New RED-Type TCP-AQM Algorithms Based on Beta Distribution Drop Functions
Abstract
1. Introduction
2. Description of the Problem and Related Works
3. Scenarios of Simulation and Metrics
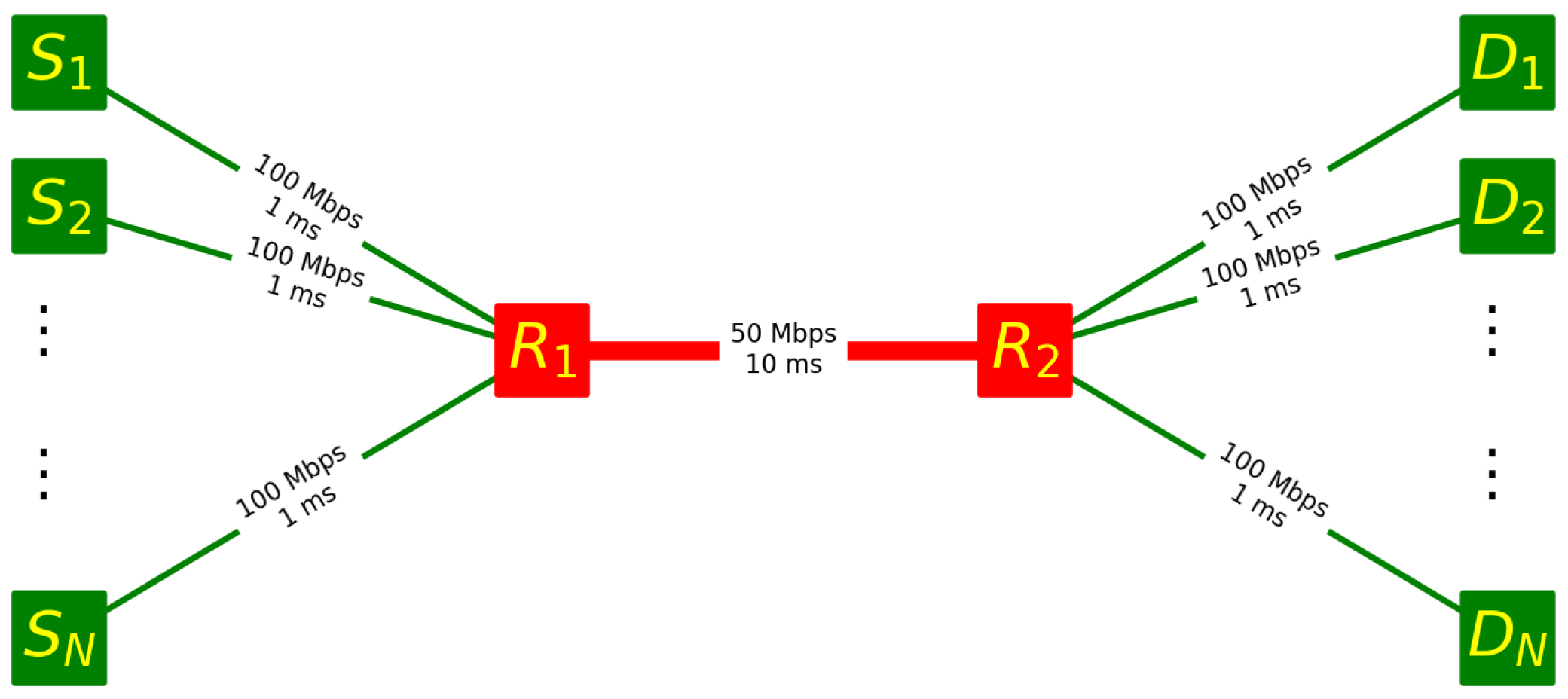
3.1. Scenarios of Simulation
- Scenario 1:
- Constant congestion level. In this case the number N of active flows is constant throughout the simulation time, which is of 250 s.
- Scenario 2:
- Changing congestion level. In this case the number N of active flows varies as a function of time according to the following distribution:
- Between 0 and 50 s, the number of active flows is .
- Between 50 and 100 s, the number of active flows is .
- Between 100 and 150 s, the number of active flows is .
- Between 150 and 200 s, the number of active flows is .
- Between 200 and 250 s, the number of active flows is .
3.2. Performance Metrics
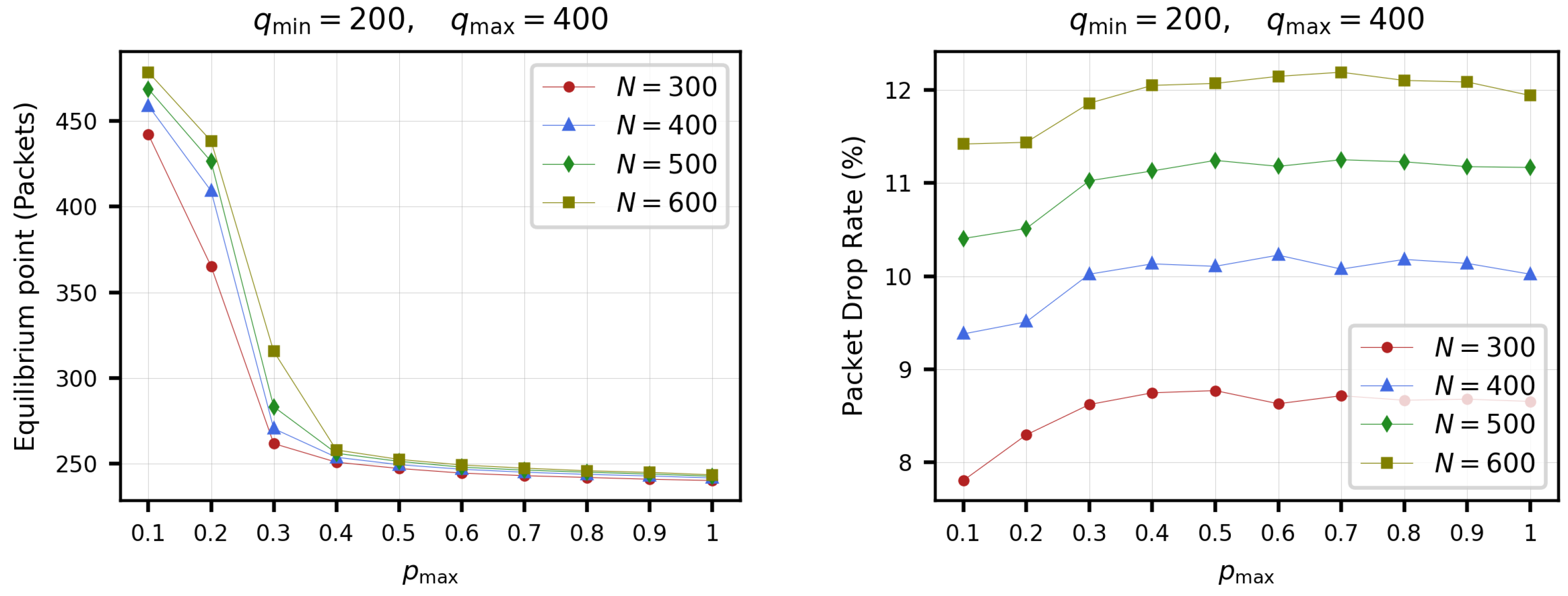
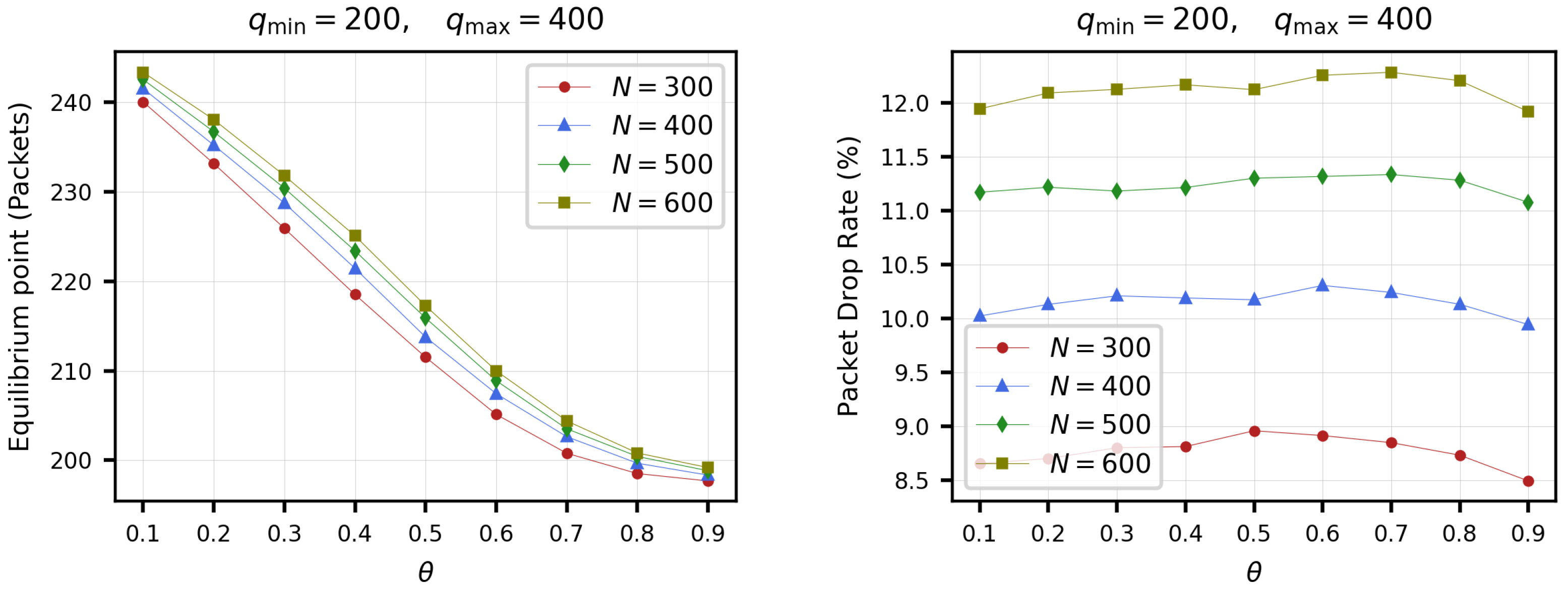
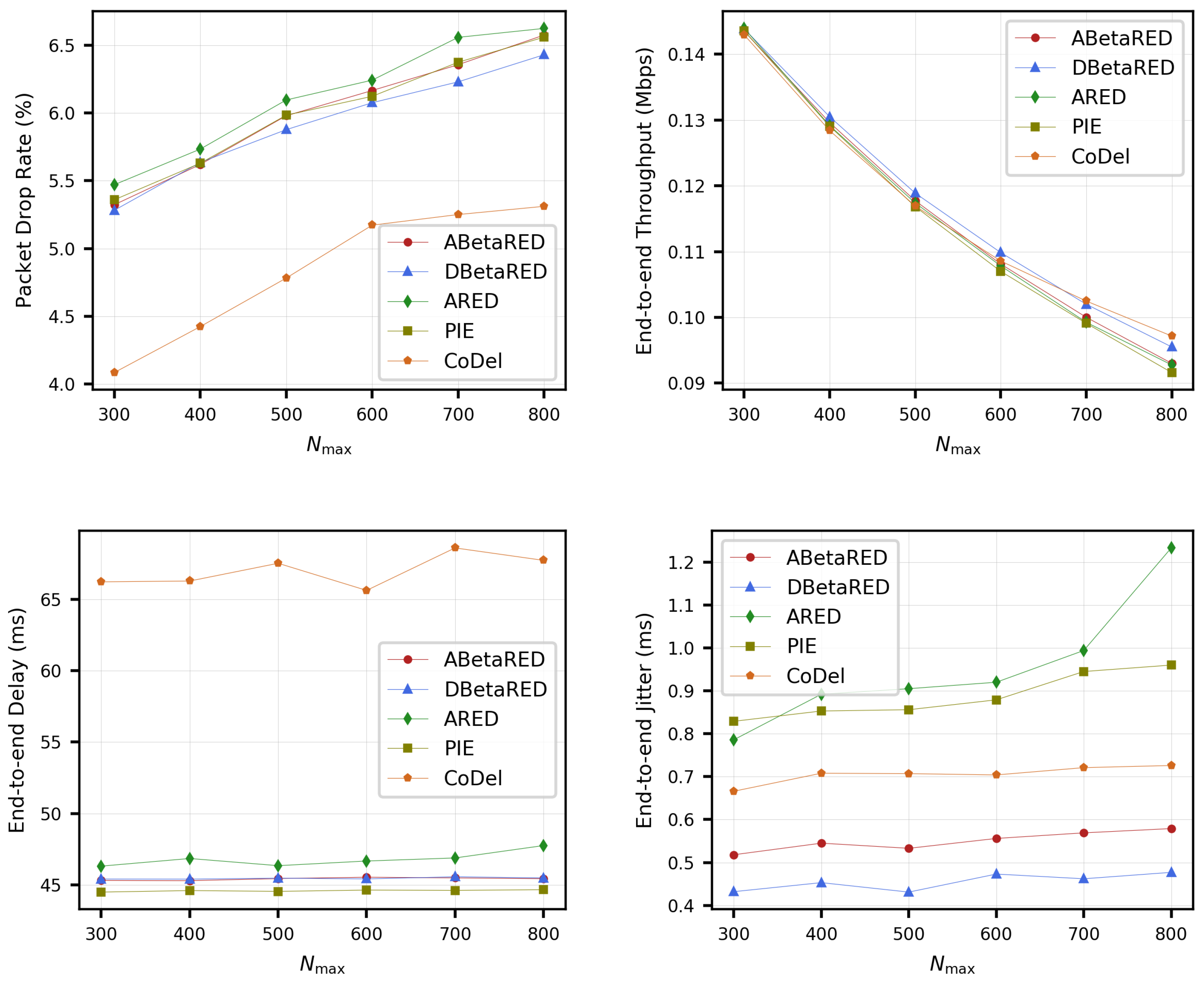
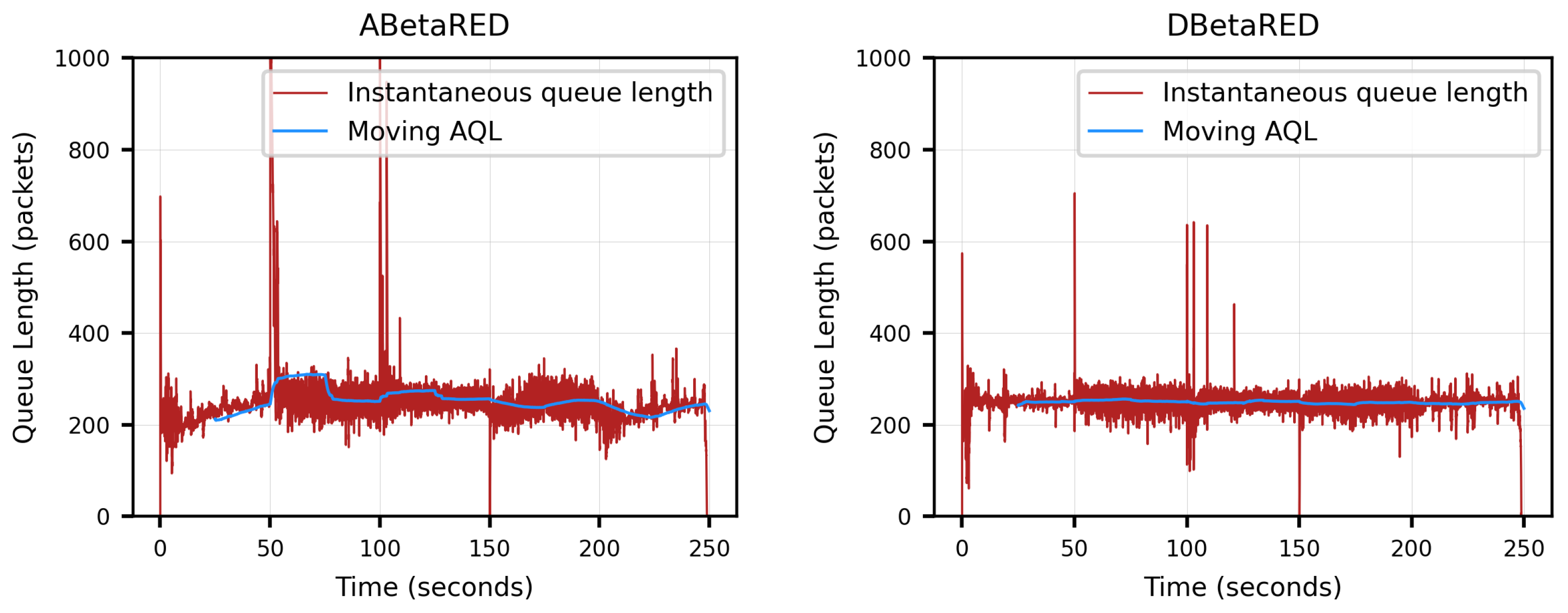
- Average queue length (AQL). The queue size indicates the number of packets pending transmission in the buffer queue. An unstable system is usually characterized by a synchronization in the TCP queues, accompanied by strong oscillations.Under suitable settings, the average queue length tends to stabilize at a value that we refer to as the equilibrium point. One of the main objectives of AQM algorithms is to stabilize the buffer queue size and, in this sense, we shall refer to the stability of an AQM algorithm as the ability to maintain the average queue length (or the average queuing delay) around a certain target value. The stability is an important performance characteristic of TCP/IP networks.
- The packet drop rate. It measures the ratio of the number of packets dropped by an AQM to the total number of packets in queue. In this count, packets dropped by the link or channel at the physical layer are not counted, considering only the drop rate at the network layer. The main objective of an AQM is to maintain a stable queue size with as low packet drop rate as possible. This increases the performance, since dropped packets are an early signal of congestion to the TCP, causing a decrease in its send rate.
- End-to-end throughput. This is a performance measure obtained between two interlocutors (server–host). It measures the actual transmission of the total data propagated with respect to the simulation time (from the time the data is sent to the time it is received). It is defined as the number of bits received correctly per unit of time. Specifically, the calculation of this metric is obtained from the ratio between the number of bits received by the server/host and the time elapsed between the reception of the first segment and the last one. To calculate the throughput in the dumbbell type topology, we have averaged the ratio between the number of bits received by the left and right hosts, and the sum of elapsed time between the reception of the first segment and the last one at each of these nodes.
- End-to-end delay (latency). It is one of the most significant metrics in a communication system and, in general terms, it is the time required to transmit a segment along its entire length, end-to-end. Specifically, it is calculated using the equation:For its calculation in the dumbbell topology, the end-to-end delay times of all the segments sent between the left and right hosts are summed, divided by the number of segments received on both hosts.
- Jitter. Jitter in a flow is defined as the variation in delay of arriving packets over time. A very high jitter can cause packet loss due to buffer overflow. In the dumbbell topology, an average value is calculated by summing the time variations between the correlative packets of all flows, and dividing by the number of variations.
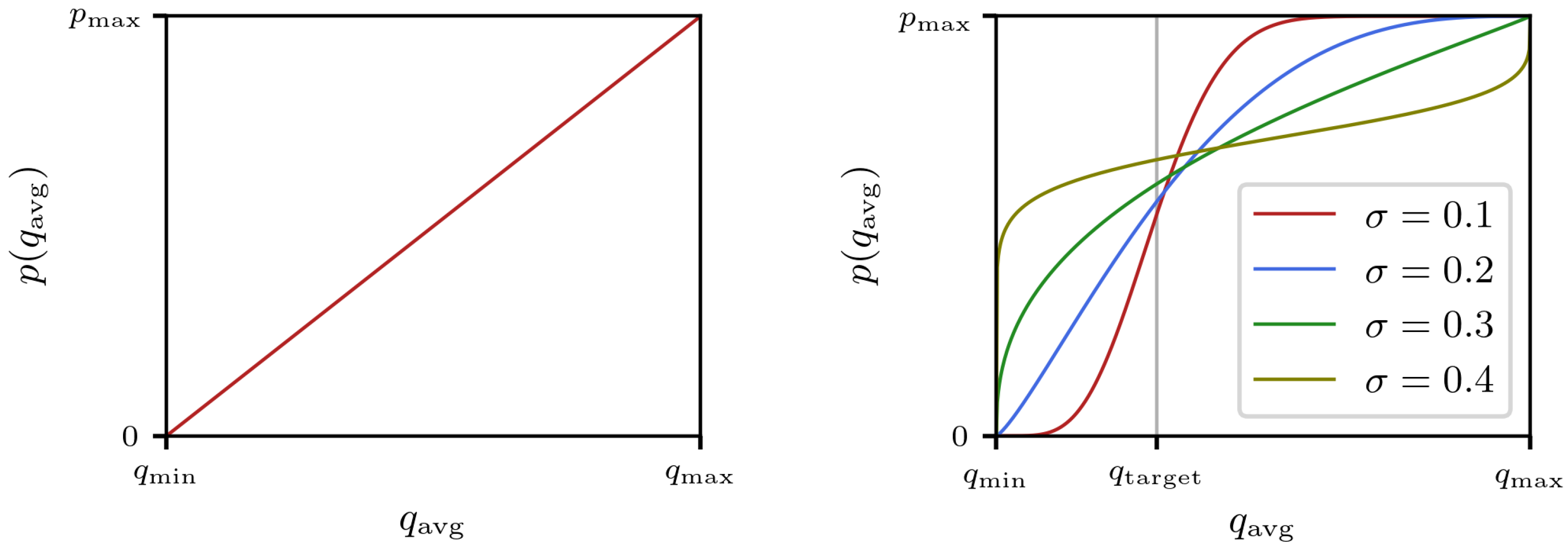
4. The Beta RED Scheme
4.1. Normalized Incomplete Beta Function
4.2. Beta RED Algorithm
| Algorithm 1 Pseudo-code outline for the Beta RED algorithm |
 |
4.3. Simulations for the BetaRED Algorithm
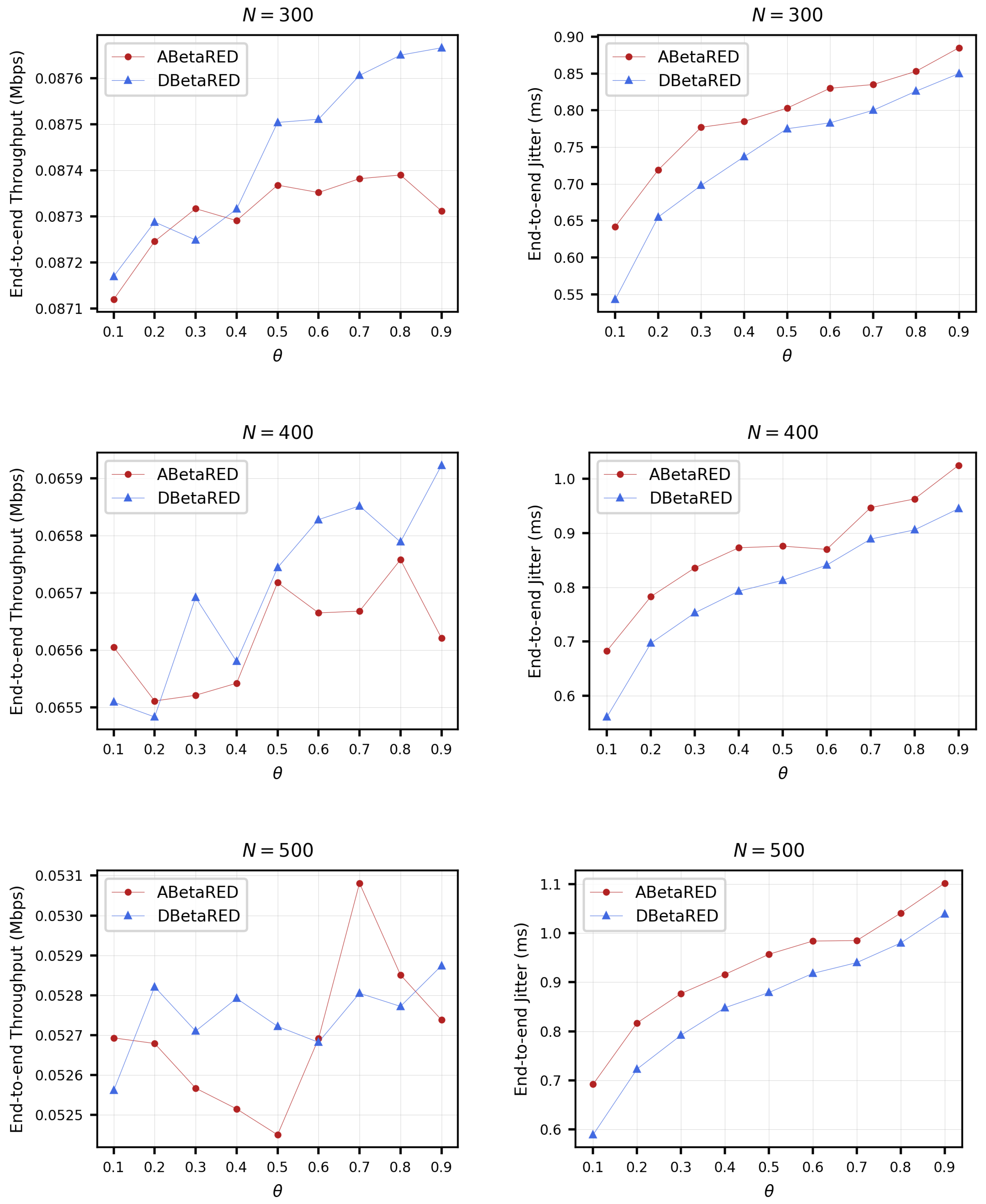
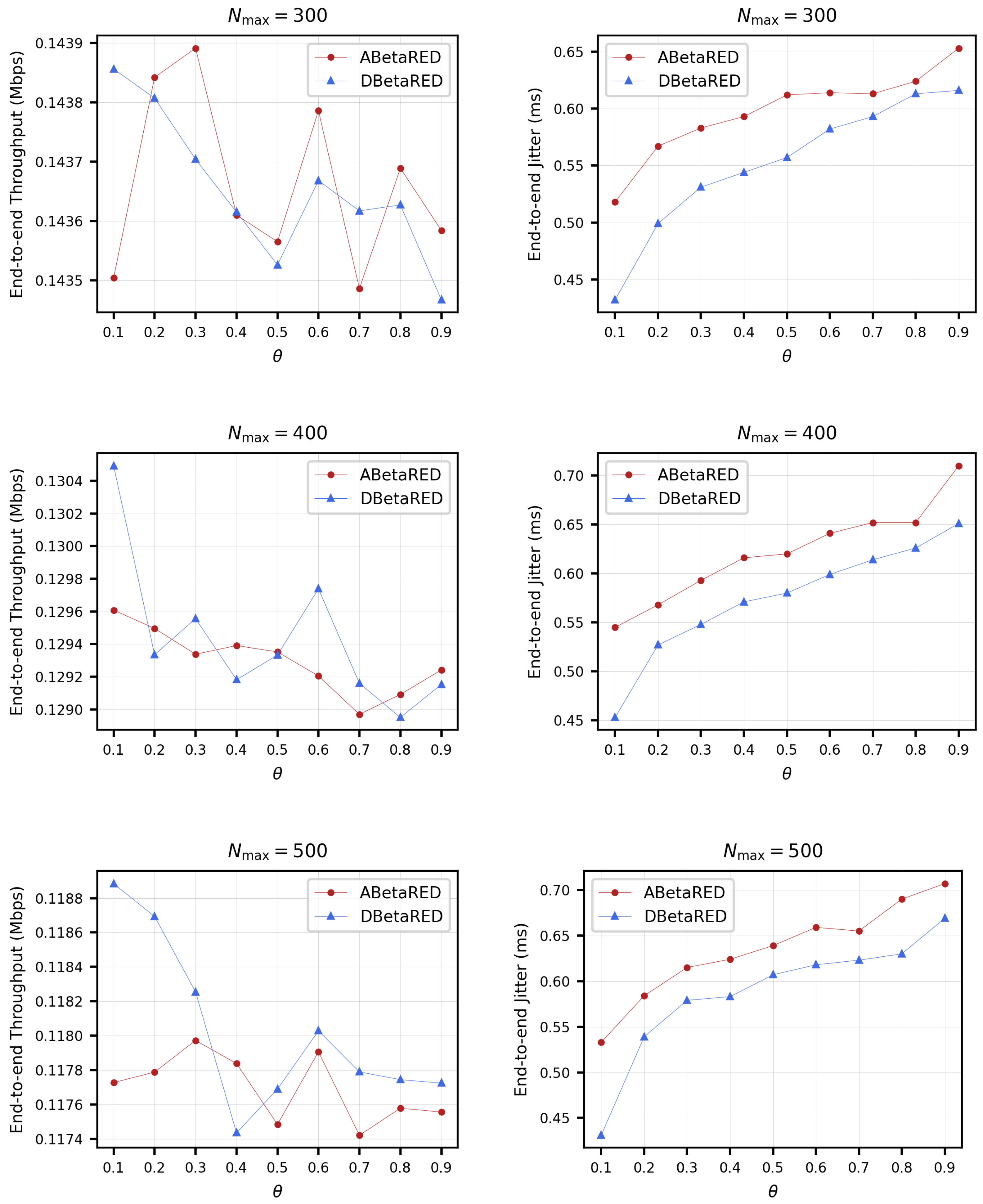
5. Dynamic Algorithms Based on BetaRED
5.1. The Adaptative Beta RED Algorithm (ABetaRED)
| Algorithm 2 Pseudo-code outline for the Adaptative Beta RED algorithm. By default, and , were set in all simulations |
 |
5.2. The Dynamic Beta RED Algorithm (DBetaRED)
| Algorithm 3 Pseudo-code outline for the Dynamic Beta RED algorithm. By default, and , were set in all simulations |
 |
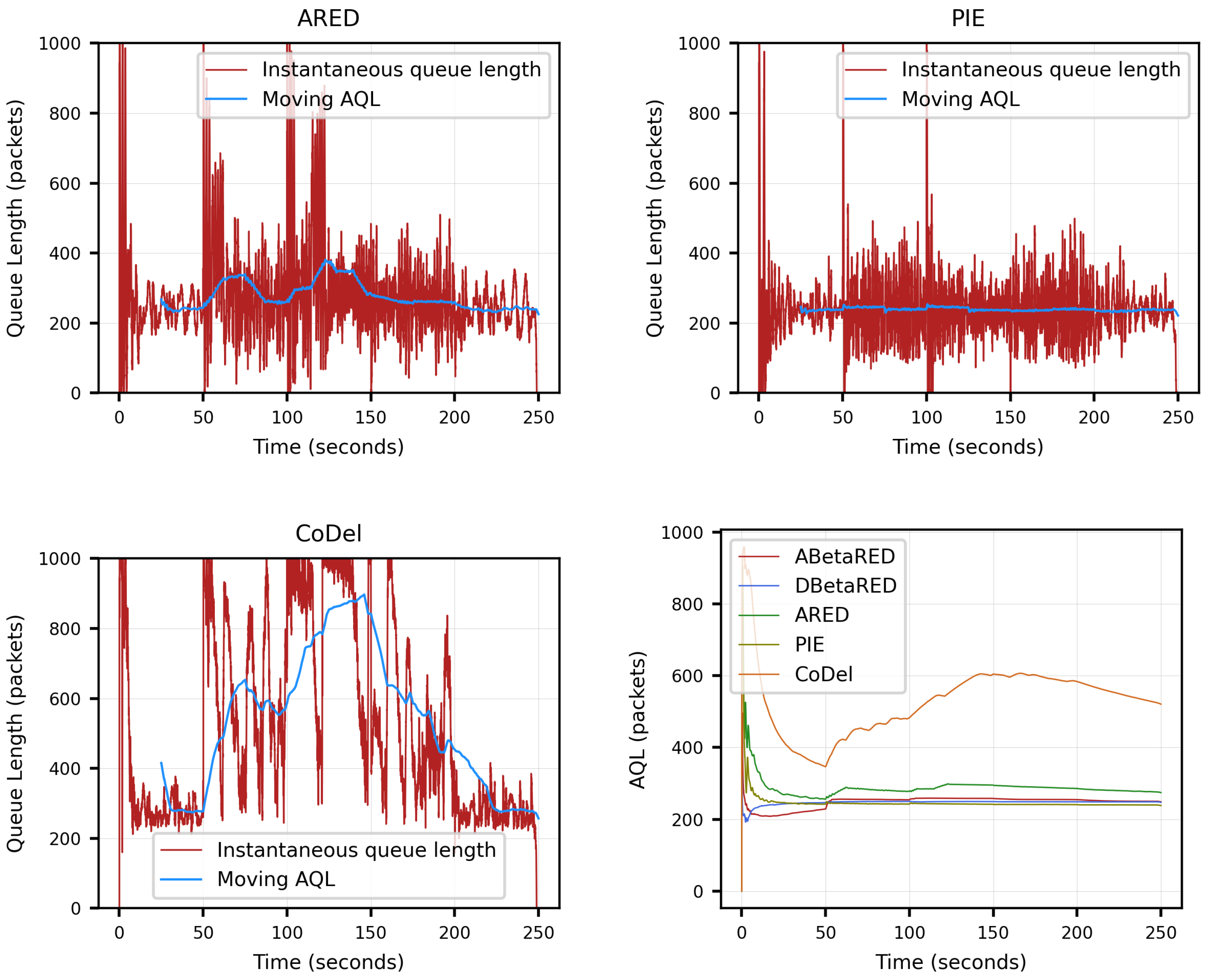
5.3. Simulations
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gettys, J. Bufferbloat: Dark Buffers in the Internet. IEEE Internet Comput. 2011, 15, 96. [Google Scholar] [CrossRef]
- Al-Saadi, R.; Armitage, G.; But, J.; Branch, P. A Survey of Delay-Based and Hybrid TCP Congestion Control Algorithms. IEEE Commun. Surv. Tuts. 2019, 21, 3609–3638. [Google Scholar] [CrossRef]
- Polese, M.; Chiariotti, F.; Bonetto, E.; Rigotto, F.; Zanella, A.; Zorzi, M. A Survey on Recent Advances in Transport Layer Protocols. IEEE Commun. Surv. Tuts. 2019, 21, 3584–3608. [Google Scholar] [CrossRef]
- Floyd, S.; Jacobson, V. Random early detection gateways for congestion avoidance. IEEE/ACM Trans. Netw. 1993, 1, 397–413. [Google Scholar] [CrossRef]
- Shorten, R.; King, C.; Wirth, F.; Leith, D. Modelling TCP congestion control dynamics in drop-tail environments. Automatica 2007, 43, 441–449. [Google Scholar] [CrossRef]
- Chen, L.; Wang, X.; Han, Z. Controlling chaos in Internet congestion control model. Chaos Solitons Fractals 2004, 21, 81–91. [Google Scholar] [CrossRef]
- Liu, F.; Guan, Z.H.; Wang, H.O. Controlling bifurcations and chaos in TCP–UDP–RED. Nonlinear Anal. Real World Appl. 2010, 11, 1491–1501. [Google Scholar] [CrossRef]
- Xiao, M.; Zheng, W.X.; Cao, J. Bifurcation control of a congestion model via state feedback. Int. J. Bifurc. Chaos 2013, 23, 1330018. [Google Scholar] [CrossRef]
- Zhang, S.; Xu, J.; Chung, K.w. On the stability and multi-stability of a TCP/RED congestion control model with state-dependent delay and discontinuous marking function. Commun. Nonlinear Sci. Numer. Simul. 2015, 22, 269–284. [Google Scholar] [CrossRef]
- Pei, L.; Wang, S. Dynamics and the periodic solutions of the delayed non-smooth Internet TCP-RED congestion control system via HB–AFT. Appl. Math. Comput. 2019, 361, 689–702. [Google Scholar] [CrossRef]
- Duran, G.; Valero, J.; Amigó, J.M.; Giménez, A.; Martinez Bonastre, O. Bifurcation analysis for the Internet congestion. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 1073–1074. [Google Scholar] [CrossRef]
- M. Amigó, J.; Duran, G.; Giménez, A.; Martínez-Bonastre, O.; Valero, J. Generalized TCP-RED dynamical model for Internet congestion control. Commun. Nonlinear Sci. Numer. Simul. 2020, 82, 105075. [Google Scholar] [CrossRef]
- Amigó, J.M.; Duran, G.; Giménez, A.; Valero, J.; Martinez Bonastre, O. Modeling a New AQM Model for Internet Chaotic Behavior Using Petri Nets. Appl. Sci. 2021, 11, 5877. [Google Scholar] [CrossRef]
- Pei, L.; Wu, F. Periodic solutions, chaos and bi-stability in the state-dependent delayed homogeneous Additive Increase and Multiplicative Decrease/Random Early Detection congestion control systems. Math. Comput. Simul. 2021, 182, 871–887. [Google Scholar] [CrossRef]
- Adams, R. Active Queue Management: A Survey. IEEE Commun. Surv. Tuts. 2013, 15, 1425–1476. [Google Scholar] [CrossRef]
- Brandauer, C.; Iannaccone, G.; Diot, C.; Ziegler, T.; Fdida, S.; May, M. Comparison of tail drop and active queue management performance for bulk-data and Web-like Internet traffic. In Proceedings of the Sixth IEEE Symposium on Computers and Communications, Hammamet, Tunisia, 5 July 2001; pp. 122–129. [Google Scholar] [CrossRef]
- Duran, G.; Valero, J.; Amigó, J.M.; Giménez, A.; Martinez Bonastre, O. Stabilizing Chaotic Behavior of RED. In Proceedings of the 2018 IEEE 26th International Conference on Network Protocols (ICNP), Cambridge, UK, 25–27 September 2018; pp. 241–242. [Google Scholar] [CrossRef]
- Amigó, J.M.; Giménez, A.; Martinez Bonastre, O.; Valero, J. Internet congestion control: From stochastic to dynamical models. Stochastics Dyn. 2021, 21, 2140009. [Google Scholar] [CrossRef]
- Feng, C.W.; Huang, L.F.; Xu, C.; Chang, Y.C. Congestion Control Scheme Performance Analysis Based on Nonlinear RED. IEEE Syst. J. 2017, 11, 2247–2254. [Google Scholar] [CrossRef]
- Adamu, A.; Shorgin, V.; Melnikov, S.; Gaidamaka, Y. Flexible Random Early Detection Algorithm for Queue Management in Routers. In Distributed Computer and Communication Networks; Vishnevskiy, V.M., Samouylov, K.E., Kozyrev, D.V., Eds.; Springer International Publishing: Cham, Switzerland, 2020; Volume 12563, pp. 196–208. [Google Scholar] [CrossRef]
- Patel, S.; Karmeshu. A New Modified Dropping Function for Congested AQM Networks. Wirel. Pers. Commun. 2019, 104, 37–55. [Google Scholar] [CrossRef]
- Xiong, N.; Yang, L.; Yang, Y.; Défago, X.; He, Y. A novel numerical algorithm based on self-tuning controller to support TCP flows. Math. Comput. Simul. 2008, 79, 1178–1188. [Google Scholar] [CrossRef]
- Bhatnagar, S.; Patel, S.; Karmeshu. A stochastic approximation approach to active queue management. Telecommun. Syst. 2018, 68, 89–104. [Google Scholar] [CrossRef]
- Sharma, N.; Rajput, S.S.; Dwivedi, A.K.; Shrimali, M. P-RED: Probability Based Random Early Detection Algorithm for Queue Management in MANET. In Advances in Computer and Computational Sciences; Bhatia, S.K., Mishra, K.K., Tiwari, S., Singh, V.K., Eds.; Springer: Singapore, 2018; pp. 637–643. [Google Scholar] [CrossRef]
- Abu-Shareha, A.A. Enhanced Random Early Detection using Responsive Congestion Indicators. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef]
- Baklizi, M. Weight Queue Dynamic Active Queue Management Algorithm. Symmetry 2020, 12, 2077. [Google Scholar] [CrossRef]
- Feng, W.C.; Kandlur, D.; Saha, D.; Shin, K. A self-configuring RED gateway. In Proceedings of the IEEE INFOCOM ’99. Conference on Computer Communications, Eighteenth Annual Joint Conference of the IEEE Computer and Communications Societies. The Future is Now (Cat. No. 99CH36320), New York, NY, USA, 21–25 March 1999; Volume 3, pp. 1320–1328, ISSN 0743-166X. [Google Scholar] [CrossRef]
- Floyd, S.; Gummadi, R.; Shenker, S. Adaptive RED: An Algorithm for Increasing the Robustness of RED’s Active Queue Management; Technical Report. 2001. Available online: http://www.icir.org/floyd/papers/adaptiveRed.pdf (accessed on 24 July 2021).
- Nichols, K.; Jacobson, V. Controlling queue delay. Commun. ACM 2012, 55, 42–50. [Google Scholar] [CrossRef]
- Nichols, K.; Jacobson, V.; McGregor, E.A.; Iyengar, E.J. Controlled Delay Active Queue Management; RFC 8289; Controlled Delay Active Queue Management. 2018. Available online: https://www.rfc-editor.org/info/rfc8289 (accessed on 24 July 2021).
- Pan, R.; Natarajan, P.; Piglione, C.; Prabhu, M.S.; Subramanian, V.; Baker, F.; VerSteeg, B. PIE: A lightweight control scheme to address the bufferbloat problem. In Proceedings of the 2013 IEEE 14th International Conference on High Performance Switching and Routing (HPSR), Taipei, Taiwan, 8–11 July 2013; pp. 148–155, ISSN 2325-5560. [Google Scholar] [CrossRef]
- Schwarzkopf, F.; Veith, S.; Menth, M. Performance Analysis of CoDel and PIE for Saturated TCP Sources. In Proceedings of the 2016 28th International Teletraffic Congress (ITC 28), Würzburg, Germany, 12–16 September 2016; pp. 175–183. [Google Scholar] [CrossRef]
- Pan, R.; Natarajan, P.; Baker, F.; White, G. Proportional Integral Controller Enhanced (PIE): A Lightweight Control Scheme to Address the Bufferbloat Problem; Technical Report RFC8033; RFC Editor. 2017. Available online: https://www.rfc-editor.org/info/rfc8033 (accessed on 24 July 2021).
- Hollot, C.; Misra, V.; Towsley, D.; Gong, W.-B. On designing improved controllers for AQM routers supporting TCP flows. In Proceedings of the IEEE INFOCOM 2001, Conference on Computer Communications, Twentieth Annual Joint Conference of the IEEE Computer and Communications Society (Cat. No. 01CH37213), Anchorage, AK, USA, 22–26 April 2001; Volume 3, pp. 1726–1734. [Google Scholar] [CrossRef]
- Kuhn, N.; Ros, D.; Bagayoko, A.B.; Kulatunga, C.; Fairhurst, G.; Khademi, N. Operating ranges, tunability and performance of CoDel and PIE. Comput. Commun. 2017, 103, 74–82. [Google Scholar] [CrossRef]
- Baker, E.F.; Fairhurst, E.G. IETF Recommendations Regarding Active Queue Management. 2015. Available online: https://www.rfc-editor.org/info/rfc7567 (accessed on 24 July 2021).
- nsnam. Network Simulator 3. 2011. Available online: https://www.nsnam.org/ (accessed on 24 July 2021).
- Ranjan, P.; Abed, E.H.; La, R.J. Nonlinear Instabilities in TCP-RED. IEEE/ACM Trans. Netw. 2004, 12, 1079–1092. [Google Scholar] [CrossRef]
- Grazia, C.A.; Patriciello, N.; Klapez, M.; Casoni, M. A cross-comparison between TCP and AQM algorithms: Which is the best couple for congestion control? In Proceedings of the 2017 14th International Conference on Telecommunications (ConTEL), Zagreb, Croatia, 28–30 June 2017; pp. 75–82. [Google Scholar] [CrossRef]



| AQM Algorithm | Name | Description | |
|---|---|---|---|
| Tunable parameters | ABetaRED, DBetaRED, ARED, CoDel, PIE | Target delay | |
| Update interval time | |||
| Alpha, Beta | Control parameters with different objectives according to the AQM. | ||
| BetaRED, ABetaRED, DBetaRED | Scale factor determining the standard deviation of the drop probability function | ||
| w | Averaging weight | ||
| BetaRED | Target queue length | ||
| Lower threshold | |||
| Upper threshold | |||
| Maximum packet drop probability | |||
| System parameters | All | B | Buffer size (maximum number of packets that the buffer of Router 1 can store) |
| C | Capacity of the channel (the maximum amount of error-free information that can be transmitted over the channel per unit time) | ||
| N | Number of flows in the dumbbell topology | ||
| M | Packet size | ||
| Variables | All | p | Drop probability |
| Current queue length at Router 1 | |||
| Average queue length at Router 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Giménez, A.; Murcia, M.A.; Amigó, J.M.; Martínez-Bonastre, O.; Valero, J. New RED-Type TCP-AQM Algorithms Based on Beta Distribution Drop Functions. Appl. Sci. 2022, 12, 11176. https://doi.org/10.3390/app122111176
Giménez A, Murcia MA, Amigó JM, Martínez-Bonastre O, Valero J. New RED-Type TCP-AQM Algorithms Based on Beta Distribution Drop Functions. Applied Sciences. 2022; 12(21):11176. https://doi.org/10.3390/app122111176
Chicago/Turabian StyleGiménez, Angel, Miguel A. Murcia, José M. Amigó, Oscar Martínez-Bonastre, and José Valero. 2022. "New RED-Type TCP-AQM Algorithms Based on Beta Distribution Drop Functions" Applied Sciences 12, no. 21: 11176. https://doi.org/10.3390/app122111176
APA StyleGiménez, A., Murcia, M. A., Amigó, J. M., Martínez-Bonastre, O., & Valero, J. (2022). New RED-Type TCP-AQM Algorithms Based on Beta Distribution Drop Functions. Applied Sciences, 12(21), 11176. https://doi.org/10.3390/app122111176









