1. Introduction
The rise of 6G communication technology represents a significant leap forward in the realm of digital connectivity. Characterized by ultra-fast data rates, low latency, and massive connectivity, 6G is set to transform various industries and applications [
1]. The Internet of Vehicles (IoV) has emerged as a transformative paradigm in smart city ecosystems, driven by advancements in vehicular communications (V2X), Geographic Information Systems (GIS), and artificial intelligence. By integrating real-time spatial data from GIS with V2X technologies, IoVs enable dynamic route optimization, traffic flow prediction, and infrastructure coordination within urban environments. For instance, GIS facilitates the aggregation of geospatial data from sensors, traffic cameras, and autonomous vehicles to generate adaptive navigation models that mitigate congestion and enhance emergency response efficiency in smart cities. However, significant challenges persist, including the need for robust data privacy frameworks to secure heterogeneous data streams from IoT sensors and social media, as well as ensuring interoperability between legacy urban systems and emerging IoV architectures [
2]. Addressing these issues will solidify the IoV’s role in shaping resilient, data-driven smart cities. Vehicles are outfitted with sensors, control and computing units, communication devices, storage, and learning capabilities. This allows IoVs to integrate seamlessly with the Internet, transportation infrastructure, and other road users via V2X communications.
In this framework, vehicles are equipped with sensors, control and computing units, communication tools, storage, and learning capabilities, enabling their integration with the Internet, transportation infrastructure, and other road users through V2X communications. Historically, the primary V2X solution was Dedicated Short-Range Communication (DSRC) in accordance with the IEEE 802.11p standard [
3]. For future applications, systems are expected to be fully automated with intelligent connections, enabling them to execute services and actions with speed, efficiency, and intelligence.
6G technology has the potential to revolutionize V2X communication, encompassing concepts like Connected Autonomous Vehicles (CAVs), the IoV, intra-vehicular communication, Vehicle-to-Vehicle (V2V) communication, and Vehicle-to-Infrastructure (V2I) communication [
4]. These advanced techniques are poised to modernize transportation by making it safer and more efficient. V2X communication facilitates the exchange of data among an ego vehicle and other transport participants, which includes other vehicles, road infrastructure, and even pedestrians. This capability is designed to improve the safety and efficiency of transportation systems by enabling real-time communication between vehicles and their surroundings [
5]. Moreover, V2X communication with 6G can be seen as a crucial technological component for the advancement of automated vehicles and intelligent transportation systems [
6]. It provides essential information that ensures vehicles can navigate safely and perform efficiently in various complex traffic conditions. As such, 6G-enabled V2X is expected to play an important role in the design and deployment of future automated vehicles and intelligent transportation.
The growing demand for enhancing smart and intelligent features, especially in the realm of intelligent cybersecurity, has become a prime concern. Achieving maximum security with minimal associated costs is critical. Intelligent systems play a crucial role in assisting Automated Vehicles (AVs) in maintaining vulnerable components, preventing reckless driving, mitigating serious accidents, improving instructive driving, and making informed decisions [
7]. These advancements reduce maintenance costs and prevent hindrances to national economic growth, highlighting the importance of integrating intelligent cybersecurity measures in the evolving IoV landscape.
V2X communication is the vital technique that facilitates interaction among vehicles, pedestrians, road facilities, and other devices. With the advent of 6G, this communication is designed to significantly improve traffic safety and operational efficiency [
8]. However, integrating V2X with 6G will introduce a variety of new risks and threats. The primary security challenge in V2X communication is to maintain the confidentiality, integrity, availability, authentication, and access control (CIA
3) of data transmitted among IoV nodes and facilities [
9]. Ensuring secure and accurate communication is crucial for the safe operation of automated vehicles. Cybersecurity threats such as eavesdropping, data alteration, and Denial-of-Service (DoS) attacks can jeopardize the integrity of V2X communication, potentially resulting in severe road safety issues.
One of the key challenges in securing the IoV is maintaining trust among nodes for credible message dissemination [
10]. Unverified messages are inherently untrusted because malicious nodes can generate false reports about non-existent incidents. With the rapid development of V2X communication, numerous security challenges have emerged, prompting the need for advanced measures. To effectively safeguard V2X networks, a holistic framework is essential for security, which integrates all components of the V2X ecosystem, encompassing IoVs, edge computing units, and central clouds.
This study addresses these pressing challenges by proposing a novel system architecture that integrates blockchain and federated learning (FL) to enhance the security and resilience of V2X communication in the emerging 6G era. The main contributions of this work are as follows:
Integrated Security Architecture: A novel system architecture is proposed that synergistically combines a partitioned blockchain with an FL pipeline. This design leverages blockchain’s decentralization for tamper-proof data exchange and FL’s distributed nature for privacy-preserving collaborative model training.
Malicious Node Mitigation Mechanism: A smart contract-based mechanism, incorporating a Random Forest classifier, is introduced to detect and isolate malicious nodes that attempt data poisoning or model corruption attacks, thereby enhancing the trustworthiness of the collaborative learning process.
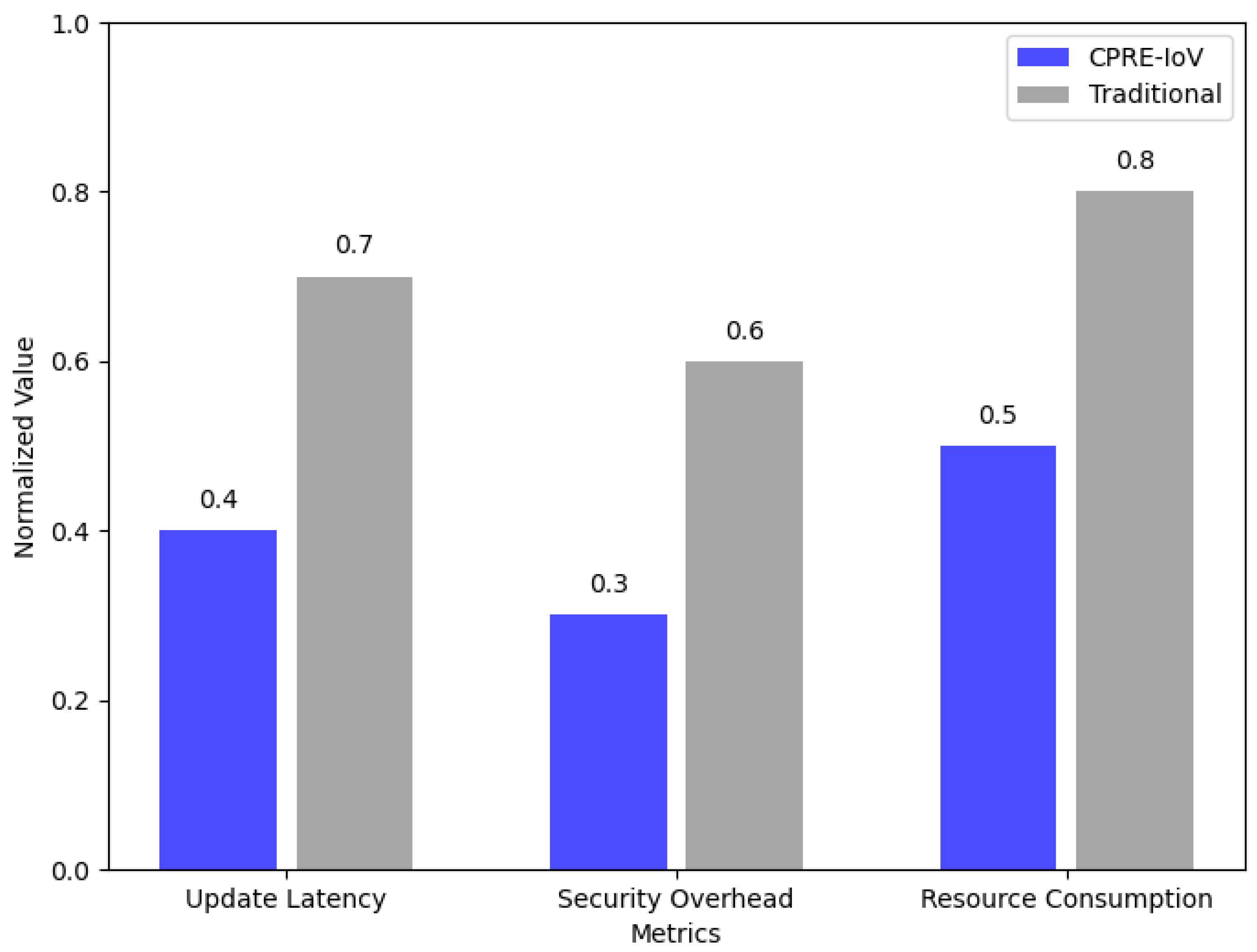
Efficient and Secure Data Offloading: A Cloud Proxy Re-Encryption Offloading (CPRE-IoV) algorithm is developed that enables secure data handling and efficient model updates, specifically designed to address the high mobility and stringent latency requirements of vehicular networks.
Comprehensive Validation: The framework’s effectiveness is validated through rigorous evaluations using a co-simulation platform of OMNeT++ and SUMO. Fault injection tests and scalability analysis demonstrate the framework’s ability to maintain high accuracy and low failure rates under various attack scenarios.
The structure of the remainder of this paper is as follows:
Section 2 provides a review of the integration architecture of the Vehicle–Road–Cloud paradigm for emerging techniques in 6G, focusing on the main security requirements and threats for IoV. In
Section 3, the proposed system architecture combining blockchain and federated learning is detailed.
Section 4 presents the CPRE-IoV algorithm.
Section 5 details the experimental evaluation and results. Finally,
Section 6 provides the conclusion of the paper and discusses future work.
2. Related Work
This section reviews key areas of related work, categorized by their approach, and positions the present contribution within the existing literature. The integration of blockchain and federated learning (FL) has emerged as a promising paradigm for securing distributed systems, particularly in the context of the Internet of Things (IoT) and the Internet of Vehicles (IoV). Several recent studies have explored this synergy, laying a foundation for privacy-preserved, decentralized machine learning. A comprehensive survey by Javed et al. [
11] provides a broad overview of the integration of blockchain and FL in IoV networks, outlining the potential benefits and research challenges. Early foundational work by Lu et al. [
12] proposed a blockchain-based FL framework for general Industrial IoT, demonstrating how blockchain can facilitate auditable and secure model aggregation, preventing single points of failure.
Building on these concepts, researchers have focused on tailoring solutions specifically for the vehicular domain. Boualouache and Ghamri-Doudane [
13] introduced Zero-x, a framework that uses blockchain and open-set FL to detect zero-day attacks in IoV, highlighting the need for adaptability against unknown threats. Similarly, Ullah et al. [
14] developed SecBFL-IoV, which focuses on resilience against data poisoning attacks by incorporating a secure blockchain-based model verification process. Another relevant approach by Ahmed et al. [
15] integrates blockchain with federated Q-learning to secure vehicular ad-hoc networks, emphasizing decision-making in dynamic environments. Many frameworks address specific threats but neglect the high latency unsuitable for mobile scenarios, or they lack mechanisms optimized for V2X data offloading challenges. Thus, a research gap exists for a holistic framework that balances robust security with the low-latency performance required for dynamic vehicular networks.
To bridge this gap, our paper proposes an architecture that synergistically integrates a partitioned blockchain, FL, and a novel proxy re-encryption offloading (CPRE-IoV) algorithm. This multi-layered system overcomes the limitations of existing solutions by design. The partitioned blockchain mitigates network latency, while our CPRE-IoV algorithm ensures efficient model updates during high mobility. Furthermore, a smart contract using a Proof-of-Trust mechanism provides a dynamic and resource-efficient defense against malicious nodes. The result is a robust framework that provides a secure, private, and efficient foundation for next-generation IoV networks, as demonstrated in the following sections.
The integration of intelligent vehicles within modern transportation networks has brought about significant advancements in vehicular communication and efficiency. However, it has also introduced substantial security and privacy challenges. Some works have focused on specific technologies to address these issues. Mumtaz et al. highlighted how blockchain can create a robust framework for intelligent vehicular communication by ensuring data integrity and secure transactions [
16]. Call admission control mechanisms play a crucial role in managing the security of ultra-dense 5G networks. Al-Rubaye et al. proposed a call admission control scheme for non-standalone 5G ultra-dense networks to ensure that network resources are allocated efficiently while maintaining security [
17]. In parallel, cloud-based management strategies have been explored to improve energy efficiency and security in vehicular networks. Zhou et al. [
18] investigated the use of fronthaul and virtualized baseband processing pools in Long-Term Evolution (LTE) networks, showcasing how cloud management can enhance both energy efficiency and data security.
The privacy of users in location-based services has also been a critical concern. Feng et al. [
19] proposed a framework to balance location privacy preservation with the quality of experience in location-based services. Wu et al. [
20] provided a robust framework for modeling control delays for edge-enabled UAVs in cellular networks. This body of work underscores the importance of developing privacy-preserving mechanisms that do not compromise service quality. Network slicing in 5G networks presents another promising avenue for enhancing vehicular communication security. D’Oro et al. demonstrated how coordinated network slicing can improve network throughput while maintaining high security standards [
21]. This work suggests that it is possible to minimize the risk of cross-traffic attacks on intelligent vehicles by isolating different types of network traffic.
In fact, maintaining secure communication systems in intelligent vehicles is critical. Saleem et al. [
22] underscored the need for robust authentication and key agreement frameworks in maintaining secure communication in intelligent vehicular systems. Guo et al. [
23] focused on uninterrupted communication on highways by developing dynamic blockage avoidance strategies and effective channel state information acquisition techniques. Lin et al. [
24] proposed a dynamic and flexible framework for managing vehicular communication security through hybrid Peer-to-Peer (P2P) client–server data transmission. Roger et al. [
25] proposed a batch-authenticated and key agreement framework for P2P-based online social networks, which ensures secure communication and data integrity in intelligent vehicular systems with adaptable data transmission methods. Fallgren et al. [
26] discussed multicast and broadcast enablers for high-performing cellular V2X systems, which are essential for secure and efficient vehicle communication. Haliloglu et al. [
27] highlighted the potential of distributed Multiple-Input Multiple-Output (MIMO) systems to enhance the security and performance of 6G networks. The privacy of energy trading in vehicle-to-grid (V2G) networks has been addressed by Shen et al., who developed a traceable and privacy-preserving authentication scheme [
28]. Nestinger et al. [
29] proposed a mobile agent-based framework for flexible automation systems, which is critical for enhancing the adaptability and security of intelligent vehicular networks.
For operational security, Wang et al. [
30] dissected the security of operational cellular IoT services, identifying various attack vectors and proposing defenses for securing these services. For collaborative detection of Distributed Denial-of-Service (DDoS) attacks over multiple network domains, Zhang et al. [
31] provided a comprehensive approach to enhancing the security of intelligent vehicular systems. Penetration testing in the IoT age, as explored by Chen et al., is crucial for identifying and mitigating vulnerabilities in intelligent vehicular networks [
32]. Dissecting operational cellular IoT service security, Wang et al. [
33] provided a comprehensive overview of the attack vectors and defenses necessary for maintaining secure intelligent vehicular communication.
Addressing the security and reliability engineering issues, Shieh et al. discussed the challenges and solutions in a rapidly evolving technological landscape, particularly relevant for the convergence of intelligent vehicular technologies [
34]. The practical privacy-preserving scheme with fault tolerance for smart grids, as proposed by Chang et al. [
35], provides a reliable approach to maintaining security in smart vehicular networks. Electric vehicle aggregation, reviewed by Nelson et al. [
36], offers insights into the benefits and vulnerabilities of managing a growing fleet of intelligent vehicles.
Artificial intelligence (AI) and machine learning (ML) techniques have been increasingly applied to address security and privacy challenges in vehicular networks [
37,
38,
39]. Pan et al. explored the use of deep learning for blind signature classification in IoT connectivity, which is crucial for maintaining secure communication channels in vehicular networks [
40]. Abdo et al. [
41] explored the role of AI in mitigating security risks in the IoV, which provides a comprehensive approach to detecting and preventing application-level attacks on the IoV. Federated learning (FL) is a cutting-edge machine learning technique designed to enhance security and privacy while maintaining manageable levels of latency, communication, and computational costs [
42]. Unlike traditional centralized learning, where data is collected and processed in a single location, FL operates by training models directly on each device or node using local datasets. These locally trained models, typically deep neural networks, are then transmitted to a central server, known as the aggregator. The aggregator combines these local models to create an improved global model, which is subsequently distributed back to the individual nodes. This process allows for continuous refinement of local models without the need to transfer large volumes of raw data, thus preserving data privacy and reducing communication overhead. In such frameworks, blockchain is employed to achieve decentralization and eliminate the risk caused by single points of failure. The locally trained models from individual nodes can be transmitted to the central cloud platform using other nodes. Despite these advancements in IoV, integrating FL with blockchain presents challenges, such as designing a flexible and robust framework to address IoV security.
To clearly situate our work within the existing body of research,
Table 1 provides a comparative summary of key related works, highlighting their methodologies, primary focus, and, most importantly, their inherent limitations. A thorough analysis of these studies reveals a recurring pattern: existing solutions often address security aspects in isolation, resulting in significant trade-offs. For instance, some blockchain-based frameworks enhance data integrity at the cost of high latency, rendering them unsuitable for real-time V2X applications. Conversely, while some AI-driven methods improve threat detection, they often rely on centralized architectures that introduce single points of failure and are vulnerable to privacy breaches and model poisoning attacks. A clear research gap therefore exists for a holistic framework that can simultaneously guarantee data integrity, preserve user privacy in a distributed learning context, and maintain the low-latency performance required for dynamic vehicular environments.
To bridge this gap, this paper proposes an innovative integrated security architecture that synergistically combines a partitioned blockchain, federated learning (FL), and a novel proxy re-encryption offloading algorithm. The primary advantage of this integrated approach is its ability to overcome the limitations of standalone solutions by creating a robust, multi-layered defense system. As shown in
Table 2, compared with other methods, by partitioning the blockchain, we mitigate the inherent latency issues, while the use of FL ensures privacy without sacrificing collaborative intelligence. The smart-contract-based malicious node detection further enhances the resilience of the FL process. The following sections will detail this proposed architecture and demonstrate its superiority in providing a secure, private, and efficient solution for next-generation IoV networks.
3. The Proposed Integrated Architecture
3.1. System Model and Security Assumptions
To provide a formal presentation, we define the system model and outline our security assumptions.
System Model: The proposed IoV network consists of three main entities:
Vehicles (IoVs): A set of vehicles , where K is the total number of vehicles. Each vehicle is equipped with sensors, computation units, and communication modules. It collects local data and trains a local model with parameters .
Infrastructure nodes: These include a set of Roadside Units (RSUs) and a set of Edge Servers . RSUs and Edge Servers act as aggregators, proxy nodes, and participants in the blockchain network.
Cloud server: A central cloud platform responsible for initializing the global model and coordinating the overall FL process, but it does not have access to raw vehicle data.
The system operates over a partitioned blockchain, comprising local micro blockchains and a global key blockchain. The goal is to collaboratively train a global model by aggregating local models in a secure and privacy-preserving manner, minimizing a global loss function .
Threat model: We assume an honest-but-curious model for the edge and cloud servers, meaning they will follow the protocol but may attempt to infer sensitive information from the data they receive. We also consider active internal attackers, where a subset of vehicle nodes are malicious. These malicious nodes can perform two types of attacks:
Data poisoning: A malicious node can manipulate its local dataset to generate a biased local model , aiming to degrade the performance of the final global model .
Model poisoning: A malicious node can directly tamper with its computed model parameters before submitting them for aggregation.
We assume the attackers cannot break the underlying cryptographic primitives (e.g., ECC, SHA-256) and cannot compromise more than a certain fraction of the network nodes required to bypass the consensus mechanism (e.g., less than for PBFT).
To address the security and privacy challenges outlined previously, this section details the proposed integrated system architecture. First, the foundational concepts of how blockchain and federated learning are adapted for the IoV context are described. Then, the novel Vehicle–Road–Cloud architecture, which combines these technologies into a cohesive and resilient framework, is presented.
3.2. Blockchain-Enabled Distributed Architecture for IoV
Blockchain is a decentralized and distributed digital ledger technology that securely records transactions across multiple devices so that the record cannot be altered retroactively [
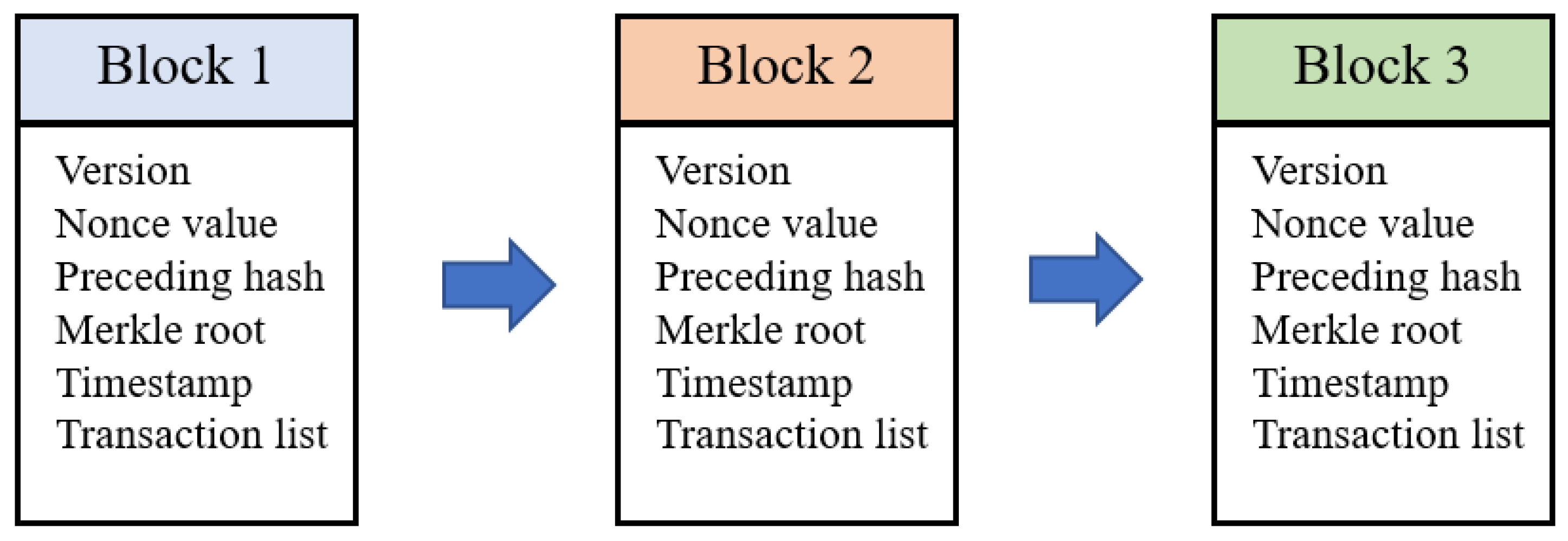
43]. It operates on the principles of cryptographic hashing and consensus algorithms to ensure the integrity, transparency, and immutability of data. As shown in
Figure 1, blockchain is a chain of blocks, where each block contains a list of transactions. These transactions are verified by network participants through cryptographic algorithms, ensuring their validity and authenticity. Once verified, the transactions are added to the block, which is then appended to the existing chain in a linear, chronological order.
One of the key features of blockchain is its decentralization. Unlike traditional centralized databases controlled by a single entity, a blockchain network is maintained by a distributed network of nodes. Each node holds a copy of the entire blockchain, and consensus protocols are employed to agree on the validity of transactions, thereby eliminating the need for intermediaries. Blockchain also enhances security through its immutable ledger. Once data is written onto a blockchain, altering it requires the alteration of all subsequent blocks, which would demand a consensus from the majority of the network. This makes blockchain highly resistant to tampering and fraud.
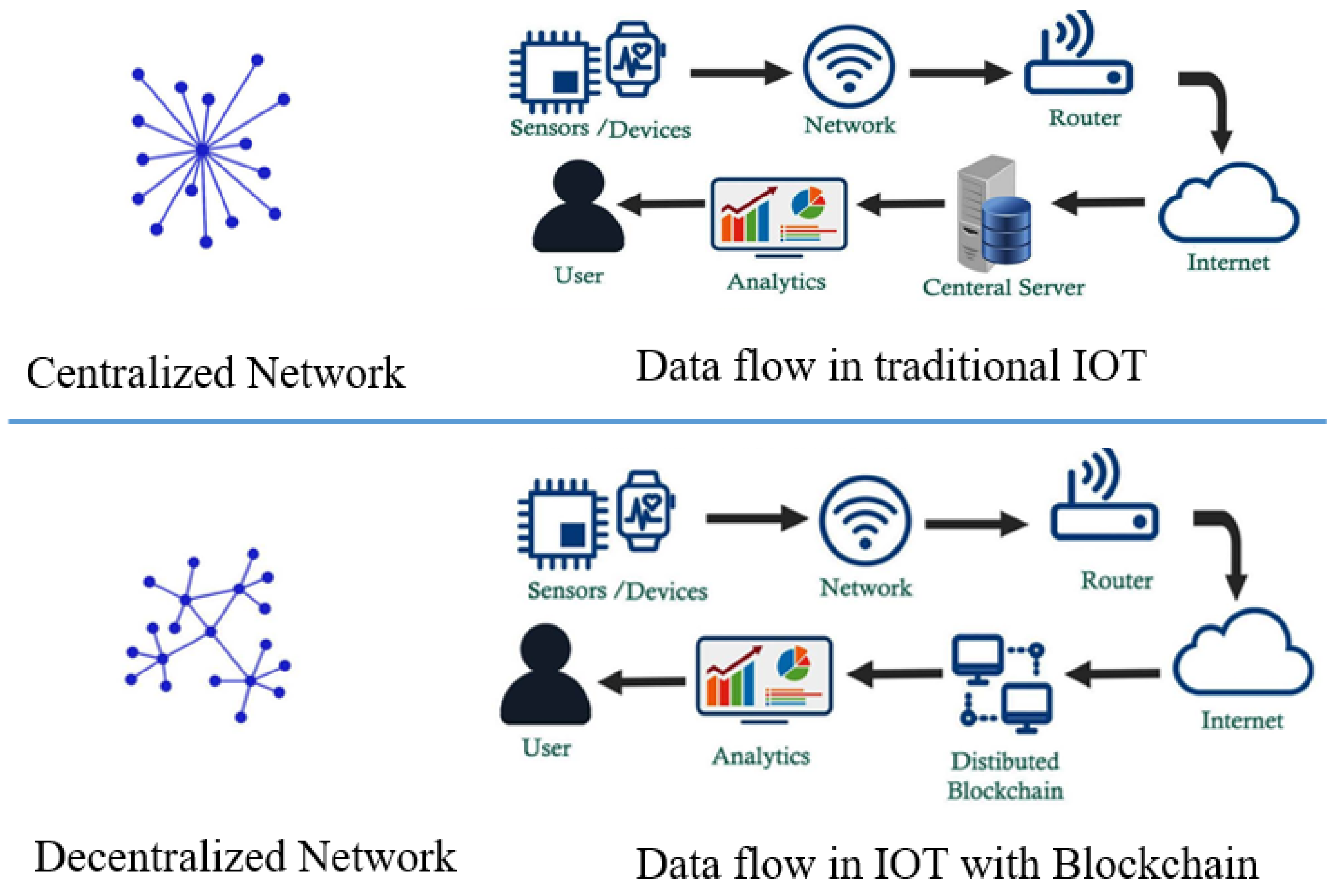
While the traditional Internet of Things (IoT) provides benefits such as data sharing, real-time analysis, and traceability, it suffers from significant security shortcomings. Ensuring data protection is essential for all IoT applications; however, one of the main challenges lies in the centralized collection of data on servers. This centralization creates an inefficient infrastructure for handling the large volumes of data generated by IoT systems and leaves it vulnerable to various attacks, including DDoS attacks, eavesdropping, and other security threats.
To address these security issues and improve the resilience of IoT systems, blockchain technology has been introduced. By employing a decentralized network, blockchain enhances security and mitigates the vulnerabilities associated with centralized data collection. This approach not only strengthens the infrastructure but also protects against common attacks and security breaches, as illustrated in
Figure 2.
3.3. Federated Learning-Enhanced Distributed Intelligence for Secure IoV Networks
Federated Learning (FL) is a machine learning method where multiple decentralized devices or servers collaboratively train a model without sharing their local data. Instead of sending raw data to a central server, each participating device trains the model locally and only shares the model updates with a central coordinator. This coordinator then aggregates these updates to create a global model, which is redistributed back to the devices for further training. This process continues iteratively. Since raw data never leaves the local devices, FL significantly enhances data privacy and security. This is particularly important in sensitive domains like healthcare, finance, and personal data. FL operates on a decentralized network of devices, reducing the need for centralized data storage and processing, which can be a bottleneck and a single point of failure. FL can scale to large numbers of devices, making it suitable for applications involving edge computing and the Internet of Things (IoT). FL allows for personalized models that can adapt to the specific data distribution of each device, improving the model’s performance for individual users while maintaining a strong global model.
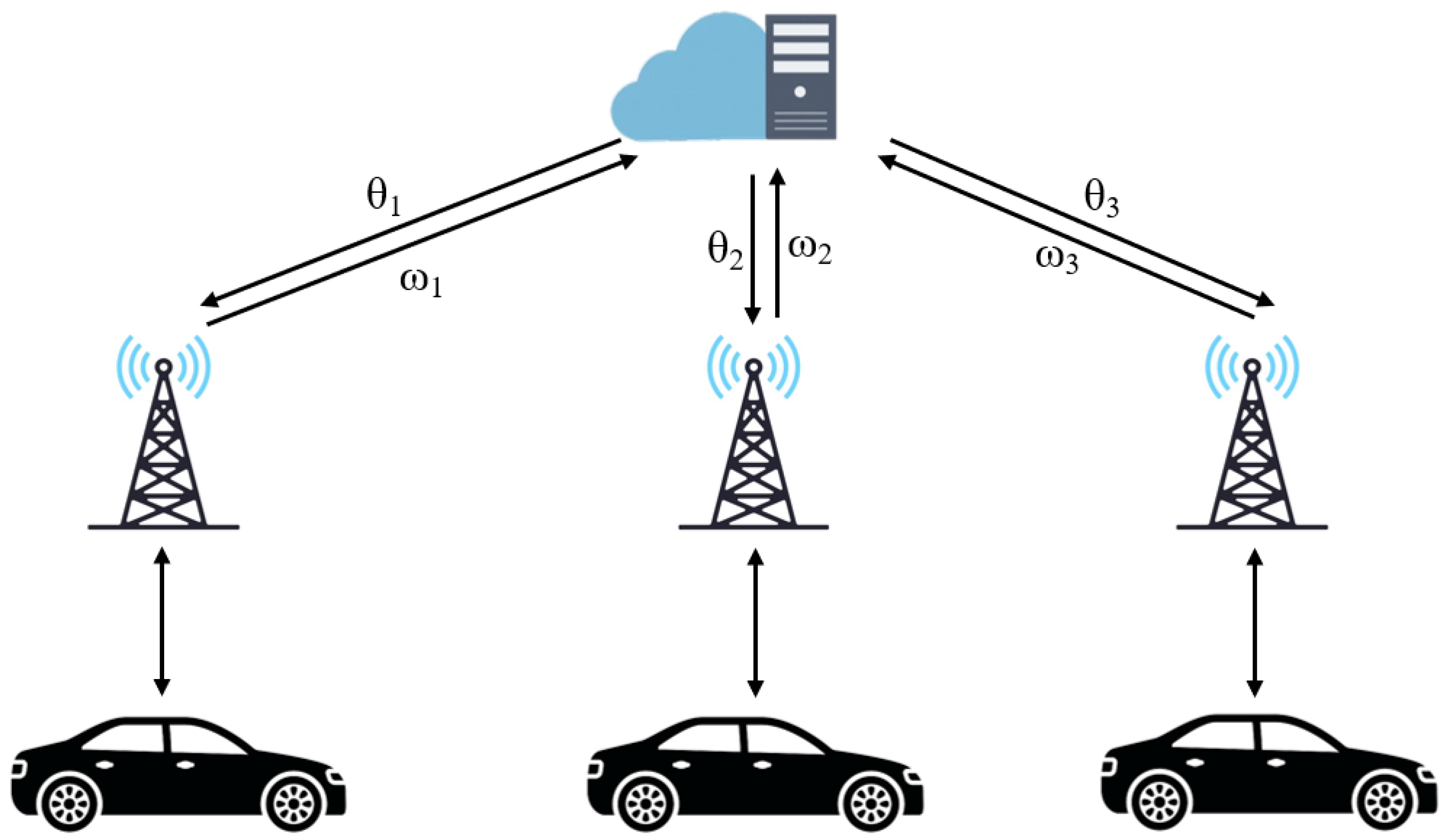
The federated learning structure for IoVs, as shown in
Figure 3, has each IoV train the model on its local data and compute model updates. Devices send their model updates to a central server. The server aggregates these updates to form a new global model. Aggregation can be done using various techniques, such as federated averaging. Ensuring that model updates are not tampered with and defending against adversarial attacks is crucial for maintaining the integrity of the federated learning process.
3.4. The Integrated Blockchain and Federated Learning Architecture
Integrating blockchain and federated learning in the IoV network can improve data privacy and security. With the increasing amount of data generated by vehicles, the decentralized framework with blockchain can enhance the robustness and reliability of the IoV network. Meanwhile, FL decentralizes the training process by allowing edge devices (vehicles) to train local models independently and aggregate updates, reducing dependency on central servers. The blockchain offers protection against malicious nodes by utilizing smart contracts, which can identify and prevent the inclusion of fraudulent or inaccurate local models in the blockchain.
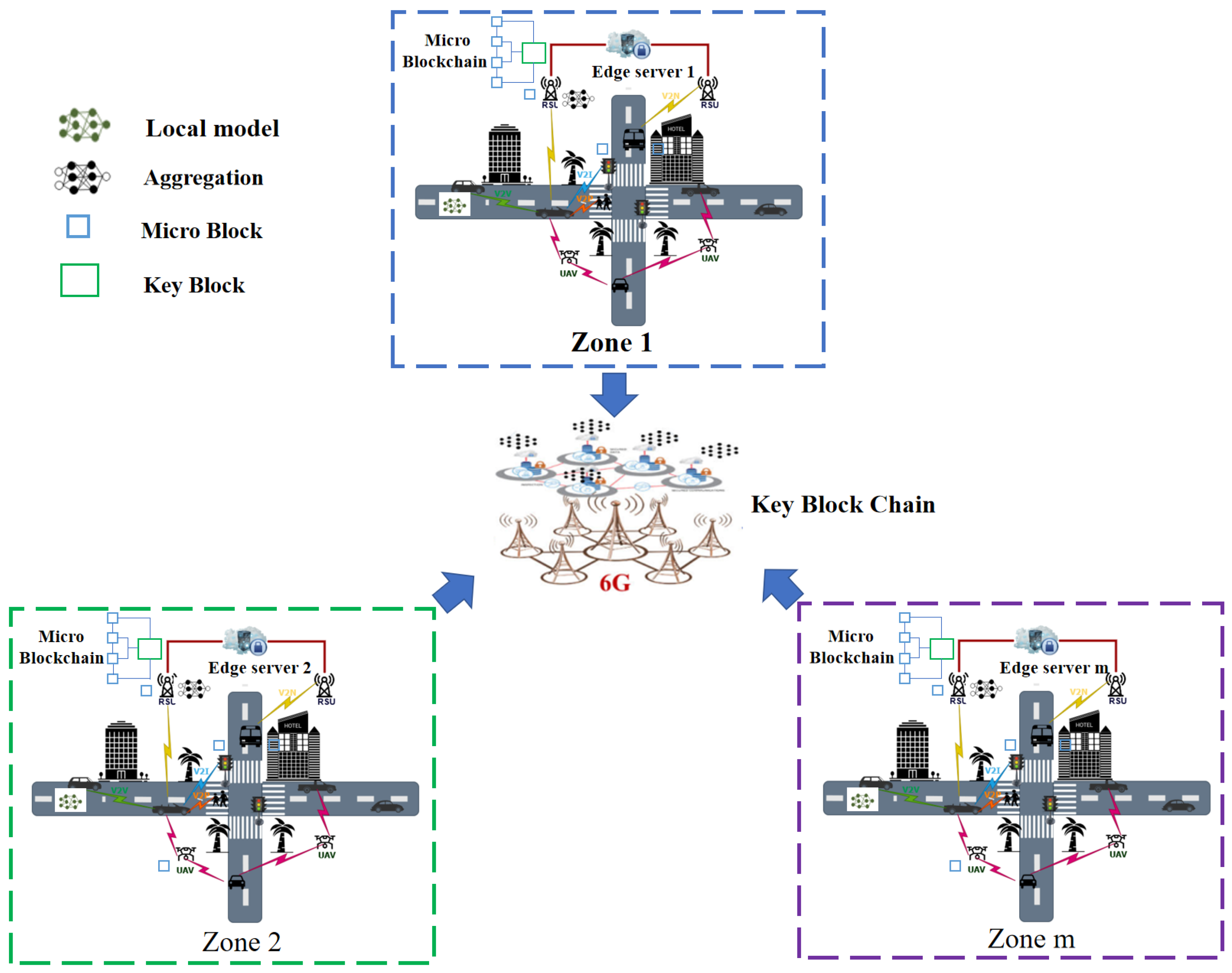
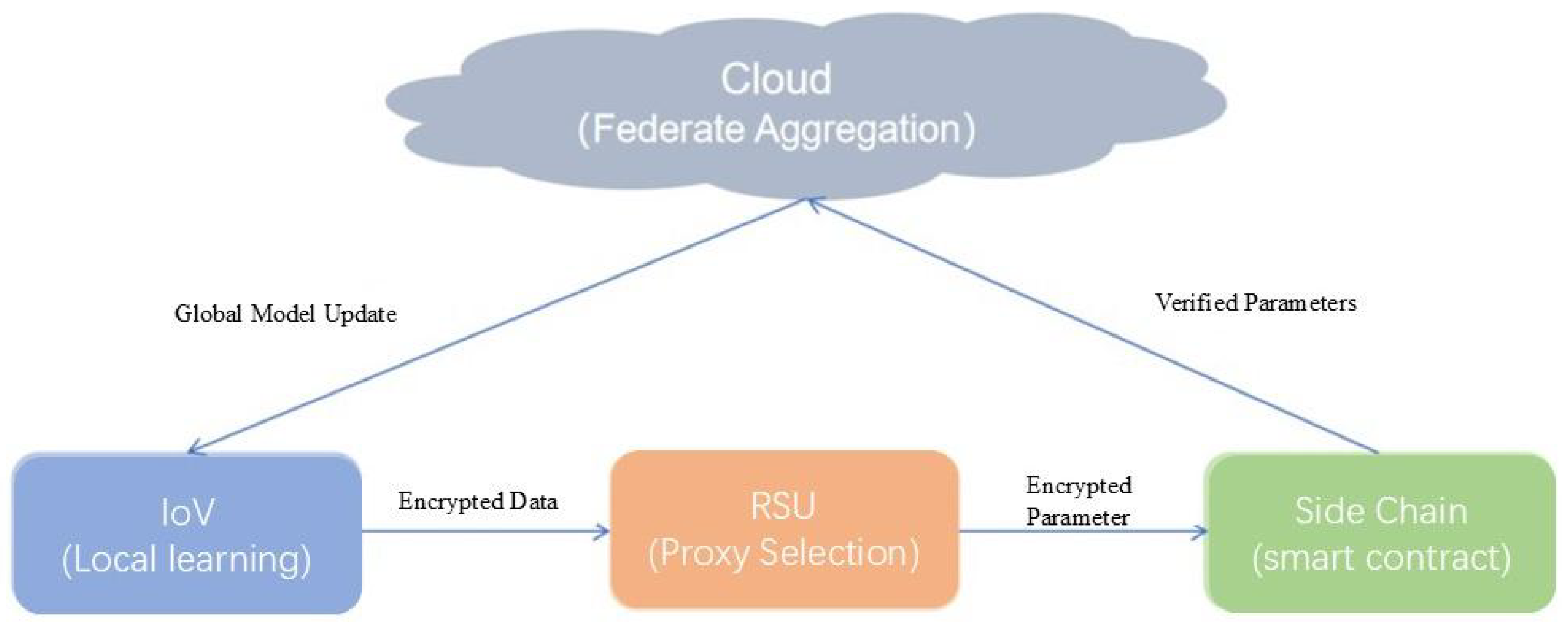
Figure 4 illustrates the Vehicle–Road–Cloud integrated architecture combining the blockchain and FL in the 6G era. To manage the network’s complexity and ensure scalability, the architecture is partitioned into two distinct blockchain layers. Within a specific geographic zone, IoVs, Roadside Units (RSUs), and other local devices form a micro blockchain. This local chain is optimized for high-frequency, low-latency operations, such as real-time data exchange, local model training, and initial participant authentication. Concurrently, edge servers from multiple zones are interconnected via the 6G backbone to form the key blockchain. This higher-level chain serves as the system’s global source of truth, responsible for inter-zone data synchronization, secure aggregation of the global model, and maintaining a tamper-proof record of significant network-wide events. This hierarchical structure effectively balances local efficiency with global consistency and security.
In a specific road segment, the edge server first uses secret sharing technology under the public infrastructure system to split the original secret into n sub-secrets and distribute them to multiple nearby IoVs. These vehicles, which receive the sub-secrets, can act as proxy vehicles for the RSU. Using the (t,n) threshold scheme, multiple proxy vehicles can reassemble the original secret value. This value, combined with the information of vehicles entering the current road segment and other authentication information, serves as credentials for participating in the formation of a collaborative proxy authentication group. Each vehicle entering a specific road segment corresponds to an authentication group, and a single proxy vehicle can participate in the authentication of multiple proxy groups. Furthermore, to ensure information security between different areas, edge servers are interconnected to form a key blockchain. This key blockchain provides the decentralized architecture for information sharing and verification among various regions. By utilizing the key blockchain, edge servers can securely exchange and validate information, ensuring that data integrity and privacy are maintained across the entire network. This approach not only enhances the security of data communication but also builds a robust and trustworthy infrastructure for the IoV in a 6G environment. Through this interconnected system, the key blockchain facilitates seamless and secure collaboration between different regions, ultimately contributing to a more efficient and reliable IoV network.
For the federated learning process, the IoVs gather their personal information during road trips, and the training process is implemented locally. For instance, for the purpose of assessing road traffic congestion conditions in different zones. Road participant detection and classification can be conducted in IoVs. The edge server can coordinate the information from the IoVs, and traffic information can be estimated by combining different zone information. The aggregator consolidates all local models and sends a global model back to all nodes for retraining and updating their local models. This process is repeated for several iterations until the global model achieves the minimum possible loss function. The loss function for the global model is defined as follows.
where
represents the training parameters of the global model, which is deployed in the central cloud platform, and
represents the parameters of the local model with edge node i. In detail, the loss functions for Mean Squared Error (MSE) can be described as below.
where
M denotes the scale of test data, and
and
represent the real and estimated outputs with the pretrained model, respectively.
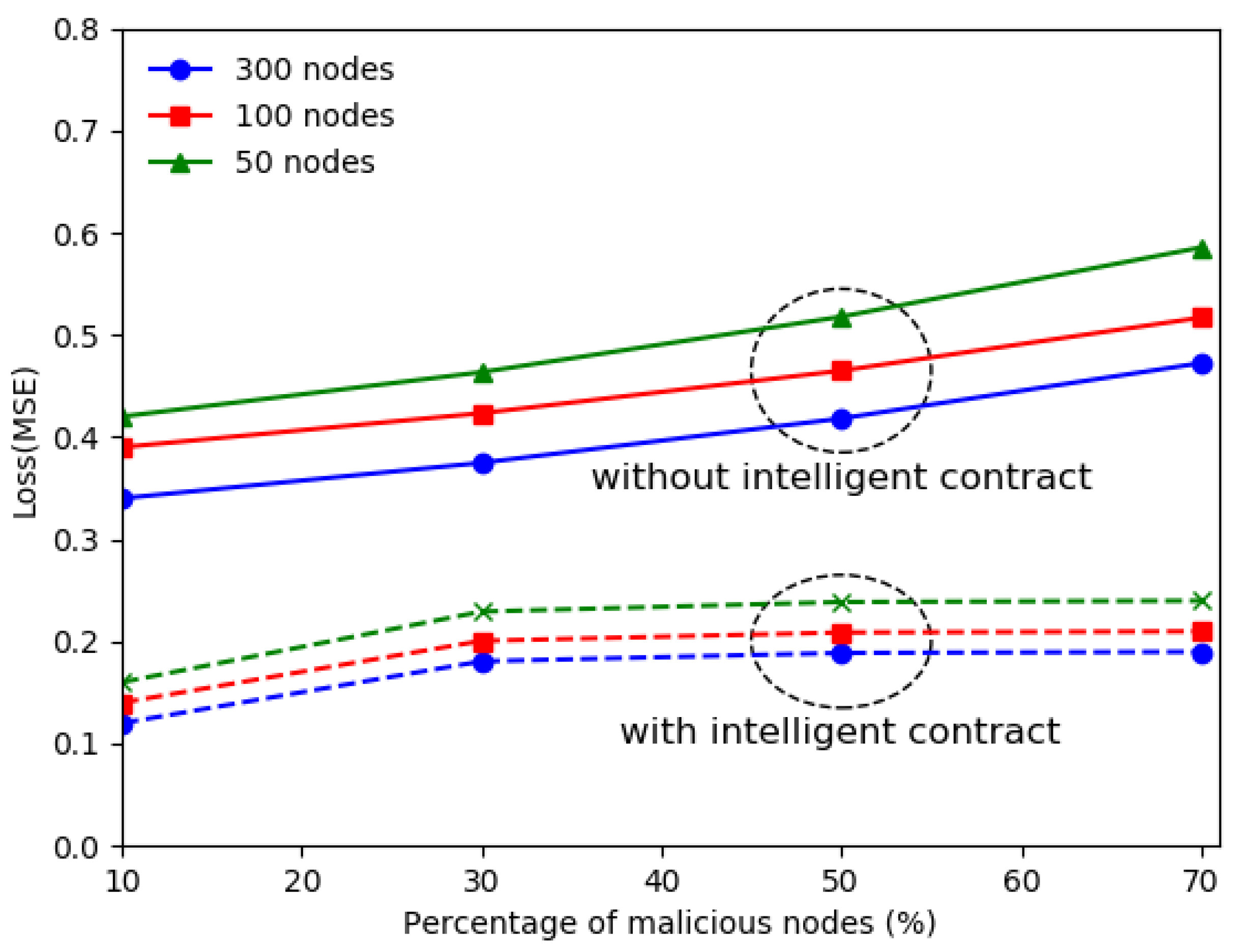
For the model training process, a malicious node might intentionally alter the training data or parameters of the local model to generate incorrect results. To safeguard local models against such malicious activities, they must be submitted to the blockchain only after undergoing a consensus algorithm. The local model can be deemed trustworthy if the trainer’s trust rating surpasses a specific threshold. Trusted neighboring nodes can also verify the pretrained local model using their captured history data and compare the outcomes with the real results. Alternatively, a smart contract can automatically verify the local model against pre-recorded data and real measured results. In this study, the machine learning technique, the random forest method, within a smart contract can be used to detect inaccuracies or anomalies in local models. The customized blockchain architecture with parallel zone blocks is used for the specific model deployment.
To safeguard the integrity of the model training process in federated learning, a malicious node might intentionally tamper with training data or local model parameters to produce erroneous results. To mitigate such threats, local models must be submitted to the blockchain only after validation through a robust consensus algorithm. In this study, a Proof-of-Trust (PoT) consensus mechanism is used, where nodes collectively evaluate the trustworthiness of a submitted local model based on predefined criteria. The PoT algorithm leverages a trust rating system, where each trainer node is assigned a dynamic trust score derived from its historical behavior, including the accuracy of prior model submissions and adherence to protocol rules. A local model is deemed trustworthy only if the trainer’s trust rating exceeds a predefined threshold, set dynamically based on the network’s security requirements.
To further ensure model integrity, trusted neighboring nodes can validate the pretrained local model by re-evaluating it against their locally stored historical data. These nodes compare the model’s predictions with real-world outcomes, calculating metrics such as Root Mean Square Error (RMSE) to quantify deviations. A model is flagged as suspicious if its performance deviates significantly from expected results. Alternatively, a smart contract can automate this verification process by executing predefined validation logic. The smart contract retrieves pre-recorded ground-truth data and real measured outcomes from the blockchain’s immutable ledger, runs the local model on this data, and computes performance metrics to detect inconsistencies. In this study, the Random Forest machine learning algorithm is integrated into the smart contract to detect anomalies in local models. The Random Forest classifier is trained on features such as model prediction errors, parameter distributions, and metadata, enabling it to identify patterns indicative of tampering or inaccuracies with high precision.
Rather than relying on a central node, certain authorized nodes, like an edge server, can function as aggregators. These nodes are tasked with regularly updating their blockchain copies until they have gathered the specific number of local models. Among the multiple aggregators, the central cloud platform first collects the required number of local models, then combines these local models to create the critical global model and adds the local model to the blockchain as a key block for the global model training. The training of a global model for each iteration can be addressed with the federated learning process. This procedure is repeated until the global model meets the real estimation requirements or achieves the intended trained loss function as described in Equation (
2).
The proposed system operates on a customized blockchain architecture featuring parallel zone blocks to optimize model deployment and scalability. The blockchain is partitioned into multiple zones, each managing a subset of nodes and their corresponding local models. Each zone operates a sub-chain with its own consensus process, reducing latency and computational overhead compared with a single global chain. Zone blocks are periodically synchronized with the main blockchain to ensure global consistency, using a cross-zone validation protocol where inter-zone nodes verify the integrity of aggregated models.
4. The CPRE-IoV Algorithm
Building on the architecture described in
Section 3, this section presents the core algorithmic innovation of the framework: the Cloud Proxy Re-Encryption Offloading (CPRE-IoV) algorithm. To provide clarity on the interaction between processes, this section details the precise sequence of operations, showing how blockchain validation is integrated with the CPRE-IoV offloading workflow. This algorithm is designed to ensure secure and efficient data handling in the face of high vehicle mobility and stringent privacy requirements. The conceptual workflow of CPRE-IoV is first outlined, followed by a detailed algorithmic implementation.
4.1. Cloud Proxy Re-Encryption Offloading Workflow
To address the high mobility of vehicle nodes and stringent data privacy requirements in Internet of Vehicles (IoV) scenarios, the blockchain-based Cloud Proxy Re-Encryption Offloading Algorithm (CPRE-IoV) is proposed. The core workflow and technical features are illustrated in
Figure 5.
The CPRE-IoV algorithm is designed to address the unique challenges of the IoV, where high mobility and stringent data privacy demands necessitate innovative solutions. By integrating blockchain technology and advanced cryptographic techniques, it ensures secure and efficient data handling across dynamic vehicular networks. This section outlines the key steps and technical features that underpin its functionality.
On-Vehicle Data Encryption and Local Training
Dynamic Proxy Node Selection and Optimization
Hierarchical Re-Encryption and On-Chain Verification
Federated Aggregation and Vehicle Model Updates
Together, these steps form a robust framework that balances security, efficiency, and scalability in IoV environments. This approach not only protects sensitive data but also enables real-time collaboration, paving the way for advanced vehicular applications.
4.2. Implementation and Algorithmic Refinements
Following the foundational framework outlined previously, this subsection details the practical implementation and algorithmic refinements of the CPRE-IoV workflow, which is formalized in Algorithm 1. The algorithm orchestrates the process for a single training round from the perspective of an individual vehicle. As such, its primary inputs include the specific vehicle’s index (k), its private local sensor data (), a set of currently available proxy nodes (), and the total number of vehicles (K) participating in the collaborative task. By executing the multi-phase workflow of secure local training, intelligent proxy selection, and robust aggregation, the algorithm’s ultimate output is the newly updated global model (), which encapsulates the collective intelligence of the network for that round.
The process begins at the individual vehicle level. Each vehicle first secures its locally gathered sensor data using its public key for encryption. This critical step ensures that raw data never leaves the vehicle in plain text, forming the foundation of our privacy-preserving approach. Subsequently, the vehicle leverages a hardware-based Trusted Execution Environment (TEE) to train its local machine learning model. This produces a set of model parameters, or updates, within an isolated and tamper-resistant environment, protecting the training process from local interference.
The core of our algorithm’s efficiency in a highly dynamic vehicular environment lies in its intelligent proxy selection mechanism. Rather than simply offloading to the nearest Roadside Unit (RSU), the vehicle dynamically evaluates a set of potential proxy nodes available in its vicinity. For each candidate proxy, a holistic ‘cost’ score is computed. This score intelligently balances the proxy’s real-time network performance (such as its available bandwidth and latency) with the vehicle’s own state (specifically its velocity, which indicates how long the connection might last) and, most importantly, the proxy’s trustworthiness. This trust is represented by a reputation score recorded immutably on the blockchain, ensuring that only reliable and well-behaved nodes are chosen for the critical task of data offloading. This multi-faceted approach prevents vehicles from connecting to congested or untrustworthy nodes, thereby enhancing both speed and security.
Once the optimal proxy is selected, the encrypted local model is securely offloaded, and its integrity is verified on-chain via a smart contract-based consensus check. The final phase involves the federated aggregation of multiple such verified models. To defend against model poisoning attacks and mitigate the impact of low-quality contributions, our framework employs a reputation-weighted averaging scheme. In this scheme, the influence of each local model on the new global model is proportional to both the size of its training dataset and the historical reputation of the contributing vehicle. This ensures that trustworthy nodes with more data have a greater, more positive impact. Finally, to optimize bandwidth for the demanding V2X environment, the updated global model undergoes adaptive compression before being broadcast back to all participating vehicles, thus completing one robust and efficient cycle of collaborative learning.
| Algorithm 1 CPRE-IoV Secure Offloading and Aggregation Workflow |
- 1:
▹ Encrypt local data using vehicle’s public key - 2:
▹ Train local model inside a TEE
- 3:
- 4:
- 5:
for all proxy do - 6:
if then - 7:
- 8:
if then - 9:
- 10:
- 11:
end if - 12:
end if - 13:
end for
- 14:
▹ Re-encrypt model for the selected proxy - 15:
- 16:
- 17:
if then return “Verification Failed” - 18:
end if
- 19:
- 20:
- 21:
for
do - 22:
- 23:
end for - 24:
- 25:
return
|
6. Conclusions and Future Work
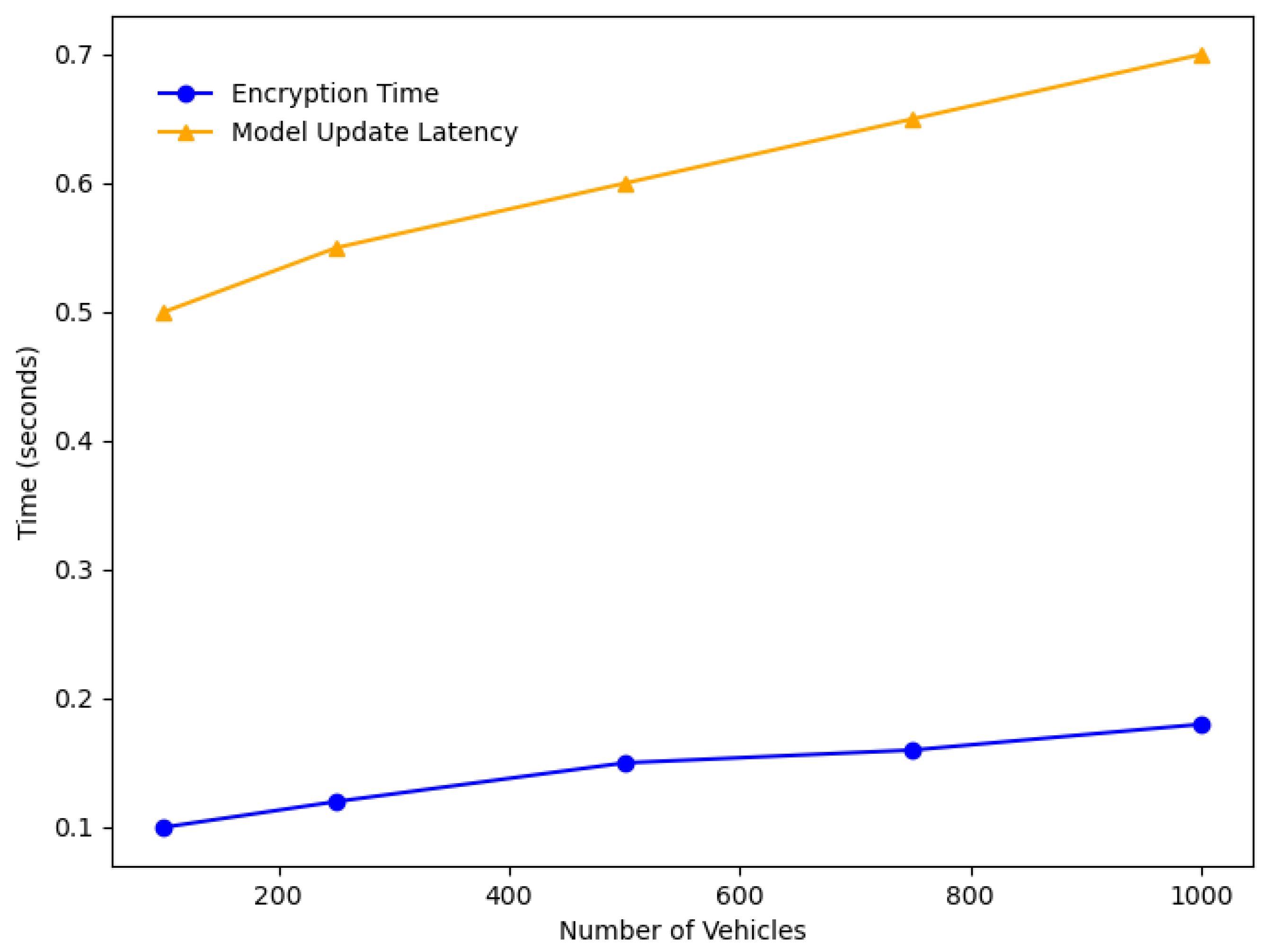
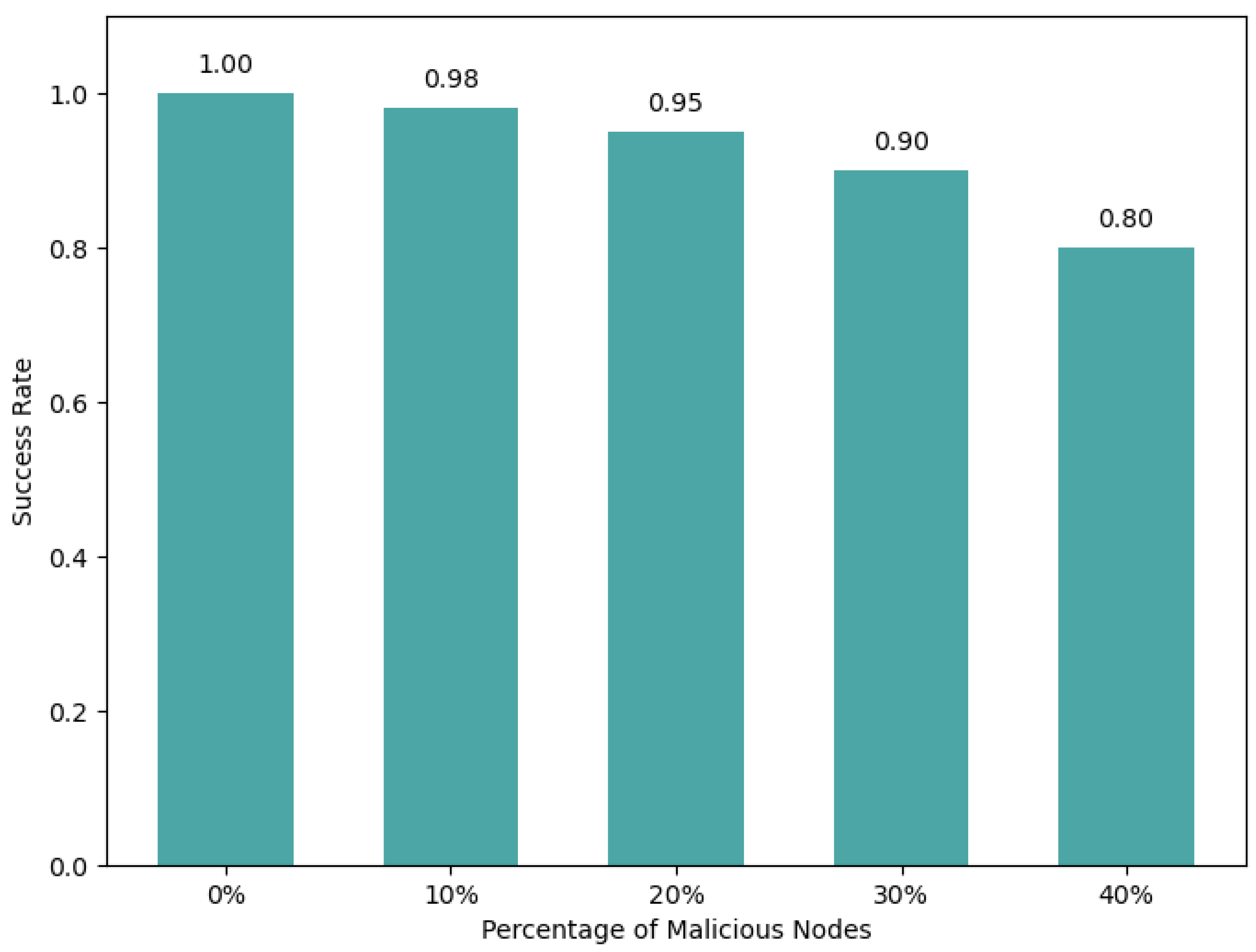
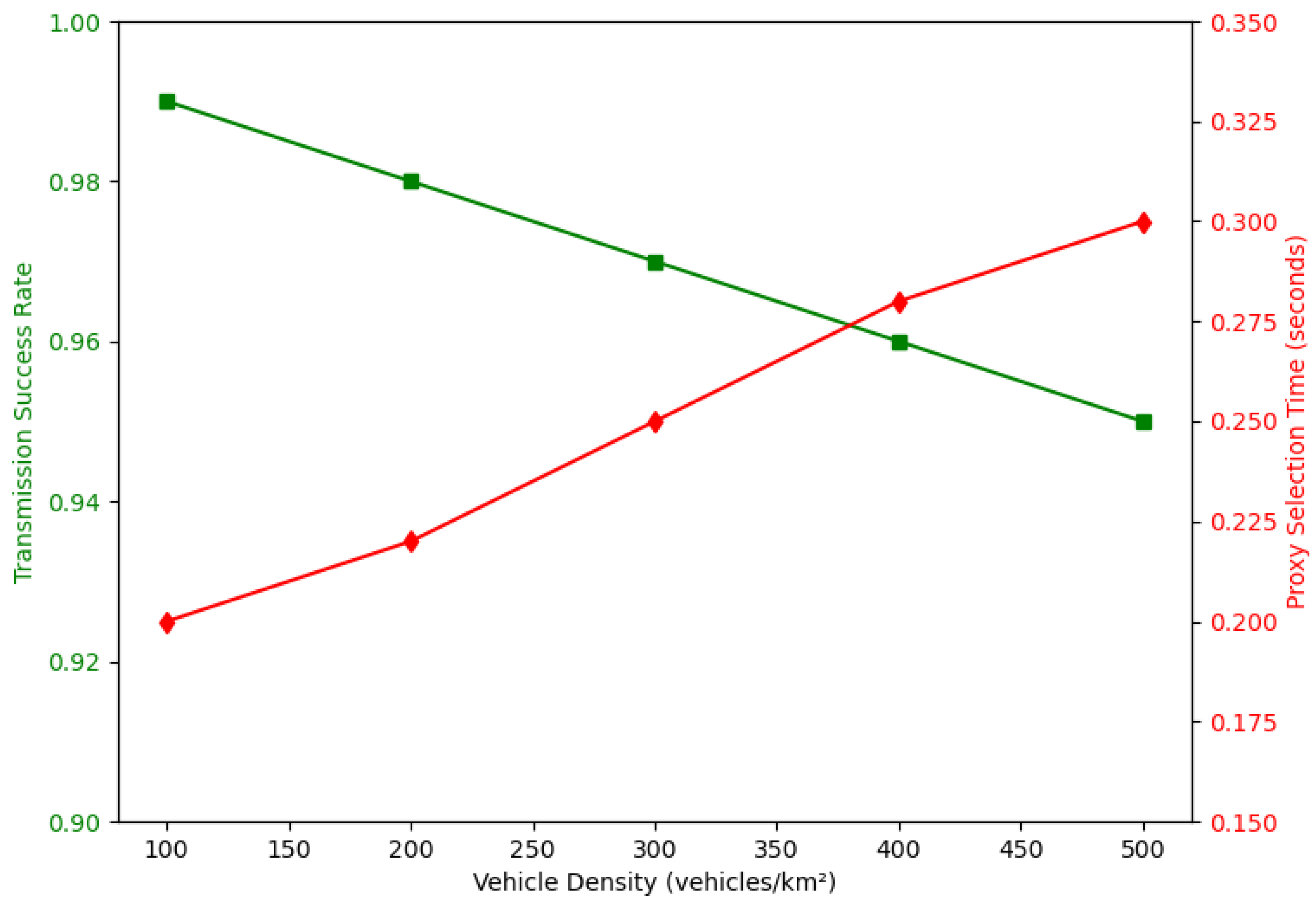
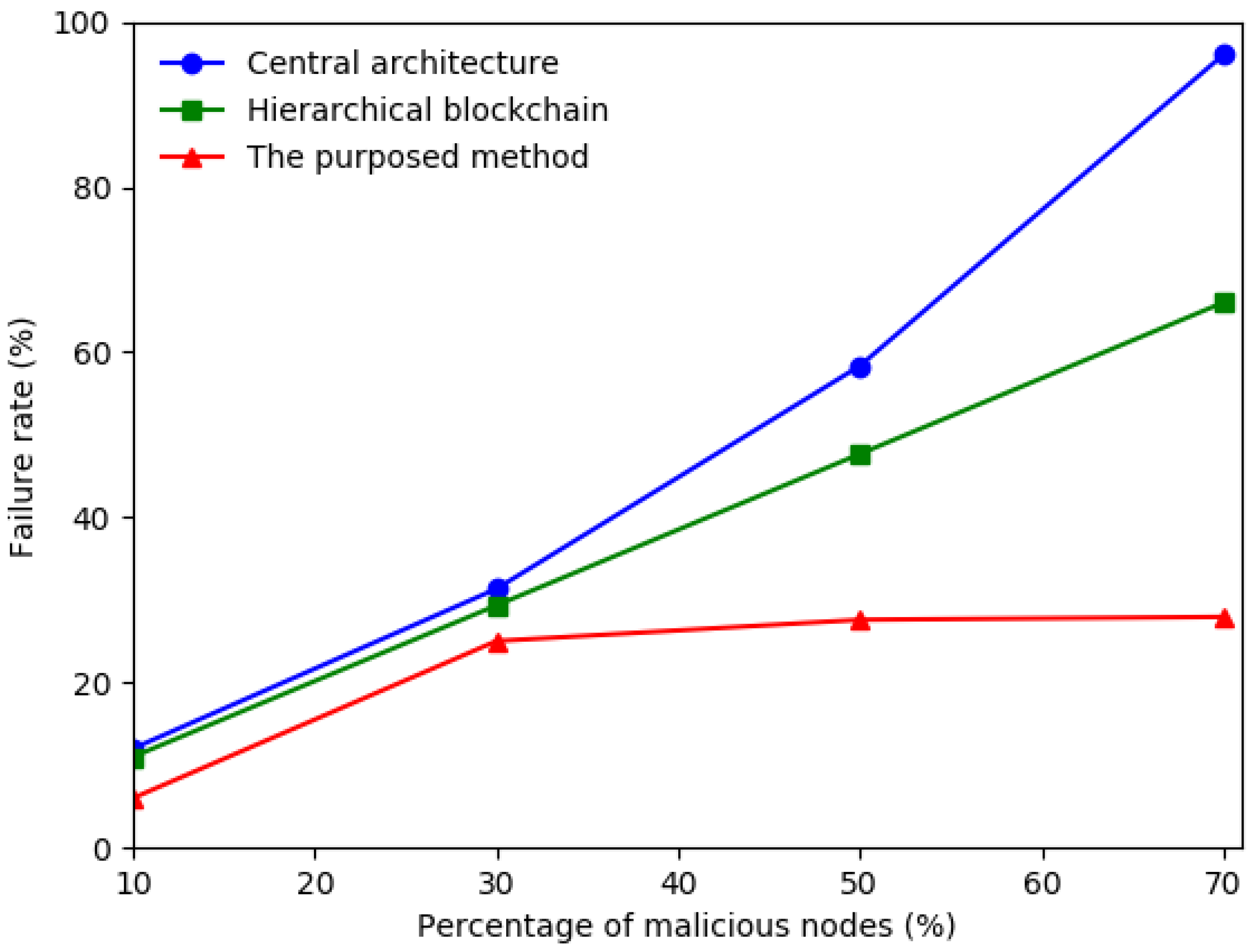
In conclusion, this paper has explored the significant security challenges in the IoV landscape, proposing a robust solution by integrating blockchain and FL technologies. The effectiveness of our framework rests on three core principles: first, a partitioned blockchain architecture that segregates local and global trust management to ensure scalability; second, the synergistic integration of privacy-preserving federated learning with a robust smart contract-based verification mechanism; and third, an intelligent proxy re-encryption offloading algorithm that dynamically adapts to the high-mobility nature of vehicular networks. The proposed architecture demonstrates how these technologies can support the secure and efficient exchange of data, meeting the stringent requirements of real-time processing and massive data handling in autonomous vehicles. Our simulation results, including a direct comparison with state-of-the-art frameworks like SecBFL-IoV, have quantitatively demonstrated our system’s superior performance in terms of both security and efficiency, particularly in reducing latency in large-scale, dynamic environments.
Despite the promising results, this study has several limitations that open avenues for future work. The evaluation relies on a simulated environment; while sophisticated, it may not capture all the unpredictable complexities of real-world network conditions, signal interference, and hardware constraints. Furthermore, while the architecture is designed for scalability, its performance with millions of nodes in a true city-scale deployment requires further investigation, particularly concerning the consensus overhead of the blockchain component. The computational overhead of the cryptographic operations, although optimized, could also pose a challenge for older, resource-constrained vehicle on-board units.
Future work should focus on addressing these limitations and expanding the framework’s capabilities. This includes investigating lightweight blockchain protocols and efficient FL algorithms that can handle the massive data volumes and real-time processing demands of autonomous vehicles without compromising on speed or security. A primary goal is to deploy the framework on a physical testbed with real vehicles to validate its real-world performance. Another promising avenue is extending the framework to support a wider range of smart city applications beyond security, such as real-time traffic management, cooperative mobility services, and predictive road maintenance, fostering a deeper integration between V2X systems and urban infrastructure. As 6G technology continues to evolve, ensuring interoperability between different IoV systems and adhering to emerging standards will be critical.