Internet of Things and Deep Learning for Citizen Security: A Systematic Literature Review on Violence and Crime
Abstract
1. Introduction
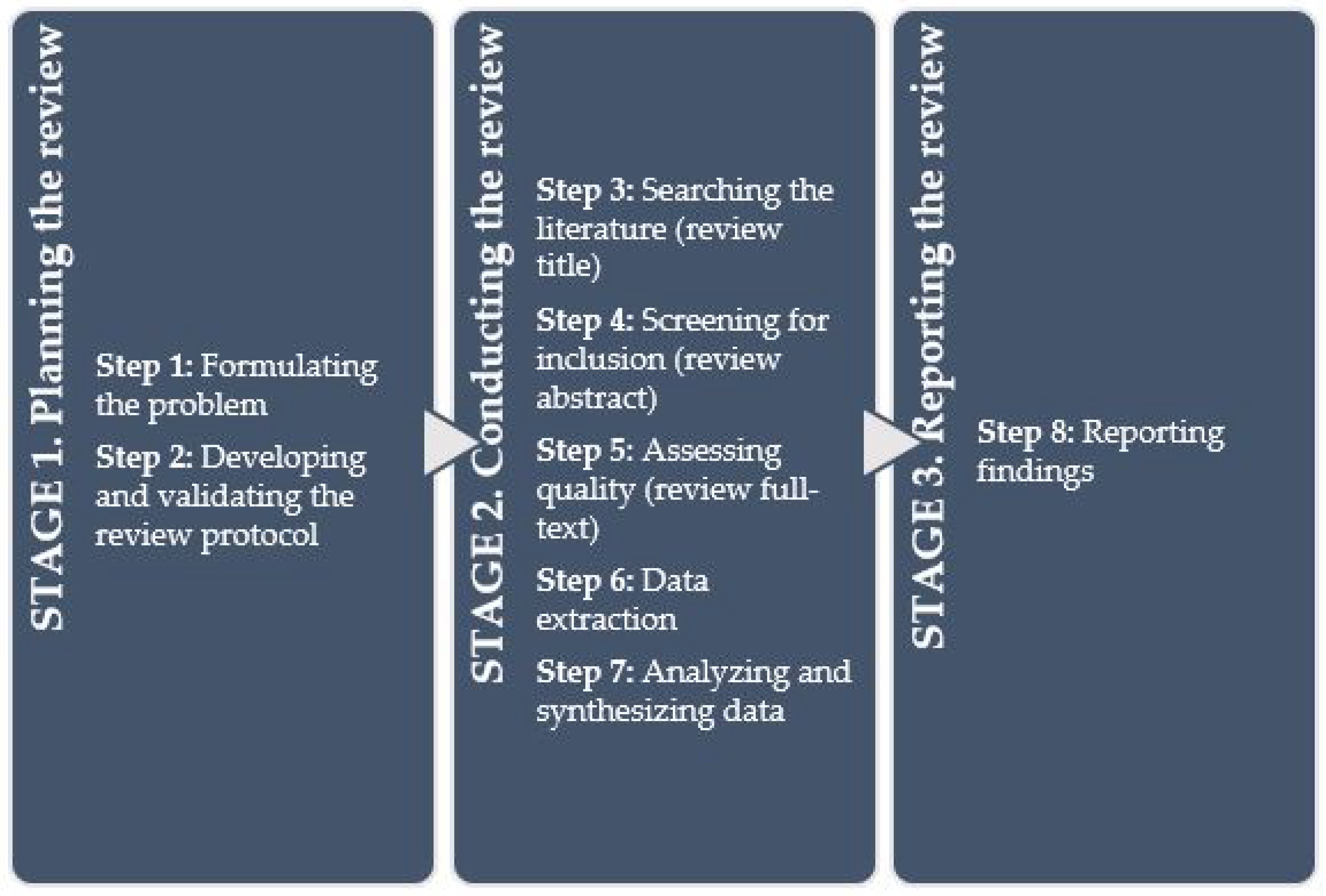
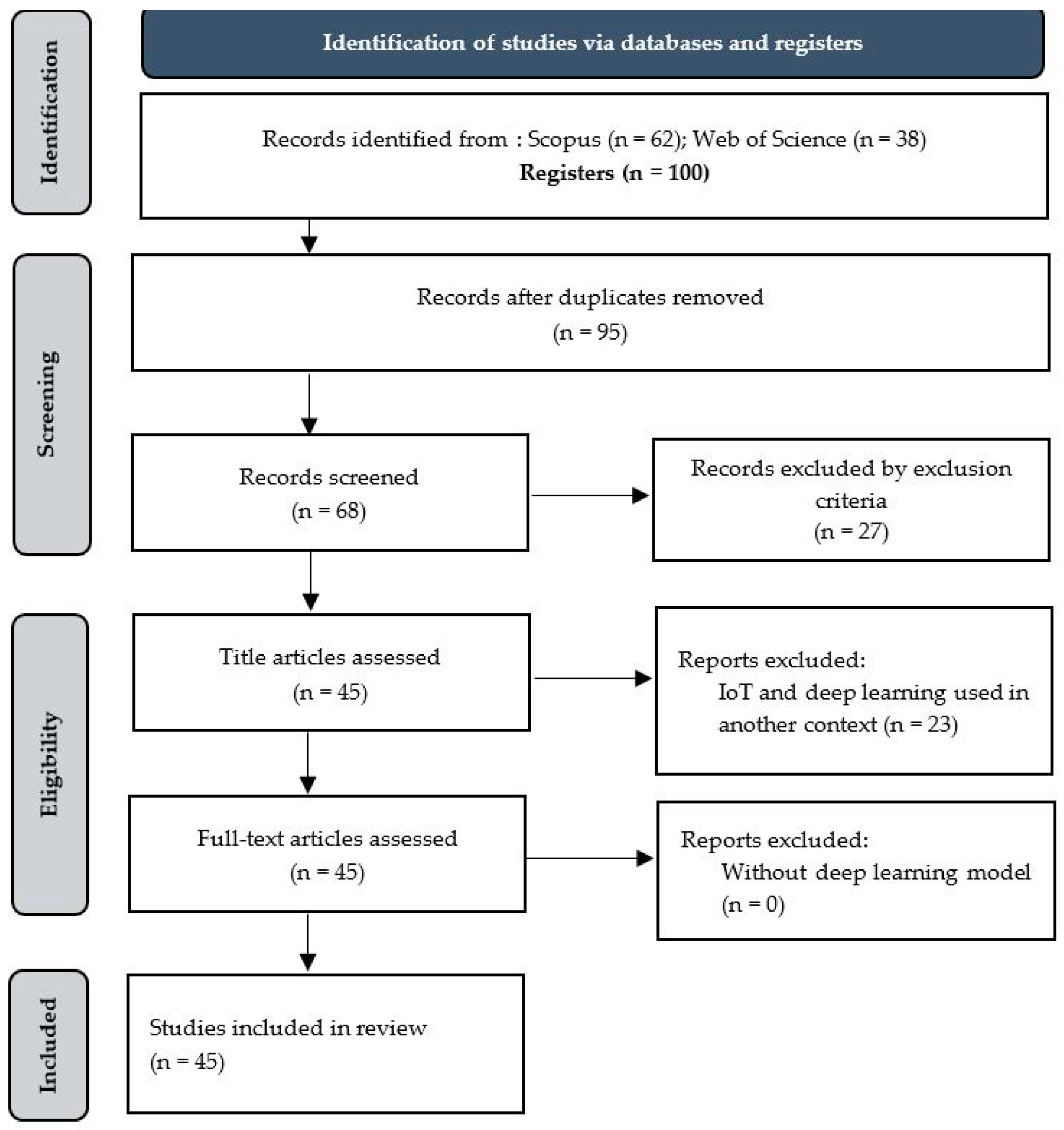
2. Methodology
2.1. Sateg 1—Planning the Review
2.1.1. Step 1 Formulating the Problem
- RQ1. What are the primary deep learning models that have been applied to detect violence and crime in smart cities?
- RQ2. How have ethical concerns related to privacy been addressed in IoT-based violence and crime detection systems in smart cities?
- RQ3. How have these proposals contributed to addressing different levels of violence?
- RQ4. What is the scope, what are the benefits, and what are the limitations of these proposals in terms of functionality?
- RQ5. What technological tools have been used to implement these proposals?
- RQ6. How reliable have these systems been based on key model evaluation metrics (accuracy, precision, recall, F1-score)?
2.1.2. Step 2 Developing and Validating the Review Protocol
crime) AND TITLE-ABS-KEY(smart AND city) AND TITLE-ABS-
KEY(internet AND of AND things OR iot)
and internet of things OR lot (Topic)
- Published outside the defined timeframe (2010–2024).
- Written in languages other than English.
- Not directly related to deep learning, IoT, and public security.
- Proposing purely theoretical models without empirical validation.
- Describing only conceptual frameworks for smart city security.
2.2. Stage 2—Conducting the Review
2.2.1. Step 3–5 Identification of Relevant Studies (Title, Abstract, and Full Text)
2.2.2. Step 6 Data Extraction
- Level 1 (★): Studies integrating IoT and deep learning;
- Level 2 (★★): Level 1 + simulation/experimentation;
- Level 3 (★★★): Level 2 + performance evaluation of the deep learning model based on accuracy, precision, recall, or F1-score;
- Level 4 (★★★★): Level 3 + application in a real-world scenario;
- Level 5 (★★★★★): Level 4 + graphical evidence of pattern recognition in a real city.
2.2.3. Step 7 Analyzing and Synthesizing Data
2.3. Sateg 3—Reporting the Review
Step 8 Reporting Findings
3. Results
3.1. RQ1—What Are the Primary Deep Learning Models That Have Been Applied to Detect Violence and Crime in Smart Cities?
3.2. RQ2—How Have Ethical Concerns Related to Privacy Been Addressed in IoT-Based Violence and Crime Detection Systems in Smart Cities?
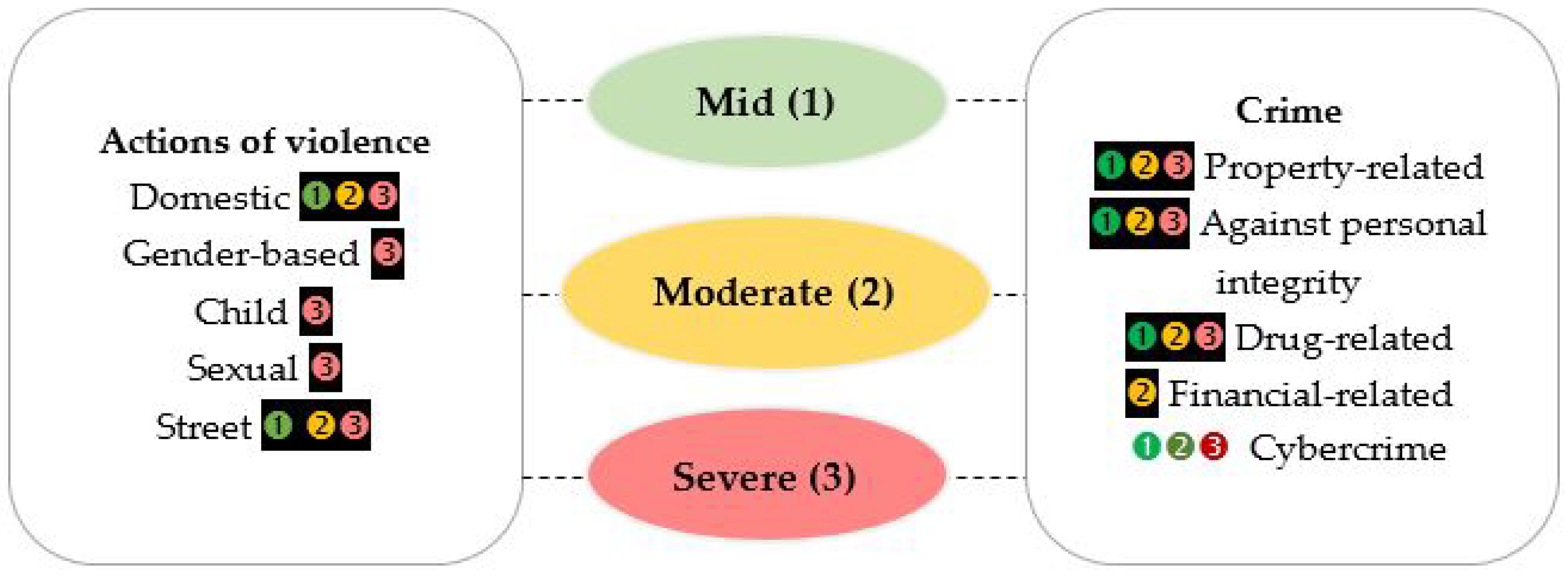
3.3. RQ3—How Have These Proposals Contributed to Addressing Different Levels of Violence?
3.3.1. Monitoring Violence Actions
3.3.2. Monitoring of Crime
3.4. RQ4—What Is the Scope, What Are the Benefits, and What Are the Limitations of These Proposals in Terms of Functionality?
3.4.1. Implementation Technical Aspects
3.4.2. Benefits and Technical Limitations
3.5. RQ5—What Technological Tools Have Been Used to Implement These Proposals?
3.6. RQ6—How Reliable Have These Systems Been Based on Key Model Evaluation Metrics (Accuracy, Precision, Recall, F1-Score)?
4. Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| ANN | Artificial Neural Network |
| BFA | Brute Force Attack |
| BILSTM | Bidirectional Long Short-Term Memory |
| CANFIS | Coactive Neuro-Fuzzy Inference System |
| CNN | Convolutional Neural Network |
| DBN | Deep Belief Network |
| DDoS | Distributed Denial of Service |
| DHLNN | Deep Hybrid Learning Neural Network |
| DIO | DODAG Information Object |
| DL | Deep Learning |
| DMLM | Deep Migration Learning Model |
| DNN | Deep Neural Network |
| DQN | Deep Q-Network |
| DRL | Deep Reinforcement Learning |
| DRL-DQN | Deep Reinforcement Learning–Deep Q-Network |
| ELM | Extreme Learning Machine |
| ELM-RNN | Extreme Learning Machine–Recurrent Neural Network |
| GA | Genetic Algorithm |
| GA-LSTM | Genetic Algorithm–Long Short-Term Memory |
| GRU | Gated Recurrent Unit |
| HCSGA | Hybrid Chicken Swarm Genetic Algorithm |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| LSTM | Long Short-Term Memory |
| LSTM-SVM | Long Short-Term Memory–Support Vector Machine |
| MA2C | Multi-Agent Actor-Critic |
| MCIDS | Multi-Cloud Intrusion Detection System |
| MDRL | Multi-Objective Deep Reinforcement Learning |
| MitM | Man-in-the-Middle Attack |
| ML | Machine Learning |
| MLP | Multi-Layer Perceptron |
| MQTT | Message Queuing Telemetry Transport |
| MRMR | Minimum Redundancy Maximum Relevance |
| O-CNN | Optimized CNN |
| PPO | Proximal Policy Optimization |
| PRISMA | Preferred Reporting Items for Systematic Reviews and Meta-Analyses |
| RBM | Restricted Boltzmann Machine |
| RF | Random Forest |
| RNN | Recurrent Neural Network |
| RPL | Routing Protocol for Low-Power and Lossy Networks |
| RQ | Research Question |
| SAE | Stacked Autoencoder |
| SCNN | Sparse Convolutional Neural Network |
| SCNN-RF | Sparse Convolutional Neural Network–Random Forest |
| SNET | Spiking Neural Network |
| SQL | Structure Query Language |
| SSD | Single-Shot MultiBox Detector |
| SVM | Support Vector Machine |
| TL-BILSTM | Transfer Learning BiLSTM |
| WDLSTM | Wavelet Deep LSTM |
| XGBoost | Extreme Gradient Boosting |
| XSS | Cross-Site Scripting |
References
- Ma, C. Smart City and Cyber-Security; Technologies Used, Leading Challenges and Future Recommendations. Energy Rep. 2021, 7, 7999–8012. [Google Scholar] [CrossRef]
- Bellini, P.; Nesi, P.; Pantaleo, G. IoT-Enabled Smart Cities: A Review of Concepts, Frameworks and Key Technologies. Appl. Sci. 2022, 12, 1607. [Google Scholar] [CrossRef]
- Xie, H.; Shi, W.; Choudhary, H.; Fu, H.; Guo, X. Big Data Analysis for Retrofit Projects in Smart Cities. In Proceedings of the 2019 3rd International Conference on Smart Grid and Smart Cities (ICSGSC), Berkeley, CA, USA, 25–28 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Gracias, J.S.; Parnell, G.S.; Specking, E.; Pohl, E.A.; Buchanan, R. Smart Cities—A Structured Literature Review. Smart Cities 2023, 6, 1719–1743. [Google Scholar] [CrossRef]
- Melibari, W.; Baodhah, H.; Akkari, N. IoT-Based Smart Cities Beyond 2030: Enabling Technologies, Challenges, and Solutions. In Proceedings of the 2023 1st International Conference on Advanced Innovations in Smart Cities (ICAISC), Jeddah, Saudi Arabia, 23–25 January 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Steenhoek, B.; Rahman, M.M.; Jiles, R.; Le, W. An Empirical Study of Deep Learning Models for Vulnerability Detection. In Proceedings of the 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE), Melbourne, Australia, 14–20 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 2237–2248. [Google Scholar] [CrossRef]
- Hu, L.; Ni, Q. IoT-Driven Automated Object Detection Algorithm for Urban Surveillance Systems in Smart Cities. IEEE Internet Things J. 2018, 5, 747–754. [Google Scholar] [CrossRef]
- Hermanus, D.R.; Supangkat, S.H.; Hidayat, F.; Sasmoko; Indrianti, Y. Smart Guard Towns: Multi-Drone Systems with Deep Learning for Situational Awareness in Urban Management and Security. In Proceedings of the 2023 10th International Conference on ICT for Smart Society (ICISS), Bandung, Indonesia, 6–7 September 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Baba, M.; Gui, V.; Cernazanu, C.; Pescaru, D. A Sensor Network Approach for Violence Detection in Smart Cities Using Deep Learning. Sensors 2019, 19, 1676. [Google Scholar] [CrossRef]
- Felson, R.B. Violence, Crime, and Violent Crime. Int. J. Confl. Violence (IJCV) 2009, 3, 23–39. [Google Scholar] [CrossRef]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L.; Gagliardi, R. Applications of Artificial Intelligence and Machine Learning in Smart Cities. Comput. Commun. 2020, 154, 313–323. [Google Scholar] [CrossRef]
- Singh, S.K.; Jeong, Y.S.; Park, J.H. A Deep Learning-Based IoT-Oriented Infrastructure for Secure Smart City. Sustain. Cities Soc. 2020, 60, 102252. [Google Scholar] [CrossRef]
- Reza, S.; Oliveira, H.S.; Machado, J.J.M.; Tavares, J.M.R.S. Urban Safety: An Image-Processing and Deep-Learning-Based Intelligent Traffic Management and Control System. Sensors 2021, 21, 7705. [Google Scholar] [CrossRef]
- United Nations Department of Economic and Social Affairs (Population Division). World Urbanization Prospects: The 2018 Revision; United Nations Department of Economic and Social Affairs: New York, NY, USA, 2018. [Google Scholar]
- Butt, U.M.; Letchmunan, S.; Hassan, F.H.; Koh, T.W. Leveraging Transfer Learning with Deep Learning for Crime Prediction. PLoS ONE 2024, 19, e0296486. [Google Scholar] [CrossRef]
- Stalidis, P.; Semertzidis, T.; Daras, P. Examining Deep Learning Architectures for Crime Classification and Prediction. Forecasting 2021, 3, 741–762. [Google Scholar] [CrossRef]
- Jeyapriyanga, S.; Ravi, C.N.; Rathiya, R.; Kalaivani, K.; Rama Devi, C.; Kumar, K.R. Implementation of a Deep Learning Framework for Intelligent Intrusion Detection in Internet of Things Networks. In Proceedings of the 5th International Conference on Inventive Research in Computing Applications ICIRCA 2023, Coimbatore, India, 3–5 August 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 1208–1213. [Google Scholar] [CrossRef]
- Page, M.J.; Moher, D.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. PRISMA 2020 Explanation and Elaboration: Updated Guidance and Exemplars for Reporting Systematic Reviews. BMJ 2021, 372, n160. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; University of Durham: Durham, UK, 2007; Volume 1, Available online: https://legacyfileshare.elsevier.com/promis_misc/525444systematicreviewsguide.pdf (accessed on 3 February 2025).
- Bastos, D.; Fernández-Caballero, A.; Pereira, A.; Rocha, N.P. Smart City Applications to Promote Citizen Participation in City Management and Governance: A Systematic Review. Informatics 2022, 9, 89. [Google Scholar] [CrossRef]
- Xiao, Y.; Watson, M. Guidance on Conducting a Systematic Literature Review. J. Plan. Educ. Res. 2019, 39, 93–112. [Google Scholar] [CrossRef]
- Mandaviya, H.; Sathwara, S. Cyber Terrorism-Related Multimedia Detection Using Deep Learning—A Survey. In Proceedings of the International Conference on Recent Trends in Machine Learning, IoT, Smart Cities and Applications, Hyderabad, India, 29–30 March 2020; Advances in Intelligent Systems and Computing. Springer: Singapore, 2021; Volume 1245, pp. 135–143. [Google Scholar] [CrossRef]
- Li, D.; Deng, L.; Lee, M.; Wang, H. IoT Data Feature Extraction and Intrusion Detection System for Smart Cities Based on Deep Migration Learning. Int. J. Inf. Manag. 2019, 49, 533–545. [Google Scholar] [CrossRef]
- Rashid, M.M.; Kamruzzaman, J.; Imam, T.; Kaisar, S.; Alam, M.J. Cyber Attacks Detection from Smart City Applications Using Artificial Neural Network. In Proceedings of the 2020 IEEE Asia-Pacific Conference on Computer Science and Data Engineering, CSDE 2020, Gold Coast, Australia, 16–18 December 2020; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2020. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Smart Grid Security: An Effective Hybrid CNN-Based Approach for Detecting Energy Theft Using Consumption Patterns. Sensors 2024, 24, 1148. [Google Scholar] [CrossRef]
- Song, S.; Dong, A.; Zhu, H.; Wang, S.; Yu, J. Intelligent Network Intrusion Detection and Situational Awareness for Cyber-Physical Systems in Smart Cities. In Proceedings of the 20th Pacific Rim International Conference on Artificial Intelligence PRICAI 2023, Jakarta, Indonesia, 15–19 November 2023; Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics). Springer: Singapore, 2024; Volume 14325, pp. 29–35. [Google Scholar] [CrossRef]
- Jain, A.A.; Srinivasa Rao, B.; Chattopadhyay, S.; Kumar, A.; Muthuraman, M.S.; Manjula, A. An Artificial Intelligence Network Based-Host Intrusion Detection System for Internet of Things Devices. In Proceedings of the 2023 4th International Conference on Electronics and Sustainable Communication Systems ICESC 2023, Coimbatore, India, 6–8 July 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 656–661. [Google Scholar] [CrossRef]
- Prazeres, N.; Costa, R.L.D.C.; Santos, L.; Rabadão, C. Engineering the Application of Machine Learning in an IDS Based on IoT Traffic Flow. Intell. Syst. Appl. 2023, 17, 200189. [Google Scholar] [CrossRef]
- Bennet, D.T.; Bennet, P.S.; Anitha, D. Securing Smart City Networks—Intelligent Detection of DDoS Cyber Attacks. In Proceedings of the 5th International Conference on Contemporary Computing and Informatics, IC3I 2022, Uttar Pradesh, India, 14–16 December 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022; pp. 1575–1580. [Google Scholar] [CrossRef]
- Sagu, A.; Gill, N.S.; Gulia, P.; Priyadarshini, I.; Chatterjee, J.M. Hybrid Optimization Algorithm for Detection of Security Attacks in IoT-Enabled Cyber-Physical Systems. IEEE Trans. Big Data 2024, 11, 35–46. [Google Scholar] [CrossRef]
- Sowmya, C.S.; Vibin, R.; Mannam, P.; Mounika, L.; Kabat, S.R.; Patra, J.P. Enhancing Smart Grid Security: Detecting Electricity Theft through Ensemble Deep Learning. In Proceedings of the 8th International Conference on Communication and Electronics Systems, ICCES 2023, Coimbatore, India, 1–3 June 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 1803–1810. [Google Scholar] [CrossRef]
- Zubair, M.; Ghubaish, A.; Unal, D.; Al-Ali, A.; Reimann, T.; Alinier, G.; Hammoudeh, M.; Qadir, J. Secure Bluetooth Communication in Smart Healthcare Systems: A Novel Community Dataset and Intrusion Detection System. Sensors 2022, 22, 8280. [Google Scholar] [CrossRef]
- Dalal, S.; Lilhore, U.K.; Sharma, N.; Arora, S.; Simaiya, S.; Ayadi, M.; Almujally, N.A.; Ksibi, A. Improving Smart Home Surveillance through YOLO Model with Transfer Learning and Quantization for Enhanced Accuracy and Efficiency. PeerJ Comput. Sci. 2024, 10, e1939. [Google Scholar] [CrossRef]
- Saheed, Y.K.; Abdulganiyu, O.H.; Tchakoucht, T.A. Modified Genetic Algorithm and Fine-Tuned Long Short-Term Memory Network for Intrusion Detection in the Internet of Things Networks with Edge Capabilities. Appl. Soft Comput. 2024, 155, 111434. [Google Scholar] [CrossRef]
- Althobaiti, M.M.; Pradeep Mohan Kumar, K.; Gupta, D.; Kumar, S.; Mansour, R.F. An Intelligent Cognitive Computing Based Intrusion Detection for Industrial Cyber-Physical Systems. Meas. J. Int. Meas. Confed. 2021, 186, 110145. [Google Scholar] [CrossRef]
- Elsayed, R.A.; Hamada, R.A.; Abdalla, M.I.; Elsaid, S.A. Securing IoT and SDN Systems Using Deep-Learning Based Automatic Intrusion Detection. Ain Shams Eng. J. 2023, 14, 102211. [Google Scholar] [CrossRef]
- Bhagat, G.; Mishra, K.; Dutta, T. X-DeepID: An Explainable Hybrid Deep Learning Method for Enhancing IoT Security with Intrusion Detection. In Communications in Computer and Information Science; Springer Science and Business Media: Cham, Switzerland, 2024; Volume 2030, pp. 42–53. [Google Scholar] [CrossRef]
- Fadhilla, C.A.; Alfikri, M.D.; Kaliski, R. Lightweight Meta-Learning BotNet Attack Detection. IEEE Internet Things J. 2023, 10, 8455–8466. [Google Scholar] [CrossRef]
- Mosaiyebzadeh, F.; Araujo Rodriguez, L.G.; Macedo Batista, D.; Hirata, R. A Network Intrusion Detection System Using Deep Learning against MQTT Attacks in IoT. In Proceedings of the 2021 IEEE Latin-American Conference on Communications, LATINCOM 2021, Santo Domingo, Dominican Republic, 17–19 November 2021; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2021. [Google Scholar] [CrossRef]
- Zhang, J. Analysis of Network Attack Detection Based on Internet of Things Network Traffic. In Proceedings of the 2nd International Conference on Cognitive Based Information Processing and Applications (CIPA 2022), Changzhou, China, 22–23 September 2022; Lecture Notes on Data Engineering and Communications Technologies. Springer: Singapore, 2023; Volume 155, pp. 719–726. [Google Scholar] [CrossRef]
- Rakha, M.A.; Akbar, A.; Chhabra, G.; Kaushik, K.; Arshi, O.; Khan, I.U. A Detailed Comparative Study of AI-Based Intrusion Detection System for Smart Cities. In Proceedings of the International Conference on Communication, Computer Sciences and Engineering, IC3SE 2024, Gautam Buddha Nagar, India, 9–11 May 2024; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2024; pp. 1783–1790. [Google Scholar] [CrossRef]
- Almasri, M.M.; Alajlan, A.M. A Novel-Cascaded ANFIS-Based Deep Reinforcement Learning for the Detection of Attack in Cloud IoT-Based Smart City Applications. Concurr. Comput. Pract. Exp. 2023, 35, e7738. [Google Scholar] [CrossRef]
- Azhar, I.; Sharif, M.; Raza, M.; Khan, M.A.; Yong, H.S. A Decision Support System for Face Sketch Synthesis Using Deep Learning and Artificial Intelligence. Sensors 2021, 21, 8178. [Google Scholar] [CrossRef]
- Dandapat, A.; Mondal, B. Design of Intrusion Detection System Using GA and CNN for MQTT-Based IoT Networks. Wirel. Pers. Commun. 2024, 134, 2059–2082. [Google Scholar] [CrossRef]
- Gupta, S.K.; Tripathi, M.; Grover, J. Hybrid Optimization and Deep Learning Based Intrusion Detection System. Comput. Electr. Eng. 2022, 100, 107876. [Google Scholar] [CrossRef]
- Jain, S.; Jatain, A.; Bhaskar, S. Smart City Management System Using IoT with Deep Learning. In Proceedings of the 4th International Conference on Communication and Electronics Systems ICCES 2019, Coimbatore, India, 17–19 July 2019; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2019; pp. 1214–1222. [Google Scholar] [CrossRef]
- Nandanwar, H.; Katarya, R. TL-BILSTM IoT: Transfer Learning Model for Prediction of Intrusion Detection System in IoT Environment. Int. J. Inf. Secur. 2024, 23, 1251–1277. [Google Scholar] [CrossRef]
- Ullah, F.U.M.; Muhammad, K.; Haq, I.U.; Khan, N.; Heidari, A.A.; Baik, S.W.; De Albuquerque, V.H.C. AI-Assisted Edge Vision for Violence Detection in IoT-Based Industrial Surveillance Networks. IEEE Trans. Ind. Inform. 2022, 18, 5359–5370. [Google Scholar] [CrossRef]
- Gayathri, P.; Stalin, A.; Anand, S. Intelligent Smart Home Security System: A Deep Learning Approach. In Proceedings of the IEEE Region 10 Humanitarian Technology Conference R10-HTC, Hyderabad, India, 16–18 September 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022; Volume 2022, pp. 438–444. [Google Scholar] [CrossRef]
- El Houda, Z.A.; Brik, B.; Khoukhi, L. “Why Should I Trust Your IDS?”: An Explainable Deep Learning Framework for Intrusion Detection Systems in Internet of Things Networks. IEEE Open J. Commun. Soc. 2022, 3, 1164–1176. [Google Scholar] [CrossRef]
- Singh, S.; Fernandes, S.V.; Padmanabha, V.; Rubini, P.E. MCIDS-Multi Classifier Intrusion Detection System for IoT Cyber Attack Using Deep Learning Algorithm. In Proceedings of the 3rd International Conference on Intelligent Communication Technologies and Virtual Mobile Networks ICICV 2021, Tirunelveli, India, 4–6 February 2021; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2021; pp. 354–360. [Google Scholar] [CrossRef]
- Sbai, O.; El Boukhari, M. Data Flooding Intrusion Detection System for Manets Using Deep Learning Approach. In ACM International Conference Proceeding Series; Association for Computing Machinery: New York, NY, USA, 2020; pp. 281–286. [Google Scholar] [CrossRef]
- Saba, T.; Khan, A.R.; Sadad, T.; Hong, S.P. Securing the IoT System of Smart City against Cyber Threats Using Deep Learning. Discret. Dyn. Nat. Soc. 2022, 2022, 1241122. [Google Scholar] [CrossRef]
- Elsaeidy, A.A.; Jamalipour, A.; Munasinghe, K.S. A Hybrid Deep Learning Approach for Replay and DDoS Attack Detection in a Smart City. IEEE Access 2021, 9, 154864–154875. [Google Scholar] [CrossRef]
- Hazman, C.; Guezzaz, A.; Benkirane, S.; Azrour, M. Enhanced IDS with Deep Learning for IoT-Based Smart Cities Security. Tsinghua Sci. Technol. 2024, 29, 929–947. [Google Scholar] [CrossRef]
- Sagu, A.; Gill, N.S.; Gulia, P. Hybrid Deep Neural Network Model for Detection of Security Attacks in IoT Enabled Environment. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 120–127. [Google Scholar] [CrossRef]
- Aljebreen, M.; Alrayes, F.S.; Aljameel, S.S.; Saeed, M.K. Political Optimization Algorithm with a Hybrid Deep Learning Assisted Malicious URL Detection Model. Sustainability 2023, 15, 16811. [Google Scholar] [CrossRef]
- Mishra, S.; Chaurasiya, V.K. Hybrid Deep Learning Algorithm for Smart Cities Security Enhancement through Blockchain and Internet of Things. Multimed. Tools Appl. 2024, 83, 22609–22637. [Google Scholar] [CrossRef]
- Krari, A.; Hajami, A.; Jarmouni, E. Detecting the RPL Version Number Attack in IoT Networks Using Deep Learning Models. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 614–623. [Google Scholar] [CrossRef]
- Elsayed, R.; Hamada, R.; Hammoudeh, M.; Abdalla, M.; Elsaid, S.A. A Hierarchical Deep Learning-Based Intrusion Detection Architecture for Clustered Internet of Things. J. Sens. Actuator Netw. 2023, 12, 3. [Google Scholar] [CrossRef]
- Tripathi, G.; Singh, K.; Vishwakarma, D.K. Applied Convolutional Neural Network Framework for Tagging Healthcare Systems in Crowd Protest Environment. Math. Biosci. Eng. 2021, 18, 8727–8757. [Google Scholar] [CrossRef]
- Tian, H.; Li, R.; Di, Y.; Zuo, Q.; Wang, J. Employing RNN and Petri Nets to Secure Edge Computing Threats in Smart Cities. J. Grid Comput. 2024, 22, 32. [Google Scholar] [CrossRef]
- Qu, A.; Tang, Y.; Ma, W. Adversarial Attacks on Deep Reinforcement Learning-Based Traffic Signal Control Systems with Colluding Vehicles. ACM Trans. Intell. Syst. Technol. 2023, 14, 113. [Google Scholar] [CrossRef]
- Mohamed Moaaz, M.; Mohamed, E.H. Violence Detection in Surveillance Videos Using Deep Learning. Int. J. Inform. 2020, 2, 558–563. [Google Scholar] [CrossRef]
- India Brand Equity Foundation. Smart Cities Mission. Available online: https://www.ibef.org/government-schemes/smart-cities-mission (accessed on 3 March 2025).
- Christopher, M. China Plans Skynet-Like CCTV Surveillance System for the Moon. Available online: https://interestingengineering.com/innovation/china-skynet-on-the-moon (accessed on 3 March 2025).
- Miranda Calero, J.A.; Rituerto-Gonzalez, E.; Luis-Mingueza, C.; Canabal, M.F.; Barcenas, A.R.; Lanza-Gutierrez, J.M.; Pelaez-Moreno, C.; Lopez-Ongil, C. Bindi: Affective Internet of Things to Combat Gender-Based Violence. IEEE Internet Things J. 2022, 9, 21174–21193. [Google Scholar] [CrossRef]
- Kaur, B.; Ahuja, L.; Kumar, V. Decision Tree Model: Predicting Sexual Offenders on the Basis of Minor and Major Victims. In Proceedings of the 2019 Amity International Conference on Artificial Intelligence (AICAI), Dubai, United Arab Emirates, 4–6 February 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 193–197. [Google Scholar] [CrossRef]
- Secretaria Municipal de Segurança Urbana. Programa Smart Sampa. Available online: https://capital.sp.gov.br/web/seguranca_urbana/w/smart-sampa-2 (accessed on 9 March 2025).
- Ciudad de México. Premio de Oro por “Mi Ciudad Segura”. Available online: https://gobierno.cdmx.gob.mx/noticias/premio-de-oro-por-mi-ciudad-segura/ (accessed on 9 March 2025).
- De Medellín, A. Ciudad Inteligente. Available online: https://www.medellin.gov.co/es/programas/ciudad-inteligente/ (accessed on 9 March 2025).
- Gobierno de Santiago. Avanza en Proyectos y Soluciones para Construir una Ciudad Inteligente y Sostenible. Available online: https://corporacionrm.cl/avanza-en-proyectos-y-soluciones-para-construir-una-ciudad-inteligente-y-sostenible/ (accessed on 9 March 2025).
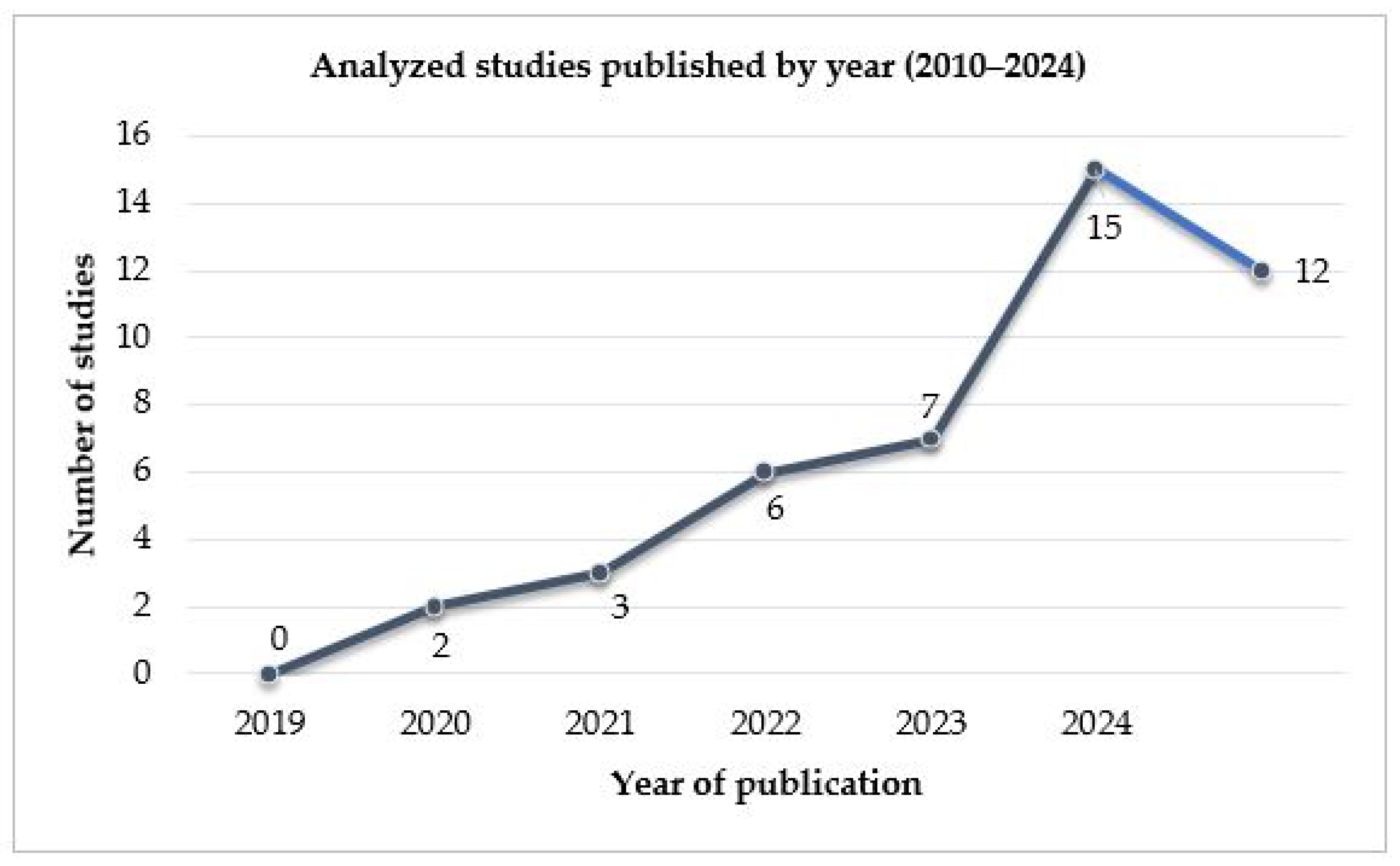
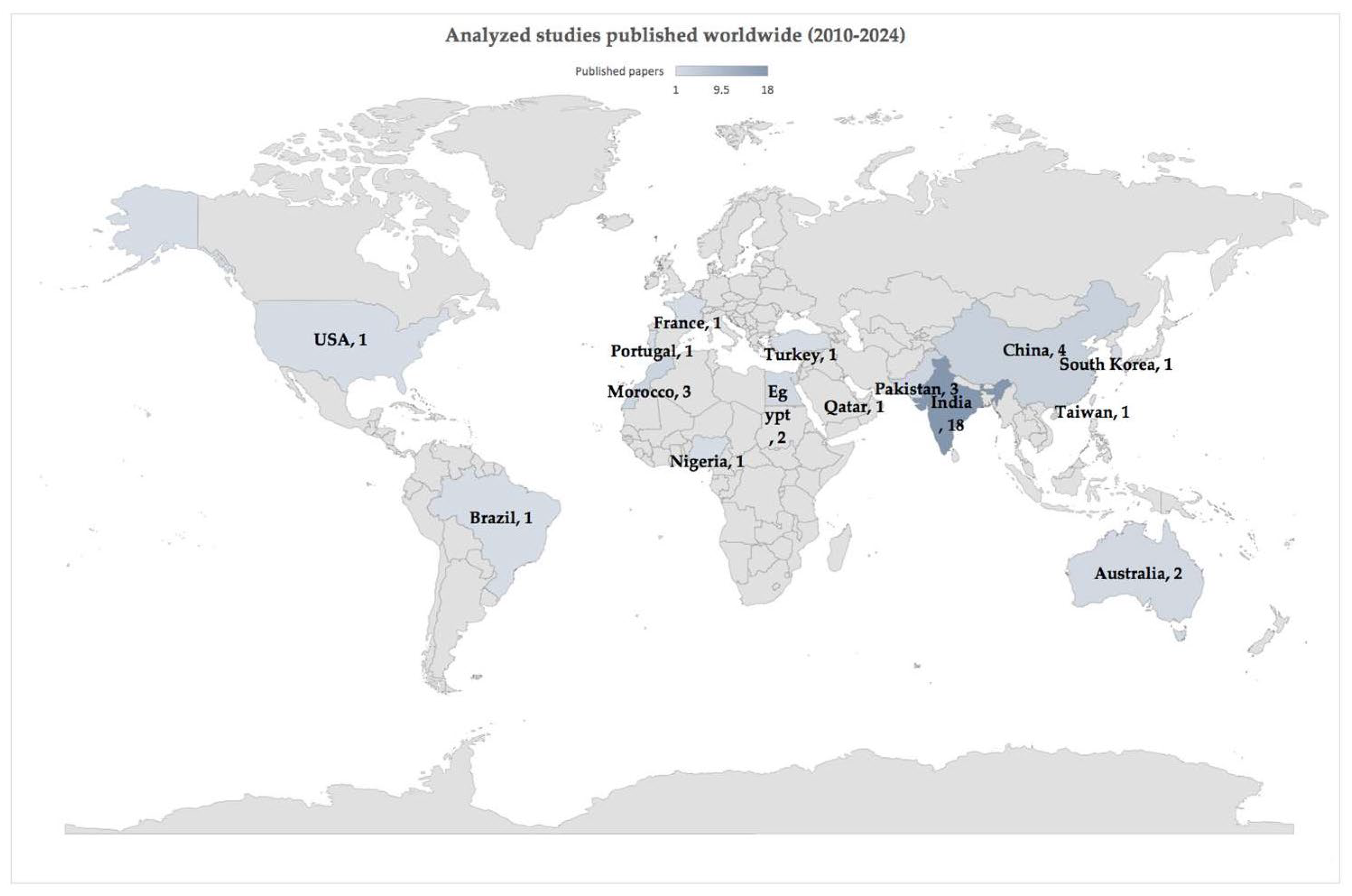

| Id | Year | Country | Information Source | Type of Paper | Quality Metric | Reference |
|---|---|---|---|---|---|---|
| S1 | 2021 | India | Scopus | Chapter | ★★★ | [22] |
| S2 | 2019 | China | Scopus | Journal | ★★★ | [23] |
| S3 | 2023 | India | Scopus | Conference | ★★★ | [17] |
| S4 | 2020 | Australia | Scopus | Conference | ★★★ | [24] |
| S5 | 2024 | Turkey | Scopus | Journal | ★★★ | [25] |
| S6 | 2024 | China | Scopus | Chapter | ★★★ | [26] |
| S7 | 2023 | India | Scopus | Conference | ★★★ | [27] |
| S8 | 2023 | Portugal | Scopus | Journal | ★★★ | [28] |
| S9 | 2022 | India | Scopus | Conference | ★★★ | [29] |
| S10 | 2024 | India | Scopus | Journal | ★★★ | [30] |
| S11 | 2024 | India | Scopus | Journal | ★★★ | [31] |
| S12 | 2022 | Qatar | Scopus | Journal | ★★★ | [32] |
| S13 | 2024 | India | Scopus | Journal | ★★★ | [33] |
| S14 | 2024 | Nigeria | Scopus | Journal | ★★★ | [34] |
| S15 | 2021 | Saudi Arabia | Scopus | Journal | ★★★ | [35] |
| S16 | 2023 | Egypt | Scopus | Journal | ★★★ | [36] |
| S17 | 2024 | India | Scopus | Chapter | ★★★ | [37] |
| S18 | 2023 | Taiwan | Scopus | Journal | ★★★ | [38] |
| S19 | 2021 | Brazil | Scopus | Conference | ★★★ | [39] |
| S20 | 2023 | China | Scopus | Chapter | ★★★ | [40] |
| S21 | 2024 | Pakistan | Scopus | Conference | ★★★ | [41] |
| S22 | 2023 | Saudi Arabia | Scopus | Journal | ★★★ | [42] |
| S23 | 2021 | Pakistan | Web of Science | Journal | ★★★ | [43] |
| S24 | 2024 | India | Scopus | Journal | ★★★ | [44] |
| S25 | 2022 | India | Scopus | Conference | ★★★ | [45] |
| S26 | 2019 | India | Scopus | Journal | ★★★★ | [46] |
| S27 | 2024 | India | Scopus | Journal | ★★★ | [47] |
| S28 | 2023 | South Korea | Scopus | Conference | ★★★★ | [48] |
| S29 | 2022 | India | Scopus | Journal | ★★ | [49] |
| S30 | 2022 | France | Scopus | Conference | ★★★ | [50] |
| S31 | 2021 | India | Scopus | Conference | ★★ | [51] |
| S32 | 2020 | Morocco | Scopus | Conference | ★★★ | [52] |
| S33 | 2023 | India | Scopus | Conference | ★★★ | [31] |
| S34 | 2022 | Saudi Arabia | Web of Science | Journal | ★★★ | [53] |
| S35 | 2021 | Australia | Web of Science | Journal | ★★★ | [54] |
| S36 | 2024 | Morocco | Web of Science | Journal | ★★★ | [55] |
| S37 | 2022 | India | Web of Science | Journal | ★★ | [56] |
| S38 | 2023 | Saudi Arabia | Web of Science | Journal | ★★★ | [57] |
| S39 | 2023 | India | Web of Science | Journal | ★★★ | [58] |
| S40 | 2023 | Morocco | Web of Science | Journal | ★★★ | [59] |
| S41 | 2023 | Egypt | Web of Science | Journal | ★★★ | [60] |
| S42 | 2021 | India | Web of Science | Journal | ★★★★ | [61] |
| S43 | 2024 | China | Web of Science | Journal | ★★★ | [62] |
| S44 | 2023 | USA | Web of Science | Journal | ★★ | [63] |
| S45 | 2023 | Pakistan | Web of Science | Journal | ★★★★ | [64] |
| Id | Proposal | Deep Learning Model Used | Used Dataset | Detected Violence Actions | Detected Crime Actions |
|---|---|---|---|---|---|
| S1 | Detection of terrorist activities on social media | CNN (Convolutional Neural Networks) | Images and videos of social media | Identification of criminal activities through images and videos on social media | Alert system for human operators to take immediate action |
| S2 | Intrusion detection | Deep Migration Learning Model (DMLM) | KDD CUP 99 | N/A | N/A |
| S3 | Real-time intrusion detection | CNN-LSTM (Long Short-Term Memory) | Bot-IoT, IoTID20 | DDoS (Distributed Denial of Service), Flood, Botnet attacks | N/A |
| S4 | Cyberattack detection | Artificial Neural Network (ANN) | UNSW NB15 | IoT attacks, unauthorized access, botnet | N/A |
| S5 | Energy theft detection | CNN | Real and synthetic data | N/A | Detection of cyberattacks on smart meters |
| S6 | Intrusion detection | LSTM-CNN | KDDCup99 | N/A | Cybercrime (malicious flow) |
| S7 | Host intrusion detection for IoT | O-CNN (Optimized CNN) | BoT-IoT | N/A | Cybercrime: DDoS, data exfiltration, key logging |
| S8 | Intrusion detection system (IDS) | Deep Neural Network (DNN) | IoT-23 y MQTT-IoT-IDS2020 | N/A | Anomaly detection and attacks in IoT device networks |
| S9 | DDoS detection | DNN with Hyperparametrization | CICDDoS 2019 dataset | N/A | Cyberattacks (DDoS, including TCP Syn, UDP flood, and ICMP attacks) |
| S10 | Attack detection in IoT | Deep Belief Networks (DBNs) + CNN | UNSW-NB15 | N/A | Property crimes |
| S11 | Intrusion detection | DNN, Extreme Gradient Boosting (XGBoost) | UNSWNB15 | N/A | Detects network intrusions, including DoS (Denial of Service), DDoS, and malicious IoT activities |
| S12 | IDS | Multi-Layer Perceptron (MLP) | BlueTack dataset | N/A | Cybercrime |
| S13 | Surveillance of smart homes | Yolo7 with transfer learning | Roboflow datasets | Street violence | Property crimes, personal crimes |
| S14 | IoT-Defender | Genetic Algorithm (GA)-LSTM | UNSW-NB15 | N/A | Cybercrime |
| S15 | IDS | GRU (Gated Recurrent Unit) | Data of CPS | N/A | DoS attacks |
| S16 | Self-adaptive traffic identification intrusion detection system | LSTM | ToN-IoT, InSDN | N/A | DoS/DDoS attacks, XSS (Cross-Site Scripting), BFA (Brute Force Attack), MitM, Backdoor, Probe, Web |
| S17 | IDS | X-DeepID (Hybrid CNN-LSTM) | ToN-IoT | N/A | Enhances intrusion detection in IoT |
| S18 | Lightweight meta-learning BotNet attack detection | Meta-Learning Ensemble (Super Learner, Subsemble, Sequential Learner) | KDD99 | N/A | Botnet traffic detection and cyberattacks in IoT categorized as malicious network flows |
| S19 | IoT-based IDS with Deep Learning | CNN-RNN-LSTM, DNN, LSTM | MQTT-IoT-IDS2020 | N/A | Message Queuing Telemetry Transport (MQTT) attacks: aggressive scanning, UDP scanning, brute force in SSH and MQTT |
| S20 | Attack detection in IoT network traffic | CNN optimized with SE-Net and Capsule Networks | Network traffic | N/A | DDoS attacks, Botnets, network traffic anomalies |
| S21 | Intrusion detection in smart cities | Gradient Boosting | IoTID20 | N/A | DoS/DDoS attacks, ransomware, port scanning, Man-in-the-Middle (MITM) attacks, malware, injection attacks |
| S22 | Cyberattack detection | Cascaded Adaptive Neuro-Fuzzy Inference System (CANFIS) + Modified Deep Reinforcement Learning (MDRL) | ISCX 2012 IDS, IoT network intrusion | N/A | Botnet malware attacks (Mirai), UDP Flooding, SMTP spam |
| S23 | Decision support system for facial sketch synthesis | Spiral-Net (Spiral Neural Network), SNET (Spiking Neural Network-based Intrusion Detection System) | CUFS, CUFSF, IIT photo-sketch dataset | Identification of suspects through sketches, facial recognition for forensic support | N/A |
| S24 | IDS | GA-CNN | MQTT-IoT-IDS2020 | N/A | DDoS, injection, ransomware |
| S25 | IDS | DHLNN optimized with HCSGA (Hybrid Chicken Swarm Genetic Algorithm) | NSL-KDD | N/A | IoT network intrusions |
| S26 | Smart urban management system | CNN | Images of CCTV | Detection of weapons (guns) | N/A |
| S27 | IoT intrusion detection | Hybrid CNN-BILSTM with Transfer Learning | N_BaIoT (data of attacks botnet). | N/A | Detection and classification of Mirai and BASHLITE attacks |
| S28 | Violence detection in industrial surveillance videos using IoT | CNN, LSTM, GRU | Hockey fight dataset | Fights, use of knives or firearms | N/A |
| S29 | IoT-based smart security system for homes | Single-Shot MultiBox Detector (SSD) | Common Objects in Context (COCO) | Unauthorized intrusion; detection of suspicious tools | Theft; unauthorized access to residential properties |
| S30 | Intrusion detection using explainable artificial intelligence (XAI) | DNN | NSL-KDD | N/A | DDoS, Probe, Backdoors, Fuzzers |
| S31 | Multi-cloud intrusion detection system (MCIDS) | CNN | UNSW-NB15 | N/A | Unauthorized access, data theft, and privacy invasion |
| S32 | Intrusion detection | DNN | CICDDoS2019 | N/A | DDoS attacks |
| S33 | Electricity theft detection | Stacked CNN + Random Forest | Electricity theft | N/A | Electricity theft |
| S34 | Intrusion detection system | Voting Classifier | ToN-IoT telemetry | N/A | Attacks like DDoS, ransomware, XSS, etc. |
| S35 | Detection of DDoS and Replay attacks | Hybrid (Restricted Boltzmann Machin (RBM) + CNN) | Smart soil | N/A | DDoS, Replay |
| S36 | Intrusion detection in IoT | LSTM | Edge-IIoT | N/A | DDoS, SQL injection, ransomware |
| S37 | Attack detection in IoT | Hybrid (CNN + DBN) | N/A | N/A | DDoS attacks, ransomware, SQL injections |
| S38 | Hybrid deep learning for detection and classification of malicious URLs | Stacked Autoencoder (SAE) and BiLSTM (Bidirectional LSTM) | Malicious URLs | Not applicable (focused on detection of malicious URLs) | Phishing, malware, defacement |
| S39 | Hybrid deep learning with Blockchain and IoT for smart city security | Hybrid LSTM-Support Vector Machine (SVM) | UNSW-NB15 | Not applicable (cyberattacks) | Cyberattacks: DoS, fuzzers, exploits, reconnaissance |
| S40 | Detection of routing protocol for low-power lossy networks (RPL) version number attacks in IoT | LSTM | Simulated Dataset with Cooja Simulator | Not applicable (cyberattacks) | Manipulation of Destination Oriented Direct Acyclic Graph Information Object (DIO) messages, increased latency |
| S41 | Hierarchical intrusion detection system | LSTM based on Recurrent Neural Network (RNN) | ToN-IoT | N/A | Various cyberattacks |
| S42 | Label health systems in mass protests | CNN | Curated protest dataset and violence data extracted from YouTube | Protests turned violent: assaults, severe disturbances | Arson, object throwing, clashes with security forces |
| S43 | Advanced security framework for edge computing in smart cities | Extreme Learning Machines (ELMs) + Replicator Neural Networks + Deep Reinforcement Learning–Deep Q-Network (DRL-DQN) | CICIDS2017 | N/A | Distributed Denial of Service (DDoS) attacks |
| S44 | Adversarial attacks on DRL-based traffic signal control systems | DRL, Proximal Policy Optimization (PPO) | Simulated traffic data based on Monaco | Vehicle collusion to alter signaling times | Traffic data manipulation to falsify conditions |
| S45 | Violence detection in surveillance videos | CNN + LSTM | Hockey fights | Fist fights, abuse with non-projectile weapons | N/A |
| Id | Scope | Testing Context | Implementation Feasibility | Code Availability | Benefits | Technical Limitations |
|---|---|---|---|---|---|---|
| S1 | Detection of terrorist activities in social networks and prediction of attacks | Simulation | High | No | Improved monitoring of online activities | Complexity in unstructured data analysis |
| S2 | Real-time analysis platform to increase security in IoT networks | Simulation | Moderate | No | Improvement in intrusion detection | Limitations in the processing capacity of the nodes |
| S3 | Real-time detection of intrusions and threats in IoT networks | Simulation | Moderate | Partial | High accuracy and lower false positive rate | Limited resources in IoT |
| S4 | Intrusion and anomaly detection to increase the security of smart city applications | Simulation | Moderate | No | Early identification of IoT attacks | Limitations on IoT resources |
| S5 | Malicious consumption detection for fraud classification | Simulation | Moderate | Yes | Increased detection of fraudulent consumption | Possible overfitting in real data |
| S6 | Intrusion detection | Simulation | Moderate | Yes | High detection accuracy | Dependence on training data |
| S7 | Intrusion detection | Simulation | Moderate | Yes | Improvement in the security of IoT devices | Optimize for data quality and resource-constrained devices |
| S8 | Detection of anomalies in IoT network traffic to protect against cyber attacks | Simulation | Moderate | Yes | Improvement in the security of IoT networks and early detection of attacks | Limited resources on IoT devices can affect performance |
| S9 | Detection of DDoS for improving security | Simulation | Moderate | No | High accuracy in detecting DDoS attacks | Need for optimization to avoid high execution times on large volumes of data |
| S10 | IoT attack detection system | Simulation | Moderate | Yes | Improved incident response | Requires advanced infrastructure |
| S11 | Network intrusion detection to improve data protection and network security | Simulation | Moderate | Yes | High detection accuracy, reduction in false positives | Complex IDS configuration |
| S12 | Intrusion detection to improve medical data protection | Simulation | Moderate | No | Improvement in data security | Limitations in processing capacity |
| S13 | Threat detection to increase security | Simulation | Moderate | Yes | Reduction in false positives | Dependence on data quality |
| S14 | Intrusion detection for improving the security in IoT | Simulation/Real | Moderate | Yes | Quickly identify attacks | Limited resources on edge devices |
| S15 | Intrusion detection for improving the security in cyber-physical systems | Simulation | Moderate | No | High detection accuracy | Attack data dependency. Computational complexity |
| S16 | Intrusion detection for improving the security in IoT | Simulation | Moderate | Yes | Improved attack detection | Dependency on quality data |
| S17 | Intrusion detection for improving the security in IoT | Simulation | Moderate | Yes | Improvement in attack detection | Complexity in implementation |
| S18 | Detection of botnets in IoT network traffic | Real | Moderate | No | Protection of IoT devices without the need for expensive infrastructure | Training data dependency |
| S19 | Detection of MQTT attacks in IoT networks | Simulation | Moderate | Yes | High precision in detecting intrusions in IoT networks | Requires preprocessing and data balancing |
| S20 | Detection and classification of intrusions to increase protection against cyberattacks | Simulation | Moderate | Yes | Improved network security | Configuration complexity |
| S21 | Detection and classification of intrusions to increase protection against cyberattacks | Simulation | Moderate | No | Improvement in intrusion detection | Challenges in data management |
| S22 | Detection and isolation of attacks to improve the security of IoT devices | Simulation | Moderate | No | High precision in detection | Dataset-dependent, captures specific attacks |
| S23 | Automatic synthesis of facial sketches improving forensic identification and reducing recognition errors | Real | Moderate | No | Improved facial identification accuracy | Limited datasets, difficulty in fine facial details |
| S24 | Intrusion detection for improving the security of systems | Simulation | Moderate | Yes | Improved detection | Data dependency |
| S25 | Intrusion detection for improving the security of systems | Simulation | Moderate | No | Improved detection | Susceptibility to data characteristics |
| S26 | Weapons detection, waste management, and traffic control to improve public safety | Real | Moderate | Yes | Improved security | Dependence on data quality |
| S27 | Efficient detection of botnet attacks in IoT | Simulation | N/A | No | High precision and robust attack classification | Requires significant computational resources |
| S28 | Automatic violence detection | Simulation | N/A | No | Improved security and reduction in manual efforts | Dependence on video quality and IoT connectivity |
| S29 | Automatic object detection and classification | Real | N/A | No | Improved security and real-time alerts | Problems with images in low lighting conditions |
| S30 | Intrusion detection | Simulation | Moderate | Yes | Reliability | Dependency on quality data |
| S31 | Intrusion detection for improving the security in IoT | Simulation | Moderate | No | Improved detection | Dependency on quality data |
| S32 | Attack detection for improving the security in IoT | Simulation | Moderate | No | Improved attack detection | Dependency on quality data |
| S33 | Detection of electricity theft in smart networks | Simulation | Moderate | No | Reduction in financial losses | Risk of overfitting and data limitation |
| S34 | Identification and prevention of intrusions in IoT networks | Simulation | Moderate | No | High precision in threat detection | Dependency on high computing resources |
| S35 | Identification of DDoS attacks in smart environments | Simulation | Moderate | No | High precision and time-efficient | Complexity when modeling temporal dependencies |
| S36 | Intrusion detection and improving security in IoT | Simulation | Moderate | No | Improved security with high precision | Processing dependence on advanced hardware |
| S37 | Intrusion detection and improving security in IoT | Simulation | Moderate | No | High accuracy in threat identification | Complexity in hyperparameter optimization processes |
| S38 | Automatic classification and detection of malicious URLs | Simulation | Complex | No | High precision, efficient detection of cyber threats | High dependence on computational resources |
| S39 | Attack classification and secure environment management for IoT transactions | Simulation | Complex | No | High precision, safety improvement | Requires high computing power |
| S40 | Identification and mitigation of Routing Protocol for Low-Power and Lossy Networks (RPL) attacks | Simulation | Complex | No | Security improvement, threat mitigation | Reliance on extensive simulations |
| S41 | Accurate detection of anomalies in IoT traffic to protect the system from cyber attacks | Simulation | Complex | No | Improved security and optimization of energy consumption | Requires specific data for training |
| S42 | Protest classification and severity labeling | Simulation | Complex | No | Faster response in emergencies | Visual data dependency; risk of model overfitting |
| S43 | Anomaly detection and improved incident response | Simulation | Moderate | No | Increase in security | Dependency on precise data |
| S44 | Adaptive traffic control resistant to adversarial attacks | Simulation | Moderate | No | Reduction in waiting time in false collisions | Reliance on accurate data and risks of bias in models |
| S45 | Violence detection in digital videos | Simulation | Moderate | No | Improvement in the detection of violence | Training data dependency |
| Category of Tools | Tools and Studies Which Applied Them |
|---|---|
| Programming languages | Python: S1, S2, S3, S4, S5, S6, S7, S8, S9, S10, S11, S12, S13, S14, S15, S16, S17, S18, S19, S20, S21, S24, S26, S27, S28, S29, S30, S31, S32, S33, S34, S35, S36, S37, S38, S39, S40, S41, S42, S43, S44, S45, S23; Java: S25; Matlab: S22 |
| Frameworks | TensorFlow: S1, S3, S5, S8, S9, S10, S11, S12, S13, S19, S20, S21, S23, S24, S27, S28, S29, S31, S32, S33, S34, S35, S36, S37, S43, S44, S45; Keras: S1, S3, S4, S5, S6, S10, S11, S13, S19, S21, S23, S24, S25, S27, S41; PyTorch: S11, S44; Scikit-learn: S3, S4, S5, S11, S12, S13, S16, S18, S19, S21 |
| Hardware | GPU: S1, S3, S5, S10, S19, S42, S35; CPU: S3, S4, S5, S13, S35; Raspberry Pi: S14, S18, S26; Intel Core i7: S3, S16, S21, S23, S33; Intel Core i5: S4, S23, S41, S44; Raspberry Pi: S14, S18, S26; NVIDIA: S10, S39, S42, S45, S23; Cloud based server: S23, S44; Google Collaboratory: S18 |
| Complementary tools | Numpy (S4, S11, S29); Pandas (S4, S11, S12); Scikit-learn (S3, S4); Wireshark (S10, S16, S40); tcpdump (S6, S14); Roboflow (S13); SHAP, LIME, RuleFit (S30); SMOTE (S21, S34); Flask (S26); GridSearchCV (S19); Zeek/Bro IDS (S18); BoT-IoT dataset (S7); SUMO (S44); Autoencoder (S36); FastText (S38); OpenCV, Matplotlib (S45); PyCharm (CE); OpenCV (S13, S29); Dask (S19) |
| Statistics | Accuracy (%) | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| Studies that use metric | 39.00 | 33.00 | 32.00 | 31.00 |
| Mean | 97.44 | 96.13 | 96.06 | 96.00 |
| Standard deviation | 4.13 | 6.09 | 6.09 | 6.08 |
| Min value | 82.26 | 77.60 | 78.90 | 75.80 |
| 25% | 97.13 | 96.91 | 96.89 | 96.29 |
| 50% | 99.28 | 98.90 | 98.60 | 98.63 |
| 75% | 99.74 | 99.54 | 99.44 | 99.29 |
| Max value | 100.00 | 100.00 | 100.00 | 100.00 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Simisterra-Batallas, C.; Pico-Valencia, P.; Sayago-Heredia, J.; Quiñónez-Ku, X. Internet of Things and Deep Learning for Citizen Security: A Systematic Literature Review on Violence and Crime. Future Internet 2025, 17, 159. https://doi.org/10.3390/fi17040159
Simisterra-Batallas C, Pico-Valencia P, Sayago-Heredia J, Quiñónez-Ku X. Internet of Things and Deep Learning for Citizen Security: A Systematic Literature Review on Violence and Crime. Future Internet. 2025; 17(4):159. https://doi.org/10.3390/fi17040159
Chicago/Turabian StyleSimisterra-Batallas, Chrisbel, Pablo Pico-Valencia, Jaime Sayago-Heredia, and Xavier Quiñónez-Ku. 2025. "Internet of Things and Deep Learning for Citizen Security: A Systematic Literature Review on Violence and Crime" Future Internet 17, no. 4: 159. https://doi.org/10.3390/fi17040159
APA StyleSimisterra-Batallas, C., Pico-Valencia, P., Sayago-Heredia, J., & Quiñónez-Ku, X. (2025). Internet of Things and Deep Learning for Citizen Security: A Systematic Literature Review on Violence and Crime. Future Internet, 17(4), 159. https://doi.org/10.3390/fi17040159






