Abstract
Digital signature with proxy delegation, which is a secure ownership enforcement tool, allows an original signer to delegate signature rights to a third party called proxy, so that the proxy can sign messages on behalf of the original signer. Many real-world applications make use of this secure mechanism, e.g., digital property transfer. A traditional digital signature mechanism is required to bind a message and its signature together for verification. This may yield extra cost in bandwidth while the sizes of message and signature are relatively huge. Message recovery signature, enabling to reduce the cost of bandwidth, embeds a message into the corresponding signature; therefore, only the signature will be transmitted to the verifier and the message can further be recovered from the signature. In this paper, we, for the first time, propose a novel digital signature scheme in the identity-based context with proxy delegation and message recovery features and, more importantly, our scheme is quantum resistant, in a particular lattice-based signature. Our scheme achieves delegation information and signature existential unforgeability against adaptive chosen warrant and identity. Compared with the seminal lattice-based message recovery signature, our scheme is independent from public key infrastructure, realizes delegation transfer of signature rights, and compresses signature length ulteriorly. To the best of our knowledge, this paper is the first of its type.
1. Introduction
Digital signature aims at message authenticity, which can be verified by everyone with a message/signature pair. Considering the practical application, a digital signature also needs to have special properties for special functionality requirements, such as signature with delegation functionality—proxy signature. Proxy signature, which was first proposed by Mambo [1], allows an original signer to delegate his signing right to a proxy signer, so that the proxy signer can sign a message on behalf of the original signer. Proxy signature is suitable for the case where the original signer is temporarily absent so that the proxy is delegated to make a signature on behalf of the original signer. It has many real-world applications (e.g., digital property transfer) and practical variants in the literature (e.g., [2]). We note that there have been some research works by far related to proxy delegation, such as [3,4,5,6,7,8,9], in which they focus on decryption delegation. This paper deals with signature delegation.
Message recovery signature is a kind of digital signature with message recovery property, and was first proposed by Nyberg and Rueppel in [10]. Compared with the traditional digital signature, a message can be embedded into the signature. As a result, only the signature itself is required in the verification stage instead of the message and signature pair in the traditional version. It reduces the amount of information to be transmitted, and thus can save the transmission bandwidth dramatically.
Combining a message recovery signature and a proxy signature, a proxy signature with message recovery emerges, which owns a hidden message and the functionality of signing right delegation transfer. Furthermore, in order to simplify key management, Singh [11] combined identity-based signature with proxy signature with message recovery, and introduced the concept of identity-based proxy signature scheme with message recovery. Such scheme can work without the existence of public key infrastructure, and the legitimacy of the user’s public key is not required to be verified.
1.1. Related Work
Many researchers have paid attention to proxy signature with message recovery, and a lot of contributions [12,13,14,15,16] have been proposed in the literature. The schemes introduced in [12,13,15,16] are based on a discrete logarithm problem, the one proposed in [14] is based on a decisional Diffie–Hellman problem and a computational Diffie-Hellman problem. However, all these problems are solvable with a quantum computer [17], so that security of schemes [12,13,14,15,16] will be unreliable in the quantum era, and it is significant to construct a quantum-resistible proxy signature with message recovery.
Lattice-based cryptography is an excellent branch of post-quantum cryptography. For almost two decades, lattice-based cryptography has been on the fast track of development. Some unsolved questions in traditional cryptography, such as construction of a fully homomorphic encryption scheme [18], have found their realization in lattice-based cryptography. Due to a reliable security guarantee and powerful functionality, lattice-based cryptography becomes the preferred tool for our topic—an identity-based proxy signature scheme with message recovery.
Lattice signature is the building foundation of our topic. In 2008, Gentry et al. [19] designed the first provably secure lattice signature scheme. In 2012, Micciancio et al. [20] proposed a new trapdoor generation algorithm and gave a lattice signature scheme with better efficiency and security. In the same year, Lyubashevsky [21] gave a lattice signature scheme with better efficiency following a special lattice with simpler computations. In 2014, Bai et al. [22] proposed an improved compression technique for lattice signature in [21]. Lattice signatures in [19,20] and [21,22] are two main frames for lattice signature schemes, and the latter is with better performance.
Lattice signature schemes [19,20,21,22] are all basic signature schemes. We will consider message recovery and delegation of signing right in identity-based environment. In 2013, Tian et al. [23] proposed lattice-based message recovery signature scheme following [21]. His scheme is based on public key infrastructure without expressing delegation of signing rights. In 2016, Wang Li [24] proposed an identity-based proxy signature scheme in lattice, which follows the idea of [19] and doesn’t hide messages. In 2017, Faguo Wu et al. [25] gave a lattice proxy signature with message recovery based on public key infrastructure.
1.2. Our Contribution
In this paper, we build an efficient and secure identity-based proxy signature scheme with message recovery in lattice-based cryptography. Our scheme is based on the lattice signature without trapdoors [21]. Inspired by the signature compression technique in [22], we introduce the random error matrix with enough small entries, let . According to the learning with errors problem, we keep instead of , as the secret key of user . Correspondingly, the signature is rather than in our scheme. These operations add more randomness to user secret key extraction, and reduce signature length with .
For proxy signature, we change the traditional idea that the original signer generates the delegated secret key and passes it to the proxy signer through the secure channel. Following the idea of two-party signature in [26], our delegated secret key is obtained with the help of proxy signer’s secret key and original signer’s public delegation information. Therefore, delegated secret key extraction is controlled by the proxy signer and original signer, and no secure channel is required between them. Moreover, anyone can verify the validity of delegation information because it is public.
Speaking of message recovery, we adopt the technique in [23]. Compared with the scheme in [23], our scheme takes the following three advantages. Firstly, our scheme is identity-based and does not rely on public key infrastructure maintenance. Secondly, our scheme realizes delegation transfer of signing rights. Thirdly, our scheme condenses signature length. The comparing details of two schemes are described in Section 5.
In addition, we divide the security definition in [11] into two factors: delegation information existential unforgeability against adaptive chosen warrant and identity, signature existential unforgeability against adaptive chosen message and identity. The former guarantees delegation information is credible, and the latter guarantees that proxy signature is credible. Our security definition is more comprehensive.
The rest of the paper is organized as follows. We present an overview of background knowledge in Section 2. Then, we propose our model and security definitions for an identity-based proxy signature scheme with message recovery in Section 3. In Section 4, we provide the identity-based proxy signature scheme with message recovery in lattice-based cryptography. Correctness, security, and performance analysis are discussed in Section 5. Finally, we conclude this paper in Section 6.
2. Preliminaries
2.1. Notations
is the set of integers, and is the set of natural numbers. Let q be a polynomial-size prime number, is the set of integers in . For and , is the unique integer satisfying , . For , is the i-th entry of e, is the Euclidean norm of e, and . For matrix , is the entry in i-th row and j-th column, is the largest Euclidean norm of its column vectors, and is its Gram–Schmidt orthogonalization. If and are two bit strings, is their concatenation, is the result of xor computation. In addition, is the prefix of with length , is the suffix of with length .
2.2. Lattice Theory
In this subsection, basic concepts and major algorithms related to our scheme are illustrated. For readers who are interested in details, please see literature [19,27,28].
Definition 1.
Algorithm TrapGen , with , outputs a pair which satisfies the following conditions: 1. follows uniform distribution with overwhelming probability; 2. , and 3.
Definition 2.
is a discrete Gaussian distribution on , with center 0 and standard deviation σ. is a matrix with m rows and n columns, and every entry in the matrix follows the distribution .
Definition 3.
For , a short basis T of , , and Gaussian parameter , algorithm SamplePre outputs some such that and .
Definition 4.
Given a uniform random matrix , the small integer solution (SIS) problem is to find a short vector , such that and for some appropriate parameter β.
Definition 5.
Given a pair , where follows uniform distribution with overwhelming probability, , for appropriate parameter σ, the learning with errors (LWE) problem is to find s.
With appropriate parameters, LWE and SIS problems are notably hard average problems in lattice theory, and they are the security basis of most cryptographic systems in lattice.
3. Identity-Based Proxy Signature with Message Recovery
Our model and security definitions for an identity-based proxy signature scheme with message recovery (IDPSWM) come from the literature [11], and two adjustments are made.
- In our model, the delegation information is public, everyone may verify its legality; whereas, in [11], the delegation information is sent to the proxy signer secretly, and only the proxy signer can verify its legality. Therefore, a secure channel is unnecessary to transmit delegation information in our model, and every user can verify delegation information legality.
- To make it easier to understand, we divide scheme security into two factors: delegation information existential unforgeability against adaptive chosen warrant and identity (EUF-ID-CWA), signature existential unforgeability against adaptive chosen message and identity (EUF-ID-CMA). EUF-ID-CWA security assures that delegation information is believable. EUF-ID-CMA security assures that signature is believable.
3.1. Our Model
There are three types of users: the original signer, the proxy signer, and the verifier, as well as a private key generator (PKG) in the system; their roles are as follows:
- : PKG inputs the security parameter n, outputs system public parameters and the system secret master key .
- : Given an identity , PKG makes use of the system secret master key and provides the secret key for the identity .
- : The original signer inputs his secret key , and the warrant w associated with proxy signer , computes the delegation , and publishes delegation information to all system users.
- : For arbitrary system users, he verifies the legality of delegation information . If it is legal, the output is 1, the delegation is accepted; otherwise, the output is 0, and the delegation is rejected.
- : The proxy signer verifies whether the delegation information is valid. If it is invalid, he rejects this delegation. Otherwise, he inputs his secret key and the delegation information , outputs the delegated secret key .
- : The proxy signer inputs his delegated secret key and the message , outputs the proxy signature .
- : For arbitrary system users, he first recovers the message associated with signature , and then verifies the legality of the message/ signature pair with regard to . If it is legal, the output is 1, the message is accepted; otherwise, the output is 0, and the message is rejected.
As to scheme correctness, seven algorithms should satisfy the following rules: For every security parameter n, , , , , , the probability of is overwhelming.
3.2. Security Definitions
Scheme security includes two factors: delegation information existential unforgeability against adaptive chosen warrant and identity (EUF-ID-CWA), signature existential unforgeability against adaptive chosen message and identity (EUF-ID-CMA).
3.2.1. EUF-ID-CWA
EUF-ID-CWA security is described by the next game between a challenger and a forger .
- Initial Phase: The challenger runs algorithm to get system public parameters and the system secret master key . returns to the forger and keeps himself.
- Query Phase: The forger makes the following queries adaptively with a polynomial bounded number, and the challenger has the obligation to make reasonable answers.1. : selects a user identity , sends it to the challenger . invokes algorithm to get the associated secret key . Then, returns to .2. : selects the original signer , the proxy signer , and the warrant w, and sends all of them to the challenger . executes query to get the associated secret key , and then invokes algorithm to get and returns it to .
- Forge Phase: The forger gives his forgery . If the following conditions are satisfied: , doesn’t occur in the query, doesn’t occur in the query, and his attack is successful.
Let be the success probability of in this game.
Definition 6.
An identity-based proxy signature scheme with message recovery (IDPSWM) is delegation information existentially unforgeable against adaptive chosen warrant and identity (EUF-ID-CWA), if for every polynomial time forger , is negligible.
3.2.2. EUF-ID-CMA
EUF-ID-CMA security is demonstrated by the following game between a challenger and a forger .
- Initial Phase: The challenger runs the algorithm to get system public parameters and the system secret master key . returns to the forger and keeps secret.
- Query Phase: The forger executes the following queries adaptively with a polynomial bounded number, and the challenger has to return reasonable answers.1. : selects a user identity and sends it to the challenger . invokes algorithm to get secret key . Then, returns to .2.: selects the original signer , the proxy signer , and the warrant w, submits them to the challenger . executes query to get the associated secret , and then invokes algorithm to get and returns it to .3. : sends the delegation information to the challenger . verifies its validity firstly. If it isn’t valid, he refuses to respond. Otherwise, executes a query to get secret key , invokes algorithm to get delegated secret key and returns it to .4. : submits and message to the challenger . verifies the legality of . If it is illegal, rejects answering the query. Otherwise, he executes the query to get the delegated secret key , invokes algorithm to get signature , and returns it to .
- Forge Phase: The forger gives his forgery .Recovering the message from , if the following conditions hold: , doesn’t occur in the query, doesn’t occur in the query, his attack is successful.
Let be the success probability of in the game.
Definition 7.
An identity-based proxy signature scheme with message recovery (IDPSWM) is signature existentially unforgeable against the adaptive chosen message and identity (EUF-ID-CMA), if, for every polynomial time forger , is negligible.
4. Our Scheme
In this section, we introduce our identity-based proxy signature scheme with message recovery from lattice assumption. Our scheme includes seven algorithms, which also can be seen from Figure 1.
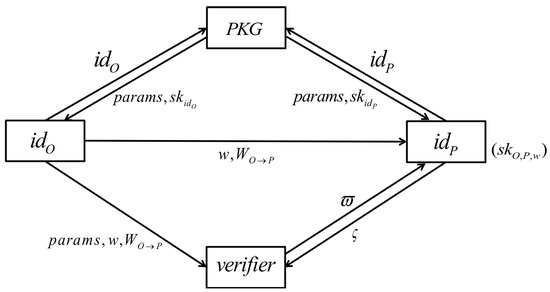
Figure 1.
Flow chart of our signature algorithm.
- : Inputting the security parameter n, PKG works as follows:1. Invoke algorithm to obtain a pair of matrices , .2. Let be a secure hash function.3. Let be secure hash functions, and the image Hamming weight is not larger than .4. Let be a secure hash function, and every column vector in the image has a small Hamming weight bounded by .5. Let be a secure hash function, where is also the length of message .6. Let , be encoding functions.Finally, PKG outputs public parameters = and the secret master key .
- : Given an identity , PKG works as follows:1. Sample , such that for all . If for some , Resample again. According to [22], the probability of for some is less than .2. Invoke algorithm , provide follows the distribution , such that .3. Return as secret key for the identity .
- : The original signer inputs his secret key , and the warrant associated with proxy signer does the following steps:1. Sample , is the uniform distribution on .2. Let , .3. Let . If , go to the first step to resample .4. Return with probability , and publish delegation information to all users.
- : For arbitrary users, he verifies the legality of delegation information as follows:1. Compute .2. If and , output 1 and accept this delegation. Otherwise, output 0 and reject it.
- : the proxy signer inputs his secret key and the delegation information , computes , outputs as the delegated secret key.
- : the proxy signer inputs his delegated secret key , the message , does the next steps.1. Sample , compute .2. Let , .3. Compute , .4. Let .5. If , go to the first step to resample y. Otherwise, return proxy signature with probability
- : For arbitrary user, he verifies the proxy signature with the next steps. Here, we think the legality of delegation information has already been verified.1. Compute .2. Compute , .3. If and , accept the signature and output 1; otherwise, output 0 and reject the signature.
5. Scheme Analysis
5.1. Parameter Setting
n is the system security parameter:
1. For the algorithm, , .
2. For the algorithm,
3. According to [22], satisfies .
4. According to [23], and are all about 100.
5. According to [22], , .
6. According to [21], M is a small constant of about 8.
5.2. Correctness of the Scheme
1. For algorithm, ,
Because in step 3 of algorithm, we have:
If , go to the first step to resample .
Therefore, , such that .
In addition, due to , and , follows uniform distribution on for , so that . So far, verification of delegation information is correct.
2. For algorithm,
Because in step 5 of algorithm, we have:
If , go to the first step to resample y.
Therefore, , such that
Due to , we have . Since , the message , and .
In addition, since , and , z follows uniform distribution on for , so that .
Up to now, proxy signature verification is successful. Combining two points, we draw a conclusion that our scheme is correct.
5.3. Security Analysis
Our scheme security consists of two parts: EUF-ID-CWA security aims at delegation information reliability, EUF-ID-CMA security aims at proxy signature reliability.
5.3.1. EUF-ID-CWA Security
Theorem 1.
Provided that the SIS problem is hard to solve, our identity-based proxy signature scheme with message recovery (IDPSWM) is delegation information existentially unforgeable against adaptive chosen warrant and identity (EUF-ID-CWA).
Proof.
We prove this theorem by contradiction. Assuming that a polynomial time forger has the ability to provide valid and fresh delegation information with some non-negligible probability , we can design an algorithm to solve an SIS instance with probability
where and are the times of queries and queries.
That is to say, with an SIS problem instance , interacts with forger to find small non-zero vector , and , such that . The details are as follows:
- Initial Phase: selects , , submits A, , and as system parameters to the forger .
- Query Phase: The forger makes the following queries, gives reasonable answers:1. query: selects a user identity , sends it to . samples , , let . He saves in the list and returns to .2. query: selects warrant associated with the original signer , the proxy signer , sends all of them to . randomly samples with Hamming weight less than or equal to , selects uniformly, let . If some entry in is larger than , resamples and again. Because , the probability that every entry in is smaller than is larger than . At last, saves in list and returns to .3. query: selects a user identity and sends it to the challenger . searches list to get , and returns . If it doesn’t exist, queries firstly.4. query: selects the original signer , the proxy signer , and the warrant , sends all of them to . looks list for and returns . If doesn’t exist, queries firstly.
- Forge Phase: The forger gives his forgery .Because queries at most times, queries at most times, so that the number of is at most . Suppose there are , , ⋯, . For , the probability of generates such that is , which is negligible, so that ∈ with overwhelming probability .
Because gives a successful forgery with probability , is a valid forgery and ∈ with probability . Supposing , we further conclude that it comes from a query rather than a query.
If comes from query, then
If ≠ or ≠, then a collision in is obtained.
Therefore, =, which leads to (because the warrant includes the identity information), and the entries of are in .
If , = , it isn’t a successful forgery.
If , let , , then , and , . The SIS instance is solved.
Now, we know comes from query, and invoke again. Due to General Forking Lemma [29], with a probability not less than
we obtain a different valid delegation information on , and .
Then, which means for . Replacing with , we have . Let , , then , . In addition, and have a variety of options, doesn’t know which pair is used to build and . Therefore, the probability of is at least . □
5.3.2. EUF-ID-CMA Security
Theorem 2.
Provided that the SIS problem is hard to solve, our identity-based proxy signature scheme with message recovery (IDPSWM) is signature existentially unforgeable against adaptive chosen message and identity (EUF-ID-CMA).
Proof.
We prove this theorem by contradiction. Assuming that a polynomial time forger has the ability to provide a valid and fresh proxy signature with some non-negligible probability , we can design an algorithm to solve an SIS problem instance with probability
where and are the times of queries and queries.
That is to say, with an SIS problem instance , interacts with forger to find a small non-zero vector , and , such that . The details are as follows:
- Initial Phase: selects , , submits A, , and as system parameters to the forger .
- Query Phase: The forger makes the following queries, gives reasonable answers:1. query: selects a user identity , and sends it to . samples , , let . He saves in the list and returns to .2. query: selects warrant associated with the original signer , the proxy signer , sends all of them to . randomly samples with Hamming weight less than or equal to , selects uniformly, let . If some entry in is larger than , resamples and again. Because , the probability that every entry in is smaller than is larger than . At last, saves in list and returns to .3. query: selects randomly, sends it to . selects uniformly and randomly. Then, saves in list and returns to .4. query: sends and submits it to . chooses with Hamming weight less than or equal to . Then, saves in list and returns to .5. query: selects a user identity , sends it to the challenger . searches list to get , returns . If it doesn’t exist, queries firstly.6. query: selects the original signer , the proxy signer , and the warrant sends all of them to . looks list for and returns . If doesn’t exist, queries firstly.7. query: sends the delegation information to the challenger . verifies its validity firstly. If it isn’t valid, he refuses to respond. Otherwise, executes query to get secret key , computes and , returns to .8. query: submits and message to the challenger . verifies the legality of . If it is illegal, rejects answering the query. Otherwise, he executes query to get the delegated secret key , invokes algorithm to get signature , and returns it to .
- Forge Phase: The forger gives his forgery signature for message .invokes again. Due to General Forking Lemma [29], with probability , we obtain a new signature for message , such thatis equivalent toand .Then, = for . Replacing with , we have . Let , , then , . In addition, and have a variety of options, doesn’t know which pair is used to build and . Therefore, the probability of is at least .
□
5.4. Performance Analysis
Regarding the performance analysis, we will focus on the following three aspects: signature compression, signing right delegation and message recovery.
Firstly, we take the signature compression technique from [22]. For hash value for user , we first sample such that for all . Then, we invoke algorithm such that . We set rather than , as the private key of user . The abandoned leads to the signature length reducing from to , which is about bits. Combining the operation , the discarded does not affect signature verification algorithm.
For signing right delegation, we make the original signer’s signature for the warrant w public for everyone. Any verifier can take to verify the original signer’s signing right transfer to the proxy signer. Besides doing the same operations with the verifier, the proxy signer must embed into the generation of proxy signature private key—the delegated secret key. Therefore, the delegated secret key is decided by the original signer and the proxy signer. The original signer can’t deny his authorization to the proxy signer, can’t generate the delegated secret key alone, so that proxy signer’s interests are protected. On the other hand, the proxy signer can’t generate the delegated secret key without the permission of the original signer, thus the interests of the original signer are protected. In addition, no secure channel is necessary between the original signer and proxy signer—because no secret information is transmitted between them.
Thirdly, we use the idea of message recovery signature in [23], hide the message in the signature, and the message can be recovered without any secret information, hence only the signature should be transmitted and everyone can verify its legality.
In Table 1, we give the performance comparison between [23] and our scheme. Two schemes are both with message recovery and quantum resistance, and the number of signature verification operations is the same. The differences between two schemes are shown in the following aspects: firstly, the scheme in [23] needs the support of public key infrastructure while our scheme does not need it. Public key infrastructure provides security assurance of the relationship between public key and private key, which is achieved by authoritative authority signing certificates for users. Therefore, public key infrastructure needs to complete certificate allocation, verification, storage and revocation operations, which requires a large amount of bandwidth resources and computing resources. In our scheme, the public key is the user’s identity, and the relationship between the public key and the private key is natural. Therefore, we no longer need the support of the complex public key infrastructure, and the system becomes concise. Secondly, the scheme in [23] does not have the function of proxy authorization, and our scheme has this function. Therefore, our scheme is more powerful. In addition, the scheme in [23] does not introduce signature compression technology, and our scheme introduces signature compression technology to make the signature length shorter. It is clear that our scheme has better functionality compared to the scheme in [23]. However, because we take the signature compression technique from [22] to condense signature length, it is necessary to ensure . To this end, we repeat operations of signing message with probability not larger than —this is our scheme’s extra computation cost. For every operation of signing message and verification, our scheme’s computation cost is comparable with that of the scheme in [23].

Table 1.
Performance comparison among Refs. [23] and [25] and our scheme.
The lattice-based proxy signature scheme with message recovery in [25] follows the same frame with the scheme in [23] and ours; we also include it in Table 1. Compared with our scheme, the scheme in [25] bases on public key infrastructure, delegation of signature right depends on secure channel and can’t be verified publicly. In addition, the scheme in [25] doesn’t take signature compression technique, its signature is longer and the number of signature operations is small. According to [30], reduction in message length will reduce energy consumption to a greater extent than reduction in computation. Overall, our scheme is more efficient.
6. Conclusions
In this paper, we first proposed the identity-based proxy signature scheme with message recovery based on the lattice assumptions. In particular, we used the signature compression technique for lattice signature without trapdoors to decrease signature length. We abandoned the secure channel between original signer and proxy signer and made the model possess better environmental adaptability. We also divided the security definition into two factors, making the security analysis much easier to be understood. We introduced the idea of message recovery signature, embedding messages into signatures and shortening the amount of information to be transmitted. For security analysis, our scheme is based on the learning with errors and the small integer solution problems. Finally, we demonstrated our performance via comparison with some related works.
Author Contributions
The first author X.L., proposed the main idea as well as the concrete schemes of the paper. The second and third authors Q.W. and W.Y., gave all the figures and tables, as well as Section 1 and Section 2. The fourth author K.L. contributed to the security analysis part. The fifth and sixth authors Z.J. and E.P., were responsible for the English writing of the whole paper. The seventh author J.C., the corresponding author, was responsible for efficiency analysis as well as the management of the research project.
Funding
This work was funded by the National Natural Science Foundation of China (No. 61502044, 61402015, 61702212); the Fundamental Research Funds for the Central Universities (No. 2015RC23); the Natural Science Foundation of Hebei Province (No. F2018408040); the Natural Science Foundation of Shandong Province (No. ZR201702180067); and the Hebei Education Funds for Youth Project (No. QN2018047).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Mambo, M.; Usuda, K.; Okamoto, E. Proxy signatures for delegating signing operation. In Proceedings of the 3rd ACM Conference on Computer and Communications Security, New Delhi, India, 14–15 March 1996; pp. 48–57. [Google Scholar]
- Wei, J.; Yang, G.; Mu, Y.; Liang, K. Anonymous Proxy Signature with Hierarchical Traceability. Comput. J. 2016, 59, 559–569. [Google Scholar] [CrossRef]
- He, K.; Liu, X.; Yuan, H.; Wei, W.; Liang, K. Hierarchical Conditional Proxy Re-Encryption: A New Insight of Fine-Grained Secure Data Sharing. In Information Security Practice and Experience, Proceedings of the 13th International Conference, ISPEC 2017, Melbourne, Australia, 13–15 December 2017; Liu, J.K., Samarati, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10701, pp. 118–135. [Google Scholar] [CrossRef]
- Shao, J.; Lu, R.; Lin, X.; Liang, K. Secure bidirectional proxy re-encryption for cryptographic cloud storage. Pervasive Mob. Comput. 2016, 28, 113–121. [Google Scholar] [CrossRef]
- Liang, K.; Susilo, W.; Liu, J.K.; Wong, D.S. Efficient and Fully CCA Secure Conditional Proxy Re-Encryption from Hierarchical Identity-Based Encryption. Comput. J. 2015, 58, 2778–2792. [Google Scholar] [CrossRef]
- Liang, K.; Chu, C.; Tan, X.; Wong, D.S.; Tang, C.; Zhou, J. Chosen-ciphertext secure multi-hop identity-based conditional proxy re-encryption with constant-size ciphertexts. Theor. Comput. Sci. 2014, 539, 87–105. [Google Scholar] [CrossRef]
- Liang, K.; Au, M.H.; Liu, J.K.; Susilo, W.; Wong, D.S.; Yang, G.; Phuong, T.V.X.; Xie, Q. A DFA-Based Functional Proxy Re-Encryption Scheme for Secure Public Cloud Data Sharing. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1667–1680. [Google Scholar] [CrossRef]
- Liang, K.; Liu, J.K.; Wong, D.S.; Susilo, W. An Efficient Cloud-Based Revocable Identity-Based Proxy Re-encryption Scheme for Public Clouds Data Sharing. In Computer Security, Proceedings of the ESORICS 2014, 19th European Symposium on Research in Computer Security, Wroclaw, Poland, 7–11 September 2014; Kutylowski, M., Vaidya, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8712, pp. 257–272. [Google Scholar] [CrossRef]
- Liang, K.; Fang, L.; Susilo, W.; Wong, D.S. A Ciphertext-Policy Attribute-Based Proxy Re-encryption with Chosen-Ciphertext Security. In Proceedings of the 2013 5th International Conference on Intelligent Networking and Collaborative Systems, Xi’an, China, 9–11 September 2013; pp. 552–559. [Google Scholar] [CrossRef]
- Nyberg, K.; Rueppel, R.A. A new signature scheme based on the DSA giving message recovery. In Proceedings of the 1st ACM conference on Computer anD Communications Security, Fairfax, VA, USA, 3–5 November 1993; pp. 58–61. [Google Scholar]
- Singh, H.; Verma, G.K. ID-based proxy signature scheme with message recovery. J. Syst. Softw. 2012, 85, 209–214. [Google Scholar] [CrossRef]
- Tiwari, N.; Padhye, S. New proxy signature scheme with message recovery using verifiable self-certified public keys. In Proceedings of the 2011 2nd International Conference on Computer and Communication Technology, Allahabad, India, 15–17 September 2011; pp. 539–544. [Google Scholar]
- Xie, Q. Provably Secure Self-certified Multi-proxy Signature with Message Recovery. J. Netw. 2012, 7, 1616. [Google Scholar] [CrossRef]
- Yoon, E.J.; Choi, Y.; Kim, C. New ID-based proxy signature scheme with message recovery. In Proceedings of the International Conference on Grid and Pervasive Computing, Seoul, Korea, 9–11 May 2013; pp. 945–951. [Google Scholar]
- Mahmoodi, A.; Mohajery, J.; Salmasizadeh, M. A certificate-based proxy signature with message recovery without bilinear pairing. Security Commun. Netw. 2016, 9, 4983–4991. [Google Scholar] [CrossRef]
- Padhye, S.; Tiwari, N. ECDLP-based certificateless proxy signature scheme with message recovery. Trans. Emerg. Telecommun. Technol. 2015, 26, 346–354. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Gentry, C. Fully homomorphic encryption using ideal lattices. In Proceedings of the 41st Annual ACM Symposium on Symposium on Theory of Computing-STOC’09, Washington, DC, USA, 31 May–2 June 2009; Volume 9. [Google Scholar]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for hard lattices and new cryptographic constructions. In Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008; pp. 197–206. [Google Scholar]
- Micciancio, D.; Peikert, C. Trapdoors for Lattices: Simpler, Tighter, Faster, Smaller. In Advances in Cryptology, Proceedings of the EUROCRYPT 2012, Cambridge, UK, 15–19 April 2012; Pointcheval, D., Johansson, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 700–718. [Google Scholar]
- Lyubashevsky, V. Lattice signatures without trapdoors. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; pp. 738–755. [Google Scholar]
- Bai, S.; Galbraith, S.D. An improved compression technique for signatures based on learning with errors. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 25–28 February 2014; pp. 28–47. [Google Scholar]
- Tian, M.; Huang, L. Lattice-based message recovery signature schemes. Int. J. Electron. Secur. Digit. Forensics 2013, 5, 257–269. [Google Scholar] [CrossRef]
- Li, W. An Identity-Based Proxy Signature Scheme from Lattices in the Standard Model. In Proceedings of the International Conference on Intelligent Networking and Collaborative Systems, Ostrawva, Czech Republic, 7–9 September 2016. [Google Scholar]
- Wu, F.; Yao, W.; Zhang, X.; Zheng, Z. An Efficient Lattice-Based Proxy Signature with Message Recovery. In Proceedings of the International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Guangzhou, China, 12–15 December 2017; Volume 10656, pp. 321–331. [Google Scholar]
- Lindell, Y. Fast Secure Two-Party ECDSA Signing. In Advances in Cryptology, Proceedingds of the CRYPTO 2017, Barbara, CA, USA, 20–24 August 2017; Katz, J., Shacham, H., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 613–644. [Google Scholar]
- Agrawal, S.; Boneh, D.; Boyen, X. Efficient lattice (H) IBE in the standard model. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; pp. 553–572. [Google Scholar]
- Applebaum, B.; Cash, D.; Peikert, C.; Sahai, A. Fast cryptographic primitives and circular-secure encryption based on hard learning problems. In Proceedings of the CRYPTO 2009, Santa Barbara, CA, USA, 16–20 August 2009; pp. 595–618. [Google Scholar]
- Bellare, M.; Neven, G. Multi-signatures in the plain public-Key model and a general forking lemma. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 390–399. [Google Scholar]
- Hill, J.; Szewczyk, R.; Woo, A.; Hollar, S.; Culler, D.; Pister, K. System architecture directions for networked sensors. SIGPLAN Not. 2000, 35, 93–104. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).