Localization of GNSS Spoofing Interference Source Based on a Moving Array Antenna
Abstract
:1. Introduction
1.1. Related Work
1.2. Our Contributions
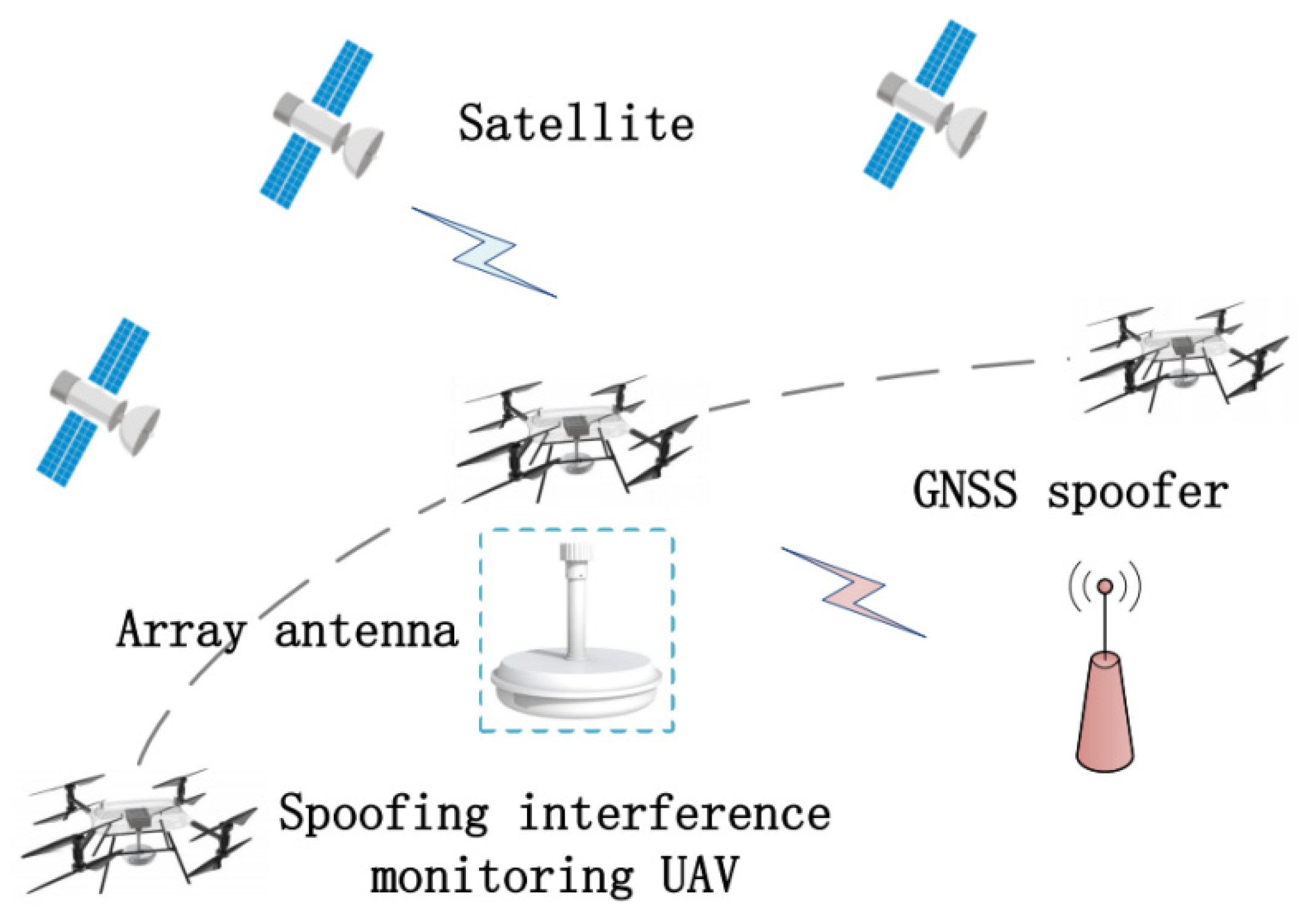
2. System Model and Signal Processing Methods
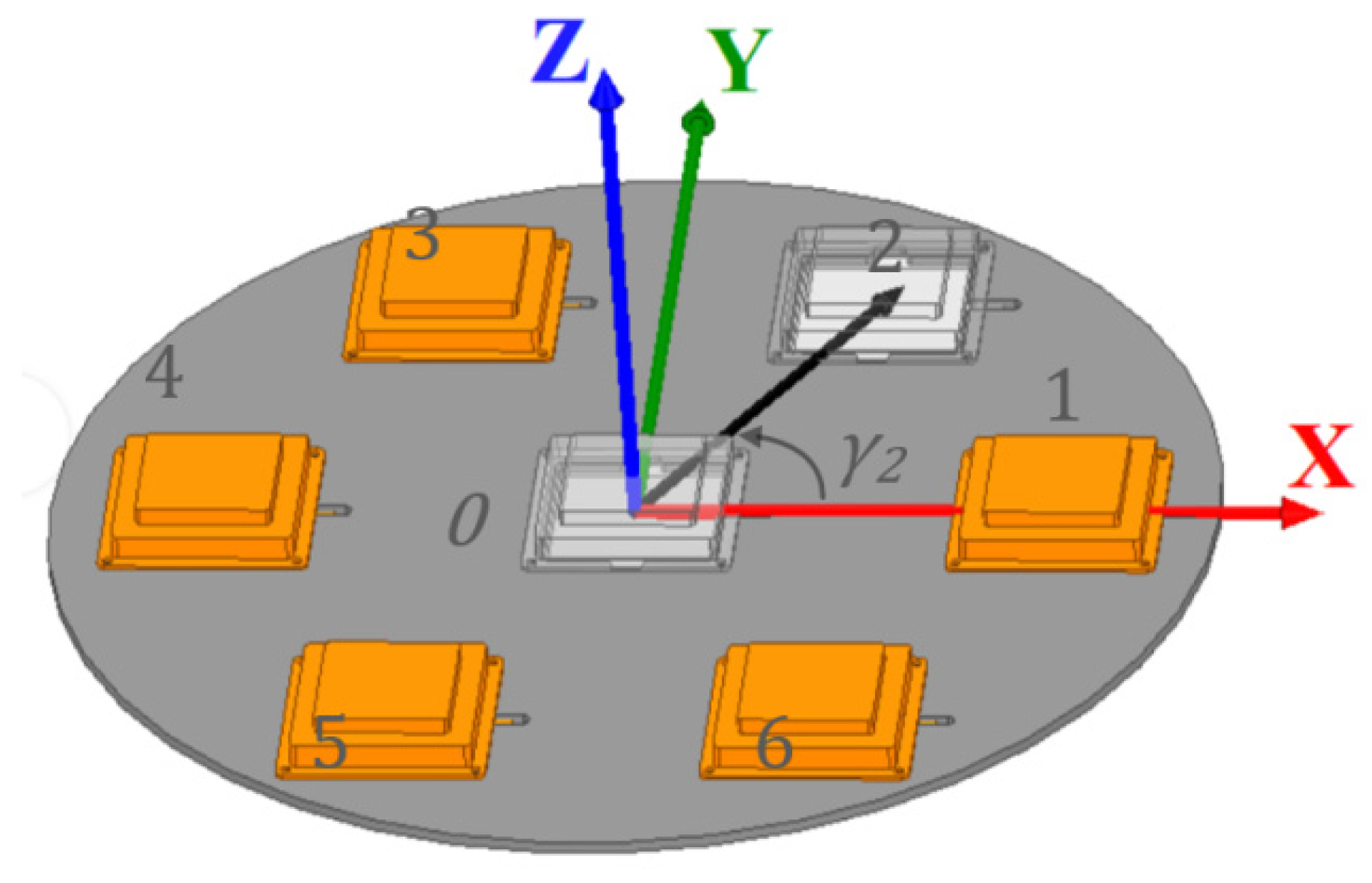
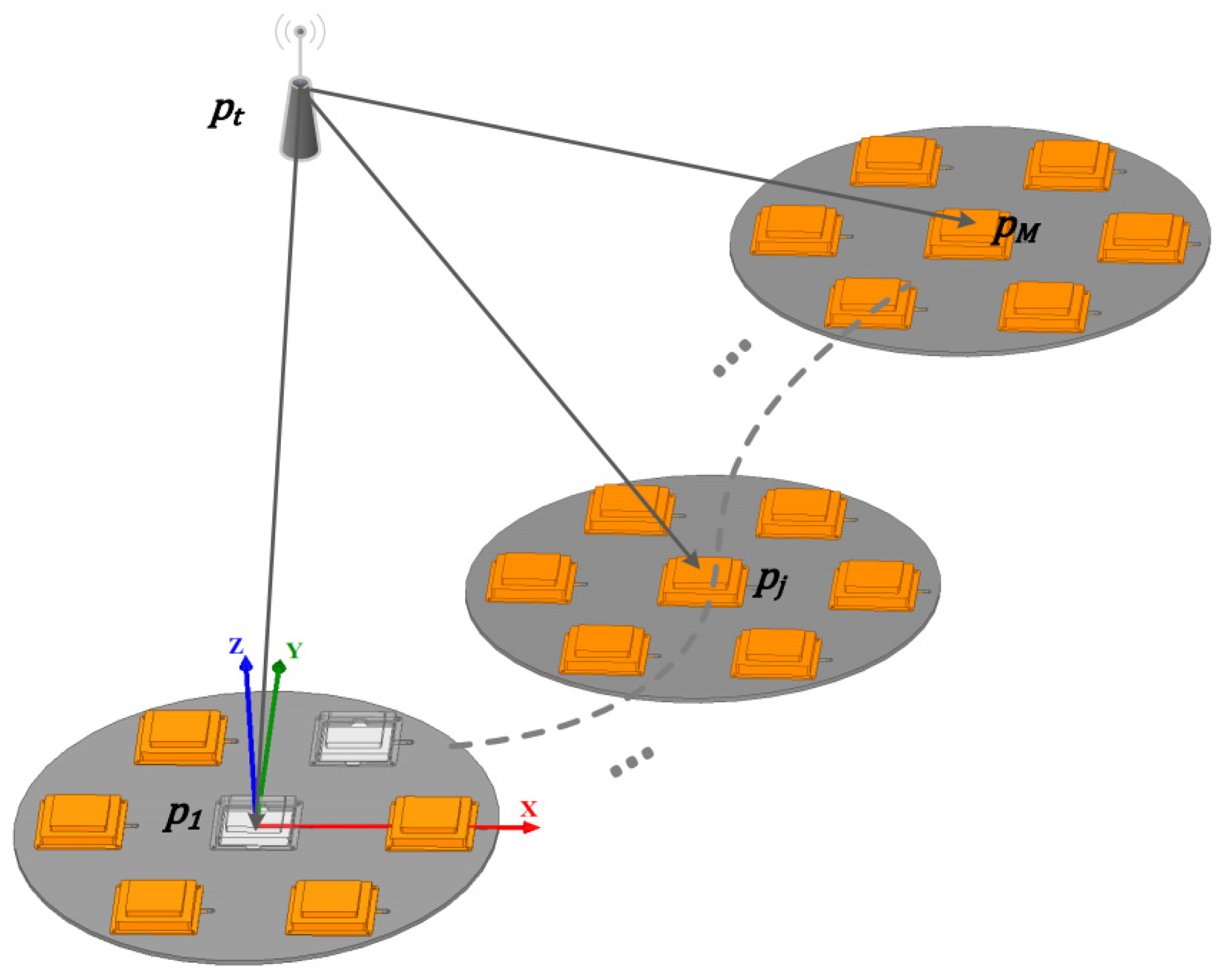
2.1. Antenna Model
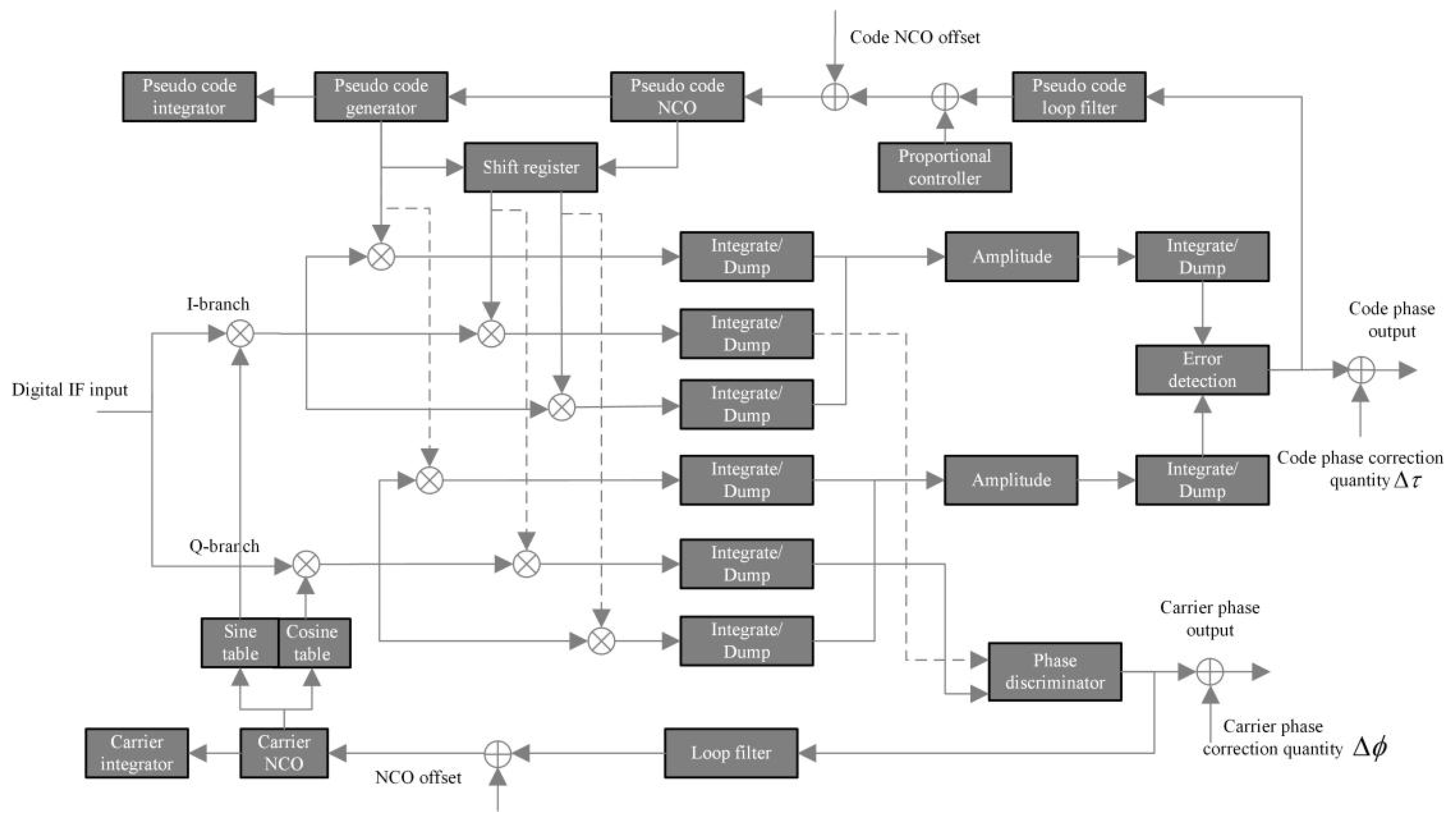
2.2. Signal Acquisition and Tracking Methods
3. Proposed Methods
3.1. Extraction of Spoofing Interference Based on the Double-Differenced Carrier Phase
3.2. Spoofing Interference Direct Location Based on Carrier Phase Single-Difference
3.3. The CRB of the Method Proposed in This Article
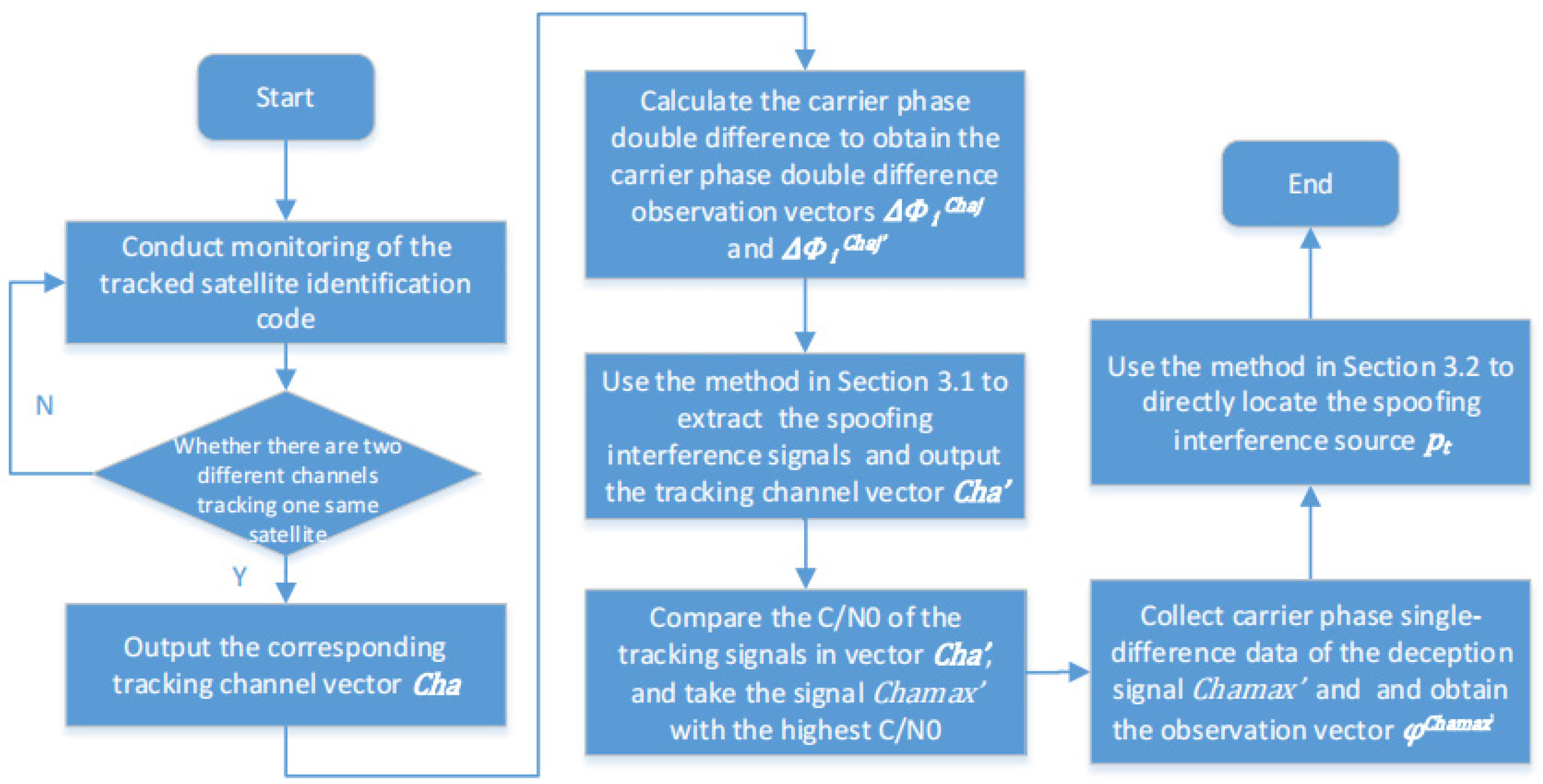
3.4. The Method Processing Flow
- We conduct real-time monitoring of the satellite identification code tracked by each tracking channel and determine whether there are two different channels tracking the same satellite. If the above conditions exist, it is judged spoofing interference is detected, and output the corresponding tracking channel vector , where and are channel numbers tracking the same satellite.
- Take any pair of tracking channels and that track the same satellite signal, take any antenna array element , and calculate the carrier phase double-difference between the other channels in and the selected channel to obtain the carrier phase double-difference observation vectors and , where the expression of double-differenced carrier phase is the same as that of Equation (5).
- After obtaining the carrier phase double-difference, use the method in Section 3.1 to extract and confirm the spoofing interference signals and output the tracking channel vector = corresponding to the deception satellite signals.
- Compare the carrier-to-noise ratio (C/N0) of the tracking signals of each channel in vector , and take the deception satellite signal with the highest C/N0 among them.
- Collect carrier phase single-difference data of the deception signal along the spoofing location path and obtain the observation vector , where the expression of carrier phase single-difference is the same as that of Equation (6).
- After acquiring the carrier phase single difference data, employ the methodology elucidated in Section 3.2 to directly ascertain the precise location of the spoofing interference and yield the spatial coordinates of its source .
- The double-differenced carrier phase-based spoofing interference extraction method enables an efficient separation between the real satellite signals and the spoofing signals, thereby facilitating the use of authentic satellite signals for determining the position of the array antenna itself.
- After implementing spoofing interference extraction, in principle, any satellite signal of the spoofing interference can be utilized to construct equation system (9). With increased signal strength, the accuracy of carrier phase measurement also improves, thus enhancing the effectiveness of the method; we select the satellite signal with the highest C/N0 for establishing the equation.
- The method presented in this paper is also applicable to multiple spoofing interference source localization scenarios; however, the applicable scenario requires that the located interfering source emits two or more spurious satellite signals. For multiple spoofing interference sources, the method in Section 3.1 of this paper can be used multiple times to extract multiple spoofing source signals. After the multiple spoofing sources are identified, the method described in Section 3.2 can be applied to each spoofing source to achieve efficient localization of multiple spoofing sources.
4. Simulations and Results
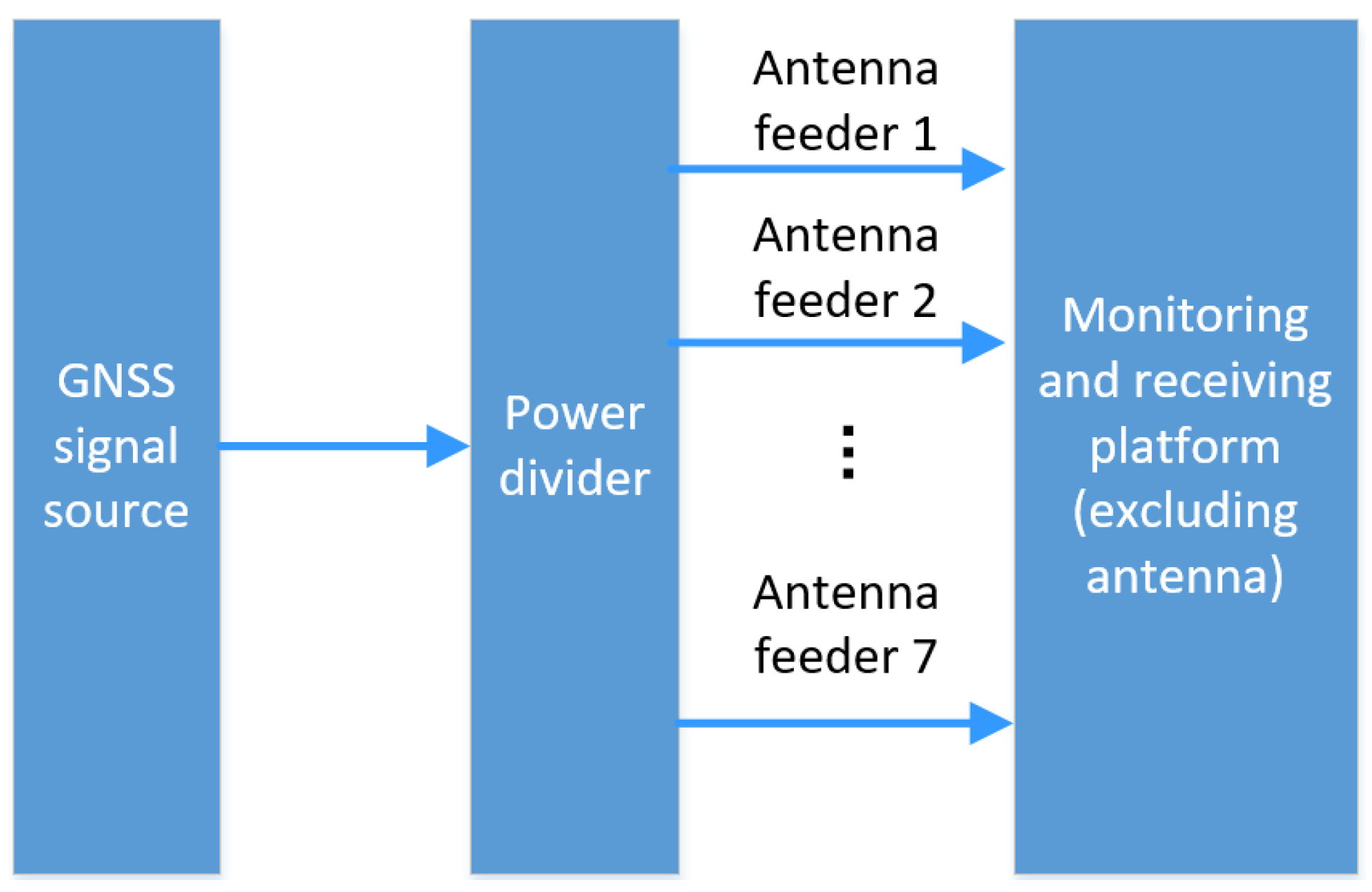
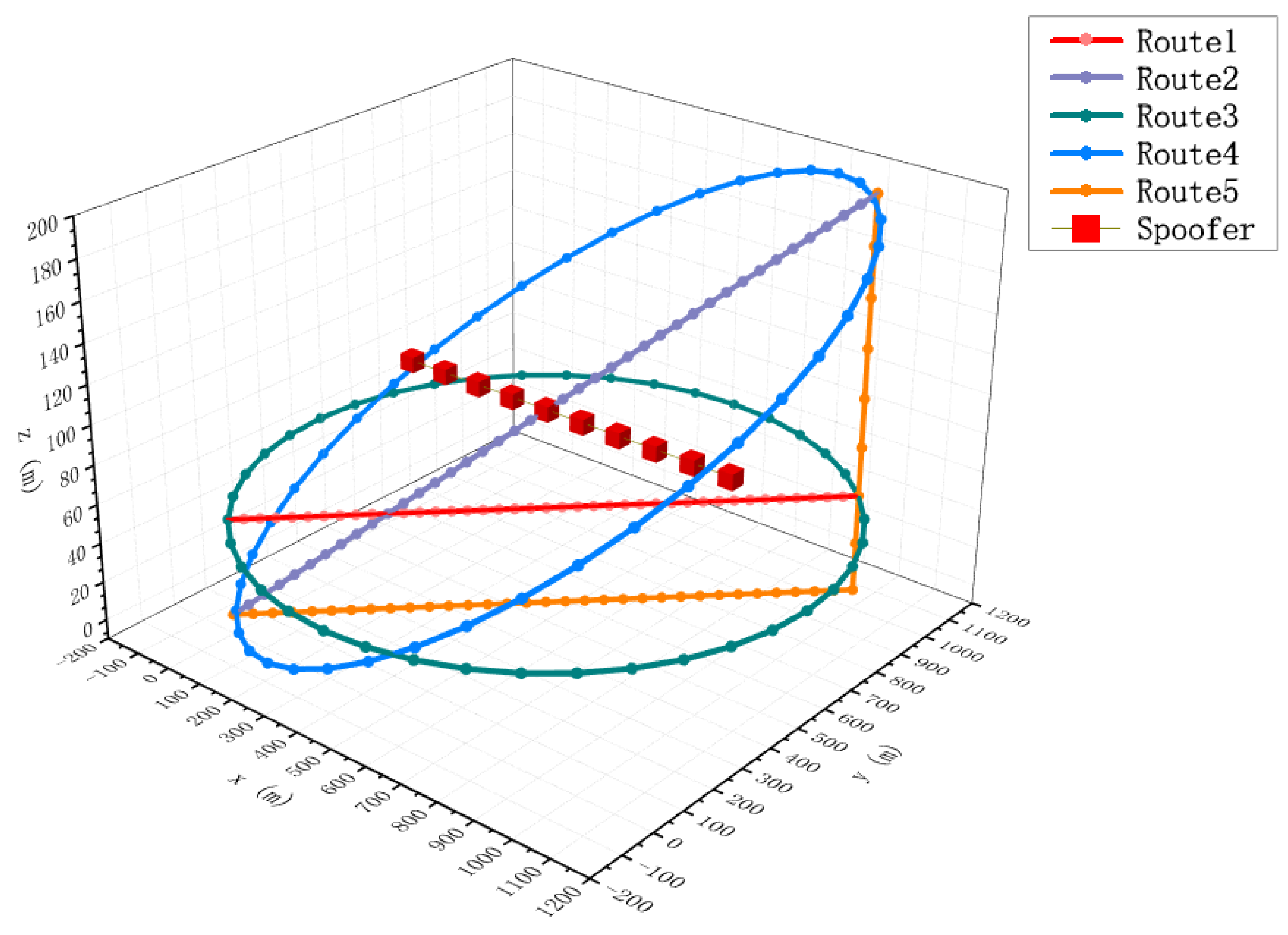
4.1. Simulation Scenario
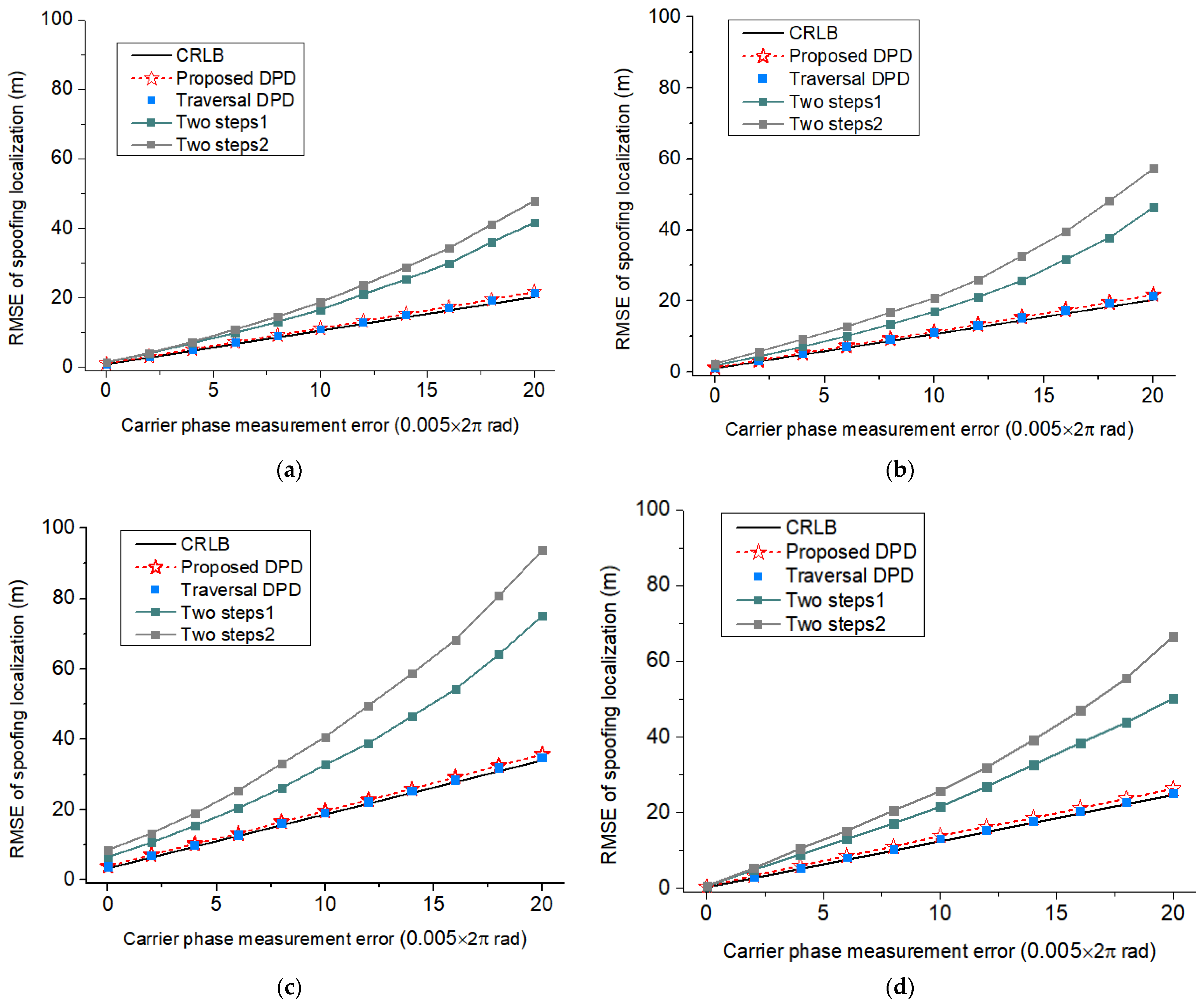
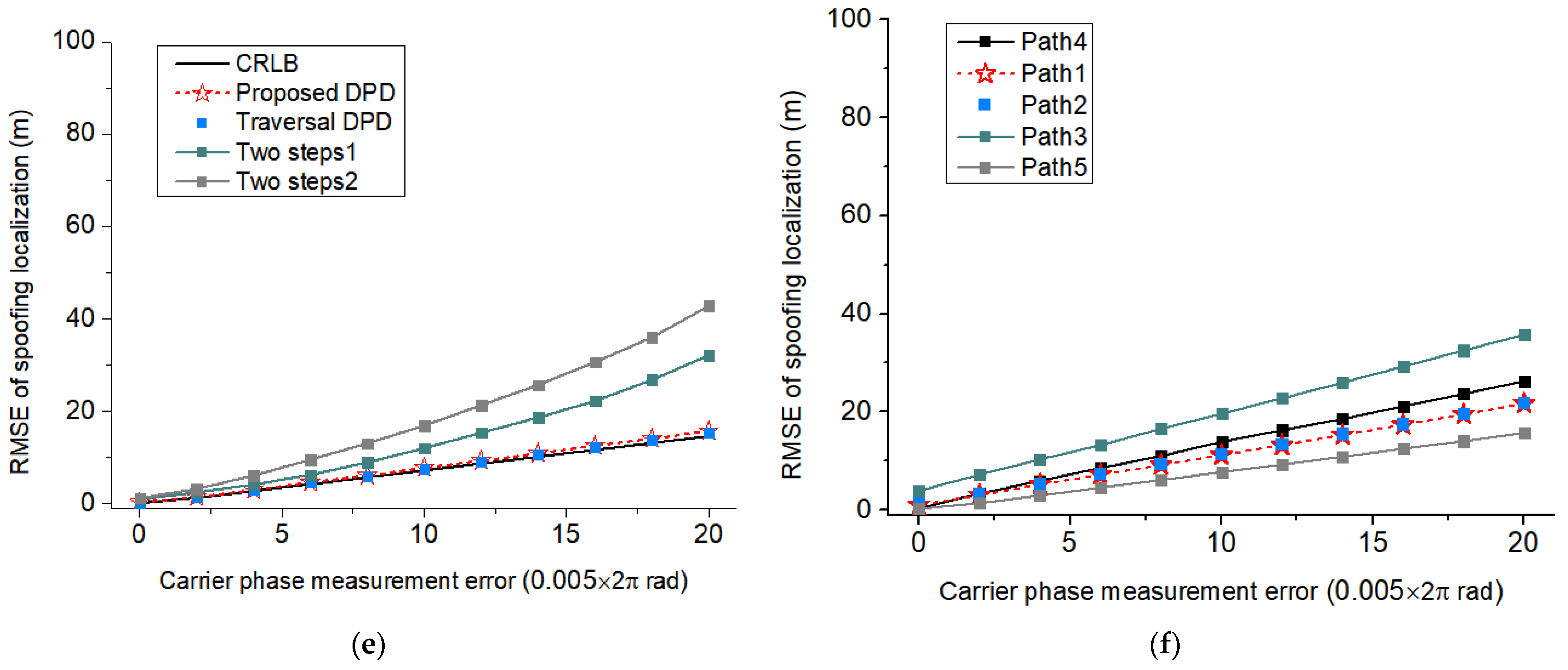
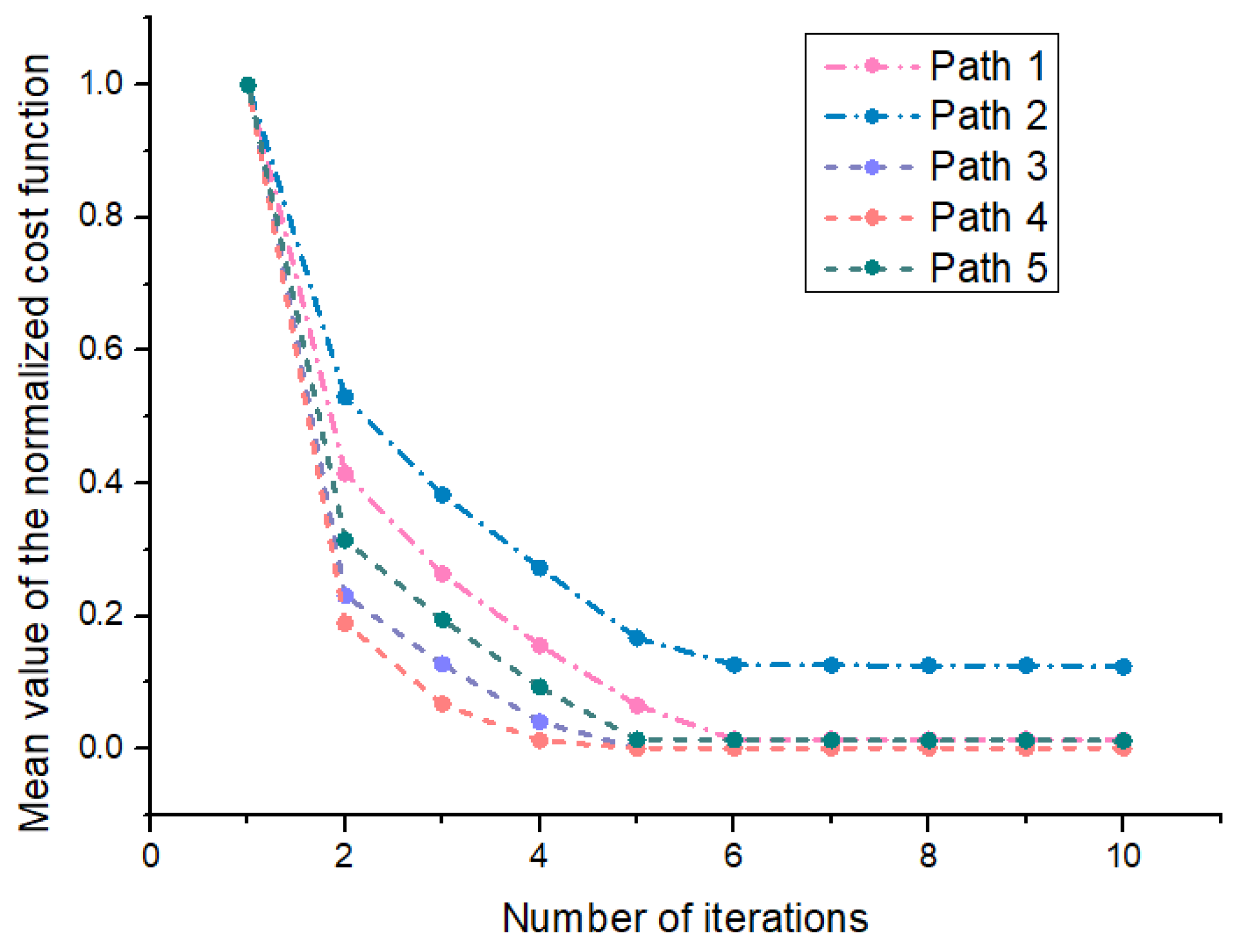
- Path 1 corresponds to the setting of covering the monitoring area with the shortest path at a fixed monitoring height under the condition that the monitoring platform height cannot be raised (such as limited airspace height or ground monitoring equipment scenarios).
- Path 2 corresponds to the setting of covering the monitoring area with the shortest path under the condition that the height of the monitoring platform can rise.
- Path 3 corresponds to the setting of covering the monitoring area with the maximum circular area under the condition that the monitoring platform height cannot be raised.
- Path 4 corresponds to the setting of covering the monitoring area with the maximum elliptical area under the condition that the height of the monitoring platform can rise.
- Path 5 corresponds to only supplementing the displacement setting in the z-direction on the basis of Path 1 under the condition that the height of the monitoring platform can rise.
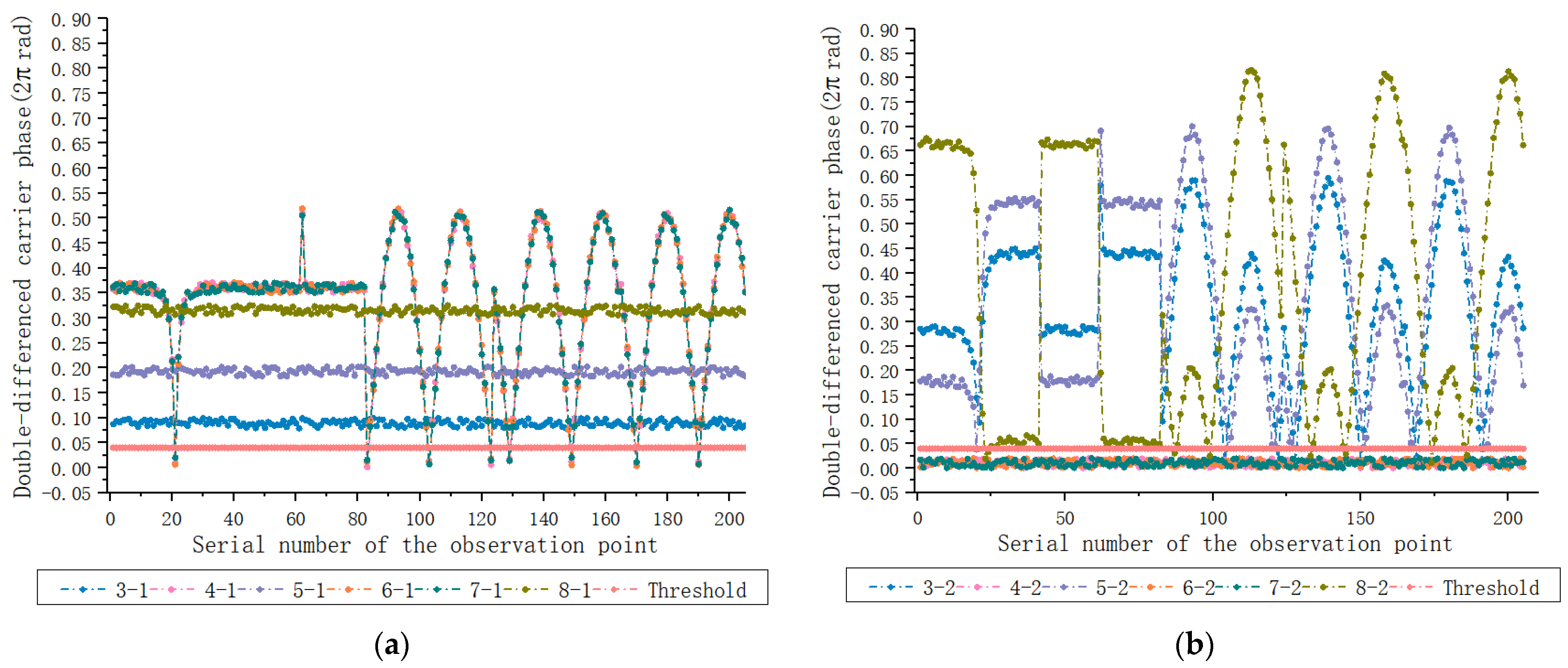
4.2. Experiment 1: Spoofing Extraction Effects Based on the Double-Difference Carrier Phase
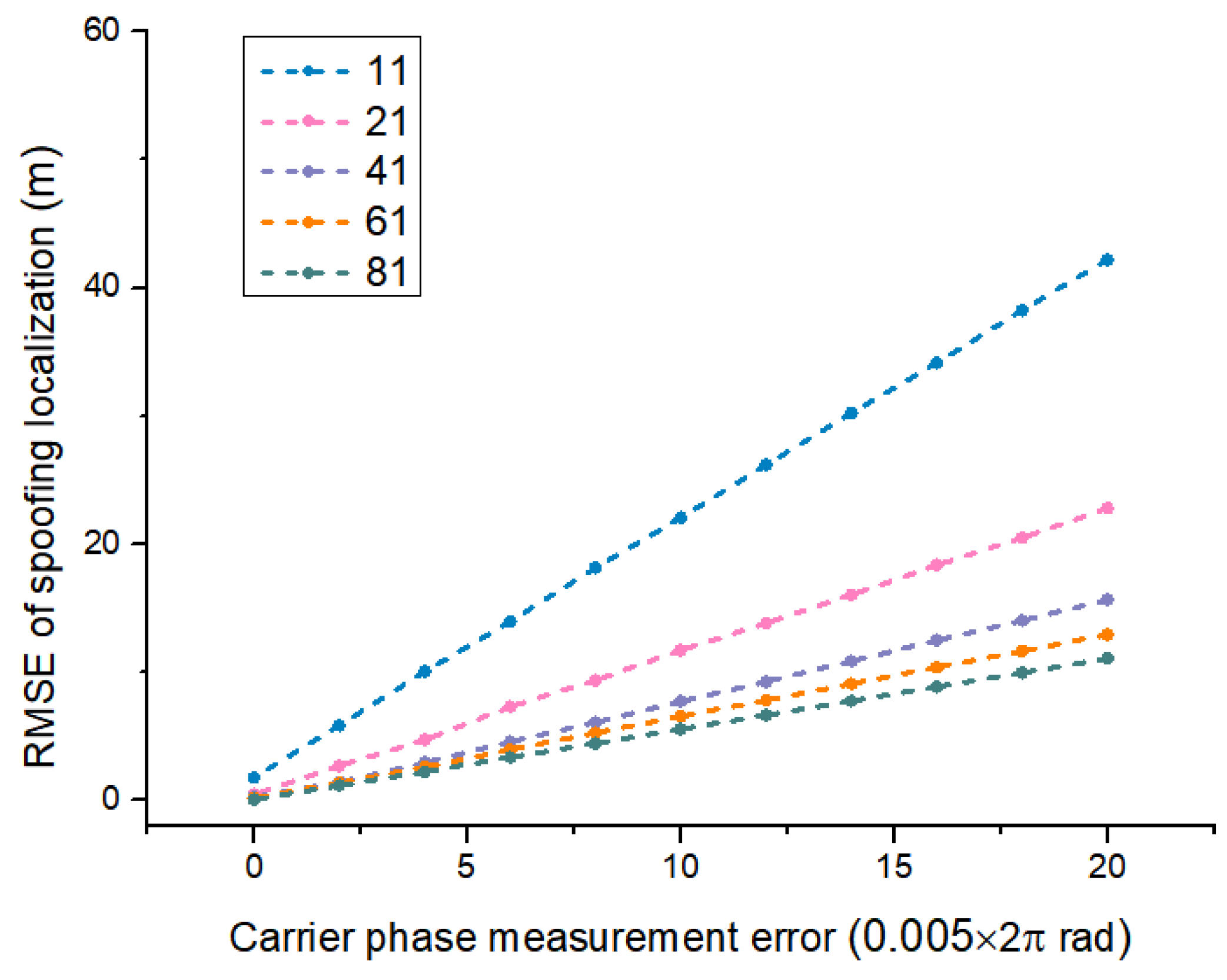
4.3. Experiment 2: Spoofing Localization Effects at Different Carrier Phase Measurement Errors
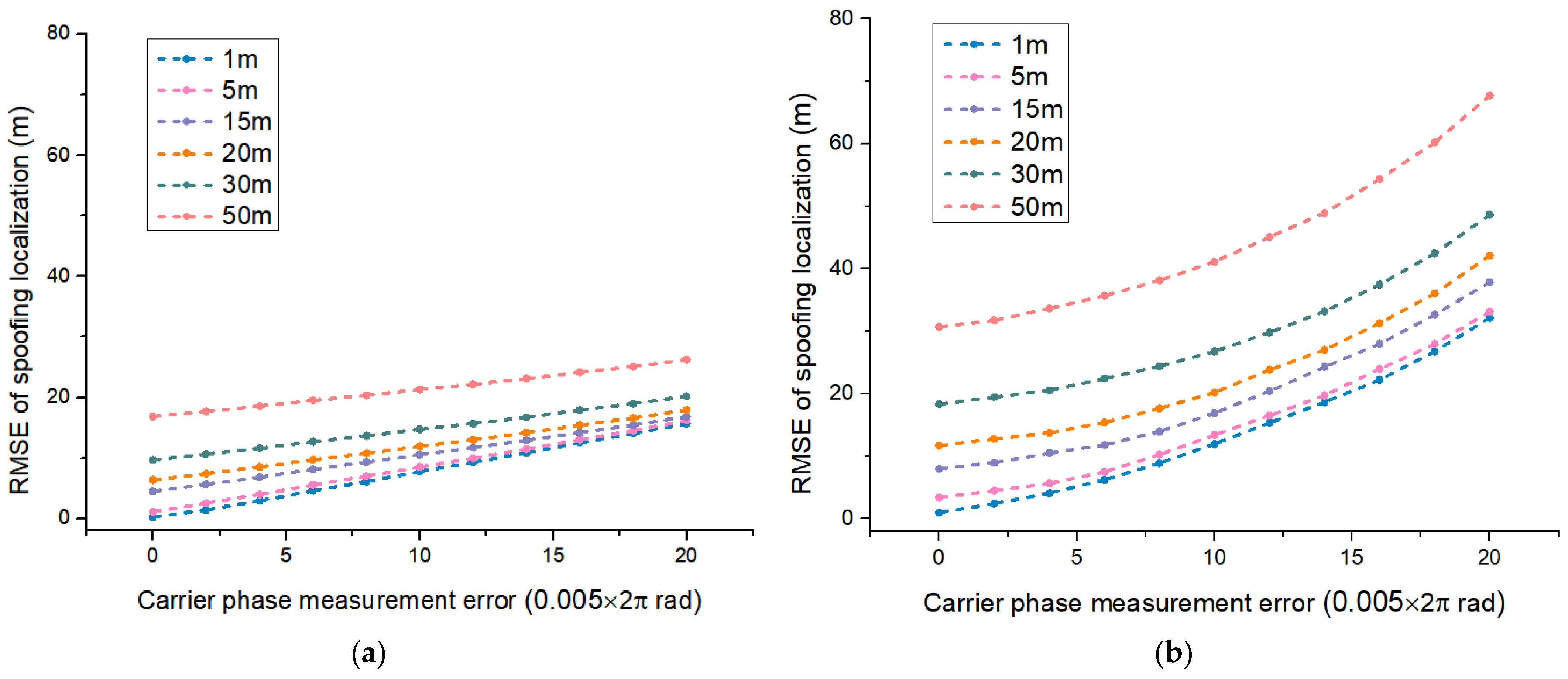
4.4. Experiment 3: Spoofing Localization Effects under Different Antenna Positioning Errors
4.5. Experiment 4: Spoofing Localization Effects Considering Varying Numbers of Observation Points
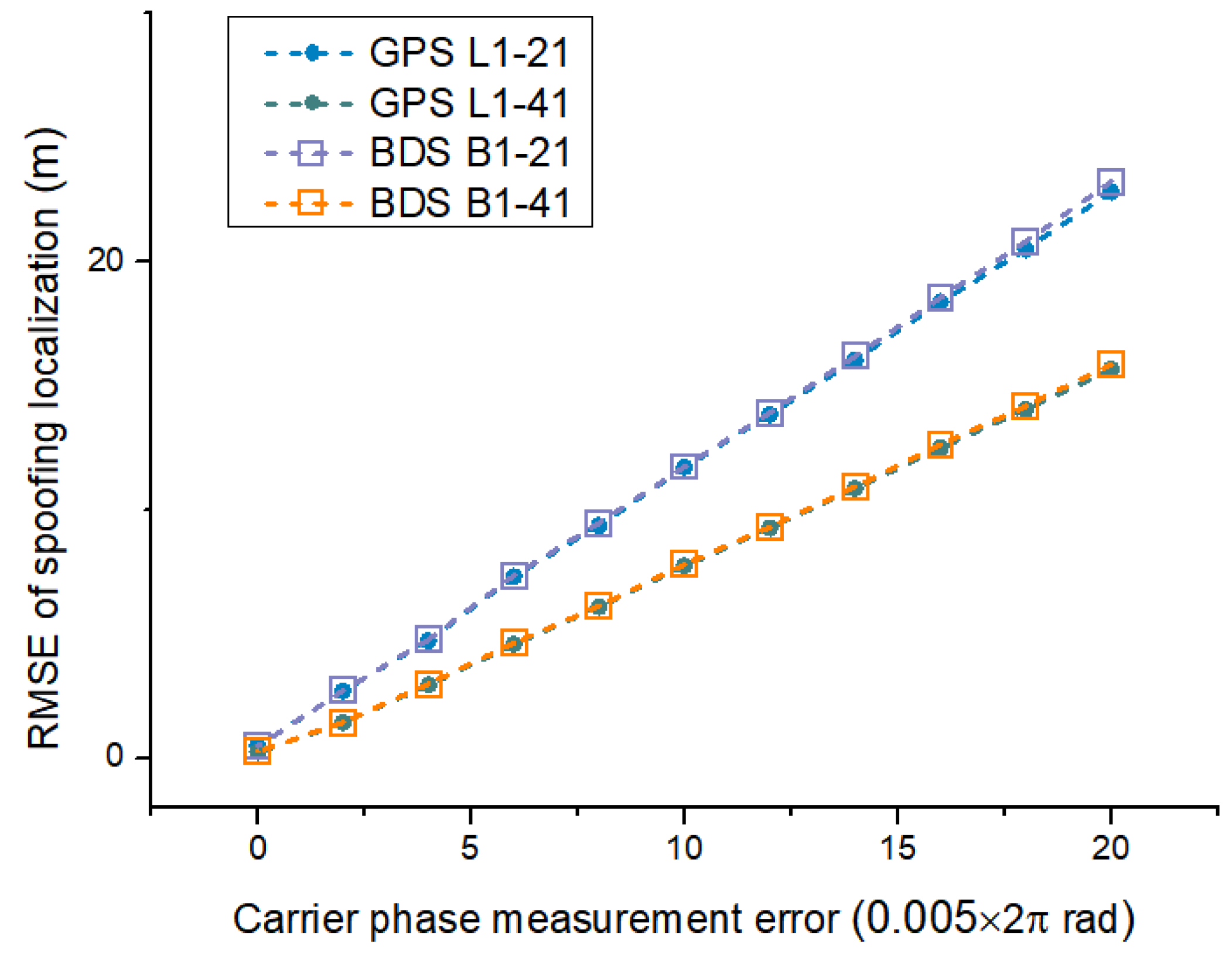
4.6. Experiment 5: Spoofing Localization Effects Considering Compatibility at Different Frequency Points
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lorraine, K.; Ramarakula, M. A Comprehensive Survey on GNSS Interferences and the Application of Neural Networks for Anti-jamming. IETE J. Res. 2021, 69, 4286–4305. [Google Scholar] [CrossRef]
- Pavlovčič-Prešeren, P.; Dimc, F.; Bažec, M. A Comparative Analysis of the Response of GNSS Receivers under Vertical and Horizontal L1/E1 Chirp Jamming. Sensors 2021, 21, 1446. [Google Scholar] [CrossRef] [PubMed]
- Liu, R.; Yang, Z.; Chen, Q.; Liao, G.; Zhen, W. GNSS multi-interference source centroid location based on clustering centroid convergence. IEEE Access 2021, 9, 108452–108465. [Google Scholar] [CrossRef]
- Truong, V.; Vervisch-Picois, A.; Rubio Hernan, J.; Samama, N. Characterization of the Ability of Low-Cost GNSS Receiver to Detect Spoofing Using Clock Bias. Sensors 2023, 23, 2735. [Google Scholar] [CrossRef] [PubMed]
- Yang, Q.; Zhang, Y.; Tang, C.K. A combined antijamming and antispoofing algorithm for GPS Arrays. Int. J. Antennas Propag. 2019, 2019, 8012569. [Google Scholar] [CrossRef]
- Wang, Y.; Hao, J.M.; Liu, W.P.; Wang, X. Dynamic evaluation of GNSS spoofing and jamming efficacy based on game theory. IEEE Access 2020, 8, 13845–13857. [Google Scholar] [CrossRef]
- Jeong, S.; Lee, J. Synthesis algorithm for effective detection of GNSS spoofing attacks. Int. J. Aeronaut. Space Sci. 2020, 21, 251–264. [Google Scholar] [CrossRef]
- Meng, L.; Yang, L.; Yang, W.; Zhang, L. A Survey of GNSS Spoofing and Anti-Spoofing Technology. Remote Sens. 2022, 14, 4826. [Google Scholar] [CrossRef]
- Wesson, K.D.; Gross, J.N.; Humphreys, T.E.; Evans, B.L. GNSS signal authentication via power and distortion monitoring. IEEE Trans. Aerosp. Electron. Syst. 2017, 54, 739–754. [Google Scholar] [CrossRef]
- Miralles, D.; Bornot, A.; Rouquette, P.; Levigne, N.; Walter, T. Assessment of GPS Spoofing Detection via Radio Power and Signal Quality Monitoring for Aviation Safety Operations. IEEE Intell. Transp. Syst. Mag. 2020, 12, 136–146. [Google Scholar] [CrossRef]
- Laverty, D.M.; Kelsey, C.; O’ Raw, J.B. GNSS time signal spoofing detector for electrical substations. IEEE Trans. Smart Grid 2021, 13, 1468–1477. [Google Scholar] [CrossRef]
- Wesson, K.D.; Rothlisberger, M.P.; Humphreys, T.E. A Proposed Navigation Message Authentication Implementation for Civil GPS Anti-Spoofing. In Proceedings of the 24th International Technical Meeting of the Satellite Division of the Institute of Navigation, Portland, OR, USA, 20–23 September 2011. [Google Scholar]
- Chen, J.; Xu, Y.; Yuan, H.; Yuan, Y. A new GNSS spoofing detection method using two antennas. IEEE Access 2020, 8, 110738–110747. [Google Scholar] [CrossRef]
- Kalantari, A.; Larsson, E.G. Statistical test for GNSS spoofing attack detection by using multiple receivers on a rigid body. EURASIP J. Adv. Signal Process. 2020, 2020, 8. [Google Scholar] [CrossRef]
- Amin, M.G.; Wang, X.; Zhang, Y.D.; Ahmad, F.; Aboutanios, E. Sparse arrays and sampling for interference mitigation and DOA estimation in GNSS. Proc. IEEE 2016, 104, 1302–1317. [Google Scholar] [CrossRef]
- Mills, K.; Ahmad, F.; Amin, M.G.; Himed, B. Fast Iterative Interpolated Beamforming for Interference DOA Estimation in GNSS Receivers Using Fully Augmentable Arrays. In Proceedings of the 2019 IEEE Radar Conference (RadarConf), Boston, MA, USA, 22–26 April 2019. [Google Scholar] [CrossRef]
- Fresno, J.M.; Robles, G.; Martínez-Tarifa, J.M.; Stewart, B.G. Survey on the Performance of Source Localization Algorithms. Sensors 2017, 17, 2666. [Google Scholar] [CrossRef] [PubMed]
- Chen, Q.D.; Tao, H.H.; Liu, R.; Zhen, W.M. Time difference estimation method for TDOA location of GNSS weak interference. J. China Acad. Electron. Inf. Technol. 2020, 15, 135–140. [Google Scholar] [CrossRef]
- Liu, R.; Yang, Z.; Chen, Q.; Liao, G.; Zhen, W. Centroid localization method of GNSS jamming source based on signal propagation correction. Syst. Eng. Electron. 2021, 43, 2083–2089. [Google Scholar] [CrossRef]
- Pavlovčič-Prešeren, P.; Dimc, F.; Bažec, M. Exploiting the Sensitivity of Dual-Frequency Smartphones and GNSS Geodetic Receivers for Jammer Localization. Remote Sens. 2023, 15, 1157. [Google Scholar] [CrossRef]
- Shang, S.; Li, H.; Peng, C.; Lu, M. A novel method for GNSS meaconer localization based on a space–time double-difference model. IEEE Trans. Aerosp. Electron. Syst. 2020, 56, 3432–3449. [Google Scholar] [CrossRef]
- Bhamidipati, S.; Gao, G.X. GPS multireceiver joint direct time estimation and spoofer localization. IEEE Trans. Aerosp. Electron. Syst. 2018, 55, 1907–1919. [Google Scholar] [CrossRef]
- Yin, J.; Wang, D.; Wu, Y. An Efficient Direct Position Determination Method for Multiple Strictly Noncircular Sources. Sensors 2018, 18, 324. [Google Scholar] [CrossRef] [PubMed]
- Weiss, A.J.; Amar, A. Direct position determination of multiple radio signals. EURASIP J. Appl. Signal Process. 2005, 1, 653549. [Google Scholar] [CrossRef]
- Li, J.; Yang, L.; Guo, F. Coherent summation of multiple short-time signals for direct positioning of a wideband source based on delay and Doppler. Digit. Signal Process. 2016, 48, 58–70. [Google Scholar] [CrossRef]
- Xu, H.; Cui, X.; Lu, M. An SDR-Based Real-Time Testbed for GNSS Adaptive Array Anti-Jamming Algorithms Accelerated by GPU. Sensors 2016, 16, 356. [Google Scholar] [CrossRef] [PubMed]
- Caizzone, S.; Elmarissi, W.; Buchner, G.; Sgammini, M. Compact 6+ 1 antenna array for robust GNSS applications. In Proceedings of the 2016 International Conference on Localization and GNSS (ICL-GNSS), Barcelona, Spain, 28–30 June 2016. [Google Scholar] [CrossRef]
- Zeng, Q.; Qiu, W.; Zhang, P.; Zhu, X.; Pei, L. A Fast acquisition algorithm based on division of GNSS signals. J. Navig. 2018, 71, 933–954. [Google Scholar] [CrossRef]
- Borio, D. GNSS Data/Pilot Combining with Extended Integrations for Carrier Tracking. Sensors 2023, 23, 3932. [Google Scholar] [CrossRef]
- Zhao, H.; Lian, B.; Feng, J. Adaptive beamforming and phase bias compensation for GNSS receiver. J. Syst. Eng. Electron. 2015, 26, 10–18. [Google Scholar] [CrossRef]
- Zhao, L.; Blunt, P.; Yang, L.; Ince, S. Performance Analysis of Real-Time GPS/Galileo Precise Point Positioning Integrated with Inertial Navigation System. Sensors 2023, 23, 2396. [Google Scholar] [CrossRef]
- Cui, J.H.; Cheng, N.P.; Ni, S.Y. Research on spoofing suppressing method using antenna array for navigation signal. ACTA Electonica Sin. 2018, 46, 365. [Google Scholar] [CrossRef]
- Roberts, G.W. Noise comparison of triple frequency GNSS carrier phase, doppler and pseudorange observables. Measurement 2019, 144, 328–344. [Google Scholar] [CrossRef]
- China Satellite Navigation Office (CSNO). Beidou/Global Navigation Satellite System (GNSS) Measurement Receiver Observation Data Quality Evaluation Method. Available online: http://www.beidou.gov.cn/yw/gfgg/201712/W020171225739347636713.pdf (accessed on 12 November 2023).
- Retscher, G.; Kiss, D.; Gabela, J. Fusion of GNSS Pseudoranges with UWB Ranges Based on Clustering and Weighted Least Squares. Sensors 2023, 23, 3303. [Google Scholar] [CrossRef] [PubMed]
- Liu, Z.; Hu, D.; Zhao, Y.; Zhao, Y. An algebraic method for moving source localization using TDOA, FDOA, and differential Doppler rate measurements with receiver location errors. EURASIP J. Adv. Signal Process. 2019, 2019, 25. [Google Scholar] [CrossRef]
- Li, J.; Lv, S.; Jin, Y.; Wang, C.; Liu, Y.; Liao, S. Geolocation and Tracking by TDOA Measurements Based on Space–Air–Ground Integrated Network. Remote Sens. 2023, 15, 44. [Google Scholar] [CrossRef]
- Magiera, J.; Katulski, R. Detection and mitigation of GPS spoofing based on antenna array processing. J. Appl. Res. Technol. 2015, 13, 45–57. [Google Scholar] [CrossRef]
- Mir, H.S.; Sahr, J.D.; Hatke, G.F.; Keller, C.M. Passive source localization using an airborne sensor array in the presence of manifold perturbations. IEEE Trans. Signal Process. 2007, 55, 2486–2496. [Google Scholar] [CrossRef]
- Kaplan, E.; Hegarty, C. Understanding GPS Principles and Applications, 2nd ed.; British Library Cataloguing in Publication Data; Artech House: Boston, MA, USA, 2006; pp. 1–723. [Google Scholar]
- Yang, R.; Ling, K.-V.; Poh, E.-K.; Morton, Y. Generalized GNSS Signal Carrier Tracking: Part I—Modeling and Analysis. IEEE Trans. Aerosp. Electron. Syst. 2017, 53, 1781–1797. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, R.; Yang, Z.; Chen, Q.; Liao, G.; Zhu, Q. Localization of GNSS Spoofing Interference Source Based on a Moving Array Antenna. Remote Sens. 2023, 15, 5497. https://doi.org/10.3390/rs15235497
Liu R, Yang Z, Chen Q, Liao G, Zhu Q. Localization of GNSS Spoofing Interference Source Based on a Moving Array Antenna. Remote Sensing. 2023; 15(23):5497. https://doi.org/10.3390/rs15235497
Chicago/Turabian StyleLiu, Rui, Zhiwei Yang, Qidong Chen, Guisheng Liao, and Qinglin Zhu. 2023. "Localization of GNSS Spoofing Interference Source Based on a Moving Array Antenna" Remote Sensing 15, no. 23: 5497. https://doi.org/10.3390/rs15235497
APA StyleLiu, R., Yang, Z., Chen, Q., Liao, G., & Zhu, Q. (2023). Localization of GNSS Spoofing Interference Source Based on a Moving Array Antenna. Remote Sensing, 15(23), 5497. https://doi.org/10.3390/rs15235497







