Triple Modular Redundancy Optimization for Threshold Determination in Intrusion Detection Systems
Abstract
1. Introduction
2. Related Work
2.1. Anomaly Detection and Classification Algorithms
2.2. EWMA Algorithm
2.3. CUSUM Algorithm
2.4. k-NN Algorithm
2.5. Comparison
3. Materials and Methods
3.1. Materials
3.2. Methods
3.2.1. Redundancy
- Hardware Redundancy
- Software Redundancy
- Information Redundancy
- Time Redundancy
3.2.2. Anomaly Detection Algorithms
- Cumulative Sum Algorithm
- -
- —Cumulative Sum;
- -
- —n-th observation;
- -
- —mean of the process estimated in real time.
- Exponentially Weighted Moving Average
- -
- —mean of the process estimated in real time in n-th observation;
- -
- —exponentially weighted moving average factor;
- K-nearest neighbors algorithm
- -
- —i-th observation;
- -
- —i-th observation.
3.2.3. Quality Parameters of Classification in Two Classes
4. Results
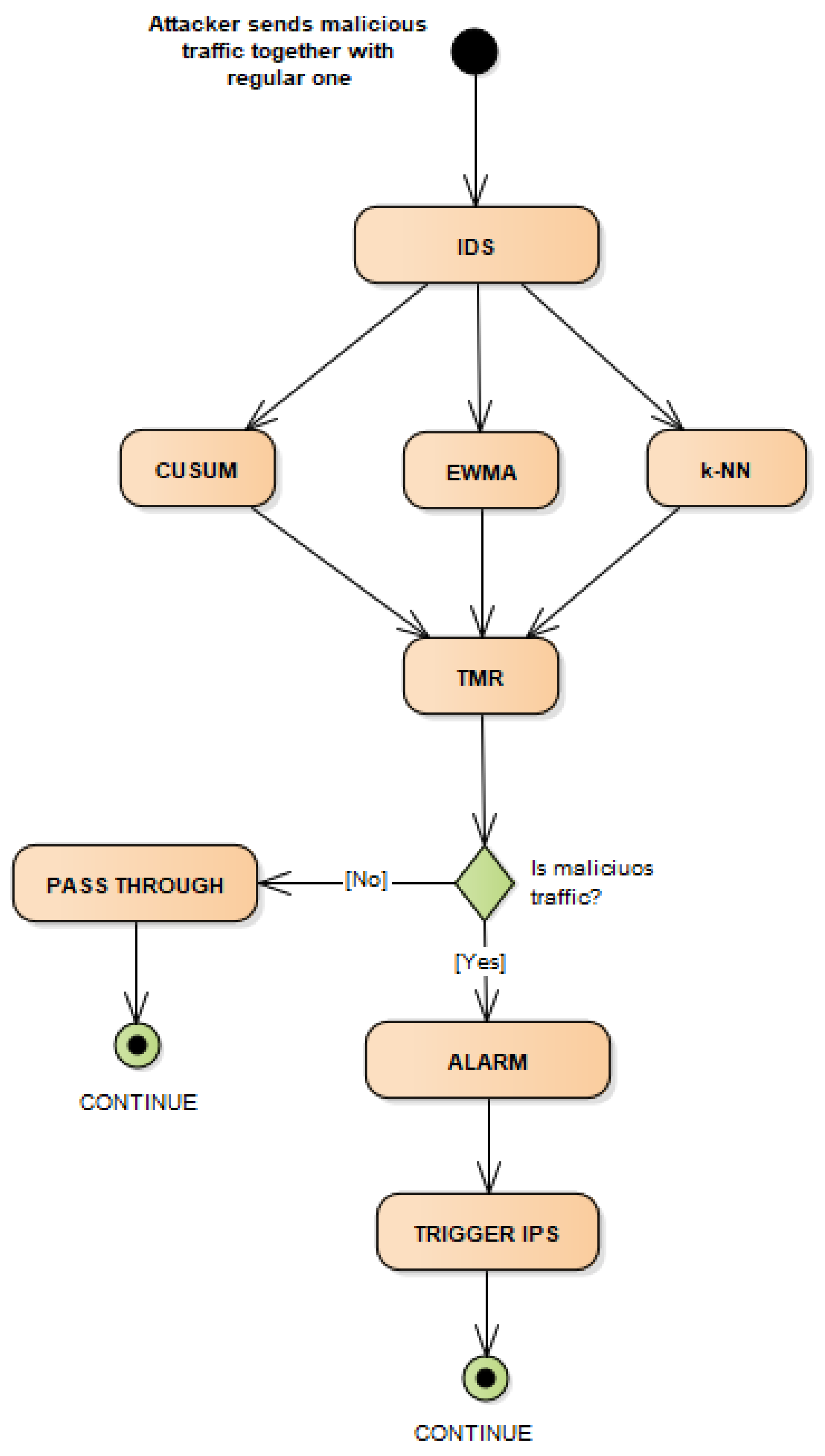
4.1. The Architecture of the Proposed Platform
| Algorithm 1: Application of triple modular redundancy for attack triggering in one IDS |
 |
4.2. Implementation
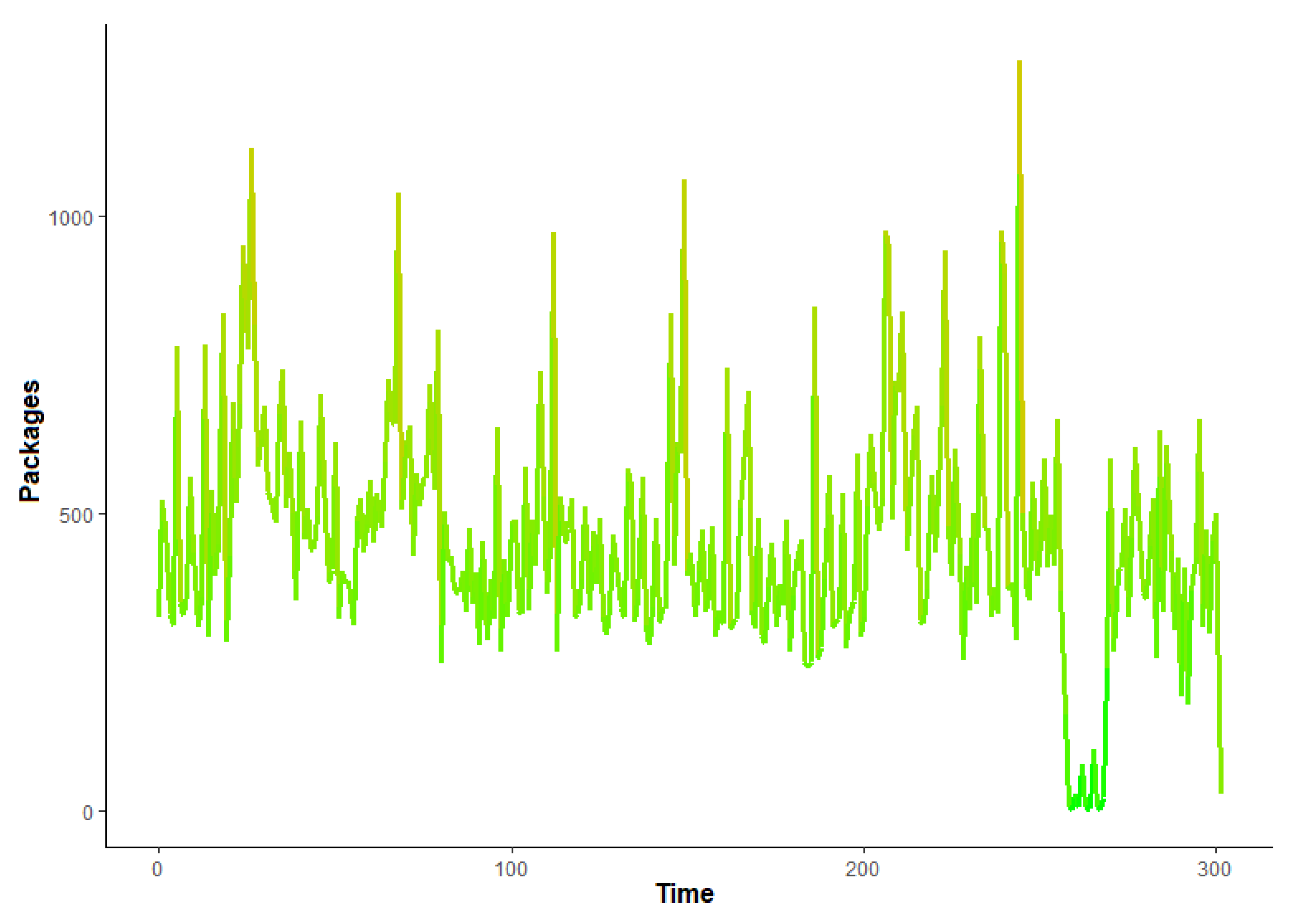
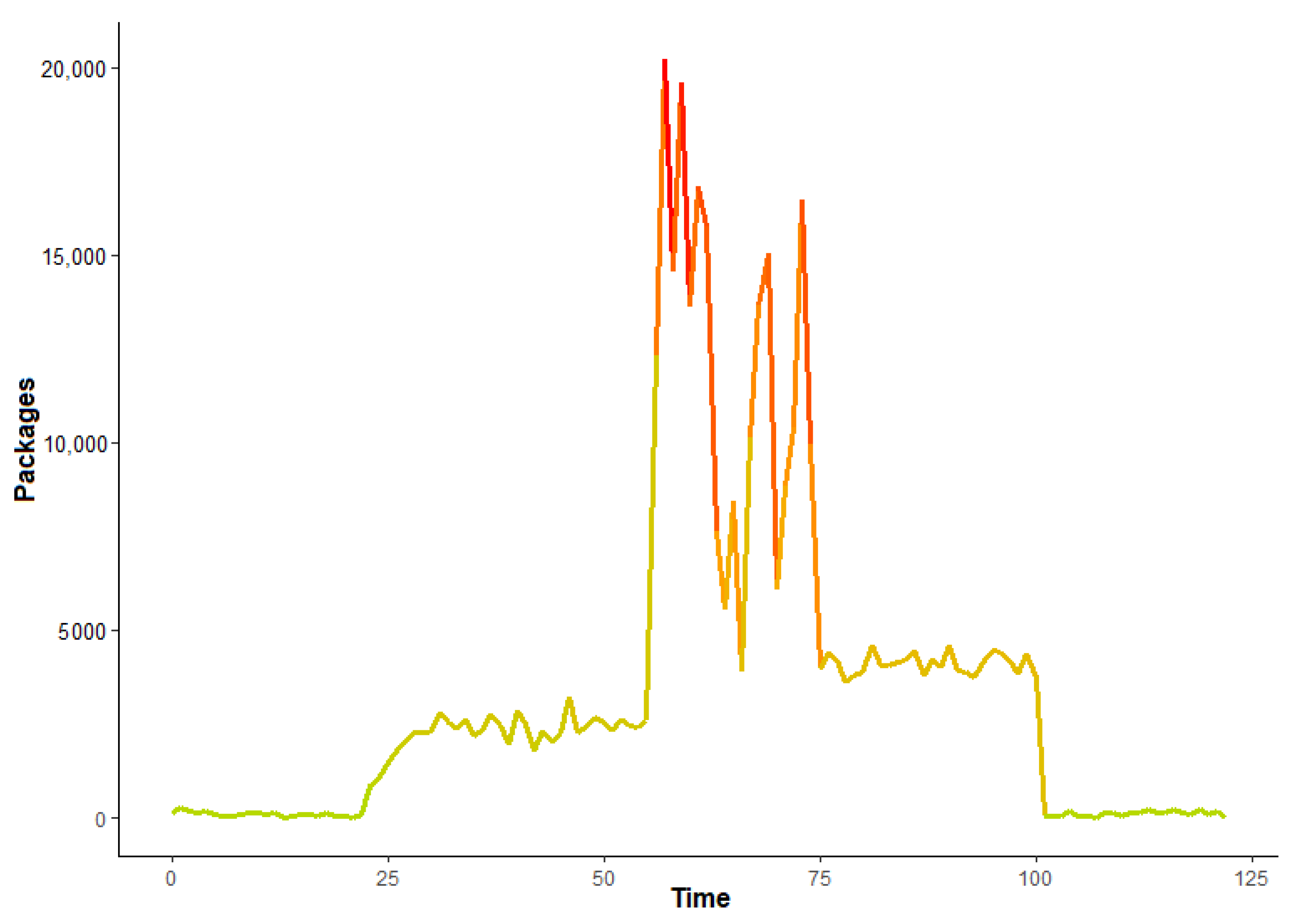
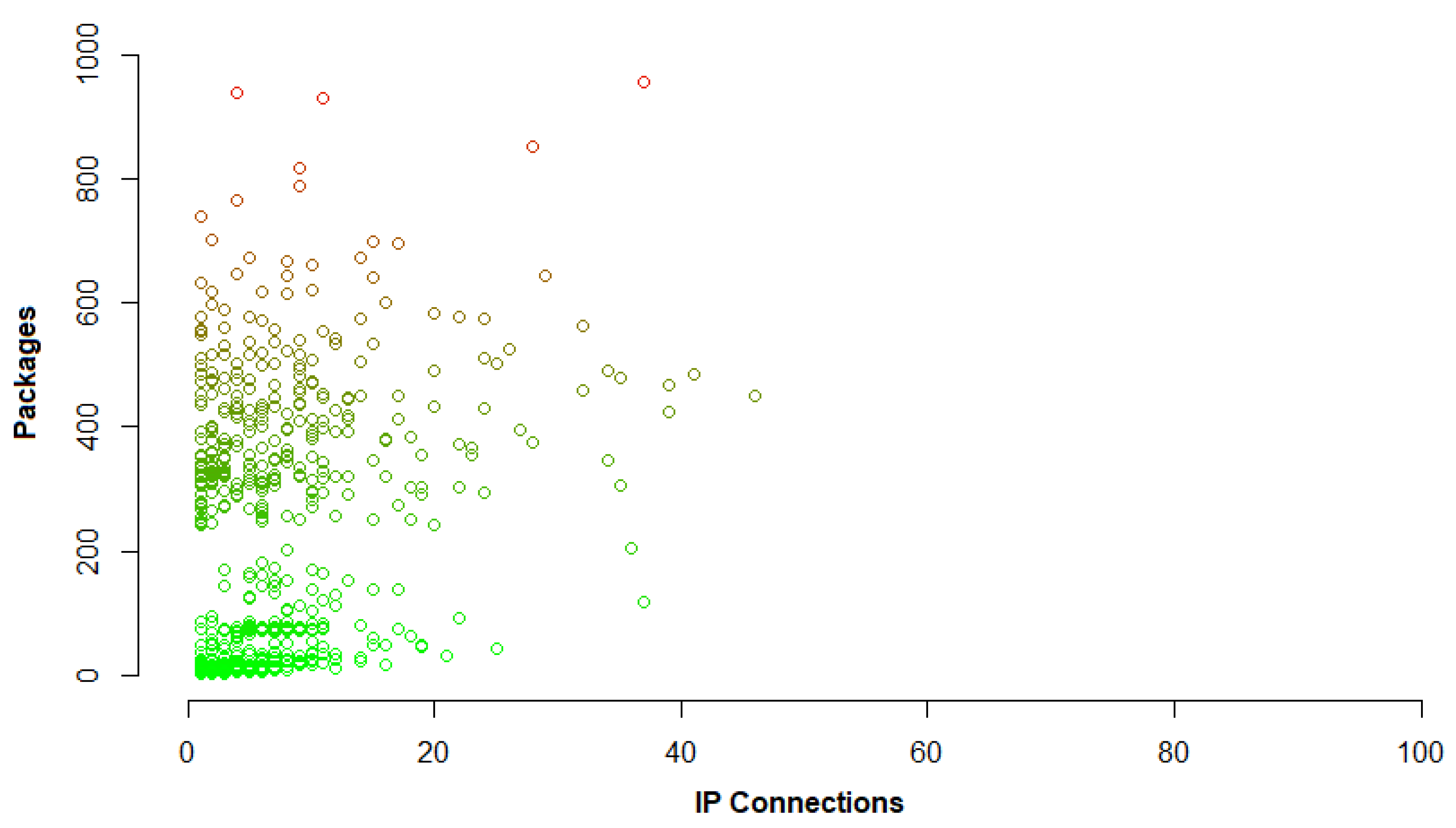
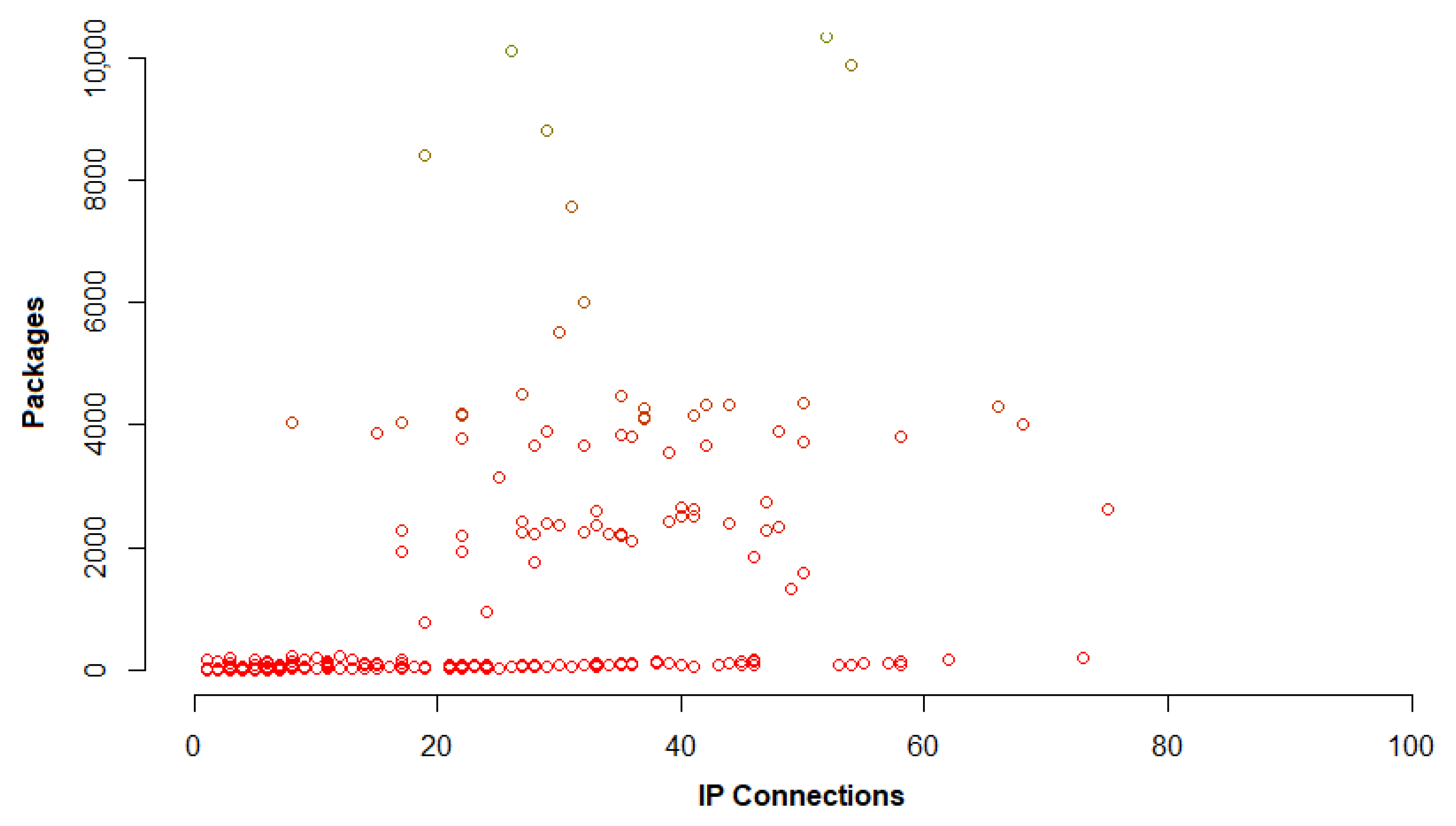
Traffic Modeling
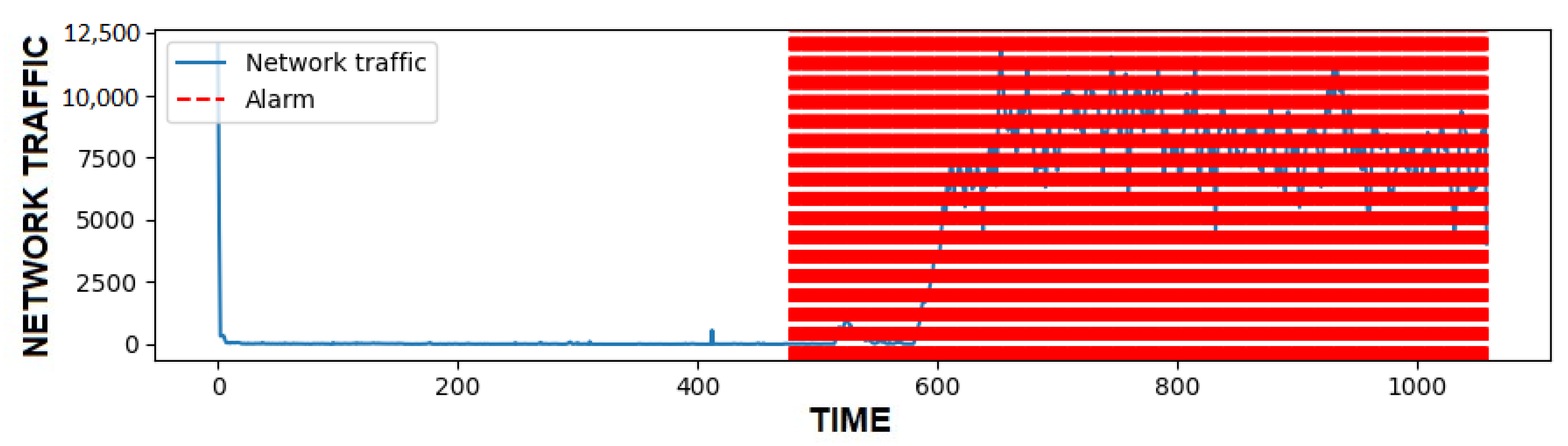
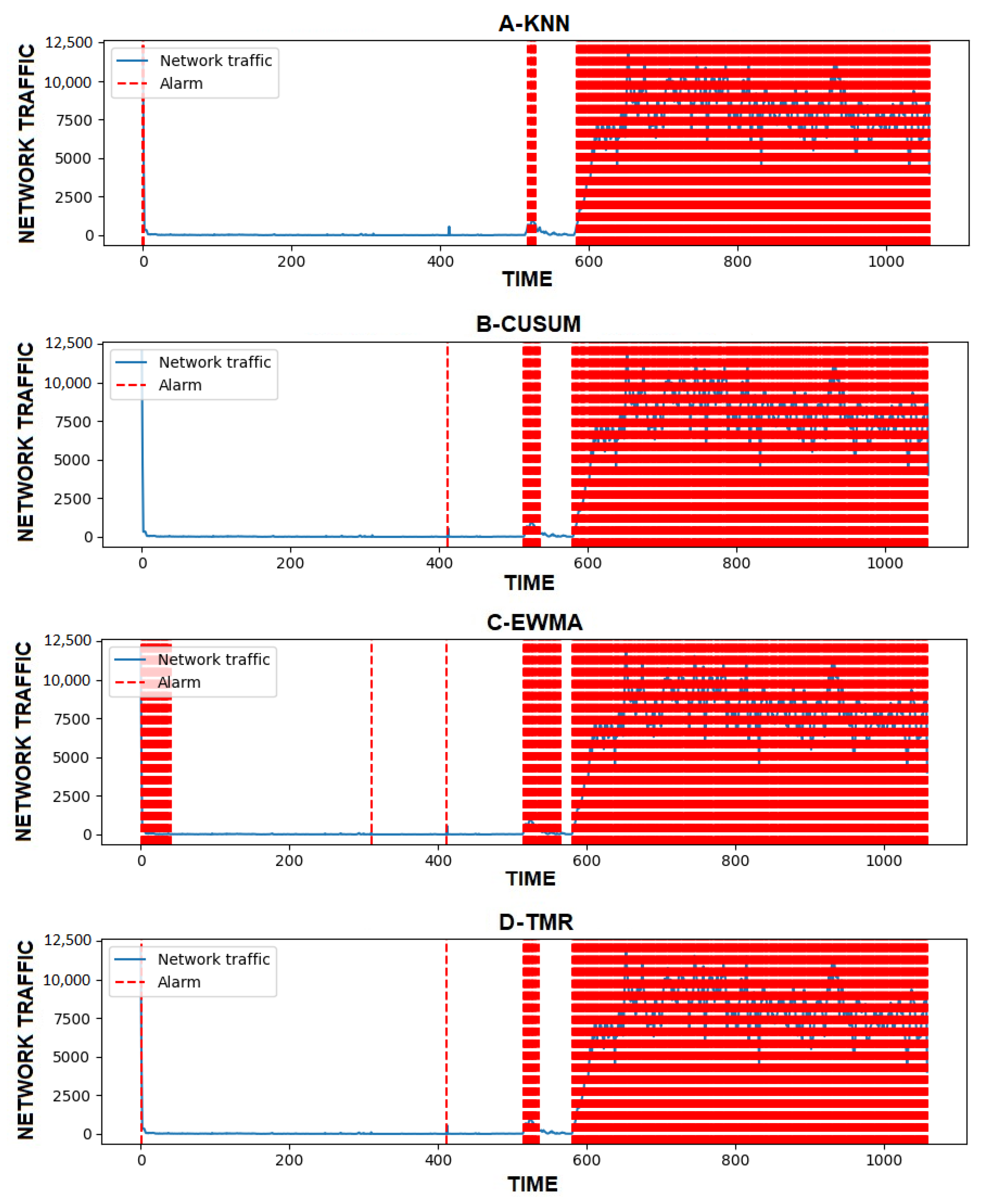
4.3. Obtained Results
5. Discussion
6. Conclusions
- New things:
- Using redundancy to get better results by including existing algorithms;
- Combining EWMA, CUSUM, and k-nearest neighbours algorithm together in one TMR;
- Using one dataset for training and other to make evaluation and to make it more comparable.
- Advantages:
- Higher accuracy than each included method individually;
- Easy for implementation using Python.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| IDS | Intrusion Detection System |
| IPS | Intrusion Prevention System |
| DDoS | Distributed Denial of Service |
| TMR | Triple Modular Redundancy |
| CUSUM | Cumulative Sum |
| EWMA | Exponentially Weighted Moving Average |
| k-NN | k-Nearest Neighbors |
| UDP | User Datagram Protocol |
| HTTP | Hypertext Transfer Protocol |
| CERT | Computer emergency response team |
| TP | True Positive |
| TN | True Negative |
| FP | False Positive |
| FN | False Negative |
References
- Pu, S. Choosing parameters for detecting DDoS attack. In Proceedings of the 2012 International Conference on Wavelet Active Media Technology and Information Processing (ICWAMTIP), Chengdu, China, 17–19 December 2012; pp. 239–242. [Google Scholar] [CrossRef]
- Lee, K.; Kim, J.; Kwon, K.H.; Han, Y.; Kim, S. DDoS attack detection method using cluster analysis. Expert Syst. Appl. 2008, 34, 1659–1665. [Google Scholar] [CrossRef]
- DDoS Attack Types and Mitigation Methods. Available online: https://www.imperva.com/learn/ddos/ddos-attacks (accessed on 12 December 2020).
- Sanmorino, A.; Yazid, S. DDoS attack detection method and mitigation using pattern of the flow. In Proceedings of the 2013 International Conference of Information and Communication Technology (ICoICT), Bandung, Indonesia, 20–22 March 2013; pp. 12–16. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 2, 1–22. [Google Scholar] [CrossRef]
- Zhang, Z.; Liu, D.; Wei, Z.; Sun, C. Research on Triple Modular Redundancy Dynamic Fault-Tolerant System Model. In Proceedings of the First International Multi-Symposiums on Computer and Computational Sciences (IMSCCS’06), Hanzhou, China, 20–24 June 2006; pp. 572–576. [Google Scholar] [CrossRef]
- Lyons, R.E.; Vanderkulk, W. The use of triple-modular redundancy to improve computer reliability. IBM J. Res. Dev. 1962, 6, 200–209. [Google Scholar] [CrossRef]
- Abraham, J.A.; Siewiorek, D.P. An algorithm for the accurate reliability evaluation of triple modular redundancy networks. IEEE Trans. Comput. 1974, 100, 682–692. [Google Scholar] [CrossRef]
- Shanbhag, S.; Wolf, T. Accurate anomaly detection through parallelism. IEEE Netw. 2009, 23, 22–28. [Google Scholar] [CrossRef]
- Machaka, P.; Bagula, A.; Nelwamondo, F. Using exponentially weighted moving average algorithm to defend against DDoS attacks. In Proceedings of the 2016 Pattern Recognition Association of South Africa and Robotics and Mechatronics International Conference (PRASA-RobMech), Stellenbosch, South Africa, 30 November–2 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, H.; Zhang, D.; Shin, K.G. Change-point monitoring for the detection of DoS attacks. Trans. Dependable Secur. Comput. 2004, 1, 193–208. [Google Scholar] [CrossRef]
- Özçelik, I.; Brooks, R.R. Cusum-entropy: An efficient method for DDoS attack detection. In Proceedings of the 2016 4th International Istanbul Smart Grid Congress and Fair (ICSG), Istanbul, Turkey, 20–21 April 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Santosh, K.M.; Isaac, E. Defending DDoS Attack using Stochastic Model based Puzzle Controller. IJCSNS Int. J. Comput. Sci. Netw. Secur. 2013, 13, 100–105. [Google Scholar]
- Rahmani, H.; Sahli, N.; Kamoun, F. A Traffic Coherence Analysis Model for DDoS Attack Detection. In Proceedings of the International Conference on Security and Cryptography, Milan, Italy, 7–10 July 2009; pp. 148–154. [Google Scholar]
- Douligeris, C.; Mitrokotsa, A. DDOS Attacks and Defense Mechanisms: A classification. In Proceedings of the I3rd IEEE International Symposium on Signal Processing and Information Technology, Darmstadt, Germany, 17 December 2003; pp. 190–193. [Google Scholar] [CrossRef]
- Mahjabin, T.; Xiao, Y.; Sun, G.; Jiang, W. A survey of distributed denial-of-service attack, prevention, and mitigation techniques. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717741463. [Google Scholar] [CrossRef]
- David, J.; Thomas, C. DDoS Attack Detection Using Fast Entropy Approach on Flow- Based Network Traffic. In Proceedings of the 2nd International Symposium on Big Data and Cloud Computing Challenges, VIT University, Chennai, India, 12–13 March 2015; pp. 30–36. [Google Scholar] [CrossRef]
- Wang, Y. A Hybrid Intrusion Detection System. Ph.D. Thesis, Iowa State University, Ames, IA, USA, 2004. [Google Scholar]
- Smaha, S.E. Haystack: An intrusion detection system. In Proceedings of the Fourth Aerospace Computer Security Applications, Orlando, FL, USA, 12–16 September 1988; pp. 37–44. [Google Scholar] [CrossRef]
- Yusof, A.R.; Udzir, N.I.; Selamat, A.; Hamdan, H.; Abdullah, M.T. Adaptive feature selection for denial of services (DoS) attack. In Proceedings of the 2017 IEEE Conference on Application, Information and Network Security (AINS), Miri, Malaysia, 13–14 November 2017; pp. 81–84. [Google Scholar] [CrossRef]
- Kim, J.; Kim, J.; Kim, H.; Shim, M.; Choi, E. CNN-Based Network Intrusion Detection against Denial-of-Service Attacks. Electronics 2020, 9, 916. [Google Scholar] [CrossRef]
- Mahfouz, A.; Abuhussein, A.; Venugopal, D.; Shiva, S. Ensemble Classifiers for Network Intrusion Detection Using a Novel Network Attack Dataset. Future Internet 2020, 12, 180. [Google Scholar] [CrossRef]
- Faizal, M.A.; Zaki, M.M.; Shahrin, S.; Robiah, Y.; Rahayu, S.S.; Nazrulazhar, B. Threshold Verification Technique for Network Intrusion Detection System. arXiv 2009, arXiv:0906.3843. [Google Scholar]
- Idika, N.; Mathur, A. Survey of Malware Detection Techniques; Purdue University: West Lafayette, Indiana, 2007. [Google Scholar]
- Patel, D.; Srinivasan, K.; Chang, C.-Y.; Gupta, T.; Kataria, A. Network Anomaly Detection inside Consumer Networks—A Hybrid Approach. Electronics 2020, 9, 923. [Google Scholar] [CrossRef]
- Ahsan, M.; Mashuri, M.; Kuswanto, H.; Prastyo, D.D. Intrusion Detection System using Multivariate Control Chart Hotelling’s T2 based on PCA. Int. J. Adv. Sci. Eng. Inf. Technol. 2018, 8, 1905–1911. [Google Scholar] [CrossRef]
- Silva, L.A.; Leithardt, V.R.Q.; Rolim, C.O.; González, G.V.; Geyer, C.F.R.; Silva, J.S. PRISER: Managing Notification in Multiples Devices with Data Privacy Support. Sensors 2019, 19, 3098. [Google Scholar] [CrossRef]
- Sales Mendes, A.; Jiménez-Bravo, D.M.; Navarro-Cáceres, M.; Reis Quietinho Leithardt, V.; Villarrubia González, G. Multi-Agent Approach Using LoRaWAN Devices: An Airport Case Study. Electronics 2020, 9, 1430. [Google Scholar] [CrossRef]
- Haider, S. A Deep CNN Ensemble Framework for Efficient DDoS Attack Detection in Software Defined Networks. IEEE Access 2020, 8, 53972–53983. [Google Scholar] [CrossRef]
- Gupta, B.B.; Dahiya, A. Distributed Denial of Service (DDoS) Attacks: Classification, Attacks, Challenges and Countermeasures, 1st ed.; CRC Press: Boca Raton, FL, USA, 2021. [Google Scholar] [CrossRef]
- Sklavounos, D.; Edoh, A.; Plytas, M. A Statistical Approach Based on EWMA and CUSUM Control Charts for R2L Intrusion Detection. In Proceedings of the 2017 Cybersecurity and Cyberforensics Conference (CCC), London, UK, 21–23 November 2017; pp. 25–30. [Google Scholar] [CrossRef]
- Leu, F.Y.; Yang, W.J. Intrusion Detection with CUSUM for TCP-Based DDoS. In Proceedings of the Embedded and Ubiquitous Computing—EUC 2005 Workshops, Nagasaki, Japan, 6–9 December 2005; pp. 1255–1264. [Google Scholar]
- Zhang, T. Cumulative sum algorithm for detecting SYN flooding attacks. arXiv 2012, arXiv:1212.5129. [Google Scholar]
- Vu, N.H.; Choi, Y.; Choi, M. DDoS attack detection using K-Nearest Neighbor classifier method. In Proceedings of the IASTED International Conference on Telehealth/Assistive Technologies, Baltimore, MD, USA, 16–18 April 2008; pp. 248–253. [Google Scholar]
- IoT Network Intrusion Dataset. Available online: https://ieee-dataport.org/open-access/iot-network-intrusion-dataset (accessed on 15 November 2020).
- Sharafaldin, I.; Lashkari, A.H.; Hakak, S.; Ghorbani, A.A. Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy. In Proceedings of the IEEE 53rd International Carnahan Conference on Security Technology, Chennai, India, 1–3 October 2019; Available online: https://www.unb.ca/cic/datasets/ddos-2019.html (accessed on 15 January 2021). [CrossRef]
- Liu, W.; Ren, P.; Liu, K.; Duan, H. Behavior-based malware analysis and detection. In Proceedings of the 2011 First International Workshop on Complexity and Data Mining, Nanjing, Jiangsu, China, 24–28 September 2011; pp. 39–42. [Google Scholar] [CrossRef]
- Zhou, Y.; Li, J. Research of network traffic anomaly detection model based on multilevel auto-regression. In Proceedings of the 2019 IEEE 7th International Conference on Computer Science and Network Technology (ICCSNT), Dalian, China, 19–20 October 2019; pp. 380–384. [Google Scholar] [CrossRef]
- Shernta, S.; Tamtum, A. Using triple modular redundant (tmr) technique in critical systems operation. Int. J. Comput. Sci. Netw. Secur. 2013, 13, 100–105. [Google Scholar] [CrossRef]
- Čabarkapa, M.; Mišić, J.; Ranđelović, D.; Nedeljković, S.; Nikolić, V. An Advanced Quick-Answering System Intended for the e-Government Service in the Republic of Serbia. Acta Polytech. Hung. 2019, 16, 153–174. [Google Scholar]
- Machaka, P.; McDonald, A.; Nelwamondo, F.; Bagula, A. Using the Cumulative Sum Algorithm against Distributed Denial of Service Attacks in Internet of Things. In Proceedings of the International Conference on Context-Aware Systems and Applications, Thu Dau Mot, Vietnam, 24–25 November 2016; pp. 66–72. [Google Scholar]
- Čisar, P.; Čisar, S.; Bošnjak, S.; Marav, S. EWMA algorithm in network practice. Int. J. Comput. 2010, 5, 160–170. [Google Scholar] [CrossRef]
- Atawodi, I. A Machine Learning Approach to Network Intrusion Detection System Using K Nearest Neighbor and Random Forest. Master’s Thesis, The University of Southern Mississippi, Hattiesburg, MS, USA, May 2019. [Google Scholar]
- Python Pandas Library. Available online: https://pandas.pydata.org/pandas-docs/version/0.17.0/generated/pandas.ewma.html (accessed on 15 November 2020).
- Scikit Learn. Available online: https://scikit-learn.org/stable/modules/generated/sklearn.neighbors.KNeighborsClassifier.html (accessed on 7 February 2021).
- Elsayed, M.; Le-Khac, N.A.; Dev, S.; Jurcut, A. DDoSNet: A Deep-Learning Model for Detecting Network Attacks. In Proceedings of the 21st IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks (IEEE WoWMOM 2020), Cork, Ireland, 31 August–3 September 2020. [Google Scholar] [CrossRef]
- Sales de Lima Filho, F.; Silveira, F.A.F.; Brito Junior, A.M.; Vargas-Solar, G.; Silveira, L.F. Smart Detection: An Online Approach for DoS/DDoS Attack Detection Using Machine Learning. Secur. Commun. Netw. 2019, 2019, 1574749. [Google Scholar] [CrossRef]
- Python and R Scripts for TMR. Available online: https://github.com/miljkomocnik/3ADetection (accessed on 10 February 2021).
| Work | Solution | CUSUM | EWMA | k-NN | TMR | Other Algorithm | Anomaly Detection | Adaptive |
|---|---|---|---|---|---|---|---|---|
| [13] | Puzzle controller | x | ||||||
| [20] | Adaptive feature | x | x | |||||
| [21] | CNN | x | x | |||||
| [25] | Hybrid | x | x | |||||
| [10] | EWMA DDoS | x | x | |||||
| [31] | Statistical | x | x | x | x | |||
| [12] | Entropy | x | x | |||||
| [32] | IDS CUSUM | x | x | x | ||||
| [33] | CUSUM Flood | x | x | |||||
| [34] | k-NN | x | ||||||
| THIS | IDS TMR | x | x | x | x | x | x |
| Predicted | |||
|---|---|---|---|
| Positive | Negative | ||
| Truth | Positive | TP | FN |
| Negative | FP | TN | |
| Triple Modular Redundancy | |||
| TP | 494 | Accuracy | 0.9036 |
| TN | 475 | F1 | 0.9059 |
| FP | 2 | Precision | 0.9780 |
| FN | 88 | Recall | 0.8436 |
| - | - | ROC (AUC) | 0.9223 |
| CUSUM | |||
| TP | 460 | Accuracy | 0.8914 |
| TN | 475 | F1 | 0.8957 |
| FP | 2 | Precision | 0.9481 |
| FN | 122 | Recall | 0.8487 |
| - | - | ROC (AUC) | 0.8930 |
| EWMA | |||
| TP | 495 | Accuracy | 0.8734 |
| TN | 437 | F1 | 0.8704 |
| FP | 40 | Precision | 0.9955 |
| FN | 87 | Recall | 0.7731 |
| - | - | ROC (AUC) | 0.8833 |
| k-NN | |||
| TP | 484 | Accuracy | 0.8715 |
| TN | 475 | F1 | 0.8716 |
| FP | 2 | Precision | 0.9665 |
| FN | 98 | Recall | 0.7938 |
| - | - | ROC (AUC) | 0.9223 |
| - | 1. Set | 2. Set | 3. Set | 4. Set | 5. Set | 6. Set | Average |
|---|---|---|---|---|---|---|---|
| Triple Modular Redundancy | |||||||
| Accuracy | 0.9488 | 0.9943 | 0.7670 | 0.7443 | 0.9829 | 0.9834 | 0.9034 |
| F1 | 1 | 1 | 0.3050 | 0.8534 | 0.9914 | 0.9916 | 0.8569 |
| Precision | 1 | 1 | 0.9 | 1 | 1 | 1 | 0.9833 |
| Recall | 1 | 1 | 0.1836 | 0.7443 | 0.9829 | 0.9834 | 0.8157 |
| k-NN | |||||||
| Accuracy | 0.8863 | 0.9715 | 0.7727 | 0.7159 | 1 | 1 | 0.8910 |
| F1 | 1 | 1 | 0.3548 | 0.8344 | 1 | 1 | 0.8648 |
| Precision | 1 | 1 | 0.8461 | 1 | 1 | 1 | 0.9743 |
| Recall | 1 | 1 | 0.2244 | 0.7159 | 1 | 1 | 0.8233 |
| CUSUM | |||||||
| Accuracy | 1 | 1 | 0.7670 | 0.6818 | 0.8806 | 0.9116 | 0.8735 |
| F1 | 1 | 1 | 0.3278 | 0.8108 | 0.9365 | 0.9537 | 0.8381 |
| Precision | 1 | 1 | 0.8333 | 1 | 1 | 1 | 0.9722 |
| Recall | 1 | 1 | 0.2040 | 0.6818 | 0.8806 | 0.9116 | 0.7796 |
| EWMA | |||||||
| Accuracy | 0.9318 | 0.9943 | 0.7556 | 0.7329 | 0.9318 | 0.8839 | 0.8717 |
| F1 | 1 | 1 | 0.2950 | 0.8459 | 0.9647 | 0.9384 | 0.8406 |
| Precision | 1 | 1 | 0.75 | 1 | 1 | 1 | 0.9583 |
| Recall | 1 | 1 | 0.1836 | 0.7329 | 0.9318 | 0.8839 | 0.7887 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Babić, I.; Miljković, A.; Čabarkapa, M.; Nikolić, V.; Đorđević, A.; Ranđelović, M.; Ranđelović, D. Triple Modular Redundancy Optimization for Threshold Determination in Intrusion Detection Systems. Symmetry 2021, 13, 557. https://doi.org/10.3390/sym13040557
Babić I, Miljković A, Čabarkapa M, Nikolić V, Đorđević A, Ranđelović M, Ranđelović D. Triple Modular Redundancy Optimization for Threshold Determination in Intrusion Detection Systems. Symmetry. 2021; 13(4):557. https://doi.org/10.3390/sym13040557
Chicago/Turabian StyleBabić, Ivan, Aleksandar Miljković, Milan Čabarkapa, Vojkan Nikolić, Aleksandar Đorđević, Milan Ranđelović, and Dragan Ranđelović. 2021. "Triple Modular Redundancy Optimization for Threshold Determination in Intrusion Detection Systems" Symmetry 13, no. 4: 557. https://doi.org/10.3390/sym13040557
APA StyleBabić, I., Miljković, A., Čabarkapa, M., Nikolić, V., Đorđević, A., Ranđelović, M., & Ranđelović, D. (2021). Triple Modular Redundancy Optimization for Threshold Determination in Intrusion Detection Systems. Symmetry, 13(4), 557. https://doi.org/10.3390/sym13040557






