An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles
Abstract
:1. Introduction
2. Analysis of Vehicular Network Security
2.1. Severe Security Threats
2.2. Vehicle Network Lacking Information Security
- (1)
- Point to line communication has poor confidentiality. The message in the CAN bus is transmitted by broadcast. All nodes can accept the message transmitted by the bus, which makes it possible to monitor the message information. The automobile bus data is easy to be captured and analyzed, and the availability and integrity can not be guaranteed.
- (2)
- The propagated message source is incomplete. There is no original address information in the protocol, and the receiving electronic control units (ECU) cannot confirm that the received data is the original data, which makes it easy for the attacker to forge and tamper with the CAN bus message by injecting false information, which allows the message to be stolen and tampered with, and the authenticity of the message cannot be guaranteed.
- (3)
- Bus vulnerability. The arbitration mechanism given priority in the CAN bus protocol makes it possible for hackers to carry out denial of service attacks on bus messages. The attacker can replay or flood the vehicle bus by means of sniffing or monitoring so that the ECU cannot send and receive messages normally.
2.3. Network Security Attacks
- (1)
- Attacks from the sensing layer (physical layer). Today’s automobile is developing towards electrification, intelligence, networking, and sharing. In order to meet the needs of all aspects, we need to be equipped with a series of advanced sensors, such as lidar, millimeter-wave radar, camera, and GPS, which are used to collect the perceived information of the external environment and provide the ability to perceive the environment for automatic driving decision-making. It is also equipped with more and more electronic control units (ECU) and wireless connections. Although these measures improve the safety and efficiency of vehicles, they also bring new weaknesses. Therefore, attacking vehicles through the physical layer will become a new threat to vehicle network security. For example, Rouf et al. [9] proposed an attack that interferes with the tire pressure monitoring system through the radio channel, making the vehicle tire pressure monitoring system ineffective. Tao et al. [14] proposed to attack the keyless start system through the control of the radio channel and illegally start the target vehicle.
- (2)
- Illegal access (data link layer). Due to the lack of data encryption and message verification mechanism in the vehicle network, once the attacker can access the network equipment, they can easily carry out the attack. The attack modes of the data link layer include frame injection, frame forgery, frame sniffing, pause, and DoS attack. The availability of the network will be seriously threatened. For example, it has been proven how to use the vulnerability of remote endpoint to destroy ECU, access the vehicle network, and then control vehicle mobility. Attackers can simply inject arbitrary messages into the CAN bus or monopolize the network by continuously sending the highest priority frames [15].
- (3)
- Attacks from the interface (application layer). In order to improve the safety and efficiency of the automobile transportation system, automobile manufacturers integrate wireless communication systems into automobiles [10]. In recent years, there have been many reports on remote network attacks on vehicles by using vulnerabilities in external network interfaces and devices [6,16]. Attack portals include Bluetooth and OBD- II, Wi-Fi, etc. In the network application layer, attackers can carry out more targeted attacks that are not easily found and are more likely to be interfered or deceived because there is no need for a physical connection [10]. Since such attacks do not have illegal access to nodes and obvious data frame exceptions, they are more difficult to detect. For such attacks, researchers at home and abroad mainly focus on the design of intrusion detection methods based on machine learning [9,10,11]. At present, there are many problems such as excessive consumption of computing resources, lack of test data sets, and model evaluation.
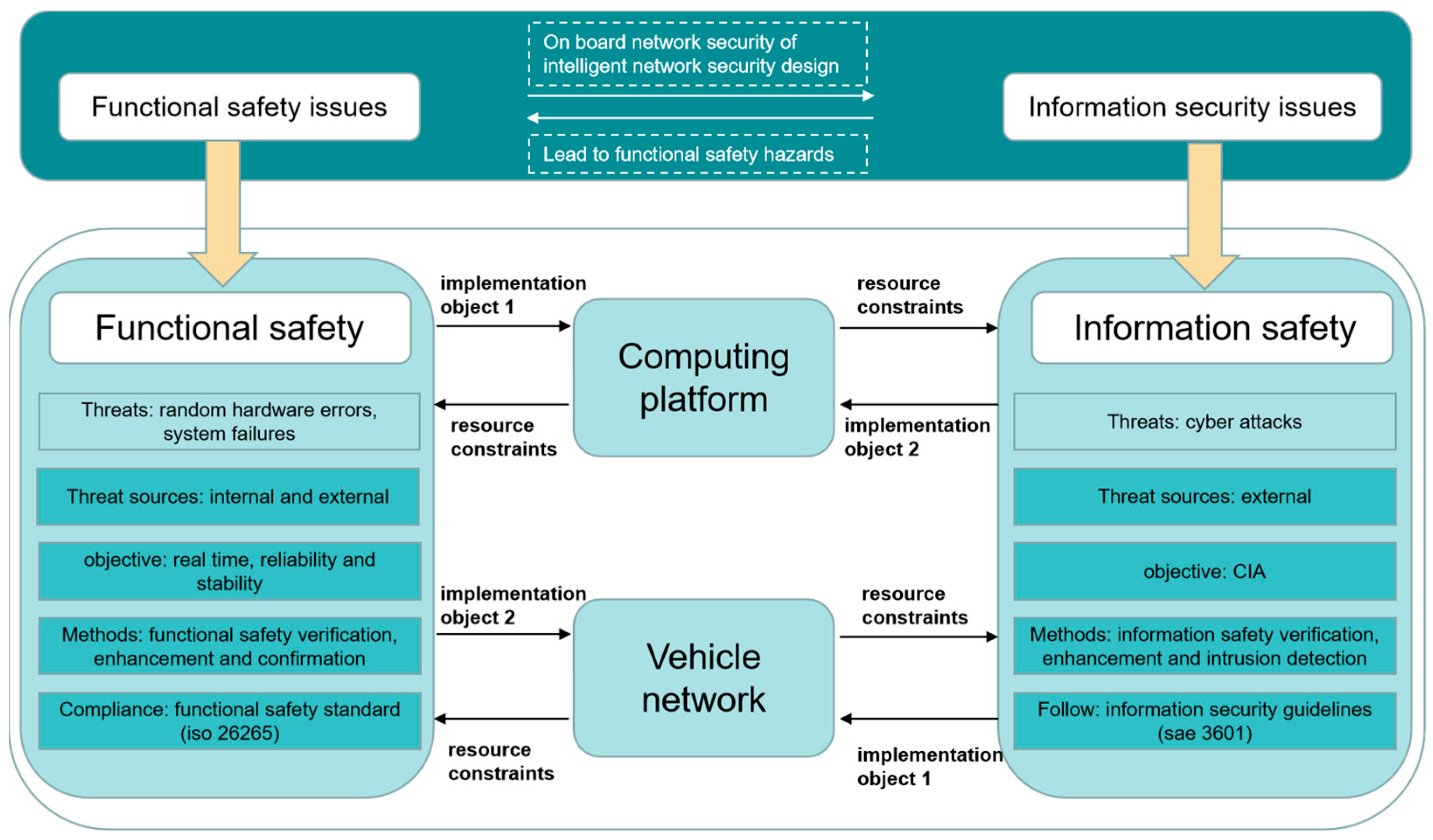
2.4. Functional Safety Guarantee of Vehicle Network
- (1)
- The constraints of computing, storage, and communication bandwidth resources make the internal hardware resource constraints of the vehicle mainly manifest as computing, storage, bandwidth, and energy constraints.
- (2)
- Complex and heterogeneous software and hardware structure. The interior of the vehicle is composed of a large number of heterogeneous and complex software and hardware components, which communicate through heterogeneous vehicle network protocols and gateways. The complexity and heterogeneity of the system not only add uncertainty to the functional security and information security but also increase the difficulty of system functional security guarantee test and verification.
- (3)
- Considering the balance of cost and performance, the computing and storage resources of ECUs in ACPs are often limited and the high cost of deployment may give low priority to network security deployment, and the vehicle network security design is subject to strict cost constraints, which also leads to the network information security enhancement scheme of traditional information can not be deployed in the automotive environment.
- (4)
- The constraints of vehicle networks on functional safety design are mainly manifested in the real-time performance of message transmission, end-to-end delay boundary, system task schedulability, and so on, which will affect the reliability and stability of the system. At present, the research work on vehicle network message schedulability analysis mainly focuses on exploring the upper bounds of communication delay [26,27,28], network message schedulability analysis [29,30], and meeting deterministic delay analysis [31].
3. Enhancement Technology of Vehicular Network Security
3.1. Vehicle Network Data Encryption Technology
3.2. Vehicle Network Message Authentication Technology
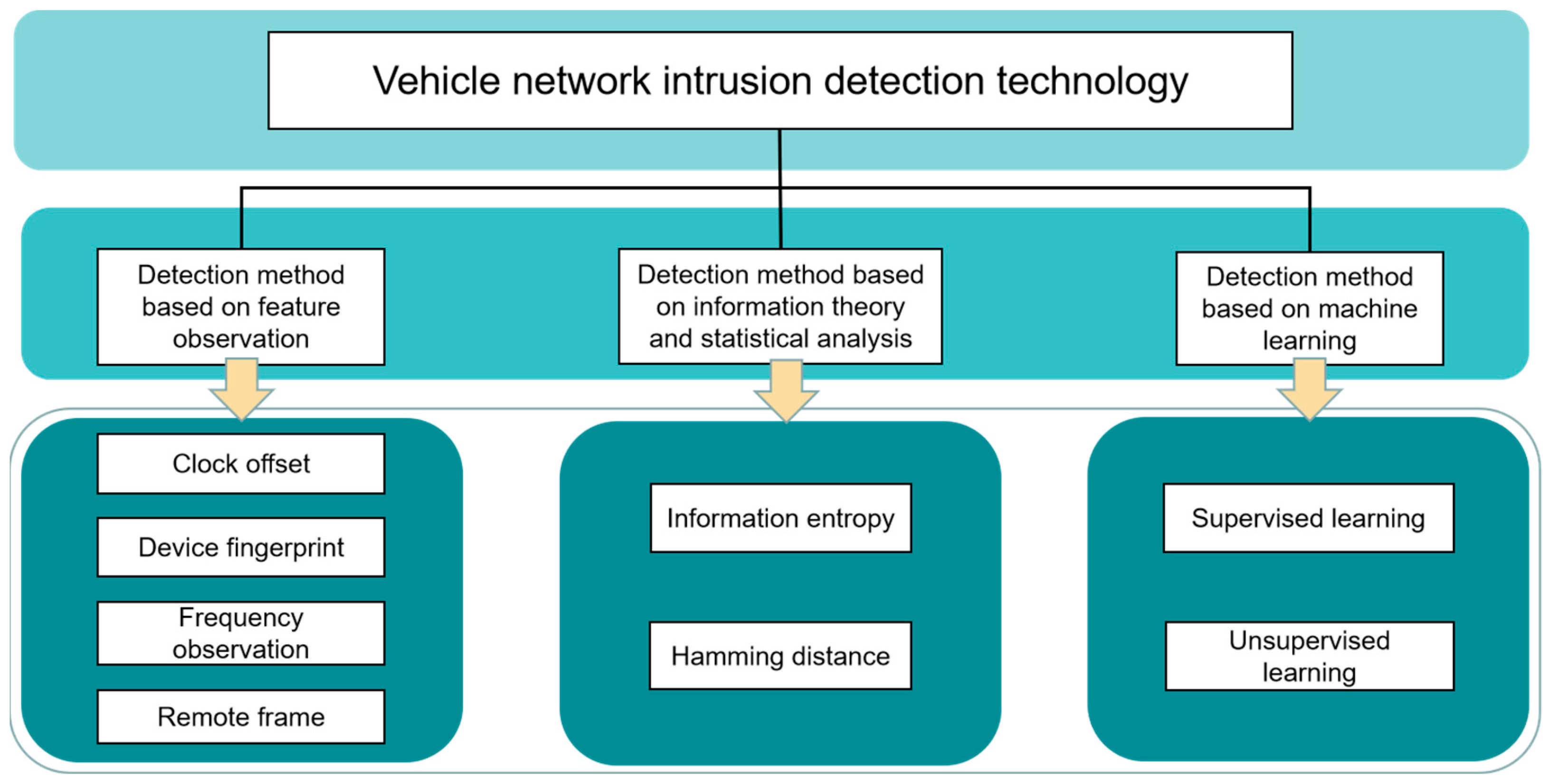
3.3. Vehicle Network Intrusion Detection Technology
- (1)
- Detection method based on feature observation
- (2)
- Detection method based on information theory and statistical analysis
- (3)
- Detection method based on machine learning
4. Recommendations
4.1. Recommendations for Vehicle Cybersecurity Threats
- Through data research and analysis, it can be concluded that whether it is based on a wired or wireless data transmission layer, or a relatively advanced application layer and perception layer, there are certain risks in their information security. The development trend of the in-vehicle network of connected vehicles will be from a composite architecture to a central computing architecture, forming a domain network architecture suitable for autonomous driving.
- The CAN bus, which plays a representative role in the in-vehicle network, is the starting point and the end of the automotive information security problem and has extremely high requirements for its security and anti-malicious attack capabilities. On the basis of the existing infrastructure, the security of the vehicle network is guaranteed by adjusting the message scheduling method and optimizing the assignment of task priorities. The development of a multi-functional, high-performance and highly adaptable information scheduling method can not only improve the utilization efficiency of the CAN bus but also balance the cost and performance of the system.
- It is an inevitable development trend to classify and isolate networks and domains, establish in-depth multi-layer architecture defenses for key modules, and use a combination of software and hardware for security protection.
- The complex heterogeneous hardware architecture and multi-source heterogeneous sensor information on intelligent vehicles increase the vulnerabilities of intelligent vehicle network security, which greatly increases the risk of vehicle networks being attacked. Reducing the time and links of the intelligent vehicle information transmission link, reducing the complexity of hardware and multi-source heterogeneous information can improve the functional safety and information security of the system, and reduce the difficulty of system testing.
- Adding data encryption and message authentication mechanisms to the vehicle network can effectively avoid illegal attacks on the vehicle network. Reducing computer resource consumption, improving relevant information datasets, and optimizing machine learning techniques can all improve the accuracy and efficiency of system security detection.
- Reduce the delay of vehicle information transmission, ensure the real-time nature of information transmission, optimize the system of vehicle communication network, research the communication architecture suitable for intelligent vehicle network transmission on the basis of traditional vehicle communication system, and reduce the information network caused by the vehicle itself paralysis.
4.2. Recommendations for Vehicle Cybersecurity Enhancement Technology
- Layout and application of technology. Limited by the communication network bandwidth and computing resources, the application of traditional information encryption and authentication technologies to intelligent vehicles with more complex information links will greatly increase the cost of network communication and the bloated degree of the system, which is not conducive to intelligent vehicle data encryption. Researching more stable and mature lightweight information security protection modules can reduce the workload of ECUs and improve the work efficiency of ECU.
- Considering the current requirements of vehicle network bandwidth resources and message response time, the problems and challenges in the design of existing message authentication protocols mainly lie in how to improve the security of message authentication and avoid the functional reliability and real-time problems caused by message schedulability due to communication bandwidth consumption.
- Considering the long life cycle of an automobile (about 20 years) and the dynamic change of the network environment, there are three main problems in the existing research. ① Detection methods often correspond to specific attack models; ② The robustness of detection effect is not strong (there are many preconditions and lack of perception of vehicle state); ③ Lack of evaluation of detection response time and impact on functional safety guarantee. Considering the key attributes of ACPs functional security, it is urgent to solve the problems through the optimization research of the intrusion detection model and algorithm to avoid the serious functional security crisis of intelligent network=connected vehicles caused by network security problems.
- The existing research on vehicle network intrusion detection methods based on information theory often ignores the impact of vehicle network information entropy jitter caused by different vehicle states on the detection results. Its detection model has high detection accuracy in limited vehicle states, but its robustness to different vehicle states needs to be improved. These problems result in these methods not meeting the high-level security requirements in the current automotive safety integration level (AISl). Therefore, this paper intends to carry out the optimization research of a state-aware vehicle network intrusion detection algorithm through the perception of the vehicle state.
- It can be seen that the framework based on machine learning can strengthen the security of the computer network in the vehicle without affecting the network performance. How to use machine learning for resource allocation and mobile target defense deployment is the future research direction. How to determine the best IP shuffle frequency and bandwidth allocation through vehicle network and provide effective and long-term mobile target defense are further problems to be solved. Building a more secure vehicle CAN network intrusion detection system through an advanced machine learning algorithm can improve the efficiency of the vehicle CAN network threat detection, reduce the false positive rate and false negative rate of intrusion detection, and lay a foundation for the development of vehicle can network security.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Brecht, B.; Therriault, D.; Weimerskirch, A.; Whyte, W.; Kumar, V.; Hehn, T.; Goudy, R. A security credential management system for V2X communications. IEEE Trans. Intell. Transp. Syst. 2018, 19, 3850–3871. [Google Scholar] [CrossRef] [Green Version]
- Greenberg, A. Hackers remotely kill a jeep on the highway—With me in it. Wired 2015, 7, 21–22. [Google Scholar]
- Ring, T. Connected cars–The next target for hackers. Netw. Secur. 2015, 2015, 11–16. [Google Scholar] [CrossRef]
- Researchers Hack BMW Cars, Discover 14 Vulnerabilities. Available online: https://www.helpnetsecurity.com/2018/05/23/hack-BMW-cars/ (accessed on 25 August 2018).
- China Information and Communication Research Institute. White paper on Internet of vehicles network security. China Inform. Secur. 2017, 10, 29–34. [Google Scholar]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive experimental analyses of automotive attack surfaces. In Proceedings of the Usenix Conference on Security, San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010. [Google Scholar]
- Woo, S.; Jo, H.J.; Lee, D.H. A practical wireless attack on the connected car and security protocol for in-vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- Foster, I.; Prudhomme, A.; Koscher, K.; Savage, S. Fast and vulnerable: A story of telematic failures. In Proceedings of the Usenix Conference on Offensive Technologies, Washington, DC, USA, 10–11 August 2015. [Google Scholar]
- Rouf, I.; Miller, R.; Mustafa, H.; Taylor, T.; Oh, S.; Xu, W.; Gruteser, M.; Trappe, W.; Seskar, I. Security and privacy vulnerabilities of in-car wireless networks: A tire pressure monitoring system case study. In Proceedings of the 19th Usenix Security Symposium; Washington, DC, USA, 11–13 August 2010.
- Khan, Z.; Chowdhury, M.; Islam, M.; Huang, C.Y.; Rahman, M. In-vehicle false information attack detection and mitigation framework using machine learning and software defined networking. arXiv 2019, arXiv:1906.10203. [Google Scholar]
- Taylor, A.; Leblanc, S.; Japkowicz, N. Anomaly detection in automobile control network data with long short-term memory networks. In Proceedings of the 3rd IEEE International Conference on Data Science and Advanced Analytics, Montreal, QC, Canada, 17–19 October 2016. [Google Scholar]
- Lv, S.; Nie, S.; Liu, L.; Lu, W. Car Hacking Research: Remote Attack Tesla Motors; Keen Security Lab of Tencent: Shenzhen, China, 2016; Volume 2016, pp. 37–45. [Google Scholar]
- Yang, T.; Kong, L.; Xin, W.; Hu, J.; Chen, Z. Resisting relay attacks on vehicular passive keyless entry and start systems. In Proceedings of the 2012 9th International Conference on Fuzzy Systems and Knowledge Discovery, Chongqing, China, 29–31 May 2012. [Google Scholar]
- Cho, K.T.; Shin, K.G. Error handling of in-vehicle networks makes them vulnerable. In Proceedings of the 23rd ACM Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Sun, J.; Iqbal, S.; Arabi, N.S.; Zulkernine, M. A classification of attacks to in-vehicle components (IVCs). Veh. Commun. 2020, 25, 100253. [Google Scholar] [CrossRef]
- Xie, G.; Chen, Y.; Liu, Y.; Li, R.; Li, K. Minimizing development cost with reliability goal for automotive functional safety during design phase. IEEE Trans. Reliab. 2017, 67, 196–211. [Google Scholar] [CrossRef]
- Pop, T.; Eles, P.; Peng, Z. Schedulability analysis for distributed heterogeneous time/event triggered real-time systems. In Proceedings of the 15th Euromicro Conference on Real-Time Systems, Porto, Portugal, 2–4 July 2003. [Google Scholar]
- Davis, R.I.; Cucu-grosjean, L.; Bertogna, M.; Burns, A. A review of priority assignment in real-time systems. J. Syst. Architect. 2016, 65, 64–82. [Google Scholar] [CrossRef] [Green Version]
- Davis, R.I.; Burns, A.; Bril, R.J.; Lukkien, J.J. Controller area network (CAN) schedulability analysis: Refuted, revisited and revised. Real-Time Syst. 2007, 35, 239–272. [Google Scholar] [CrossRef] [Green Version]
- Xie, G.; Zeng, G.; Liu, Y.; Zhou, J.; Li, R.; Li, K. Fast functional safety verification for distributed automotive applications during early design phase. IEEE Trans. Ind. Electron. 2018, 65, 4378–4391. [Google Scholar] [CrossRef]
- Xie, Y.; Zeng, G.; Kurachi, R.; Takada, H.; Xie, G. Security/timing-aware design space exploration of CAN FD for automotive cyber-physical systems. IEEE Trans. Ind. Inform. 2019, 15, 1094–1104. [Google Scholar] [CrossRef]
- PiryadarshiniI, I. Introduction on Cyber Security; John Wiley & Sons: New York, NY, USA, 2019; pp. 1–37. [Google Scholar]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A survey of intrusion detection for in-vehicle networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Lee, H.; Geum, Y. Development of the scenario-based technology roadmap considering layer heterogeneity: An approach using CIA and AHP. Technol. Forecast. Soc. Chang. 2017, 117, 12–24. [Google Scholar] [CrossRef]
- Peng, C.; Zeng, H. Response time analysis of digraph real-time tasks scheduled with static priority: Generalization, approximation, and improvement. Real-Time Syst. 2018, 54, 91–131. [Google Scholar] [CrossRef]
- Chen, G.; Guan, N.; Liu, D.; He, Q.; Huang, K.; Stefanov, T.; Yi, W. Utilization-based scheduling of flexible mixed-criticality real-time tasks. IEEE Trans. Comput. 2018, 67, 543–558. [Google Scholar] [CrossRef] [Green Version]
- Xie, G.; Zeng, G.; Kurachi, R.; Takada, H.; Li, Z.; Li, R.; Li, K. WCRT analysis of CAN messages in gateway-integrated in-vehicle networks. IEEE Trans. Veh. Technol. 2017, 66, 9623–9637. [Google Scholar] [CrossRef]
- Davis, R.I.; Altmeyer, S.; Reineke, J. Response-time analysis for fixed-priority systems with a write-back cache. Real-Time Syst. 2018, 54, 912–963. [Google Scholar] [CrossRef] [Green Version]
- Chang, W.; Chakraborty, S. Resource-aware automotive control systems design: A cyber-physical systems approach. Found. Trends Electron. Des. Autom. 2016, 10, 249–369. [Google Scholar]
- Vatanpavar, K.; Al Faruque, M.A. ACQUA: Adaptive and cooperative quality-aware control for automotive cyber-physical systems. In Proceedings of the 36th IEEE/ACM International Conference on Computer-Aided Design, Irvine, CA, USA, 13–16 November 2017. [Google Scholar]
- Wang, E.; Xu, W.; Sastry, S.; Liu, S.; Zeng, K. Hardware module-based message authentication in intra-vehicle networks. In Proceedings of the 8th ACM/IEEE International Conference on Cyber-Physical Systems, Pittsburgh, PA, USA, 18–20 April 2017. [Google Scholar]
- Siddiqui, A.S.; Gui, Y.; Plusquellic, J.; Saqib, F. Secure communication over CAN bus. In Proceedings of the 60th IEEE International Midwest Symposium on Circuits and Systems, Boston, MA, USA, 6–9 August 2017. [Google Scholar]
- Gu, Z.; Han, G.; Zeng, H.; Zhao, Q. Security-aware mapping and scheduling with hardware co-processors for Flex Ray-based distributed embedded systems. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 3044–3057. [Google Scholar] [CrossRef]
- Herrewege, A.V.; Singelee, D.; Verbauwhede, I. CAN AUTH-a simple, backward compatible broadcast authentication protocol for CAN bus. In Proceedings of the ECRYPT Workshop on Lightweight Cryptography, Louvain-la-Neuve, Belgium, 28–29 January 2011. [Google Scholar]
- Jo, H.J.; Kim, J.H.; Choi, H.Y.; Choi, W.; Lee, D.H.; Lee, I. MAuth-CAN: Masque-Rade-Attack-Proof authentication for in-vehicle networks. IEEE Trans. Veh. Technol. 2020, 69, 2204–2218. [Google Scholar] [CrossRef]
- Cho, K.T.; Shin, K.G. Fingerprinting electronic control units for vehicle intrusion detection. In Proceedings of the 25th USENIX Security Symposium, Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- Halder, S.; Conti, M.; Das, S.K. COIDS: A clock offset based intrusion detection system for controller area networks. In Proceedings of the 21st International Conference on Distributed Computing and Networking, Kolkata, India, 4–7 January 2020. [Google Scholar]
- Li, F.; Wang, C. Research on Intrusion Detection Technology Based on Association Rules Mining in Vehicular Networks. Data Mining 2017, 7, 65–69. [Google Scholar] [CrossRef]
- Lee, H.; Jeong, S.H.; Kim, H.K. OTIDS: A novel intrusion detection system for in-vehicle network by using remote frame. In Proceedings of the 15th Annual Conference on Privacy, Security and Trust, Calgary, AB, Canada, 27–29 August 2017. [Google Scholar]
- Li, F.; Liao, Z.; Zhang, P. A Method and System of On-Board Network Intrusion Detection Based on Clock Offset. China Patent CN201811137466.0, 22 January 2019. [Google Scholar]
- Guan, Y. Research on in Car CAN Bus Intrusion Detection Algorithm. Master’s Thesis, Harbin Institute of Technology, Harbin, China, 2019. [Google Scholar]
- Qin, H.; Yan, M.; Ji, H.; Wang, J.; Wang, Y. A Vehicle-Mounted Network Intrusion Detection Method Based on Message Sequence Prediction. China Patent CN201910499446.6, 20 August 2019. [Google Scholar]
- Cho, K.T.; Shin, K.G. Viden: Attacker identification on in-vehicle networks. In Proceedings of the 24th ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October November 2017. [Google Scholar]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 30th International Conference on Information Networking. Off Jalan Sepanggar Bay, Locked Bag 100, Kota Kinabalu, Sabah, Malaysia, 13–15 January 2016. [Google Scholar]
- Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a spoofing attack on an in-vehicle CAN bus based on the deep features of an ECU fingerprint signal. Smart Cities 2020, 3, 17–30. [Google Scholar] [CrossRef] [Green Version]
- Ning, J.; Liu, J. An experimental study towards attacker identification in automotive networks. In Proceedings of the 2019 IEEE Global Communications Conference, Waikoloa, HI, USA, 9–13 December 2019. [Google Scholar]
- Wang, Q.; Sawhney, S. VeCure: A practical security framework to protect the CAN bus of vehicles. In Proceedings of the 2014 International Conference on the Internet of Things, IOT 2014, Cambridge, MA, USA, 6–8 October 2014. [Google Scholar]
- Van Wyk, F.; Wang, Y.; Khojandi, A.; Masoud, N. Real-time sensor anomaly detection and identification in automated vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 21, 1264–1276. [Google Scholar] [CrossRef]
- Marchetti, M.; Stabili, D.; Guido, A.; Colajanni, M. Evaluation of anomaly detection for in-vehicle networks through information-theoretic algorithms. In Proceedings of the 2nd IEEE International Forum on Research and Technologies for Society and Industry Leveraging a Better Tomorrow, Bologna, Italy, 7–9 September 2016. [Google Scholar]
- Müter, M.; Asaj, N. Entropy-based anomaly detection for in-vehicle networks. In Proceedings of the 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 1110–1115. [Google Scholar]
- Wu, W.; Huang, Y.; Kurachi, R.; Zeng, G.; Xie, G.; Li, R.; Li, K. Sliding window optimized information entropy analysis method for intrusion detection on in-vehicle networks. IEEE Access 2018, 6, 45233–45245. [Google Scholar] [CrossRef]
- Yu, H.; Qin, G.; Sun, M.; Yan, X.; Wang, X. Cyber security and anomaly detection method for in-vehicle CAN. J. Jilin Univ. (Eng. Technol. Ed.) 2016, 46, 1246–1253. [Google Scholar]
- Yan, X. CAN Bus Anomaly Detection Method Based on Renyi Information Entropy. Master’s Thesis, Jilin University, Changchun, China, 2017. [Google Scholar]
- Wu, L.; Qin, G.; Yu, H. Anomaly detection method for in-vehicle CAN bus based random forest. J. Jilin Univ. (Sci. Ed.) 2018, 56, 663–668. [Google Scholar]
- Jeon, B.; Ju, H.; Jung, B.; Kim, K.; Lee, D. A study on traffic characteristics for anomaly detection of Ethernet-based IVN. In Proceedings of the 10th International Conference on Information and Communication Technology Convergence, Jeju Island, Korea, 16–18 October 2019. [Google Scholar]
- Mousavinejad, E.; Yang, F.; Han, Q.L.; Ge, X.; Vlacic, L. Distributed cyber-attacks detection and recovery mechanism for vehicle platooning. IEEE Trans. Intell. Transp. Syst. 2020, 21, 3821–3834. [Google Scholar] [CrossRef] [Green Version]
- Gmiden, M.; Gmiden, M.H.; Trabelsi, H. An Intrusion Detection Method for Securing In-Vehicle CAN bus. In Proceedings of the 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering, Sousse, Tunisia, 19–21 December 2016. [Google Scholar]
- Theissler, A. Anomaly detection in recordings from in-vehicle networks. Big Data Appl. 2014, 3, 23–37. [Google Scholar]
- Casillo, M.; Coppola, S.; Santo, M.D.; Pascale, F.; Santonicola, E. Embedded intrusion detection system for detecting attacks over CAN-BUS. In Proceedings of the 4th International Conference on System Reliability and Safety, Rome, Italy, 20–22 November 2019. [Google Scholar]
- Dosovitskiy, A.; Ros, G.; Codevilla, F.; Lopez, A.; Koltun, V. CARLA: An open urban driving simulator. arXiv 2017, arXiv:1711.03938. [Google Scholar]
- Biggio, B.; Nelson, B.; Laskov, P. Poisoning attacks against support vector machines. arXiv 2012, arXiv:1206.6389. [Google Scholar]
- Demontis, A.; Melis, M.; Biggio, B. Yes, machine learning can be more secure! a case study on android malware detection. IEEE Trans. Dependable Secure Comput. 2017, 16, 711–724. [Google Scholar] [CrossRef] [Green Version]
- Biggio, B.; Corona, I.; Maiorca, D.; Nelson, B.; Šrndić, N.; Laskov, P.; Giacinto, G.; Roli, F. Evasion attacks against machine learning at test time. In Proceedings of the Joint European Conference on Machine Learning and Knowledge Discovery in Databases, Prague, Czech Republic, 23–27 September 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 387–402. [Google Scholar]
- Kolosnjaji, B.; Demontis, A.; Biggio, B.; Maiorca, D.; Giacinto, G.; Eckert, C.; Roli, F. Adversarial malware binaries: Evading deep learning for malware detection in executables. In Proceedings of the 26th European Signal Processing Conference, Rome, Italy, 3–7 September 2018. [Google Scholar]
- Biggio, B.; Roli, F. Wild patterns: Ten years after the rise of adversarial machine learning. Pattern Recogn. 2018, 84, 317–331. [Google Scholar] [CrossRef] [Green Version]
- Apruzzese, G.; Andreolini, M.; Ferretti, L.; Marchetti, M.; Colajanni, M. Modeling realistic adversarial attacks against network intrusion detection systems. arXiv 2021, arXiv:2106.09380. [Google Scholar] [CrossRef]
- Apruzzese, G.; Andreolini, M.; Marchetti, M.; Colacino, V.G.; Russo, G. AppCon: Mitigating evasion attacks to ML cyber detectors. Symmetry 2020, 12, 653. [Google Scholar] [CrossRef] [Green Version]
- Pawlicki, M.; Choraś, M.; Kozik, R. Defending network intrusion detection systems against adversarial evasion attacks. Future Gener. Comput. Syst. 2020, 110, 148–154. [Google Scholar] [CrossRef]
- Usama, M.; Asim, M.; Latif, S.; Qadir, J.; Ala-Al-Fuqaha. Generative adversarial networks for launching and thwarting adversarial attacks on network intrusion detection systems. In Proceedings of the 15th IEEE International Wireless Communications and Mobile Computing Conference, Tangier, Morocco, 24–28 June 2019. [Google Scholar]
- Kumar, K.; Vishnu, C.; Mitra, R.; Mohan, C. Black-box adversarial attacks in autonomous vehicle technology. In Proceedings of the 2020 IEEE Applied Imagery Pattern Recognition Workshop (AIPR), Washington, DC, USA, 13–15 October 2020. [Google Scholar]
- Talpur, A.; Gurusamy, M. Adversarial Attacks Against Deep Reinforcement Learning Framework in Internet of Vehicles. In Proceedings of the 2021 IEEE Globecom Workshops (GC Wkshps), Madrid, Spain, 7–11 December 2021. [Google Scholar]
- Qayyum, A.; Usama, M.; Qadir, J.; Al-Fuqaha, A. Securing connected & autonomous vehicles: Challenges posed by adversarial machine learning and the way forward. IEEE Commun. Surv. Tutor. 2020, 22, 998–1026. [Google Scholar]
- Luo, F.; Hou, S. Cyberattacks and countermeasures for intelligent and connected vehicles. SAE Int. J. Passeng. Cars-Electron. Electr. Syst. 2019, 12, 55–67. [Google Scholar] [CrossRef]
- Gurgens, S.; Zelle, D. A hardware-based solution for freshness of secure onboard communication in vehicles. In Proceedings of the 4th International Workshop on the Security of Industrial Control Systems and Cyber-Physical Systems, Barcelona, Spain, 6–7 September 2018. [Google Scholar]
- Sarpm. Secure Message Authentication Protocol for CAN. Master’s Thesis, Middle East Technical University, Ankara, Turkey, 2020. [Google Scholar]
- Kang, K.D. A Practical and Lightweight Source Authentication Protocol Using One-Way Hash Chain in Can. Master’s Thesis, Daegu Gyeongbuk Institute of Science & Technology, Daegu, Korea, 2017. [Google Scholar]
- Kang, M.J.; Kang, J.W. A novel intrusion detection method using deep neural network for in-vehicle network security. In Proceedings of the 83rd IEEE Vehicular Technology Conference, Nanjing, China, 15–18 May 2016. [Google Scholar]

| Attack Mode | Document | Attack Entrance | Attack Model | CIA Threat |
|---|---|---|---|---|
| Direct physics | Document [6] | CAN illegal access OBD port | Frame sniffing, message playback, etc. | Integrity and confidentiality |
| Document [7,8] | OBD port | Frame sniffing, message playback, and camouflage, DOS attack, etc. | Integrity, confidentiality usability | |
| A little distance Wireless attack | Document [9] | Bluetooth | Frame sniffing, message playback, and camouflage | Integrity and confidentiality |
| Document [10] | TMPS, tire pressure monitoring system | Sniffing, message replay, and camouflage | Integrity and confidentiality | |
| Integrity and confidentiality | Document [11,12,13] | Remote wireless/Wi-Fi, etc. | Message replay and camouflage, etc. | Integrity and confidentiality |
| Technology | Scope of Application | Representative Literature and Technology | Information Security Guarantee | Characteristics and Challenges |
|---|---|---|---|---|
| Data encryption | Data link layer | Lightweight AES [74], hardware password acceleration module [75], MAC decomposition transmission [76] | Safety, Integrity, and Correctness | The enhancement of network message transmission security, integrity, and correctness mainly includes: Facing the balance between security and computing resources |
| Message authentication | Physical layer, Data link layer | TESLA [35], MAuth-CAN [36], One-way hash chain [77] | Correctness | The enhanced protection of the correctness of network message transmission mainly faces the network band Design constraints in broadband networks |
| Intrusion detection | Physical layer, Data link layer, Application layer | A class of SVM [59], deep neural network [78], Bayesian network [60], rnn-lstm [46] | Availability and Integrity | To enhance the protection of network availability and integrity, the main challenge is to provide High detection accuracy and robustness, reducing false alarm rate and detection response time |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guan, T.; Han, Y.; Kang, N.; Tang, N.; Chen, X.; Wang, S. An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles. Sustainability 2022, 14, 5211. https://doi.org/10.3390/su14095211
Guan T, Han Y, Kang N, Tang N, Chen X, Wang S. An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles. Sustainability. 2022; 14(9):5211. https://doi.org/10.3390/su14095211
Chicago/Turabian StyleGuan, Tian, Yi Han, Nan Kang, Ningye Tang, Xu Chen, and Shu Wang. 2022. "An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles" Sustainability 14, no. 9: 5211. https://doi.org/10.3390/su14095211
APA StyleGuan, T., Han, Y., Kang, N., Tang, N., Chen, X., & Wang, S. (2022). An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles. Sustainability, 14(9), 5211. https://doi.org/10.3390/su14095211






