Effective Consensus-Based Distributed Auction Scheme for Secure Data Sharing in Internet of Things
Abstract
:1. Introduction
- A consensus-based distributed reverse auction framework for data sharing is proposed, where symmetric participants are grouped into clusters for privacy, and they reach consensus on the auction result without relying on any fully trusted or semi-trusted auctioneers;
- An incentive compatible privacy-preserving reverse auction mechanism is proposed to prompt data owners to share their data without worrying about privacy leakages. Differential privacy, symmetric encryption and zero-knowledge proofs are incorporated to design the auction mechanism, and a trade-off between privacy preservation and social efficiency of the auction is made;
- An effective hybrid consensus algorithm is constructed, where different kinds of witnesses are selected using anonymous verifiable random functions without peer interactions, and different operations can be conducted in parallel by varying witnesses. In this way, bidders reach consensus on the auction result with low computation costs without performing the auction processes repeatedly.
2. Related Works
2.1. Auction for Data Sharing in IoT
2.2. Blockchain for Data Sharing in IoT
3. Preliminaries
3.1. Traceable Ring Signature
- Gen: this takes security parameter and outputs a public/secret-key pair .
- Sig: this takes a secret key, , where , a tag , and a message and outputs signature .
- Ver: this takes tag , message , and signature and outputs a bit.
- Trace: this takes tag and two message/signature pairs, and outputs one of the following strings: “indep”, “linked”, or , where .
3.2. Distributed Laplacian Perturbation
3.3. Pedersen Commitment
- Com: this commits to a message using blinding factor and outputs .
- Vfy: this verifies whether X commits to x with blinding factor r and outputs ⊤ on success; otherwise, it outputs ⊥.
3.4. Zero-Knowledge Range Proof
- : this takes as the security parameter, n as the range bit-width, and m as the vector cardinality and outputs as the common reference string (CRS).
- : this takes a commitment X along with the opening vectors x and r and generates an argument to prove
- : this returns ⊤ if it accepts ; otherwise, it returns ⊥.
3.5. Anonymous Verifiable Random Function
- : this chooses a generator g of a group of order p such that . It then samples a random and outputs , where .
- : this computes and and outputs .
- : this outputs 1 if and verifies, and 0 otherwise.
- : this chooses a random , computes , sets , and outputs .
4. System Model and Design Goals
4.1. System Model
4.2. Threat Model and Design Goals
- (1)
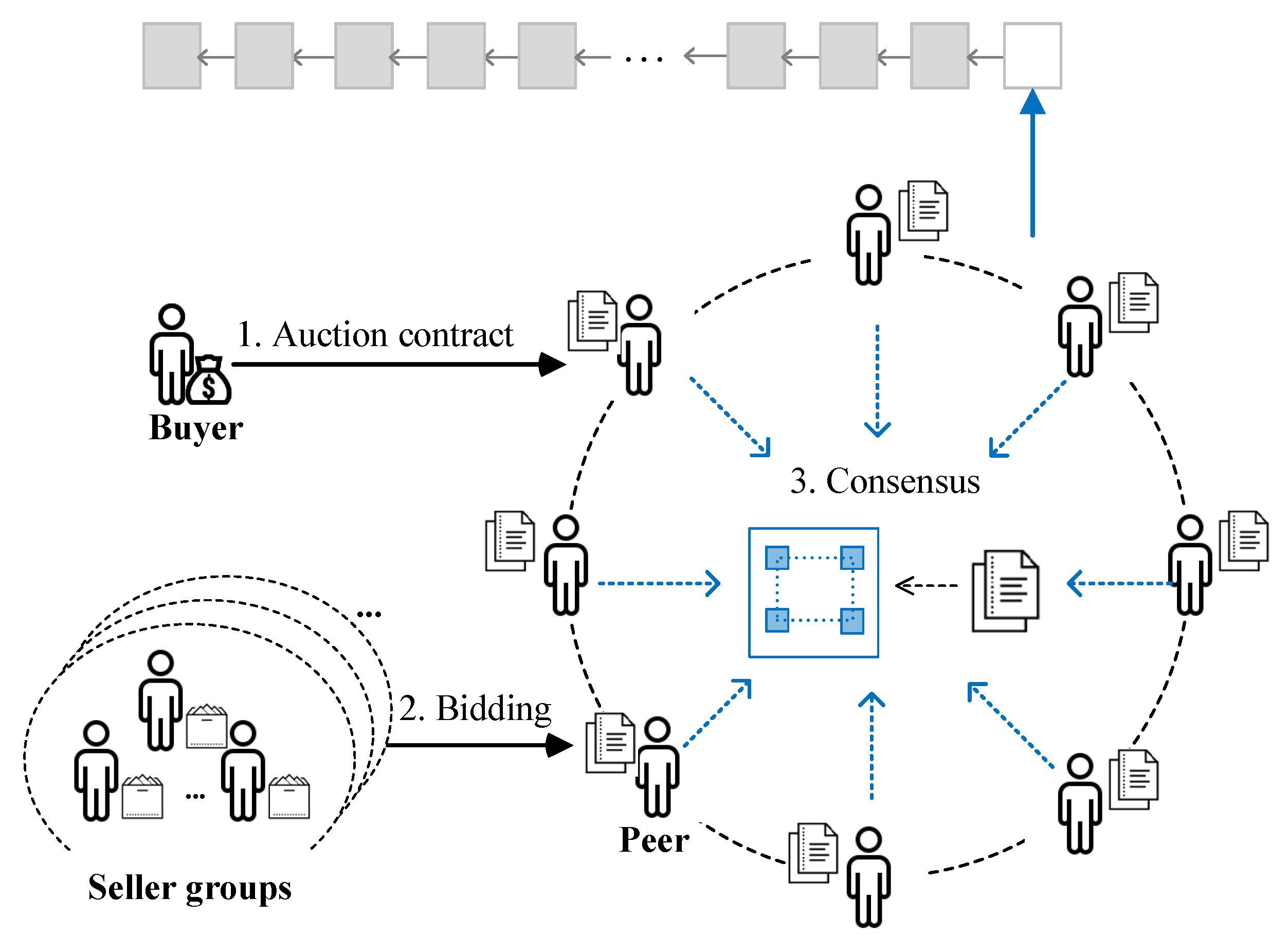
- Distributed Auction.All participants are in a symmetric structure. Auction allocation and pricing do not depend on trusted third parties. Bidders reach consensus on the auction result in a P2P manner with the assistance of smart contracts.
- (2)
- Privacy Preservation.First, the real identities of the data providers and data consumers participating in the auction are hidden and cannot be inferred from the user account address, public key, signature and other information. Second, bidders submit their own bids without knowing others’ valuation, and all bids remain private throughout the auction process.
- (3)
- Incentive Compatibility.The bidders can obtain highest utility if and only if they submit their bids truthfully.
- (4)
- Collusion Resistance.Bidders can not collude together to manipulate the auction results for illicit profit. Peer nodes are prevented from colluding to announce false auction results for unfair profits.
- (5)
- Efficiency.The overhead realizing the above goals should be acceptable from the perspective of system users. The consensus process should minimize communication and computation overhead instead of repeating the costly auction assignment and verification calculation by all miners.
5. Effective Consensus-Based Distributed Reverse Auction
5.1. Preparation Stage
| Algorithm 1 Bidder Grouping and Key Establishment |
| Input: Seller registration information, pseudo-random function (PRF), ; Output: , seller groups;
|
5.2. Auction Stage
| Algorithm 2 Bidding Information Processing and Valid Price Determination |
| Input: Bidding information , the number of clusters , the acceptable price of buyer Output: Group average bid , group supply volume , valid price
|
5.2.1. Bidding
5.2.2. Auction Allocation
- (i)
- The valuation and supply of a seller group is recorded as , respectively. Then, the seller groups’ valuations are arranged in ascending order.
- (ii)
- Plot the supply of seller groups versus the valuation of seller groups in ascending order. Similarly, plot the revealed acceptable price of buyer in the same figure. The intersection shows the valid price . It is defined as the key price of winning sellers. Finally, a bidder wins if, and only if, his bid value is smaller than the key price: .
- (i)
- Winning sellers prove that their committed bid values are indeed smaller than the valid price, i.e., .
- (ii)
- The proofs are verified according to the on-chain commitment. Bidders who can provide valid proofs are the final winners. The winners are saved to the set .
5.3. Consensus Stage
5.3.1. Witness Selection
| Algorithm 3 Witness selection. |
| Input: ; Output: ;
|
5.3.2. Auction Allocation by Proposer
5.3.3. Verification by Validators
| Algorithm 4 Validator verification. |
| Input: ; Output: , ;
|
6. Theoretical Analysis
6.1. Privacy Preservation
6.2. Incentive Compatibility
6.3. Collusion Resistance
7. Performance Analysis
7.1. Computation and Communication Cost
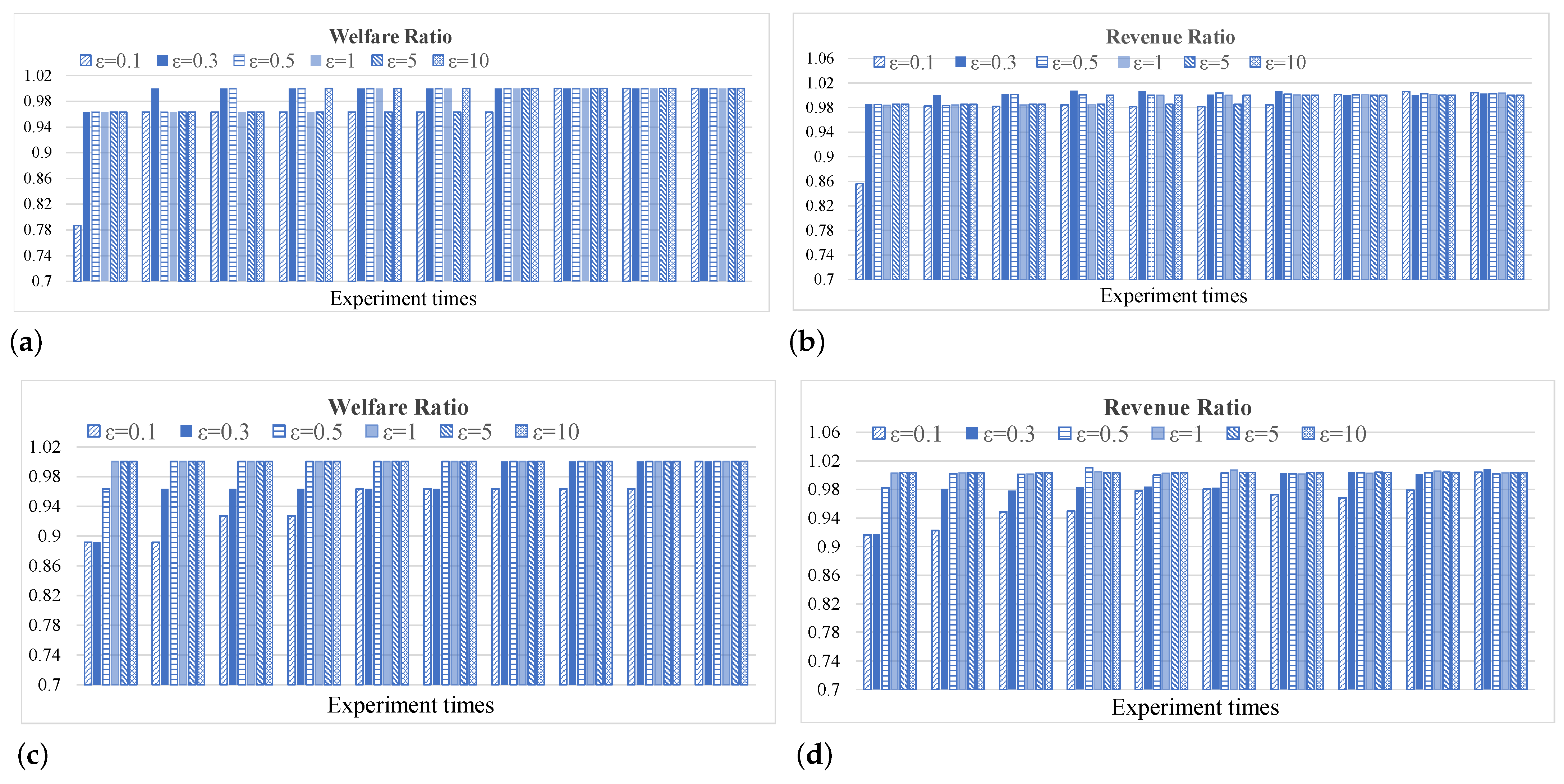
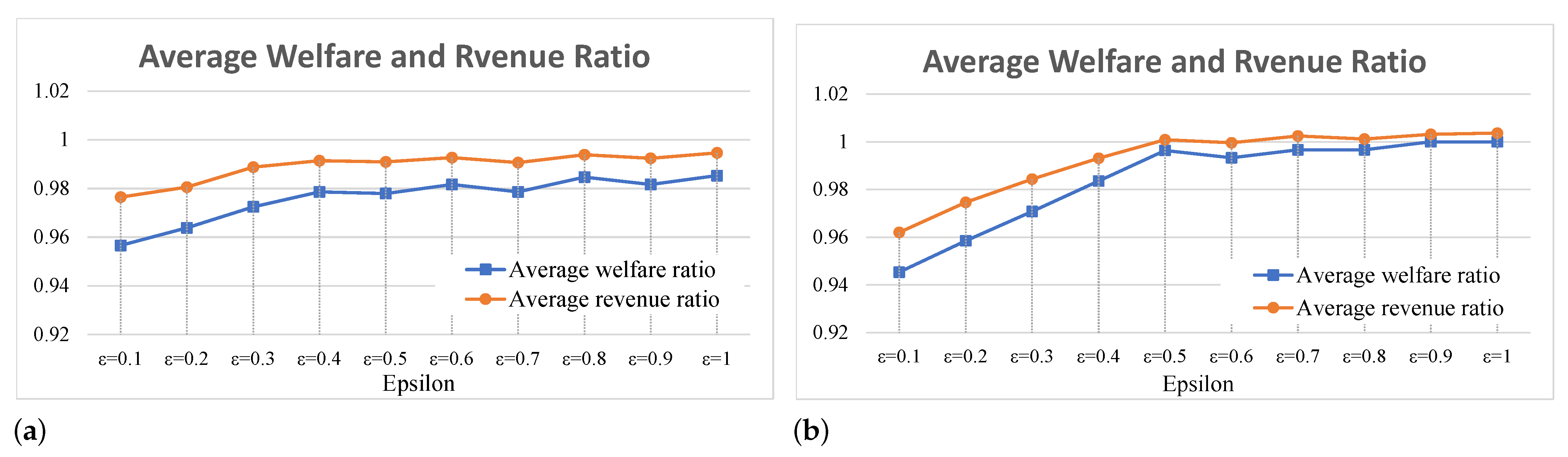
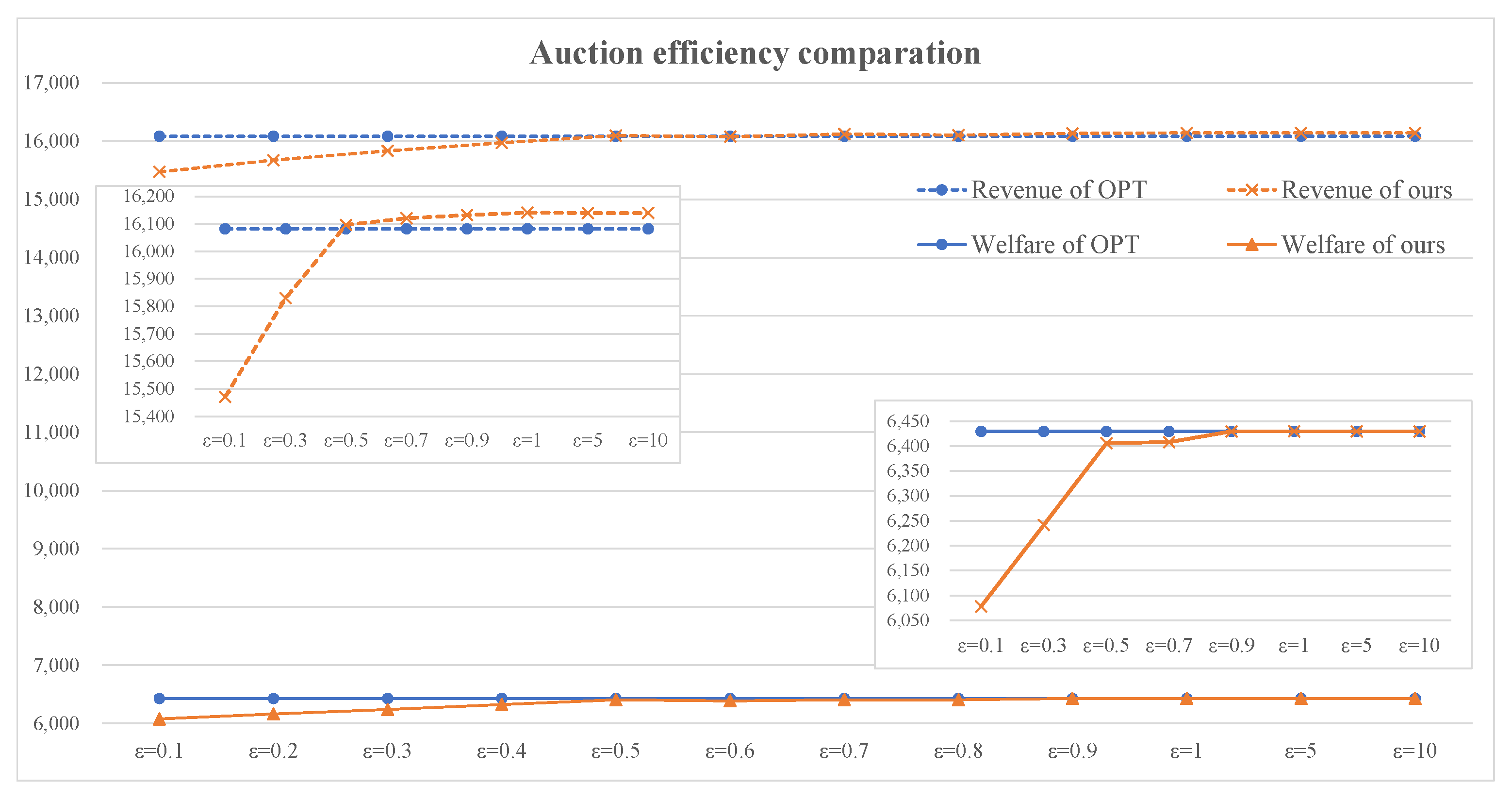
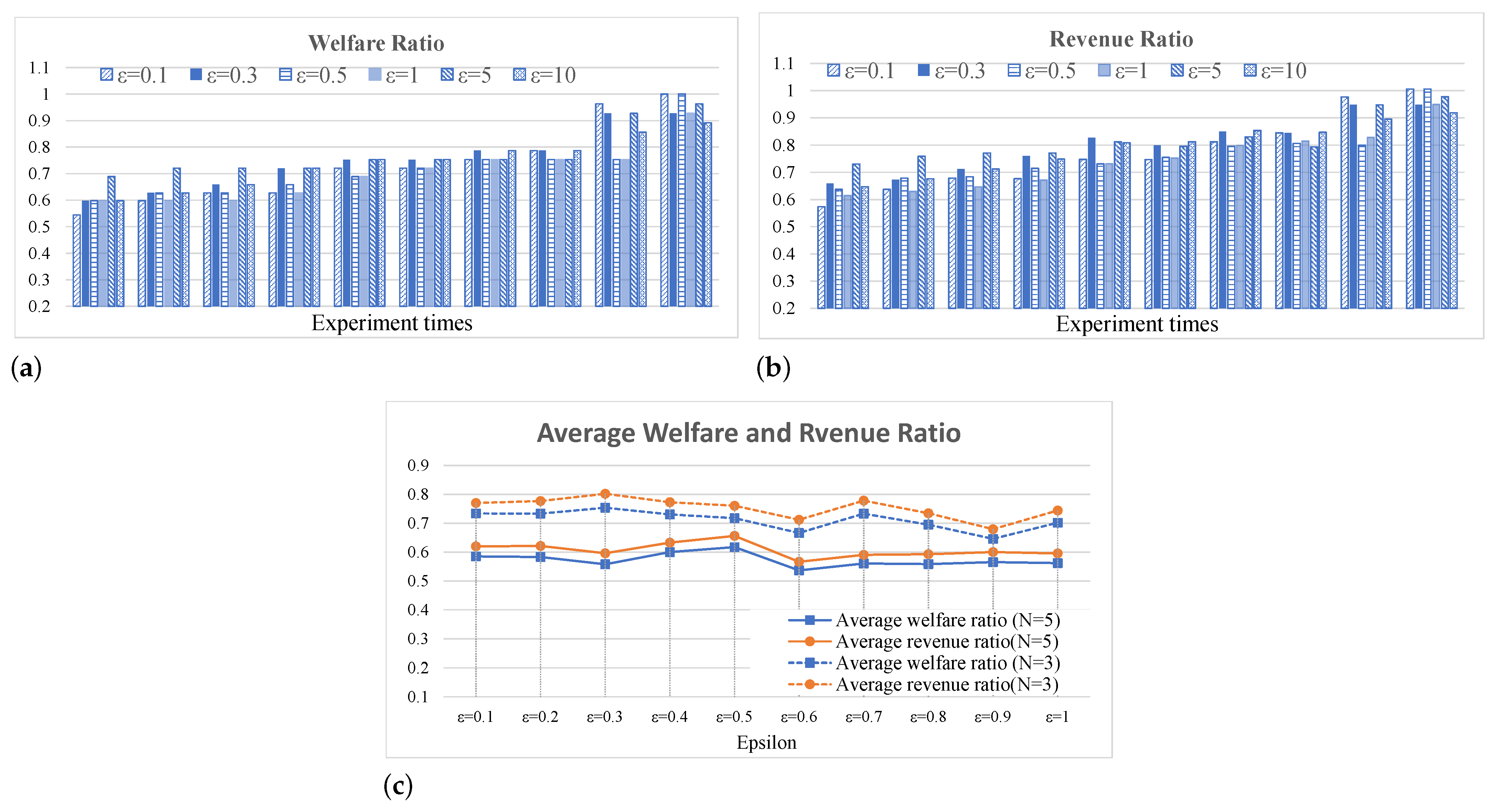
7.2. Trade-Off between Privacy and Social Efficiency
7.3. Deployment and Execution Cost
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Liang, F.; Yu, W.; An, D.; Yang, Q.; Fu, X.; Zhao, W. A survey on big data market: Pricing, trading and protection. IEEE Access 2018, 6, 15132–15154. [Google Scholar] [CrossRef]
- Byabazaire, J.; O’Hare, G.; Delaney, D. Data quality and trust: Review of challenges and opportunities for data sharing in iot. Electronics 2020, 9, 2083. [Google Scholar] [CrossRef]
- An, D.; Yang, Q.; Yu, W.; Li, D.; Zhang, Y.; Zhao, W. Towards truthful auction for big data trading. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–7. [Google Scholar]
- Cao, X.; Chen, Y.; Liu, K.R. Data trading with multiple owners, collectors, and users: An iterative auction mechanism. IEEE Trans. Signal Inf. Process. Netw. 2017, 3, 268–281. [Google Scholar] [CrossRef]
- Gao, W.; Yu, W.; Liang, F.; Hatcher, W.G.; Lu, C. Privacy-preserving auction for big data trading using homomorphic encryption. IEEE Trans. Netw. Sci. Eng. 2020, 7, 776–791. [Google Scholar] [CrossRef]
- Feng, Z.; Chen, J.; Liu, T. An online truthful auction for iot data trading with dynamic data owners. In Proceedings of the International Conference on Collaborative Computing: Networking, Applications and Worksharing, Virtual Event, 16–18 October 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 554–571. [Google Scholar]
- Hou, L.; Zhao, S.; Xiong, X.; Zheng, K.; Chatzimisios, P.; Hossain, M.S.; Xiang, W. Internet of things cloud: Architecture and implementation. IEEE Commun. Mag. 2016, 54, 32–39. [Google Scholar] [CrossRef] [Green Version]
- Manzoor, A.; Braeken, A.; Kanhere, S.S.; Ylianttila, M.; Liyanage, M. Proxy re-encryption enabled secure and anonymous iot data sharing platform based on blockchain. J. Netw. Comput. Appl. 2021, 176, 1–17. [Google Scholar] [CrossRef]
- Jiang, T.; Fang, H.; Wang, H. Blockchain-based internet of vehicles: Distributed network architecture and performance analysis. IEEE Internet Things J. 2018, 6, 4640–4649. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet Things J. 2018, 6, 4660–4670. [Google Scholar] [CrossRef]
- Chen, C.; Wu, J.; Lin, H.; Chen, W.; Zheng, Z. A secure and efficient blockchain-based data trading approach for internet of vehicles. IEEE Trans. Veh. Technol. 2019, 68, 9110–9121. [Google Scholar] [CrossRef]
- Guo, J.; Ding, X.; Wang, T.; Jia, W. Combinatorial resources auction in decentralized edge-thing systems using blockchain and differential privacy. Inf. Sci. 2022, 607, 211–229. [Google Scholar] [CrossRef]
- Guo, J.; Ding, X.; Wu, W. A double auction for charging scheduling among vehicles using dag-blockchains. arXiv 2020, arXiv:2010.01436. [Google Scholar]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The blockchain model of cryptography and privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar]
- Su, Z.; Wang, Y.; Xu, Q.; Zhang, N. Lvbs: Lightweight vehicular blockchain for secure data sharing in disaster rescue. IEEE Trans. Dependable Secur. Comput. 2022, 19, 19–32. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N. Bsis: Blockchain-based secure incentive scheme for energy delivery in vehicular energy network. IEEE Trans. Ind. Inform. 2019, 15, 3620–3631. [Google Scholar] [CrossRef]
- Cao, X.; Chen, Y.; Liu, K.R. An iterative auction mechanism for data trading. In Proceedings of the 2017 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), New Orleans, LA, USA, 5–9 March 2017; pp. 5850–5854. [Google Scholar]
- Susanto, H.; Zhang, H.; Ho, S.-Y.; Liu, B. Effective mobile data trading in secondary ad-hoc market with heterogeneous and dynamic environment. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 645–655. [Google Scholar]
- Jiao, Y.; Wang, P.; Niyato, D.; Alsheikh, M.A.; Feng, S. Profit maximization auction and data management in big data markets. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Huang, Q.; Gui, Y.; Wu, F.; Chen, G.; Zhang, Q. A general privacy-preserving auction mechanism for secondary spectrum markets. IEEE/ACM Trans. Netw. 2015, 24, 1881–1893. [Google Scholar] [CrossRef]
- Wang, Q.; Huang, J.; Chen, Y.; Tian, X.; Zhang, Q. Privacy-preserving and truthful double auction for heterogeneous spectrum. IEEE/ACM Trans. Netw. 2019, 27, 848–861. [Google Scholar] [CrossRef]
- Cheng, K.; Wang, L.; Shen, Y.; Liu, Y.; Wang, Y.; Zheng, L. A lightweight auction framework for spectrum allocation with strong security guarantees. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Toronto, ON, Canada, 6–9 July 2020; pp. 1708–1717. [Google Scholar]
- Wang, Z.; Li, J.; Hu, J.; Ren, J.; Li, Z.; Li, Y. Towards privacy-preserving incentive for mobile crowdsensing under an untrusted platform. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 2053–2061. [Google Scholar]
- Cheng, K.; Tong, W.; Zheng, L.; Fu, J.; Mu, X.; Shen, Y. A secure and fair double auction framework for cloud virtual machines. IEEE Access 2021, 9, 87982–87994. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Deal: Differentially private auction for blockchain-based microgrids energy trading. IEEE Trans. Serv. Comput. 2019, 13, 263–275. [Google Scholar] [CrossRef]
- Brakerski, Z.; Vaikuntanathan, V. Efficient fully homomorphic encryption from (standard) lwe. SIAM J. Comput. 2014, 43, 831–871. [Google Scholar] [CrossRef]
- Li, M.; Weng, J.; Yang, A.; Lu, W.; Zhang, Y.; Hou, L.; Liu, J.-N.; Xiang, Y.; Deng, R.H. Crowdbc: A blockchain-based decentralized framework for crowdsourcing. IEEE Trans. Parallel Distrib. Syst. 2018, 30, 1251–1266. [Google Scholar] [CrossRef]
- Feng, J.; Liu, N.; Cao, J.; Zhang, Y.; Lu, G. Securing traffic-related messages exchange against inside-and-outside collusive attack in vehicular networks. IEEE Internet Things J. 2019, 6, 9979–9992. [Google Scholar] [CrossRef]
- Xiong, W.; Xiong, L. Anti-collusion data auction mechanism based on smart contract. Inf. Sci. 2021, 555, 386–409. [Google Scholar] [CrossRef]
- Li, M.; Weng, J.; Yang, A.; Liu, J.-N.; Lin, X. Toward blockchain-based fair and anonymous ad dissemination in vehicular networks. IEEE Trans. Veh. Technol. 2019, 68, 11248–11259. [Google Scholar] [CrossRef]
- Dai, W.; Dai, C.; Choo, K.-K.R.; Cui, C.; Zou, D.; Jin, H. Sdte: A secure blockchain-based data trading ecosystem. IEEE Trans. Inf. Forensics Secur. 2019, 15, 725–737. [Google Scholar] [CrossRef]
- Li, C.; Liang, S.; Zhang, J.; Wang, Q.-E.; Luo, Y. Blockchain-based data trading in edge-cloud computing environment. Inf. Process. Manag. 2022, 59, 102786. [Google Scholar] [CrossRef]
- Fujisaki, E.; Suzuki, K. Traceable ring signature. In Proceedings of the International Workshop on Public Key Cryptography, Beijing, China, 16–20 April 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 181–200. [Google Scholar]
- Ács, G.; Castelluccia, C. I have a dream!(differentially private smart metering). In Proceedings of the International Workshop on Information Hiding, Prague, Czech Republic, 18–20 May 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 118–132. [Google Scholar]
- Pedersen, T.P. Non-interactive and information-theoretic secure verifiable secret sharing. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 11–15 August 1991; Springer: Berlin/Heidelberg, Germany, 1991; pp. 129–140. [Google Scholar]
- Bünz, B.; Bootle, J.; Boneh, D.; Poelstra, A.; Wuille, P.; Maxwell, G. Bulletproofs: Short proofs for confidential transactions and more. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 315–334. [Google Scholar]
- Ganesh, C.; Orlandi, C.; Tschudi, D. Proof-of-stake protocols for privacy-aware blockchains. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, 19–23 May 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 690–719. [Google Scholar]
- Blass, E.O.; Kerschbaum, F. Strain: A secure auction for blockchains. In Proceedings of the European Symposium on Research in Computer Security, Barcelona, Spain, 3–7 September 2018; pp. 87–110. [Google Scholar]
- Kotz, S.; Kozubowski, T.; Podgórski, K. The Laplace Distribution and Generalizations: A Revisit with Applications to Communications, Economics, Engineering, and Finance; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2001. [Google Scholar]
- McSherry, F.; Talwar, K. Mechanism design via differential privacy. In Proceedings of the 48th Annual IEEE Symposium on Foundations of Computer Science (FOCS’07), Providence, RI, USA, 21–23 October 2007; pp. 94–103. [Google Scholar]
- Wu, S.; Chen, Y.; Wang, Q.; Li, M.; Wang, C.; Luo, X. Cream: A smart contract enabled collusion-resistant e-auction. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1687–1701. [Google Scholar] [CrossRef]
- Kaggle, Online Auctions Dataset: Modeling Online Auctions Dataset from Ebay. 2010. Available online: https://www.kaggle.com/datasets/onlineauctions/online-auctions-dataset (accessed on 1 July 2022).
- Goldberg, A. Competitiveness via consensus. In Proceedings of the 14th Annual ACM-SIAM Symposium on Discrete Algorithms, Baltimore, MD, USA, 12–14 January 2003; pp. 215–222. [Google Scholar]


| Entity | Preparation Stage | Auction Stage | Consensus Stage | ||||
|---|---|---|---|---|---|---|---|
| Key Establishment | Commitment | Perturbation | Cryptogram | Bulletproofs | |||
| Buyer | - | - | - | - | - | ||
| Bidders | 1 | - | |||||
| Witnesses | - | ||||||
| - | - | ||||||
| - | - | ||||||
| Entity | Preparation Stage | Auction Stage | Consensus Stage | ||||
|---|---|---|---|---|---|---|---|
| Overhead | Content | Overhead | Content | Overhead | Content | ||
| Buyer | - | - | |||||
| Bidders | - | - | |||||
| Witnesses | - | - | - | - | |||
| - | - | - | - | ||||
| - | - | - | - | ||||
| Entity | Function | Transaction Cost | Execution Cost | Total Cost | |
|---|---|---|---|---|---|
| Buyer | Publish contract | 619,778 | 619,778 | 1,239,556 | |
| Start auction | 46,998 | 46,998 | 93,996 | ||
| Bidder | Register | 110,034 | 110,034 | 220,068 | |
| Commit | 98,366 | 98,366 | 196,732 | ||
| Witness | Valid price | 43,544 | 43,544 | 87,088 | |
| Start voting | 73,791 | 73,791 | 147,582 | ||
| Vote | 72,331 | 72,331 | 144,662 | ||
| Start voting | 53,891 | 53,891 | 107,782 | ||
| Vote | 72,331 | 72,331 | 144,662 | ||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jia, X.; Song, X.; Sohail, M. Effective Consensus-Based Distributed Auction Scheme for Secure Data Sharing in Internet of Things. Symmetry 2022, 14, 1664. https://doi.org/10.3390/sym14081664
Jia X, Song X, Sohail M. Effective Consensus-Based Distributed Auction Scheme for Secure Data Sharing in Internet of Things. Symmetry. 2022; 14(8):1664. https://doi.org/10.3390/sym14081664
Chicago/Turabian StyleJia, Xuedan, Xiangmei Song, and Muhammad Sohail. 2022. "Effective Consensus-Based Distributed Auction Scheme for Secure Data Sharing in Internet of Things" Symmetry 14, no. 8: 1664. https://doi.org/10.3390/sym14081664
APA StyleJia, X., Song, X., & Sohail, M. (2022). Effective Consensus-Based Distributed Auction Scheme for Secure Data Sharing in Internet of Things. Symmetry, 14(8), 1664. https://doi.org/10.3390/sym14081664






