Abstract
The rapid devolopment of Internet of Vehicles (IoV) and Autonomous Connected Vehicles (ACVs) has increased the complexity of in-vehicle networks, exposing security vulnerabilities in traditional Controller Area Network (CAN) systems. CAN security faces dual challenges: stringent computational constraints imposed by automotive functional safety requirements and the impracticality of protocol modifications in multi-device networks. To address this, we propose a lightweight intrusion detection algorithm leveraging information entropy to analyze side-channel CAN message ID distributions. Evaluated in terms of detection accuracy, false positive rate, and sensitivity to bus load variations, the algorithm was implemented on an NXP MPC-5748G embedded platform through the AutoSar Framework. Experimental results demonstrate robust performance under low computational resources, achieving high detection accuracy with high recall (>80%) even at 10% bus load fluctuation thresholds. This work provides a resource-efficient security framework compatible with existing CAN infrastructures, effectively balancing attack detection efficacy with the operational constraints of automotive embedded systems.
1. Introduction
The rapid advancement of Internet of Vehicles (IoV) and Autonomous Connected Vehicles (ACVs) has intensified cybersecurity challenges in automotive systems. Modern ACVs rely heavily on Controller Area Network (CAN) buses for communications between electronic control units (ECUs), yet their open architecture renders them vulnerable to attacks [1]. While existing solutions predominantly employ fixed-rule detection or machine learning models [2], they face critical limitations in real-time responsiveness or computational complexity, particularly for resource-constrained automotive embedded systems.
This work addresses CAN bus security by proposing an information entropy-based intrusion detection algorithm that combines statistical hypothesis testing with adaptive threshold optimization. The methodology capitalizes on the stability of CAN message ID frequency distributions under normal conditions, quantified through Shannon entropy, to detect malicious traffic patterns. Building upon foundational work in [3], our approach introduces two key innovations: (1) a two-tailed statistical test leveraging baseline entropy distribution to minimize false positives and (2) Receiver Operating Characteristic (ROC) curve-guided threshold selection to balance sensitivity and specificity.
Current research presents diverging perspectives on optimal detection methods. Cryptographic solutions [4] theoretically ensure message authenticity but face deployment barriers due to legacy ECU compatibility issues. Deep learning approaches [3] achieve high accuracy in lab environments yet demand impractical computational resources. Voltage fingerprinting methods [5,6,7,8,9,10], while effective for ECU authentication, struggle with changing environments. In contrast, our entropy-based framework demonstrates a pragmatic compromise between detection efficacy and computational efficiency.
Experimental validation on hardware (manufactured by NXP Semiconductors N.V., Eindhoven, Netherlands) demonstrates the algorithm’s capability to detect 100% of anomalies under 10% bus load variation, achieving 80% accuracy with <20% false positive rates. Remarkably, it maintains a 100 ms detection duration and <10 KB memory footprint, outperforming comparable methods in resource efficiency. These results validate the viability of lightweight statistical approaches for securing legacy automotive networks during the transitional period toward fully encrypted vehicular architectures.
2. Background
2.1. Information Entropy Model
Let discrete random variable X represent CAN message IDs with possible values and corresponding probability distribution . The Shannon entropy is defined as [3]
Under normal operating conditions, CAN message ID frequencies remain stable, resulting in entropy fluctuations typically below 0.1 bits. During cyberattacks, abrupt changes in message distributions cause significant entropy deviations. Our algorithm detects anomalies by monitoring real-time entropy variations against baseline levels.
2.2. Normal Distribution Hypothesis and Two-Tailed Testing on CAN
Under normal operating conditions without intrusions, the frequency distribution of CAN message IDs remains stable, resulting in minimal fluctuations in information entropy values. We therefore posit that variations in CAN bus entropy follow a Gaussian distribution. Assuming entropy values follow during stable operation, where and represent baseline mean and variance respectively, the detection framework implements the following:
- Baseline Establishment: Collect normal CAN messages to calculate
- Real-Time Computation: Compute windowed entropy ():
- Hypothesis Testing: Construct test statisticReject null hypothesis when (, ).
2.3. ROC Curve Optimization
To balance sensitivity and false positives, we implement ROC-guided threshold tuning [11]:
- Dataset preparation: Let be the labeled dataset, where is the entropy value of the k-th observation window, and is a binary label (0 = normal, 1 = attack).
- Threshold Sweeping: For any candidate threshold , we define
- Optimal Threshold: Select minimizing
3. Related Works
Research on the security of in-vehicle CANs primarily focuses on two main directions: protocol-based encryption security solutions and intrusion detection systems (IDSs) [4]. Protocol encryption approaches enhance message integrity verification through CAN protocol modifications such as incorporating message authentication codes (MACs). Although extensively studied in early works [12,13,14], these methods face three fundamental deployment challenges: (1) mandatory ECU hardware modifications, (2) excessive computational overhead, and (3) non-trivial real-time constraints.
Conversely, IDS solutions have gained prominence due to their protocol independence and minimal bandwidth consumption. Existing intrusion detection algorithms can be categorized into four groups based on data types: entropy-based, content-based, frequency-based, and voltage signal-based methods.
Entropy-based methods [3,15,16] quantify uncertainty in CAN ID distributions, demonstrating particular efficacy against traffic anomalies like Denial-of-Service (DoS) attacks. Their limitation lies in detecting stealthy attacks that mimic legitimate patterns (e.g., precisely timed replay attacks). Content-based approaches [17,18] employ deep learning to analyze payload legitimacy. While achieving laboratory accuracy exceeding 95%, their practical deployment is hindered by substantial training data requirements and computational complexity. Frequency-based techniques [19,20,21,22] monitor temporal message characteristics, including clock skew and inter-arrival intervals. These methods achieve low false positive rates but prove ineffective against aperiodic or context-aware attacks. Voltage signal-based methods [5,6,7,8,9,10,23] exploit physical-layer characteristics for ECU authentication. These methods achieve microsecond-level fingerprinting accuracy, yet remain vulnerable to environmental drift and require continuous recalibration.
Under the strict resource constraints of contemporary automotive embedded platforms, entropy-based anomaly detection algorithms demonstrate significant practical advantages. Compared with methods requiring complex models (e.g., deep learning) or high-precision signal acquisition (e.g., voltage fingerprinting), entropy algorithms only require statistical analysis of CAN ID frequency distributions, featuring low computational complexity and minimal storage requirements. While current entropy-based detection algorithms remain constrained in addressing complex attack scenarios (e.g., precise replay attacks), their efficiency and low deployment costs in resource-constrained environments have gained widespread recognition. The subsequent sections detail key technical implementations, hardware adaptation strategies, and experimental validation outcomes.
4. Threat Model
4.1. Attack Type
We consider an attacker who can inject malicious CAN frames via physical access (e.g., OBD-II port) or short-range wireless interfaces, but cannot compromise ECU firmware. The attacker has full knowledge of the CAN protocol and possesses vehicle-specific ID allocation information. The attacker can launch various attacks, including the following:
- DoS Attack: The adversary floods the bus with high-priority frames (e.g., ID = 0x000 at 500 fps), causing entropy to drop below (see Equation (3)).
- Injection Attack: The attacker records legitimate messages (e.g., brake commands) and re-injects them at inappropriate times.
The current detection framework focuses on batch message injection attacks that cause observable entropy deviations. Single-frame injection scenarios, while theoretically possible, require different detection paradigms and are reserved for future research. This design choice aligns with automotive safety priorities where sustained attacks pose greater immediate risks.
4.2. Attack Impact on Entropy
The entropy deviation under DoS attacks is
where is the entropy deviation under DoS attack, and is the count of attack frames per window.
For injection attacks, the entropy deviation is defined as
where is the entropy deviation under injection attack, and and represent the original and injected message distributions, respectively.
5. System Models
The proposed system architecture comprises three tightly coupled modules, as conceptually illustrated in Figure 1. The data flow initiates from the CAN bus interface, where raw messages are timestamped, and then processed through an entropy-based detection pipeline.
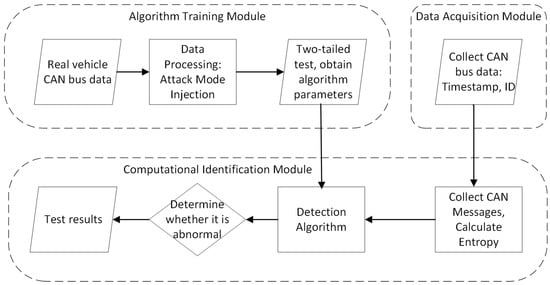
Figure 1.
Workflow of the intrusion detection system: starting from real-vehicle CAN data, progressing through attack injection and parameter training, then to data acquisition and entropy-based computation, and finally to anomaly detection.
5.1. Data Acquisition Module
The data acquisition module utilizes the CAN bus interface within the AUTOSAR framework to ensure seamless integration with existing vehicle network systems. When the CAN receiver detects an interrupt, the module is triggered and subsequently transfers the received CAN message IDs and contents to the upper-layer detection program via Direct Memory Access (DMA) for further analysis.
To precisely identify each CAN message, the module generates a unique timestamp upon message reception. This timestamp serves as a unique identifier to distinguish and tag different CAN messages, providing accurate temporal references for subsequent data analysis and anomaly detection. The process employs standard CAN message processing patterns, delivering reliable data support for the entire intrusion detection system.
5.2. Computational Identification Module
The computational identification module receives CAN message IDs from the data acquisition module and analyzes them using parameters provided by the algorithm training module. After accumulating 100 CAN messages, the module calculates the information entropy of these message IDs, to measure the probability distribution of CAN IDs, according to Equation (1).
The module then employs a two-tailed statistical test to determine whether the computed entropy falls within the normal range, thereby identifying potential network anomalies or attacks, according to Equation (5). The two-tailed test helps determine if the sample mean significantly differs from the expected value, evaluating whether the information entropy significantly deviates from normal communication patterns.
Finally, the module generates a binary detection output, where a value of 0 indicates normal entropy conditions while a value of 1 signals abnormal patterns that may trigger security alerts or initiate countermeasures. Key performance metrics demonstrate the system’s real-time capability, including a fixed processing window of 100 messages for entropy calculation, detection latency constrained to under 100 ms to meet automotive timing requirements, and memory consumption maintained below 10 KB to ensure compatibility with resource-constrained ECUs.
For each detection window of N messages, the algorithm computes Shannon entropy by iterating over n unique CAN IDs (fixed for a given vehicle, e.g., in our experiments). This requires operations per window. The Z-score calculation involves constant-time arithmetic operations . The per-window complexity is . This linear complexity enables deployment on resource-constrained ECUs without hardware accelerators.
Compared to state-of-the-art approaches, the proposed entropy-based detection achieves better computational efficiency. The entropy model proposed in recent research [16] involves signal processing with complexity for Fourier transforms (where N is the size of the sliding window), while the deep learning method [17] requires operations per detection window due to matrix multiplications in neural networks (where N is the feature dimension).
5.3. Algorithm Training Module
The algorithm training module uses CAN bus data collected during stable vehicle operation as baseline information for the training process, according to Equation (4). During training, the module first injects attack patterns into normal data to generate abnormal data, simulating the impact of cyber attacks on CAN bus communication.
The training module then splits the received CAN message sequences according to configurable granularity. After obtaining the entropy data, it uses the Cumulative Distribution Function (CDF) to estimate the normal distribution parameters of the collected data. This step is based on the assumption that CAN ID frequency values follow a normal distribution over a certain period.
The module then uses the normal distribution model to test the injected attack data. To optimize the detection method, it employs Receiver Operating Characteristic (ROC) curve analysis to determine the optimal detection threshold, according to Equation (8). Ultimately, the module establishes an optimal threshold for subsequent real-time CAN monitoring and anomaly detection.
6. Experiments and Results
6.1. Real-World Dataset Validation
To validate the effectiveness of the proposed algorithm, we conducted experiments using a real-world dataset collected from a real vehicle. The dataset includes 71 unique CAN message IDs with varying payloads and periodicities, simulating typical in-vehicle communication patterns.
For a DoS attack, following the evaluation methodology of [15], we injected DoS attack frames (ID = 0x000) at 30% bus load penetration to create an adversarial testing environment. The comparative analysis was performed using 500 ms time windows for both methods. For the baseline approach [15], we implemented their fixed threshold detection with as recommended in their original work, which yielded 92% accuracy with an 18% false positive rate at 100% recall. Our adaptive entropy-based method demonstrated superior performance with 99% accuracy and only a 1% false positive rate (FPR) while maintaining 100% recall, as detailed in Table 1.

Table 1.
Performance comparison with fixed-threshold method.
For injection attacks, we injected recorded legitimate messages at 30% bus load penetration. As shown in Table 2, our method maintains superior performance with 99% accuracy and 1% false positive rate at 90% recall, while the fixed-threshold approach suffers from higher false alarms (29% FPR) despite achieving full recall:

Table 2.
Performance comparison for injection attack detection.
The performance improvement stems from two key algorithmic innovations: our threshold searching mechanism enables the algorithm to adapt to different datasets rapidly, compared to the fixed threshold approach.
6.2. Hardware-in-the-Loop Evaluation
6.2.1. Platform Configuration
The testbed comprised an NXP MPC5748G development board (32-bit Power Architecture MCU with 2 MB Flash) and a USBCAN-II FD interface device (manufactured by GCGtec Co., Shenyang, China) supporting CAN FD at 5 Mbps, configured with standard 120 termination resistance to emulate automotive network conditions. The experiment environment is shown in Figure 2.
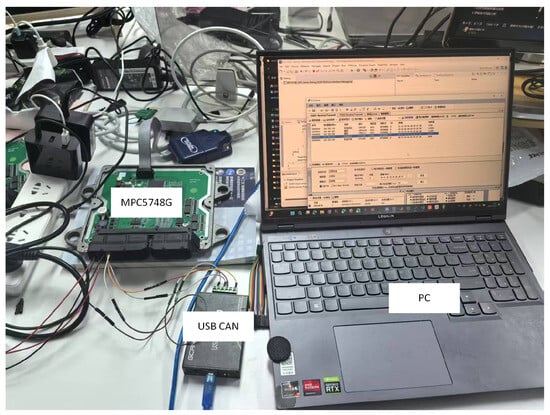
Figure 2.
Hardware platform of the experiment. (1) MPC5748G board, (2) USBCAN-II FD, and (3) PC.
A Simulink (R2022a) model generated both normal and malicious CAN frames with periods ranging from 10 ms to 1155 ms, covering typical in-vehicle communication intervals. The model implemented 71 distinct CAN IDs with payload patterns derived from real-world vehicle data captures.
6.2.2. Evaluation Methodology
The experimental procedure involves configuring the USBCAN-II FD device to emulate CAN bus traffic while the MPC5748G processes incoming messages for anomaly detection. Based on actual vehicle data, the simulation implements 71 unique frame types with periodicities spanning 10–1155 ms.
The algorithm performs 100 independent detection cycles, respectively, on both normal CAN bus traffic and attack-injected compromised networks, where the attack-injected network injects malicious frames at 9.28% bus load penetration (equivalent to 1 attack frame per 10.8 normal frames based on the 500 kbps CAN FD bandwidth). The detection algorithm processes this mixed traffic on the MPC5748G platform, with performance metrics shown in Table 3, calculated under attack or normal conditions, while execution timing was measured via S32 Design Studio’s µs-resolution debugger across all 71 simulated message types (10–1155 ms periods) derived from production vehicle data.

Table 3.
Performance metric evaluation framework.
6.2.3. Evaluation Results
As shown in Table 4, The experimental results demonstrate the algorithm’s effectiveness in detecting various attack types while maintaining low false positive rates. The system achieved a detection accuracy of 84% with a recall (REC) higher than 80% under normal or attack conditions. The execution time, which is the program running time after collecting CAN messages within the time window, for the detection algorithm was consistently below 100 ms, ensuring real-time performance on the MPC5748G platform.

Table 4.
Performance metric evaluation.
7. Conclusions
This study presented a lightweight entropy-based intrusion detection system for automotive CANs, leveraging Shannon entropy analysis of CAN message ID distributions and a two-tailed statistical test with adaptive threshold optimization. The algorithm, implemented on an NXP MPC5748G platform, achieved 84.5% accuracy and 85.6% recall under 9.28% bus load penetration. Key innovations include ROC curve-guided threshold selection, ensuring compatibility with resource-constrained ECUs. Hardware-in-the-loop validation confirmed real-time performance, with detection latency constrained to 70 ms per 100 message windows. The solution addresses critical limitations of cryptographic and machine learning-based approaches by offering a protocol-agnostic, low-overhead detection framework. Future work will focus on adaptive threshold tuning for evolving attack patterns while maintaining the algorithm’s sub 100 ms execution time and sub 10 KB memory footprint.
Author Contributions
Conceptualization, J.C. and Z.W.; methodology, J.C.; software, J.C.; validation, J.C.; formal analysis, J.C.; investigation, J.C.; resources, Z.W.; data curation, J.C.; writing—original draft preparation, J.C.; writing—review and editing, J.C. and Z.W.; visualization, J.C.; supervision, Z.W.; project administration, Z.W.; funding acquisition, Z.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Training data and evaluation results are available at https://github.com/Richardchen97/CANIDlightweight.git (accessed on 17 June 2025).
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental Security Analysis of a Modern Automobile. IEEE Secur. Priv. 2010, 8, 44–50. [Google Scholar]
- Marchetti, M.; Stabili, D. READ: Reverse Engineering of Automotive Data Frames. IEEE Trans. Inf. Forensics Secur. Publ. Inf. 2018, 13, 3173–3186. [Google Scholar] [CrossRef]
- Müter, M.; Asaj, N. Entropy-based Anomaly Detection for In-Vehicle Networks. In Proceedings of the 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; Volume 1, pp. 1110–1115. [Google Scholar]
- Xun, Y.; Deng, Z.; Liu, J.; Zhao, Y. Side Channel Analysis: A Novel Intrusion Detection System Based on Vehicle Voltage Signals. IEEE Trans. Veh. Technol. 2023, 72, 7240–7250. [Google Scholar] [CrossRef]
- Choi, W.; Joo, K.; Jo, H.J.; Park, M.C.; Lee, D.H. VoltageIDS: Low-Level Communication Characteristics for Automotive Intrusion Detection System. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2114–2129. [Google Scholar] [CrossRef]
- Murvay, P.S.; Groza, B. Source Identification Using Signal Characteristics in Controller Area Networks. IEEE Signal Process. Lett. 2014, 21, 395–399. [Google Scholar] [CrossRef]
- Kneib, M.; Schell, O.; Huth, C. On the Robustness of Signal Characteristic-Based Sender Identification. arXiv 2019, arXiv:1911.09881. [Google Scholar]
- Yin, L.; Xu, J.; Wang, C.; Wang, Q.; Zhou, F. Detecting CAN Overlapped Voltage Attacks with an Improved Voltage-Based In-Vehicle Intrusion Detection System. J. Syst. Archit. 2023, 143, 102957. [Google Scholar] [CrossRef]
- Lalouani, W.; Dang, Y.; Younis, M. Mitigating Voltage Fingerprint Spoofing Attacks on the Controller Area Network Bus. Clust. Comput. 2023, 26, 1447–1460. [Google Scholar] [CrossRef]
- Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal. Smart Cities 2020, 3, 17–30. [Google Scholar] [CrossRef]
- Fawcett, T. An Introduction to ROC Analysis. Pattern Recognit. Lett. 2006, 27, 861–874. [Google Scholar] [CrossRef]
- Nilsson, D.K.; Larson, U.E.; Jonsson, E. Efficient In-Vehicle Delayed Data Authentication Based on Compound Message Authentication Codes. In Proceedings of the 2008 IEEE 68th Vehicular Technology Conference, Calgary, AB, Canada, 21–24 September 2008; pp. 1–5. [Google Scholar]
- Szilagyi, C.J. Low Cost Multicast Network Authentication for Embedded Control Systems. Ph.D. Dissertation, Carnegie Mellon University, Pittsburgh, PA, USA, 2012. [Google Scholar]
- Zago, G.M.; de Freitas, E.P. A Quantitative Performance Study on CAN and CAN FD Vehicular Networks. IEEE Trans. Ind. Electron. 2017, 65, 4413–4422. [Google Scholar] [CrossRef]
- Wu, W.; Huang, Y.; Kurachi, R.; Zeng, G.; Xie, G.; Li, R.; Li, K. Sliding Window Optimized Information Entropy Analysis Method for Intrusion Detection on In-Vehicle Networks. IEEE Access 2018, 6, 45233–45245. [Google Scholar] [CrossRef]
- Liu, W.; Qin, G.; Liang, Y.; Song, J.; Liu, Q.; Zhou, X. ETFIDS: An Entropy-Driven, Time-Frequency Analysis Framework for In-Vehicle CAN Signal Intrusion Detection. IEEE Internet Things J. 2025, 12, 21507–21522. [Google Scholar] [CrossRef]
- Amato, F.; Coppolino, L.; Mercaldo, F.; Moscato, F.; Nardone, R.; Santone, A. CAN-Bus Attack Detection with Deep Learning. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5081–5090. [Google Scholar] [CrossRef]
- Martinelli, F.; Mercaldo, F.; Nardone, V.; Santone, A. Car Hacking Identification Through Fuzzy Logic Algorithms. In Proceedings of the 2017 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE), Naples, Italy, 9–12 July 2017; pp. 1–7. [Google Scholar]
- Cho, K.T.; Shin, K.G. Viden: Attacker Identification on In-Vehicle Networks. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1109–1123. [Google Scholar]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion Detection System Based on the Analysis of Time Intervals of CAN Messages for In-Vehicle Network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016; pp. 63–68. [Google Scholar]
- Taylor, A.; Japkowicz, N.; Leblanc, S. Frequency-Based Anomaly Detection for the Automotive CAN Bus. In Proceedings of the 2015 World Congress on Industrial Control Systems Security (WCICSS), London, UK, 14–16 December 2015; pp. 45–49. [Google Scholar]
- Roeschlin, M.; Camurati, G.; Brunner, P.; Mridula, S.; Srdjan, C. EdgeTDC: On the Security of Time Difference of Arrival Measurements in CAN Bus Systems. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 27 February–3 March 2023. [Google Scholar]
- Kneib, M.; Huth, C. Scission: Signal Characteristic-Based Sender Identification and Intrusion Detection in Automotive Networks. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 787–800. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).