Research on Secure State Estimation and Recovery Control for CPS under Stealthy Attacks
Abstract
:1. Introduction
- (1)
- For the case of attacks on a CPS containing multiple sensors, an optimal state estimation method based on improved Kalman filtering is proposed, which can achieve the estimation of the actual state of the CPS after the attack.
- (2)
- Based on the estimated optimal state, a recovery control strategy is designed. And, combined with the detection method based on improved residuals, a framework for the security defense process is given.
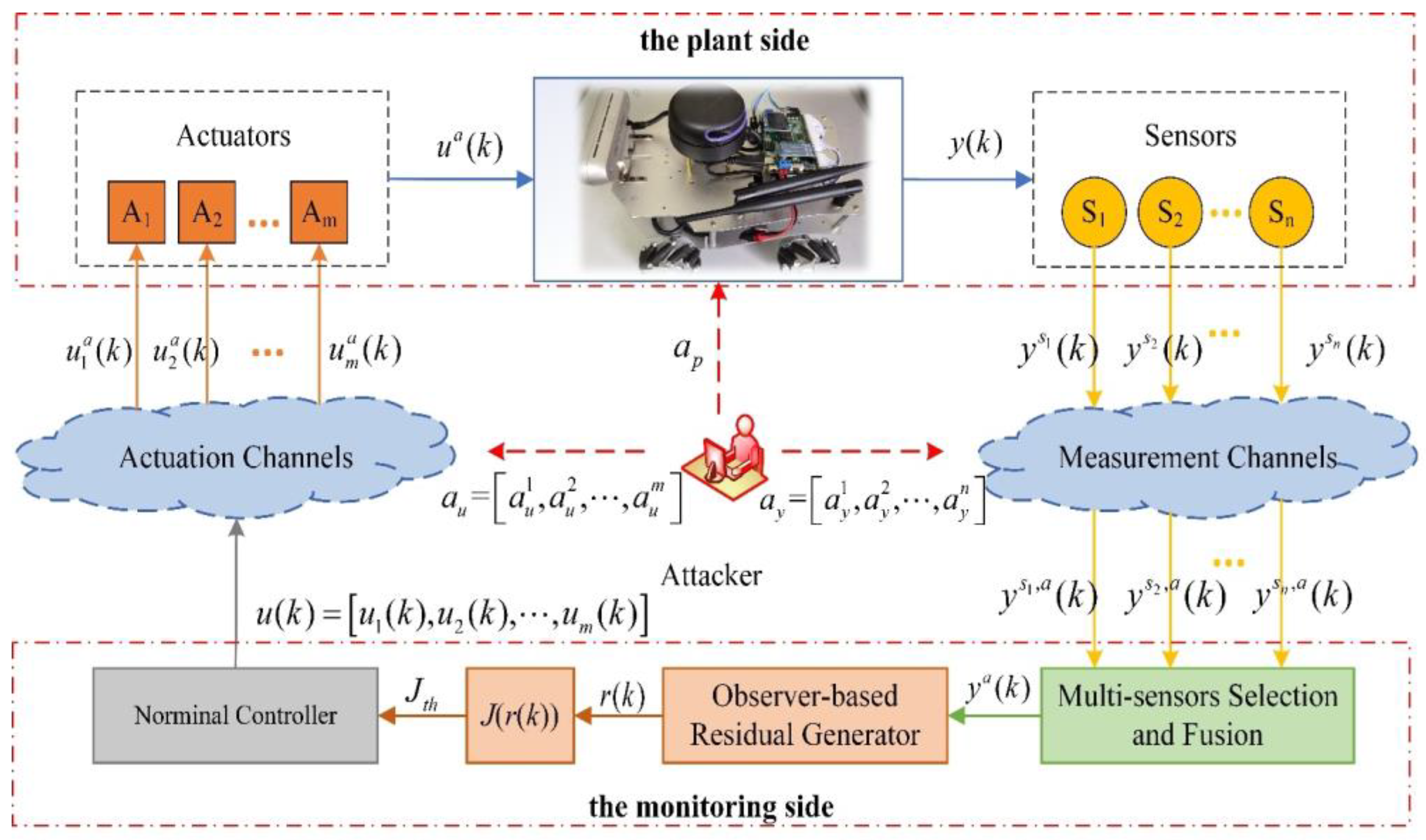
2. Model Building and Detection Methods
2.1. System Modelling
2.2. Description of Stealthy Attacks
- (1)
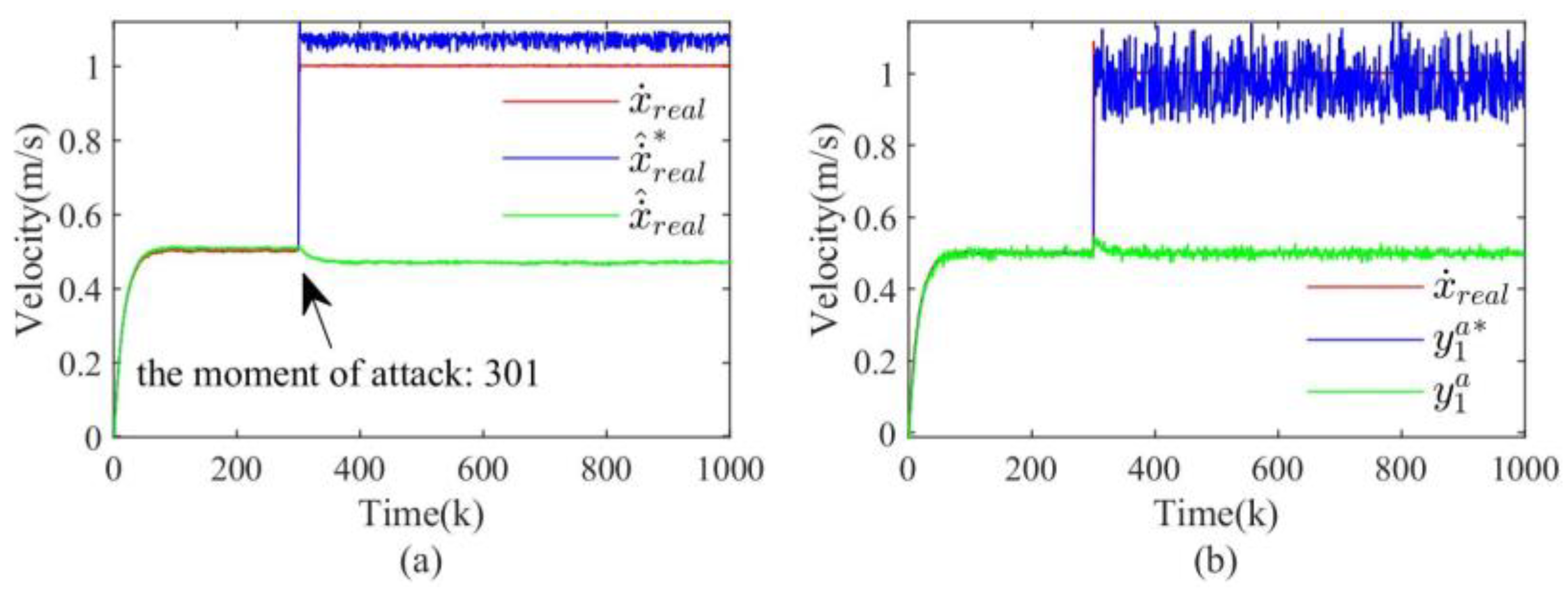
- Zero-dynamics attack: It requires complete knowledge of the system model to design attack signals against the actuators. It evades the detector of (3) by adding the attack signal to the actuator input without affecting the sensor measurement output, i.e., [32]. Therefore, the attack form can be expressed as , where the system zero and the corresponding input zero direction can be calculated by solving the following equation.where is the initial state of the system for which the input sequence results in an identically zero output.
- (2)
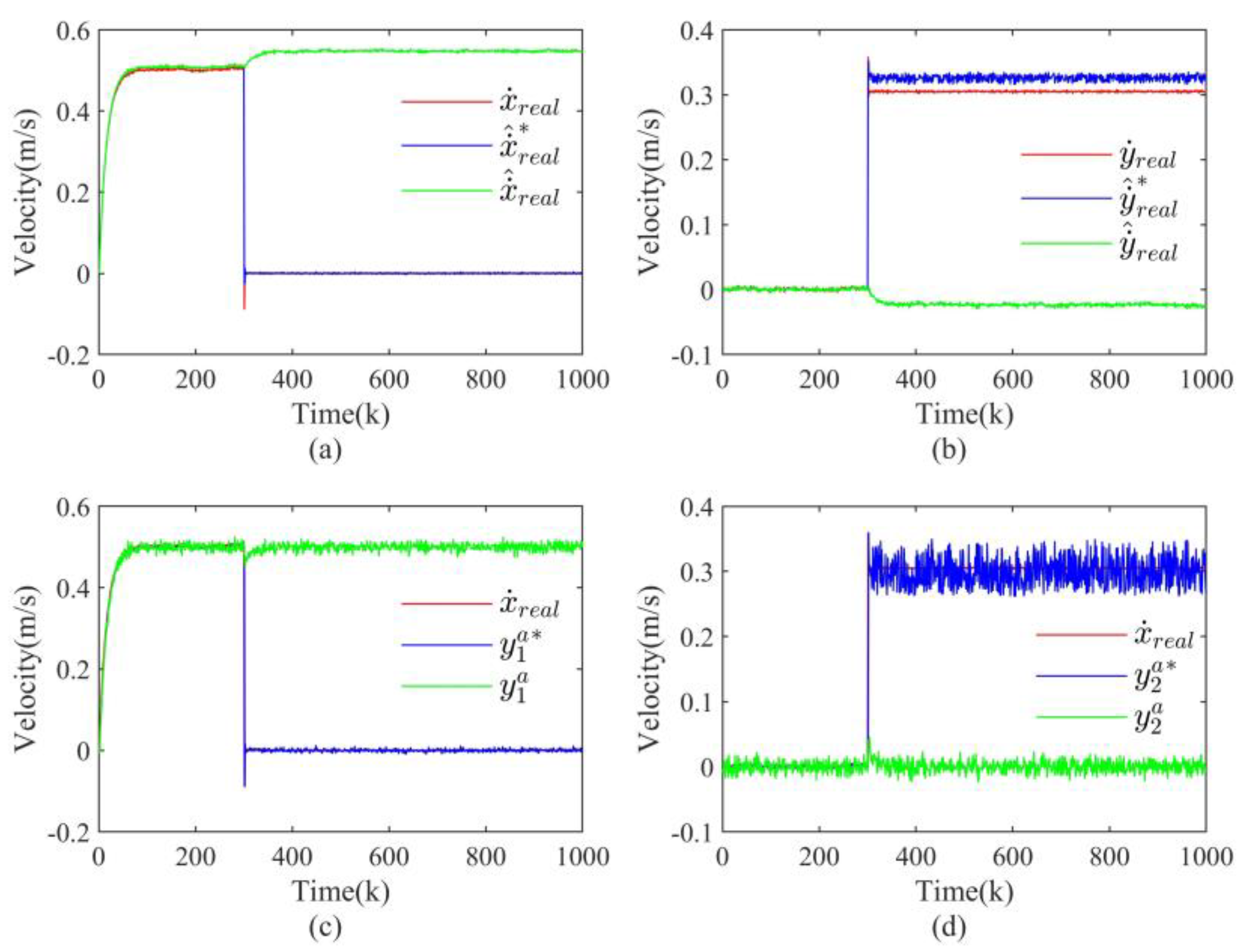
- Covert attack: It also requires complete knowledge of the system model and attacks against both actuation channels and measurement channels. In the actuation channels, the performance of the control system is affected by applying an additive signal ; however, in the measurement channels, the effect of the input attack on the measurement is eliminated by carefully designing a signal [33]. Given the discrete linear model in (1), can be calculated by the following equation.
- (3)
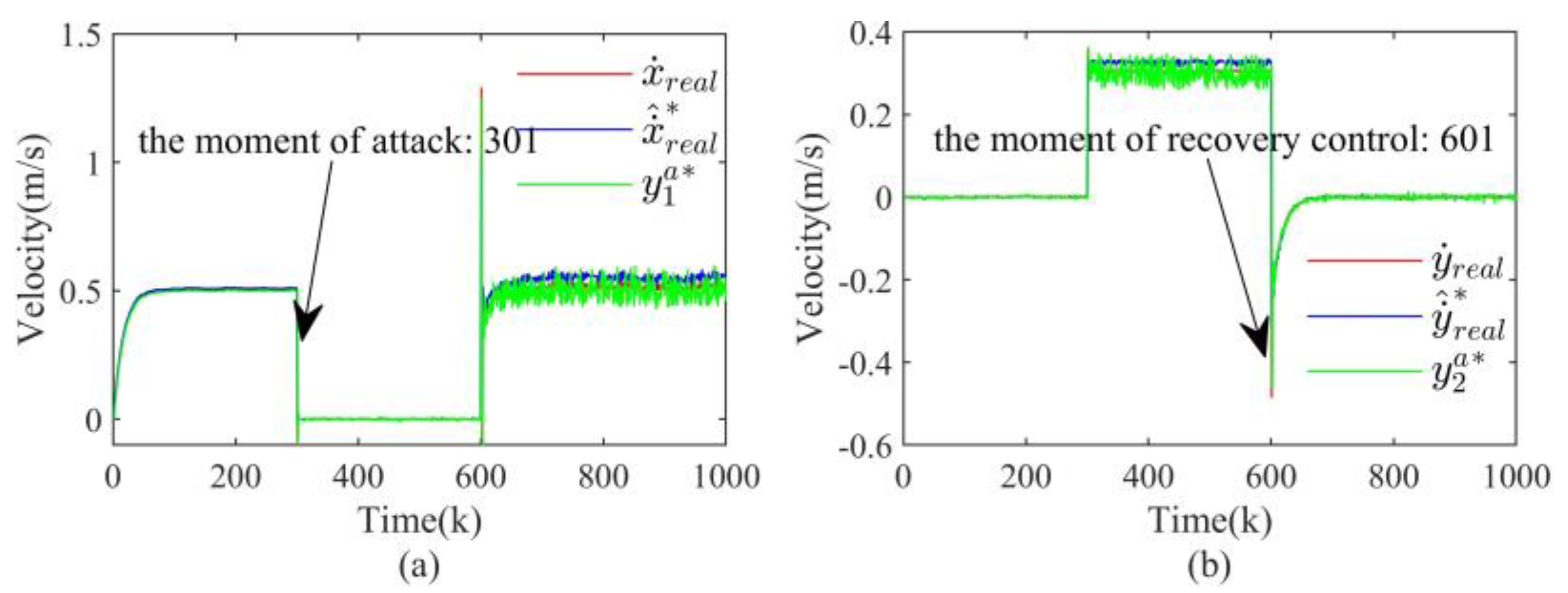
- Replay attack: It does not require knowledge of the system model. It only needs to be able to access the signal transmission channels, to attack the control signals, and to record and re-cover the measurement data. The replay attack can be specifically described as [34]: in the measurement channels, the measurement data in the steady-state of the system are recorded in advance, and the actual measurement values are overwritten with the recorded data when the attack is performed (i.e., ); while in the actuation channels, is designed to affect the performance of the system. Obviously, the replay attack is stealthy in the steady-state of the system.
2.3. Detection Method
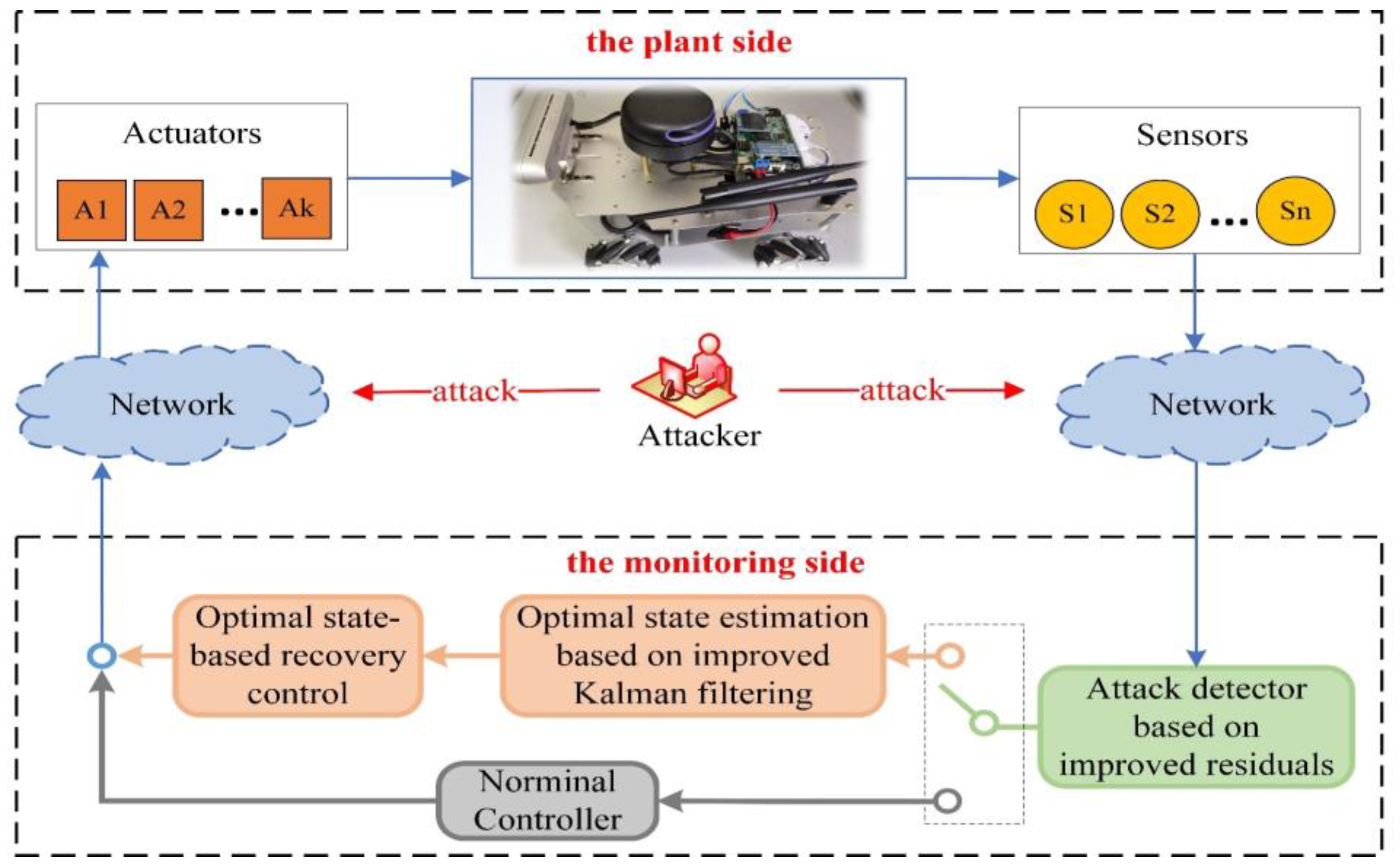
3. State Estimation and Recovery Control
3.1. Optimal State Estimation Based on Improved Kalman Filtering
3.2. The Recovery Control Strategy Based on Optimal State
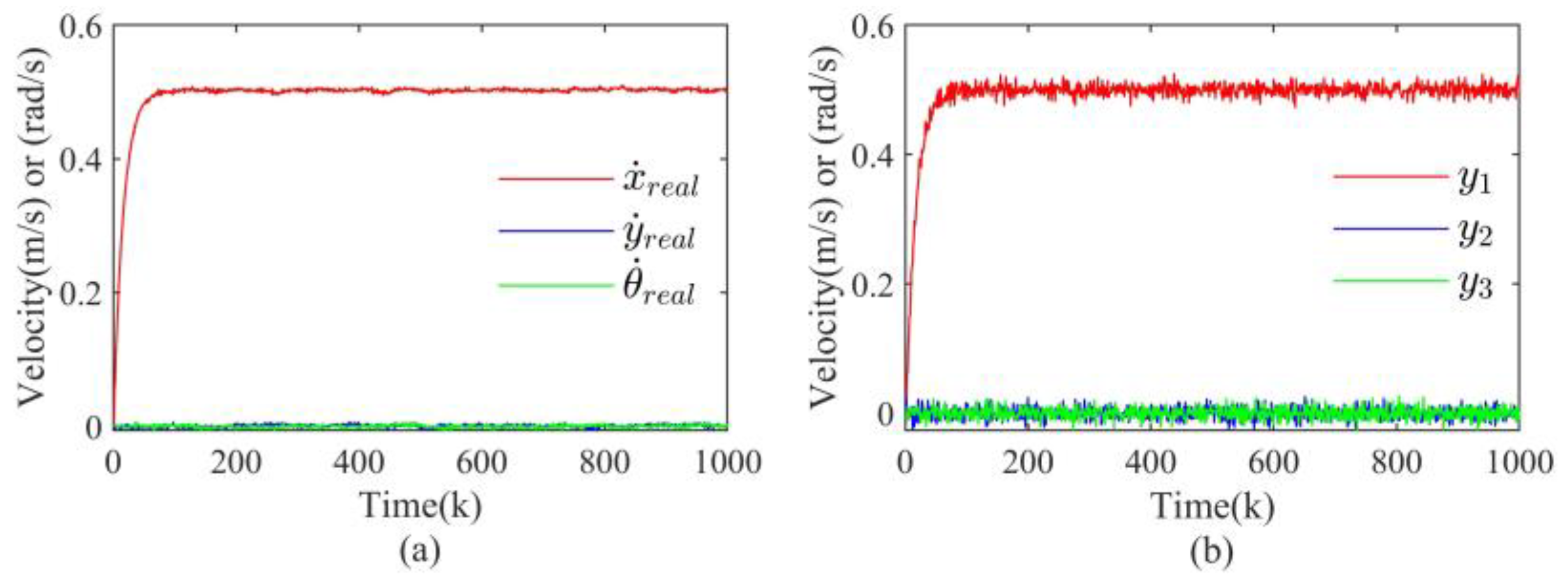
4. Simulation Results
4.1. Simulation Setup
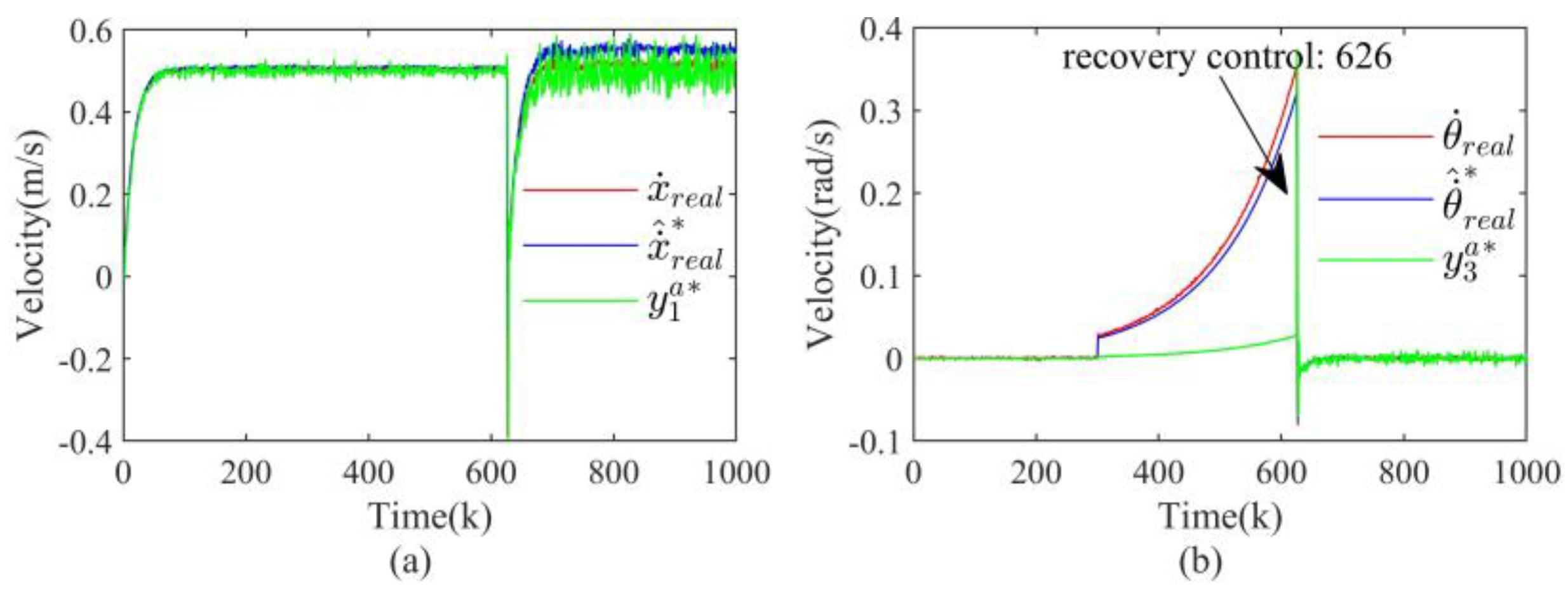
4.2. Results Discussion
4.2.1. Zero-Dynamics Attack
4.2.2. Covert Attack
4.2.3. Replay Attack
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ashibani, Y.; Mahmoud, Q.H. Cyber physical systems security: Analysis, challenges and solutions. Comput. Secur. 2017, 68, 81–97. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Salman, O.; Noura, H.N.; Kaaniche, N.; Chehab, A.; Malli, M. Cyber-physical systems security: Limitations, issues and future trends. Microprocess. Microsyst. 2020, 77, 103201. [Google Scholar] [CrossRef]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-physical systems security—A survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Wright, A. On Sapphire and type-safe languages. Commun. ACM 2003, 46, 120. [Google Scholar] [CrossRef]
- Peng, Y.; Lu, T.; Liu, J.; Gao, Y.; Guo, X.; Xie, F. Cyber-physical system risk assessment. In Proceedings of the Ninth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Beijing, China, 16–18 October 2013; pp. 442–447. [Google Scholar]
- Adams, C. Learning the lessons of WannaCry. Comput. Fraud Secur. 2018, 2018, 6–9. [Google Scholar] [CrossRef]
- Li, C.; Guan, L.; Lin, J.; Luo, B.; Cai, Q.; Jing, J.; Wang, J. Mimosa: Protecting private keys against memory disclosure attacks using hardware transactional memory. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1196–1213. [Google Scholar] [CrossRef]
- Rubio-Hernan, J.; De Cicco, L.; Garcia-Alfaro, J. On the use of watermark-based schemes to detect cyber-physical attacks. EURASIP J. Inf. Secur. 2017, 2017, 1–25. [Google Scholar] [CrossRef]
- Patil, N.V.; Rama Krishna, C.; Kumar, K. Distributed frameworks for detecting distributed denial of service attacks: A comprehensive review, challenges and future directions. Concurr. Comput. Pract. Exp. 2021, 33, e6197. [Google Scholar] [CrossRef]
- Dibaji, S.M.; Pirani, M.; Flamholz, D.B.; Annaswamy, A.M.; Johansson, K.H.; Chakrabortty, A. A systems and control perspective of CPS security. Annu. Rev. Control 2019, 47, 394–411. [Google Scholar] [CrossRef]
- Ghaderi, M.; Gheitasi, K.; Lucia, W. A blended active detection strategy for false data injection attacks in cyber-physical systems. IEEE Trans. Control Netw. Syst. 2020, 8, 168–176. [Google Scholar] [CrossRef]
- Griffioen, P.; Weerakkody, S.; Sinopoli, B. A moving target defense for securing cyber-physical systems. IEEE Trans. Autom. Control 2020, 66, 2016–2031. [Google Scholar] [CrossRef]
- Ghaderi, M.; Gheitasi, K.; Lucia, W. A novel control architecture for the detection of false data injection attacks in networked control systems. In Proceedings of the 2019 American Control Conference, Philadelphia, PA, USA, 10–12 July 2019; pp. 139–144. [Google Scholar]
- Yang, B.; Xin, L.; Long, Z. An improved Residual-based detection method for stealthy anomalies on mobile robots. Machines 2022, 10, 446. [Google Scholar] [CrossRef]
- Ding, S.X.; Yang, G.; Zhang, P.; Ding, E.L.; Jeinsch, T.; Weinhold, N.; Schultalbers, M. Feedback control structures, embedded residual signals, and feedback control schemes with an integrated residual access. IEEE Trans. Control Syst. Technol. 2009, 18, 352–367. [Google Scholar] [CrossRef]
- Mo, Y.; Weerakkody, S.; Sinopoli, B. Physical authentication of control systems: Designing watermarked control inputs to detect counterfeit sensor outputs. IEEE Control Syst. Mag. 2015, 35, 93–109. [Google Scholar]
- Yang, W.; Zheng, Z.; Chen, G.; Tang, Y.; Wang, X. Security analysis of a distributed networked system under eavesdropping attacks. IEEE Trans. Circuits Syst. II Express Briefs 2019, 67, 1254–1258. [Google Scholar] [CrossRef]
- Forti, N.; Battistelli, G.; Chisci, L.; Sinopoli, B. A Bayesian approach to joint attack detection and resilient state estimation. In Proceedings of the 2016 IEEE 55th Conference on Decision and Control, Las Vegas, NV, USA, 12–14 December 2016; pp. 1192–1198. [Google Scholar]
- Zhang, K.; Jiang, B.; Ding, S.X.; Zhou, D. Robust asymptotic fault estimation of discrete-time interconnected systems with sensor faults. IEEE Trans. Cybern. 2020, 52, 1691–1700. [Google Scholar] [CrossRef]
- Yang, H.; Yin, S.; Han, H.; Sun, H. Sparse actuator and sensor attacks reconstruction for linear cyber-physical systems with sliding mode observer. IEEE Trans. Ind. Inform. 2021, 18, 3873–3884. [Google Scholar] [CrossRef]
- Liu, X.; Ngai, E.C.H.; Liu, J. Secure information fusion using local posterior for distributed cyber-physical systems. IEEE Trans. Mob. Comput. 2020, 20, 2041–2054. [Google Scholar] [CrossRef]
- Rana, M.M.; Bo, R.; Abdelhadi, A. Distributed grid state estimation under cyber attacks using optimal filter and Bayesian approach. IEEE Syst. J. 2020, 15, 1970–1978. [Google Scholar] [CrossRef]
- Chen, G.; Zhang, Y.; Gu, S.; Hu, W. Resilient state estimation and control of cyber-physical systems against false data injection attacks on both actuator and sensors. IEEE Trans. Control Netw. Syst. 2021, 9, 500–510. [Google Scholar] [CrossRef]
- Chen, J.; Shi, Y. Stochastic model predictive control framework for resilient cyber-physical systems: Review and perspectives. Philos. Trans. R. Soc. A 2021, 379, 20200371. [Google Scholar] [CrossRef] [PubMed]
- Ge, H.; Yue, D.; Xie, X.; Deng, S.; Dou, C. A unified modeling of muti-sources cyber-attacks with uncertainties for CPS security control. J. Frankl. Inst. 2021, 358, 89–113. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, B.; Xu, X.; Usman; Li, L. Research on cyber-physical system control strategy under false data injection attack perception. Trans. Inst. Meas. Control 2022, 01423312211069371. [Google Scholar] [CrossRef]
- Zhang, D.; Han, Q.L.; Zhang, X.M. Network-based modeling and proportional–integral control for direct-drive-wheel systems in wireless network environments. IEEE Trans. Cybern. 2019, 50, 2462–2474. [Google Scholar] [CrossRef] [PubMed]
- Kazemy, A.; Lam, J.; Zhang, X.M. Event-triggered output feedback synchronization of master–slave neural networks under deception attacks. IEEE Trans. Neural Netw. Learn. Syst. 2020, 33, 952–961. [Google Scholar] [CrossRef] [PubMed]
- Zhang, X.M.; Han, Q.L.; Ge, X. A novel approach to H∞ performance analysis of discrete-time networked systems subject to network-induced delays and malicious packet dropouts. Automatica 2020, 136, 110010. [Google Scholar] [CrossRef]
- Xin, L.; Yang, B.; Long, Z. The sensor-actuators stealthy cyber-attacks framework on networked control systems: A data-driven approach. Asian J. Control 2023. [Google Scholar] [CrossRef]
- Ding, S.X.; Li, L.; Zhao, D.; Louen, C.; Liu, T. Application of the unified control and detection framework to detecting stealthy integrity cyber-attacks on feedback control systems. Automatica 2022, 142, 110352. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef]
- Smith, R.S. Covert misappropriation of networked control systems: Presenting a feedback structure. IEEE Control Syst. Mag. 2015, 35, 82–92. [Google Scholar]
- Mo, Y.; Sinopoli, B. Secure control against replay attacks. In Proceedings of the 2009 47th Annual Allerton Conference on Communication, Control, and Computing, Monticello, IL, USA, 30 September–2 October 2009; pp. 911–918. [Google Scholar]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, B.; Xin, L.; Long, Z. Research on Secure State Estimation and Recovery Control for CPS under Stealthy Attacks. Actuators 2023, 12, 427. https://doi.org/10.3390/act12110427
Yang B, Xin L, Long Z. Research on Secure State Estimation and Recovery Control for CPS under Stealthy Attacks. Actuators. 2023; 12(11):427. https://doi.org/10.3390/act12110427
Chicago/Turabian StyleYang, Biao, Liang Xin, and Zhiqiang Long. 2023. "Research on Secure State Estimation and Recovery Control for CPS under Stealthy Attacks" Actuators 12, no. 11: 427. https://doi.org/10.3390/act12110427
APA StyleYang, B., Xin, L., & Long, Z. (2023). Research on Secure State Estimation and Recovery Control for CPS under Stealthy Attacks. Actuators, 12(11), 427. https://doi.org/10.3390/act12110427









