1. Introduction
In today’s fast-paced world, where the number of internet-connected devices is increasing and online applications are growing at a rapid pace, information security is becoming an absolute necessity. Since the beginning of the World Wide Web, 1.2 billion websites have been developed [
1], and a huge number and variety of online applications are integrated with various web services, such as e-commerce, online banking, online shopping, online education, e-healthcare, and industrial control systems (ICS) for critical infrastructure, etc.
Nowadays, cyber attackers are highly skilled and well-equipped to carry out successful attacks on businesses and governments [
2]. Cybercrime is big business today, and the volume of stolen information is enormous. There are many different categories of malware [
3]. This poses a huge risk to governments, businesses, and consumers around the world. We do not have to go far back in time to remember the massive attack on a bank in Bangladesh, where USD 81 million was reportedly stolen. This is a constant reminder of how effective these attacks can be; the bank’s own computers were used to transfer large sums of money. No business is safe, no matter how large. Statistics show that 20% of affected businesses fall into the small business category, 33% into the SME category, and 41% into the large business category. The more widespread the threat, the more important it becomes to be aware of the issues and protect the important information. Eighty-two percent of organizations have been exposed to at least one or more attacks in which data are stolen and used to cripple the victim’s services. The organizations that were affected by DDoS attacks reported a 26% drop in performance of their services and 41% reported an outage of the affected services [
3].
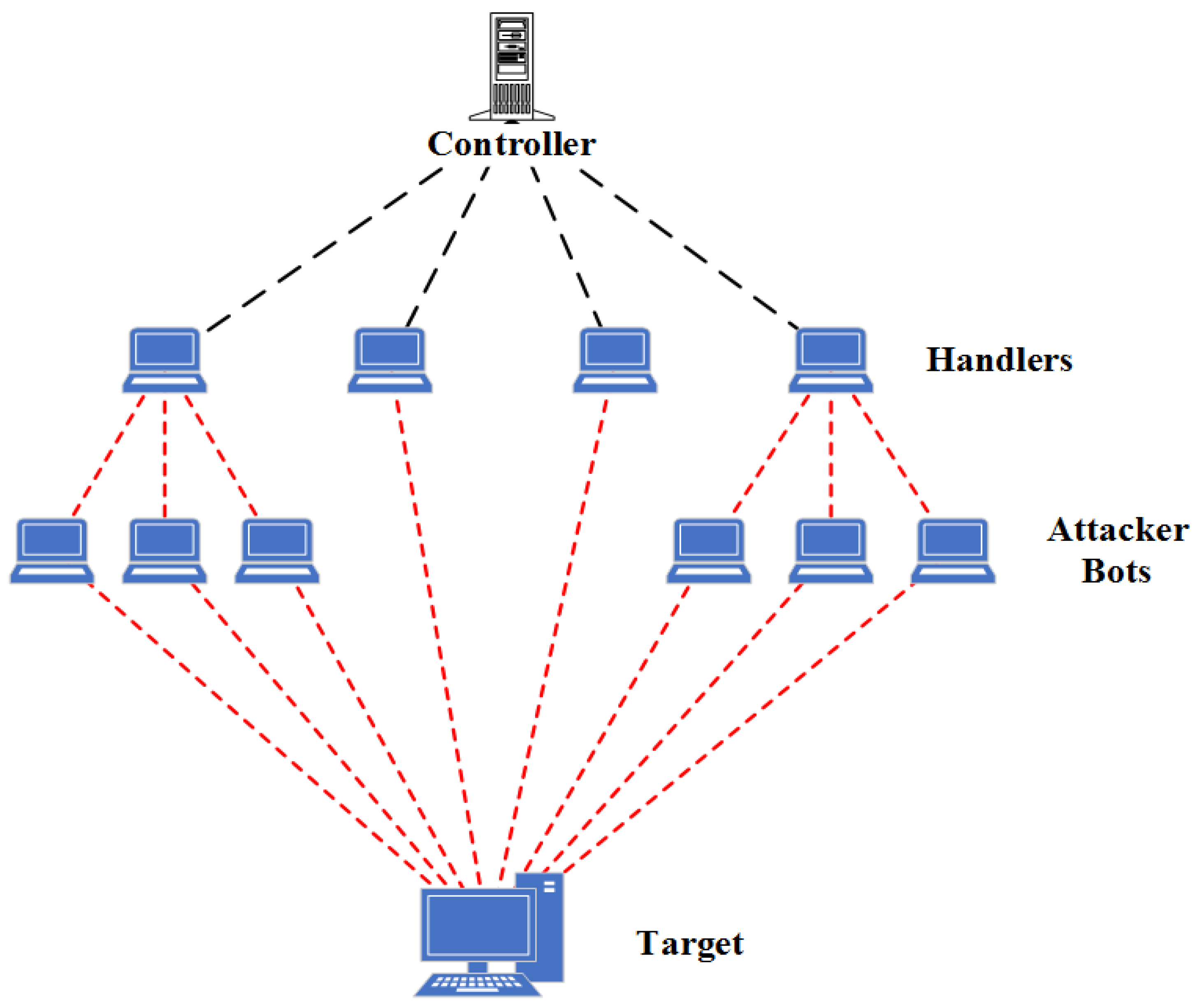
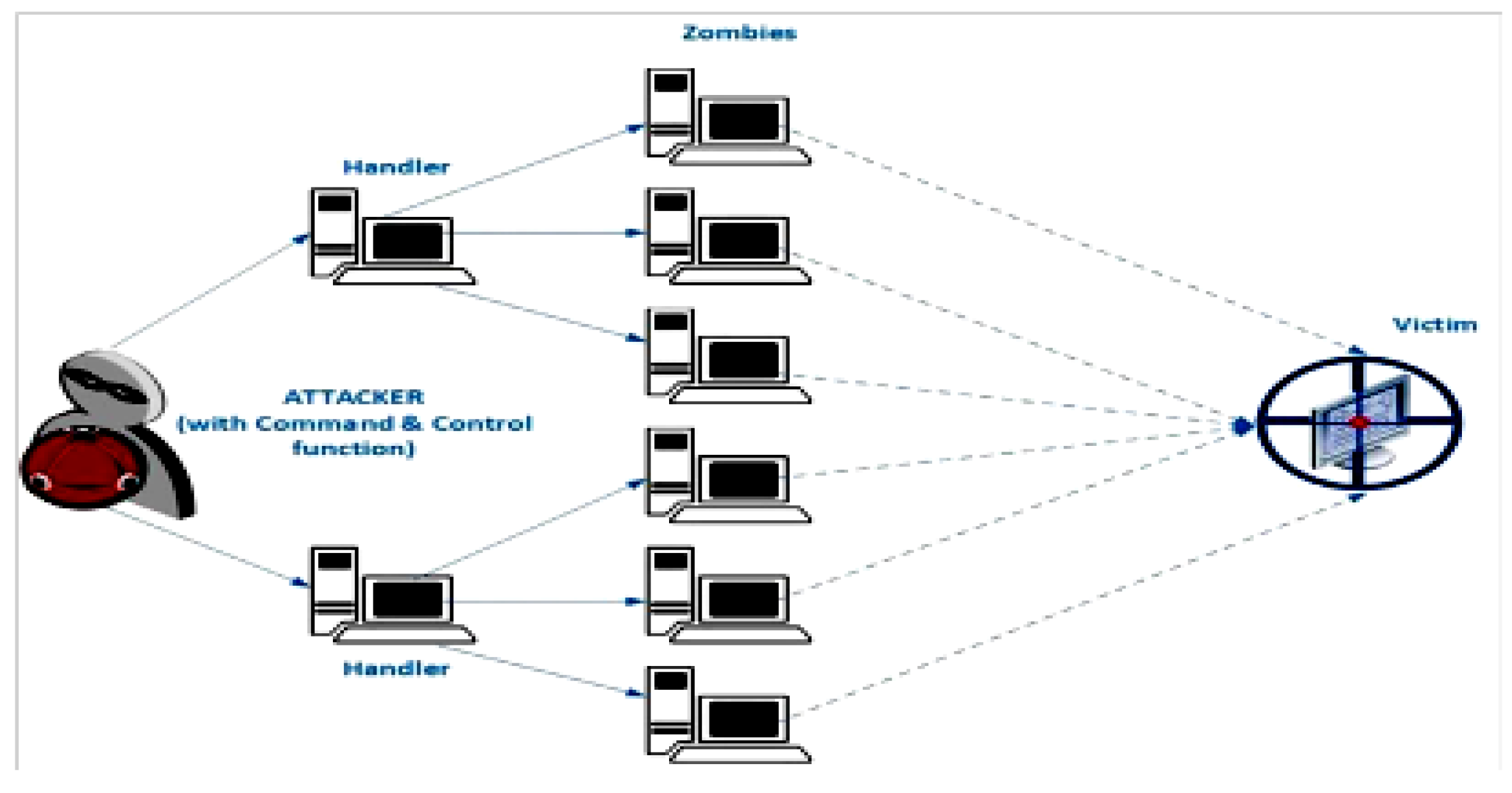
Figure 1 shows an environment of DDoS attacks.
The attacker makes precise imitations of human users’ behaviors in an effort to avoid being noticed while conducting the assault. To launch an HTTP-GET flood DDoS assault, the malicious user separates his attack techniques based on rate, admission pattern, etc. Several significant concerns and challenges that have surfaced from recent research have drawn increasing attention in the area of HTTP-GET flood DDoS assault detection. When working in the vicinity of conflicting HTTP-GET flood DDoS attacks [
1], numerous challenges arise, that are also only partially addressed or unresolved. DDoS attacks are disciplined, distributed, and remotely organized networks that use deployed computers (also called Bots or Zombies) to send an immense number of uninterrupted and synchronous requests to the victim system(s). DDoS attacks are increasing in strength, regularity, and complexity.
Malicious users are constantly evolving their experience, adapting their techniques, and using advanced technologies to launch various DDoS attacks. While there are various solutions to detect, defend against, or mitigate DDoS attacks, malicious users continue to develop new approaches and means to circumvent these countermeasures [
3]. DDoS events are still among the biggest threats to the network. Recently, DDoS outbreaks at the application layer of internet servers have become widespread, resulting in huge revenue losses for targets [
4]. In TCP/IP layer attacks, the online server is crushed and the number of requests per second is limited. Slowloris, zero-day attacks, and DDoS assaults that take advantage of Apache or Windows vulnerabilities fall under this category [
5].
The solutions offered to understand DDoS attacks at the TCP/IP layer capture only a subset of DDoS incidents at the application layer. The resolutions that detect entire types of application-layer attacks are very complicated in formula. One set of tasks in detecting a DDoS outbreak at the TCP/IP layer is the unavailability of landscapes to detect such incidents [
6]. HTTP-GET DDoS attacks are a risk for all web servers, as bots are able to impersonate humans and make it difficult to distinguish malicious requests from real ones. Regardless of industry or scale, enterprises around the world are increasingly becoming targets of DDoS attacks.
Complexity and strength of these attacks are increasing exponentially as the number of admitted systems increase, vulnerabilities go un-patched, and business impact increases [
7]. DDoS attacks have a strong impact on the cyber domain. Cyber attacks are feared to disrupt the regular functioning of the organization through IP overflow, bandwidth spoofing, intensive memory resources, and root sane or mouse damage [
8]. A slow-moving DDoS attack has the capacity to mimic real traffic with its traffic. It is simple to avoid detection by current systems. Based on their rank values, rank correlation techniques can detect significant differences between attack traffic and legitimate traffic [
9].
DoS attack has serious impacts on information servers, internet servers, and cloud computing servers [
10,
11]. Botnets, DDoS, hacking, malware, pharming, phishing, ransomware, spam, spoofing, and spyware are some of the most frequent hazards [
12]. According to Ginni Rometty, Chief Executive Officer IBM, the biggest risk to any or all businesses worldwide is a cyberattack. With that, there is an increase in cybercriminals [
9]. Malicious users use numerous hacking methods to hack client servers. DDoS attacks are very wide-ranging attacks and occur between other cyber attacks; detecting DDoS attacks is not easy. Three basic types of DDoS attacks are described below.
1.1. Volume Based DDoS Attack
Volume based DDoS attacks consist of faked packet floods such as ICMP floods, UDP floods, and others. The objective of this attack is to use all of the target site’s bandwidth, and it is measured in bits per second (bps). Various prominent types of DDoS attacks are shown in
Figure 2.
1.2. Protocol Based DDoS Attack
Protocol based DDoS attacks appear in a variety of forms, such as SYN floods, fragmented pack attacks, ping of death, smurf DDoS, and others. Attacks are measured in packets per second (pps). Such types of attacks use real server resources, as well as those of central communications devices like firewalls and load balancers.
1.3. TCP/IP Layer Based DDoS Attack
TCP/IP layer based DDoS attack comprise GET/POST floods, low and slow-speed attacks, potential Windows or Open BSD attacks, Apache-driven attacks, and more. Such attacks seem to be legitimate and innocent applications, and they target the web server. The extent is measured by requests per second.
The number of attacks and the associated traffic volume continue to increase dramatically. With such traffic intensity, the network infrastructure upstream of the intended victim is also severely impacted, so attack traffic must be filtered as close as possible to the sources of attack. However, it is difficult to predict and identify such nodes, as attacks originate from widely distributed nodes and spread across multiple locations. To successfully respond by disrupting traffic, the mitigation approach must detect malicious traffic and respond with minimal impact on legitimate traffic. The attacker launches a new attack, known as increasing DDoS attack and proxy DDoS attack. We develop a detection algorithm to solve this problem. The detection algorithm uses deep-learning techniques to detect malicious traffic and separate legitimate traffic from malicious traffic. The algorithm classifies traffic into three categories: (1) normal traffic (2) suspicious traffic (3) malicious traffic. The main contributions of this study are summarized below.
We addressed novel application layer DDoS attack by analyzing the characteristics of incoming data packets including size of HTTP frame packets, number of IP addresses sent, constant mappings of ports, and number of IP addresses using proxy IP.
We analyzed the client’s behavior in public attacks using standard datasets, CTU-13 dataset, real web logs (dataset) from our organization, and experimentally created datasets from DDoS attack tools such as Slow Lairs, Hulk, Golden Eyes, and Xerex.
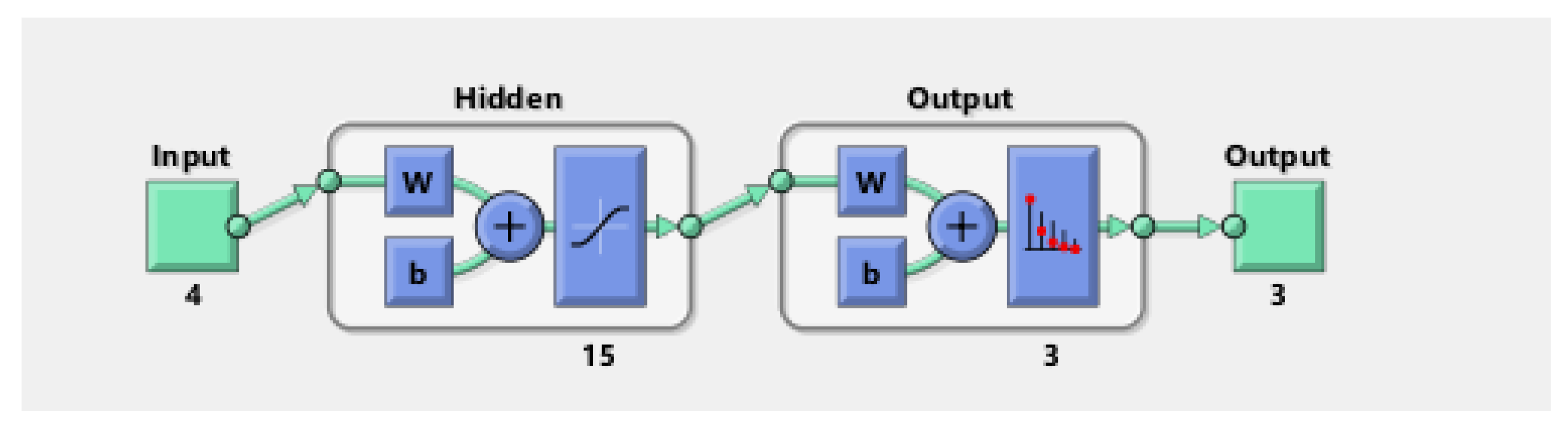
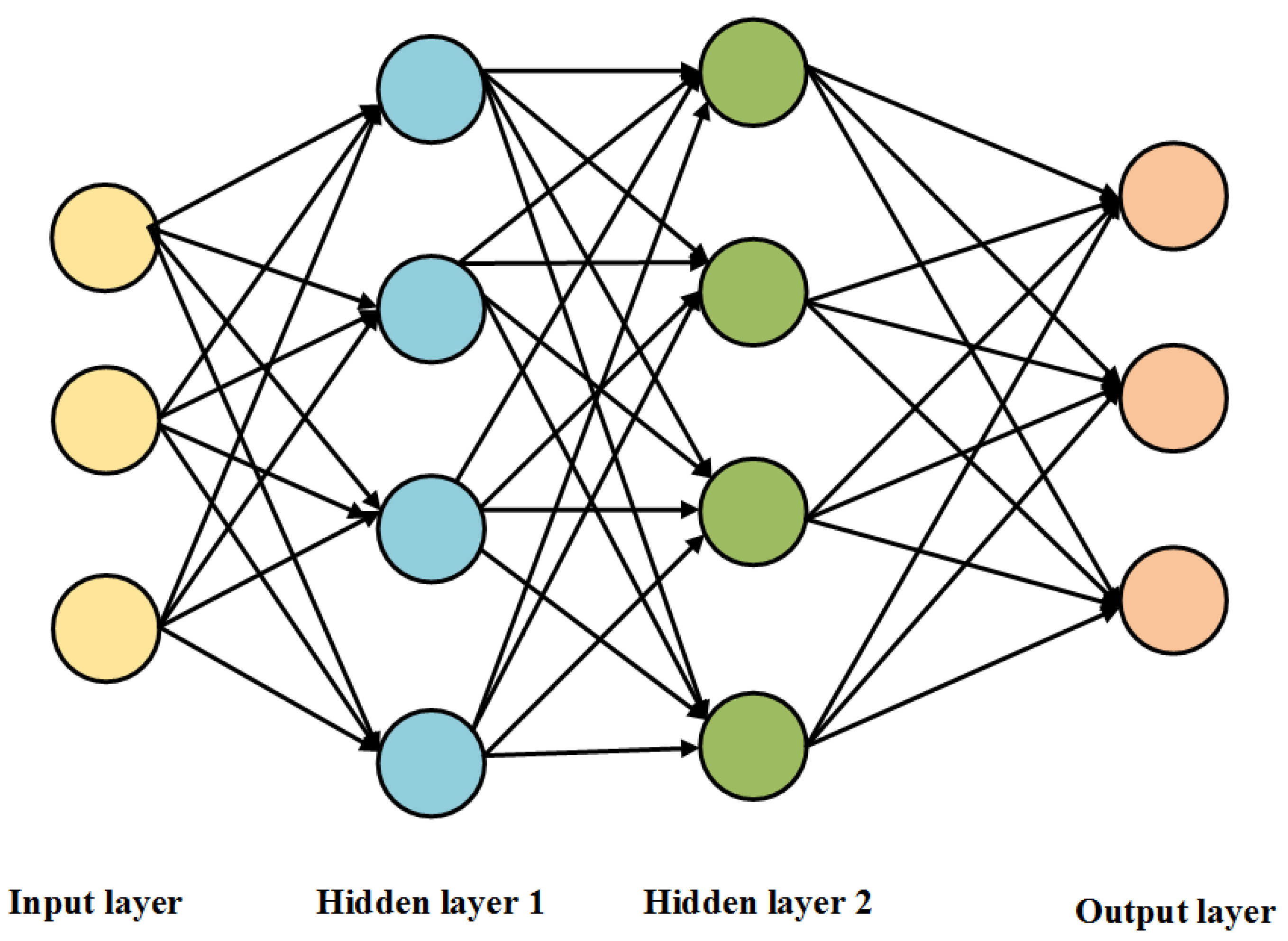
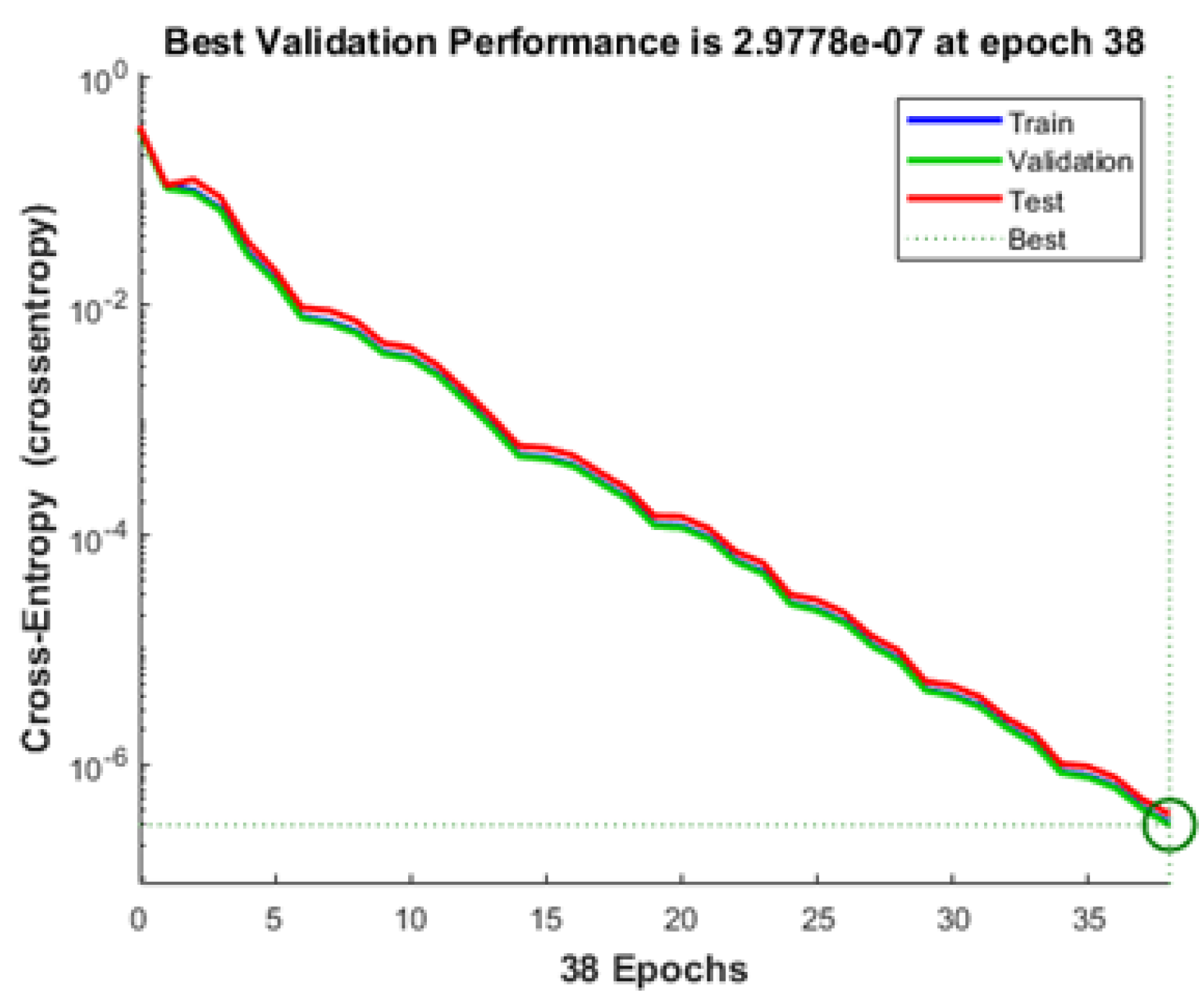
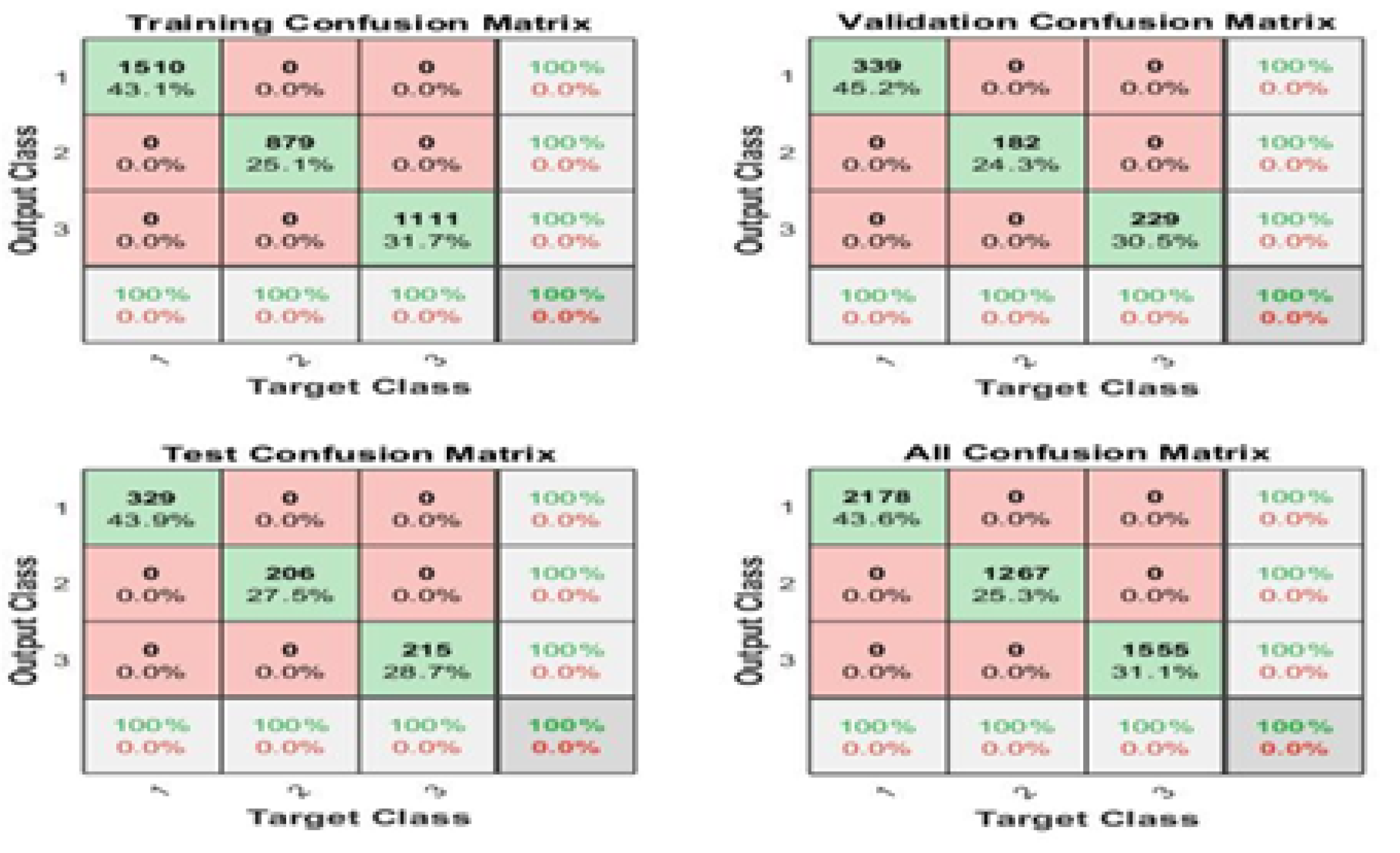
A deep learning classification algorithm, multilayer perceptron (MLP), is proposed to evaluate the effectiveness of attack detection based on metrics.
Our proposed MLP classification model provided the lowest value of false positives as compared with conventional classifiers such as Naïve Bayes, Decision Stump, Logistic Model Tree, Naïve Bayes Updateable, Naïve Bayes Multinomial Text, AdaBoostM1, Attribute Selected Classifier, Iterative Classifier, and OneR.
The rest of the article is organized as follows.
Section 2 briefly describes the literature review; the problem motivation is discussed in
Section 3. Chart flow and research methodology are presented in
Section 4. The proposed attack classification model is briefly described in
Section 5 and simulation results are elaborated upon in
Section 6. Finally,
Section 7 concludes this study along with future work.
2. Literature Review
Machine learning algorithms are being widely used by research community in every field of life. Prominent application areas of machine learning algorithms include image processing, forecasting, recommendation systems, healthcare, banking system, defence, education, robotics, etc. [
13]. Deep learning is a subset of machine learning. In this study, we have used a deep learning algorithm, namely, multilayer perceptron (MLP), for effective and efficient detection of DDoS attacks. State-of-art literature on DDoS attack detection is summarized in the following.
Authors of [
14] have focused on mitigating multi-page HTTP DDoS attacks with slow-moving targets that target public servers. The conceptual proof model was used in a simple and validated the argument. In [
15], the authors compared the probability similarity between cyber attack, DDoS, and mathematical prototypical probability, Levy Walks. This variation aimed to determine the suitability of Levy walk as prototypical similarity with DDoS potential features. In [
16], the authors experimented with the clever subject of comedy measurement that utilizes a conference seeking philosophy and a brilliant channel that sets shares in the traditional way. Multilayer perceptron with genetic algorithm (MLP-GA) is proposed in [
17] to detect DDoS attacks. The authors examined the areas of incoming pockets as well.
It is assumed that the non-receiver of an unusual collection returns once at the time of publication. However, the authors of [
18] provided a sequence of events for experimental distribution to test the capabilities. The authors did not show a positive impact on stock recovery, but in cases where DDoS attacks cause disruptions within the services sent by the client, the study experienced a strong negative impact. The current unit of current methods was created due to the actual malfunction of DDoS attack detection in the application layer.
The authors of [
19] developed a phase-based system with downloading local packets, fine-field extraction of these local units needed for detection, and the use of a separator for attack detection. The study at [
20] examined the impact of a DDoS attack on a state-of-the-art gift network and evaluated network security mechanisms such as a router protection system and network servers. In [
21], the authors presented a solution for such a type of DDoS attack. When the server exceeded the limit of its application, the author then proposed a solution and sent a random number, which can be selected at an unconsidered time value, to the requesting client.
Research at [
22] provided a design that increases resilience to DDoS attacks by upgrading the roles of a virtual network and the software that defines a network. In the first phase, the proposed design defines the roles of the virtual network by solving the linear system. In phase two, to increase the previous protection against DDoS attacks, special VNF filters and a second path through these VNF filters were established by solving another linear system. SDN controller switches routes with a second attack to DDoS traffic filtering methods to prevent congestion under DDoS attacks. In [
23], the authors provided a flexible identifier that is set periodically in the background and can make additional data selections. The authors provided applications related to the occurrence of a DDoS-based attack group and a metalfolding model that combines two orthogonal oddity-based attack modes.
In [
24], the authors provided a DDoS detection combining a fully based standard and an exceptionally dependent method in which three types of machine applications are found. The author first studied the performance of the proposed system under conditions enforced by normal saturation and TFN2K attacks. Then, the authors apply small costs, such as a saturation period with key traffic attack points, to soak the victim. The authors of [
25] investigated our hypotheses about the problem in the existing diagnosis method of the attack on the DoS application base with a strong attack on the algorithm of the CUSUM system. In [
26], the researchers developed bio-roused conflicts, based largely on the DDoS Assault framework, with the goal of achieving a faster space. The given prototype can be a bio-roused bat algorithm system, which usually handles the fast and timely location of a DDoS application over HTTP floods.
The authors of [
27] proposed a cloud-based firewall to reduce DDoS attacks on the smartest grid network AMI. The Promoted Firewall is not only able to reduce the impact of DDoS attacks, but can also prevent attacks before they start. In [
28], the authors demonstrated another planning phase to detect and prevent multiple DDoS TCP (CS_DDoS) attacks during the day. The proposed CS_DDoS framework provides response protection for deleted records. In [
29], the authors provided an event detection module to limit the proliferation of internet of things (IoT) services. It was modified from the current monitoring modules with information-based filters. The proposed module focuses on system behavior during DDoS attacks and detects them using NTP-collected information used in the synchronization service. The author performed a demo test with an advanced module that generates a fake DDoS attack. The result showed that the deployed modules obtain high memory and accurate values, which show their effectiveness in capturing real-time events in IoT.
A study done by [
30] presented exponentially weighted moving normal (EWMA) search for amazing mine learning and DDoS base discovery attacking internet of things (IoT). The authors investigated the tradeoff between statistical detection rate, warning, and localization delay. In [
31], the authors narrow down the classification of DDoS threats that support unusual behavior in the application layer and provide elliptical data on various DDoS tools. In addition, the author distinguishes methods of DDoS detective work based on viewing, blocking, detecting, and minimizing comments. In [
32], a step-by-step approach to DDoS attack mitigation was presented, where the entire process of mitigating DDoS attacks was forced to a single layer or multiple layers. To increase the security of DDoS attacks, the go-layer process has become a useful solution. The authors of [
33] presented a new plastic strategy for detecting Al-DDoS attacks. Their aforementioned work differs from the previous method by considering the detection of Al-DDoS attacks in critical spine motions.
A distributed, useable, automated, and interactive ISP standard was presented by the study’s authors in [
34]. It not only distributes computing complexity and storage to adjacent places, but also facilitates the early identification of DDoS attacks and flash occurrences. Using an independent multi-agent system and agents that depend on particle evolution to facilitate effective communication and precise decision-making, the authors of [
35] present a unique DDoS attack detection and prevention technique. Multiple intermediate agents are used to detect DDoS attacks, and the coordinating agent is updated. A secure root system and an access system that can identify nearby attacks on the RPL protocol have been suggested by experts of [
36] in order to mitigate the effects of such attacks. To find the malicious node, the IDS is developed, taking into account the location data and the received signal strength. Researchers discovered perplexing real-time blocking DDoS application layer assaults on the web in [
37] that seek to be discovered quickly and quickly. ARTP is a machine learning technique for quick and accurate app DDoS detection using multiple flood requests. The work’s goal was achieved by measuring LLDoS databases through tests, and the findings showed how valuable the proposed model is.
A hybrid protocol proposed by the authors of [
38] is the best suited protocol for cloud computing to detect DDoS attacks. The authors of [
39] provide a new approach presented in this study. With the presence of these types of malicious nodes, attacks can be classified as active and inactive. In [
40], the authors propose to identify the DDoS attack and mitigation model using the feature selection method. In the presented study, the network traffic is primarily analyzed according to the Hellinger degree. When a certain distance is detected, all data packets are analyzed and classified into two categories based on the selected segmentation factor, such as DDoS and official application groups [
41]. The authors have addressed the problem and developed a secure system for these programs. The experts of [
42] proposed a botnet detection method that can manage multiple datasets and also detect botnets in the network. In [
43], researchers addressed the need to prevent DDoS attacks by defining and demonstrating a mixed identification model by introducing an advanced and effective method to identify and effectively distinguish flooding in a hot crowd.
In addition to introducing a multi-level classification method based on the presented set of entropy-based features with machine learning divisors to improve the low visibility and accuracy, the authors of [
44] also introduced a set of novel entropy-based symbols to help reliably detect DDoS attacks. In [
45], researchers discussed four important network protection schemes against end-to-end network attacks, end-to-end, victim, and distributed schemes with a focus on two innovative models, Gossip and D- WARD. In [
46], the authors introduced a reduction method based on the fuzzy control system. It looks like inserting two new matrices.
In [
47], the researchers presented a novel selection algorithm, Dynamic Ant Colony System, with a choice of three levels of renewal function. The presented method uses different levels of pheromones to make the ants stronger. The proposed method by the authors of [
48] is contrasted with a different hybrid algorithm that is provided with 10-fold cross-validation. The proposed method outperforms existing methods in terms of accuracy, detection rate, and false alarm rate, according to the database-based test results of KDD CUP 99. In [
49], the experts proposed a new method to mark a packet that could be forwarded from the attacker’s side to the victim’s side. It allows the victim to ensure the necessary protection for internet service providers (ISPs).
In the manuscript, [
50], the authors propose a defense system called SkyShield. This scheme uses a graphical data framework to identify and mitigate DDoS attacks at the application level. First, they proposed new split calculations in two graphs that improve the effect of network dynamics and increase the accuracy of detection. Second, they used an atypical graph to help identify the malicious predators of a persistent attack. In [
51], the researchers proposed the concept of a system of experts. This program automatically resets security apps about incoming traffic. To achieve this, it is proposed to use a model, reasoning, and performance-based loop (LRA-M). In this case, it describes the structures of the corresponding system and defines its building blocks. In [
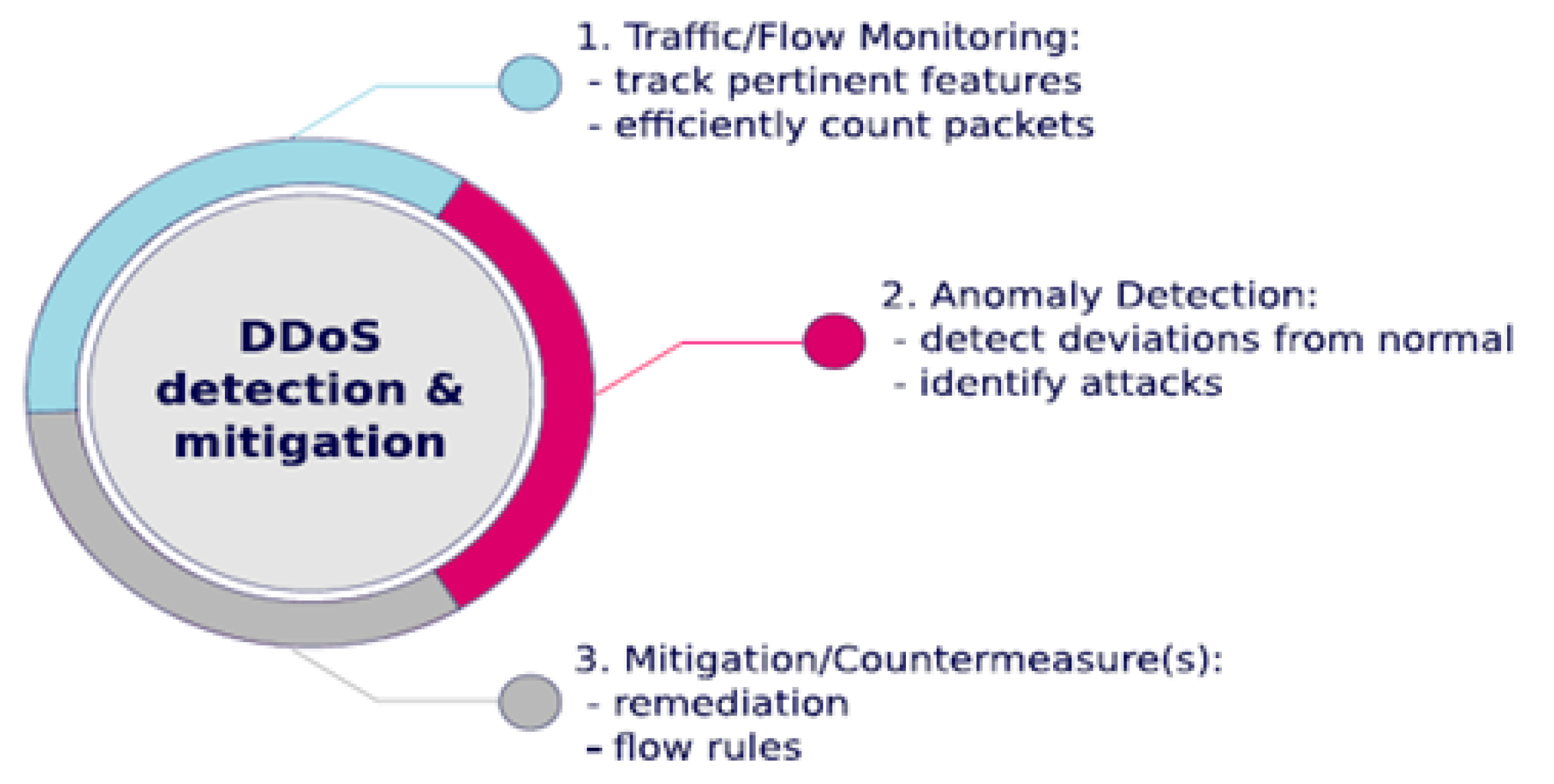
52], the authors used a state-of-the-art SDN model, employing a new method for DDoS detection and mitigation known as State Sec. They demonstrated the benefits of this type of method, as shown in
Figure 3.
The authors of [
53] analyzed a number of current machine learning (ML) research projects that spread SDN for NIDS implementation. It was discovered that deep learning techniques had been looked into for the creation of SDN-based NIDS. Key steps of DDoS detection and mitigation in software-defined networking are shown in
Figure 3. A brand-new authentication method was put forth in [
53] as a defence against DDoS assaults on approved domain name servers. For duplicate resolvers, the solution employed the DNAME record to sign the domain redirection guide and then correctly reroute traffic to their downstream query domains. Many domains can be connected to vast and flexible provisioning and release of approved services to quickly raise demand in response to DDoS attacks. Results from imitations show that this solution works.
In [
54], the authors proposed a new confusing discovery system with a unique parallel session feature attack detection (SFAD). The proposed process consists of two main steps. The first step is to set up smooth windows to collect web access information for different users; the second one is the PageRank method, used to control the weight information of web pages and calculate the similarity information for users. In [
55], the authors proposed a IDS design that used ML algorithms such as Hidden Markov Model with a multi-pronged approach. This approach was developed and proven to solve common bugs in using the Hidden Markov Model in IDS, commonly referred to as the curse of size.
Based on psychologically inspired computations using entropy two-address representation, the inventors of the DDoS detection and defence technique developed their method in [
56]. A vector segmentation technique is installed for support, the flow table features are retrieved, and the DDoS assault model is developed. In [
57], the authors focused on internal DoS/DDoS attacks on WAMS devices using potential resources. To counter this type of attack, the authors propose an earlier and stronger extension of the multipath TCP (MPTCP) transport protocol, which they call MPTCP-H.
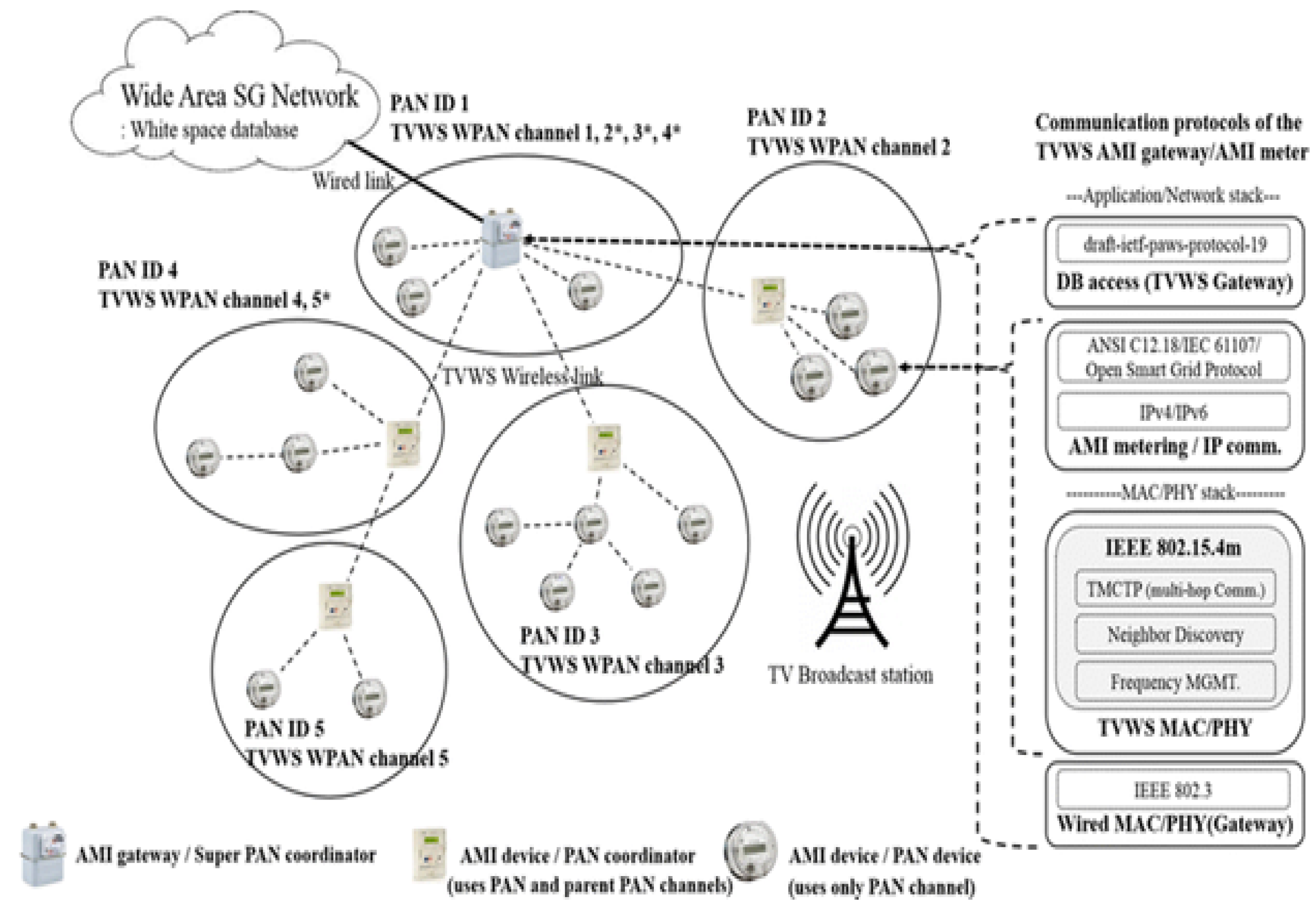
In [
58], the authors proposed a fault detection method based on the study of mobile cloud computing that includes various client networks, as shown in
Figure 4. The presented method does not require rule checking and its problem can be adapted to the needs of client networks. The authors of [
59] have developed a collection-based approach to classify data representing the flow of network traffic. It combines normal traffic with DDoS.
The authors of [
60] provided a general overview of the use of SDN to improve network security, as shown in
Figure 5. In particular, the authors examined recent research that emphasizes the use of SDN for network security. These include attack detection and mitigation, network traffic monitoring, service chaining, policy adaptation and management, centralized box deployment, and smart network security. On the basis of the newly announced Boltzmann Restricted Machines, the authors of [
61] proposed an ingenious city-based diagnostic paradigm (RBMs). RBMs process the data produced by smart metres and sensors in real time by utilizing their capacity to unconventionally learn high-level aspects of raw data. In [
62], the authors presented a new method for detecting the involvement of network devices in DDoS attacks. For this purpose, the traces next to the source are examined to detect inconsistent behavior.
In [
63], the authors proposed ForChaos, a lightweight detection algorithm for IoT devices based on predictive and chaotic perception to detect flooding and DDoS attacks. In [
64], the authors first developed the new Chinese Remainder Theorem based on the Reversible Sketch (CRT-RS). It can not only compress and consolidate large network traffic, but is also able to detect atypical keys as unwanted/malicious or network traffic sources. The literature review is summarized in
Table 1,
Table 2 and
Table 3.