Sparse Decomposition-Based Anti-Spoofing Framework for GNSS Receiver: Spoofing Detection, Classification, and Position Recovery
Abstract
1. Introduction
- (1)
- Unlike methods the proposed in [7,8,9], which only focus on spoofing detection, we devise a sparse decomposition algorithm with non-negative constraints limited by received signal power magnitudes, which not only achieves accurate spoofing detection but also simultaneously extracts key features of the received signal’s contributing components, achieving reliable spoofing classification.
- (2)
- Distinct from the methods introduced in [5,17,18,19,20], we adopt Advanced Iterative Hard Thresholding (AIHT) to integrate the key features extracted from our sparse decomposition method into Auxiliary Peak Tracking (APT), enabling separate tracking of spoofing and authentic components of each satellite to derive the true and spoofed pseudo-range measurements of each satellite. In this way, the intrinsic inconsistency of the spoofing signals can be further exploited without any extra devices and prior assumptions.
- (3)
- By leveraging the inherent inconsistency of spoofing properties, we incorporate the Hausdorff distance to determine the most overlapped position sets to identify genuine position trajectories in general scenarios. Compared with the methods proposed in [10,18,20], this mitigates the impacts of spoofing in position recovery without specific initial state limitations.
- (4)
- The efficacy and advantage of the proposed anti-spoofing framework are fully illustrated by extensive experiments conducted on the public TEXBAT dataset, showing that our algorithm detects 98% of spoofing attacks and guarantees stable position recovery with an average RMSE of 6.32 m across various time periods.
2. Problem Background
2.1. Spoofing Signal Model
2.2. Analysis of the Spoofed Receiver Correlators
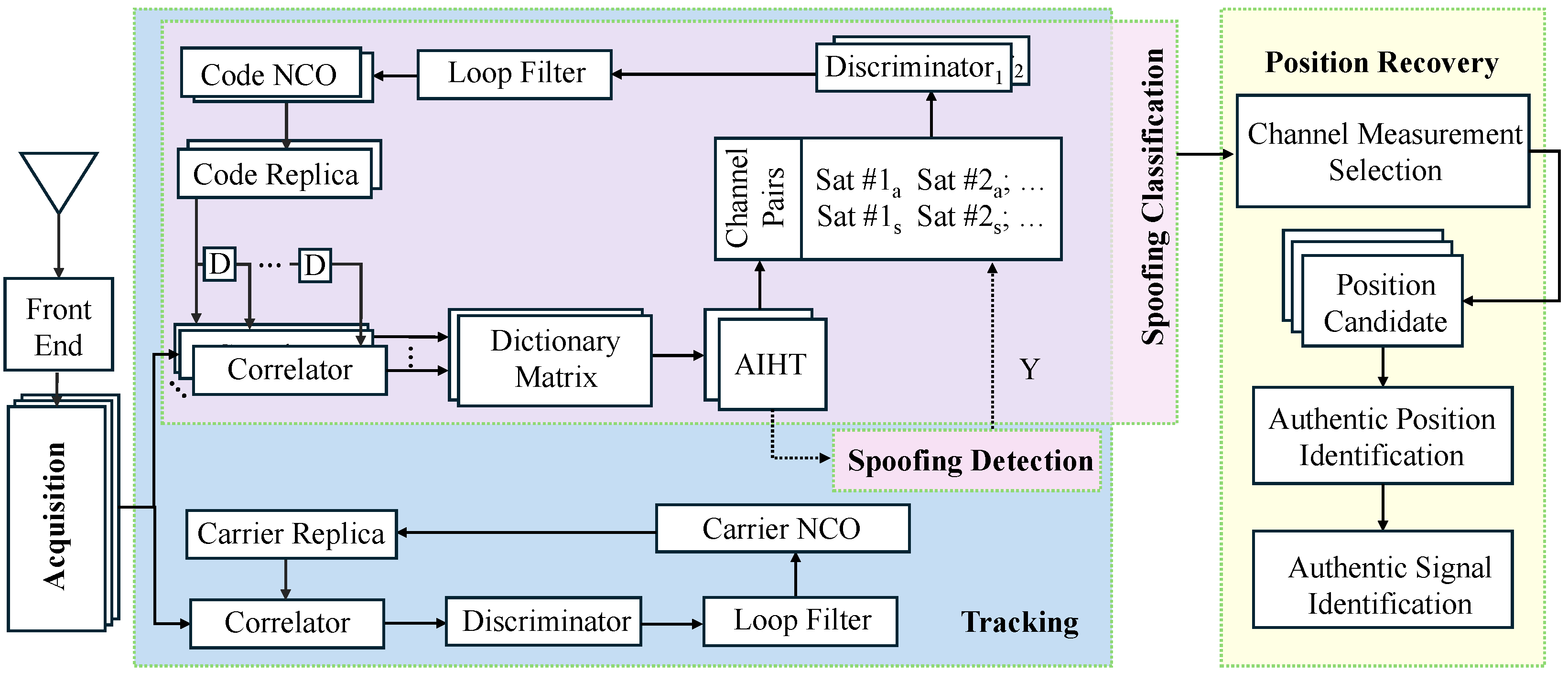
3. Methodology
- i
- In the detection phase, we leverage the sparse nature of the spoofed ACF and apply the AIHT algorithm with an additional non-negative constraint to enhance the accuracy of spoofing interference detection;
- ii
- During the classification stage, we introduce an AIHT-based APT method that tracks both authentic and counterfeit components of the same satellite using dual channels, termed a channel pair. Using code phase gap estimations from the modified AIHT, this method allows for continuous adjustments to the channel pairs.
- iii
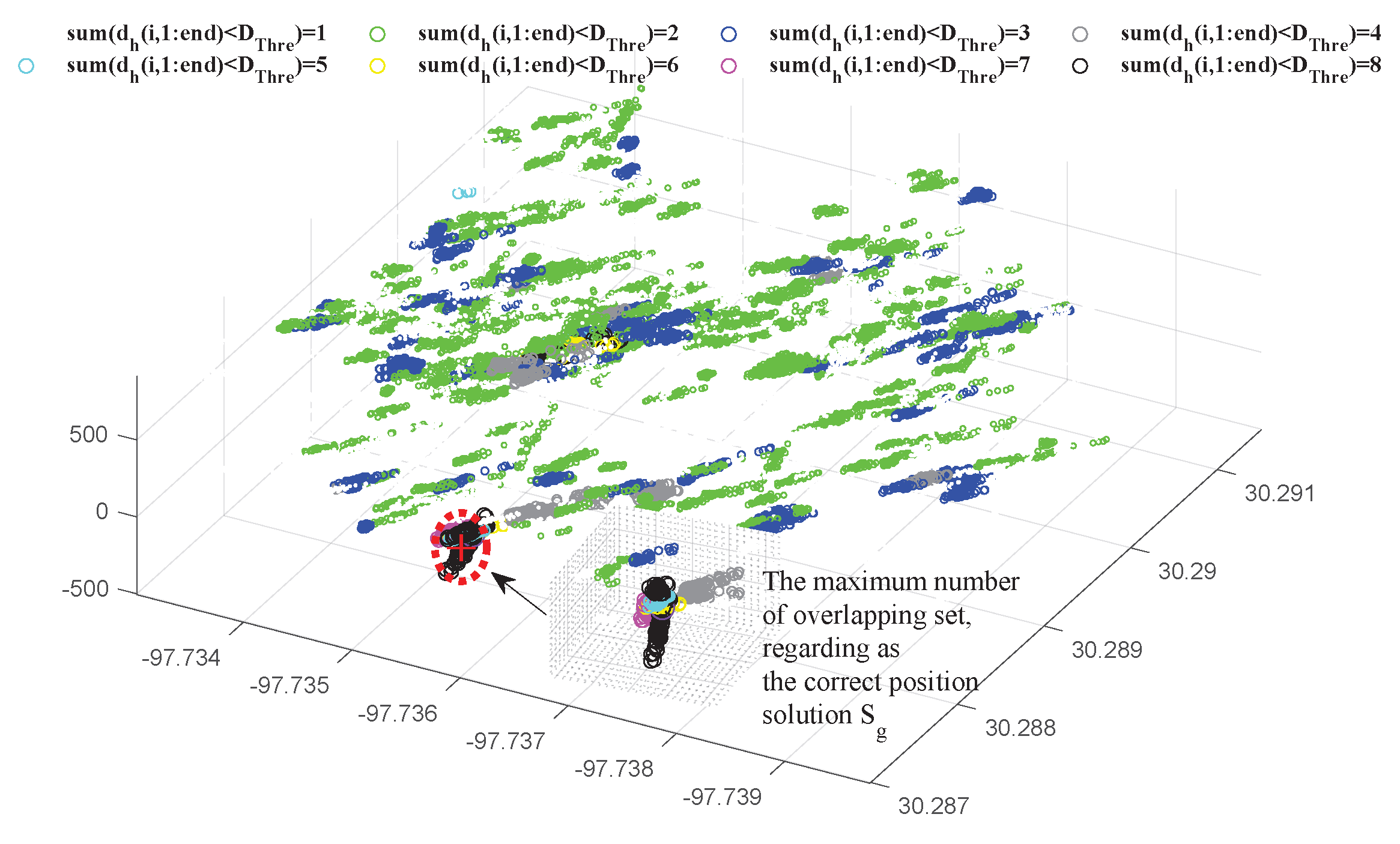
- Finally, by employing different selection schemes, we obtain various position results; we then apply Hausdorff distance to identify the most consistent result, where the greatest number of candidate position sets overlap. This result is considered to be the true position, and the channels within the corresponding selection scheme are recognized for tracking authentic components.
3.1. Sparse Decomposition-Based Spoofing Detection
- Amplitude: The relative amplitude of each component corresponds to the element value in . Elements below are disregarded.
- Count: When the target receiver works normally, exhibits a single peak and has an element exceeding . During spoofing, displays superimposed peaks from and such that two elements in exceed .
- Code Phase: With N set, the non-zero indices in identify the code phase of the peaks of and , denoted as and , respectively, enabling precise mapping of contributing components’ code phases in constructing .
3.2. Advanced IHT Algorithm
3.3. Spoofing Classification via AIHT-Based APT Algorithm
- (1)
- Initial Correction: Since it remains unclear which of the two elements corresponds to , we begin by recovering the correlation peaks and , which represent two distinct components of the overall received signal from the pth spoofed satellite. This is done using the coefficients and from :where and denote that the matrices only contain the non-zero element at the estimated code phase and , indicating the specific peaks extracted from the overall signal.
- (2)
- Channel Allocation for Tracking: Two separate channels, referred to as a channel pair, are allocated to track the pth spoofed satellite. For a GNSS receiver tracking P satellites, a total of P channel pairs, comprising independent digital channels, are required:where represents a channel pair tracking different components of a single satellite for . Each channel within a pair is dedicated to one of the two corrected correlation peaks, and , ensuring simultaneous tracking of both signal components. Specifically, tracks , associated with , while tracks , associated with .
- (3)
- Continuous Update and Tracking: AIHT-based correction is continuously repeated to update coefficients and in each channel, guaranteeing continuous correlation peak corrections and consequently steady tracking across all tracking pairs.
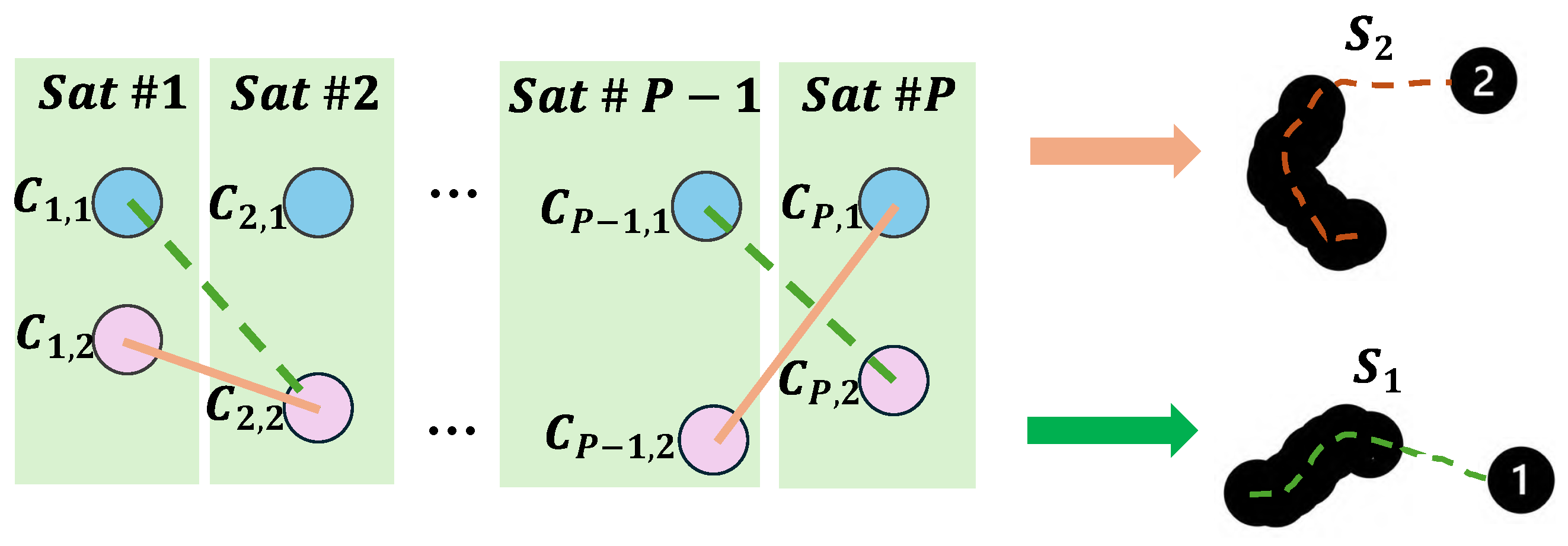
3.4. Position Recovery
- (1)
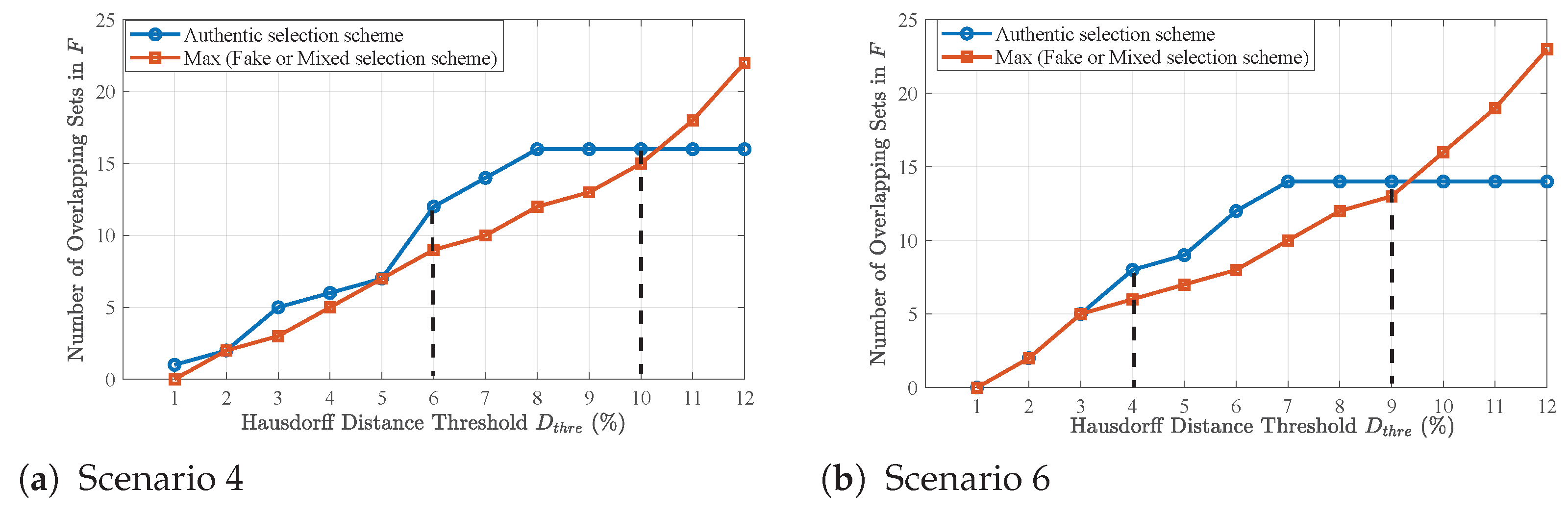
- Authentic selection schemes (P sets): Composed of channels that exclusively track genuine signals; when , these sets tend to produce consistent position results.
- (2)
- Fake selection schemes (P sets): Made up of channels that only track spoofed signals; these sets exhibit varied position outcomes due to the spoofing signals’ inability to continuously generate drag-off phases while simultaneously ensuring a uniform position across all satellites.
- (3)
- Mixed selection schemes ( sets): Consisting of channels tracking both genuine and spoofed signals, the position results from these sets also vary significantly.
3.5. System Overview
- If our algorithm is initiated before spoofing attacks, it confirms that the target receiver is not under spoof, and no further steps are implemented unless the outcome of the AIHT algorithm suggests an opposite decision.
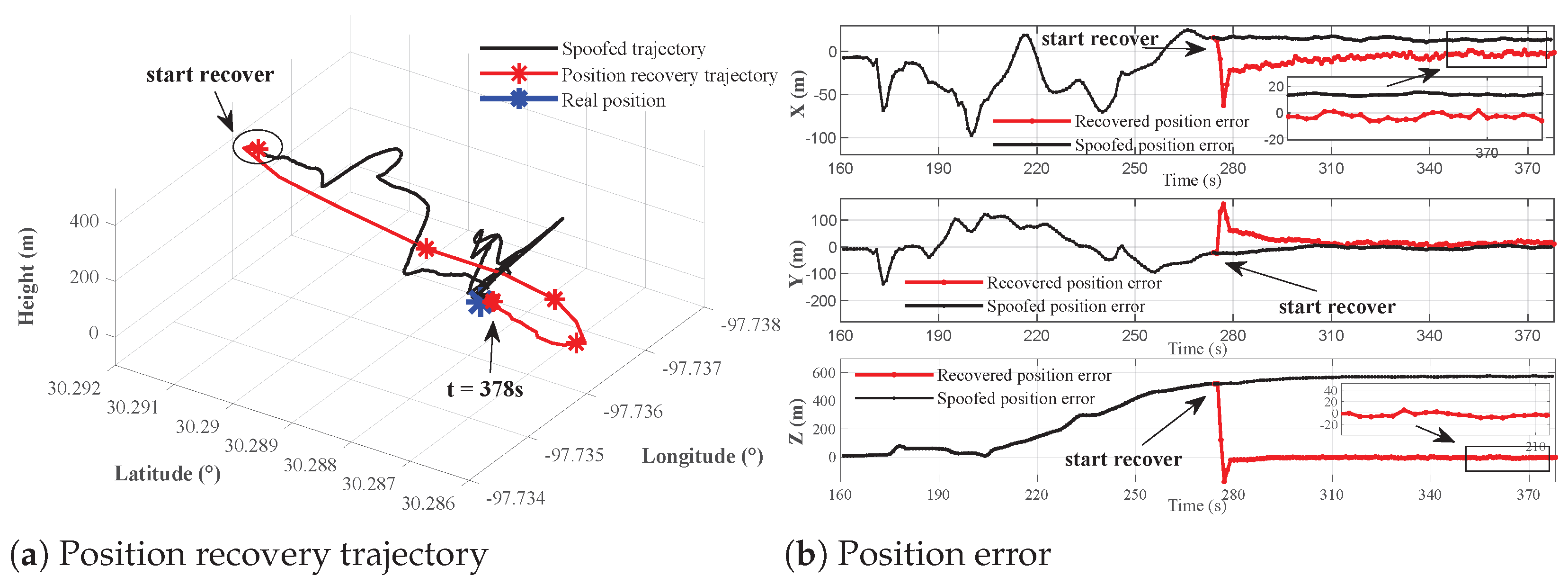
- If our algorithm is run after spoofing attacks, the receiver switches to alarm mode to perform classification and position recovery. The authentic position solution is identified by selecting the gth row (or column) of the distance matrix F with the highest number of overlapping sets.
| Algorithm 1: The proposed spoofing detection, classification and position recovery algorithm. |
| Input: Satellite number P, correlation outputs , prior coefficient level K, reconstruction error , threshold and . Output: Receiver state, selection scheme of () or column () in F.
|
4. Experimental Results
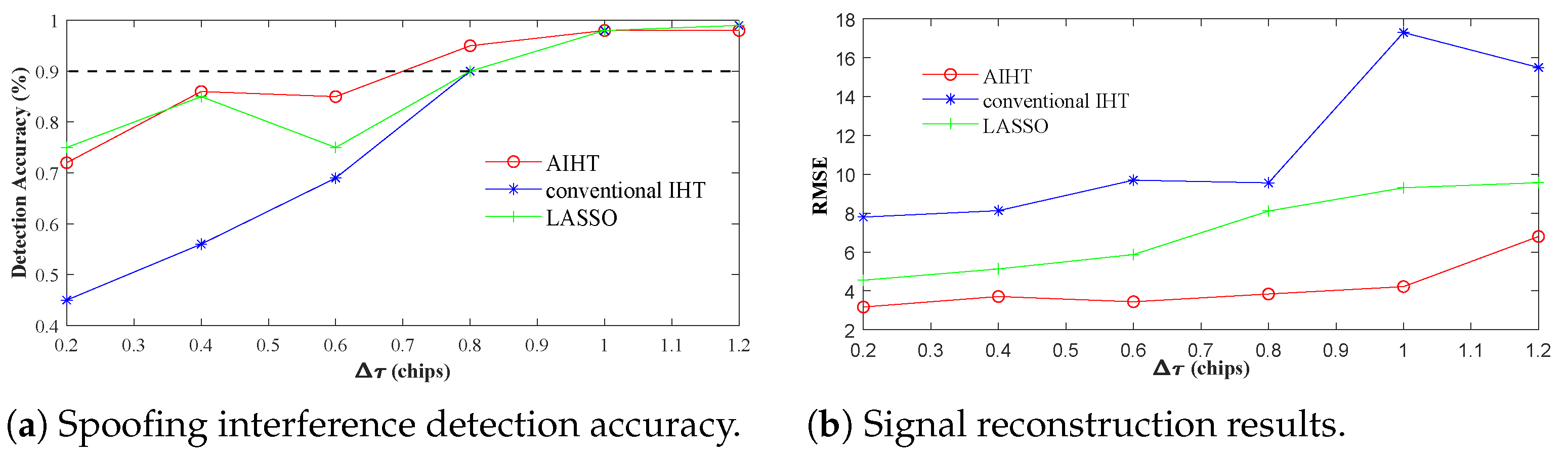
4.1. Performance Analysis of AIHT Algorithm
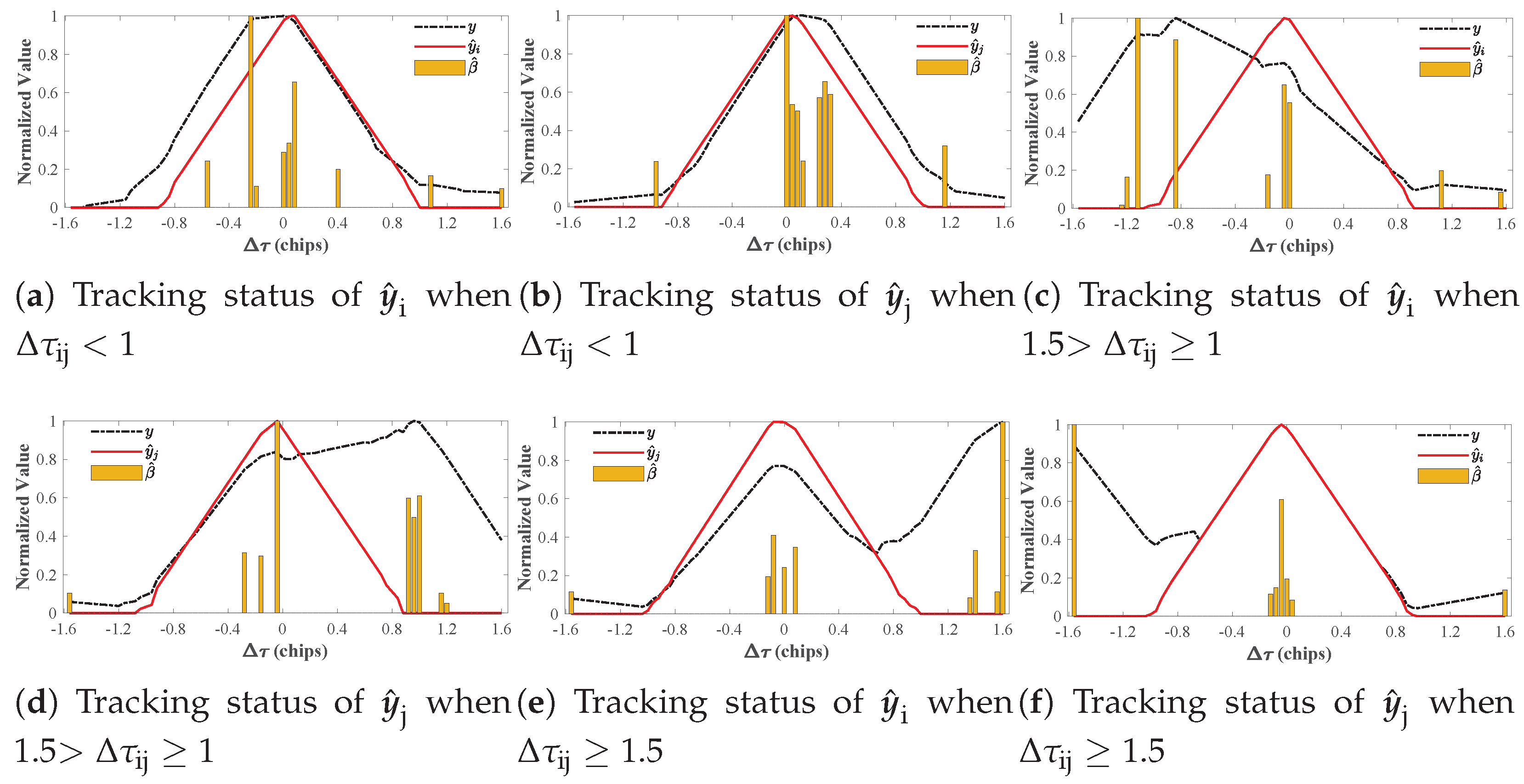
4.2. Robustness Analysis of DLL Under AIHT-Based APT Algorithm
4.3. Evaluation of the Receiver’s Position Recovery Results
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kaplan, E.D.; Hegarty, C. Understanding GPS/GNSS: Principles and Applications; Artech House: Norwood, MA, USA, 2017. [Google Scholar]
- He, Y.; Zhuang, X.; Hou, Y.; Wu, L. Robust blind space-time adaptive processing for measurement error mitigation in GNSS receivers. IET Commun. 2023, 17, 1021–1036. [Google Scholar] [CrossRef]
- Bhatti, J.; Humphreys, T.E. Hostile control of ships via false GPS signals: Demonstration and detection. Navig. J. Inst. Navig. 2017, 64, 51–66. [Google Scholar] [CrossRef]
- Guo, Y.; Wu, M.; Tang, K.; Tie, J.; Li, X. Covert spoofing algorithm of UAV based on GPS/INS-integrated navigation. IEEE Trans. Veh. Technol. 2019, 68, 6557–6564. [Google Scholar] [CrossRef]
- Wang, Y.; Kou, Y.; Huang, Z.; Zhao, Y. GNSS spoofing maximum-likelihood estimation switching between MEDLL and CADLL. GPS Solut. 2023, 27, 148. [Google Scholar] [CrossRef]
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Zhou, Z.; Li, H.; Chen, Z.; Lu, M. Velocity Consistency Checking based GNSS Spoofing Detection Method for Vehicles. IEEE Trans. Veh. Technol. 2023. [Google Scholar] [CrossRef]
- Fang, J.; Yue, J.; Xu, B.; Hsu, L.T. A post-correlation graphical way for continuous GNSS spoofing detection. Measurement 2023, 216, 112974. [Google Scholar] [CrossRef]
- Sun, C.; Cheong, J.W.; Dempster, A.G.; Zhao, H.; Bai, L.; Feng, W. Robust spoofing detection for GNSS instrumentation using Q-channel signal quality monitoring metric. IEEE Trans. Instrum. Meas. 2021, 70, 8504115. [Google Scholar] [CrossRef]
- Schmidt, E.; Gatsis, N.; Akopian, D. A GPS spoofing detection and classification correlator-based technique using the LASSO. IEEE Trans. Aerosp. Electron. Syst. 2020, 56, 4224–4237. [Google Scholar] [CrossRef]
- Wang, H.; Li, H.; Zhong, M.; Lu, M. A Space-Time-Ambiguity Decomposition Method for DOA Estimation Enhancing Anti-Spoofing Via Rotating Dual Antennas. IEEE Trans. Aerosp. Electron. Syst. 2024, 60, 7643–7662. [Google Scholar] [CrossRef]
- He, L.; Li, H.; Lu, M. Dual-antenna GNSS spoofing detection method based on Doppler frequency difference of arrival. Gps Solut. 2019, 23, 78. [Google Scholar] [CrossRef]
- Shang, X.; Sun, F.; Liu, B.; Zhang, L.; Cui, J. GNSS Spoofing Mitigation With a Multicorrelator Estimator in the Tightly Coupled INS/GNSS Integration. IEEE Trans. Instrum. Meas. 2022, 72, 2529013. [Google Scholar] [CrossRef]
- Kujur, B.; Khanafseh, S.; Pervan, B. Optimal INS Monitor for GNSS Spoofer Tracking Error Detection. Navig. J. Inst. Navig. 2024, 71, navi.629. [Google Scholar] [CrossRef]
- Bai, L.; Sun, C.; Dempster, A.G.; Zhao, H.; Feng, W. GNSS Spoofing Detection and Mitigation With a Single 5G Base Station Aiding. IEEE Trans. Aerosp. Electron. Syst. 2024, 60, 4601–4620. [Google Scholar] [CrossRef]
- Kujur, B.; Khanafseh, S.; Pervan, B. Detecting GNSS spoofing of ADS-B equipped aircraft using INS. In Proceedings of the 2020 IEEE/ION Position, Location and Navigation Symposium (PLANS), Portland, OR, USA, 20–23 April 2020; pp. 548–554. [Google Scholar] [CrossRef]
- Kuusniemi, H.; Blanch, J.; Chen, Y.H.; Lo, S.; Innac, A.; Ferrara, G.; Honkala, S.; Bhuiyan, M.Z.H.; Thombre, S.; Söderholm, S.; et al. Feasibility of fault exclusion related to advanced RAIM for GNSS spoofing detection. In Proceedings of the 30th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2017), Portland, OR, USA, 25–29 September 2017; pp. 2359–2370. [Google Scholar]
- Zhou, W.; Lv, Z.; Wu, W.; Shang, X.; Ke, Y. Anti-spoofing technique based on vector tracking loop. IEEE Trans. Instrum. Meas. 2023, 72, 8504516. [Google Scholar] [CrossRef]
- Xu, B.; Jia, Q.; Hsu, L.T. Vector tracking loop-based GNSS NLOS detection and correction: Algorithm design and performance analysis. IEEE Trans. Instrum. Meas. 2019, 69, 4604–4619. [Google Scholar] [CrossRef]
- Shang, X.; Sun, F.; Zhang, L.; Cui, J.; Zhang, Y. Detection and mitigation of GNSS spoofing via the pseudorange difference between epochs in a multicorrelator receiver. Gps Solut. 2022, 26, 37. [Google Scholar] [CrossRef]
- Humphreys, T.E.; Bhatti, J.A.; Shepard, D.; Wesson, K. The Texas Spoofing Test Battery: Toward a Standard for Evaluating GPS Signal Authentication Techniques; The University of Texas: Austin, TX, USA, 2012. [Google Scholar]
- Mohimani, H.; Babaie-Zadeh, M.; Jutten, C. A fast approach for overcomplete sparse decomposition based on smoothed L0 norm. IEEE Trans. Signal Process. 2008, 57, 289–301. [Google Scholar] [CrossRef]
- Blanchard, J.D.; Cermak, M.; Hanle, D.; Jing, Y. Greedy algorithms for joint sparse recovery. IEEE Trans. Signal Process. 2014, 62, 1694–1704. [Google Scholar] [CrossRef]
- Foucart, S.; Lecué, G. An IHT algorithm for sparse recovery from subexponential measurements. IEEE Signal Process. Lett. 2017, 24, 1280–1283. [Google Scholar] [CrossRef]
- Blumensath, T.; Davies, M.E. Iterative hard thresholding for compressed sensing. Appl. Comput. Harmon. Anal. 2009, 27, 265–274. [Google Scholar] [CrossRef]
- Huttenlocher, D.P.; Klanderman, G.A.; Rucklidge, W.J. Comparing images using the Hausdorff distance. IEEE Trans. Pattern Anal. Mach. Intell. 1993, 15, 850–863. [Google Scholar] [CrossRef]
- Humphreys, T. TEXBAT Data Sets 7 and 8; The University of Texas: Austin, TX, USA, 2016. [Google Scholar]
- Söderholm, S.; Bhuiyan, M.Z.H.; Thombre, S.; Ruotsalainen, L.; Kuusniemi, H. A multi-GNSS software-defined receiver: Design, implementation, and performance benefits. Ann. Telecommun. 2016, 71, 399–410. [Google Scholar] [CrossRef]










| (chip) | Direction | RMSE (m) | |
|---|---|---|---|
| 0 s–80 s | 80 s–end | ||
| non-spoofing | X | 14.4, 159.1 | 4.9, 9.3 |
| Y | 25.6, 18.1 | 7.0, 8.2 | |
| Z | 17.5, 49.8 | 6.1, 8.3 | |
| X | 37.8, 349.4 | 3.7, 9.4 | |
| Y | 33.4, 76.6 | 5.3, 10.1 | |
| Z | 71.6, 222.4 | 6.4, 9.8 | |
| X | 13.1, 527.1 | 3.2, 7.4 | |
| Y | 34.7, 82.3 | 14.1, 11.9 | |
| Z | 62.4, 187.8 | 6.2, 10.1 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, Y.; Zhuang, X.; Xu, B. Sparse Decomposition-Based Anti-Spoofing Framework for GNSS Receiver: Spoofing Detection, Classification, and Position Recovery. Remote Sens. 2025, 17, 2703. https://doi.org/10.3390/rs17152703
He Y, Zhuang X, Xu B. Sparse Decomposition-Based Anti-Spoofing Framework for GNSS Receiver: Spoofing Detection, Classification, and Position Recovery. Remote Sensing. 2025; 17(15):2703. https://doi.org/10.3390/rs17152703
Chicago/Turabian StyleHe, Yuxin, Xuebin Zhuang, and Bing Xu. 2025. "Sparse Decomposition-Based Anti-Spoofing Framework for GNSS Receiver: Spoofing Detection, Classification, and Position Recovery" Remote Sensing 17, no. 15: 2703. https://doi.org/10.3390/rs17152703
APA StyleHe, Y., Zhuang, X., & Xu, B. (2025). Sparse Decomposition-Based Anti-Spoofing Framework for GNSS Receiver: Spoofing Detection, Classification, and Position Recovery. Remote Sensing, 17(15), 2703. https://doi.org/10.3390/rs17152703







