Observer-Based Active Control Strategy for Networked Switched Systems against Two-Channel Asynchronous DoS Attacks
Abstract
:1. Introduction
- An observer-based active control strategy is proposed for networked switched systems, which exhibits resilience and robustness against two-channel asynchronous DoS attacks and asynchronous switching behaviors. In addition, the buffer size design approach is proposed.
- The switching signals are designed to ensure the ISS of the networked switched systems under active control strategy against two-channel asynchronous DoS attacks and asynchronous switching behaviors, specifically, the quantitative relationship between the frequency and duration of two-channel DoS attacks and the switching frequency is revealed under ISS conditions. The results can be degraded to the non-switched system case.
- Unlike [26,37,38,43] that only consider the case of full-state measurements, the case of partial-state measurements is studied, and a mode-dependent finite-time observer is designed to rapidly and accurately estimate the system state. In addition, external disturbances are also considered in our work.
- In the existing methods [37,38,43], the effectiveness of active control strategies often relies on assuming that the DoS signals adhere to specific patterns. However, in our work, the effectiveness of the active control strategy is only related to the frequency and duration of DoS attacks, without making any assumptions about specific patterns for DoS attacks, which is more general and challenging.
2. Problem Statement and Preliminaries
2.1. Networked Switched Linear System
2.2. Two-Channel Asynchronous DoS Attacks
2.3. Control Objective
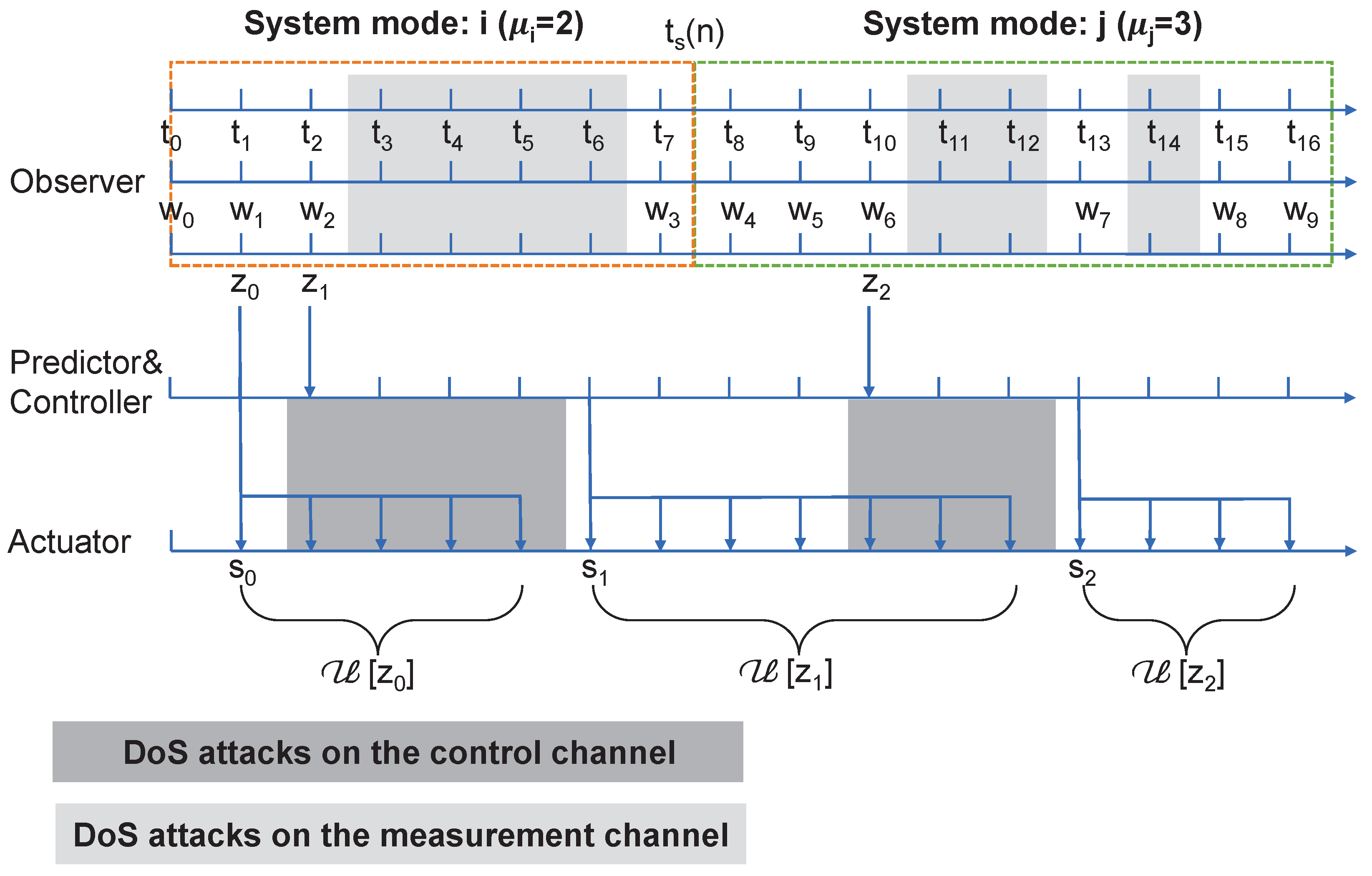
3. Observer-Based Active Control Strategy
3.1. Mode-Dependent Finite-Time Observer Design
3.2. Active Control Strategy
- Step 1: The observer resets the estimate of the system state when it receives consecutive measurement signals with the same mode i from the sensor, and then sends it to the predictor.
- Step 2: Based on the estimate , the system’s mode and the actual control signals, the predictor predicts the system state and the controller generate the control sequence and transmit it to the buffer at by using one data packet.
- Step 3: The buffer discards the outdated control signals and sequentially sends the control signals to the actuator, one by one, at each sampling instant. The actuator holds the control signal until the next sampling instant. Return to Step 1.
3.3. Buffer Size Design
4. Input-to-State Stability Analysis
4.1. Dynamics under Two-Channel DoS Attacks without Asynchronous Switching
4.2. Dynamics under Two-Channel DoS Attacks with Asynchronous Switching
4.3. Input-to-State Stability Analysis
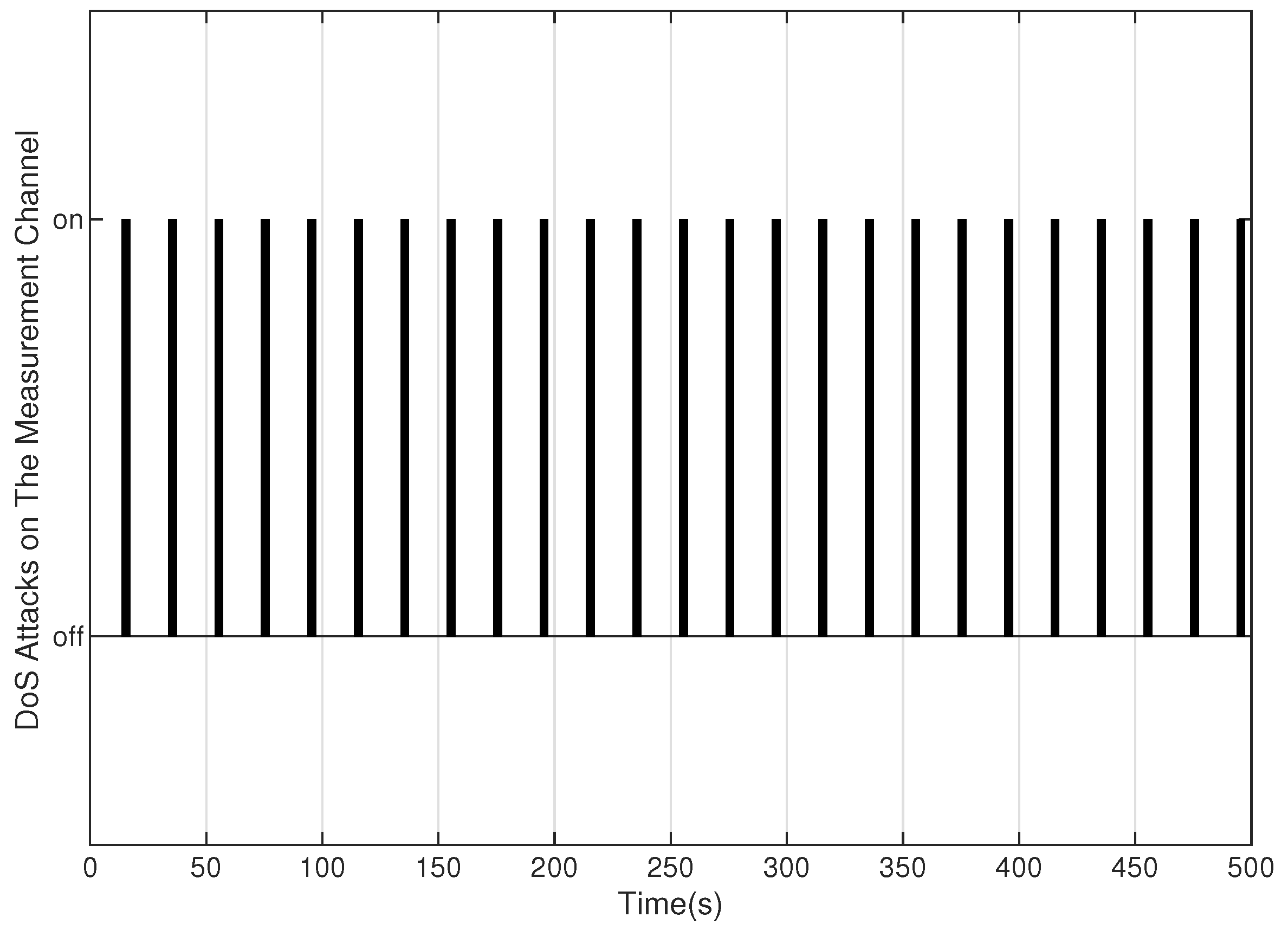
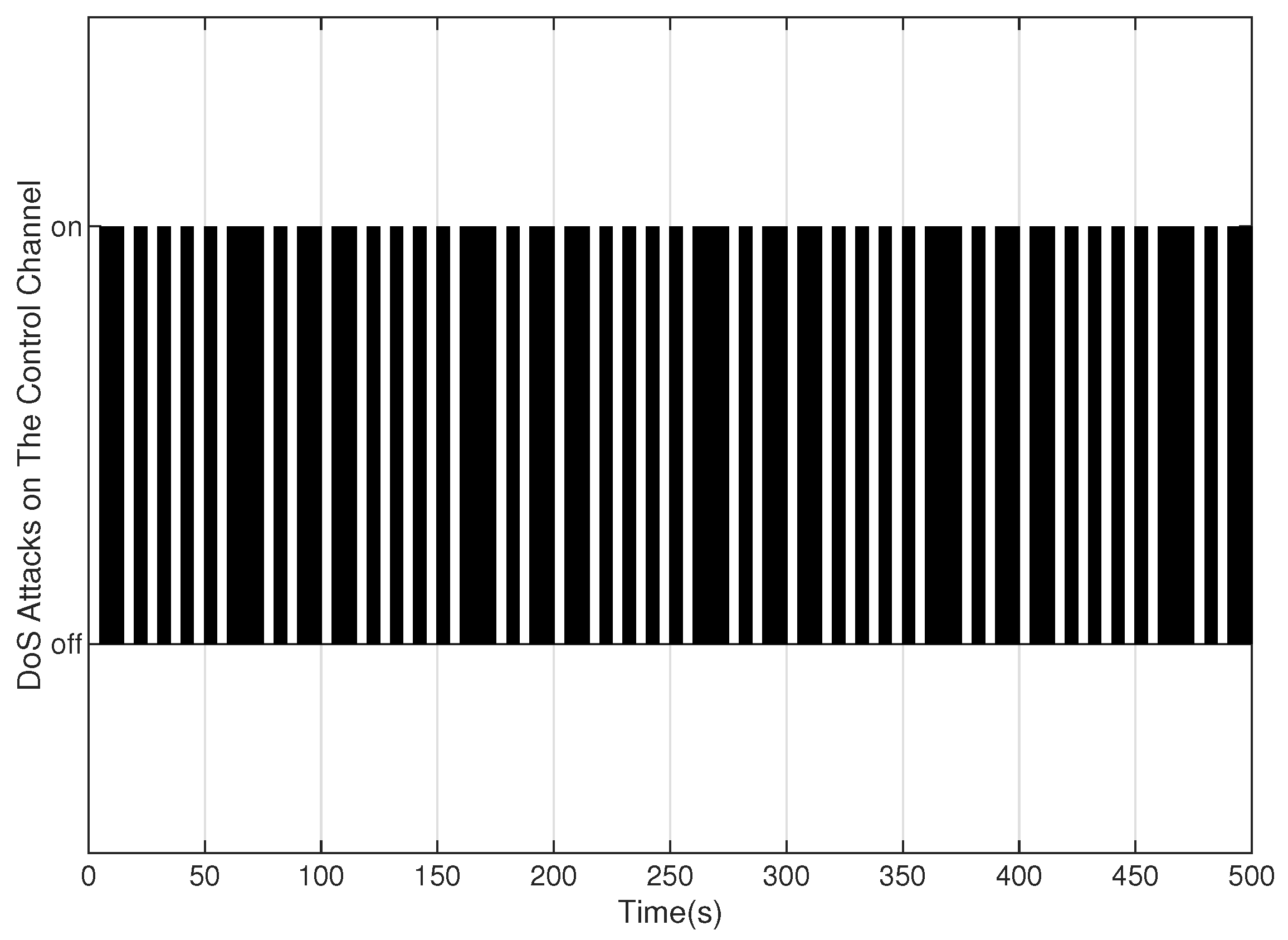
5. Numerical Example
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
References
- Lee, E.A. Cyber physical systems: Design challenges. In Proceedings of the 2008 11th IEEE International Symposium on Object and Component-Oriented Real-Time Distributed Computing (ISORC), Orlando, FL, USA,, 5–7 May 2008. [Google Scholar]
- Sha, L.; Gopalakrishnan, S.; Liu, X.; Wang, Q. Cyber-physical systems: A new frontier. In Proceedings of the 2008 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC 2008), Taichung, Taiwan, 11–13 June 2008; pp. 1–9. [Google Scholar]
- Farraj, A.; Hammad, E.; Kundur, D. A cyber-physical control framework for transient stability in smart grids. IEEE Trans. Smart Grid 2016, 9, 1205–1215. [Google Scholar] [CrossRef]
- Peng, C.; Sun, H.; Yang, M.; Wang, Y.L. A survey on security communication and control for smart grids under malicious cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1554–1569. [Google Scholar] [CrossRef]
- Liu, X.; Li, L.; Li, Z.; Chen, X.; Fernando, T.; Iu, H.H.C.; He, G. Event-trigger particle filter for smart grids with limited communication bandwidth infrastructure. IEEE Trans. Smart Grid 2017, 9, 6918–6928. [Google Scholar] [CrossRef]
- Hu, F.; Lu, Y.; Vasilakos, A.V.; Hao, Q.; Ma, R.; Patil, Y.; Zhang, T.; Lu, J.; Li, X.; Xiong, N.N. Robust cyber–physical systems: Concept, models, and implementation. Future Gener. Comput. Syst. 2016, 56, 449–475. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. False data injection attacks against state estimation without knowledge of estimators. IEEE Trans. Autom. Control 2022, 67, 4529–4540. [Google Scholar] [CrossRef]
- Horak, T.; Cervenanska, Z.; Huraj, L.; Vazan, P.; Janosik, J.; Tanuska, P. The vulnerability of securing IoT production lines and their network components in the Industry 4.0 concept. IFAC-PapersOnLine 2020, 53, 11237–11242. [Google Scholar] [CrossRef]
- Mishra, A.; Joshi, B.K.; Arya, V.; Gupta, A.K.; Chui, K.T. Detection of Distributed Denial of Service (DDoS) Attacks Using Computational Intelligence and Majority Vote-Based Ensemble Approach. Int. J. Softw. Sci. Comput. Intell. (IJSSCI) 2022, 14, 1–10. [Google Scholar] [CrossRef]
- Cvitić, I.; Perakovic, D.; Gupta, B.B.; Choo, K.K.R. Boosting-based DDoS detection in internet of things systems. IEEE Internet Things J. 2021, 9, 2109–2123. [Google Scholar] [CrossRef]
- Yan, J.J.; Yang, G.H. Secure state estimation with switched compensation mechanism against DoS attacks. IEEE Trans. Cybern. 2021, 52, 9609–9620. [Google Scholar] [CrossRef]
- Li, D.; Dong, J. Fuzzy Control Based on Reinforcement Learning and Subsystem Error Derivatives for Strict-Feedback Systems with an Observer. IEEE Trans. Fuzzy Syst. 2022, 31, 2509–2521. [Google Scholar] [CrossRef]
- Jin, Z.; Zhang, S.; Hu, Y.; Zhang, Y.; Sun, C. Security State Estimation for Cyber-Physical Systems against DoS Attacks via Reinforcement Learning and Game Theory. Actuators 2022, 11, 192. [Google Scholar] [CrossRef]
- Chen, H.; Zong, G.; Zhao, X.; Gao, F.; Shi, K. Secure filter design of fuzzy switched CPSs with mismatched modes and application: A multidomain event-triggered strategy. IEEE Trans. Ind. Inform. 2023, 19, 10034–10044. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. Distributed secure state estimation for linear systems against malicious agents through sorting and filtering. Automatica 2023, 151, 110927. [Google Scholar] [CrossRef]
- Persis, C.D.; Tesi, P. Input-to-State Stabilizing Control Under Denial-of-Service. IEEE Trans. Autom. Control 2015, 60, 2930–2944. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. Stability analysis for cyber-physical systems under denial-of-service attacks. IEEE Trans. Cybern. 2020, 51, 5304–5313. [Google Scholar] [CrossRef]
- Li, Z.; Zhou, C.; Che, W.; Deng, C.; Jin, X. Data-Based Security Fault Tolerant Iterative Learning Control under Denial-of-Service Attacks. Actuators 2022, 11, 178. [Google Scholar] [CrossRef]
- Chen, H.; Zong, G.; Gao, F.; Shi, Y. Probabilistic event-triggered policy for extended dissipative finite-time control of MJSs under cyber-attacks and actuator failures. IEEE Trans. Autom. Control, 2023; early access. [Google Scholar] [CrossRef]
- Feng, S.; Tesi, P. Resilient control under denial-of-service: Robust design. Automatica 2017, 79, 42–51. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. Detection and identification of sparse sensor attacks in cyber physical systems with side information. IEEE Trans. Autom. Control, 2022; early access. [Google Scholar] [CrossRef]
- Li, X.J.; Shen, X.Y. A data-driven attack detection approach for DC servo motor systems based on mixed optimization strategy. IEEE Trans. Ind. Inform. 2019, 16, 5806–5813. [Google Scholar] [CrossRef]
- Guo, L.; Yu, H.; Hao, F. Event-triggered control for stochastic networked control systems against denial-of-service attacks. Inf. Sci. 2020, 527, 51–69. [Google Scholar] [CrossRef]
- Shisheh Foroush, H.; Martínez, S. On triggering control of single-input linear systems under pulse-width modulated DoS signals. SIAM J. Control Optim. 2016, 54, 3084–3105. [Google Scholar] [CrossRef]
- Fu, J.; Qi, Y.; Xing, N.; Li, Y. A new switching law for event-triggered switched systems under DoS attacks. Automatica 2022, 142, 110373. [Google Scholar] [CrossRef]
- Hu, S.; Yue, D.; Chen, X.; Cheng, Z.; Xie, X. Resilient H∞ filtering for event-triggered networked systems under nonperiodic DoS jamming attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 51, 1392–1403. [Google Scholar] [CrossRef]
- Zhang, X.M.; Han, Q.L.; Ge, X.; Ding, L. Resilient control design based on a sampled-data model for a class of networked control systems under denial-of-service attacks. IEEE Trans. Cybern. 2019, 50, 3616–3626. [Google Scholar] [CrossRef]
- Zhao, N.; Shi, P.; Xing, W.; Lim, C.P. Event-triggered control for networked systems under denial of service attacks and applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 69, 811–820. [Google Scholar] [CrossRef]
- Liu, D.; Ye, D. Pinning-observer-based secure synchronization control for complex dynamical networks subject to DoS attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2020, 67, 5394–5404. [Google Scholar] [CrossRef]
- Lu, A.Y.; Yang, G.H. Input-to-state stabilizing control for cyber-physical systems with multiple transmission channels under denial of service. IEEE Trans. Autom. Control 2017, 63, 1813–1820. [Google Scholar] [CrossRef]
- Wakaiki, M.; Yamamoto, Y. Stability analysis of sampled-data switched systems with quantization. Automatica 2016, 69, 157–168. [Google Scholar] [CrossRef]
- Liberzon, D. Finite data-rate feedback stabilization of switched and hybrid linear systems. Automatica 2014, 50, 409–420. [Google Scholar] [CrossRef]
- Yang, D.; Zong, G.; Shi, Y.; Shi, P. Adaptive tracking control of hybrid switching Markovian systems with its applications. SIAM J. Control Optim. 2023, 61, 434–457. [Google Scholar] [CrossRef]
- Qu, H.; Zhao, J. Stabilisation of switched linear systems under denial of service. IET Control Theory Appl. 2020, 14, 1438–1444. [Google Scholar] [CrossRef]
- Wang, Y.W.; Zeng, Z.H.; Liu, X.K.; Liu, Z.W. Input-to-state stability of switched linear systems with unstabilizable modes under DoS attacks. Automatica 2022, 146, 110607. [Google Scholar] [CrossRef]
- Zhao, R.; Zuo, Z.; Wang, Y.; Zhang, W. Active control strategy for switched systems against asynchronous DoS attacks. Automatica 2023, 148, 110765. [Google Scholar] [CrossRef]
- Zhao, R.; Zuo, Z.; Wang, Y.; Zhang, W. Active control strategy for disturbed switched systems under asynchronous dos attacks. IEEE Control Syst. Lett. 2022, 6, 2701–2706. [Google Scholar] [CrossRef]
- Zhao, X.; Liu, H.; Zhang, J.; Li, H. Multiple-mode observer design for a class of switched linear systems. IEEE Trans. Autom. Sci. Eng. 2013, 12, 272–280. [Google Scholar] [CrossRef]
- Chen, L.; Zhu, Y.; Ahn, C.K. Adaptive neural network-based observer design for switched systems with quantized measurements. IEEE Trans. Neural Netw. Learn. Syst. 2021; early access. [Google Scholar] [CrossRef]
- Sun, Y.C.; Yang, G.H. Event-triggered resilient control for cyber-physical systems under asynchronous DoS attacks. Inf. Sci. 2018, 465, 340–352. [Google Scholar] [CrossRef]
- Hu, S.; Yue, D.; Han, Q.L.; Xie, X.; Chen, X.; Dou, C. Observer-based event-triggered control for networked linear systems subject to denial-of-service attacks. IEEE Trans. Cybern. 2019, 50, 1952–1964. [Google Scholar] [CrossRef]
- Li, T.; Chen, B.; Yu, L.; Zhang, W.A. Active security control approach against DoS attacks in cyber-physical systems. IEEE Trans. Autom. Control 2020, 66, 4303–4310. [Google Scholar] [CrossRef]
- Hespanha, J.P.; Morse, A.S. Stability of switched systems with average dwell-time. In Proceedings of the 38th IEEE conference on decision and control (Cat. No. 99CH36304), Phoenix, AZ, USA, 7–10 December 1999; Volume 3, pp. 2655–2660. [Google Scholar]
- Sontag, E.D.; Agrachev, A.A.; Morse, A.S.; Sussmann, H.J.; Utkin, V.I. Input to State Stability: Basic Concepts and Results; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- O’Reilly, J. Observers for Linear Systems; Academic Press: Cambridge, MA, USA, 1983. [Google Scholar]





Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yin, J.; Lu, A. Observer-Based Active Control Strategy for Networked Switched Systems against Two-Channel Asynchronous DoS Attacks. Actuators 2023, 12, 335. https://doi.org/10.3390/act12080335
Yin J, Lu A. Observer-Based Active Control Strategy for Networked Switched Systems against Two-Channel Asynchronous DoS Attacks. Actuators. 2023; 12(8):335. https://doi.org/10.3390/act12080335
Chicago/Turabian StyleYin, Jiayuan, and Anyang Lu. 2023. "Observer-Based Active Control Strategy for Networked Switched Systems against Two-Channel Asynchronous DoS Attacks" Actuators 12, no. 8: 335. https://doi.org/10.3390/act12080335
APA StyleYin, J., & Lu, A. (2023). Observer-Based Active Control Strategy for Networked Switched Systems against Two-Channel Asynchronous DoS Attacks. Actuators, 12(8), 335. https://doi.org/10.3390/act12080335





