Abstract
In recent years, some general cryptographic technologies have been widely used in network platforms related to the national economy and people’s livelihood, effectively curbing network security risks and maintaining the orderly operation and normal order of society. However, due to the fast development and considerable benefits of quantum computing, the classical cryptosystem faces serious security threats, so it is crucial to analyze and assess the anti-quantum computing ability of cryptographic algorithms under the quantum security model, to enhance or perfect the design defects of related algorithms. However, the current design and research of anti-quantum cryptography primarily focus on the cryptographic structure or working mode under the quantum security model, and there is a lack of quantum security analysis on instantiated cryptographic algorithms. This paper investigates the security of AES-OTR, one of the third-round algorithms in the CAESAR competition, under the Q2 model. The periodic functions of the associated data were constructed by forging the associated data according to the parallel and serial structure characteristics of the AES-OTR algorithm in processing the associated data, and the periodic functions of the associated data were constructed multiple times based on the Simon quantum algorithm. By using the collision pair, two collision forgery attacks on the AES-OTR algorithm can be successfully implemented, and the period s is obtained by solving with a probability close to 1. The attacks in this paper caused a significant threat to the security of the AES-OTR algorithm.
1. Introduction
1.1. Background
The field of modern cryptography has changed dramatically since the quantum computer [1] was proposed in 1980. Research on quantum-resistant cryptosystems is also being accelerated internationally to meet the need of the post-quantum cryptography era. In 2016, the National Institute of Standards and Technology (NIST) publicly solicited quantum-resistant cryptographic algorithms worldwide and planned to formulate preliminary standards for quantum-resistant cryptography in 2022 to promote the standardization of quantum-resistant cryptographic algorithms. The security of some common block cipher structures and working modes has been demonstrated [2,3,4]. Recently, Chinese experts and scholars have conducted extensive cross-studies on the security analysis of cryptographic algorithm patterns and structures and the evaluation of attack resources under the quantum security model [5,6,7].
Quantum algorithms employ the coherence and superposition of quantum to accelerate computing and achieve parallel computing. Currently, commonly used quantum algorithms include the Shor algorithm [8], Simon algorithm [9], and Grover algorithm [10]. Among them, the Shor algorithm can solve large integer factorization and discrete logarithm problems in polynomial time, which seriously affect the security of RSA and Diffie–Hellman public-key cryptosystems. In the security analysis of symmetric cryptographic algorithms, Simon and Grover quantum search algorithms are often employed. The Grover algorithm is employed to search for a specific element from n unclassified elements. Since Simon’s algorithm is the simplest algorithm for determining the nontrivial periods, this study primarily uses the Simon algorithm.
Recently, based on the Simon and Grover algorithm, security analysis approaches such as quantum differential and linear analysis [11], quantum correlated key attack [12,13], and quantum sliding attack [14] have been proposed and applied. According to the work of Zhandry [15], the standard security model (Q1 model) and the quantum security model (Q2 model) are the two models for the quantum analysis of current cryptographic algorithms. In the Q1 model, the adversary can only collect and query data in a traditional way and employs quantum computers to process and calculate the data. In the Q2 model, the adversary queries the random oracle machine by constructing a quantum superposition state and uses the quantum computer to receive the corresponding quantum superposition state output. For example, Soukharev et al. [16] proposed the quantum security models INT-PTXT (plaintext integrity under quantum attack) and INT-qCTXT (ciphertext integrity under quantum attack) for authentication and encryption under the Q2 model.
1.2. Related Work
In 2014, NIST launched the Competition for Authenticated Encryption: Security, Applicability and Robustness (CAESAR) [17] for the global collection of authenticated encryption schemes, aiming to develop new and more efficient authenticated encryption schemes that are more secure than the Advanced Encryption Standard Galois/Counter Mode [18], and combine security, applicability, and robustness. The AES-OTR algorithm [19] is one of the candidate algorithms to enter the CAESAR competition’s third round. AES-OTR is an authenticated encryption algorithm that combines the AES algorithm [20] with the OTR mode of operation [21]. The OTR operation mode is extensively employed in the design of authentication encryption algorithms such as AEZ [22] and ESTATE [23] due to low computational complexity, parallelism, and inverse freedom. Its authentication part function, AFE, is a variant of PMAC [24]. In the case of a known pair of plaintext and s + 1 (s > 0) pair of plaintexts, Zheng et al. [25] proposed a traditional forgery attack on the AES-OTR algorithm by reusing associated data and public message codes. The probability of a successful attack was computed as and (where m is the length of the blocks and n is the number of the blocks), and the possibility of forgery was proved. Since AES-OTR is the fastest algorithm implemented in hardware in the CAESAR competition, it is crucial to evaluate the performance of its high-speed applications. For the first time, Banik et al. [26] employed an 8-bit serial AES circuit to compactly implement three authenticated encryption algorithms, CLOC [27], SILC [28], and AES-OTR [19]. Ueno et al. [29] parallelized the encryption core part of AES into the Feistel network’s data path corresponding to the OTR algorithm and proposed a scalable AES-OTR hardware architecture with a smaller area and higher throughput quantity. The actual efficiency of the AES-OTR hardware implementation is assessed using FPGA and ASIC, and authentication and encryption can be completed with low energy consumption. Mancillas [30] established the AES-OTR algorithm’s superiority in high-speed and ultra-high-speed authentication and encryption applications, demonstrating that when the underlying algorithm is AES and has certain requirements for hardware speed, AES-OTR outperforms the OCB structure.
The AES-OTR authentication encryption algorithm processes associated data in two structures: serial and parallel. This study employs the relative independence between the AES-OTR algorithm’s modules to deal with the associated data’s parallel and serial structural characteristics. The data’s collision form is constructed and combined with the Simon quantum algorithm to solve the collision period, the AES-OTR algorithm’s collision forgery attack under quantum computing is proposed, and its feasibility and efficiency are verified.
2. AES-OTR Algorithm Description
2.1. Basic Symbols
First, some symbols in the AES-OTR authentication encryption algorithm are explained. and represent the binary strings of n bits and indefinite lengths, respectively, and represents an empty string. A set of strings of length represented as (), indicating that the string P is divided into m blocks with a block-length of 128 bits, and is employed to represent a sequence of r zero characters. Representing the first bits of the string, as . Furthermore, when , and when . Thus, when the processed data’s length is not a multiple of the 128-bit packet’s length, it must be padded according to the following rules, referred to as
The AES-OTR algorithm’s encryption authentication part is , corresponding to , and k represents the size of the key K; n represents the size of the public message code N (Nonce); t represents the size of the generated Tag; and AD, M, and C represent the variable length’s associated with data, plaintext, and ciphertext, respectively. The decryption and verification part can be expressed as if the verification is successful, where the plaintext M is output; otherwise, the output shows that the verification fails.
2.2. Plaintext Encryption
Assuming an n-variable encrypted Boolean function , an authentication encryption scheme based on an OTR operation mode is denoted by , and AES-OTR’s encryption and decryption functions are represented as and , respectively. The plaintext and ciphertext are firstly processed in two blocks when encrypting and decrypting after two rounds of Feistel permutation, and different input masks are employed in each round’s underlying function. Figure 1 and Figure 2 show the encryption-processing procedures for the first m − 1 blocks and the m-th block, respectively, assuming that m plaintext blocks are processed.
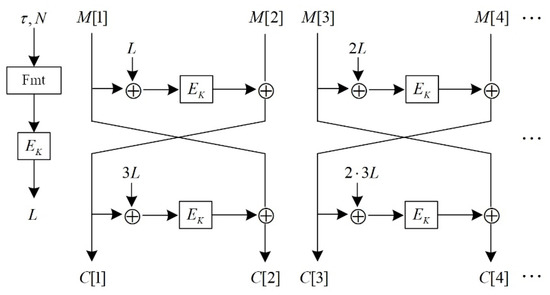
Figure 1.
AES-OTR algorithm handles plaintext blocks other than the last block.
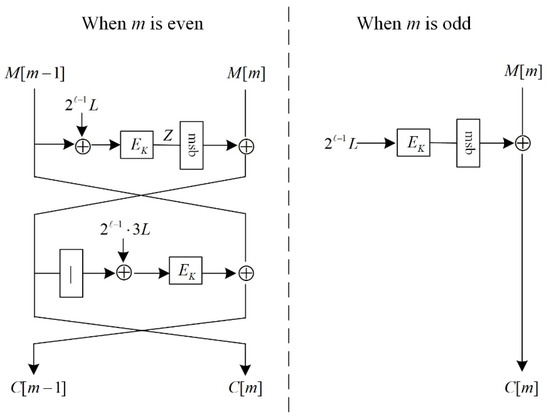
Figure 2.
AES-OTR processing the last plaintext block.
The generation of the parameter L in the process can be expressed as . It is crucial to distinguish between odd-numbered and even-numbered blocks since the plaintext is to be grouped in pairs. If the plaintext pair of the encrypted pair of odd-numbered and even-numbered blocks is represented as , then for , after encryption processing, the plaintext pair of the i-th pair of odd-numbered and even-numbered blocks can be expressed as
It is essential to judge the parity of the last plaintext block’s index number m when processing the last plaintext block so that different structures are employed for encryption processing. Figure 2 shows the schematic diagram. According to the definition of reference [31], the specific expression of the multiple function 2X is as follows:
where represents the left cyclic shift of 1 bit of string X.
2.3. Associated Data Processing
When AES-OTR processes the associated data, it first divides the associated data into 128-bit blocks, represented as , and represents the i-th associated data block. When the last block is less than 128 bits, it must be padded to 128 bits, which is expressed as or . AES-OTR employs both parallel and serial structures to process the associated data and finally generate TA. Figure 3 and Figure 4 show the structure diagrams.
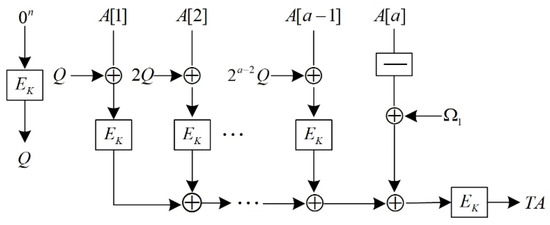
Figure 3.
AES-OTR processes the associated data in parallel.
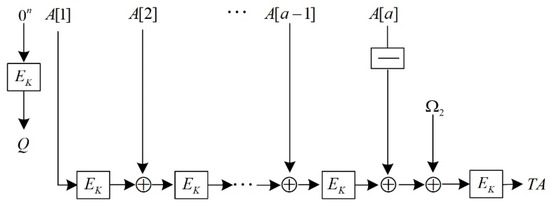
Figure 4.
AES-OTR processes the associated data in serial.
As shown in Figure 3, according to whether the last associated data block needs to be padded, the value of the input mask is as follows:
As shown in Figure 4, according to whether the last associated data block needs to be padded, the value of the input mask is as follows:
2.4. Tag Generation Process
Figure 5 shows the tag generation process. The intermediate value TE is obtained by employing the input mask to encrypt the checksum, and then the XOR operation is performed using the TA obtained in the associated data processing; finally, the Tag is obtained to complete the authentication. The checksum’s expression in the process is related to the parity of the plaintext block m. When m is an even number,
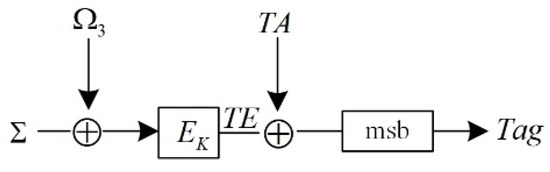
Figure 5.
The generation process of AES-OTR’s Tag.
When m is odd,
As shown in Figure 5, according to whether the last plaintext block needs to be padded, the value of the input mask is as follows:
3. Collision Forgery Attack Based on Quantum Computing
For the collision forgery attack under quantum computing for the AES-OTR cryptographic algorithm, it is crucial to first construct a periodic function that satisfies the Simon assumption according to the cryptographic algorithm’s structural characteristics, and then employ the Simon algorithm to search and solve to obtain s, and realize the collision forgery attack after recovering the period. Algorithm 1 shows the analysis idea of this study. This section explains the qubit, Hadamard transform, transform, quantum parallelism, and Simon quantum algorithm in turn.
| Algorithm 1 Collision Forgery Attack on AES-OTR Algorithm under Quantum Computing |
| 1: Investigating the two structural characteristics of the authentication encryption algorithm AES-OTR serial and parallel processing of the associated data, and forging the associated data; 2: Determining the periodic function f of the associated data; ; 4: The two groups of the associated data A and B are processed, and the generated authentication tag , and the forgery attack is completed. |
3.1. Qubit
The classical bit is the fundamental unit of classical computation, with a certain 0 or 1, representing a low level and high level, respectively. Qubits, unlike classical bits, are indeterminate. The superposition state of the qubit is the squared probability of plus the squared probability of that can be represented by a linear combination as . Where, and are complex numbers, and .
3.2. Hadamard Transform
The quantum logic gate circuit, the single-quantum Hadamard gate converts into and into in the quantum logic gate circuit, which can be expressed as . Each qubit is transformed between and and between and for multi-qubit Hadamard gates. This n-bit Hadamard gate can be represented by a matrix as
where is the tensor product and is the inner product.
3.3. Transform and Quantum Parallelism
If is the n-qubit data register, is the n-qubit destination register. Defining an n-variable encrypted Boolean function , when the adversary computes f(x), it is equivalent to applying transformation to , which can be expressed as . Similarly, when the adversary applies the transformation to the input superposition state , the resulting output superposition state is
Thus, the quantum computer can simultaneously realize the mapping of different x values to f(x) through one transformation; that is, quantum parallelism is realized.
3.4. Simon Quantum Algorithm
Given an n-variable Boolean function , for any , there is a nontrivial period s, such that , where , then how to solve the value of s is the Simon problem.
However, the condition of the function f in the Simon problem is rather harsh, and according to [32], the Simon assumption’s condition can usually be relaxed appropriately. For an n-variable Boolean function , it is generally assumed that for any , there is always a such that . Under these conditions, this study completes the construction of the periodic function f, so that the collision forgery attack under the AES-OTR algorithm’s quantum computing is investigated.
The Simon algorithm, as the simplest algorithm for determining quantum periods, queries the relevant cryptosystem’s quantum superposition state in the form of . Through sub-quantum query, the function’s nontrivial period s can be searched for, while the traditional query approach’s complexity is . Simon’s algorithm achieves an exponential speedup compared to traditional approaches. The details of Simon’s algorithm(Algorithm 2) are shown below.
| Algorithm 2 Simon Algorithm |
1: Initializing the state of the quantum registers of the two n-dimensional vectors to ; 2: Applying the Hadamard transform into the first register to obtain the superposition state: ; 3: Applying the transformation to the superposition state in the previous step to obtain ; 4: If f(z) is obtained by measuring the second register, the first register will have the following collision: ; 5: Performing the Hadamard transform on the first n qubits again to obtain ; 6: Repeating the above steps n − 1 times to obtain n − 1 linear equations, solve the equation system, and obtain the nontrivial period s. |
4. Construction of the Collision Form of AES-OTR
4.1. Collision Form When Processing AD Parallelly
Figure 6 shows the process of constructing a collision form for parallel processing of the associated data. First, it is assumed that there is an existing set of associated data . Since the attack approach proposed in this study has nothing to do with whether the last associated data block needs to be filled, for the convenience of explanation, the following assumes that the last associated data block is exactly 128 bits; i.e., it has not been padded. When processing the associated data in parallel, set the intermediate variables obtained after the first a−1-linked data packets are encrypted with AES to be in turn; then, the intermediate variables and output expressions of the associated data processing are as follows:
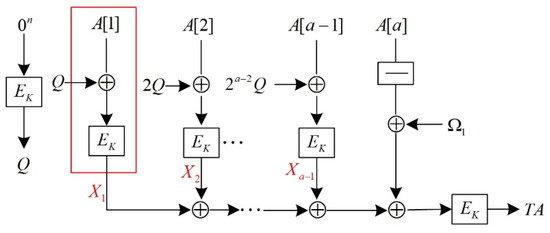
Figure 6.
Constructing a collision form for parallel processing of the associated data.
As shown in the above formula, to output the final TA value, the intermediate variable must undergo a series of XOR operations in a linear form. Furthermore, under the same set of K and Nonce, the output Ek is only related to the input associated data blocks. Thus, a set of collisions can be constructed by conducting a suitable linear transformation on the associated data blocks so that the final input value remains unchanged.
When the first two associated data blocks and are employed as forged objects, let the forged two new associated data blocks be and , where and ; then, the forged block of associated data is . The intermediate variables obtained are after the first a − 1-associated data blocks are encrypted with AES. Thus, after processing the first two associated data blocks, the obtained intermediate variable expressions are as follows:
Therefore, after the associated data processing, there is the following output:
When generating the Tag, ; thus, for the associated data A there is
Thus, for , forgery verification is completed. We can further extend the above approach. For a set of known associated data , process the first a−1-associated data blocks, and the obtained intermediate variables and final output are recorded as follows:
Arbitrarily selecting two associated data blocks and as the forgery objects, and setting the forged two new associated data blocks as and , where and , then the associated data’s re-forged block can be expressed as . After the first a−1-associated data blocks are encrypted with AES, the intermediate variables obtained are in turn . Thus, after processing the two associated data blocks of and , the obtained intermediate variable expression is as follows:
Therefore, after the associated data processing, there is the following output:
When generating the Tag, ; thus, for the associated data A there is
Thus, , and the same message authentication code is generated; the forgery verification thus is completed. Next, we can implement the collision forgery attack of the AES-OTR algorithm under quantum computing using the two sets of collision pairs arbitrarily forged above when processing the associated data in parallel.
4.2. Collision Form When Processing AD Serially
Figure 7 shows the process of constructing a collision form for serial processing of the associated data. It is assumed that a set of associated data is known to the adversary for the structural analysis when serially processing the associated data, as described in Section 4.1. Denoting the intermediate variables before the AES encryption processing operation of the first a-associated data block as in turn, then the output expressions of the intermediate variables and associated data processing are as follows:
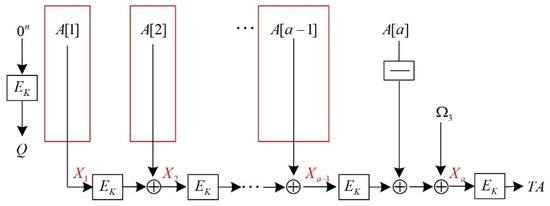
Figure 7.
Constructing a collision form for serial processing of associated data.
As shown in the above formula, when serially processing the associated data, the final output value TA is only related to the intermediate variable ; thus, the associated data blocks can be appropriately transformed during forgery so that the intermediate variable and the associated data block are unaffected. Furthermore, under the same set of K and Nonce, the output is only related to the input-associated data blocks. Thus, by appropriately transforming the associated data blocks, the input value of the final can be kept unchanged, thereby constructing a set of collisions.
If starting from the third intermediate variable as the attack target, setting the intermediate variables before each associated data block performs the AES encryption processing operation as in turn, and the forged new block of associated data is , where
Thus, after processing the forged new associated data blocks, the obtained intermediate variables and the final output expression are as follows:
When generating the Tag, ; thus, for the associated data A there is
Therefore, , and forgery verification is completed. We can further extend the above approach. For a set of known associated data , starting from the p-th intermediate variable as the attack target, and setting the intermediate variables before each associated data block performs the AES encryption processing operation as , where , and the associated data’s forged new set is , where
The corresponding intermediate variables and final output expressions are as follows:
Similarly, can be proven, and the forgery verification can be completed again. Thus, we can achieve the AES-OTR algorithm’s collision forgery attack under quantum computing using the above two blocks of forged collision pairs when serially processing the associated data.
5. Collision Forgery Attack on AES-OTR
Assuming that the encryption oracle machine is represented as , and is an n-variable Boolean function, the block cipher algorithm must be employed to complete the function’s construction to obtain a periodic function related to the input. Whether the external variable b is introduced or not, the periodic function’s construction primarily has the following two forms:
Among them, is a function constructed by the block cipher algorithm . From the expression, the period in is s, and the period in is . The solution of the nontrivial period s is performed using Simon’s quantum algorithm. Figure 8 shows the quantum circuit diagram of Simon’s algorithm.
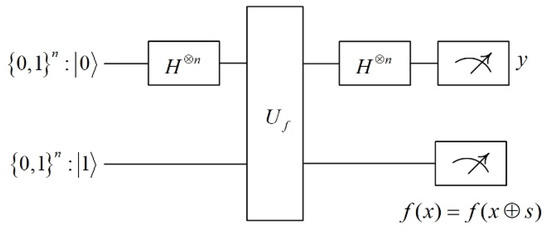
Figure 8.
Quantum circuit diagram of Simon’s algorithm.
This section employs the Simon quantum algorithm to perform a collision forgery attack on the AES-OTR authentication encryption algorithm under quantum computing. Thus, we must first construct a periodic function that satisfies the Simon problem’s condition. Given a certain set of K and Nonce, we construct using an arbitrary constant . Section 4.1 and Section 4.2 of this study describe the construction of the collision form for processing associated data in parallel and serially, respectively. The following uses parallel processing of associated data as an example to conduct a collision forgery attack on the AES-OTR algorithm under quantum computing.
Assuming an existing set of associated data , when two new associated data blocks and are employed to forge the associated data blocks and , respectively, the forged new associated data is represented as , where and . Then, for the input , bring it into the process of parallel processing of associated data, there is
Expanding on this basis, arbitrarily selecting two associated data blocks and as forged objects, and setting the forged two new associated data blocks as and , where and , then the re-forged block of associated data can be represented as . Thus, bringing the input into the process of parallel processing of associated data, there is
According to the construction of the collision form in parallel processing of associated data in Section 4.1, we can find that when the constructed function satisfies . Thus, for a certain set of K and Nonce, and will generate the same authentication Tag.
Thus, by using the Simon quantum algorithm to search out the period , the authentication Tag’s forgery can be completed, and the time complexity is close to 1. Therefore, the collision forgery attack on the AES-OTR algorithm is completed under quantum computing. The proposed attack approach’s success rate is analyzed as follows.
For the Simon algorithm with suitable commitments, [33] presents the following theorem:
Theorem 1.
If , then after cn queries, the Simon quantum algorithm returns s with a probability of . Then, when , there is
Thus, the Simon algorithm computes s with a probability close to 1 when the number of queries is large enough, indicating that the approach is feasible and efficient.
Similarly, the collision forgery attack on the AES-OTR algorithm under quantum computing can be completed again by combining the construction of the collision form when serially processing associated data in Section 4.2. The following uses serial processing of the associated data as an example to conduct a collision forgery attack on the AES-OTR algorithm under quantum computing.
Setting the intermediate variables before each associated data block performs the AES encryption processing operation as in turn, and the forged new block of associated data is , where ,, , …, and . Then, for the input , bring it into the process of serial processing of the associated data, and due to , ,, there is
Expanding on this basis, For a set of known associated data , starting from the p-th intermediate variable as the attack target, and setting the intermediate variables before each associated data block performs the AES encryption processing operation as , where , the associated data’s forged new set is , where , , , …, . Thus, bringing the input into the process of serial processing of the associated data, due to , , , there is
According to the construction of the collision form in serial processing of associated data in Section 4.2, we can find that when the constructed function satisfies . Thus, for a certain set of K and Nonce, and will generate the same authentication Tag.
Thus, by using the Simon quantum algorithm to search out the period , the authentication Tag’s forgery can be completed, and the time complexity is close to 1. Therefore, the collision forgery attack on the AES-OTR algorithm is completed under quantum computing. Furthermore, when the number of queries is large enough, the Simon algorithm calculates s with a probability close to 1.
For the two structures of parallel and serial processing of associated data, both use the pre-constructed collision form, and then use the Simon quantum algorithm to attack. Therefore, the two methods are more or less the same. However, a detailed analysis reveals that this operation is more efficient and feasible for parallel processing of associated data. When serially processing associated data, more data blocks need to be processed, and the operation is more cumbersome, so the efficiency is not good. This is also the direction we need to improve in the next step. At the same time, it also shows that for the structure of serial processing of associated data, the security is higher during encryption and decryption.
6. Conclusions and Future Work
This study proposes a collision forgery attack on the AES-OTR algorithm under quantum computing by making full use of the relative independence between different modules of the AES-OTR authentication encryption algorithm, the characteristics of parallel and serial structures in associated data processing, and the simplicity of intermediate variable generation. It is demonstrated that the AES-OTR algorithm faces a serious threat when the associated data and Nonce are reused. The periodic function f of the associated data is constructed by analyzing the collision form of the associated data, and is combined with the Simon quantum algorithm to solve the collision period s with a success rate close to 1, so that ; then, when employing the fake associated data to process, the same authentication Tag is generated. The effect of monitoring or tampering is achieved without being discovered by a third party, which has good feasibility and efficiency.
To address the cryptographic crisis in the post-quantum era, current anti-quantum cryptography design and research primarily focus on the cryptographic structure or working mode under the quantum security model, excluding quantum security analysis of instantiated cryptographic algorithms. In this study, the research on collision forgery attacks under quantum computing of AES-OTR helps enrich the security analysis of specific authentication encryption algorithms, thus offering ideas for enhancing the design scheme of related quantum-resistant cryptographic algorithms. The next stage is to develop a polynomial time quantum discriminator with as many rounds as possible. In addition to employing the Simon algorithm to search for the period s, the Grover algorithm can also be combined to enhance the exhaustive search key’s speed to realize the quantum key recovery attack.
Author Contributions
Conceptualization, L.C. and Y.W.; methodology, L.C.; validation, L.C. and Y.W.; formal analysis, L.C. and X.W.; investigation, X.W.; resources, Y.W.; data curation, X.P.; writing—original draft preparation, L.C.; writing—review and editing, L.C. and Y.W.; supervision, X.P.; project administration, Y.W.; funding acquisition, Y.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Research on the Security of AES and Related Cryptographic Algorithms in the General Project of Shaanxi Provincial Foundation Fund (2021JM-254).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Benioff, P. The computer as a physical system: A microscopic quantum mechanical Hamiltonian model of computers as represented by Turing machines. J. Stat. Phys. 1980, 22, 563–591. [Google Scholar] [CrossRef]
- Song, F.; Yun, A. Quantum security of NMAC and related constructions. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Cham, Switzerland, 2017; pp. 283–309. [Google Scholar]
- Czajkowski, J.; Hülsing, A.; Schaffner, C. Quantum indistinguishability of random sponges. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2019; Springer: Cham, Switzerland, 2019; pp. 296–325. [Google Scholar]
- Hosoyamada, A.; Iwata, T. 4-round Luby-Rackoff construction is a qPRP. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Springer: Cham, Switzerland, 2019; pp. 145–174. [Google Scholar]
- Yu, B.; Sun, B.; Liu, G.; Luo, Y.; Zhang, Z. Quantum cryptanalysis on some generalized unbalanced Feistel networks. J. Cryptol. Res. 2021, 8, 960–973. [Google Scholar]
- Li, Y.; Lin, H.; Yi, Z.; Xie, H. Quantum cryptanalysis of MIBS. J. Cryptol. Res. 2021, 8, 989–998. [Google Scholar]
- Liang, M.; Luo, Y.; Liu, F. A survey on quantum-secure symmetric cryptography. J. Cryptol. Res. 2021, 8, 925–947. [Google Scholar]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Simon, D.R. On the power of quantum computation. SIAM J. Comput. 1997, 26, 1474–1483. [Google Scholar] [CrossRef]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Quantum differential and linear cryptanalysis. arXiv 2015, arXiv:1510.05836. [Google Scholar] [CrossRef]
- Roetteler, M.; Steinwandt, R. A note on quantum related-key attacks. Inf. Process. Lett. 2015, 115, 40–44. [Google Scholar] [CrossRef] [Green Version]
- Hosoyamada, A.; Aoki, K. On quantum related-key attacks on iterated Even-Mansour ciphers. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2019, 102, 27–34. [Google Scholar] [CrossRef]
- Dong, X.; Dong, B.; Wang, X. Quantum attacks on some Feistel block ciphers. Des. Codes Cryptogr. 2020, 88, 1179–1203. [Google Scholar] [CrossRef]
- Zhandry, M. How to construct quantum random functions. In Proceedings of the 2012 IEEE 53rd Annual Symposium on Foundations of Computer Science, Washington, DC, USA, 20–23 October 2012; pp. 679–687. [Google Scholar]
- Soukharev, V.; Jao, D.; Seshadri, S. Post-quantum security models for authenticated encryption. In Post-Quantum Cryptography; Springer: Cham, Switzerland, 2016; pp. 64–78. [Google Scholar]
- CAESAR-Competition for Authenticated Encryption: Security, Applicability, and Robustness. [DB/OL]. Available online: http://competitions.cr.yp.to/caesar.html (accessed on 1 April 2022).
- McGrew, D.; Viega, J. The Galois/counter mode of operation (GCM). Submiss. NIST Modes Oper. Process 2004, 20. 0278-0070. [Google Scholar]
- Minematsu, K. AES-OTR v3. Submiss. CAESAR Compet. 2016. Available online: http://www.nuee.nagoya-u.ac.jp/labs/tiwata/diac2016/slides/diac2016_17_Kazuhiko.pdf (accessed on 26 May 2022).
- Daemen, J.; Rijmen, V. The Design of Rijndael; Springer: New York, NY, USA, 2002. [Google Scholar]
- Minematsu, K. Parallelizable rate-1 authenticated encryption from pseudorandom functions. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, 11–15 May 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 275–292. [Google Scholar]
- Hoang, V.T.; Krovetz, T.; Rogaway, P. Robust authenticated-encryption AEZ and the problem that it solves. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26–30 April 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 15–44. [Google Scholar]
- Chakraborti, A.; Datta, N.; Jha, A.; Mancillas-López, C.; Nandi, M.; Sasaki, Y. ESTATE: A lightweight and low energy authenticated encryption mode. IACR Trans. Symmetric Cryptol. 2020, S1, 350–389. [Google Scholar] [CrossRef]
- Rogaway, P. Efficient instantiations of tweakable blockciphers and refinements to modes OCB and PMAC. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Jeju Island, Korea, 5–9 December 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 16–31. [Google Scholar]
- Zheng, X.; Fu, Y.; Song, H. Forgery Attack on Authentication Encryption Algorithm AES-OTR. Comput. Appl. Softw. 2017, 34, 320–324. [Google Scholar]
- Banik, S.; Bogdanov, A.; Minematsu, K. Low-area hardware implementations of CLOC, SILC and AES-OTR. In Proceedings of the 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; pp. 71–74. [Google Scholar]
- Iwata, T.; Minematsu, K.; Guo, J.; Morioka, S. CLOC: Authenticated encryption for short input. In Proceedings of the International Workshop on Fast Software Encryption, London, UK, 3–5 March 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 149–167. [Google Scholar]
- Iwata, T.; Minematsu, K.; Guo, J.; Morioka, S. SILC: Simple lightweight CFB. CAESAR Submiss. 2014. Available online: https://competitions.cr.yp.to/round1/silcv1.pdf (accessed on 26 May 2022).
- Ueno, R.; Homma, N.; Iida, T.; Minematsu, K. High throughput/gate FN-based hardware architectures for AES-OTR. In Proceedings of the 2019 IEEE International Symposium on Circuits and Systems (ISCAS), Sapporo, Japan, 26–29 May 2019; pp. 1–4. [Google Scholar]
- Mancillas-López, C.; Ovilla-Martínez, B. An Ultra-Fast Authenticated Encryption Scheme with Associated Data Using AES-OTR. J. Circuits Syst. Comput. 2022, 31, 2250167. [Google Scholar] [CrossRef]
- Iwata, T.; Kurosawa, K. Omac: One-key cbc mac. In Proceedings of the International Workshop on Fast Software Encryption, Lund, Sweden, 24–26 February 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 129–153. [Google Scholar]
- Santoli, T.; Schaffner, C. Using Simon's algorithm to attack symmetric-key cryptographic primitives. arXiv 2016, arXiv:1603.07856. [Google Scholar] [CrossRef]
- Kaplan, M.; Leurent, G.; Leverrier, A.; Naya-Plasencia, M. Breaking symmetric cryptosystems using quantum period finding. In Proceedings of the Annual international Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 207–237. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).