Force-Based Self-Organizing MANET/FANET with a UAV Swarm
Abstract
:1. Introduction
1.1. Mobile Ad Hoc Networks (MANETs), Flying Ad Hoc Networks (FANETs)
1.2. Using Drones to Deploy MANETs
- Flexibility of resource sourcing and maintenance: since the collective of drones (the swarm) is comprised of physically distinct and independently operating devices, the deployment of such a swarm (including the addition and removal of drones during operation) can be very flexible. The operations are the sum of the actions of independent units, which allows for different stakeholders and operators to pool their resources while each maintaining separate responsibility and ownership for the resources they contributed. Especially in cases where large-scale infrastructure, beyond the financial or operational resources of any one party, has been rendered inoperable, this enables smaller parties to come together and collectively solve a problem/provide a service.
- Adaptive network topology [7,16]: when drones are launched with the express goal of becoming members in a MANET, their movement can be designed to contribute to this goal. Due to this, drones that have no other objective can collaborate with those that do by optimizing their position to improve the overall performance of the MANET. This strengthens the ability of the MANET to respond to changing demand profiles and to client terminal movement.
- Exploiting advantages of aerial positions: purely through their ability to move in 3D space, drones can assume positions that offer advantages due to (a) not being restricted by obstacles on the ground (regarding signal transmission), (b) not being affected by conditions on the ground (with regard to the safety of the device). This does come at the price of increased operational cost (as the flight operations require continuous investment of resources) but a sufficiently large number of drones can offset this at least regarding node availability (by retiring drones that are low on battery and sending them home to re-charge).
- Reactivity and resilience: not only can drones position themselves to optimize the topology, but they can dynamically amend their positioning to ensure desired levels of redundancy. This allows them to establish a topology not only suitable for the current state of affairs but also for potential future conditions.
1.3. Real-World Challenges to Drone-Based MANETs
1.4. Contributions of the Paper
2. Mobile Ad Hoc Networks (MANETs)
2.1. Mobile Ad Hoc Networks (MANETs): Applications and Challenges
2.2. Scope of the Paper
2.3. Target MANET-Applications and -Scenarios
2.3.1. Disaster Response
2.3.2. Wilderness Exploration
2.3.3. Contested Environments
3. Modeling MANETs
3.1. Nodes and Clients
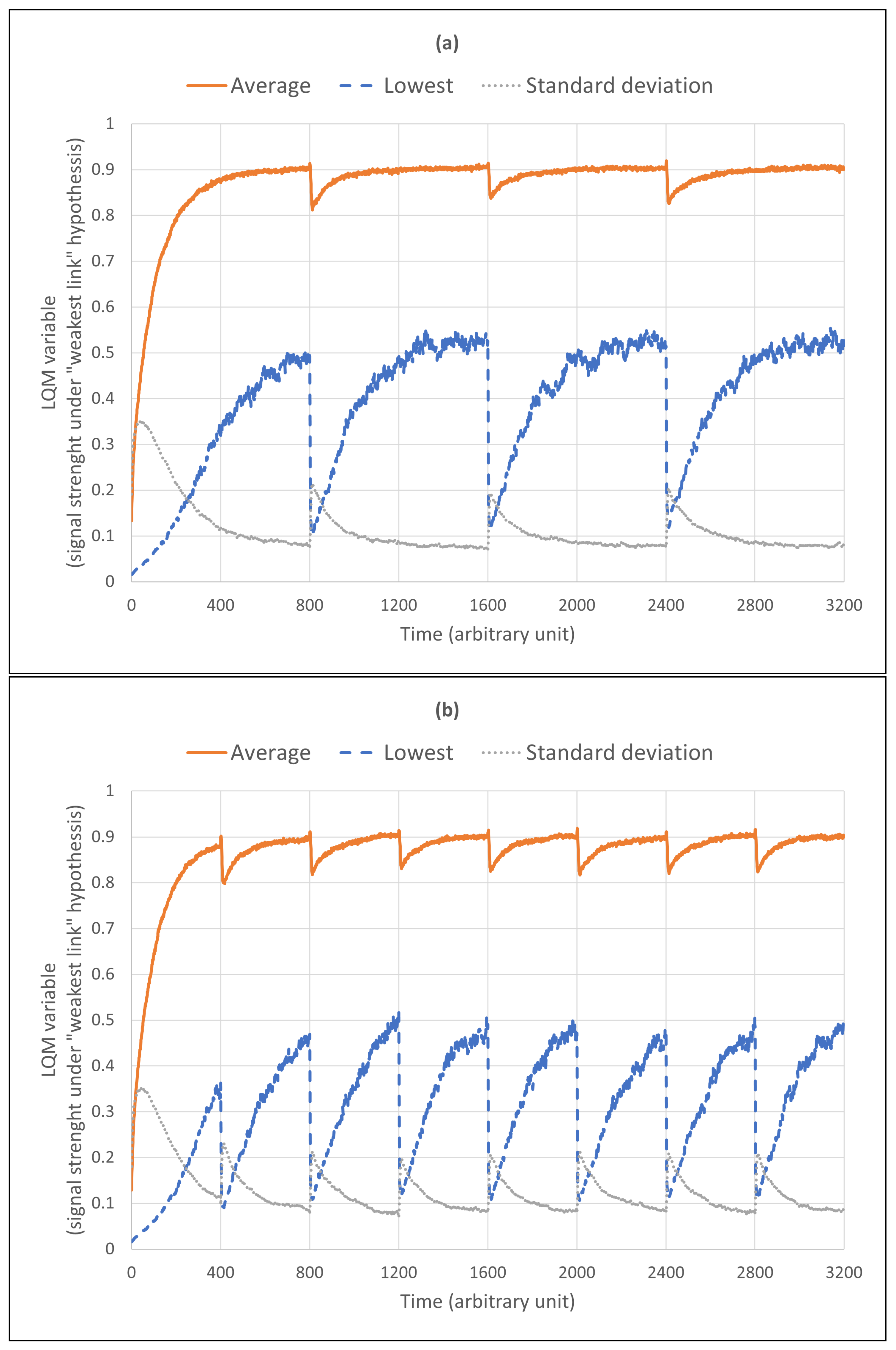
3.2. Link Quality Metric (LQM)
3.3. Stress Level
3.4. Miscellaneous Modeling Choices
3.4.1. Position, Navigation and Timing (PNT)
3.4.2. Central Dispatch
4. A Novel Self-Organizing Approach to Drone-Based MANETs
4.1. Drone Movement
4.1.1. Moving Towards Clients
Mathematical Modeling of the Attraction of Affiliated Clients
4.1.2. Moving Away from Other Drones
Mathematical Modeling of the Repulsion from Other Drones
4.1.3. Maintaining Connectivity and Routing
Mathematical Modeling of the Force Ensuring Connectivity
4.1.4. Overall Movement
Mathematical Modeling of the Overall Force Governing a Node’s Movement
4.2. Dynamic Drone Deployment and Recall
4.2.1. Dynamic Deployment
4.2.2. Dynamic Recall
4.3. Dynamic Adaptive Topology Management
5. Performance Evaluation
5.1. Numerical Experiment Setup
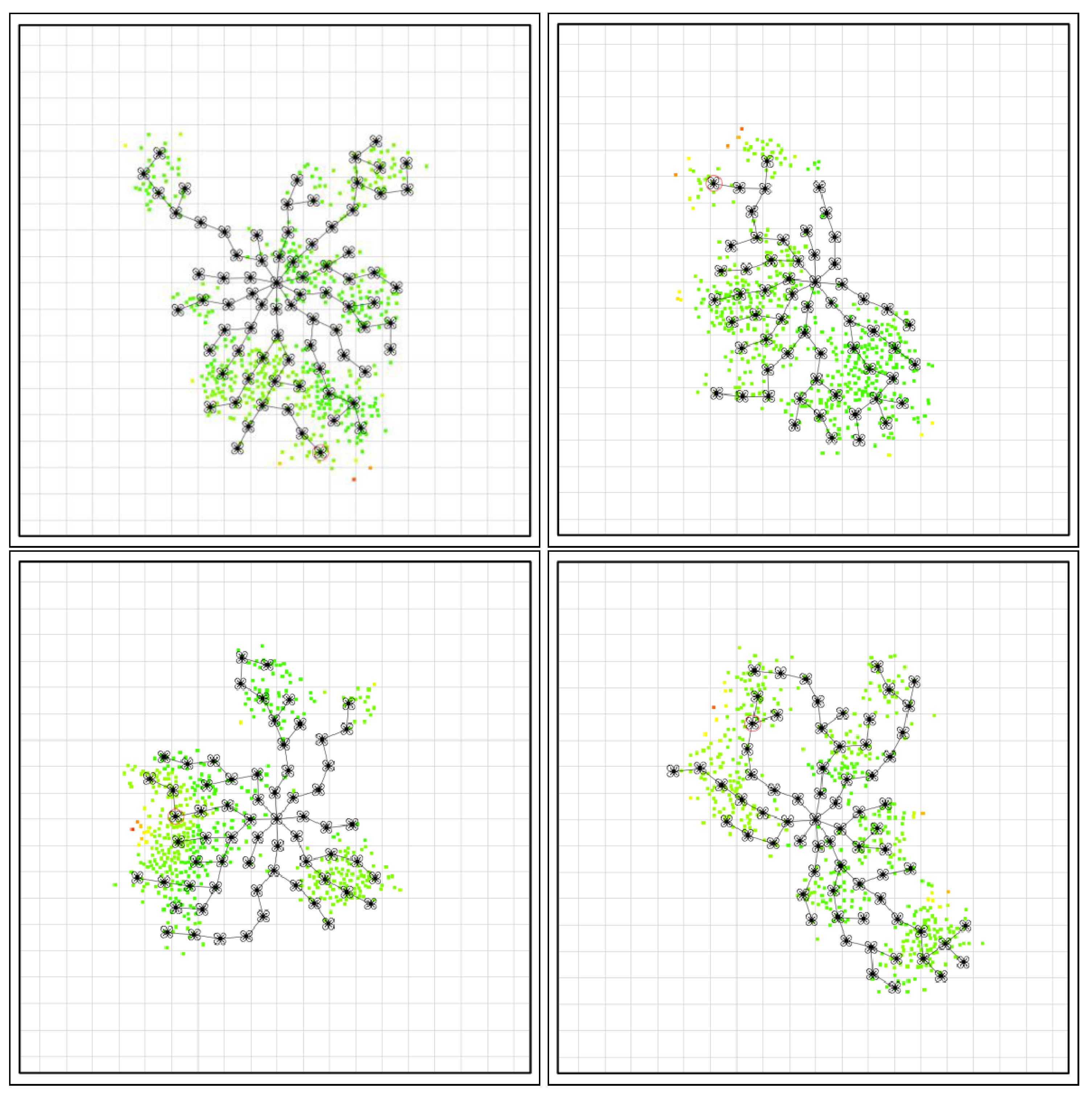
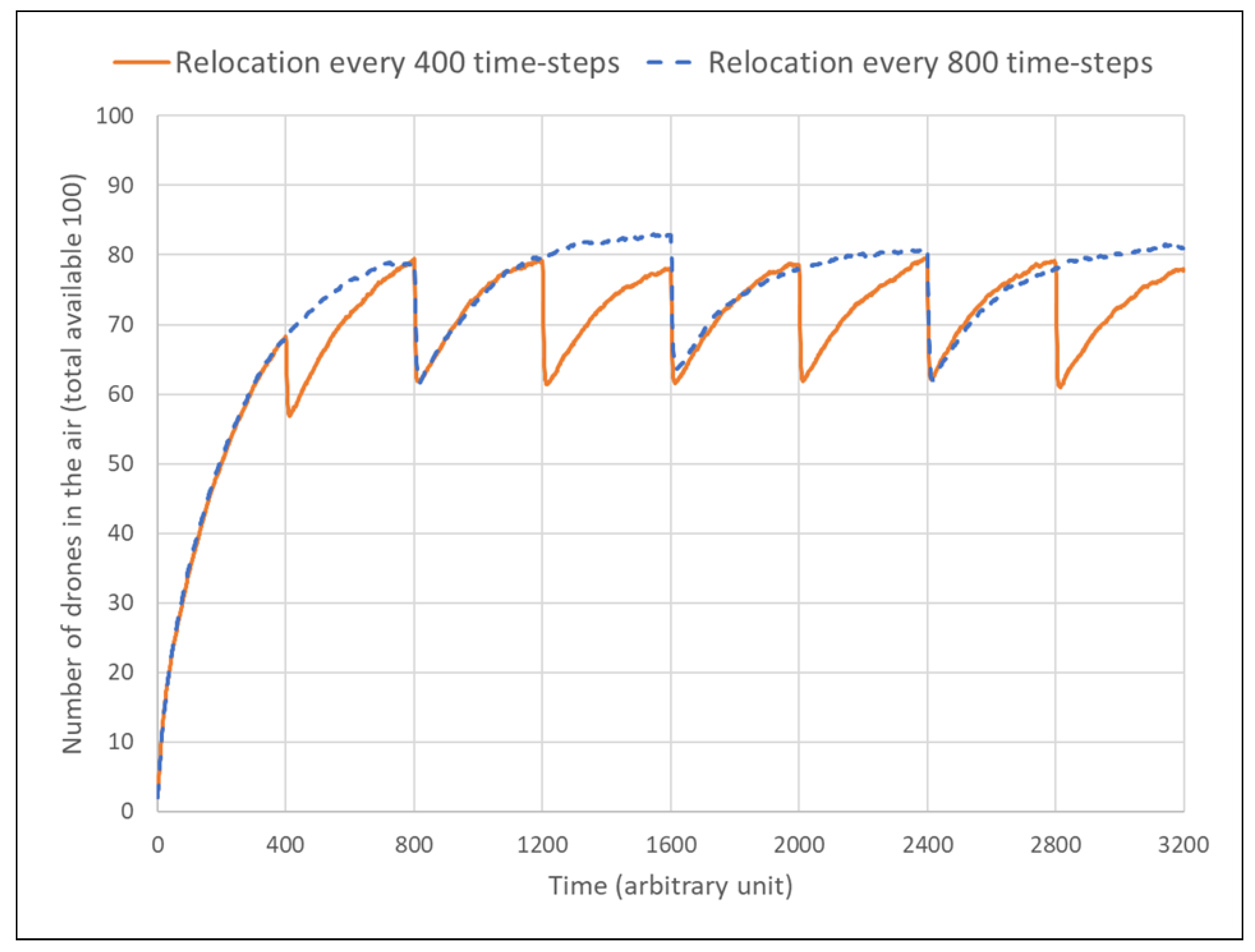
5.2. Results
- Swarm size appears to saturate at around 80 for the used values (coverage area, number of clients/clusters), which is lower than the total number of drones available (100), indicating the system’s ability to commit only the necessary resources.
- After relocation, the total number of drones in the air does not drop below about 60, so the adaptation process is not equivalent to a “reboot”. Only about 25% of the swarm (≈20 units) is being “retired” (then progressively replaced), whereas the remaining 75% just “follow the clients” in their migration.
6. Conclusions and Future Work
6.1. Summary
6.2. Conclusions
6.3. Future Work
- We have not explored extreme outlier scenarios, such as the case where there are no clients present or where all clients have aggregated at the extreme ends of the map.
- The introduction mentions resilience as a benefit for MANET’s (see Section 1.2). The MANET approach we developed does not provide any redundancy. However, we expect that this can be designed into the swarm and are hoping to proceed with work focusing on this (and the formal verification thereof) in the near future.
- We argue that the parameters needed to control energy efficiency are already included in the force-based control of the nodes in the network: in Section 4.1.3, Equation (7), we set the inter-drone distance for which the value of this force becomes infinitesimally small to 1. As distance affects energy efficiency later work can use this part of the model to modulate the power required for inter-drone communication.Similarly, the LQM (Section 3.2) is set to plateau for the distance value of 1. Despite this connection to the energy cost incurred when transmitting data over the resulting MANET, our current investigations do not assess this cost.Future work, especially work directed at specific applications, will include considerations for this network performance indicator.
- During performance evaluation we noted that small changes in the setup as well as in Equations (5)–(7) led to peculiar emergent behaviors of the swarm (such as, e.g., a long arm of connected drones swaying from left to right until they connect with a client). Future work will investigate the design and use of such behaviors and the environmental conditions necessary to achieve them.
- In Equation (2) we defined the LQM value as simply the weakest link in the route from root to client. We can define this value in a more complex manner to reflect additional properties of the connection, the resulting LQM will be subject to the signal deterioration in the entire route to the root. The recursive definition for for any node i connected to the best available access point j is thus:Under this revised definition, any sub-optimal link anywhere in the connection to the router will further degrade the overall LQM value (the presented work only considers the last link). This affects the deployment of additional nodes in at least two ways. Firstly, since sub-optimal links closer to the router may further lower the LQM value this directly impacts the deployment of additional nodes, which may now be deployed earlier (thereby potentially improving the individual link quality and thus the overall connectivity). Secondly, the LQM values now reflect the actual connection quality better and are thus more likely to result in new nodes being dispatched to the locations where they are needed most. To motivate the latter claim, consider two routes of LQM value , one where all links are perfect except one and another where all links have the sub-optimal value of . The second route would (correctly) receive a much lower overall LQM value and thus be allocated an additional drone first. Exploring the impact of this revised performance measure is future work.
- In Section 2.3 we have specifically restricted our scenario to the 2D domain. With a large number of projects in our labs being rooted in the maritime sector, the presented work currently meets our needs. That being said, while we do not foresee any issues with extending the theory to 3D in general, working on an amended approach for obstacle-rich environments or challenging landscapes (such as, e.g., urban canyons or indoor search-and-rescue) is considered future work.
Author Contributions
Funding
Conflicts of Interest
References
- Li, X.; Chen, J.; Li, J. FATES: A Framework with Adaptive Track-Explore Strategy for Moving Targets Search by a FANET. In Proceedings of the 2018 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Ubiquitous Computing & Communications, Big Data & Cloud Computing, Social Computing & Networking, Sustainable Computing & Communications (ISPA/IUCC/BDCloud/SocialCom/SustainCom), Melbourne, VIC, Australia, 11–13 December 2018; pp. 856–861. [Google Scholar] [CrossRef]
- Shumeye Lakew, D.; Sa’ad, U.; Dao, N.N.; Na, W.; Cho, S. Routing in Flying Ad Hoc Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutorials 2020, 22, 1071–1120. [Google Scholar] [CrossRef]
- Singh, H.; Verma, S.; Adhya, A. A Brief Review on Position-based Routing Protocols in Flying Ad-hoc Networks. In Proceedings of the 2022 5th International Conference on Contemporary Computing and Informatics (IC3I), Uttar Pradesh, India, 14–16 December 2022; pp. 1423–1428. [Google Scholar] [CrossRef]
- El-Zoghby, A.M.; Mosharafa, A.; Azer, M.A. Anonymous Routing Protocols in MANETs, a Security Comparative Analysis. In Proceedings of the 2018 14th International Computer Engineering Conference (ICENCO), Cairo, Egypt, 29–30 December 2018; pp. 254–259. [Google Scholar] [CrossRef]
- Sathyaraj, P.; Devi, S.; Swethareddy, A.; Manimegalai, L.; Kannan, K.; Babu, M. A Dynamic Resource Allocation Protocol: Device to Device Communication For MANETs. In Proceedings of the 2022 International Conference on Advanced Computing Technologies and Applications (ICACTA), Coimbatore, India, 4–5 March 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Singal, G.; Laxmi, V.; Gaur, M.; Rao, D.V.; Kushwaha, R. UAVs Reliable Transmission for Multicast Protocols in FANETs. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; pp. 130–135. [Google Scholar] [CrossRef]
- Kadivar, M. An Adaptive Yao-based topology control algorithm for wireless ad-hoc networks. In Proceedings of the 2020 10th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 29–30 October 2020; pp. 457–462. [Google Scholar] [CrossRef]
- Jasim, K.S.; Ali Alheeti, K.M.; Najem Alaloosy, A.K.A. A Review Paper on Secure Communications in FANET. In Proceedings of the 2021 International Conference of Modern Trends in Information and Communication Technology Industry (MTICTI), Sana’a, Yemen, 4–6 December 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Hamdi, M.M.; Yussen, Y.A.; Mustafa, A.S. Integrity and Authentications for service security in vehicular ad hoc networks (VANETs): A Review. In Proceedings of the 2021 3rd International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 11–13 June 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Al-shareeda, M.A.; Alazzawi, M.A.; Anbar, M.; Manickam, S.; Al-Ani, A.K. A Comprehensive Survey on Vehicular Ad Hoc Networks (VANETs). In Proceedings of the 2021 International Conference on Advanced Computer Applications (ACA), Maysan, Iraq, 25–26 July 2021; pp. 156–160. [Google Scholar] [CrossRef]
- Hameed, A.G.; Mahmoud, M.S. Vehicular Ad-hoc Network (VANET) – A Review. In Proceedings of the 2022 Iraqi International Conference on Communication and Information Technologies (IICCIT), Basrah, Iraq, 7–8 September 2022; pp. 367–372. [Google Scholar] [CrossRef]
- Ramphull, D.; Mungur, A.; Armoogum, S.; Pudaruth, S. A Review of Mobile Ad hoc NETwork (MANET) Protocols and their Applications. In Proceedings of the 2021 5th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 6–8 May 2021; pp. 204–211. [Google Scholar] [CrossRef]
- Hui, Z.; Lingli, Z.; Yonghang, Y.; Linlin, C. A Review of Gateway Load Balancing Methods in Connecting MANET into Internet. In Proceedings of the 2022 24th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 13–16 February 2022; pp. 330–335. [Google Scholar] [CrossRef]
- Shah, N.; El-Ocla, H.; Shah, P. Adaptive Routing Protocol in Mobile Ad-Hoc Networks Using Genetic Algorithm. IEEE Access 2022, 10, 132949–132964. [Google Scholar] [CrossRef]
- Dash, Y. Nature Inspired Routing in Mobile Ad Hoc Network. In Proceedings of the 2021 3rd International Conference on Advances in Computing, Communication Control and Networking (ICAC3N), Greater Noida, India, 17–18 December 2021; pp. 1299–1303. [Google Scholar] [CrossRef]
- Pandey, P.; Singh, R. An Intelligent and Adaptive Multipath Routing Scheme for Mobile Ad Hoc Network. In Proceedings of the 2023 6th International Conference on Information Systems and Computer Networks (ISCON), Mathura, India, 3–4 March 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Margaryan, R.A.; Muratchaev, S.S.; Volkov, A.S.; Afonin, I.L.; Zhuravlev, I.A. Development of an Adaptive Routing Algorithm in MANET. In Proceedings of the 2022 Conference of Russian Young Researchers in Electrical and Electronic Engineering (ElConRus), Saint Petersburg, Russia, 25–28 January 2022; pp. 57–63. [Google Scholar] [CrossRef]
- Lansky, J.; Rahmani, A.M.; Zandavi, S.M.; Chung, V.; Yousefpoor, E.; Yousefpoor, M.S.; Khan, F.; Hosseinzadeh, M. A Q-learning-based routing scheme for smart air quality monitoring system using flying ad hoc networks. Sci. Rep. 2022, 12, 20184. [Google Scholar] [CrossRef] [PubMed]
- Erim, O.; Wright, C. Optimized mobility models for disaster recovery using UAVs. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Anttonen, A.; Mämmelä, A.; Höyhtyä, M.; Saffre, F.; Karvonen, H. Self-Organizing UAV Swarm Placement via Layered Loose Coupling and User Prioritization. In Proceedings of the 2023 IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Toronto, ON, Canada. to be published.
- Mason, R. Feasibility of Laser Power Transmission to a High-Altitude Unmanned Aerial Vehicle; RAND Corporation: Santa Monica, CA, USA, 2011. [Google Scholar]
- Hildmann, H.; Eledlebi, K.; Saffre, F.; Isakovic, A.F. The Swarm Is More Than the Sum of Its Drones. In Development and Future of Internet of Drones (IoD): Insights, Trends and Road Ahead; Krishnamurthi, R., Nayyar, A., Hassanien, A.E., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 1–55. [Google Scholar] [CrossRef]
- IEEE P1939.1/D5.0; IEEE Draft Standard for a Framework for Structuring Low Altitude Airspace for Unmanned Aerial Vehicle (UAV) Operations. IEEE: Piscataway, NJ, USA, 2021; pp. 1–90.
- IEEE P1939.1/D6.0; IEEE Approved Draft Standard for a Framework for Structuring Low Altitude Airspace for Unmanned Aerial Vehicle (UAV) Operations. IEEE: Piscataway, NJ, USA, 2021; pp. 1–92.
- Mikula, B.; Košuda, M. Aviation Regulations for Drone Operations in the Slovak Republic and the EU. In Proceedings of the 2022 New Trends in Aviation Development (NTAD), Novy Smokovec, Slovakia, 24–25 November 2022; pp. 145–150. [Google Scholar] [CrossRef]
- Kandeel, M.E.; Salameh, H.B.; Elrefae, G.A.; Qasim, A. Regulations for UAV Operation in Social Applications and Services: A General Perspective. In Proceedings of the 2022 Ninth International Conference on Social Networks Analysis, Management and Security (SNAMS), Milan, Italy, 29 November–1 December 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Saffre, F.; Hildmann, H.; Karvonen, H.; Lind, T. Self-Swarming for Multi-Robot Systems Deployed for Situational Awareness. In New Developments and Environmental Applications of Drones: Proceedings of FinDrones; Lipping, T., Linna, P., Narra, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2022; pp. 51–72. [Google Scholar]
- Husain, Z.; Al Zaabi, A.; Hildmann, H.; Saffre, F.; Ruta, D.; Isakovic, A.F. Search and Rescue in a Maze-like Environment with Ant and Dijkstra Algorithms. Drones 2022, 6, 273. [Google Scholar] [CrossRef]
- Gripsy, J.V.; Jayanthiladevi, A. Energy Optimization and Dynamic Adaptive Secure Routing for MANET and Sensor Network in IoT. In Proceedings of the 2023 7th International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 23–25 February 2023; pp. 1283–1290. [Google Scholar] [CrossRef]
- Satyanarayana, P.; Bhoomika, K.; Mukesh, D.; Srujana, P.; Bai, R.M.; Sriramam, Y.S.S. Implementation of Improved Energy Balanced Routing Protocol to Enlarge Energy Efficiency in MANET for IoT Applications. In Proceedings of the 2023 9th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 17–18 March 2023; Volume 1, pp. 380–385. [Google Scholar] [CrossRef]
- Lohokare, J.; Dani, R. An Intelligent cloud ecosystem for disaster response and management leveraging opportunistic IoT mesh networks. In Proceedings of the 2021 International Conference on Information and Communication Technologies for Disaster Management (ICT-DM), Hangzhou, China, 3–5 December 2021; pp. 125–133. [Google Scholar] [CrossRef]
- Arputha Babu John, A.; Dutta, R. Cooperative trajectory planning in an intercommunicating group of UAVs for convex plume wrapping. In Proceedings of the 2017 IEEE 38th Sarnoff Symposium, Newark, NJ, USA, 18–20 September 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Kurode, E.; Vora, N.; Patil, S.; Attar, V. MANET Routing Protocols with Emphasis on Zone Routing Protocol—An Overview. In Proceedings of the 2021 IEEE Region 10 Symposium (TENSYMP), Jeju, Republic of Korea, 23–25 August 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Yang, T.; Foh, C.H.; Heliot, F.; Leow, C.Y.; Chatzimisios, P. Self-Organization Drone-Based Unmanned Aerial Vehicles (UAV) Networks. In Proceedings of the ICC 2019—2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Du, Z.; Wang, X.; Wang, S.; Chen, J.; Xu, K. Toward UAV Communication Network Self-Organization: A Game-Theoretic Distributed Control Approach. In Proceedings of the 2022 IEEE International Conference on Unmanned Systems (ICUS), Guangzhou, China, 28–30 October 2022; pp. 121–127. [Google Scholar] [CrossRef]
- Horváth, D.; Gazda, J.; Šlapak, E.; Maksymyuk, T.; Dohler, M. Evolutionary Coverage Optimization for a Self-Organizing UAV-Based Wireless Communication System. IEEE Access 2021, 9, 145066–145082. [Google Scholar] [CrossRef]
- Mämmelä, A.; Riekki, J.; Kiviranta, M. Loose Coupling: An Invisible Thread in the History of Technology. IEEE Access 2023, 11, 59456–59482. [Google Scholar] [CrossRef]
- Yan, Z.; Jouandeau, N.; Cherif, A.A. A Survey and Analysis of Multi-Robot Coordination. Int. J. Adv. Robot. Syst. 2013, 10, 399. [Google Scholar] [CrossRef]
- Kang, H.; Kim, H.; Kwon, Y.M. RECEN:Resilient MANET Based Centralized Multi Robot System Using Mobile Agent System. In Proceedings of the 2019 IEEE Symposium Series on Computational Intelligence (SSCI), Xiamen, China, 6–9 December 2019; pp. 1952–1958. [Google Scholar] [CrossRef]
- Ahn, S.; Lim, Y. A modified centralized DNS approach for the dynamic MANET environment. In Proceedings of the 2009 9th International Symposium on Communications and Information Technology, Icheon, Republic of Korea, 28–30 September 2009; pp. 1506–1510. [Google Scholar] [CrossRef]
- Sun, W.; Zhang, Z.; Chen, W.; Peng, B.; Xu, Y. Decentralized Execution of Composite Service in MANETs. In Proceedings of the 2008 IEEE Asia-Pacific Services Computing Conference, Yilan, Taiwan, 9–12 December 2008; pp. 355–360. [Google Scholar] [CrossRef]
- Tharani, S.; Arutchelvan, G.; Arulanandam, G. Location based clustering implemented for multicast backbone MANET. In Proceedings of the 2017 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 6–8 April 2017; pp. 0728–0732. [Google Scholar] [CrossRef]
- Liang, C.K.; Chung, C.Y.; Li, C.F. A Virtual Force Based Movement Scheme for Area Coverage in Directional Sensor Networks. In Proceedings of the 2014 Tenth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kitakyushu, Japan, 27–29 August 2014; pp. 718–722. [Google Scholar] [CrossRef]
- Eledlebi, K.; Ruta, D.; Hildmann, H.; Saffre, F.; Al Hammadi, Y.; Isakovic, A.F. Coverage and Energy Analysis of Mobile Sensor Nodes in Obstructed Noisy Indoor Environment: A Voronoi-Approach. IEEE Trans. Mob. Comput. 2022, 21, 2745–2760. [Google Scholar] [CrossRef]
- Moole, S.R. Comparison of Effectiveness of Machine Learning Algorithms for Vehicle Path Prediction. In Proceedings of the 2021 IEEE Integrated STEM Education Conference (ISEC), Princeton, NJ, USA, 13 March 2021; p. 210. [Google Scholar] [CrossRef]
- Majd, A.; Ashraf, A.; Troubitsyna, E.; Daneshtalab, M. Integrating Learning, Optimization, and Prediction for Efficient Navigation of Swarms of Drones. In Proceedings of the 2018 26th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP), Cambridge, UK, 21–23 March 2018; pp. 101–108. [Google Scholar] [CrossRef]
- Hamilton, T.; Ochmanek, D.A. Operating Low-Cost, Reusable Unmanned Aerial Vehicles in Contested Environments: Preliminary Evaluation of Operational Concepts; RAND Corporation: Santa Monica, CA, USA, 2020. [Google Scholar] [CrossRef]
- Ameigeiras, P.; Wang, Y.; Navarro-Ortiz, J.; Mogensen, P.E.; Lopez-Soler, J.M. Traffic models impact on OFDMA scheduling design. EURASIP J. Wirel. Commun. Netw. 2012, 2012, 61. [Google Scholar] [CrossRef]
- Pinell, C.; Prol, F.S.; Bhuiyan, M.Z.H.; Praks, J. Receiver architectures for positioning with low earth orbit satellite signals: A survey. EURASIP J. Adv. Signal Process. 2023, 2023, 60. [Google Scholar] [CrossRef]
- Kassas, Z.M.; Kozhaya, S.; Kanj, H.; Saroufim, J.; Hayek, S.W.; Neinavaie, M.; Khairallah, N.; Khalife, J. Navigation with Multi-Constellation LEO Satellite Signals of Opportunity: Starlink, OneWeb, Orbcomm, and Iridium. In Proceedings of the 2023 IEEE/ION Position, Location and Navigation Symposium (PLANS), Monterey, CA, USA, 24–27 April 2023; pp. 338–343. [Google Scholar] [CrossRef]
| 1 | 2 | 3 | 4 | |
|---|---|---|---|---|
| 1 | — | 1.06 | 1.3 | 1.5 |
| 2 | 1.06 | 1.3 | 1.5 | 1.68 |
| 3 | 1.3 | 1.5 | 1.68 | 1.84 |
| 4 | 1.5 | 1.68 | 1.84 | 1.98 |
| … | ||||
| 9 | 2.25 | 2.37 | 2.49 | 2.6 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saffre, F.; Hildmann, H.; Anttonen, A. Force-Based Self-Organizing MANET/FANET with a UAV Swarm. Future Internet 2023, 15, 315. https://doi.org/10.3390/fi15090315
Saffre F, Hildmann H, Anttonen A. Force-Based Self-Organizing MANET/FANET with a UAV Swarm. Future Internet. 2023; 15(9):315. https://doi.org/10.3390/fi15090315
Chicago/Turabian StyleSaffre, Fabrice, Hanno Hildmann, and Antti Anttonen. 2023. "Force-Based Self-Organizing MANET/FANET with a UAV Swarm" Future Internet 15, no. 9: 315. https://doi.org/10.3390/fi15090315
APA StyleSaffre, F., Hildmann, H., & Anttonen, A. (2023). Force-Based Self-Organizing MANET/FANET with a UAV Swarm. Future Internet, 15(9), 315. https://doi.org/10.3390/fi15090315







