Abstract
The vehicles in the fifth-generation (5G)-enabled vehicular networks exchange the data about road conditions, since the message transmission rate and the downloading service rate have been considerably brighter. The data shared by vehicles are vulnerable to privacy and security issues. Notably, the existing schemes require expensive components, namely a road-side unit (RSU), to authenticate the messages for the joining process. To cope with these issues, this paper proposes a provably secure efficient data-sharing scheme without RSU for 5G-enabled vehicular networks. Our work included six phases, namely: TA initialization (TASetup) phase, pseudonym-identity generation (PIDGen) phase, key generation (KeyGen) phase, message signing (MsgSign) phase, single verification (SigVerify) phase, and batch signatures verification (BSigVerify) phase. The vehicle in our work has the ability to verify multiple signatures simultaneously. Our work not only achieves privacy and security requirements but also withstands various security attacks on the vehicular network. Ultimately, our work also evaluates favourable performance compared to other existing schemes with regards to costs of communication and computation.
1. Introduction
With the continuous increasing demand for fifth-generation (5G) technology, research on the management of vehicle-to-everything (V2X) communication has emerged. Unlike the conventional vehicular networks, the V2X communication provides networks, things, users, and vehicles with reliable connectivity, manageable, operable, controllable, and high-quality [1,2,3,4].
The characteristics of 5G-enabled vehicular networks have a wide high bandwidth and coverage area. Based on data shared by 5G wireless, during peak periods, the data transmission rate can approach 20 Gb/s, while the average data transfer rate is over 100 Mb/s [5,6,7,8]. The capacity of the supported network is 1000 times that of conventional networks, and it can give a more steady connection [9,10,11].
Each vehicle in V2X communication is usually fitted with several expensive sensors, such as cameras of high-resolution, radars of microwave, and lidars of multi-beam, to get comprehensive and reliable data within urban or highway areas [12,13,14,15,16,17]. Moreover, each vehicle has installed wireless devices, namely onboard units (OBUs), to share large amounts of traffic-related information with others and connect technologies of heterogeneous wireless access during the outside world [18,19,20].
There are mainly two categories of data shared by vehicles in V2X communication [21,22]. One is calamities noticed by users, such as nearby hotel ratings and parking lot occupancy. The other is that information is collected by sensors when the vehicle crosses the road environment, such as conditions of the poor road, congestion of traffic, and extreme weather. With these data shared, vehicles offer the driver and passenger a comfortable driving experience, satisfactory transport access, and a safe driving environment.
Given the fact the 5G-enabled vehicular network exploits wireless channels, the data shared by vehicles have security and privacy vulnerabilities [23]. The third-party has the ability to change, delete, and alter the data shared by the vehicle to cause damage to the road environment. Meanwhile, when an attacker exposes any personal data of the user (e.g., location or identity), it will cause criminal charges. Therefore, several scholars have focused on achieving security and privacy requirements for vehicular networks by proposing sophisticated data-sharing schemes.
Nevertheless, these schemes require expensive components called road-side units (RSUs) to cooperate in the mutual authentication phase, which raises the latency of the vehicular networks. Besides, studies [11,24] have proven that a compromised RSU causes leakage of secret information preserved in the RSU.
Hence, the main motivation of this paper is to reduce the massive overhead of performance system in terms of communication and computation costs by proposing a lightweight operations instead of bilinear pair and map-to-point function operations. Our proposed solution does not use RSU to authenticate the vehicle during mutual authentication process. Our proposed solution applies the 5G technology to the fast exchange of messages among vehicles. This work is carried out in our simulation experiments with regards to network simulator (OMNeT++) and traffic simulator (SUMO) to analyze the results. The major contributions of our work can be listed as follows:
- We retrospectively analyze the taxonomy of existing schemes for vehicular networks. Furthermore, some security vulnerabilities of these schemes are highlighted. Then, we present the vehicular network architecture with regard to the system model and security goals.
- We propose a provably secure with an efficient data-sharing scheme for 5G-enabled vehicular networks. To improve efficiency further, our work does not use an expansive component called RSU for the authentication process.
- We implement simulation experiments over a simulation platform (traffic generation simulator and network generation simulator), displaying that the performance efficiency of our work in terms of computation and communication costs has been enhanced compared with the existing works.
The remainder of our work is organized as follows: Section 2 reviews the taxonomy of the existing schemes. Section 3 introduces vehicular network architecture. The six algorithms of the proposed scheme are provided in Section 4. The security analysis and performance comparison of our work are presented in Section 5 and Section 6, respectively. Section 7 shows the conclusions of our work.
2. Related Work
In this section, we retrospectively analyze some related work focusing on data-sharing among vehicles for vehicular networks. The taxonomy of existing schemes is as below. Additionally, we provide a critical analysis of the related work as well.
2.1. Massive Certificate-Based (MCB) Schemes
The fundamental concept of Massive Certificate-Based (MCB) schemes is that TA is responsible for issuing and preloading massive numbers of certificates (roughly 44,000) and their relevant pair-keys (private and public) to participating vehicles. These certificates are assigned based on level of the anonymity to archive security and privacy for vehicular networks.
Several scholars [25,26,27,28,29,30,31,32,33] have proposed MCB schemes for vehicular networks. However, there are three main drawbacks of the MCB schemes: (i) massive certificate arrangement burden for TA owing to the huge pool of anonymous certificates and the relevant pair-keys are needed; (ii) storage arrangement burden owing to limit vehicle storage, and (iii) massive computation and communication overheads owing to the need to verify certification in the investigation methods.
2.2. Group Signature-Based (GSB) Schemes
Chaum and van Heyst [34] first proposed the fundamental concept of group signatures in 1991. The group members are permitted to sign information anonymously on behalf of all members.
Several scholars [35,36,37,38,39] have proposed GSB schemes to overcome the drawbacks arising MCB schemes in a vehicular network. However, there are two main drawbacks of the GSB schemes: (i) the massive size of the Certification revocation list (CRL) owing to the number of blocked vehicle’s number is growing; and (ii) massive overheads of communication and computation owing to the two pairing-based operations that are needed.
2.3. Pseudonym Identity-Based (PIB) Schemes
To overcome the limitations concerning the two above (MCB and GSB) schemes, several scholars proposed Pseudonym Identity-Based (PIB) schemes to provide high-level security in vehicular networks.
In 2015, He et al. [40] first used elliptic curve cryptography rather than pairing-based cryptography to provide efficient performance and secure communications. In the scheme presented by He et al. [40], the private key of the system is saved on each vehicle. Nevertheless, if the vehicle is compromised by an adversary, the whole system is insecure. In 2017, Zhang et al. [41] designed a mutual authentication and preservation scheme to achieve distributed aggregate for the vehicular network. In the scheme designed by Zhang et al. [41], RSU is accountable for producing secret shares for vehicles within its communication area. In the same year, Azees et al. [42] designed an anonymous authentication by helping RSU to secure communication in vehicular networks. In 2018, Pournaghi et al. [43] combined the TPD of RSU and TPD of vehicles to achieve high-level security. In their scheme, the TA is saved with two private keys on the TPD of RSU. Therefore, RSU is responsible for temporarily computing the specific timestamp and generating the signature key of the vehicle. In 2019, Alazzawi et al. [44] designed a pseudonym-based system to achieve a robust integrity scheme. The scheme proposed by Alazzawi et al. [44] has not achieved likability requirements, since only one pseudonym identity is used within all travailing. Furthermore, the system’s secret key is saved on the RSU without using the TPD, which makes it an easy task for the attacker to disclose the key. In the same year, Bayat et al. [45] designed a pseudonym-based to design a RSU-based authentication scheme. RSU is responsible for preloading a pool of signature keys and pseudonym-IDs to each vehicle.
Ali and Li [46] proposed an authentication data-sharing scheme by using RSU to authenticate a large number of messages for vehicle-to-infrastructure (V2I) communication. This scheme replaced map-to-point hash functions by general one-way hash functions to sign message and verify signature. Nevertheless, this scheme uses bilinear pair operations, which are considered time-consuming and complicated.
Al-Shareeda et al. [47] designed a data-sharing scheme by using bilinear pair cryptography and cryptographic hash function. This scheme applies RSU to generate a signature key for the corresponding pseudonym-ID for authentic vehicles. This scheme is vulnerable to a massive overhead of performance costs as it uses complicated operations and is time-consuming.
Alshudukhi et al. [48] applied elliptic curve cryptography to propose an authentication data-sharing scheme for vehicular network. The TA in this scheme saves the system’s private key to each RSU. Once a vehicle wants to join the system, RSU computes and preloads security parameters to vehicles. However, since this scheme uses a large number of multiplication point operations based on ECC, the performance costs is challenged.
Ali et al. [49] constructed a hybrid signcryption based on and public key infrastructure and certificateless cryptosystem to provide security criteria in a single logical phase. This scheme uses bilinear pair operations to sign messages and verify signatures, which causes a massive overhead of performance system.
2.4. Critical Analysis
The summation of related work is as follows. The majority of existing schemes are based on three classes of approaches: (i) Massive certificate-based (MCB) schemes, (ii) Group signature-based (GSB) schemes, and (iii) Pseudonym identity-based (PIB) schemes. The first two approaches required high overhead costs to sign messages and verify signatures, which is not suitable for deployment in vehicular networks. In contracts, the third approach is called pseudonym identity-based (PIB) schemes, proposed by the researcher to address the overhead costs of the system. Our work is based on the third approach to address the existing scheme based on PIB schemes by applying 5G technology and avoiding using RSU.
Since the existing PIB schemes apply RSU to participate authentication process, if they make assumptions that no other things can discover the secrets in a TPD of a vehicle, if a vehicle is corrupted in one RSU, the third party can calculate the RSU’s master key.
3. Vehicular Network Architecture
This section presents the vehicular network architecture with regard to the system model and security goals in our work for 5G-enabled vehicular networks.
3.1. System Model
As presented in Figure 1, the three main entities are called: trusted authority (TA), 5G-base station (5G-BS), and onboard unit (OBU) for 5G-enabled vehicular networks. The main work of these entities is explained in the following steps.
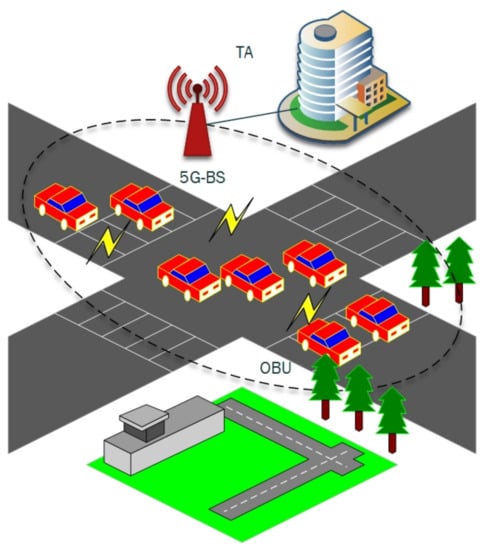
Figure 1.
The System Model of 5G-enabled Vehicular Networks.
- Trusted Authority (TA): TA is trustworthy by all entities in the 5G-enabled vehicular networks and has sufficient resources with regards to storage, communication, and computation. The TA is also in charge of generating the initial parameters of the network and registering the vehicles.
- 5G-base Station (5G-BS): is a radio receiver and has sufficient fast-moving and broad-spectrum in 5g-enabled vehicular networks. The main task of 5G-BS is to connect vehicles and TA. The 5G-BS does not save or compute the data regarding vehicular networks.
- Onboard Unit (OBU): Each enrolled vehicle has one onboard unit (OBU) for sending and receiving information about the surrounding environment. Each OBU has TPD to preserve sensitive data and do computation processes for cryptographic operations. OBU is a considered as a terminal node in networks which enjoys all types of services for 5G technology. Therefore, this work adds a security algorithm in a secure processing service (SPS) layer in each node for the simulation, as shown in Figure 2. The main reason behind using the SPS layer is to implement an authentication process that is higher than the MAC and physical layer.
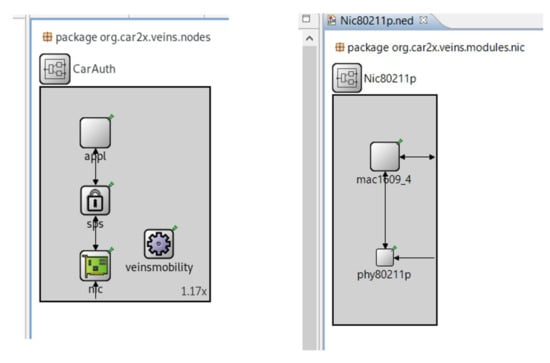 Figure 2. Authentication Node Layers in OMNeT++.
Figure 2. Authentication Node Layers in OMNeT++.
Device-to-Device (D2D) Communication
The D2D wireless network in 5G technology is determined as direct communication among vehicles (terminal nodes) without passing via infrastructure node. In a traditional network, all data must go through the infrastructure node called the base station, even if it is inside the range of D2D communication. As a result, D2D communication can considerably increase the network’s spectral efficiency in this instance.
3.2. Security Goals
In this section, the security requirements should be achieved in our work.
- Authentication and Integrity: To make sure that the message transmitted has been carried out by a registered vehicle. Besides, the message has not been tampered with.
- Privacy Preserving: The original identity of the message broadcasting vehicle must be protected and the message should not disclose the identity to other units so that an attacker cannot utilize their identity for themselves.
- Traceability: When issuing a forged message, the vehicle has the traceable to its signer and that power must lie with the TA.
- Replaying Resistance: Our work should be capable of resisting replay attackers to avoid repeating the message sent by the registered vehicle.
4. Proposed Scheme
To address limitations in the existing schemes, this paper proposes a provably secure efficient data-sharing scheme for 5G-enabled vehicular networks. Our work has six phases, namely: TA initialization (TASetup) phase, pseudonym-ID generation (PIDGen) phase and key generation (KeyGen) phase, message signing (MsgSign) phase, single verification (SigVerify) phase, and batch signatures verification (BSigVerify) phase.
Our work is based on the scheme proposed by [50]. However, unlike the scheme proposed by [50], the proposed scheme uses 5G-BS to provide high-efficiency data-sharing among vehicles. This paper carried out the simulation experiments with regard to network simulators and traffic simulators (SUMO) to analyze the results of these phases. Furthermore, the proposed scheme does not need an expensive component (RSU) to authenticate the messages. Vehicles in our work can renew the security groups by sending a request to TA through 5G-BS wirelessly, which avoids repeat parameters used. The proposed scheme should be divided into the following phases:
- TASetup: The TA executes TASetup phase to obtain security parameter . The network parameters and the private (secret) keys and are returned on this algorithm. The system parameters are considered as an implicit input to all methods explained below.
- PIDGen and KeyGen: The TA executes the PIDGen and KeyGen algorithms to return the pseudonym-ID and the signature key , respectively.
- MsgSign: The registered vehicle executes MsgSign algorithm. The safety-related message for a pseudonym-ID is taken as input for returning the signature .
- SigVerify: The verifying vehicle executes SigVerify algorithm. Once receiving a signature on a safety-related message for a pseudonym-ID from a vehicle , if the signature is legitimate, it results true; otherwise, it outputs false.
- BSigVerify: The verifying vehicle executes SigVerify algorithm. Once receiving a batch of n signature () on n safety-related messages () for n pseudonym-IDs () from n vehicles () simultaneously, if the signatures () are legitimate, it results true; otherwise, it results false.
4.1. TASetup
The TA executes the TASetup algorithm to return the network parameters and the private (secret) keys and as the following steps.
- Given a network parameter , TA selects a generator g based on a group G of the order prime q.
- Four cryptographic general hash functions, , , and , are chosen by TA and set as , , and .
- TA sets the randomly picked number as a private (secret) key, then measures its corresponding public key for private key extraction.
- TA sets the randomly picked number as a private (secret) key, then measures its corresponding public key for traceability.
- The network public parameters are set as , , . Note that private (secret) keys and are only known to TA.
Since our work is based on 5G technology, it is an easy task to renew the groups to avoid repeating them during the next steps. The renew process executes between vehicle and TA through 5G-BS.
4.2. PIDGen and KeyGen
To achieve mutual authentication and privacy-preservation in our work, the pseudonym-IDs () that are particularly concerned with the relevant original identities should be used by following these steps:
- User submits the original identity of his/her vehicle to TA via secure communication. TA is responsible for testing the validity of .
- Once confirmed the authenticity of , TA sets a group of the randomly selected values {, , …} as a private key and then measures the relevant public keys , where and .
- TA then computes a group of for vehicle as , where and .
- Once calculating the , TA sets randomly selected values as a signature keys, where and .
- Ultimately, TA preloads the network parameters and groups {, , } to TPD of vehicle through a secure channel.
4.3. MsgSign
Prior to sending the safety-related messages to public channel in 5G-enabled vehicular network, vehicle signs them to achieve integrity and authentication. The message-signature tuples on one message by participating vehicle is demonstrated as the following steps.
- Vehicle sets the randomly selected a signature key , a relevant and pseudonym-ID from the groups , , and , respectively.
- Vehicle sets the randomly picked value and calculates .
- Vehicle signs message as , where is a freshness timestamp.
- Vehicle computes signature .
- Finally, vehicle broadcasts the message-signature tuples to others in 5G-enabled vehicular networks.
4.4. SigVerify
Once the verifying vehicle has acquired a single tuple signed by , the following steps should be executed.
- Upon receiving the message-signature tuples , the verifying vehicle tests the brightness of timestamp . Verifying vehicle rejects the message if it is not valid.
- If is fresh, verifying vehicle then calculates and .
- Finally, verifying vehicle checks whether Equation (1) holds or not.
If Equation (1) is achieved, then the verifying vehicle accepts the message ; otherwise, the rejects it. The correctness of the SigVerify’s Equation is explained as follows:
4.5. BSigVerify
Upon receiving n message-signature tuples , ,…, simultaneously. Verifying vehicle uses the system public parameters , , to verify batch messages as the following steps.
- Verifying vehicle tests the validity of , and drops the messages if some of them are not valid.
- Verifying vehicle sets the randomly selected n values , where for and is typically acceptable [51].
- Verifying vehicle then calculates and , where .
- Finally, verifying vehicle checks whether Equation (2) holds or not.
If Equation (2) is achieved, then the verifying vehicle accepts the messages; otherwise, the discards them. The correctness of the BSigVerify’s Equation is explained as follows:
5. Security Analysis
In this section, the security definition, provable security, and security level of our work are analyzed in the following subsections.
5.1. Security Definition
The security model for the proposed scheme is provided by a game activated between a polynomial-time adversary and a challenger . In the model, adversary can access polynomially bounded queries oracle adaptively to challenger as the following steps.
Setup: In this process, a TASetup algorithm of the 5G-enabled vehicular networks is simulated. runs the TASetup algorithm to compute the network parameters and the private (secret) keys and . Once receiving this query, sends to .
When sending the information query , sets the randomly selected number and saves (, ) in the list . Then, returns to .
GenerateVeh: When receiving the original identity of vehicle , computes pseudonym-IDs and signature keys of vehicle . Then saves {, , } in the list .
CorruptVeh: When receiving the original identity of vehicle , sends pseudonym-IDs and signature keys of vehicle to .
SignatureGen: When submitting pseudonym-ID and message M by , produces and returns the relevant the message-signature tuples to .
Upon performing the above queries, forges the signature of safety-related message related with original identity of vehicle .
Forgery: When the below steps are achieved, wins the game.
- is a legal signature of the message .
- signature of has not been queried in the CorruptVeh and SignatureGen.
Let the function indicate the advantage of in breaking the proposed scheme .
Definition 1.
The proposed scheme Ω for 5G-enabled vehicular networks is chosen-message and chosen-identity secure, when the function is negligible for .
5.2. Provable Security
According to Definition 1, the selected message and chosen identity of our work utilizing the random oracle model (ROM) are analyzed. Figure 3 shows a game between a challenger and an attacker .
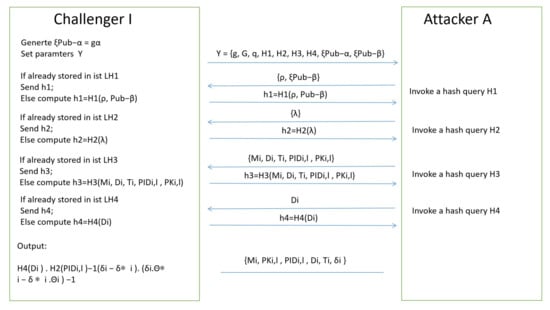
Figure 3.
A game between a challenger and an attacker .
Theorem 1.
Supposing that the underlying DLP is unsolvable, the proposed scheme for 5G-enabled vehicular networks is secure in the ROM.
Proof.
Suppose that an attacker of polynomial-time can forge a legal the message-signature tuples by an advantage of non-negligible , then challenger could resolve DLP with advantage of non-negligible via working the as a subroutine. Consider be an example of the DLP, and main work of the is to calculate . Initially, produces , , to . Then runs oracle-queries adaptively modeled by as the following steps. □
Oracle initializes the form of in the list firstly. Once a query is issued by , tests whether the form of existing in the list . If exists, produces to , otherwise, sets the randomly selected nonce , produces to to and puts to the list .
Oracle initializes the form of in the list firstly. Once a query is issued by , tests whether the form of existing in the list . If exists, produces to , otherwise, sets the randomly selected nonce , produces to to and puts to the list .
Oracle initializes the form of in the list firstly. Once a query is issued by , tests whether the form of existing in the pool . If exists, produces to , otherwise, sets the randomly selected nonce , produces to to and puts to the list .
Oracle initializes the form of in the list firstly. Once a query is issued by , tests whether the form of existing in the list . If exists, produces to , otherwise, sets the randomly selected nonce , produces to to and puts to the list .
Oracle(GenerateVeh): initializes the form of in the list firstly. Once sending a query to by , tests whether the form of existing in the pool . If exists, results to , otherwise, runs the following two points.
- If , sets the randomly selected three values , and , calculates and holds . saves , and in the list , and respectively. Finally, returns to .
- If , sets the randomly selected three values , and , calculates , and . saves , and in the list , and respectively. Ultimately, results to .
Oracle(CorruptVeh): invokes from and produces to .
Oracle(SignatureGen): When receiving a query with pseudonym-ID and message from , sets the randomly selected three values , and and calculates , . saves and in the list and , respectively. Finally, returns the message-signature tuples to .
At last, outputs the message-signature tuples to . If , then ends the game. verifies whether Equation (3) holds.
When it is wrong, then breaks the game by using forking lemma in [52]. When the attempts the process with a various chosen , then can result in another valid message-signature tuple with the advantage . Therefore, it obtains the following equation.
Thus, according to the above two equations, it can be respectively concluded as follows.
- ,
- ,
Based on the above two equations, results . as the output of the DLP. The following events to resolve the DLP by are analyzed.
- indicates the event that = .
- indicates the event that can fabricate two legal signatures.
Let indicates the value of oracle queries. Therefore, it outputs , . The advantage and that could resolve the DLP is as follows.
=
Thus, resolves the DLP with an advantage of non-negligible owing to the bounded and non-negligible . Hence, this completes the security proof for the proposed scheme.
5.3. Security Requirements
Our work should be achieved the security goals (Section 3.2) concerning security requirements as follows.
- Authentication and Integrity: Once the vehicle sending the message-signature tuples to others, the checker in our work checks the correctness for testing the tuple’s integrity and authenticity. According to Theorem 1 in Section 5.2, there is no attacker of polynomial-time that could impersonate/generate a legitimate message if the DLP is hardness.
- Privacy Preserving: In the PIDGen and KeyGen phase, the vehicle’s true identity is hidden in the by TA, where and . To disclose the vehicle’s true identity from , requires to calculate based on . Nevertheless, this process contradicts the hardness of CDHP. Thus, our work satisfies privacy preserving.
- Traceability: By tracing the origin of messages sent, the TA is able to revoke and block the enrollment of any attacker that attempts to broadcast forge messages or disturb the system in 5G-enable vehicular networks. Once receiving the forge message, the vehicle reports it to the TA to verify its aid and, if available in the list, calculates the as utilizing master key . Thus, the function of traceability is provided by our work.
- Replaying Resistance: Our work can resist replay attacks by utilizing timestamp in the message-signature tuples . It denotes the signing time of tuples. Let is the arrival time of the message. It requires to verify if . When this condition holds, then there is no replay attacks.
5.4. Security Level
In this section, we show the security level of our work compared to the existing schemes in terms of privacy and security requirements. Therefore, we summarize and compare the security and piracy requirements of our work with the existing works He et al. [40], Azees et al. [42], Pournaghi et al. [43], and Bayat et al. [45] in Table 1. Thereby, all related works require RSU aid. Schemes of Azees et al. [42] and Bayat et al. [45] are vulnerable to replay attacks. Azees et al.’s scheme [42] is not satisfied by mutual authentication. As a result of Table 1, it can be concluded that our work achieves better security properties as compared to other works tabulated in that table.

Table 1.
Comparison of Security Properties.
6. Performance Comparison
In this section, the performance comparison of our work is evaluated with regard to costs of communication and computation. Meanwhile, the performance of our work is compared with schemes He et al. [40], Azees et al. [42], Pournaghi et al. [43], and Bayat et al. [45] via an experiment of simulation.
As presented in Figure 4, this work utilizes traffic generation simulator and network generation simulator such as OpenStreetMap [53], GatcomSUMO [54], SUMO [55] OMNeT++ [56], VEINS [57], Simu5G [58], and MIRACL [59,60] to execute experiments of simulation for 5G-enabled vehicular networks. OpenStreetMap is a very real trusted map website. GatcomSUMO is a java-based program utilized to facilitate the connection between the generation of traffic (SUMO) and the generation of the network (OMNeT++). SUMO is a road traffic simulation with a highly portable. OMNeT++ is a open-architecture for networks. Veins are joined with the generation of road traffic and the generation of networks. INET is a framework OMNeT++ suited for wired, wireless, and mobile networks. Simu5G is suited for a 5G-enabled vehicular network. MIRACL is a cryptographic library utilized to run operations based on cryptography algorithms. Table 2 lists the parameters of the simulation experiment.
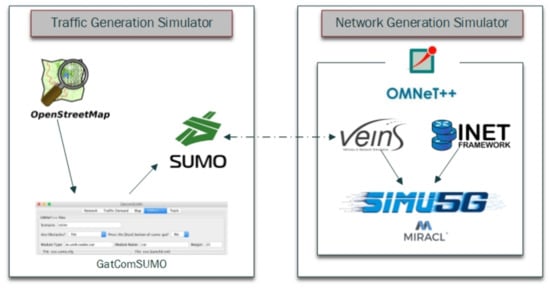
Figure 4.
Simulation Experiments for 5G-enabled Vehicular Networks.

Table 2.
Parameters of Simulation Experiment.
6.1. Computation Costs
For a fair evaluation, the notations with the costs of the execution time of some cryptographic operations are tabulated in Table 3. This paper considers the computation overheads of generating pseudonym-IDs, signed message, and verification process, and compares them with existing schemes in Table 4.

Table 3.
Notation with its Costs of Execution Time.

Table 4.
The Cost of Computation of Five Authentication Schemes.
In the MsgSign phase of the scheme of He et al. [40], the user needs to run three operations with regard to ECC scalar multiplication and three operations with regard to general hash function. Hence, the cost of computation of the MsgSign phase is ms. In the SigVerify phase of He et al.’s scheme [40], the user needs to run five operations with regard to scalar multiplication, one operation with regard to addition point and two operations with regard to hash function. Hence, the cost of computation of the SigVerify phase is ms. In the BSigVerify phase of He et al.’s scheme [40], the vehicle needs to run (2 + 3n) operations with regard to scalar multiplication, (2n − 1) operations with regard to addition point and (2n) operations with regard to hash function. Hence, the cost of computation of the BSigVerify phase is ms.
In the MsgSign phase of Azees et al.’s scheme [42], the user needs to run one operation with regard to BP scalar multiplication and one operation with regard to general hash function. Hence, the cost of computation of the MsgSign phase is ms. In the SigVerify phase of Azees et al.’s scheme [42], the user needs to run two operations with regard to bilinear pair, five operations with regard to scalar multiplication, and two operations with regard to addition point. Hence, the cost of computation of the SigVerify phase is ms. In the BSigVerify phase of Azees et al.’s scheme [42], the user needs to run (1 + n) operations with regard to bilinear pair, (5n) operations with regard to scalar multiplication, and (2n) operations with regard to addition point. Hence, the cost of computation of the BSigVerify phase is ms.
In the MsgSign phase of Pournaghi et al.’s scheme [43], the user needs to run three operations with regard to scalar BP multiplication, one operation with regard to addition point, two operations with regard to general hash function, and one operation with regard to MapToPoint hash function. Hence, the cost of computation of the MsgSign phase is ms. In the SigVerify phase of the Pournaghi et al.’s scheme [43], the user needs to run three operations with regard to bilinear pair, one operation with regard to scalar multiplication, and one operation with regard to MapToPoint hash function. Hence, the cost of computation of the SigVerify phase is ms. In the BSigVerify phase of Pournaghi et al.’s scheme [43], the user needs to run three operations with regard to bilinear pair, (n) operations with regard to scalar multiplication, and (n) operations with regard to MapToPoint hash function. Hence, the cost of computation of the BSigVerify phase is ms.
In the MsgSign phase of Bayat et al.’s scheme [45], the user needs to run only one operation with regard to MapToPoint hash function. Hence, the cost of computation of the MsgSign phase is ms. In the SigVerify phase of the Bayat et al.’s scheme [45], the user needs to run three operations with regard to bilinear pair, one operation with regard to scalar multiplication, and one operation with regard to MapToPoint hash function. Hence, the cost of computation of the SigVerify phase is ms. In the BSigVerify phase of Bayat et al.’s scheme [45], the user needs to run three operations with regard to bilinear pair, (n) operations with regard to scalar multiplication, and (n) operations with regard to MapToPoint hash function. Hence, the cost of computation of the BSigVerify phase is ms.
In the MsgSign phase of our work, the user needs to run one operation with regard to ECC scalar multiplication and two operations with regard to general hash function. Hence, the cost of computation of the MsgSign phase is ms. In the SigVerify phase of our work, the vehicle needs to run four operations with regard to scalar multiplication, one operation with regard to addition point and two operations with regard to hash function. Hence, the cost of computation of the SigVerify phase is ms. In the BSigVerify phase of our work, the user needs to run (2 + 2n) operations with regard to scalar multiplication, (n) operations with regard to addition point, and (2n) operations with regard to hash function. Hence, the cost of computation of the BSigVerify phase is ms.
Furthermore, the entire time is based on the runtime of each cryptographic operation. The elapsed time (ET) between the exit and entrance is the overhead cost.
where, M is the message number, is the entrance time of message i, and is the exit time of message i. Figure 5 and Figure 6 depict the average time to sign and verify a message between the proposed and scheme of He et al. [40]. The main reason for comparing our work against only He et al. [40] is to the same cryptography operations (e.g., ECC) used to sign message and verify signature. Additionally, the cost of He et al.’s scheme [40] is most efficient compared with other schemes according to Table 4. The results of the experimental methods show that our work is much more efficient than existing methods.
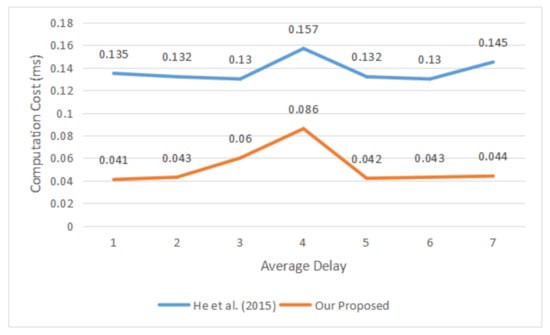
Figure 5.
Average Time to Sign Message.
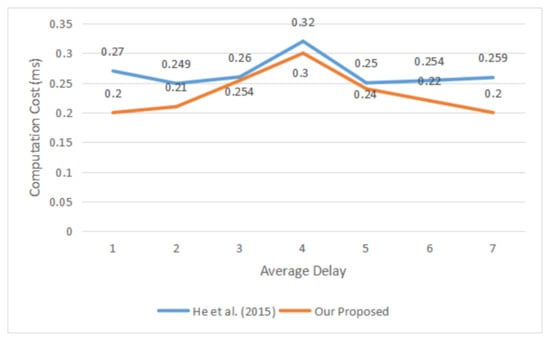
Figure 6.
Average Delay to Verify Message.
6.2. Communication Costs
In this section, the primary concentrate is the cost of communication included in the timestamps, signatures, and pseudonym-IDs for the message-signature tuples. Table 5 shows the sizes of cryptographic elements used for communication costs.

Table 5.
The Sizes of Elements Used.
In the scheme of He et al. [40], the signer broadcasts the message-signature tuple to the recipient, where , and is a timestamp. Consequently, the cost of communication is 3 × 320 + 160 + 32 = 1152 bits. In the scheme of Azees et al. [42], the signer broadcasts the message-signature tuple to the recipient, where , , , c is a hash operation. Consequently, the cost of communication is 6 × 1024 + 3 × 160 + 32 = 6656 bits. In Pournaghi et al.’s scheme [43], the signer sends the message-signature tuple to the recipient, where and . Consequently, the cost of communication is 2 × 1024 + 2 × 160 = 2368 bits. In Bayat et al.’s scheme [45] the signer broadcasts the message-signature tuple to the recipient, where and . Consequently, the cost of communication is 2 × 1024 + 1 × 160 = 2208 bits. In our work, the signer sends the message-signature tuple to others in 5G-enabled vehicular networks, where , is the timestamp and is a hash operations. Consequently, the cost of communication is 2 × 320 + 2 × 160 + 32 = 992 bits.
Communication cost comparisons for all works are presented in Table 6. Similar to the cost of computation, our work is significantly better than other existing works, as presented in Figure 7.

Table 6.
The Costs of Communication Comparison.
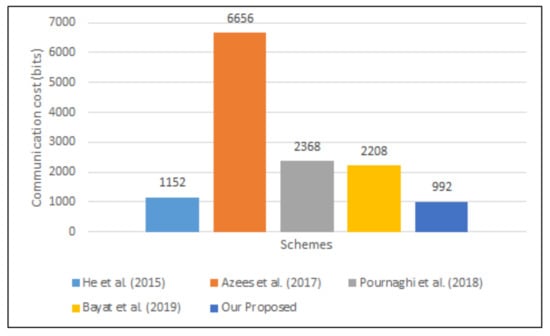
Figure 7.
The Costs of Communication Comparison.
7. Conclusions
This paper proposed a provably secure with efficient data-sharing scheme without using RSU for 5G-enabled vehicular networks. Our work does not use an expansive component called RSU for the authentication process to improve efficiency further. Furthermore, the provable security displayed that our work is secure against adaptive selected-message attacks based on the random oracle model. Furthermore, our work not only achieves the requirements of security (message authentication and integrity, identity privacy preservation, and traceability) but also resists the security attacks such as replay attacks. This work carried out our simulation experiments with regard to network simulator (OMNeT++) and traffic simulator (SUMO) to analyze the results. Lastly, this paper reduces the computation cost to sign the message, verify signature, and batch signature verification by 66.67%, 19.98%, and 20.01%, respectively. This paper reduces the communication overhead the message-signature-tuple size by 13.89%.
The major limitation the proposed approach is uses large numbers (e.g., four operations) of ECC-based multiplication point to verify messages sent among vehicles. A fast-moving vehicle requires fast verification by using lightweight operations to verify messages. Therefore, in future work, it will contain the design of a fog computing-based authentication scheme that uses an operation based on ECC cryptographic algorithm in 5G-enabled vehicular networks.
Author Contributions
Conceptualization, writing—review and editing, M.A.A.-S.; writing—original draft preparation, investigation, supervision, S.M.; funding acquisition, software, visualization, B.A.M.; methodology, funding acquisition, resources, Z.G.A.-M.; project administration, funding acquisition, software, A.Q.; funding acquisition, investigation, resources, A.J.A.; data curation, software, visualization, G.A.; visualization, methodology, visualization, supervision, A.A.S.; and investigation, methodology, validation, K.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research has been funded by the Scientific Research Deanship at the University of Ha’il, Saudi Arabia, through project number RG-21098.
Institutional Review Board Statement
Not Applicable.
Informed Consent Statement
Not Applicable.
Data Availability Statement
Not Applicable.
Acknowledgments
We would like to acknowledge the Scientific Research Deanship at the University of Ha’il, Saudi Arabia, for funding this research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Al-Mekhlafi, Z.G.; Qtaish, A.; Alzahrani, A.J.; Alshammari, G.; Sallam, A.A.; Almekhlafi, K. CM-CPPA: Chaotic Map-Based Conditional Privacy-Preserving Authentication Scheme in 5G-Enabled Vehicular Networks. Sensors 2022, 22, 5026. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S. Man-In-The-Middle Attacks in Mobile Ad Hoc Networks (MANETs): Analysis and Evaluation. Symmetry 2022, 14, 1543. [Google Scholar] [CrossRef]
- Cheng, X.; Chen, C.; Zhang, W.; Yang, Y. 5G-enabled cooperative intelligent vehicular (5GenCIV) framework: When Benz meets Marconi. IEEE Intell. Syst. 2017, 32, 53–59. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Khalil, A.; Hasbullah, I.H. Security and Privacy Schemes in Vehicular Ad-Hoc Network With Identity-Based Cryptography Approach: A Survey. IEEE Access 2021, 9, 121522–121531. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Towards identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Access 2021, 9, 113226–113238. [Google Scholar] [CrossRef]
- Prasad, K.S.V.; Hossain, E.; Bhargava, V.K. Energy efficiency in massive MIMO-based 5G networks: Opportunities and challenges. IEEE Wirel. Commun. 2017, 24, 86–94. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Al-Mekhlafi, Z.G.; Qtaish, A.; Alzahrani, A.J.; Alshammari, G.; Sallam, A.A.; Almekhlafi, K. Chebyshev Polynomial-Based Scheme for Resisting Side-Channel Attacks in 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 5939. [Google Scholar] [CrossRef]
- Fascista, A.; Coluccia, A.; Wymeersch, H.; Seco-Granados, G. Downlink single-snapshot localization and mapping with a single-antenna receiver. IEEE Trans. Wirel. Commun. 2021, 20, 4672–4684. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks. Sensors 2022, 22, 1696. [Google Scholar] [CrossRef] [PubMed]
- Dong, P.; Zheng, T.; Yu, S.; Zhang, H.; Yan, X. Enhancing vehicular communication using 5G-enabled smart collaborative networking. IEEE Wirel. Commun. 2017, 24, 72–79. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Password-Guessing Attack-Aware Authentication Scheme Based on Chinese Remainder Theorem for 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 1383. [Google Scholar] [CrossRef]
- Alazzawi, M.A.; Al-behadili, H.A.; Srayyih Almalki, M.N.; Challoob, A.L.; Al-shareeda, M.A. ID-PPA: Robust identity-based privacy-preserving authentication scheme for a vehicular ad-hoc network. In Proceedings of the International Conference on Advances in Cyber Security, Penang, Malaysia, 8–9 December 2020; Springer: Singapore, 2020; pp. 80–94. [Google Scholar]
- Al Shareeda, M.; Khalil, A.; Fahs, W. Realistic heterogeneous genetic-based RSU placement solution for V2I networks. Int. Arab J. Inf. Technol. 2019, 16, 540–547. [Google Scholar]
- Hamdi, M.M.; Mustafa, A.S.; Mahd, H.F.; Abood, M.S.; Kumar, C.; Al-shareeda, M.A. Performance Analysis of QoS in MANET based on IEEE 802.11 b. In Proceedings of the 2020 IEEE International Conference for Innovation in Technology (INOCON), Bangalore, India, 6–8 November 2020; pp. 1–5. [Google Scholar]
- Hamdi, M.M.; Audah, L.; Rashid, S.A.; Al Shareeda, M. Techniques of Early Incident Detection and Traffic Monitoring Centre in VANETs: A Review. J. Commun. 2020, 15, 896–904. [Google Scholar] [CrossRef]
- Al-shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H.; Khalil, A.; Alazzawi, M.A.; Al-Hiti, A.S. Proposed efficient conditional privacy-preserving authentication scheme for v2v and v2i communications based on elliptic curve cryptography in vehicular ad hoc networks. In Proceedings of the International Conference on Advances in Cyber Security, Penang, Malaysia, 8–9 December 2020; Springer: Singapore, 2020; pp. 588–603. [Google Scholar]
- Al-shareeda, M.A.; Alazzawi, M.A.; Anbar, M.; Manickam, S.; Al-Ani, A.K. A Comprehensive Survey on Vehicular Ad Hoc Networks (VANETs). In Proceedings of the 2021 International Conference on Advanced Computer Applications (ACA), Maysan, Iraq, 25–26 July 2021; pp. 156–160. [Google Scholar]
- Xu, W.; Zhou, H.; Cheng, N.; Lyu, F.; Shi, W.; Chen, J.; Shen, X. Internet of vehicles in big data era. IEEE/CAA J. Autom. Sin. 2017, 5, 19–35. [Google Scholar] [CrossRef]
- Cheng, J.; Cheng, J.; Zhou, M.; Liu, F.; Gao, S.; Liu, C. Routing in internet of vehicles: A review. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2339–2352. [Google Scholar] [CrossRef]
- Bai, F.; Krishnan, H. Reliability analysis of DSRC wireless communication for vehicle safety applications. In Proceedings of the 2006 IEEE intelligent transportation systems conference, Toronto, ON, Canada, 17–20 September 2006; pp. 355–362. [Google Scholar]
- Yang, Q.; Zhu, B.; Wu, S. An architecture of cloud-assisted information dissemination in vehicular networks. IEEE Access 2016, 4, 2764–2770. [Google Scholar] [CrossRef]
- Cui, J.; Ouyang, F.; Ying, Z.; Wei, L.; Zhong, H. Secure and efficient data sharing among vehicles based on consortium blockchain. IEEE Trans. Intell. Transp. Syst. 2021, 23, 8857–8867. [Google Scholar] [CrossRef]
- Lai, C.; Lu, R.; Zheng, D.; Shen, X. Security and privacy challenges in 5G-enabled vehicular networks. IEEE Netw. 2020, 34, 37–45. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Chang, V.; Deborah, J.; Balusamy, B. Computationally efficient privacy preserving authentication and key distribution techniques for vehicular ad hoc networks. Clust. Comput. 2017, 20, 2439–2450. [Google Scholar] [CrossRef]
- Cincilla, P.; Hicham, O.; Charles, B. Vehicular PKI Scalability-consistency Trade-offs in Large Scale Distributed Scenarios. In Proceedings of the 2016 IEEE Vehicular Networking Conference (VNC), Columbus, OH, USA, 8–10 December 2016; pp. 1–8. [Google Scholar]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An efficient pseudonymous authentication-based conditional privacy protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]
- Joshi, A.; Gaonkar, P.; Bapat, J. A Reliable and Secure Approach for Efficient Car-to-Car Communication in Intelligent Transportation Systems. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 1617–1620. [Google Scholar]
- Lu, R.; Lin, X.; Luan, T.H.; Liang, X.; Shen, X. Pseudonym changing at social spots: An effective strategy for location privacy in vanets. IEEE Trans. Veh. Technol. 2011, 61, 86–96. [Google Scholar] [CrossRef]
- Thenmozhi, T.; Somasundaram, R. Pseudonyms based blind signature approach for an improved secured communication at social spots in VANETs. Wirel. Pers. Commun. 2015, 82, 643–658. [Google Scholar] [CrossRef]
- Rajput, U.; Abbas, F.; Oh, H. A hierarchical privacy preserving pseudonymous authentication protocol for VANET. IEEE Access 2016, 4, 7770–7784. [Google Scholar] [CrossRef]
- Asghar, M.; Doss, R.R.M.; Pan, L. A Scalable and Efficient PKI based Authentication Protocol for VANETs. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, Australia, 21–23 November 2018; pp. 1–3. [Google Scholar]
- Förster, D.; Kargl, F.; Löhr, H. PUCA: A pseudonym scheme with user-controlled anonymity for vehicular ad-hoc networks (VANET). In Proceedings of the 2014 IEEE Vehicular Networking Conference (VNC), Paderborn, Germany, 3–5 December 2014; pp. 25–32. [Google Scholar]
- Sun, Y.; Zhang, B.; Zhao, B.; Su, X.; Su, J. Mix-zones optimal deployment for protecting location privacy in VANET. Peer Peer Netw. Appl. 2015, 8, 1108–1121. [Google Scholar] [CrossRef]
- Chaum, D.; Van Heyst, E. Group signatures. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1991; pp. 257–265. [Google Scholar]
- Shao, J.; Lin, X.; Lu, R.; Zuo, C. A Threshold Anonymous Authentication Protocol for VANETs. IEEE Trans. Veh. Technol. 2015, 65, 1711–1720. [Google Scholar] [CrossRef]
- Alimohammadi, M.; Pouyan, A.A. Sybil attack detection using a low cost short group signature in VANET. In Proceedings of the 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC), Rasht, Iran, 8–10 September 2015; pp. 23–28. [Google Scholar]
- Zhang, L.; Wu, Q.; Qin, B.; Domingo-Ferrer, J.; Liu, B. Practical secure and privacy-preserving scheme for value-added applications in VANETs. Comput. Commun. 2015, 71, 50–60. [Google Scholar] [CrossRef]
- Cui, J.; Wang, Y.; Zhang, J.; Xu, Y.; Zhong, H. Full Session Key Agreement Scheme Based on Chaotic Map in Vehicular Ad hoc Networks. IEEE Trans. Veh. Technol. 2020, 69, 8914–8924. [Google Scholar] [CrossRef]
- Lim, K.; Tuladhar, K.M.; Wang, X.; Liu, W. A scalable and secure key distribution scheme for group signature based authentication in VANET. In Proceedings of the 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York City, NY, USA, 19–21 October 2017; pp. 478–483. [Google Scholar]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Domingo-Ferrer, J.; Qin, B.; Hu, C. Distributed aggregate privacy-preserving authentication in VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 18, 516–526. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deboarh, L.J. EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Pournaghi, S.M.; Zahednejad, B.; Bayat, M.; Farjami, Y. NECPPA: A novel and efficient conditional privacy-preserving authentication scheme for VANET. Comput. Networks 2018, 134, 78–92. [Google Scholar] [CrossRef]
- Alazzawi, M.; Lu, H.; Yassin, A.; Chen, K. Efficient Conditional Anonymity with Message Integrity and Authentication in a Vehicular Ad hoc Network. IEEE Access 2019, 7, 71424–71435. [Google Scholar] [CrossRef]
- Bayat, M.; Pournaghi, M.; Rahimi, M.; Barmshoory, M. NERA: A New and Efficient RSU based Authentication Scheme for VANETs. Wirel. Networks 2019, 26, 1–16. [Google Scholar] [CrossRef]
- Ali, I.; Li, F. An efficient conditional privacy-preserving authentication scheme for Vehicle-To-Infrastructure communication in VANETs. Veh. Commun. 2020, 22, 100228. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. SE-CPPA: A Secure and Efficient Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. Sensors 2021, 21, 8206. [Google Scholar] [CrossRef] [PubMed]
- Alshudukhi, J.S.; Al-Mekhlafi, Z.G.; Mohammed, B.A. A Lightweight Authentication With Privacy-Preserving Scheme for Vehicular Ad Hoc Networks Based on Elliptic Curve Cryptography. IEEE Access 2021, 9, 15633–15642. [Google Scholar] [CrossRef]
- Ali, I.; Chen, Y.; Ullah, N.; Afzal, M.; Wen, H. Bilinear pairing-based hybrid signcryption for secure heterogeneous vehicular communications. IEEE Trans. Veh. Technol. 2021, 70, 5974–5989. [Google Scholar] [CrossRef]
- Li, J.; Choo, K.K.R.; Zhang, W.; Kumari, S.; Rodrigues, J.J.; Khan, M.K.; Hogrefe, D. EPA-CPPA: An efficient, provably-secure and anonymous conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Veh. Commun. 2018, 13, 104–113. [Google Scholar] [CrossRef]
- Liu, J.K.; Yuen, T.H.; Au, M.H.; Susilo, W. Improvements on an authentication scheme for vehicular sensor networks. Expert Syst. Appl. 2014, 41, 2559–2564. [Google Scholar] [CrossRef]
- Pointcheval, D.; Stern, J. Security arguments for digital signatures and blind signatures. J. Cryptol. 2000, 13, 361–396. [Google Scholar] [CrossRef]
- Haklay, M.; Weber, P. Openstreetmap: User-generated street maps. IEEE Pervasive Comput. 2008, 7, 12–18. [Google Scholar] [CrossRef]
- Abenza, P.P.G.; Malumbres, M.P.; Peral, P.P. 10 GatcomSUMO: A Graphical Tool for VANET Simulations Using SUMO and OMNeT+. In Proceedings of the SUMO 2017–Towards Simulation for Autonomous Mobility, Berlin, Germany, 8–10 May 2017; p. 113. [Google Scholar]
- Behrisch, M.; Bieker, L.; Erdmann, J.; Krajzewicz, D. SUMO–simulation of urban mobility: An overview. In Proceedings of the SIMUL 2011, The Third International Conference on Advances in System Simulation, ThinkMind, Barcelona, Spain, 23–29 October 2011. [Google Scholar]
- Varga, A. Discrete event simulation system. In Proceedings of the European Simulation Multiconference (ESM’2001), Prague, Czech Republic, 7–9 June 2001; pp. 1–7. [Google Scholar]
- Sommer, C.; German, R.; Dressler, F. Bidirectionally coupled network and road traffic simulation for improved IVC analysis. IEEE Trans. Mob. Comput. 2010, 10, 3–15. [Google Scholar] [CrossRef]
- Nardini, G.; Sabella, D.; Stea, G.; Thakkar, P.; Virdis, A. Simu5G–An OMNeT++ library for end-to-end performance evaluation of 5G networks. IEEE Access 2020, 8, 181176–181191. [Google Scholar] [CrossRef]
- Scott, M. MIRACL-A Multiprecision Integer and Rational Arithmetic C/C++ Library. Available online: http://www.shamus.ie (accessed on 2003).
- Ltd, S.S. Multi Precision Integer and Rational Arithmetic Cryptographic Library (MIRACL). Available online: http://www.certivox.com/miracl/ (accessed on 2018).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).