Abstract
Counterfeit products are internationally regarded as “the world’s second greatest public health hazards after drugs”. Counterfeiters produce counterfeit brand clothing and then sell them to consumers through unofficial channels; thus, consumers spend a lot of money without getting the value they deserve. With the rise of e-shopping, the safety and security of branded clothing supply chains are also under threat. Counterfeit branded apparel manufacturers generate profits while genuine manufacturers suffer, which ultimately violates the interests of the public. This study proposes a traceable anti-counterfeit management system for branded clothing based on Hyperledger Fabric technology. This system can achieve full traceability of the production information of branded clothing. It uses the unique characteristics of blockchain, such as being unforgeable, traceable, open, and transparent, and collectively ‘maintaining’, to record the specific production processes of the brand clothing, and ensure the authenticity and legitimacy of the production information of brand clothing. The end-user can self-verify the product’s authenticity by sharing the product’s details on the immutable framework. It solves problems surrounding information asymmetry, opaque supply chain data, and easy falsification in the production process of branded clothing in traditional branded clothing supply chains.
1. Introduction
1.1. Background
Branded clothing is favored by consumers, and is a target for counterfeiters who profit illegally. Regarding a brand-name product, especially an international brand, one must focus on the quality of the product, as well as the production, management, and use of legal methods to defend the interests and honor of the brand against counterfeiting. The situation is global, with up to 5% of EU imports being counterfeit [1]. Counterfeiting rings not only operate formulaically, to sell counterfeit products, they also exploit the transmission effects of the internet, to dump counterfeit goods through informal channels. Although social media networks are not the primary venues for commerce, such platforms are powerful tools for marketing products. They can drive sales to online stores with little or no regulation. The most extensive online platforms—YouTube, Facebook, WhatsApp, WeChat, Instagram, and TikTok—have billions of active users, and just as many potential customers. Studies have shown that almost one-fifth of the content posted on social media concerning branded apparel is illegal [2]. According to statistics, in 2020, the fashion industry will lose more than USD 50 billion due to counterfeit products. Designer clothing are the most counterfeited products, followed by cosmetics, watches, jewelry, and luggage. By 2022, the global trade in fakes is expected to reach USD 4.2 trillion [3].
From the above data, it is clear that counterfeiters make huge illegal financial gains by falsifying branded clothing, to the detriment of consumers. Moreover, cross-border issues deserve attention. Many counterfeiters sell foreign branded clothing in their own countries. Because customers do not have enough understanding of foreign brands, it is easy to buy counterfeit clothes, which could lead to certain economic losses. The root cause of this phenomenon is that consumers are unaware of the production process of branded clothing in the traditional supply chain. The entire process, from design, production, to sales of branded clothing, goes through many links, and any problems will eventually be harmful to consumers. In the traditional supply chain, only the brand company, manufacturer, and retailer have the core information of the brand clothing. The end consumer does not know the whole supply process of the brand clothing. This results in opaque and unequal information in the supply chain. In this model, consumers can easily suffer financial losses due to information asymmetry. Therefore, effective management methods and traceability technologies are the only way to achieve information symmetry between buyers and sellers.
As for the centralized management of traditional blockchain—we used blockchain technology to conduct decentralized control of data in the supply chain. Blockchain technology can solve the information opacity in brand clothing supply chains, protect the end consumers, and defend the legitimate rights of anti-counterfeiting detection. Therefore, this study proposes an anti-counterfeiting management system for traceable branded clothing based on Hyperledger Fabric technology. Most new technologies rely on the futuristic characteristics of the internet [4]. We utilized a decentralized, open, autonomous, and immutable blockchain for anti-counterfeit traceability of branded clothing through the effective combination of internet of things technology and blockchain technology. Hyperledger Fabric, as a new blockchain framework, focuses more on privacy protection and performance expansion and performs better than Ethereum in large supply chain operations. Therefore, Hyperledger Fabric technology is proposed as the main technology for research and discussion. More attention will be paid to data security, privacy protection, and regulations from the clothing supply chain to the commercial supply chain. Blockchain technology can provide good support in regard to the needs of the business supply chain. The combination of blockchain and supply chain management could solve problems and challenges, including the development trends surrounding commercial supply chains in the future. Therefore, blockchain-based product traceability systems are receiving increasing attention from the industry and academia [5].
1.2. Related Works
Traditional anti-counterfeiting methods on the market, regarding branded clothing, include trademark anti-counterfeiting, logo anti-counterfeiting, wheat washing anti-counterfeiting, laser engraved buttons, semi-invisible pattern lining, anti-counterfeit sewing thread, and direct printing anti-counterfeit marks on garments. However, these current anti-counterfeiting methods have some shortcomings. For example, it is difficult for consumers to recognize and identify (authenticity), and anti-counterfeiting costs are relatively high [6]. For this reason, many ideas have been proposed to get rid of these traditional (and easily forged) anti-counterfeiting methods, e.g., by combining modern technology with traditional techniques. Table 1 presents different anti-counterfeiting solutions for clothing. Although some articles use blockchain technology, they still have some shortcomings.

Table 1.
Comparison with existing anti-counterfeiting traceability methods.
Alzahrani et al. [7] similarly expressed that traditional supply chains have a single point of processing, storage, and failure problems in regard to anti-counterfeiting traceability through a centralized authority. Therefore, the technology of ‘block supply chain’ is proposed, which is a new decentralized supply chain that uses blockchain and communication technology to detect counterfeit attacks. However, the processes of some data are not well expressed. The framework proposed by Zhu et al. [8] for anti-counterfeit traceability of pharmaceuticals based on blockchain is also worth learning, which can ensure the transparency and openness of the pharmaceutical supply chain; the smart contract-based access control policy model is about preventing the drug information from being changed or disclosed at the nodes of the blockchain. The security of the framework would go further if the privacy of the data were enhanced. Bullón Pérez [9] present an updated traceability scheme and proposal for the apparel industry for ready-to-wear apparel, tracking suppliers and customers throughout the logistics chain. However, less specific data flow frameworks make this aspect unconvincing. Yiu et al. [10] present a feasible mechanism for developing a product orientation and traceability ecosystem using blockchain technology, mainly through a series of security and threat analyses, mainly for Near Field Communication (NFC) enabled anti-counterfeiting systems to identification. There is a lack of discussion in conjunction with physical objects. Agrawal et al. [11] presented a specific case study using blockchain technology to verify and track the supply chain of off-the-shelf apparel. However, it is difficult for buyers to self-verify the transaction information on the blockchain, as they lack some IoT technology.
The methods proposed above are all dedicated toward product anti-counterfeit traceability, but the current anti-counterfeit traceability methods still have some problems for buyers and supply chain participants. For buyers, currently proposed anti-counterfeit traceability methods do not provide a platform for anti-counterfeit inquiries and an arbitration mechanism. For supply chain participants, the current problem is that it is difficult to effectively manage the supply chain, find the source of the problem, and there is the lack of an arbitration mechanism to maintain the supply chain. In this paper, we propose an anti-counterfeit and traceable management system for brand clothing with the Hyperledger Fabric framework. This paper involves a cryptographic mechanism to encrypt the data, which further ensure the security of the data. It also combines the internet of things and blockchain technologies to trace the supply chain information of the production and sales process of branded clothing in real-time. The characteristics of blockchain are used to ensure the transparency and traceability of data in the supply chain. The proposed scheme ensures the correct transmission of data.
The paper is written in the following structure. Section 2 focuses on the relevant techniques used in our proposed scheme. Section 3 presents our specific proposal and the detailed process. In Section 4, we perform a security analysis and a discussion of the relevant features of the scheme. Section 5 gives a discussion of computational costs, communication performance, and comparisons. Finally, in Section 6, we present a summary of our scheme.
2. Preliminary
2.1. Blockchain
Blockchain is an important concept of Bitcoin, which is essentially a distributed database [12]. It has the characteristics of high reliability and high confidentiality and has good prospects in regard to effectively solving the trust problem between the two parties [13]. As the underlying technology of Bitcoin, blockchain is a string of data blocks generated using cryptographic methods of correlation, each containing information about a batch of Bitcoin network transactions, used to verify the validity of its information and to generate the next block. Blockchain technology has the following five characteristics: (1) characteristic distributed database; (2) uniqueness—each record is a timestamp and cannot be tampered; (3) transparency of data; (4) irreversibility of records; and (5) traceability. The application of blockchain technology in a supply chain and logistics is widely recognized as it records and stores all transaction information of stakeholders in the supply chain in a tamper-evident manner. It makes supply chain information more transparent and the receipt of information more symmetrical. Blockchain may significantly impact supply chain management, its relationships, and governance structures [14].
2.2. Hyperledger Fabric
Hyperledger Fabric (Hyperledger Architecture) is an open-source project launched by the Linux Foundation in 2015 to advance blockchain digital technology and transaction validation, with investments in industry giants, including finance, manufacturing, logistics shipping, and security consulting [15]. Hyperledger Fabric builds on the foundation of public chains to create an efficient, low-cost operating model, known as the federated chain model. Areas of application include, but are not limited to, dispute resolution, trade logistics, foreign exchange netting, food safety, contract management, diamond provenance, reward point management, low liquidity securities trading and settlements, identity management, and settlements via digital currencies [16]. Compared to the previous Ethereum platform, Hyperledger Fabric addresses performance scalability and privacy issues through fine-grained access control. Compared with Hyperledger Sawtooth, Hyperledger Fabric establishes the concept of the channel, which provides more comprehensive data protection and can better resist attacks from attackers. It is clear that Hyperledger Fabric allows fine-grained control over consistency, which improves performance, scalability, and privacy [17]. The introduction of the channel in Hyperledger Fabric plays a very good role in data privacy protection [18]. One of the frameworks of Hyperledger Fabric is shown in Figure 1.
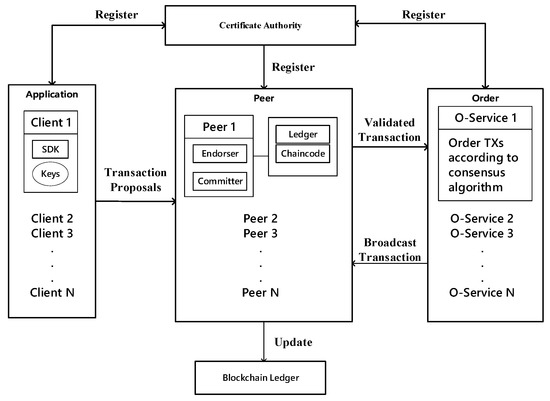
Figure 1.
Hyperledger Fabric framework diagram.
From Figure 1, we can see that the Hyperledger Fabric framework consists of four main parts: the application, the peer node, the order (ordering service node), and the certificate authority (CA) node.
Application: the Hyperledger Fabric provides an APP platform for clients to allow people or departments involved in the supply chain to more easily interface to the transactions within the blockchain. The initiation of transactions is done through the Software Development Kit (SDK), the SDK version is Fabric Node SDK 1.4. All communication messages need to contain signatures, and the signature certificates and public and private keys are obtained through the CA node. The client submits a transaction proposal to the endorsing node (endorser) and obtains the endorsed transactions from the endorser node. After collecting enough transactions, it broadcasts them to the sorting service node.
Peer node: the peer node is the main body involved in the transaction, which can represent each member involved in the chain, and is responsible for the execution of the smart contract in the consensus link. It contains various types of nodes; the main participating transaction nodes are the endorser node and committer node. The peer node also stores the ledger data and the chain code. After receiving a transaction proposal from the client, the endorsing node verifies the transaction signature, simulates the transaction’s execution, performs a signature endorsement on the result, and then sends the validated transaction to the order. The endorsing nodes are dynamic roles and are bound to specific chain codes that specify which nodes must complete a valid transaction endorsement. The peer node is the endorsing node only when the client initiates a transaction endorsement request to the peer node; otherwise, the peer node is just an ordinary committer node. It is only responsible for verifying the transaction.
Order: the primary function is to sort the transactions to ensure data consistency on each peer node. Order sorts transactions according to consensus algorithms and broadcasts the sorted transactions into the blockchain. The peer node updates the transactions to the ledger after passing the transaction information broadcasts by the order node to ensure data integrity. After receiving the sorted transaction information of the order node, the peer node will upload its data to the blockchain network and update the data in the blockchain network.
CA node: the peer node is responsible for authorizing and authenticating all nodes that join the blockchain, including the upper layer clients. Each of them has its certificate issued for Identification in the transaction process. For the Hyperledger Fabric blockchain framework, there are high requirements for authentication, from which, CA nodes play the role of authorizing users and signing transmissions. Peer nodes use digital certificates issued by CA for authentication, encrypting data transmission, authorizing users, managing user certificates, and other features to ensure data security in the blockchain network.
2.3. Elliptic Curve Digital Signature Algorithm (ECDSA)
Scott Vanstone first proposed the elliptic curve signature algorithm (ECDSA) in 1992 [19]. The security of the elliptic curve crypto signature regime is based on the intractability of the elliptic curve discrete logarithm problem. The elliptic curve discrete logarithm problem is far more complex than the discrete logarithm problem, and elliptic curve cryptosystems have higher cryptographic strength. This brings the benefits of smaller computational parameters, shorter keys, faster operations, and shorter signatures. Elliptic curve ciphers are therefore particularly suitable for applications where processing power, storage space, bandwidth, and power consumption are limited.
We can analyze how ECDSA works by simulating the signing and verification of messages between user A and user B using ECDSA. User A first sets the elliptic curve parameters , its corresponding key pair , is the private key of user A, is the public key of user A. User A can compute the public key from the private key , where is the parameter point in the ECDSA elliptic curve.
Signature process:
- User A generates a random number based on the ECDSA algorithm, uses points to calculate the public key .
- User A calculates the hash value of the message : .
- User A calculates the eigenvalues of an elliptic curve , of which , ( is the multiplicative inverse of the modulus of ).
- is the digital signature of user A. User A sends the elliptic curve parameters and User A’s public key to User B for verification of the correctness of the signature.
Validation process:
- User B calculates the hash value of the message : .
- Calculation and .
- The calculation , if then the signature is validated.
2.4. Smart Contract
Blockchain is a global decentralized distributed database ledger, and smart contracts are software programs executed in a decentralized manner based on blockchain technology [20]. Blockchain technology can achieve collaboration and trust between multiple enterprise entities through smart contracts, thereby expanding the scope and depth of mutual cooperation between parties [21]. An event-driven, stateful program runs on top of the blockchain system and can hold and process digital assets on the blockchain ledger. The development of blockchain technology provides an excellent operating basis for smart contracts, which can play an important role in the blockchain. Smart contracts guarantee important features of blockchain technology: data cannot be deleted or modified, only added, ensuring traceability of history, while the cost of doing malicious acts will be high, as its malicious acts will be recorded forever.
Smart contracts based on blockchain technology can bring into play the advantages of smart contracts, in terms of cost efficiency, and avoid the interference of malicious acts in the normal execution of contracts. The smart contract is written into the blockchain in digital form. The characteristics of blockchain technology guarantee that the whole process of storage, reading, and execution is transparent, traceable, and unchangeable. At the same time, a state machine system is built by the consensus algorithm that comes with the blockchain, which enables smart contracts to operate efficiently.
2.5. BAN Logic
BAN logic, introduced by Burrows, Abadi, and Needham, is a cognitive logic for analyzing security protocols. It models the knowledge of topics in a protocol at a level of abstraction [22]. Specifically, BAN logic helps users determine whether the information exchanged is trustworthy, resistant to eavesdropping, or both. BAN logic begins in situations where information is vulnerable to tampering during the exchange period. Typical BAN logic includes: (1) verifying the source of the message; (2) verifying the ‘freshness’ of the message; (3) verifying the credibility of the source.
2.6. Threat Model
In related works, we conducted a brief review of previous research and identified problems and shortcomings that some research currently has. As a result, we compiled some possible threat patterns usually caused by security issues and vulnerabilities in the system. The security of the blockchain is also relative and, therefore, this system is potentially risky.
- Mutual authentication: the current internet environment is due to the network nature of blockchain. Participants need to authenticate with each other to determine whether they are receiving correct and secure messages. This feature comes about precisely because of the decentralized blockchain network. This also allows the communication between the two in the blockchain network to be secure and guaranteed.
- Data integrity: when using the system for transactions, all data present in the system must be processed in an integrated manner. The system must ensure the integrity of the data when conducting transactions and the system must ensure that the data cannot be tampered with by anyone when it is transmitted and stored.
- Non-repudiation: the transactions in the blockchain network are transmitted and stored through the chain code; therefore, to perform anti-counterfeiting and traceability verification, all transactions must be verified by an ECDSA digital signature to ensure the non-repudiation of the data. The deployment of the chain code ensures that the data have a non-repudiation effect and it makes the information more secure.
- Known attack problems: blockchain networks are also subject to attacks by illegal nodes and illegal persons, which contain different types of attacks.
- (1).
- Man-in-the-middle attacks: in a blockchain network, when the sender communicates with the receiver, an attacker performs a man-in-the-middle attack by intercepting messages during the communication process. The specific process is: the attacker intercepts the message sent by the sender to the receiver and tampers with the message content. The attacker sends the altered message to the receiver instead of the sender to perform the man-in-the-middle attack.
- (2).
- Replay attack: an attacker will resend the data obtained after eavesdropping on the sender to the receiver untouched. The attacker does not need to know the exact meaning of the data, but only know what the data do to attack the receiver, by sending the data again without knowing its content.
3. Proposed Scheme
3.1. System Architecture
For the process of clothing production, from the time a company decides to start producing clothing to the time the finished garment appears. It goes through the following stages. The supply chain flow of brand clothing is shown in Figure 2—brand company (BC), material supplier (MS), manufacturer (MF), retailer (R) form the alliance chain. The alliance chain, together with the customer (CU) and third party (TP), will form a Hyperledger Fabric-based brand clothing anti-counterfeiting management system. The system framework is shown in Figure 2.
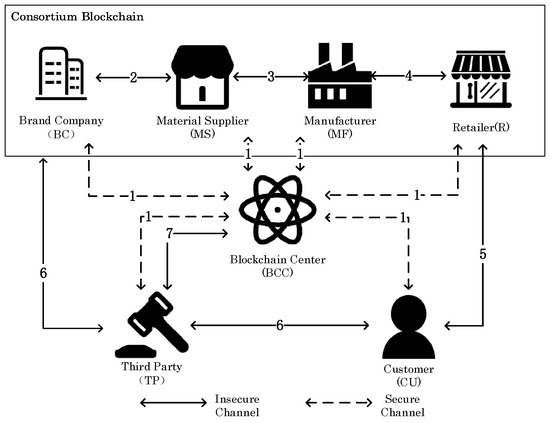
Figure 2.
System framework diagram.
- Brand company (BC): the brand clothing company. This role manages and determines the design and production of clothing. The production of brand clothing requires a license from the company. The supply chain only works when the brand clothing company decides to produce the clothing.
- Material supplier (MS): this role provides the raw materials for the production of clothing products. The BC will first send the production license of the clothing and the transaction information of all types of orders to MS, which will provide the raw materials according to the orders and keep a record of the origin of the raw materials.
- Manufacturer (MF): first, the MF receives the raw materials and order information from the MS. The MF is then responsible for processing the raw materials into garments. MF will inlay the unique identification code on each garment. Each piece of clothing corresponds to a unique identification code. Domestic and foreign customers can scan the identification code through the client interface to enter the blockchain network to query the information of the brand clothing.
- Retailer (R): the retailer will receive the garments from the manufacturer, confirm the order information, return it to the MF, and sell the garments to the customer, and then upload the transaction information to the blockchain.
- Customer (CU): the customer can use the mobile app or scan the code to see all of the information about the product. Moreover, the CU could inspect the entire production process of a finished product.
- Blockchain center (BCC): a Hyperledger Fabric-based blockchain framework that detects the legitimacy of participants. Moreover, it will record various information uploaded to the blockchain by participants.
- Third Party (TP): all transactions can be accessed by linking to the blockchain network, regardless of whether the clothing is at the design stage, the raw material supply stage, the clothing design stage, or the retail stage. All information can be accessed to detect counterfeit or illegal branded products.
There are the seven ‘actors’ from the supply chain flow framework for a Hyperledger Fabric-based anti-counterfeit management system for traceable brand clothing. The specific process is shown in Sequence Figure 3. The specific steps are:
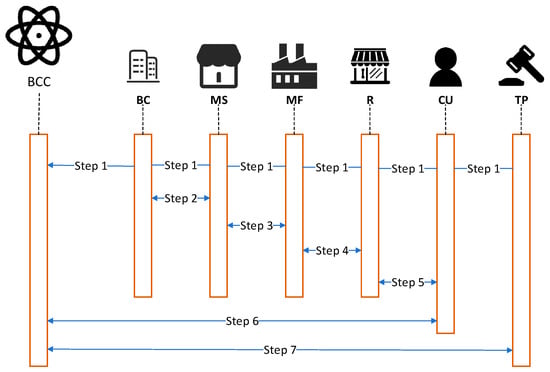
Figure 3.
Stakeholders’ transaction sequence diagram.
- Step 1.
- This step is the registration phase for each role in the system. All participants in the clothing brand company (BC), material supplier (MS), manufacturer (MF), retailer (R), customer (CU), and third party (TP) need to be authenticated at the CA node in the blockchain network. After passing authentication, the roles can exchange information through the channel.
- Step 2.
- When the BC wants to produce clothes, the BC first sends the production certificate, raw material order, and the production plan to the MS. The MS confirms the production information and starts to collect the raw material, and the MS sends a response message to BC when it is finished. BC uploads the relevant information to the blockchain center through the sorting node and updates the local ledger after ensuring the ordering information is correct.
- Step 3.
- When the MS prepares raw materials for garment production, it will send the raw materials and production information to the MF, which will compare the production information with the raw materials received in reality to ensure the legitimacy of the data, and send a response message to the MS. When the MF processes the raw materials into garments, it will mark a unique identification code on each garment, and the CU can check the information of the garments on the blockchain, according to the identification code.
- Step 4.
- The R will send the order to the MF, which will confirm the order from the R, provide the garment based on the order information, upload the confirmed order information to the blockchain center, and then send the garment and certificate to the R. After confirming that the garment information is the same as the order, the R will return the confirmed information to MF.
- Step 5.
- The CU can purchase brand clothing through the R. After the R determines the transaction information applied by the CU, it will upload the transaction information to the blockchain center. At this point, the whole supply chain ends, and all data will be operated on the chain at various stages, and the integrity of the data will be guaranteed.
- Step 6.
- The CU can use the identification code on the garment to join the blockchain network with an app or client to check the garment’s production process and raw material information. If the CU finds out that he/she has purchased a counterfeit garment, he/she can submit an arbitration application with a third party.
- Step 7.
- The third party will go to the blockchain center to examine the information based on the arbitration request provided by the CU for each transaction and operation in the supply chain, and check whether the name-brand clothing is correct or not in the supply chain during the process. The legitimacy and validity of the brand clothing can be verified by examining the signature information of each department.
3.2. Hyperledger Fabric Detailed Transaction Information Flow
The transaction process in the Hyperledger Fabric-based blockchain framework is shown in Figure 4, which shows in detail how two companies in the supply chain interact with each other. If Company A and Company B interact for necessary information in the supply chain, Company A and Company B will each form an organization (as Organization A and Organization B). They will also register through a certificate authority (CA) node, which will return their corresponding public and private keys and digital identity credentials. Company A and Company B then create their respective Organization (Org), which will contain various nodes (endorser node, committer node, anchor node, and leader node), collectively known as peer nodes. Each peer node in an organization can deploy one or more chain codes and will store a copy of the ledger in the channel. The order node sorts and packages the transactions and information interactions generated in the channel, and uploads transaction information to the Blockchain Center. At this point, Company A and Company B can conduct transactions and information interactions in the Hyperledger Fabric network framework.
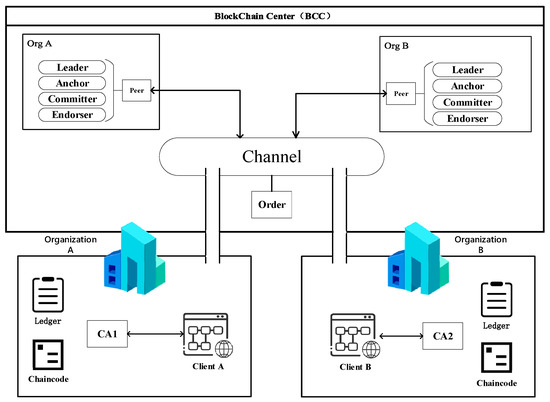
Figure 4.
Trading Information Framework of Hyperledger Fabric.
Suppose that Organization A and Organization B want to interact with each other. In that case, firstly, Organization A and Organization B register with the CA node of each organization through the client of each organization, and the CA node returns the authentication certificate, public key, and private key to verify the validity of their identities. Organization A encrypts the transaction information with the distributed public key and uploads the encrypted information to the blockchain through the order node via the peer node. Organization B receives the transaction information uploaded to the blockchain by Organization A through the channel and triggers the chain code to update the local blockchain ledger for data storage. In the overall framework, the information interaction between two different functions is mainly done through channels.
3.3. Initialization Phase
During the initialization phase, each company with different roles forms an organization. Figure 5 represents the basic chain code structure in the Hyperledger Fabric network architecture that we designed. The left side of the structure stores the information of designer apparel, and the right side shows the structure and enumeration of role types of the roles participating in the supply chain. When a designer apparel product is manufactured in the supply chain, each detail is appended to the chain code structure through the roles involved in the supply chain.
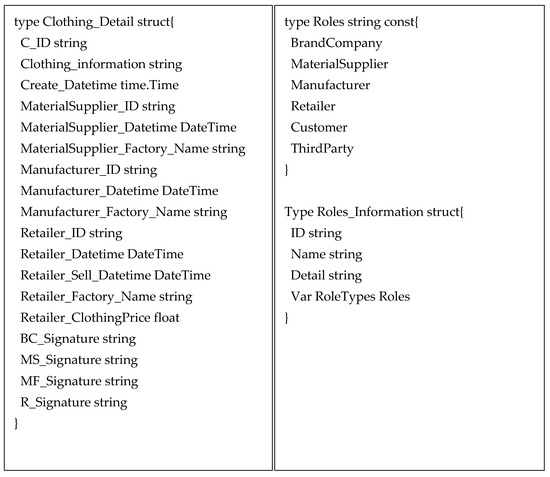
Figure 5.
Chain code of famous brand clothing structure.
3.4. Registration Phase
All nodes that want to join the Hyperledger Fabric blockchain network, including the BC, MS, MF, R, CU, and TH, need to register with the certificate authority (CA) node in the Blockchain Center, and will be given a corresponding public and private key. We use ‘Roles X’ to represent all arbitrary roles in the blockchain system; Figure 6 represents the flowchart of the registration phase.
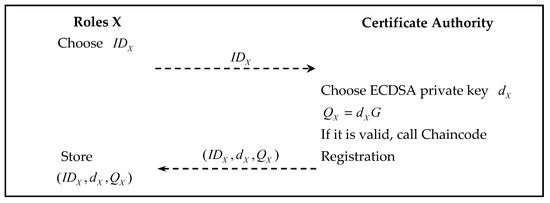
Figure 6.
Registration Stage Flow Chart.
- Step 1.
- The name is generated for all roles (Roles X) participating in the anti-counterfeit and traceable management system. The generated is then sent through the application to the CA nodes in the blockchain network for registration and verification, for the legitimacy of their identities.
- Step 2.
- The CA node in the blockchain network generates the private key based on the system role and calculate the public key :After verifying the registration of all system roles, the chain code Algorithm 1 is triggered. The CA node sends the generated to Roles X.
Algorithm 1. A scheme for a chain code registration. var X[]Roles X
func Registration (X_name string, X_detail string, var X_role RoleType) (C_ID string) {
C_ID = GenerateUniqueID()
X = append (X, Roles X{
ID: C_ID,
Name: X_name,
Detail: X_detail,
Role: X_role,
})
return C_ID
} - Step 3.
- The role in the system receives its signature message parameter and stores it.
3.5. Clothing Design Phase
This phase is the clothing design phase, and the main players involved are the brand company (BC) and material supplier (MS). The flowchart is shown in Figure 7, and the related chain code is shown in Algorithms 2 and 3.
| Algorithm 2. A scheme for a communication protocol. |
| func Sign (h string,k string, d string)(r string, s string){ (x,y) = k*G; r = x%n s = (h + r*d)/x%n return r,s } func Verify(h string,r string,s string)(result string){ u1 = h/s%n u2 = r/s%n (x,y) = u1*G + u2*Q If x = r{ return “valid” }else{ return “invalid” } } |
| Algorithm 3. Chain code of the clothing design phase. |
| func BrandCompany (ID_BC string, ID_MS string, C_INF string, C_IDs []string, Signature string) { for i:= 0; i < C_IDs.Length; i++ { index:= SearchC_ID(C_IDs[i]); TP[index].Clothing_Detail.BrandCompany_ID = ID_BC TP[index].Clothing_Detail..Clothing_information = C_INF TP[index].Clothing_Detail.Create_Datetime = time.Now() TP[index].Clothing_Detail.MaterialSupplier_ID = ID_MS TP[index].Clothing_Detail.BC_Signature = Signature } } func MaterialSupplier (ID_BC string, ID_MS string, MSname string, C_IDs []string, Signature string) { for i:= 0; i < C_IDs.Length; i++ { index:= SearchC_ID(C_IDs[i]); TP[index].Clothing_Detail.MaterialSupplier_ID = ID_MS TP[index].Clothing_Detail.MaterialSupplier_Factory_Name =MSname TP[index].Clothing_Detail. MaterialSupplier_Datetime = time.Now() TP[index].Clothing_Detail.BrandCompany_ID = ID_BC TP[index].Clothing_Detail.MS_Signature = Signature } } |
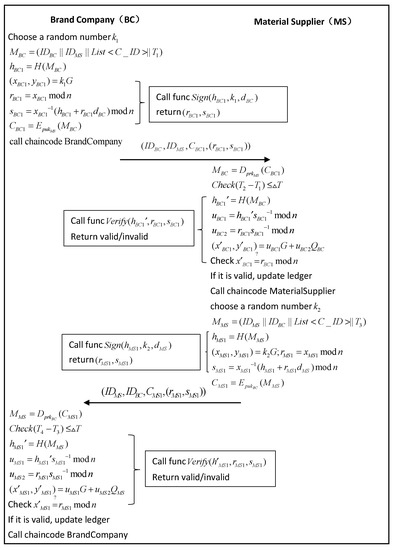
Figure 7.
Clothing design phase.
- Step 1.
- When the BC wants to produce branded clothes, the MS needs to be provided with information on the raw materials required for the production of branded clothes as well as product information. The BC randomly selects a random number and generates a message containing a list of :The BC calculates its hash value and executes the “Sign” algorithm used to generate the signature ; The “Sign” algorithm is shown in Algorithm 2:Its generated encrypted messages is encrypted by the MS public key:Then BC executes the chain code function “BrandCompany”, and the algorithm is shown in Algorithm 3. Send the message to the MS.
- Step 2.
- The MS receives the above message at a time and first decrypts the message with its private key:Subsequently, MS verifies the validity of the timestamp:The MS then uses “Verify” in Algorithm 2 to compute the hash value to verify the message:If the signature is valid, MS executes the chain code function “MaterialSupplier” with the algorithm shown in Algorithm 3. The MS will provide raw material and update the local ledger based on the transaction information in the encrypted message . The MS randomly selects a random number for generating the response message:The MS calculates its hash value and executes the “Sign” algorithm in Algorithm 2 to generate the signature :Its generated encrypted messages are encrypted by the BC’s public key:Send the response message to the BC.
- Step 3.
- The BC receives the response message and first decrypts the message with the private key:The validity of the timestamp is then confirmed by comparing:The BC verifies the message by computing the hash value of “Verify” in Algorithm 2:If the signature is valid, the BC updates the response message from the MS to its book, and the BC executes the chain code function “BrandCompany” with the algorithm shown in Algorithm 3.
After the above three steps, the clothing design phase is complete. Moreover, the raw material quantity and designer clothing design details should be updated in the account book.
3.6. Clothing Production Phase
This phase is the clothing production phase; the main players involved are the material supplier (MS) and manufacturer (MF). The flowchart is shown in Figure 8, and the related chain code is shown in Algorithm 4.
| Algorithm 4. Chain code of clothing production phase. |
| func MaterialSupplier (ID_ MS string, ID_MF string, MSname string, C_IDs []string, Signature string) { for i:= 0; i < C_IDs.Length; i++ { index:= SearchC_ID(C_IDs[i]); TP[index].Clothing_Detail.MaterialSupplier_ID = ID_MS TP[index].Clothing_Detail.MaterialSupplier_Factory_Name =MSname TP[index].Clothing_Detail. MaterialSupplier_Datetime = time.Now() TP[index].Clothing_Detail. Manufacturer _ID = ID_MF TP[index].Clothing_Detail.MS_Signature = Signature } } func Manufacturer (ID_ MF string, ID_MS string, MFname string, C_IDs []string, Signature string) { for i:= 0; i < C_IDs.Length; i++ { index:= SearchC_ID(C_IDs[i]); TP[index].Clothing_Detail.Manufacturer_ID = ID_MF TP[index].Clothing_Detail.Manufacturer _Factory_Name =MSname TP[index].Clothing_Detail.Manufacturer _Datetime = time.Now() TP[index].Clothing_Detail.MaterialSupplier _ID = ID_MS TP[index].Clothing_Detail.MF_Signature = Signature } } |
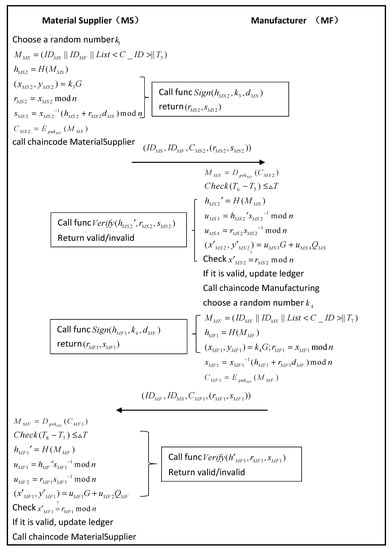
Figure 8.
Clothing production phase.
- Step 1.
- The MS provides raw materials for branded apparel to the MF for manufacturing branded clothing based on production information provided by the BC, and the MS needs to provide raw material information and production information for branded clothing to the MF. The MF produces clothes based on raw materials received in real life. The MS randomly selects a random number and generates a message containing a list of :The MS calculates its hash value and executes the “Sign” algorithm in Algorithm 2 to generate the signature :Its generated encrypted messages are encrypted by the MF’s public key:Then, the MS executes the chain code function “MaterialSupplier”; the algorithm is shown in Algorithm 4. Send the production-related information of the branded clothing to MF .
- Step 2.
- The MF receives the above message and first decrypts the message with its private key:Subsequently, the MF checks the validity of the timestamp:The MF then verifies the message by calculating the hash value with “Verify” in Algorithm 2:If the signature is valid, the MS updates the local ledger with the transaction information in the encrypted message . The MF executes the chain code function “Manufacturer” with the algorithm shown in Algorithm 4. After the manufacturing of the designer clothes is completed, the MF sends a response message to the MS. The MF randomly selects a random number for generating the response message:The MF calculates its hash value and executes the “Sign” algorithm in Algorithm 2 to generate the signature :Its generated encrypted messages are encrypted by the MS public key:Send the response message to the MS.
- Step 3.
- The MS receives the response message and first decrypts the message with the private key:The validity of the timestamp is then confirmed by calculating:The MS verifies the message by calculating the hash value of “Verify” in Algorithm 2:If the signature is valid, the MS updates the MF’s response message to its book, and the MS executes the chain code function “MaterialSupplier” with the algorithm shown in Algorithm 4.
After the above three steps, the clothing production phase is complete. The information of the produced branded clothing in the ledger should be updated.
3.7. Clothing Distribution Phase
This phase is the clothing production phase; the main players involved are manufacturer (MF) and the retailer (R). The flowchart is shown in Figure 9, and the related chain code is shown in Algorithm 5.
| Algorithm 5. Chain code of the clothing distribution phase. |
| func Manufacturer (ID_ MF string, ID_R string, MFname string, C_IDs []string, Signature string) { for i:= 0; i < C_IDs.Length; i++ { index:= SearchC_ID(C_IDs[i]); TP[index].Clothing_Detail.Manufacturer_ID = ID_MF TP[index].Clothing_Detail.Manufacturer _Factory_Name = MSname TP[index].Clothing_Detail.Manufacturer _Datetime = time.Now() TP[index].Clothing_Detail.MaterialSupplier _ID = ID_MS TP[index].Clothing_Detail.MF_Signature = Signature } } func Manufacturer (ID_ R string, ID_MF string, R_sell_datetime string, C_IDs []string, Signature string) { for i:= 0; i < C_IDs.Length; i++ { index:= SearchC_ID(C_IDs[i]); TP[index].Clothing_Detail.Retailer_ID = ID_MF TP[index].Clothing_Detail.Retailer _Sell_Datetime = R_sell_datetime TP[index].Clothing_Detail.Retailer _Datetime = time.Now() TP[index].Clothing_Detail.Retailer _ID = ID_R TP[index].Clothing_Detail.R_Signature = Signature } } |
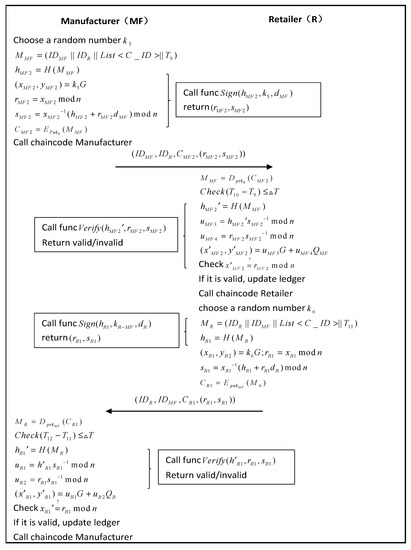
Figure 9.
Clothing distribution phase.
- Step 1.
- The MF processes and manufactures the raw materials based on the raw material and production information provided by the MS, and sends the manufactured branded clothes to retailers for sale. The MF needs to provide branded clothing products and information on the production of branded clothing to the R. The R sells branded clothes based on the received in real life. MF randomly selects a random number and generates a message containing a list of .The MF calculates its hash value and executes the “Sign” algorithm in Algorithm 2 to generate the signature :Its generated encrypted messages are encrypted by the R’s public key:Then, the MF executes the chain code function “Manufacturer”; the algorithm is shown in Algorithm 5. Send the information related to the production of brander clothes to the R.
- Step 2.
- The R receives the above message and first decrypts the message with its private key:The R will then check the validity of the timestamp:Then, the R verifies the message by calculating the hash value with “Verify” in Algorithm 2:If the signature is valid, the R updates the local ledger based on the transaction information in the encrypted message . The R executes the chain code function “Retailer” with the algorithm shown in Algorithm 5. After the retailer receives the branded clothes products from the manufacturer, the R sends a response message to the MF. The R randomly selects a random number for generating the response message:The R calculates its hash value and executes the “Sign” algorithm in Algorithm 2 to generate the signature :Its generated encrypted messages is encrypted by the MF’s public key:Send the response message to the MF.
- Step 3.
- The MF receives the response message and first decrypts the message with the private key:Then to confirm the validity of the timestamp:The MF verifies the message by calculating the hash value of “Verify” in Algorithm 2:If the signature is valid, the MF updates the response message from the R to its book, and the MF performs the chain code function “Manufacturer” to the chain and updates the book information; the algorithm is shown in Algorithm 5.
After the above three steps, the clothing distribution phase is complete. The information of the designer apparel received by the retailer in the ledger should be updated.
3.8. User Authentication Phase
After a consumer receives the branded clothing item, to verify the legitimacy of his/her branded clothes, the consumer can connect to the blockchain hub via an application to query the information about the apparel, to confirm the correctness of the apparel. The process is shown in Figure 10.
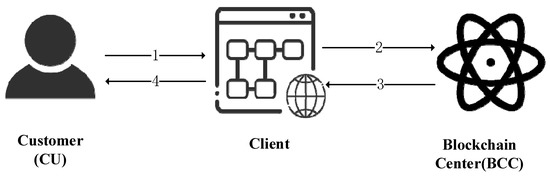
Figure 10.
Flow chart of user query information.
- Step 1.
- Customers use the application to search for consumption information, such as the number of the designer apparel (C_ID), the designer apparel company logo, the manufacturer logo, and the purchase time stamp.
- Step 2.
- The client can call the GetHistoryForKey () method of the ChaincodeStubInterface interface to query its history. Its chain code algorithm is shown in Algorithm 6 to query the ledger.
| Algorithm6. Call the chaincode to query the ledger |
| historyIter, err := stub.GetHistoryForKey(yourKey) if err != nil { fmt.Println(errMsg) return shim.Error(errMsg) } if historyIter.HasNext() { modification, err := historyIter.Next() if err != nil { fmt.Println(errMsg) return shim.Error(errMsg) } fmt.Println(“Returning information related to”, string(modification.Value)) |
- Step 3.
- If the C_ID provided by the client is legitimate and valid, then the blockchain center will return the ledger information associated with it. If the C_ID provided cannot be queried in the blockchain center’s ledger, we could confirm it is an illegally counterfeited brand-name clothing item.
- Step 4.
- The APP program displays the results of the chain code, in which consumers can get the legitimacy and production information of the branded clothing products to confirm whether they are buying the legal and correct goods.
3.9. Arbitration Phase
In fact, when any of the actors involved in the supply chain have doubts about the authenticity of the designer apparel, they can arbitrate the system’s legitimacy through a third party arbiter. Among the arbiters are the four supply chain sectors of the federated chain and the consumer. The third party validates the arbitration requests of its actors; the third party validation phase is shown in Figure 11.
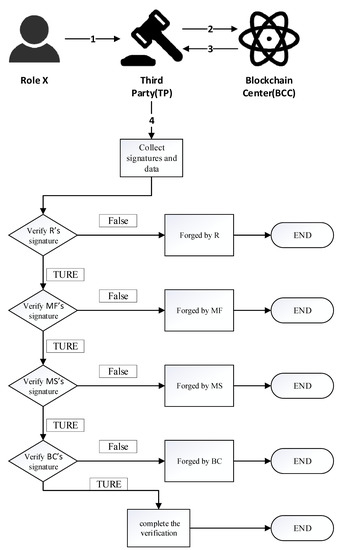
Figure 11.
Arbitration phase flow chart.
- Step 1.
- All participants provide information, such as the number (C_ID) and signature message of the designer apparel to the third party to query and verify the legitimacy of the designer apparel.
- Step 2.
- The third party sends a request with the participant’s signature information and C_ID to the blockchain center via its C_ID.
- Step 3.
- The blockchain center verifies the legitimacy of its signature and returns a list of its corresponding messages if it is legitimate.
- Step 4.
- The third party checks the signature and the steps are:
- The third party will first collect signatures and data.
- Check the signature of the retailer (R), and if the R’s signature is illegal, determine that the R falsified the record.
- If the signature of the retailer (R) is legal, the signature of the manufacturer (MF) is examined, and if the MF’s signature is illegal, the MF is judged to have falsified the record.
- After the signature of the manufacturer (MF) is deemed legal, the signature of the material supplier (MS) is checked, and if the signature of the MS is illegal, the MS is judged to have falsified the record.
- If the signature of the material supplier (MS) is legal, then inspect the signature of the brand company (BC), and if the BC’s signature is illegal, determine that the BC falsified the record. If all signatures are valid and legal, the third party determines that there are no illegal records.
4. Security Analysis
4.1. Mutual Authentication
In the mutual authentication phase, we use BAN logic for mutual authentication between two participants, where we first list the relevant symbols of BAN logic, as follows:
| believes (belief rule) | |
| sees (seeing rule) | |
| once said (message meaning rule) | |
| has jurisdiction over (jurisdiction rule) | |
| The message is new (freshness rule) | |
| The message is encrypted by a key | |
| and use a shared key to communicate |
We take user A and user B as an example in this phase. We mainly use BAN logic to make the authentication between company A and company B. The objectives of the authentication analysis are shown below.
According to the BAN logic authentication algorithm, the following ideal form is generated:
We present the following assumptions to analyze the proposed program:
- User B authenticates User ABy M1 and the seeing rule, we can derive:(Statement 1)By A2 and the freshness rule, we can derive:(Statement 2)By (Statement 1) and the message meaning rule, we can derive:(Statement 3)By (Statement 2), (Statement 3), and the nonce verification rule, we can derive:(Statement 4)By (Statement 4) and the belief rule, we can derive (G4):(Statement 5)By (Statement 5), A6, and the jurisdiction rule, we can derive (G3):(Statement 6)By (Statement 4) and the belief rule, we can derive (G8):(Statement 7)By (Statement 7), A8, and the belief rule, we can derive (G7):(Statement 8)
- User B authenticates User ABy M2 and the seeing rule, we can derive:(Statement 9)By A3 and the freshness rule, we can derive:(Statement 10)By (Statement 9) and the message meaning rule, we can derive:(Statement 11)By (Statement 10), (Statement 11) and the nonce verification rule, we can derive:(Statement 12)By (Statement 12) and the belief rule, we can derive (G2):(Statement 13)By (Statement 13), A5, and the jurisdiction rule, we can derive (G1):(Statement 14)By (Statement 12) and the belief rule, we can derive (G6):(Statement 15)By (Statement 15), A7, and the belief rule, we can derive (G5):(Statement 16)
According to (Statement 6), (Statement 8), (Statement 14), and (Statement 16), we can prove that mutual authentication between user A and user B is possible. Two different users can authenticate their identities to each other.
4.2. Data Integrity
In this study, we used the Elliptic Curve Encryption Algorithm (ECDSA) to sign the message transmission between participants, to ensure the integrity and ‘tamper proofness’ of the message transmission process. We use the clothing design phase as an example; when the designer apparel company wants to send a message to the raw material provider for information interaction, the designer apparel company generates the ECDSA signed value . The branded clothing company sends its public key , digital signature , and a message encrypted with the manufacturer’s public key to the manufacturer. An external attacker cannot obtain the manufacturer’s private key because it is not available. Thus, it is impossible to attack the data after it has undergone ECDSA signing. The manufacturer receives the message and decrypts it with its private key. Calculation:
Determine if the data are complete by comparing whether and are equal.
From the above description, we can see that this study uses the ECDSA signature technique to ensure the integrity of the data during transmission effectively.
4.3. Non-Repudiation
Since each stage requires signature verification by ECDSA, we can achieve the problem of data non-repudiation by verifying ECDSA. Since each data transmission requires the signature of its private key, the receiver also needs the public key for verification. The receiver will not reject the content of the message sent by the sender after verifying the correctness and legitimacy of the message. Table 2 shows the non-repudiation in each stage.

Table 2.
Non-repudiation of the proposed scheme.
4.4. Resist Known Attacks
4.4.1. Man-in-the-Middle Attack
The man-in-the-middle attack means that, after the sender of a transaction comes through the blockchain to send a transaction, the receiver has not confirmed it as yet. By modifying the data in the transaction, the attacker can change the data in the transaction into a new transaction. This can make the transaction received by the receiver different from the one sent by the sender. In severe cases, the transaction will be considered illegitimate and will not be validated. We prevent man-in-the-middle attacks by adding encryption and decryption mechanisms to the communication protocol. These encryptions and decryptions are shown in the following equations. Equations (5), (6), (13), (14), (21), (22), (29), (30), (37), (38), (45) and (46). For example, in the clothing design phase, when the designer apparel company wants to send a message to the raw material provider for information interaction, the BC encrypts it using the public key of the MS, and the MS decrypts it after receiving the encrypted message with the private key of the MS. The related equation is:
Scenario: the attacker eavesdrops or tampers with the message sent by the sender and then changes the content of the message before sending it to the receiver.
Analysis: the sender encrypts the message with the public key of the receiver, and the receiver can only decrypt the message if it has its associated private key. The attacker cannot decrypt the message because it does not have the receiver’s private key and, thus, cannot tamper with the message to perform a man-in-the-middle attack.
4.4.2. Replay Attack
To prevent replay attacks, we add information, such as timestamps, when verifying messages. The timestamp needs to be verified in each data transmission phase, and the verification process is shown in the following equations. Equations (7), (15), (23), (31), (39) and (47). For example, in the clothing design phase, when the designer apparel company wants to send a message to the raw material provider for information interaction, the designer apparel company will add a timestamp to the message when sending the message, where the timestamp is unique. BC adds the timestamp to the message M. Then, the message is encrypted and MS de-crypts it after receiving the encrypted message. The validity of the timestamp is then checked. The relevant equation is:
Scenario: after the attacker eavesdrops on the message sent by the sender, the attacker sends the same message to the receiver to perform a replay attack.
Analysis: the receiver decrypts the received encrypted message to get the unique timestamp in the message and then subtracts the timestamp from the current time, and if the timestamp is invalid, it is determined to be a replay attack.
4.5. Privacy Protection
For data privacy protection at the ledger level, Hyperledger Fabric invokes the concept of a channel. The role of a channel isolates the scope of data flow in the blockchain network, and members of organizations not within the channel have no access to data within the channel. Within the same Hyperledger Fabric federation network, participants can create multiple different channels according to their business needs, thus ensuring that data flows only within a specific organization. The introduction of channels greatly protects the privacy of data. The participants authenticate and register by sending them to the CA node. If the CA verifies the legitimacy of the participant, it will return its corresponding public-private key .
Scenario: Non-supply chain participants want to access information in the supply chain for illegal access to information.
Analysis: Non-supply chain participants cannot join the channel by authenticating with CA nodes, as they cannot join the channel. Therefore, the data in the channel cannot be accessed. Thus, the privacy of information is protected.
4.6. Traceability and Tamper-Proof
After the information of famous brand clothing is uploaded to the blockchain, the information about famous brand clothing in the ledger will be kept in the blockchain forever and cannot be tampered with. All the production process and transaction information related to brand clothing will be tracked throughout the process. For example, in the clothing design phase, when the brand company wants to send a message to the raw material provider for information interaction, we can compare and verify if the blockchain data between BC and MS is legitimate if we want to verify and track it. The equation is:
Scenario: the customer found a manufacturing flaw in the brand clothing, but could not identify where the error had occurred.
Analysis: use the traceability and immutability in blockchain to verify and compare information in blockchain to ensure that it is traceable.
5. Discussion
5.1. Communication Analysis
In Table 3, we analyze the communication efficiency of the system. Communication efficiency analysis includes the registration phase, clothing design phase, clothing production phase, and clothing distribution phase. Due to the different communication environments, we will discuss 3G, 4G, and 5G separately. The maximum transmission speed of 3G is 6 Mbps, 4G is 100 Mbps, and the maximum transmission speed of 5G is 20 Gbps.

Table 3.
Communication cost comparison table.
By analyzing the communication protocol, we assume that the identity information (ID) requires 144 bits, the cryptographic message requires at least 512 bits, and the signed message requires 1024 bits. Let us take the clothing distribution phase as an example. The MF sends two IDs, a signed message and an encrypted message. The encrypted message includes two IDs and timestamps and two others. The total size is 2 × 144 bits + 1 × 1024 bits + 2 × 144 bits + 1 × 80 bits + 2 × 320 bits = 2320 bits. The response message sent by the MS consists of two IDs, a signature message, and an encrypted message. The encrypted message includes two IDs, a timestamp, and four others. Total size is 2 × 144 bits + 1 × 1024 bits + 2 × 144 bits + 1 × 80 bits + 4 × 320 bits = 2980 bits. The clothing distribution phase total is 2320 bits + 2980 bits = 5300 bits. We can conclude that the transmission of all messages in 3G requires 883 µs; in 4G, it costs 53 µs; while in 5G, it only costs 0.265 µs.
5.2. Computation Cost
In this study, we analyze the calculated costs. In each phase, each participant needs to perform asymmetric encryption and decryption using ECDSA. This includes a series of calculations, such as calculating hash functions, addition, subtraction, multiplication, and division as the basis for calculating cost calculations. We compare the computational costs of each phase in Table 4 for the effective perception of computational costs.

Table 4.
Calculated cost comparison.
5.3. Blockchain Architecture Comparison
There are many blockchain architectures on the market (it is an evolving technology). From the earliest bitcoin, Ethereum, to the present Hyperledger Fabric. Each blockchain architecture has its own characteristics. Table 5 presents a comparison of the main architectures in blockchain.

Table 5.
Comparison table of main features of blockchain architecture.
Through the comparison table above, we can easily see that Hyperledger Fabric is more suitable for the application of the federation chain. Hyperledger Fabric has high TPS and supports smart contract deployment. Hyperledger Fabric is the most appropriate blockchain architecture for our proposed framework.
5.4. Comparison
In Table 6, we compare our previous solution with the one proposed in this paper. The focus of our proposed solution is to create traceable anti-counterfeit management of branded clothing. The non-repudiation, privacy, and integrity of the information are guaranteed in all aspects. For security during the process of information transmission, we also make a guarantee of information security by referring to cryptography. We further improved the anti-counterfeit traceability technology by learning from previous solutions.

Table 6.
Comparison of the tobacco products logistics system.
We made some comparisons with previous studies, absorbed the advantages, and made improvements. We put forward a complete system framework and continued the characteristics of blockchain technology. Compared with previous studies, we added security analysis to the framework to discuss whether data are secure or not. It is not hard to see how well we have implemented data privacy and traceability, and used digital signature technology to secure communications in the supply chain. Combined with internet of things radio frequency technology, customers can easily query the production information of brand clothing for anti-counterfeiting traceability.
6. Conclusions
We proposed a Hyperledger Fabric-based anti-counterfeit management system for traceable designer apparel. We contributed to the anti-counterfeiting of brand-name clothing. In this paper, we proposed a system framework that combined blockchain and supply chain, and analyzed and explained each process in the supply chain in detail. The production and sales processes are recorded in the blockchain network so that customers could easily trace the anti-counterfeiting of the purchased branded clothing through the blockchain network. The third party arbitration mechanism can also be used to check the illegal part of the supply chain easily. It provides adequate protection for the whole production parties and customers of brand clothing.
We used the Elliptic Curve Encryption Algorithm (ECDSA) to ensure the security of the entire system. We encrypted the communication in every process in the supply chain by ECDSA to ensure the system’s data integrity, non-repudiation, and privacy. By deploying and designing the chain code, we also further secured the data uploading operation and updating in the system. In particular, we used BAN logic to analyze the authentication of the identity.
By comparing with the contributions of previous solutions, this system focuses more on the security protection of data. We elaborated the system framework and analyzed the system security in all aspects through cryptography. The same analysis for communication also indicates that the system has better performance in the communication process.
In summary, the contributions made in this paper are as follows:
- We propose a Hyperledger Fabric-based anti-counterfeit management system for traceable branded clothing, which provides a comprehensive plan for the design, production, distribution, and sale of branded clothing. It ensures the security of the data in the supply chain.
- With the chain code algorithm to maintain and constrain the ledger, designer apparel products are difficult to forge by malicious attackers.
- The identity verification stage is designed in the supply chain to stop counterfeit substitution by illegal companies for the production process.
- A unique identification code is added for customers to check and analyze the authenticity of clothing, and for facilitates to query and update the data in the blockchain.
- We use BAN logic to prove the security of inter-company authentication.
Author Contributions
Conceptualization, C.-L.C. and X.S.; methodology, C.-L.C., X.S. and Y.-Y.D.; validation, W.W., Y.-Y.D., C.-M.W. and J.C.; investigation, C.-L.C., X.S. and Y.-Y.D.; data analysis, X.S., W.W., Y.-Y.D., C.-M.W. and J.C.; writing—original draft preparation, C.-L.C. and X.S.; writing—review and editing, W.-J.T., W.W., Y.-Y.D., C.-M.W. and J.C.; supervision, C.-L.C. and W.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Ministry of Science and Technology, Taiwan, R.O.C., under contract MOST 110-2218-E-305-001–MBK and contract MOST 110-2410-H-324-004-MY2, the Education and Teaching Reform Project of the Xiamen University of Technology (no. JG2021007), and the National Natural Science Foundation of China (no. 51808474).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data used to support the findings of this study are available from the corresponding author upon request.
Conflicts of Interest
The authors declare no conflict of interest.
Notations
| The Identity of | |
| is the ith identity of brand clothes for each brand clothing | |
| is a set of | |
| The elliptic curve defined on finite group | |
| A generating point based on the elliptic curve | |
| The ith random value on the elliptic curve | |
| The ECDSA’s private key of the party | |
| The ECDSA’s public key of the party | |
| Elliptic curve signature value of | |
| An ECDSA signature value of | |
| Encrypt/decrypt the message with a public key or private key of the party | |
| The hash value of a message is calculated by a one-way hash function | |
| The ith hash value of | |
| The ith timestamp | |
| The threshold for checking the validity of a timestamp | |
| The message (clothing information and create datetime) from the brand company | |
| The message (material supplier datetime and material supplier name) from the material supplier | |
| The message (manufacturer datetime and manufacturer name) from the manufacturer | |
| The message (retailer datetime, retailer sell datetime, retailer name, and clothing price) from the retailer | |
| Verify if is equal to or not |
References
- Modgil, S.; Sonwaney, V. Planning the application of blockchain technology in identification of counterfeit products: Sectorial prioritization. IFAC-Pap. Line 2019, 52, 1–5. [Google Scholar] [CrossRef]
- Counterfeit Luxury Goods|World Trademark Review. Available online: https://www.worldtrademarkreview.com/anti-counterfeiting/counterfeit-luxury-goods (accessed on 20 September 2021).
- What Impact Do Counterfeits Have on the Fashion Industry? Available online: https://www.redpoints.com/blog/fashion-counterfeit-impact/ (accessed on 20 September 2021).
- Li, C.T.; Shih, D.H.; Wang, C.C.; Chen, C.L.; Lee, C.C. A blockchain based data aggregation and group authentication scheme for electronic medical system. IEEE Access 2020, 8, 173904–173917. [Google Scholar] [CrossRef]
- Ding, Q.; Gao, S.; Zhu, J. Permissioned blockchain-based double-layer framework for product traceability system. IEEE Access 2019, 8, 6209–6225. [Google Scholar] [CrossRef]
- Rui-lin, Z. Research on anti-counterfeiting technology for clothing. Silk 2011, 11, 26–28. [Google Scholar]
- Alzahrani, N.; Bulusu, N. Block-supply chain: A new anti-counterfeiting supply chain using NFC and blockchain. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems, Munich, Germany, 15 June 2018; pp. 30–35. [Google Scholar] [CrossRef]
- Zhu, P.; Hu, J.; Zhang, Y. A blockchain based solution for medication anti-counterfeiting and traceability. IEEE Access 2020, 8, 184256–184272. [Google Scholar] [CrossRef]
- Bullón, P.J.; Queiruga-Dios, A.; Gayoso Martínez, V. Traceability of ready-to-wear clothing through blockchain technology. Sustainability 2020, 12, 7491. [Google Scholar] [CrossRef]
- Yiu, N.C.K. Toward Blockchain-Enabled Supply Chain Anti-Counterfeiting and Traceability. Future Internet 2021, 13, 86. [Google Scholar] [CrossRef]
- Agrawal, T.K.; Kumar, V.; Pal, R. Blockchain-based framework for supply chain traceability: A case example of textile and clothing industry. Comput. Ind. Eng. 2021, 154, 107130. [Google Scholar] [CrossRef]
- Crosby, M.; Pattanayak, P.; Verma, S. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Chen, C.L.; Deng, Y.Y.; Li, C.T.; Zhu, S.; Chiu, Y.J.; Chen, P.Z. An IoT-based traceable drug anti-counterfeiting management system. IEEE Access 2020, 8, 224532–224548. [Google Scholar] [CrossRef]
- Schmidt, C.G.; Wagner, S.M. Blockchain and supply chain relations: A transaction cost theory perspective. J. Purch. Supply Manag. 2019, 25, 100552. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference 2018, Porto, Portugal, 23–26 April 2018. [Google Scholar]
- Hyperledger Blockchain Performance Metrics White Paper—Hyperledger. Available online: https://www.hyperledger.org/learn/publications/blockchain-performance-metrics# (accessed on 20 September 2021).
- Valenta, M.; Sandner, P. Comparison of Ethereum, Hyperledger Fabric and Corda. Ebook Frankf. Sch. Blockchain Cent. 2017, 1–8. Available online: http://www.smallake.kr/wp-content/uploads/2017/07/2017_Comparison-of-Ethereum-Hyperledger-Corda.pdf (accessed on 23 October 2021).
- Nasir, Q.; Qasse, I.A.; Abu Talib, M. Performance analysis of hyperledger fabric platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef] [Green Version]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Vivar, A.L.; Orozco, A.L.S.; Villalba, L.J.G. A security framework for Ethereum smart contracts. Comput. Commun. 2021, 172, 119–129. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y.; Weng, W.; Sun, H.; Zhou, M. A Blockchain-Based Secure Inter-Hospital EMR Sharing System. Appl. Sci. 2020, 10, 4958. [Google Scholar] [CrossRef]
- Yogesh, P.R. Formal verification of secure evidence collection protocol using BAN logic and AVISPA. Procedia Comput. Sci. 2020, 167, 1334–1344. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).