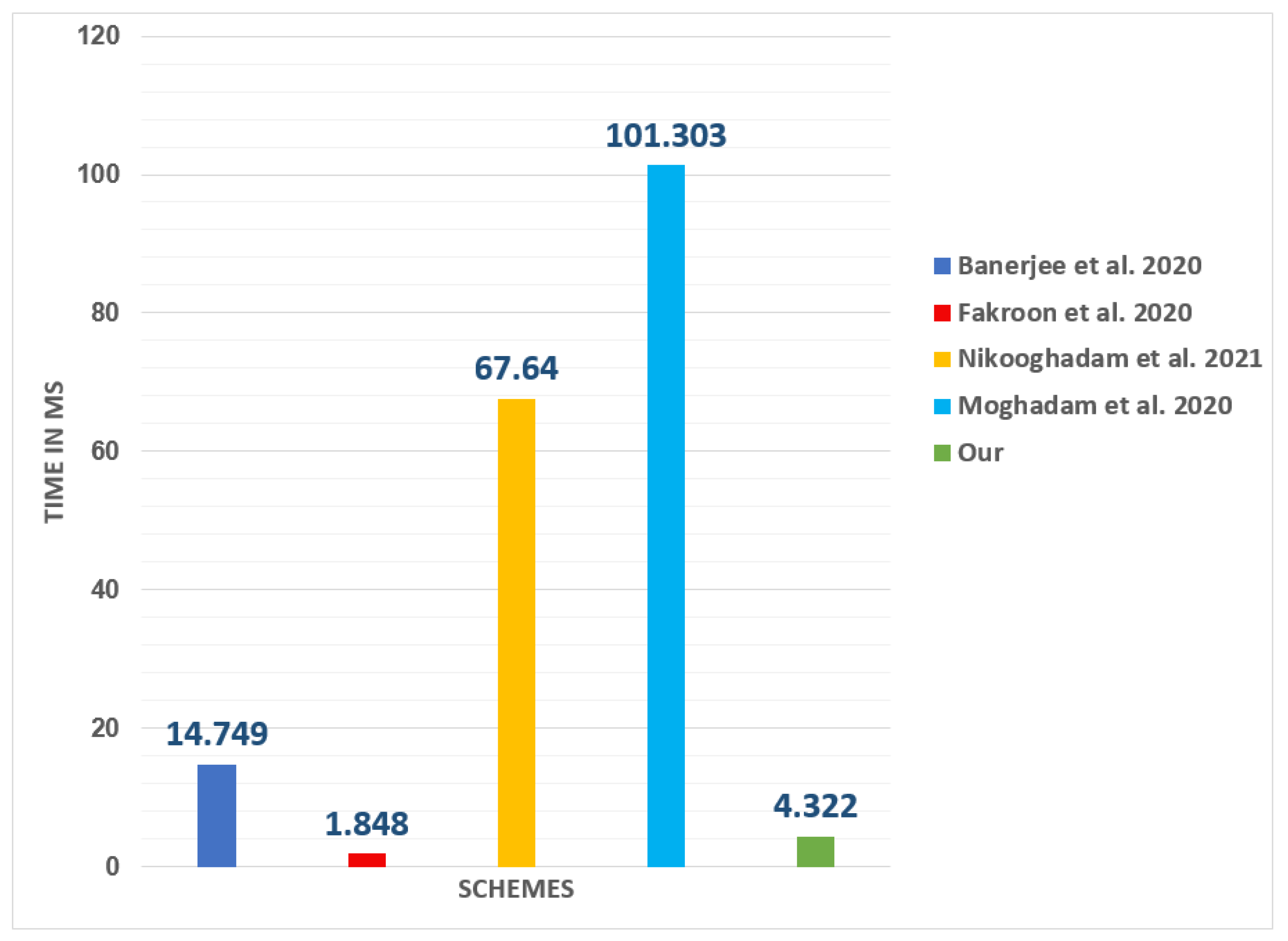
5.3. Computation Analysis
6. Limitations and Challenges
- Limited Resources: WSNs have resource constraints regarding memory, processing power, and battery life. Therefore, security protocols must be designed with these limitations in mind, to ensure they do not consume too much energy or memory.
- Limited Physical Security: Sensor nodes are often deployed in unattended environments vulnerable to physical attacks. Security protocols should be designed to withstand physical attacks, such as tampering, destruction, or theft of the nodes.
- Communication Overhead: Security protocols often introduce additional communication overheads, leading to increased latency, energy consumption, and reduced network performance. Therefore, it is essential to design security protocols that minimize communication overheads, while providing sufficient security.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Oueida, S.; Kotb, Y.; Aloqaily, M.; Jararweh, Y.; Baker, T. An edge computing based smart healthcare framework for resource management. Sensors 2018, 18, 4307. [Google Scholar] [CrossRef] [PubMed]
- Al Shabibi, M.A.K.; Kesavan, S.M. Iot based smart wheelchair for disabled people. In Proceedings of the 2021 International Conference on System, Computation, Automation and Networking (ICSCAN), Puducherry, India, 30–31 July 2021; pp. 1–6. [Google Scholar]
- Bourgeois-Doyle, R.I. George J. Klein: The Great Inventor; Number 2; NRC Research Press: Ottawa, ON, Canada, 2004. [Google Scholar]
- Khan, N.A.; Jhanjhi, N.; Brohi, S.N.; Almazroi, A.A.; Almazroi, A.A. A secure communication protocol for unmanned aerial vehicles. Comput. Mater. Contin. 2022, 70, 601–618. [Google Scholar]
- Rahimunnisa, K.; Atchaiya, M.; Arunachalam, B.; Divyaa, V. AI-based smart and intelligent wheelchair. J. Appl. Res. Technol. 2020, 18, 362–367. [Google Scholar] [CrossRef]
- Haseeb-ur Rehman, R.M.A.; Liaqat, M.; Aman, A.H.M.; Almazroi, A.A.; Hasan, M.K.; Ali, Z.; Ali, R.L. LR-AKAP: A Lightweight and Robust Security Protocol for Smart Home Environments. Sensors 2022, 22, 6902. [Google Scholar] [CrossRef] [PubMed]
- Kumar, D.; Maurya, A.K.; Baranwal, G. IoT services in healthcare industry with fog/edge and cloud computing. In IoT-Based Data Analytics for the Healthcare Industry; Elsevier: Amsterdam, The Netherlands, 2021; pp. 81–103. [Google Scholar]
- Udaya, R.V.; Poojasree, S. An IOT Driven Eyeball And Gesture-Controlled Smart Wheelchair System for Disabled Person. In Proceedings of the 2022 8th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 25–26 March 2022; Volume 1, pp. 1287–1291. [Google Scholar]
- Mohamed, M.N. Hajj & Umrah from A to Z; IslamKotob: Riyadh, Saudi Arabia, 1996. [Google Scholar]
- Liaqat, M.; Gani, A.; Anisi, M.H.; Ab Hamid, S.H.; Akhunzada, A.; Khan, M.K.; Ali, R.L. Distance-based and low energy adaptive clustering protocol for wireless sensor networks. PLoS ONE 2016, 11, e0161340. [Google Scholar] [CrossRef]
- Haseeb-Ur-Rehman, R.M.A.; Liaqat, M.; Aman, A.H.M.; Ab Hamid, S.H.; Ali, R.L.; Shuja, J.; Khan, M.K. Sensor cloud frameworks: State-of-the-art, taxonomy, and research issues. IEEE Sens. J. 2021, 21, 22347–22370. [Google Scholar] [CrossRef]
- Ali, Z.; Hussain, S.; Rehman, R.H.U.; Munshi, A.; Liaqat, M.; Kumar, N.; Chaudhry, S.A. ITSSAKA-MS: An improved three-factor symmetric-key based secure AKA scheme for multi-server environments. IEEE Access 2020, 8, 107993–108003. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Shon, T.; Al-Turjman, F.; Alsharif, M.H. Correcting design flaws: An improved and cloud assisted key agreement scheme in cyber physical systems. Comput. Commun. 2020, 153, 527–537. [Google Scholar] [CrossRef]
- Ali, Z.; Ghani, A.; Khan, I.; Chaudhry, S.A.; Islam, S.H.; Giri, D. A robust authentication and access control protocol for securing wireless healthcare sensor networks. J. Inf. Secur. Appl. 2020, 52, 102502. [Google Scholar] [CrossRef]
- Ghani, A.; Mansoor, K.; Mehmood, S.; Chaudhry, S.A.; Rahman, A.U.; Saqib, M.N. Security and key management in IoT-based wireless sensor networks: An authentication protocol using symmetric key. Int. J. Commun. Syst. 2019, 32, e4139. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and Security Improvements of ‘Two-Factor User Authentication in Wireless Sensor Networks’. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Chen, T.H.; Shih, W.K. A Robust Mutual Authentication Protocol for Wireless Sensor Networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Suh, G.E.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. In Proceedings of the 2007 44th ACM/IEEE Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Aysu, A.; Gulcan, E.; Moriyama, D.; Schaumont, P.; Yung, M. End-to-end design of a PUF-based privacy preserving authentication protocol. In Cryptographic Hardware and Embedded Systems—CHES 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 556–576. [Google Scholar]
- Majzoobi, M.; Elnably, A.; Koushanfar, F. FPGA Time-Bounded Unclonable Authentication. In Information Hiding; Böhme, R., Fong, P.W.L., Safavi-Naini, R., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; pp. 1–16. [Google Scholar] [CrossRef]
- Rührmair, U. SIMPL systems: On a public key variant of physical unclonable functions. In SOFSEM 2011: Theory and Practice of Computer Science; SOFSEM 2011; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 6543. [Google Scholar]
- Bassil, R.; El-Beaino, W.; Kayssi, A.; Chehab, A. A PUF-based ultra-lightweight mutual-authentication RFID protocol. In Proceedings of the 2011 International Conference for Internet Technology and Secured Transactions, Abu Dhabi, United Arab Emirates, 11–14 December 2011; pp. 495–499. [Google Scholar]
- Kulseng, L.; Yu, Z.; Wei, Y.; Guan, Y. Lightweight mutual authentication and ownership transfer for RFID systems. In Proceedings of the 2010 IEEE Infocom, San Diego, CA, USA, 14–19 March 2010; pp. 1–5. [Google Scholar]
- Zhang, X.; Huang, W.; Xu, H.; Wang, Y. The lightweight ownership transfer protocol using physically unclonable function. Int. J. Secur. Its Appl. 2016, 10, 115–128. [Google Scholar] [CrossRef]
- Jung, S.W.; Jung, S. HRP: A HMAC-based RFID mutual authentication protocol using PUF. In Proceedings of the The International Conference on Information Networking 2013 (ICOIN), Bangkok, Thailand, 28–30 January 2013; pp. 578–582. [Google Scholar]
- Lee, Y.S.; Lee, H.J.; Alasaarela, E. Mutual authentication in wireless body sensor networks (WBSN) based on physical unclonable function (PUF). In Proceedings of the 2013 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013; pp. 1314–1318. [Google Scholar]
- Cortese, P.F.; Gemmiti, F.; Palazzi, B.; Pizzonia, M.; Rimondini, M. Efficient and practical authentication of PUF-based RFID tags in supply chains. In Proceedings of the 2010 IEEE International Conference on RFID-Technology and Applications, Guangzhou, China, 17–19 June 2010; pp. 182–188. [Google Scholar]
- Wallrabenstein, J.R. Practical and secure IoT device authentication using physical unclonable functions. In Proceedings of the 2016 IEEE 4th international conference on future internet of things and cloud (FiCloud), Vienna, Austria, 22–24 August 2016; pp. 99–106. [Google Scholar]
- Sutar, S.; Raha, A.; Raghunathan, V. D-PUF: An intrinsically reconfigurable DRAM PUF for device authentication in embedded systems. In Proceedings of the 2016 International Conference on Compliers, Architectures, and Sythesis of Embedded Systems (CASES), Pittsburgh, PA, USA, 2–7 October 2016; pp. 1–10. [Google Scholar] [CrossRef]
- Challa, S.; Wazid, M.; Das, A.K.; Kumar, N.; Reddy, A.G.; Yoon, E.J.; Yoo, K.Y. Secure signature-based authenticated key establishment scheme for future IoT applications. IEEE Access 2017, 5, 3028–3043. [Google Scholar] [CrossRef]
- Jia, X.; He, D.; Li, L.; Choo, K.K.R. Signature-based three-factor authenticated key exchange for internet of things applications. Multimed. Tools Appl. 2018, 77, 18355–18382. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Masud, M.; Gaba, G.S.; Alqahtani, S.; Muhammad, G.; Gupta, B.B.; Kumar, P.; Ghoneim, A. A lightweight and robust secure key establishment protocol for internet of medical things in COVID-19 patients care. IEEE Internet Things J. 2020, 8, 15694–15703. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Advances in Cryptology—EUROCRYPT 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 337–351. [Google Scholar]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Shetty, S.; JPC Rodrigues, J.; Park, Y. LDAKM-EIoT: Lightweight device authentication and key management mechanism for edge-based IoT deployment. Sensors 2019, 19, 5539. [Google Scholar] [CrossRef]
- Hussain, S.; Ullah, S.S.; Uddin, M.; Iqbal, J.; Chen, C.L. A comprehensive survey on signcryption security mechanisms in wireless body area networks. Sensors 2022, 22, 1072. [Google Scholar] [CrossRef] [PubMed]
- Shreya, S.; Chatterjee, K.; Singh, A. A smart secure healthcare monitoring system with Internet of Medical Things. Comput. Electr. Eng. 2022, 101, 107969. [Google Scholar] [CrossRef]
- Sharma, G.; Kalra, S. A lightweight user authentication scheme for cloud-IoT based healthcare services. Iran. J. Sci. Technol. Trans. Electr. Eng. 2019, 43, 619–636. [Google Scholar] [CrossRef]
- Chang, C.C.; Lee, J.S.; Lo, Y.Y.; Liu, Y. A secure authentication scheme for telecare medical information systems. In Advances in Intelligent Information Hiding and Multimedia Signal Processing, Proceeding of the Twelfth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kaohsiung, Taiwan, 21–23 November 2016; Springer: Cham, Switzerland, 2017; Volume 1, pp. 303–312. [Google Scholar]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. An improved and provably secure three-factor user authentication scheme for wireless sensor networks. Peer-to-Peer Netw. Appl. 2018, 11, 1–20. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA Tool for the Automated Validation of Internet Security Protocols and Applications. In Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef]
- Fakroon, M.; Alshahrani, M.; Gebali, F.; Traore, I. Secure remote anonymous user authentication scheme for smart home environment. Internet Things 2020, 9, 100158. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H.; Islam, S.H.; Moghadam, M.F. A provably secure and lightweight authentication scheme for Internet of Drones for smart city surveillance. J. Syst. Archit. 2021, 115, 101955. [Google Scholar] [CrossRef]
- Moghadam, M.F.; Nikooghadam, M.; Jabban, M.A.B.A.; Alishahi, M.; Mortazavi, L.; Mohajerzadeh, A. An Efficient Authentication and Key Agreement Scheme Based on ECDH for Wireless Sensor Network. IEEE Access 2020, 8, 73182–73192. [Google Scholar] [CrossRef]
- Eastlake, D., 3rd; Jones, P. US Secure Hash Algorithm 1 (SHA1). RFC 2001, 3174, 1–22. [Google Scholar]
- Alotaibi, M. An Enhanced Symmetric Cryptosystem and Biometric-Based Anonymous User Authentication and Session Key Establishment Scheme for WSN. IEEE Access 2018, 6, 70072–70087. [Google Scholar] [CrossRef]
- Ali, Z.; Alzahrani, B.A.; Barnawi, A.; Al-Barakati, A.; Vijayakumar, P.; Chaudhry, S.A. TC-PSLAP: Temporal Credential-Based Provably Secure and Lightweight Authentication Protocol for IoT-Enabled Drone Environments. Secur. Commun. Netw. 2021, 2021, 9919460. [Google Scholar] [CrossRef]
| Scheme | Year | Drawbacks |
|---|---|---|
| Shreya et al. [44] | 2022 | Using IoMT devices entails new security and privacy problems, such as unwanted access to private medical information or the danger of data breaches because of device or communication channel flaws. |
| Masud et al. [36] | 2021 | It is prone to session key leakage, offline password guessing, and traceability attacks. |
| Zhou et al. [35] | 2019 | It is open to man-in-the-middle, privileged insider, impersonation and replay attacks. Moreover, its computation cost is very high |
| Sharma et al. [45] | 2019 | It is open to privileged insider and password guessing attacks |
| Wazid et al. [42] | 2019 | It is open to impersonation and lacks anonymity property attacks |
| Chang et al. [46] | 2017 | Its disadvantage is that the user ID and OTP are not secured throughout the login and authentication process |
| Wu et al. [47] | 2018 | It is not secure against user impersonation attacks and can also not provide user anonymity |
| Symbols | Representations |
|---|---|
| nth sensor node, its personal identity, pseudo-random identity | |
| sth server, its personal identity, pseudo-random identity | |
| Trusted Authority and its secret master-key | |
| Maximum admissible transmission-delay and present-time | |
| Shared session key between and | |
| Shared-secret-key among the and | |
| Shared-secret-key among the and server | |
| Current timestamps of , , and | |
| ith random value of 160 bits | |
| Verify if i equals to j | |
| Cryptographic one way hash function | |
| An adversary and privileged insider | |
| Bitwise exclusive or and concatenation-operators |
| Server | Trusted Authority |
|---|---|
| Select an identity | |
| Picks arbitrary number | |
| and Pseudo-random identity | |
| COMPUTE: | |
| Store | |
| tuple in the database | |
| Save |
| Sensor Node | Trusted Authority |
|---|---|
| Select an identity | |
| Picks arbitrary number | |
| and Pseudo-random identity | |
| COMPUTE: | |
| Store | |
| tuple in the database | |
| Save |
| Sensor Node () | Trusted Authority () | Server () |
|---|---|---|
| Select and | ||
| COMPUTE: | ||
| and check if exists in DB. | ||
| IF TRUE: | ||
| IF TRUE: | ||
| Pick and | ||
| and | ||
| IF TRUE: | ||
| IF TRUE: | ||
| Pick and | ||
| IF TRUE: | ||
| Pick | ||
| IF TRUE: | ||
| [49] | [50] | [51] | [52] | Our | |
|---|---|---|---|---|---|
| Sensor node anonymity | ✓ | ✓ | ✓ | ✓ | ✓ |
| Ephemeral Secret Leakage (ESL) | ✓ | ✗ | ✓ | ✗ | ✓ |
| Protection against RA | ✓ | ✓ | ✓ | ✓ | ✓ |
| Efficient protocol design | ✗ | ✓ | ✓ | ✗ | ✓ |
| Stolen verifier attack | ✗ | ✓ | ✗ | ✗ | ✓ |
| Stolen attack | ✓ | ✓ | ✓ | ✓ | ✓ |
| Untraceability | ✓ | ✓ | ✓ | ✓ | ✓ |
| Parallel attack | ✗ | ✓ | ✓ | ✓ | ✓ |
| Reply Attack | ✓ | ✗ | ✗ | ✓ | ✓ |
| Sensor nodes | ✗ | ✓ | ✓ | ✓ | ✓ |
| Server | ✓ | ✓ | ✓ | ✓ | ✓ |
| MITM attack | ✓ | ✓ | ✗ | ✓ | ✓ |
| Insider attack | ✓ | ✓ | ✗ | ✗ | ✓ |
| Mutual Authentication | ✓ | ✓ | ✗ | ✓ | ✓ |
| Formal automated security verification | ✓ | ✓ | ✓ | ✗ | ✓ |
| Protocols | # of Messages | # of Bytes |
|---|---|---|
| Banerjee et al. [49] | 4 | |
| Fakroon et al. [50] | 4 | |
| Nikooghadam et al. [51] | 4 | |
| Moghadam et al. [52] | 4 | |
| Our | 4 |
| Notations | Explanation | ≈ Computation Time |
|---|---|---|
| Hash function | ms | |
| Scalar multiplication | ms | |
| Symmetric enc/dec | ms | |
| Fuzzy extractor | ms | |
| function | ||
| Bilinear pairing | ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almazroi, A.A.; Liaqat, M.; Ali, R.L.; Gani, A. SLMAS: A Secure and Light Weight Mutual Authentication Scheme for the Smart Wheelchair. Appl. Sci. 2023, 13, 6564. https://doi.org/10.3390/app13116564
Almazroi AA, Liaqat M, Ali RL, Gani A. SLMAS: A Secure and Light Weight Mutual Authentication Scheme for the Smart Wheelchair. Applied Sciences. 2023; 13(11):6564. https://doi.org/10.3390/app13116564
Chicago/Turabian StyleAlmazroi, Abdulwahab Ali, Misbah Liaqat, Rana Liaqat Ali, and Abdullah Gani. 2023. "SLMAS: A Secure and Light Weight Mutual Authentication Scheme for the Smart Wheelchair" Applied Sciences 13, no. 11: 6564. https://doi.org/10.3390/app13116564
APA StyleAlmazroi, A. A., Liaqat, M., Ali, R. L., & Gani, A. (2023). SLMAS: A Secure and Light Weight Mutual Authentication Scheme for the Smart Wheelchair. Applied Sciences, 13(11), 6564. https://doi.org/10.3390/app13116564