Explainable AI-Based DDOS Attack Identification Method for IoT Networks
Abstract
:1. Introduction
- We propose and implemented a novel method that consists of two key components: anomaly detection using autoencoder and XAI-based explanation of the most influential features for each anomalous instance.
- We suggest a method for selecting features for DDoS attack flow detection. By deciding which features are independent and most important for a DDoS attack, the methodology can reduce the amount of features.
- We present a comprehensive evaluation of the proposed method on the USB-IDS dataset and implemented a lightweight model, as it needs to deploy on IoT devices.
2. Background and Related Work
2.1. Explainable Artificial Intelligence
2.2. SHapley Additive Explanation
- Local accuracy;
- Missingnes;
- Consistency.
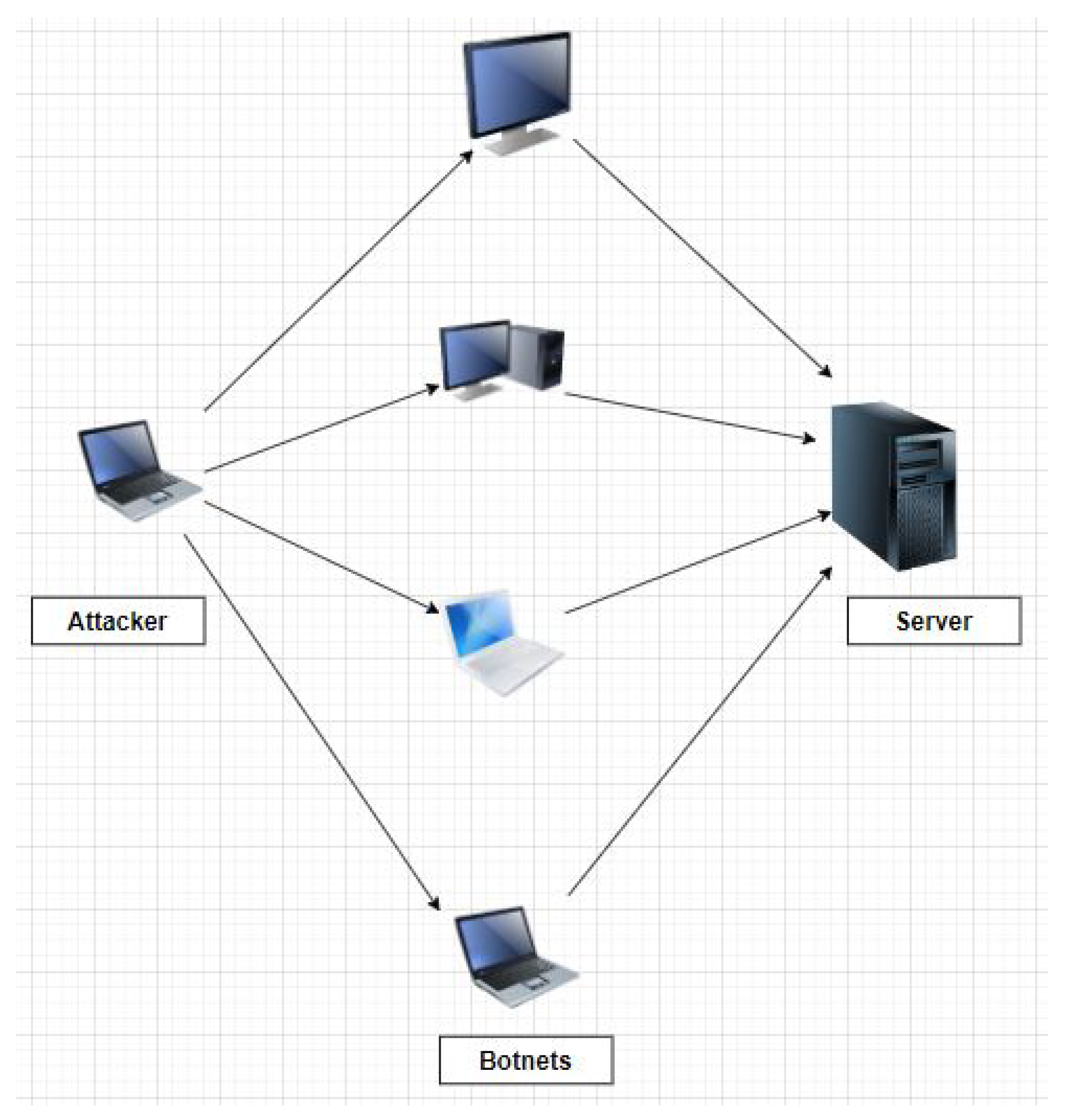
2.3. DDoS Attack
2.4. DDoS Detection
3. Methodology
3.1. Feature Extraction from Network Traffic
3.2. Anomaly Detection
3.3. Explain Anomalies
| Algorithm 1 Calculate SHAP values for top-R features. |
| Require: X—Anomaly instance that need to explain, X1..j—instances used by kernel SHAP, |
| Reconstruction errorList—a ranked list of errors for each feature, f—autoencoder model |
| Ensure: shaptopRfeatures—SHAP values for each feature within topRfeatures |
| topRfeatures ←top value from Error List |
| for each i ϵ topRfeatures do |
| explainer ← shap.KernelExplainer(f , X1..j) |
| shaptopRfeatures[i] ← explainer.shapvalues(X, i) |
| end for |
| return shaptopRfeatures |
3.4. Most Informative Features for DDoS Attacks
3.4.1. State Exhaustion Attack Based Features
3.4.2. Application Layer-Based Attack Features
3.4.3. Volumetric-Based Attack Features
3.5. Mapping the Most Influential Features with DDoS Features
| Algorithm 2 Finding the most influential DDoS features. |
| Require: shaptopRfeatures, DDoS features |
| Ensure: Most Influential DDoS features |
| for ai in shaptopRfeatures do |
| for dai in DDoS features do |
| if ai == dai |
| Most Influential DDoS features ← ai |
| end for |
| end for |
| return MostInfluentialDDoSfeatures |
4. Experimental Evaluation
4.1. Dataset
4.2. Experimental Environment
5. Results and Discussion
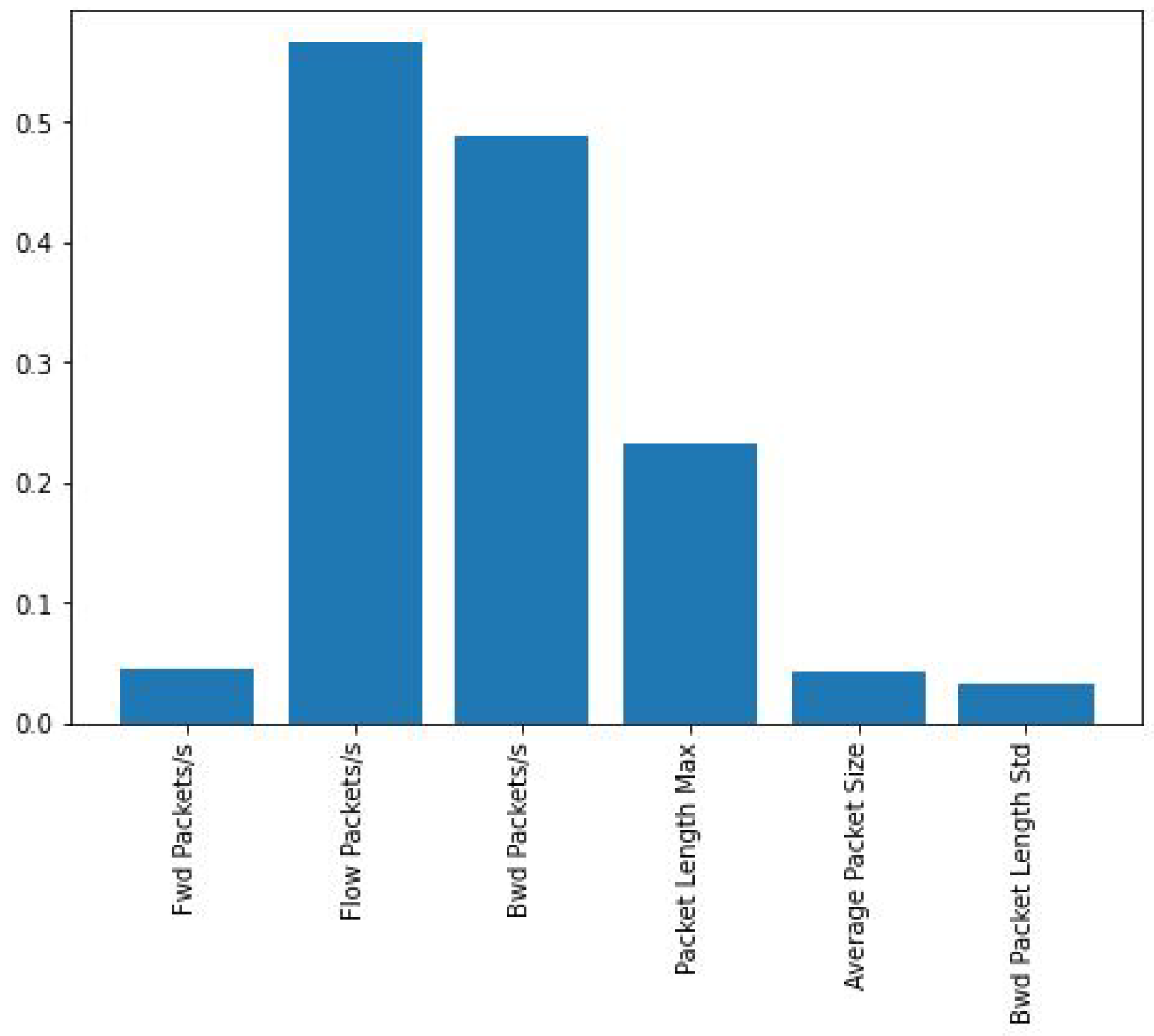
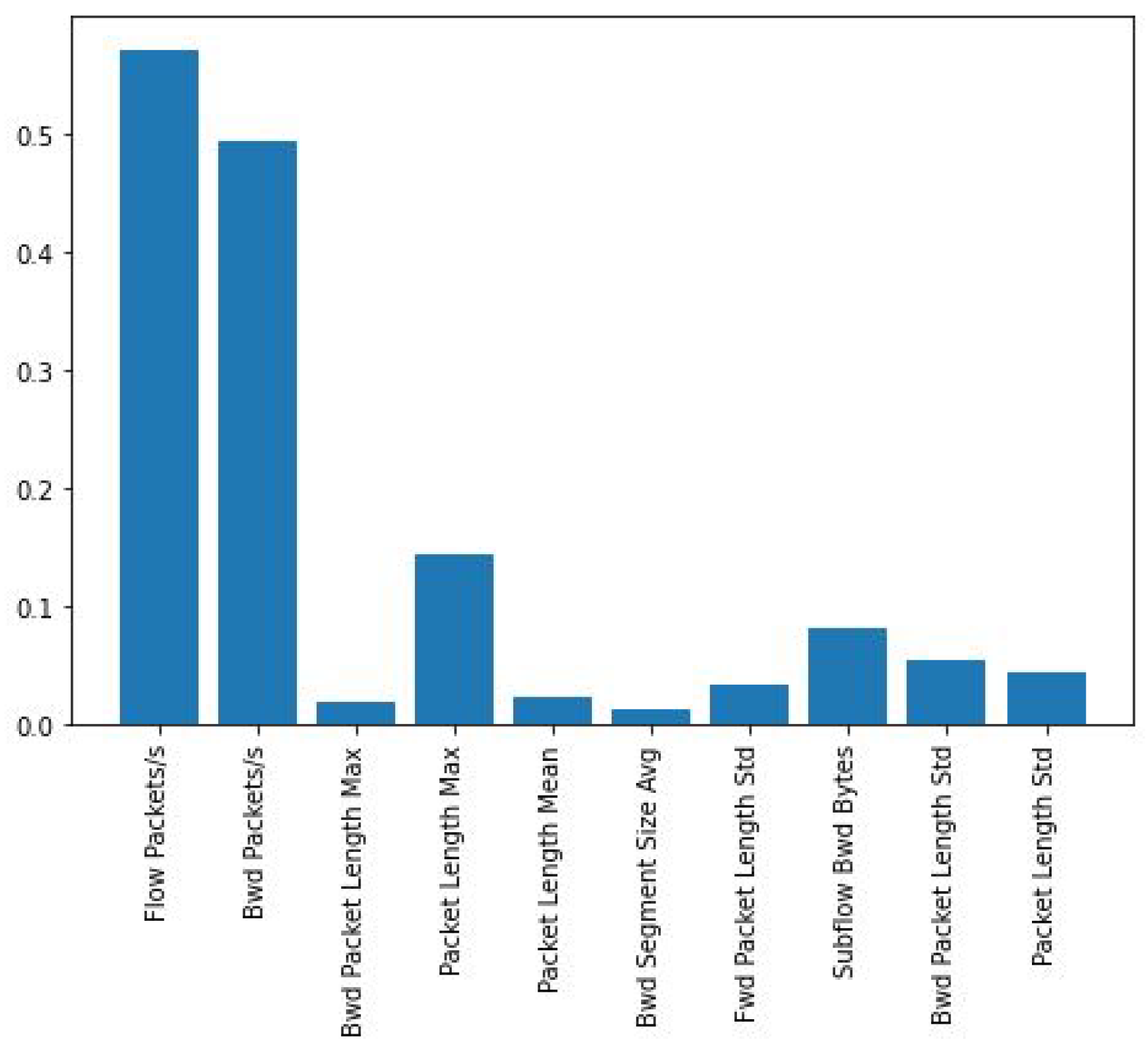
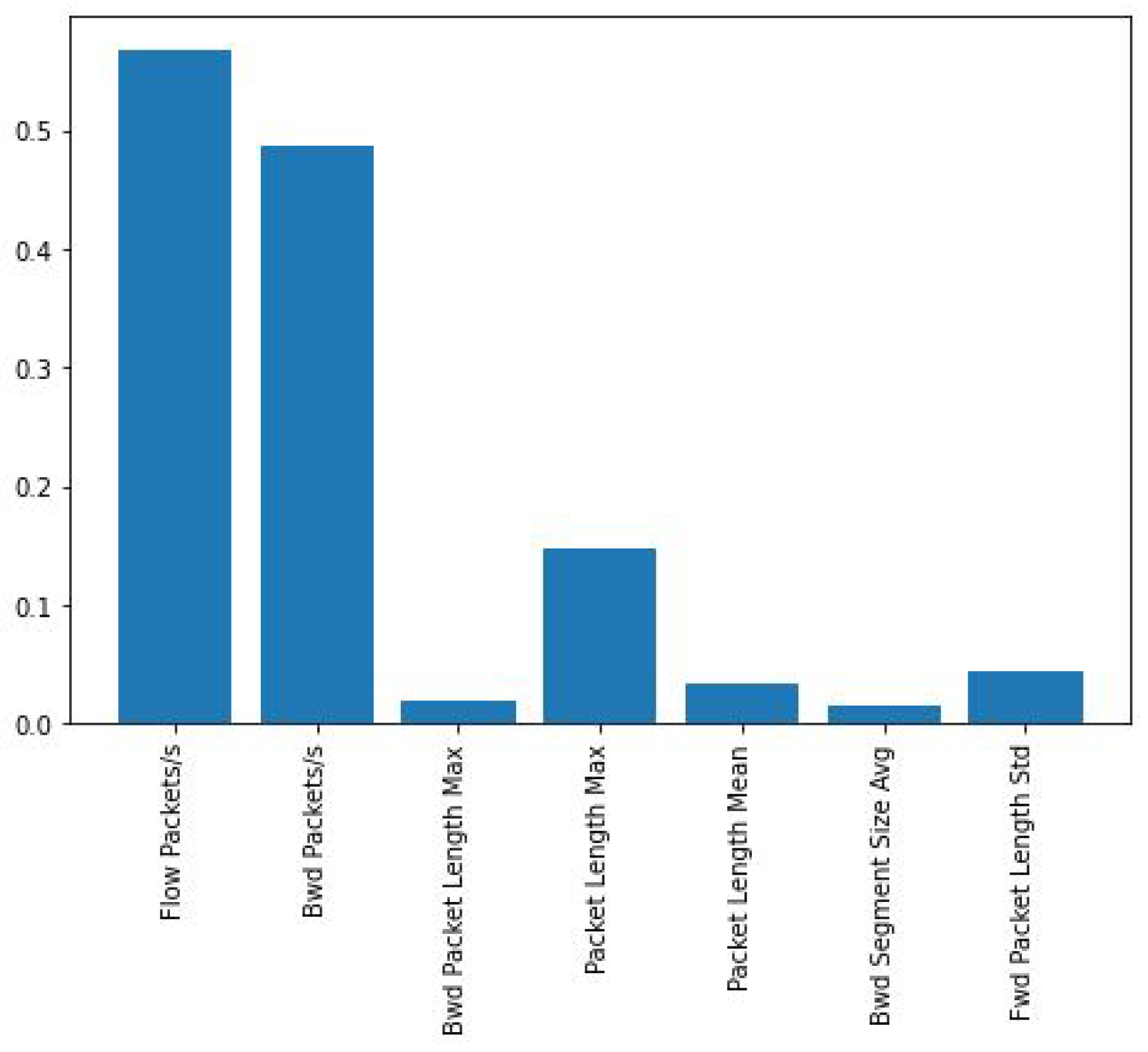
Explainability
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Liu, X.; Ren, J.; He, H.; Zhang, B.; Wang, Q.; Zheng, Z. All-Packets-Based Multi-Rate DDoS Attack Detection Method in ISP Layer. Secur. Commun. Netw. 2022, 2022, 7551107. [Google Scholar] [CrossRef]
- Kaur, D.; Kaur, P. Empirical Analysis of Web Attacks. Procedia Comput. Sci. 2016, 78, 298–306. [Google Scholar] [CrossRef]
- Network Security Infrastructure Report: NETSCOUT; NETSCOUT: Westford, MA, USA, 2019.
- Alzahrani, S.; Hong, L. Generation of DDoS attack dataset for effective IDS development and evaluation. J. Inf. Secur. 2018, 9, 225–241. [Google Scholar] [CrossRef]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Kalkan, K.; Altay, L.; Gür, G.; Alagöz, F. JESS: Joint Entropy-Based DDoS Defense Scheme in SDN. IEEE J. Sel. Areas Commun. 2018, 36, 2358–2372. [Google Scholar] [CrossRef]
- Ahmed, M.E.; Ullah, S.; Kim, H. Statistical Application Fingerprinting for DDoS Attack Mitigation. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1471–1484. [Google Scholar] [CrossRef]
- Wang, A.; Chang, W.; Chen, S.; Mohaisen, A. Delving Into Internet DDoS Attacks by Botnets: Characterization and Analysis. IEEE/ACM Trans. Netw. 2018, 26, 2843–2855. [Google Scholar] [CrossRef]
- Jemal, I.; Haddar, M.A.; Cheikhrouhou, O.; Mahfoudhi, A. Performance evaluation of Convolutional Neural Network for web security. Comput. Commun. 2021, 175, 58–67. [Google Scholar] [CrossRef]
- Matta, V.; Di Mauro, M.; Longo, M. DDoS Attacks with Randomized Traffic Innovation: Botnet Identification Challenges and Strategies. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1844–1859. [Google Scholar] [CrossRef]
- Jia, Y.; Zhong, F.; Alrawais, A.; Gong, B.; Cheng, X. FlowGuard: An Intelligent Edge Defense Mechanism Against IoT DDoS Attacks. IEEE Internet Things J. 2020, 7, 9552–9562. [Google Scholar] [CrossRef]
- Dwivedi, R.; Dave, D.; Naik, H.; Singhal, S.; Omer, R.; Patel, P.; Qian, B.; Wen, Z.; Shah, T.; Morgan, G.; et al. Explainable AI (XAI): Core Ideas, Techniques, and Solutions. ACM Comput. Surv. 2023, 55, 1–33. [Google Scholar] [CrossRef]
- Salih, A.A.; Abdulazeez, A.M. Evaluation of classification algorithms for intrusion detection system: A review. J. Soft Comput. Data Min. 2021, 2, 31–40. [Google Scholar] [CrossRef]
- Lundberg, S.M.; Lee, S.I. A unified approach to interpreting model predictions. Adv. Neural Inf. Process. Syst. 2017, 30, 4768–4777. [Google Scholar]
- Verma, V.; Kumar, V. DoS/DDoS attack detection using machine learning: A review. In Proceedings of the International Conference on Innovative Computing & Communication (ICICC), Delhi, India, 20–21 February 2021. [Google Scholar]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Network Anomaly Detection: Methods, Systems and Tools. IEEE Commun. Surv. Tutor. 2014, 16, 303–336. [Google Scholar] [CrossRef]
- Xiang, Y.; Li, K.; Zhou, W. Low-Rate DDoS Attacks Detection and Traceback by Using New Information Metrics. IEEE Trans. Inf. Forensics Secur. 2011, 6, 426–437. [Google Scholar] [CrossRef]
- NG, B.A.; Selvakumar, S. Anomaly detection framework for Internet of things traffic using vector convolutional deep learning approach in fog environment. Future Gener. Comput. Syst. 2020, 113, 255–265. [Google Scholar] [CrossRef]
- Zheng, J.; Li, Q.; Gu, G.; Cao, J.; Yau, D.K.Y.; Wu, J. Realtime DDoS Defense Using COTS SDN Switches via Adaptive Correlation Analysis. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1838–1853. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J.; Alazab, A. A Novel Ensemble of Hybrid Intrusion Detection System for Detecting Internet of Things Attacks. Electronics 2019, 8, 1210. [Google Scholar] [CrossRef]
- Ravi, N.; Shalinie, S.M. Learning-Driven Detection and Mitigation of DDoS Attack in IoT via SDN-Cloud Architecture. IEEE Internet Things J. 2020, 7, 3559–3570. [Google Scholar] [CrossRef]
- Yuan, X.; Li, C.; Li, X. DeepDefense: Identifying DDoS Attack via Deep Learning. In Proceedings of the 2017 IEEE International Conference on Smart Computing (SMARTCOMP), Hong Kong, China, 29–31 May 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Ateş, Ç.; Özdel, S.; Anarım, E. Clustering based DDoS attack detection using the relationship between packet headers. In Proceedings of the 2019 Innovations in Intelligent Systems and Applications Conference (ASYU), Izmir, Turkey, 31 October–2 November 2019; pp. 1–6. [Google Scholar]
- Ge, M.; Fu, X.; Syed, N.; Baig, Z.; Teo, G.; Robles-Kelly, A. Deep Learning-Based Intrusion Detection for IoT Networks. In Proceedings of the 2019 IEEE 24th Pacific Rim International Symposium on Dependable Computing (PRDC), Kyoto, Japan, 1–3 December 2019; pp. 256–25609. [Google Scholar] [CrossRef]
- Kaur, G.; Gupta, P. Hybrid approach for detecting ddos attacks in software defined networks. In Proceedings of the 2019 Twelfth International Conference on Contemporary Computing (IC3), Noida, India, 8–10 August 2019; pp. 1–6. [Google Scholar]
- Ujjan, R.M.A.; Pervez, Z.; Dahal, K.; Bashir, A.K.; Mumtaz, R.; González, J. Towards sFlow and adaptive polling sampling for deep learning based DDoS detection in SDN. Future Gener. Comput. Syst. 2020, 111, 763–779. [Google Scholar] [CrossRef]
- ur Rehman, S.; Khaliq, M.; Imtiaz, S.I.; Rasool, A.; Shafiq, M.; Javed, A.R.; Jalil, Z.; Bashir, A.K. DIDDOS: An approach for detection and identification of Distributed Denial of Service (DDoS) cyberattacks using Gated Recurrent Units (GRU). Future Gener. Comput. Syst. 2021, 118, 453–466. [Google Scholar] [CrossRef]
- Cui, J.; Wang, M.; Luo, Y.; Zhong, H. DDoS detection and defense mechanism based on cognitive-inspired computing in SDN. Future Gener. Comput. Syst. 2019, 97, 275–283. [Google Scholar] [CrossRef]
- Zhou, L.; Zhu, Y.; Zong, T.; Xiang, Y. A feature selection-based method for DDoS attack flow classification. Future Gener. Comput. Syst. 2022, 132, 67–79. [Google Scholar] [CrossRef]
- Callado, A.; Kamienski, C.; Szabo, G.; Gero, B.P.; Kelner, J.; Fernandes, S.; Sadok, D. A Survey on Internet Traffic Identification. IEEE Commun. Surv. Tutor. 2009, 11, 37–52. [Google Scholar] [CrossRef]
- Lashkari, A.H.; Draper-Gil, G.; Mamun, M.S.I.; Ghorbani, A.A. Characterization of tor traffic using time based features. In Proceedings of the ICISSp, Porto, Portugal, 19–21 February 2017; pp. 253–262. [Google Scholar]
- Friedman, L.; Komogortsev, O.V. Assessment of the Effectiveness of Seven Biometric Feature Normalization Techniques. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2528–2536. [Google Scholar] [CrossRef]
- Singh, J.; Nene, M.J. A survey on machine learning techniques for intrusion detection systems. Int. J. Adv. Res. Comput. Commun. Eng. 2013, 2, 4349–4355. [Google Scholar]
- Haider, S.; Akhunzada, A.; Mustafa, I.; Patel, T.B.; Fernandez, A.; Choo, K.K.R.; Iqbal, J. A deep CNN ensemble framework for efficient DDoS attack detection in software defined networks. IEEE Access 2020, 8, 53972–53983. [Google Scholar] [CrossRef]
- Kalutharage, C.S.; Liu, X.; Chrysoulas, C. Explainable AI and Deep Autoencoders Based Security Framework for IoT Network Attack Certainty. In Proceedings of the International Workshop on Attacks and Defenses for Internet-of-Things, Copenhagen, Denmark, 30 September 2022; pp. 41–50. [Google Scholar]
- Kumar, P.; Tripathi, M.; Nehra, A.; Conti, M.; Lal, C. SAFETY: Early Detection and Mitigation of TCP SYN Flood Utilizing Entropy in SDN. IEEE Trans. Netw. Serv. Manag. 2018, 15, 1545–1559. [Google Scholar] [CrossRef]
- Xie, Y.; Yu, S.Z. Monitoring the Application-Layer DDoS Attacks for Popular Websites. IEEE/ACM Trans. Netw. 2009, 17, 15–25. [Google Scholar] [CrossRef]
- Catillo, M.; Vecchio, A.D.; Ocone, L.; Pecchia, A.; Villano, U. USB-IDS-1: A Public Multilayer Dataset of Labeled Network Flows for IDS Evaluation. In Proceedings of the 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), Taipei, Taiwan, 21–24 June 2021; pp. 1–6. [Google Scholar]
- Catillo, M.; Del Vecchio, A.; Pecchia, A.; Villano, U. Transferability of machine learning models learned from public intrusion detection datasets: The CICIDS2017 case study. Softw. Qual. J. 2022, 30, 955–981. [Google Scholar] [CrossRef]









| Feature | Details |
|---|---|
| fwd-TCP-num | amount of TCP packets forwarded |
| fwd-ACK-num | Amount of ACK flags on forwarded packets |
| fwd-max-ACK | Maximum ACK interval for forwarded packets |
| fwd-SYN-num | SYN flag amount for forwarded packets |
| fwd-SYN-rate | SYN flag transmission rate of forwarded packets |
| Feature | Details |
|---|---|
| src-port | Source port |
| dst-port | Destination port |
| protocol | protocol |
| Feature | Details |
|---|---|
| flow-duration | Flow Duration |
| tot-fwd-pkts | Total amount of packets forwarded |
| tot-bwd-pkts | Total Number of back/forward packets |
| tot-len-bwd-pkts | Total length of backward and forward packets |
| fwd-pkts-len-min | The minimum forward packet length |
| Fwd-Packet-Length-Std | Length variation of forward packets |
| bwd-pkts-len-max | The maximum back-forward packet length |
| flow-packets/s | Packets transferred per second |
| bwd-IAT-tot | Total time interval of the back-forward packets |
| bwd-IAT-mean | Mean time interval of the back-forward packets |
| fwd-psh-num | Number of packets with the PSH flag in forward packets |
| Bwd-Packets/s | back-forward packets transferred per second |
| fwd-ent-int | Time interval entropy of forwarded packets |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kalutharage, C.S.; Liu, X.; Chrysoulas, C.; Pitropakis, N.; Papadopoulos, P. Explainable AI-Based DDOS Attack Identification Method for IoT Networks. Computers 2023, 12, 32. https://doi.org/10.3390/computers12020032
Kalutharage CS, Liu X, Chrysoulas C, Pitropakis N, Papadopoulos P. Explainable AI-Based DDOS Attack Identification Method for IoT Networks. Computers. 2023; 12(2):32. https://doi.org/10.3390/computers12020032
Chicago/Turabian StyleKalutharage, Chathuranga Sampath, Xiaodong Liu, Christos Chrysoulas, Nikolaos Pitropakis, and Pavlos Papadopoulos. 2023. "Explainable AI-Based DDOS Attack Identification Method for IoT Networks" Computers 12, no. 2: 32. https://doi.org/10.3390/computers12020032
APA StyleKalutharage, C. S., Liu, X., Chrysoulas, C., Pitropakis, N., & Papadopoulos, P. (2023). Explainable AI-Based DDOS Attack Identification Method for IoT Networks. Computers, 12(2), 32. https://doi.org/10.3390/computers12020032










