Knowledge Mapping with CiteSpace, VOSviewer, and SciMAT on Intelligent Connected Vehicles: Road Safety Issue
Abstract
1. Introduction
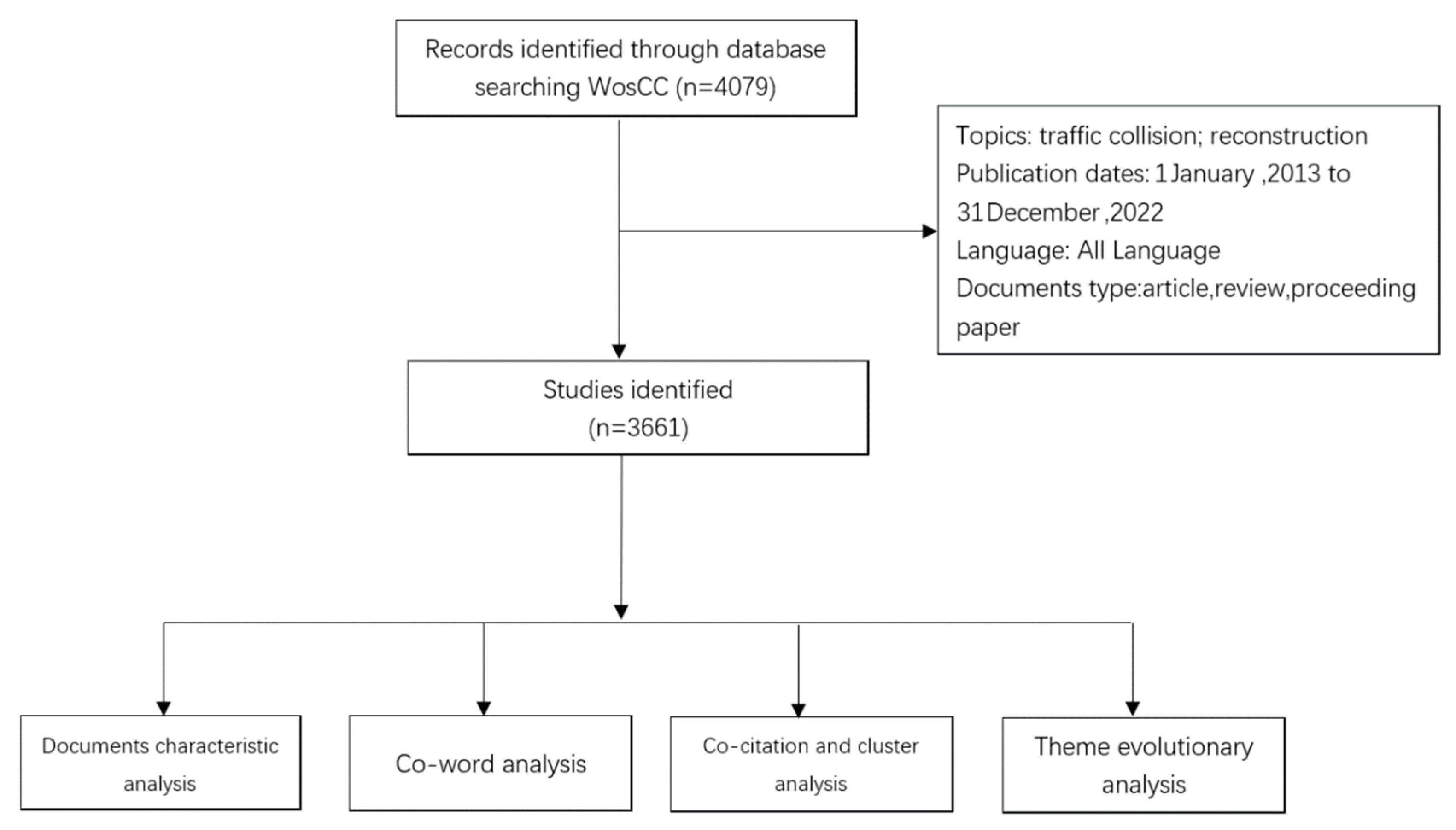
2. Materials and Methods
2.1. Data Resource and Search Strategy
2.2. Bibliometric Analysis
2.2.1. Document Characteristic Analysis
2.2.2. Co-Word Analysis
2.2.3. Co-Citation and Cluster Analysis
2.2.4. Theme Evolution Analysis
3. Results
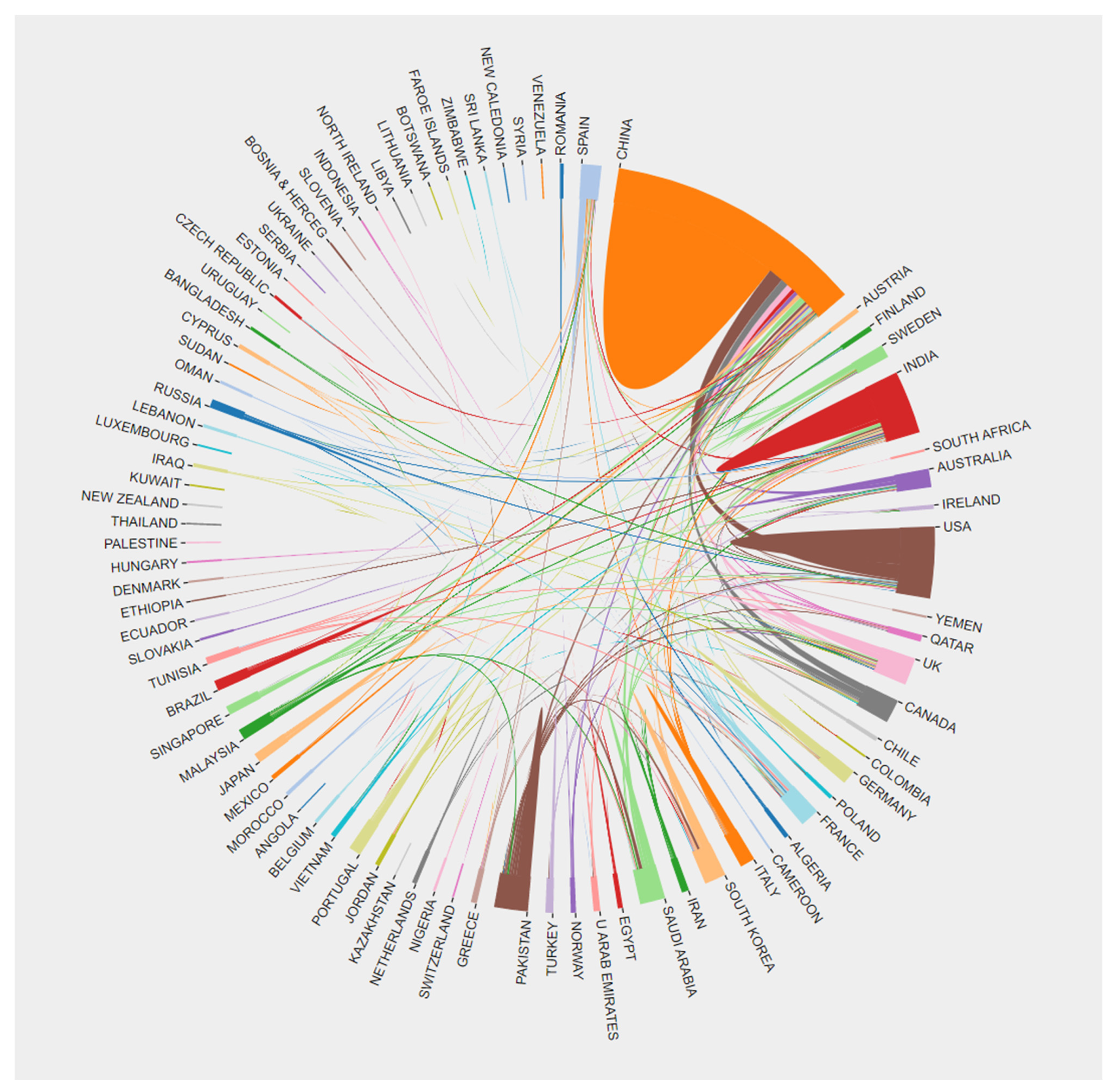
3.1. Documents Characteristic Analysis
3.1.1. Number of Publications
3.1.2. Networks
3.1.3. Dual-Map Overlay of Journals
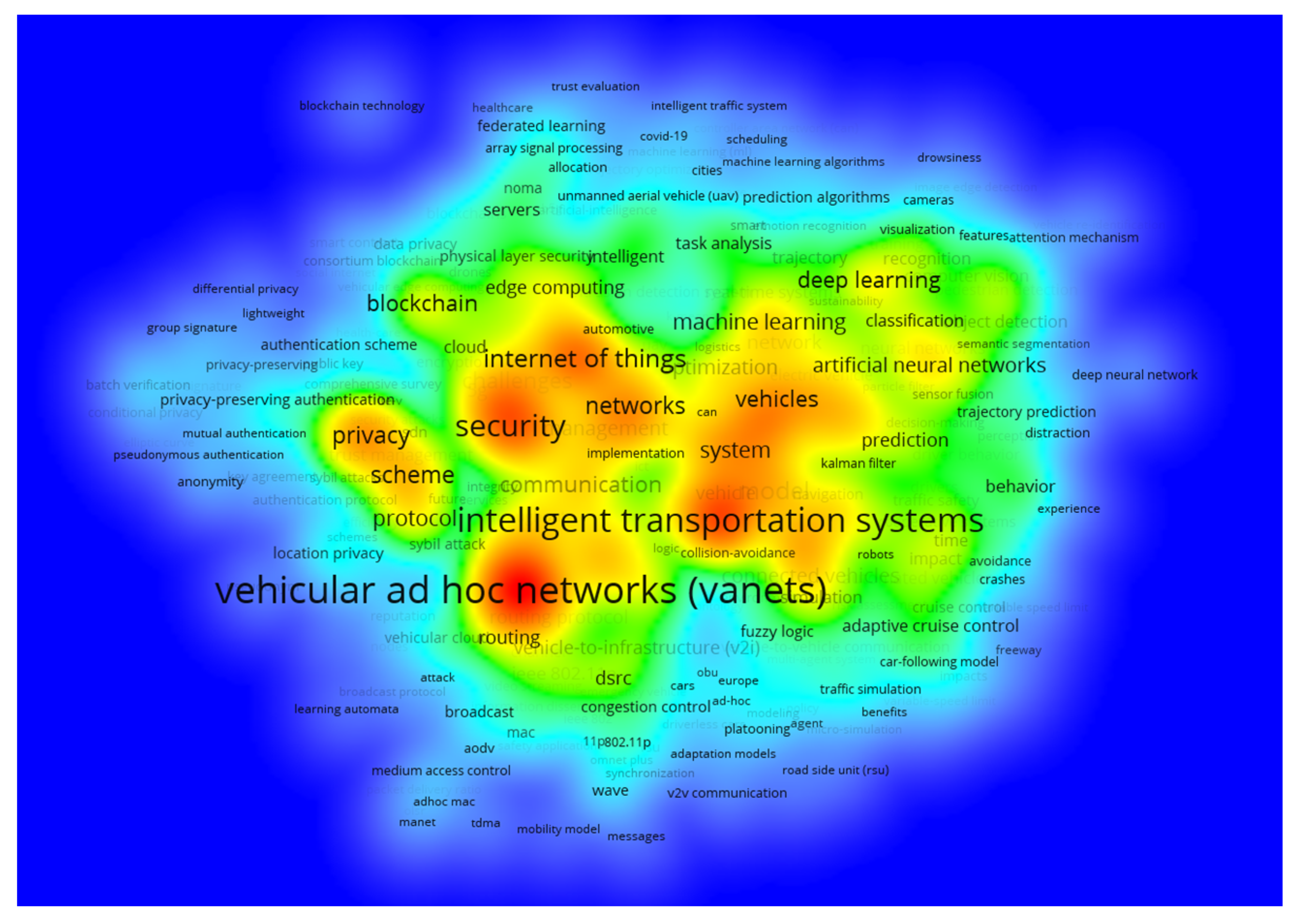
3.2. Co-Word Analysis
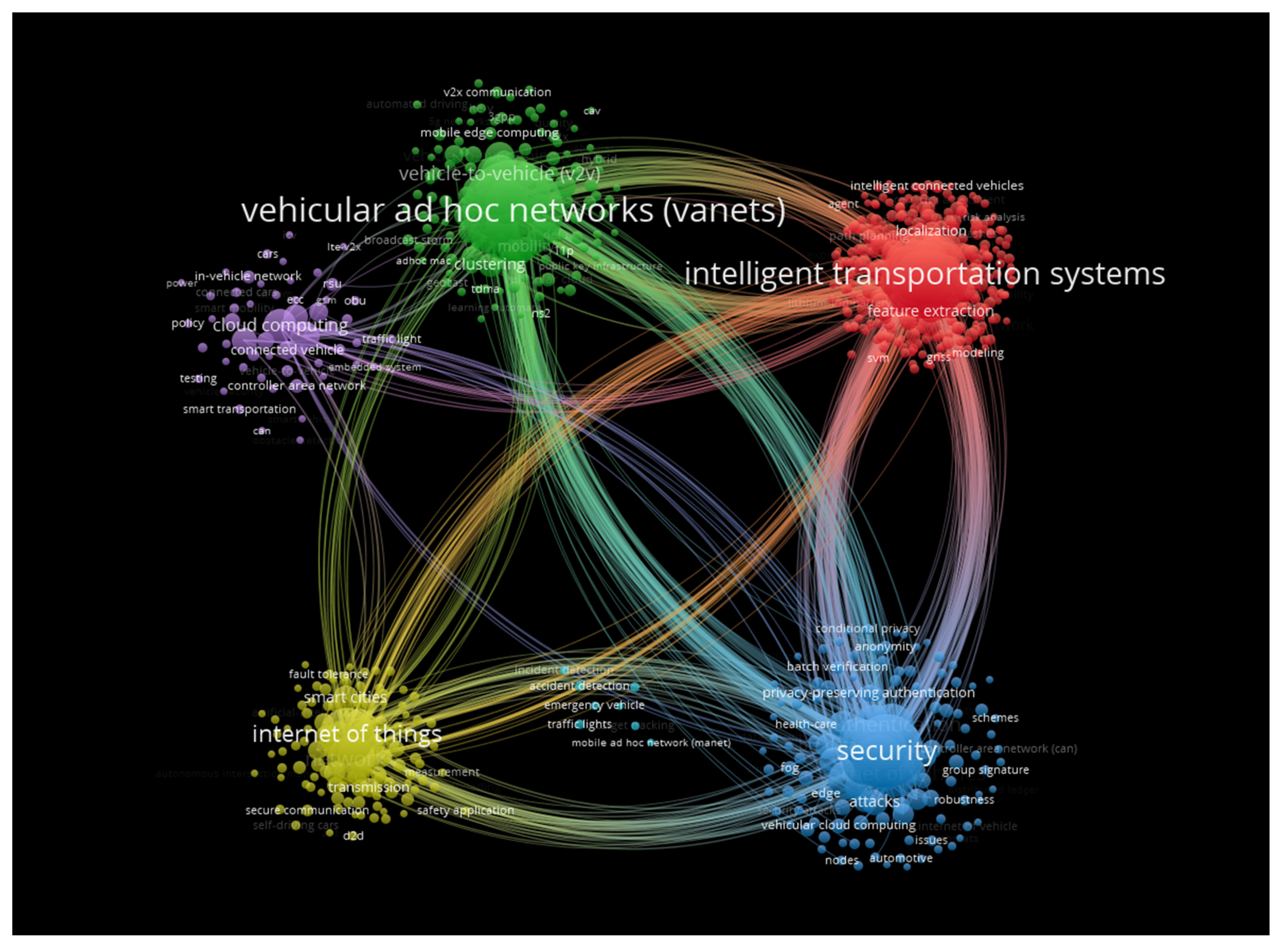
3.3. Co-Citation and Cluster Analysis
3.3.1. Citing Articles and Cited References
- Cluster#0 VEHICULAR CLOUD COMPUTING
- Cluster#1 TRUST MANAGEMENT
- Cluster#2 LEARNING-BASED RESOURCE ALLOCATION
- Cluster#3 INTRUSION DETECTION SYSTEM
- Cluster#4 VANET SYSTEM
3.3.2. Citation Bursts
3.3.3. Betweenness Centrality
3.4. Theme Evolutionary Analysis
3.4.1. Thematic Overlapping
3.4.2. Thematic Evolution
3.4.3. Strategic Coordinate Diagram
4. Discussion
4.1. Documents Characteristic Analysis
4.2. Co-Word Analysis
4.3. Co-Citation and Cluster Analysis
4.3.1. Overview of Clusters
- Research Base
- Research Frontier
- Research Base
- Research Frontier
- Research Base
- Research Frontier
- Research Base
- Research Frontier
- Research Base
- Research Frontier
4.3.2. Citation Burst & Centrality Betweenness Analysis
4.4. Theme Evolutionary Analysis
4.5. Research Strengths and Limitations
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- World Health Organization. Global Plan for the Decade of Action for Road Safety 2021–2030. Available online: https://www.who.int/publications/m/item/global-plan-for-the-decade-of-action-for-road-safety-2021-2030 (accessed on 13 January 2023).
- Liu, J.; Liu, J. Intelligent and Connected Vehicles: Current Situation, Future Directions, and Challenges. IEEE Commun. Stand. Mag. 2018, 2, 59–65. [Google Scholar] [CrossRef]
- Talebpour, A.; Mahmassani, H.S. Influence of Connected and Autonomous Vehicles on Traffic Flow Stability and Throughput. Transp. Res. Part C Emerg. Technol. 2016, 71, 143–163. [Google Scholar] [CrossRef]
- Guan, T.; Han, Y.; Kang, N.; Tang, N.; Chen, X.; Wang, S. An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles. Sustainability 2022, 14, 5211. [Google Scholar] [CrossRef]
- Dibaei, M.; Zheng, X.; Jiang, K.; Abbas, R.; Liu, S.; Zhang, Y.; Xiang, Y.; Yu, S. Attacks and Defences on Intelligent Connected Vehicles: A Survey. Digit. Commun. Netw. 2020, 6, 399–421. [Google Scholar] [CrossRef]
- Golestan, K.; Soua, R.; Karray, F.; Kamel, M.S. Situation Awareness within the Context of Connected Cars: A Comprehensive Review and Recent Trends. Inf. Fusion 2016, 29, 68–83. [Google Scholar] [CrossRef]
- Shevchenko, O. Intelligent Connected Mobility 4.0: Regulatory Concepts. Maastricht J. Eur. Comp. Law 2022, 29, 85–99. [Google Scholar] [CrossRef]
- Chen, C. Searching for Intellectual Turning Points: Progressive Knowledge Domain Visualization. Proc. Natl. Acad. Sci. USA 2004, 101, 5303–5310. [Google Scholar] [CrossRef]
- Al-Sultan, S.; Al-Doori, M.M.; Al-Bayatti, A.H.; Zedan, H. A Comprehensive Survey on Vehicular Ad Hoc Network. J. Netw. Comput. Appl. 2014, 37, 380–392. [Google Scholar] [CrossRef]
- Whaiduzzaman, M.; Sookhak, M.; Gani, A.; Buyya, R. A Survey on Vehicular Cloud Computing. J. Netw. Comput. Appl. 2014, 40, 325–344. [Google Scholar] [CrossRef]
- Mejri, M.N.; Ben-Othman, J.; Hamdi, M. Survey on VANET Security Challenges and Possible Cryptographic Solutions. Veh. Commun. 2014, 1, 53–66. [Google Scholar] [CrossRef]
- Zeadally, S.; Hunt, R.; Chen, Y.-S.; Irwin, A.; Hassan, A. Vehicular Ad Hoc Networks (VANETS): Status, Results, and Challenges. Telecommun. Syst. 2010, 50, 217–241. [Google Scholar] [CrossRef]
- Engoulou, R.G.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET Security Surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Ilarri, S.; Hermoso, R.; Trillo-Lado, R.; Rodríguez-Hernández, M.D.C. A Review of the Role of Sensors in Mobile Context-Aware Recommendation Systems. Int. J. Distrib. Sens. Netw. 2015, 11, 489264. [Google Scholar] [CrossRef]
- Saini, M.; Alelaiwi, A.; Saddik, A.E. How Close Are We to Realizing a Pragmatic VANET Solution? A Meta-Survey. ACM Comput. Surv. 2015, 48, 1–40. [Google Scholar] [CrossRef]
- Zekri, A.; Jia, W. Heterogeneous Vehicular Communications: A Comprehensive Study. Ad Hoc Netw. 2018, 75–76, 52–79. [Google Scholar] [CrossRef]
- Zheng, K.; Zheng, Q.; Chatzimisios, P.; Xiang, W.; Zhou, Y. Heterogeneous Vehicular Networking: A Survey on Architecture, Challenges, and Solutions. IEEE Commun. Surv. Tutor. 2015, 17, 2377–2396. [Google Scholar] [CrossRef]
- MacHardy, Z.; Khan, A.; Obana, K.; Iwashina, S. V2X Access Technologies: Regulation, Research, and Remaining Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 1858–1877. [Google Scholar] [CrossRef]
- Ilarri, S.; Delot, T.; Trillo-Lado, R. A data management perspective on vehicular networks. IEEE Commun. Surv. Tutor. 2015, 17, 2420–2460. [Google Scholar] [CrossRef]
- Yang, Y.; Hua, K. Emerging Technologies for 5G-Enabled Vehicular Networks. IEEE Access 2019, 7, 181117–181141. [Google Scholar] [CrossRef]
- Dorri, A.; Steger, M.; Kanhere, S.S.; Jurdak, R. BlockChain: A Distributed Solution to Automotive Security and Privacy. IEEE Commun. Mag. 2017, 55, 119–125. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for Secure and Efficient Data Sharing in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2019, 6, 4660–4670. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Ye, D.; Kim, D.I.; Zhao, J. Toward Secure Blockchain-Enabled Internet of Vehicles: Optimizing Consensus Management Using Reputation and Contract Theory. IEEE Trans. Veh. Technol. 2019, 68, 2906–2920. [Google Scholar] [CrossRef]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- Mikavica, B.; Kostić-Ljubisavljević, A. Blockchain-Based Solutions for Security, Privacy, and Trust Management in Vehicular Networks: A Survey. J. Supercomput. 2021, 77, 9520–9575. [Google Scholar] [CrossRef]
- Abbas, S.; Talib, M.A.; Ahmed, A.; Khan, F.; Ahmad, S.; Kim, D.-H. Blockchain-Based Authentication in Internet of Vehicles: A Survey. Sensors 2021, 21, 7927. [Google Scholar] [CrossRef]
- Jabbar, R.; Dhib, E.; Said, A.B.; Krichen, M.; Fetais, N.; Zaidan, E.; Barkaoui, K. Blockchain Technology for Intelligent Transportation Systems: A Systematic Literature Review. IEEE Access 2022, 10, 20995–21031. [Google Scholar] [CrossRef]
- Jan, S.A.; Amin, N.U.; Othman, M.; Ali, M.; Umar, A.I.; Basir, A. A Survey on Privacy-Preserving Authentication Schemes in VANETs: Attacks, Challenges and Open Issues. IEEE Access 2021, 9, 153701–153726. [Google Scholar] [CrossRef]
- Silva, L.; Magaia, N.; Sousa, B.; Kobusinska, A.; Casimiro, A.; Mavromoustakis, C.X.; Mastorakis, G.; de Albuquerque, V.H.C. Computing Paradigms in Emerging Vehicular Environments: A Review. IEEE/CAA J. Autom. Sin. 2021, 8, 491–511. [Google Scholar] [CrossRef]
- Tang, F.; Kawamoto, Y.; Kato, N.; Liu, J. Future Intelligent and Secure Vehicular Network toward 6G: Machine-Learning Approaches. Proc. IEEE 2020, 108, 292–307. [Google Scholar] [CrossRef]
- He, Y.; Zhao, N.; Yin, H. Integrated Networking, Caching, and Computing for Connected Vehicles: A Deep Reinforcement Learning Approach. IEEE Trans. Veh. Technol. 2018, 67, 44–55. [Google Scholar] [CrossRef]
- Molina-Masegosa, R.; Gozalvez, J. LTE-V for Sidelink 5G V2X Vehicular Communications: A New 5G Technology for Short-Range Vehicle-To-Everything Communications. IEEE Veh. Technol. Mag. 2017, 12, 30–39. [Google Scholar] [CrossRef]
- Naik, G.; Choudhury, B.; Park, J.-M. IEEE 802.11bd & 5G NR V2X: Evolution of Radio Access Technologies for V2X Communications. IEEE Access 2019, 7, 70169–70184. [Google Scholar] [CrossRef]
- Lamssaggad, A.; Benamar, N.; Hafid, A.S.; Msahli, M. A Survey on the Current Security Landscape of Intelligent Transportation Systems. IEEE Access 2021, 9, 9180–9208. [Google Scholar] [CrossRef]
- Tang, F.; Mao, B.; Kato, N.; Gui, G. Comprehensive Survey on Machine Learning in Vehicular Network: Technology, Applications and Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 2027–2057. [Google Scholar] [CrossRef]
- Bangui, H.; Ge, M.; Buhnova, B. A Hybrid Machine Learning Model for Intrusion Detection in VANET. Computing 2021, 104, 503–531. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet Security Challenges and Solutions: A Survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Sakiz, F.; Sen, S. A Survey of Attacks and Detection Mechanisms on Intelligent Transportation Systems: VANETs and IoV. Ad Hoc Netw. 2017, 61, 33–50. [Google Scholar] [CrossRef]
- Cunha, F.; Villas, L.; Boukerche, A.; Maia, G.; Viana, A.; Mini, R.A.F.; Loureiro, A.A. F. Data Communication in VANETs: Protocols, Applications and Challenges. Ad Hoc Netw. 2016, 44, 90–103. [Google Scholar] [CrossRef]
- Manvi, S.S.; Tangade, S. A Survey on Authentication Schemes in VANETs for Secured Communication. Veh. Commun. 2017, 9, 19–30. [Google Scholar] [CrossRef]
- Li, W.; Song, H. ART: An Attack-Resistant Trust Management Scheme for Securing Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2016, 17, 960–969. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Zhou, M.; Hu, X.; Wang, L.; Zhang, Y.; Yu, F.R.; Hu, B. Privacy-Preserving Content Dissemination for Vehicular Social Networks: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2019, 21, 1314–1345. [Google Scholar] [CrossRef]
- Sharma, S.; Kaushik, B. A Survey on Internet of Vehicles: Applications, Security Issues & Solutions. Veh. Commun. 2019, 20, 100182. [Google Scholar] [CrossRef]
- Hussain, R.; Hussain, F.; Zeadally, S. Integration of VANET and 5G Security: A Review of Design and Implementation Issues. Future Gener. Comput. Syst. 2019, 101, 843–864. [Google Scholar] [CrossRef]
- Sommer, C.; German, R.; Dressler, F. Bidirectionally Coupled Network and Road Traffic Simulation for Improved IVC Analysis. IEEE Trans. Mob. Comput. 2011, 10, 3–15. [Google Scholar] [CrossRef]
- Behrisch, M.; Bieker, L.; Erdmann, J.; Krajzewicz, D. SUMO-Simulation of Urban Mobility. In Proceedings of the SIMUL 2011: The 3rd International Conference on Advances in System Simulation, Barcelona, Spain, 23 October 2011. [Google Scholar]
- Gozalvez, J.; Sepulcre, M.; Bauza, R. IEEE 802.11p Vehicle to Infrastructure Communications in Urban Environments. IEEE Commun. Mag. 2012, 50, 176–183. [Google Scholar] [CrossRef]
- Hartenstein, H.; Laberteaux, K.P. A Tutorial Survey on Vehicular Ad Hoc Networks. IEEE Commun. Mag. 2008, 46, 164–171. [Google Scholar] [CrossRef]
- Tonguz, O.; Wisitpongphan, N.; Bai, F. DV-CAST: A Distributed Vehicular Broadcast Protocol for Vehicular Ad Hoc Networks. IEEE Wirel. Commun. 2010, 17, 47–57. [Google Scholar] [CrossRef]
- Alsabaan, M.; Alasmary, W.; Albasir, A.; Naik, K. Vehicular Networks for a Greener Environment: A Survey. IEEE Commun. Surv. Tutor. 2013, 15, 1372–1388. [Google Scholar] [CrossRef]
- Stanica, R.; Chaput, E.; Beylot, A.-L. Reverse Back-off Mechanism for Safety Vehicular Ad Hoc Networks. Ad Hoc. Netw. 2014, 16, 210–224. [Google Scholar] [CrossRef]
- Joerer, S.; Segata, M.; Bloessl, B.; Lo Cigno, R.; Sommer, C.; Dressler, F. A Vehicular Networking Perspective on Estimating Vehicle Collision Probability at Intersections. IEEE Trans. Veh. Technol. 2014, 63, 1802–1812. [Google Scholar] [CrossRef]
- Santa, J.; Pereñíguez, F.; Cano, J.C.; Skarmeta, A.F.; Calafate, C.T.; Manzoni, P. Comprehensive Vehicular Networking Platform for V2I and V2V Communications within the Walkie-Talkie Project. Int. J. Distrib. Sens. Netw. 2013, 9, 676850. [Google Scholar] [CrossRef]
- Ghosh, A.; Paranthaman, V.V.; Mapp, G.; Gemikonakli, O. Exploring Efficient Seamless Handover in VANET Systems Using Network Dwell Time. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 227. [Google Scholar] [CrossRef]
- Karagiannis, G.; Altintas, O.; Ekici, E.; Heijenk, G.; Jarupan, B.; Lin, K.; Weil, T. Vehicular Networking: A Survey and Tutorial on Requirements, Architectures, Challenges, Standards and Solutions. IEEE Commun. Surv. Tutor. 2011, 13, 584–616. [Google Scholar] [CrossRef]
- Kenney, J.B. Dedicated Short-Range Communications (DSRC) Standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Lu, N.; Cheng, N.; Zhang, N.; Shen, X.; Mark, J.W. Connected Vehicles: Solutions and Challenges. IEEE Internet Things J. 2014, 1, 289–299. [Google Scholar] [CrossRef]
- Sharef, B.T.; Alsaqour, R.A.; Ismail, M. Vehicular Communication Ad Hoc Routing Protocols: A Survey. J. Netw. Comput. Appl. 2014, 40, 363–396. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Ren, S.; He, K.; Girshick, R.; Sun, J. Faster R-CNN: Towards Real-Time Object Detection with Region Proposal Networks. IEEE Trans. Pattern Anal. Mach. Intell. 2017, 39, 1137–1149. [Google Scholar] [CrossRef]
- Shen, Z.; Ji, W.; Yu, S.; Cheng, G.; Yuan, Q.; Han, Z.; Liu, H.; Yang, T. Mapping the Knowledge of Traffic Collision Reconstruction: A Scientometric Analysis in CiteSpace, VOSviewer, and SciMAT. Sci. Justice 2023, 63, 19–37. [Google Scholar] [CrossRef]
- Cobo, M.J.; López-Herrera, A.G.; Herrera-Viedma, E.; Herrera, F. SciMAT: A New Science Mapping Analysis Software Tool. J. Am. Soc. Inf. Sci. Technol. 2012, 63, 1609–1630. [Google Scholar] [CrossRef]
- Araniti, G.; Campolo, C.; Condoluci, M.; Iera, A.; Molinaro, A. LTE for Vehicular Networking: A Survey. IEEE Commun. Mag. 2013, 51, 148–157. [Google Scholar] [CrossRef]
- Singh, P.K.; Nandi, S.K.; Nandi, S. A Tutorial Survey on Vehicular Communication State of the Art, and Future Research Directions. Veh. Commun. 2019, 18, 100164. [Google Scholar] [CrossRef]
- Ali, Q.; Ahmad, N.; Malik, A.; Ali, G.; Rehman, W. Issues, Challenges, and Research Opportunities in Intelligent Transport System for Security and Privacy. Appl. Sci. 2018, 8, 1964. [Google Scholar] [CrossRef]
- Gupta, N.; Prakash, A.; Tripathi, R. Medium Access Control Protocols for Safety Applications in Vehicular Ad-Hoc Network: A Classification and Comprehensive Survey. Veh. Commun. 2015, 2, 223–237. [Google Scholar] [CrossRef]
- Ekedebe, J.; Yu, W.; Song, H.; Lu, C. On a Simulation Study of Cyber Attacks on Vehicle-To-Infrastructure Communication (V2I) in Intelligent Transportation System (ITS). In Proceedings of the Society of Photo-Optical Instrumentation Engineers (SPIE) 9497, Mobile Multimedia/Image Processing, Security, and Applications 2015, Baltimore, MD, USA, 21 May 2015. [Google Scholar]
- Sharma, S.; Kaul, A. A Survey on Intrusion Detection Systems and Honeypot Based Proactive Security Mechanisms in VANETs and VANET Cloud. Veh. Commun. 2018, 12, 138–164. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Shen, X. SPARK: A New VANET-Based Smart Parking Scheme for Large Parking Lots. In Proceedings of the IEEE INFOCOM 2009—The 28th Conference on Computer Communications 2009, Rio de Janeiro, Brazil, 19–25 April 2009. [Google Scholar] [CrossRef]
- Li, L.; Liu, J.; Cheng, L.; Qiu, S.; Wang, W.; Zhang, X.; Zhang, Z. CreditCoin: A Privacy-Preserving Blockchain-Based Incentive Announcement Network for Communications of Smart Vehicles. IEEE Trans. Intell. Transp. Syst. 2018, 19, 2204–2220. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C.M. Blockchain-Based Decentralized Trust Management in Vehicular Networks. IEEE Internet Things J. 2019, 6, 1495–1505. [Google Scholar] [CrossRef]
- Azam, F.; Yadav, S.K.; Priyadarshi, N.; Padmanaban, S.; Bansal, R.C. A Comprehensive Review of Authentication Schemes in Vehicular Ad-Hoc Network. IEEE Access 2021, 9, 31309–31321. [Google Scholar] [CrossRef]
- Grover, J. Security of Vehicular Ad Hoc Networks Using Blockchain: A Comprehensive Review. Veh. Commun. 2022, 34, 100458. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zhao, J.; Niyato, D.; Guan, Y.L.; Yuen, C.; Sun, S.; Lam, K.-Y.; Koh, L.H. Blockchain for the Internet of Vehicles towards Intelligent Transportation Systems: A Survey. IEEE Internet Things J. 2021, 8, 4157–4185. [Google Scholar] [CrossRef]
- Cui, J.; Ouyang, F.; Ying, Z.; Wei, L.; Zhong, H. Secure and Efficient Data Sharing among Vehicles Based on Consortium Blockchain. IEEE Trans. Intell. Transp. Syst. 2022, 23, 8857–8867. [Google Scholar] [CrossRef]
- Firdaus, M.; Rhee, K.-H. On Blockchain-Enhanced Secure Data Storage and Sharing in Vehicular Edge Computing Networks. Appl. Sci. 2021, 11, 414. [Google Scholar] [CrossRef]
- Chen, S.; Hu, J.; Shi, Y.; Peng, Y.; Fang, J.; Zhao, R.; Zhao, L. Vehicle-To-Everything (V2x) Services Supported by LTE-Based Systems and 5G. IEEE Commun. Stand. Mag. 2017, 1, 70–76. [Google Scholar] [CrossRef]
- Zhou, H.; Xu, W.; Chen, J.; Wang, W. Evolutionary V2X Technologies toward the Internet of Vehicles: Challenges and Opportunities. Proc. IEEE 2020, 108, 308–323. [Google Scholar] [CrossRef]
- Noor-A-Rahim, M.; Liu, Z.; Lee, H.; Khyam, M.O.; He, J.; Pesch, D.; Moessner, K.; Saad, W.; Poor, H.V. 6G for Vehicle-To-Everything (V2X) Communications: Enabling Technologies, Challenges, and Opportunities. Proc. IEEE 2022, 110, 712–734. [Google Scholar] [CrossRef]
- Alalewi, A.; Dayoub, I.; Cherkaoui, S. On 5G-V2X Use Cases and Enabling Technologies: A Comprehensive Survey. IEEE Access 2021, 9, 107710–107737. [Google Scholar] [CrossRef]
- Tan, K.; Bremner, D.; Le Kernec, J.; Zhang, L.; Imran, M. Machine Learning in Vehicular Networking: An Overview. Digit. Commun. Netw. 2022, 8, 18–24. [Google Scholar] [CrossRef]
- Bazzi, A.; Berthet, A.O.; Campolo, C.; Masini, B.M.; Molinaro, A.; Zanella, A. On the Design of Sidelink for Cellular V2X: A Literature Review and Outlook for Future. IEEE Access 2021, 9, 97953–97980. [Google Scholar] [CrossRef]
- Amoozadeh, M.; Raghuramu, A.; Chuah, C.; Ghosal, D.; Zhang, H.M.; Rowe, J.; Levitt, K. Security Vulnerabilities of Connected Vehicle Streams and Their Impact on Cooperative Driving. IEEE Commun. Mag. 2015, 53, 126–132. [Google Scholar] [CrossRef]
- Menouar, H.; Guvenc, I.; Akkaya, K.; Uluagac, A.S.; Kadri, A.; Tuncer, A. UAV-Enabled Intelligent Transportation Systems for the Smart City: Applications and Challenges. IEEE Commun. Mag. 2017, 55, 22–28. [Google Scholar] [CrossRef]
- Ali, I.; Hassan, A.; Li, F. Authentication and Privacy Schemes for Vehicular Ad Hoc Networks (VANETs): A Survey. Veh. Commun. 2019, 16, 45–61. [Google Scholar] [CrossRef]
- Bhatia, J.; Modi, Y.; Tanwar, S.; Bhavsar, M. Software Defined Vehicular Networks: A Comprehensive Review. Int. J. Commun. Syst. 2019, 32, e4005. [Google Scholar] [CrossRef]
- Chowdhury, A.; Karmakar, G.; Kamruzzaman, J.; Jolfaei, A.; Das, R. Attacks on Self-Driving Cars and Their Countermeasures: A Survey. IEEE Access 2020, 8, 207308–207342. [Google Scholar] [CrossRef]
- Fogue, M.; Garrido, P.; Martinez, F.J.; Cano, J.-C.; Calafate, C.T.; Manzoni, P. Evaluating the Impact of a Novel Message Dissemination Scheme for Vehicular Networks Using Real Maps. Transp. Res. Part C Emerg. Technol. 2012, 25, 61–80. [Google Scholar] [CrossRef]
- Harri, J.; Filali, F.; Bonnet, C. Mobility Models for Vehicular Ad Hoc Networks: A Survey and Taxonomy. IEEE Commun. Surv. Tutor. 2009, 11, 19–41. [Google Scholar] [CrossRef]
- Uzcategui, R.A.; De Sucre, A.J.; Acosta-Marum, G. Wave: A Tutorial. IEEE Commun. Mag. 2009, 47, 126–133. [Google Scholar] [CrossRef]
- Sou, S.-I. Modeling Emergency Messaging for Car Accident over Dichotomized Headway Model in Vehicular Ad-Hoc Networks. IEEE Trans. Commun. 2013, 61, 802–812. [Google Scholar] [CrossRef]
- Santa, J.; Pereñíguez, F.; Moragón, A.; Skarmeta, A.F. Experimental Evaluation of CAM and DENM Messaging Services in Vehicular Communications. Transp. Res. Part C Emerg. Technol. 2014, 46, 98–120. [Google Scholar] [CrossRef]
- Wang, B.; Han, Y.; Wang, S.; Tian, D.; Cai, M.; Liu, M.; Wang, L. A Review of Intelligent Connected Vehicle Cooperative Driving Development. Mathematics 2022, 10, 3635. [Google Scholar] [CrossRef]
- Khan, S.K.; Shiwakoti, N.; Stasinopoulos, P.; Chen, Y. Cyber-attacks in the next-generation cars, mitigation techniques, anticipated readiness and future directions. Accid. Anal. Prev. 2020, 148, 105837. [Google Scholar] [CrossRef]
- Huang, X.; He, P.; Rangarajan, A.; Ranka, S. Intelligent intersection: Two-stream convolutional networks for real-time near-accident detection in traffic video. ACM Trans. Spat. Algorithms Syst. 2020, 6, 1–28. [Google Scholar] [CrossRef]
- Zheng, Y.; Zhang, G.; Li, Y.; Li, Z. Optimal jam-absorption driving strategy for mitigating rear-end collision risks with oscillations on freeway straight segments. Accid. Anal. Prev. 2020, 135, 105367. [Google Scholar] [CrossRef] [PubMed]





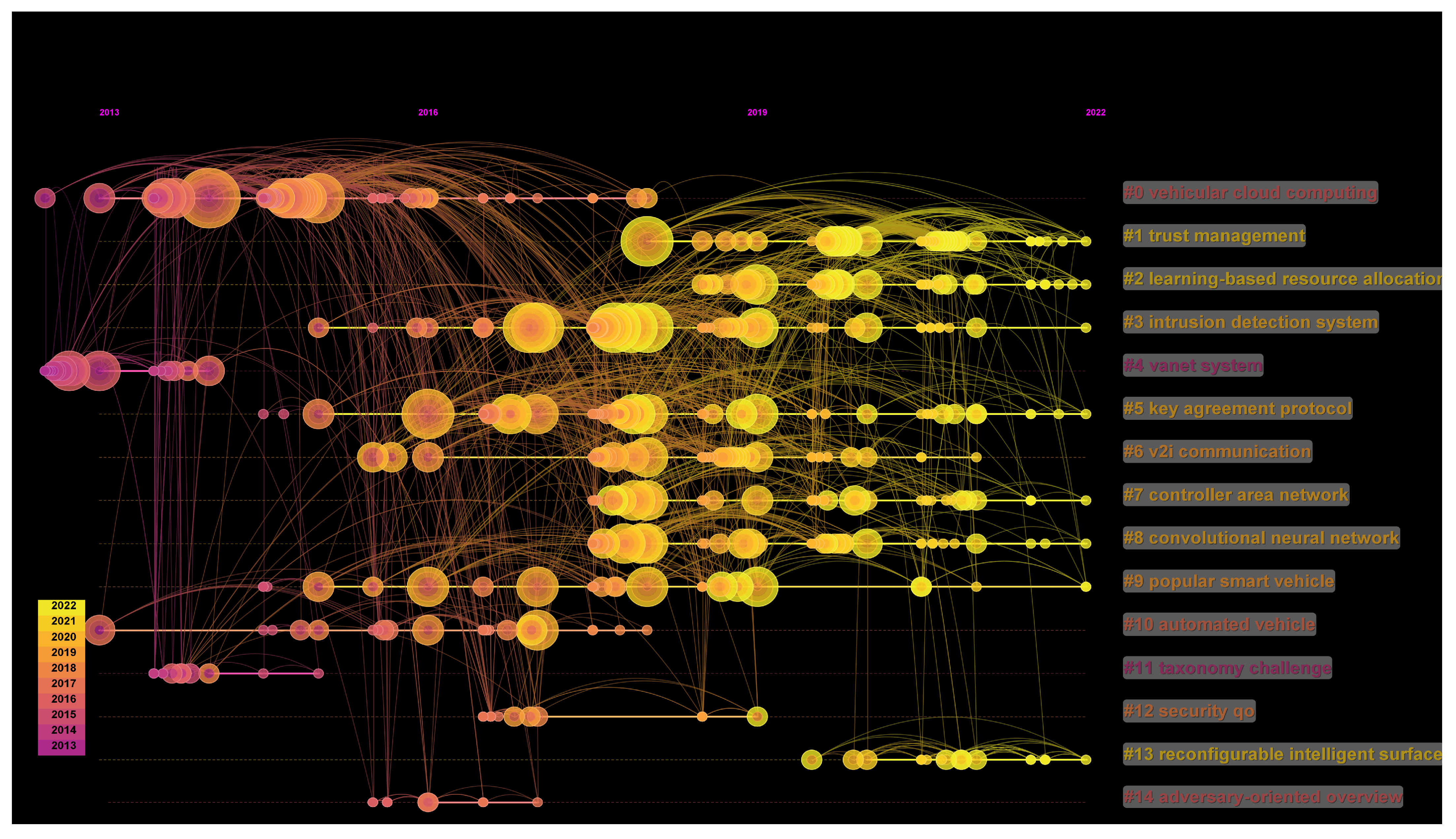

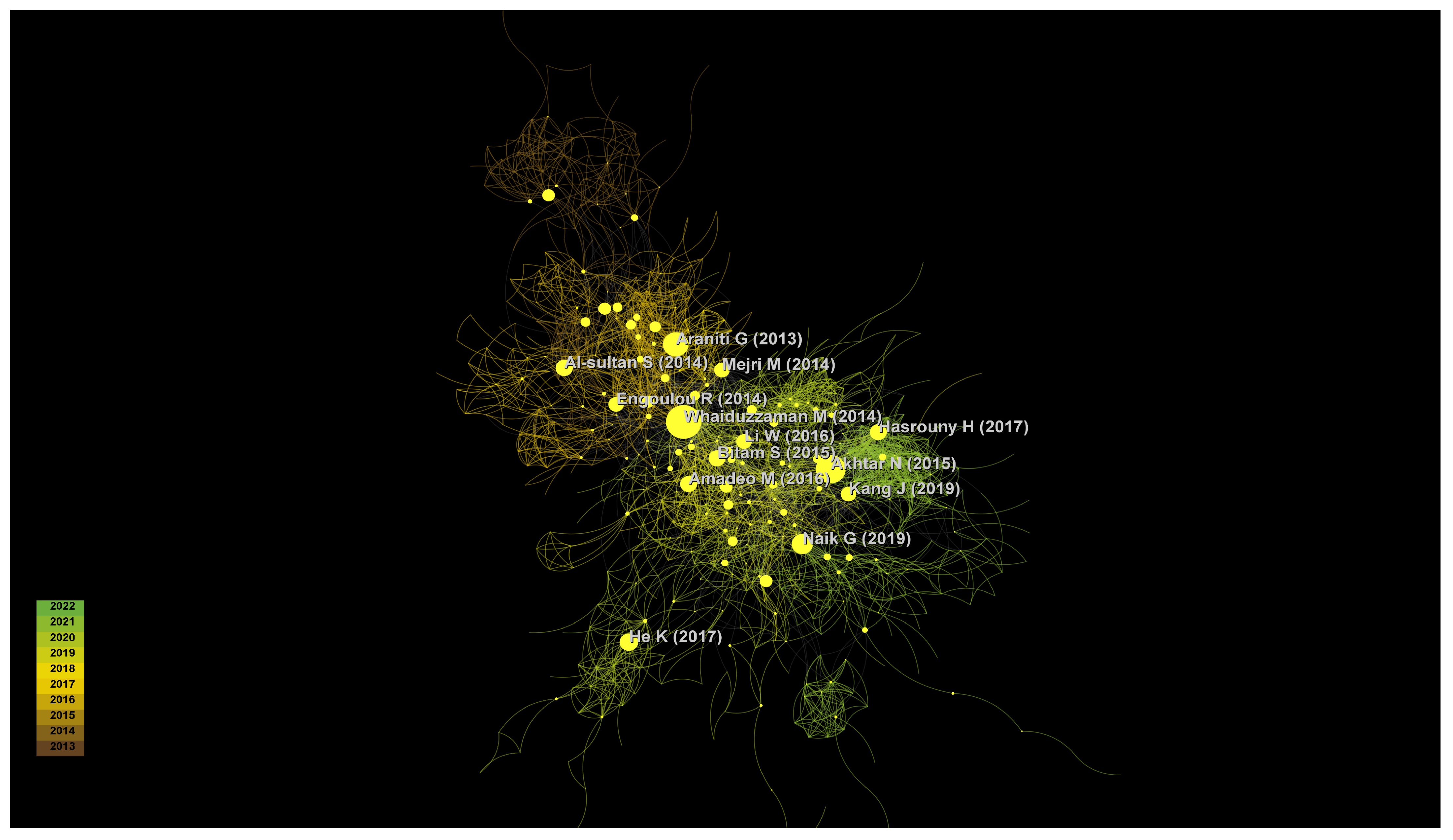
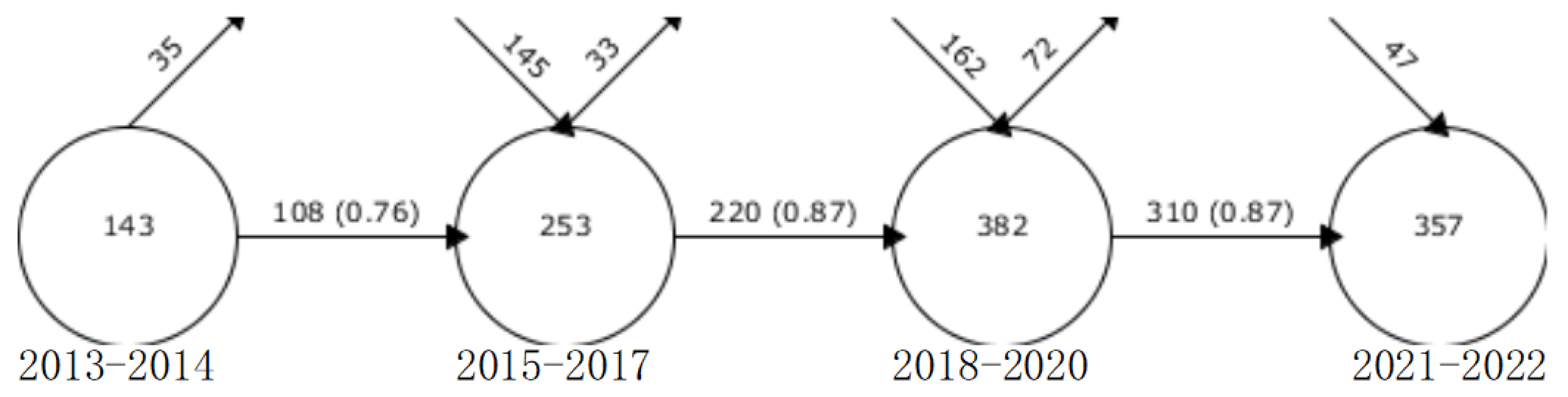


| Cluster-ID | Size | Silhouette | Mean (Year) | Label (LLR) |
|---|---|---|---|---|
| 0 | 114 | 0.785 | 2015 | vehicular cloud computing; using VANET; data management perspective |
| 1 | 67 | 0.905 | 2020 | trust management; using blockchain; security privacy |
| 2 | 66 | 0.853 | 2020 | learning-based resource allocation; machine learning |
| 3 | 65 | 0.792 | 2018 | intrusion detection system; using fog computing; routing protocol |
| 4 | 62 | 0.932 | 2013 | VANET system; back-off mechanism; vehicular networking perspective |
| 5 | 60 | 0.863 | 2018 | key agreement protocol; efficient conditional privacy-preserving authentication scheme |
| 6 | 54 | 0.804 | 2019 | v2i communication; architectural design |
| 7 | 50 | 0.858 | 2019 | controller area network; analyzing cyberattack effect |
| 8 | 44 | 0.874 | 2019 | convolutional neural network; vehicular network |
| 9 | 32 | 0.907 | 2018 | popular smart vehicle; cpss-based approach; vehicular social network |
| 10 | 28 | 0.935 | 2016 | automated vehicle |
| 11 | 22 | 0.959 | 2014 | taxonomy challenge; low-overhead link quality assessment |
| 12 | 20 | 0.92 | 2017 | security qo; multihop data dissemination |
| 13 | 18 | 0.991 | 2021 | reconfigurable intelligent surface; irs-assisted secure uav transmission |
| 14 | 15 | 0.985 | 2016 | adversary-oriented overview; collaborative multi-hop vehicular communication |
| Cited References | Citing Articles | ||
|---|---|---|---|
| Cites | Author, Year, Journal, Volume, Page | Coverage% | Author (Year) Title |
| 80 | Al-sultan S, 2014, J NETW COMPUT APPL, 37, 380 [9] | 26 | ILARRI, S (2015.0) A data management perspective on vehicular networks. IEEE Communications Surveys and Tutorials, V17, P41 DOI 10.1109/COMST.2015.2472395 [19] |
| 40 | Whaiduzzaman M, 2014, J NETW COMPUT APPL, 40, 325 [10] | 24 | SAINI, M (2015.0) How close are we to realizing a pragmatic VANET solution? a meta-survey. ACM Computing Surveys, V48, P40 DOI 10.1145/2817552 [15] |
| 31 | Mejri M, 2014, VEH COMMUN, 1, 53 [11] | 18 | ZEKRI, A (2018.0) Heterogeneous vehicular communications: a comprehensive study. AD HOC Networks, V75-76, P28 DOI 10.1016/j.adhoc.2018.03.010 [16] |
| 31 | Zeadally S, 2012, TELECOMMUN SYST, 50, 217 [12] | 15 | ZHENG, K (2015.0) Heterogeneous vehicular networking: a survey on architecture, challenges, and solutions. IEEE Communications Surveys and Tutorials, V17, P20 DOI 10.1109/COMST.2015.2440103 [17] |
| 28 | Engoulou R, 2014, COMPUT COMMUN, 44, 1 [13] | 14 | MACHARDY, Z (2018.0) V2x access technologies: regulation, research, and remaining challenges. IEEE Communications Surveys and Tutorials, V20, P20 DOI 10.1109/COMST.2018.2808444 [18] |
| Cited References | Citing Articles | ||
|---|---|---|---|
| Cites | Author, Year, Journal, Volume, Page | Coverage% | Author (Year) Title |
| 40 | Yang Z, 2019, IEEE Internet Things, 6, 1495 [20] | 28 | MIKAVICA, B (2021.0) Blockchain-based solutions for security, privacy, and trust management in vehicular networks: a survey. Journal of Supercomputing, V77, P56 DOI 10.1007/s11227-021-03659-x [25] |
| 33 | Dorri A, 2017, IEEE COMMUN MAG, 55, 119 [21] | 23 | ABBAS, S (2021.0) Blockchain-based authentication in the internet of vehicles: a survey. SENSORS, V21, P42 DOI 10.3390/s21237927 [26] |
| 27 | Kang J, 2019, IEEE Internet Things, 6, 4660 [22] | 22 | JABBAR, R (2022.0) Blockchain technology for intelligent transportation systems: a systematic literature review. IEEE Access, V10, P37 DOI 10.1109/ACCESS.2022.3149958 [27] |
| 27 | Kang J, 2019, IEEE T VEH TECHNOL, 68, 2906 [23] | 21 | JAN, S (2021.0) A survey on privacy-preserving authentication schemes in VANETs: attacks, challenges and open issues. IEEE Access DOI 10.1109/ACCESS.2021.3125521 [28] |
| 27 | Lu Z, 2018, IEEE Access, 6, 0 [24] | 21 | SILVA, L (2021.0) Computing paradigms in emerging vehicular environments: a review. IEEE-CAA Journal of Automatica Sinica DOI 10.1109/JAS.2021.1003862 [29] |
| Cited References | Citing Articles | ||
|---|---|---|---|
| Cites | Author, Year, Journal, Volume, Page | Coverage% | Author (Year) Title |
| 42 | Tang F, 2020, P IEEE, 108, 292 [30] | 23 | LAMSSAGGAD, A (2021.0) A survey on the current security landscape of intelligent transportation systems. IEEE Access DOI 10.1109/ACCESS.2021.3050038 [34] |
| 25 | He Y, 2018, IEEE T VEH TECHNOL, 67, 44 [31] | 19 | TANG, F (2021.0) Comprehensive survey on machine learning in the vehicular network: technology, applications and challenges. IEEE Communications Surveys and Tutorials, V23, P31 DOI 10.1109/COMST.2021.3089688 [35] |
| 23 | Machardy Z, 2018, IEEE COMMUN SURV TUT, 20, 1858 [18] | 14 | SILVA, L (2021.0) Computing paradigms in emerging vehicular environments: a review. IEEE-CAA Journal of Automatica Sinica DOI 10.1109/JAS.2021.1003862 [29] |
| 23 | Molina-masegosa R, 2017, IEEE VEH TECHNOL MAG, 12, 30 [32] | 12 | BANGUI, H (2021.0) A hybrid machine learning model for intrusion detection in VANET. Computing, V104, P29 DOI 10.1007/s00607-021-01001-0 [36] |
| 22 | Naik G, 2019, IEEE Access, 7, 70169 [33] | 12 | YANG, Y (2019.0) Emerging technologies for 5 g-enabled vehicular networks. IEEE Access DOI 10.1109/ACCESS.2019.2954466 [20] |
| Cited References | Citing Articles | ||
|---|---|---|---|
| Cites | Author, Year, Journal, Volume, Page | Coverage% | Author (Year) Title |
| 69 | Hasrouny H, 2017, VEH COMMUN, 7, 7 [37] | 26 | WANG, X (2019.0) Privacy-preserving content dissemination for vehicular social networks: challenges and solutions. IEEE Communications Surveys and Tutorials, V21, P32 DOI 10.1109/COMST.2018.2882064 [42] |
| 50 | Sakiz F, 2017, AD HOC NETW, 61, 33 [38] | 21 | SHARMA, S (2019.0) A survey on internet of vehicles: applications, security issues & solutions. Vehicular Communications, V20, P44 DOI 10.1016/j.vehcom.2019.100182 [43] |
| 32 | Cunha F, 2016, AD HOC NETW, 44, 90 [39] | 18 | LAMSSAGGAD, A (2021.0) A survey on the current security landscape of intelligent transportation systems. IEEE Access DOI 10.1109/ACCESS.2021.3050038 [34] |
| 30 | Manvi S, 2017, VEH COMMUN, 9, 19 [40] | 13 | HUSSAIN, R (2019.0) Integration of VANET and 5 g security: a review of design and implementation issues. Future Generation Computer Systems -the International Journal of Escience, V101, P22 DOI 10.1016/j.future.2019.07.006 [44] |
| 28 | Li W, 2016, IEEE T INTELL TRANSP, 17, 960 [41] | 13 | ZEKRI, A (2018.0) Heterogeneous vehicular communications: a comprehensive study. AD HOC Networks, V75-76, P28 DOI 10.1016/j.adhoc.2018.03.010 [16] |
| Cited References | Citing Articles | ||
|---|---|---|---|
| Cites | Author, Year, Journal, Volume, Page | Coverage% | Author (Year) Title |
| 22 | Sommer C, 2011, IEEE T MOBILE COMPUT, 10, 3 [45] | 11 | ALSABAAN, M (2013) Vehicular networks for a greener environment: a survey. IEEE Communications Surveys and Tutorials, V15, P17 DOI 10.1109/SURV.2012.101912.00184 [50] |
| 11 | Behrisch M, 2011 [46], P 3 INT C ADV SYST S, 0, 63 | 8 | STANICA, R (2014) Reverse back-off mechanism for safety vehicular ad hoc networks. AD HOC Networks, V16, P15 DOI 10.1016/j.adhoc.2013.12.012 [51] |
| 10 | Gozalvez J, 2012, IEEE COMMUN MAG, 50, 176 [47] | 7 | JOERER, S (2014) A vehicular networking perspective on estimating vehicle collision probability at intersections. IEEE Transactions on Vehicular Technology, V63, P11 DOI 10.1109/TVT.2013.2287343 [52] |
| 10 | Hartenstein H, 2008, IEEE COMMUN MAG, 46, 164 [48] | 7 | SANTA, J (2013) Comprehensive vehicular networking platform for v2i and v2v communications within the walkie-talkie project. INTERNATIONAL JOURNAL OF DISTRIBUTED SENSOR NETWORKS DOI 10.1155/2013/676850 [53] |
| 9 | Tonguz O, 2010, IEEE WIREL COMMUN, 17, 47 [49] | 6 | GHOSH, A (2014) Exploring efficient seamless handover in VANET systems using network dwell time. EURASIP JOURNAL ON Wireless Communications AND NETWORKING DOI 10.1186/1687-1499-2014-227 [54] |
| Ref. | Title | Burst | Year | Duration |
|---|---|---|---|---|
| Al-sultan S, 2014 [9] | Al-sultan S, 2014, J NETW COMPUT APPL, V37, P380, DOI 10.1016/j.jnca.2013.02.036, DOI | 21.43 | 2014 | 2015–2018 |
| Zeadally S, 2012 [12] | Zeadally S, 2012, TELECOMMUN SYST, V50, P217, DOI 10.1007/s11235-010-9400-5, DOI | 16.25 | 2012 | 2014–2017 |
| Karagiannis G, 2011 [55] | Karagiannis G, 2011, IEEE COMMUN SURV TUT, V13, P584, DOI 10.1109/SURV.2011.061411.00019, DOI | 14.81 | 2011 | 2014–2016 |
| Kenney J, 2011 [56] | Kenney J, 2011, P IEEE, V99, P1162, DOI 10.1109/JPROC.2011.2132790, DOI | 14.24 | 2011 | 2014–2016 |
| Whaiduzzaman M, 2014 [10] | Whaiduzzaman M, 2014, J NETW COMPUT APPL, V40, P325, DOI 10.1016/j.jnca.2013.08.004, DOI | 12.02 | 2014 | 2015–2018 |
| Sommer C, 2011 [45] | Sommer C, 2011, IEEE T MOBILE COMPUT, V10, P3, DOI 10.1109/TMC.2010.133, DOI | 11.93 | 2011 | 2013–2016 |
| Lu N, 2014 [57] | Lu N, 2014, IEEE Internet Things, V1, P289, DOI 10.1109/JIOT.2014.2327587, DOI | 11.08 | 2014 | 2018–2019 |
| Sharef B, 2014 [58] | Sharef B, 2014, J NETW COMPUT APPL, V40, P363, DOI 10.1016/j.jnca.2013.09.008, DOI | 10.97 | 2014 | 2015–2018 |
| He D, 2015 [59] | He D, 2015, IEEE T INF FOREN SEC, V10, P2681, DOI 10.1109/TIFS.2015.2473820, DOI | 10.67 | 2015 | 2018–2020 |
| Ren S, 2015 [60] | Ren S, 2015, ADV NEUR IN, V28, P0, DOI 10.1109/TPAMI.2016.2577031, DOI | 10.29 | 2015 | 2019–2020 |
| Centrality | Author | Year | Source | Vol | Page |
|---|---|---|---|---|---|
| 0.16 | Whaiduzzaman M | 2014 | J NETW COMPUT APPL | 40 | 325 |
| 0.13 | Akhtar N | 2015 | IEEE T VEH TECHNOL | 64 | 248 |
| 0.12 | Araniti G | 2013 | IEEE COMMUN MAG | 51 | 148 |
| 0.1 | Naik G | 2019 | IEEE Access | 7 | 70169 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ji, W.; Yu, S.; Shen, Z.; Wang, M.; Cheng, G.; Yang, T.; Yuan, Q. Knowledge Mapping with CiteSpace, VOSviewer, and SciMAT on Intelligent Connected Vehicles: Road Safety Issue. Sustainability 2023, 15, 12003. https://doi.org/10.3390/su151512003
Ji W, Yu S, Shen Z, Wang M, Cheng G, Yang T, Yuan Q. Knowledge Mapping with CiteSpace, VOSviewer, and SciMAT on Intelligent Connected Vehicles: Road Safety Issue. Sustainability. 2023; 15(15):12003. https://doi.org/10.3390/su151512003
Chicago/Turabian StyleJi, Wei, Shengnan Yu, Zefang Shen, Min Wang, Gang Cheng, Tiantong Yang, and Quan Yuan. 2023. "Knowledge Mapping with CiteSpace, VOSviewer, and SciMAT on Intelligent Connected Vehicles: Road Safety Issue" Sustainability 15, no. 15: 12003. https://doi.org/10.3390/su151512003
APA StyleJi, W., Yu, S., Shen, Z., Wang, M., Cheng, G., Yang, T., & Yuan, Q. (2023). Knowledge Mapping with CiteSpace, VOSviewer, and SciMAT on Intelligent Connected Vehicles: Road Safety Issue. Sustainability, 15(15), 12003. https://doi.org/10.3390/su151512003









