The Future of Cybersecurity in the Age of Quantum Computers
Abstract
1. Introduction
- (i)
- Protecting each Internet-connected legacy computer individually from quantum attacks;
- (ii)
- Segregating all quantum computing activities from mainstream Internet.
- There is a growing interest in cloud-based quantum computers;
- Recent advances indicate that quantum-as-a-service (QaaS) is currently a real option [11];
- At least six QaaS providers [12], including Amazon and IBM, have already launched their “Quantum-as-a-Service” for scientists, researchers, and developers to build, test, and run quantum computing algorithms;
- IBM is even offering its QaaS free [13];
- Subscription to such a QaaS offering can be mandated to deploy specific security protocols to access the QaaS;
- Based on a recent report on “zero-vulnerability computing (ZVC)” [14], this paper builds rational support for a hypothetical question that is relevant to the safety of quantum computing: will ZVC’s encryption agnosticism make it quantum-safe?
- ZVC’s encryption-agnostic security protocol can potentially provide unbreakable end-to-end security to access QaaS and isolate it from the rest of the Internet;
- Since the QaaS access authentication approach proposed in this paper virtually eliminates all the probabilities of exposing legacy computers to encryption-breaking quantum algorithms, the recent failures of PQC algorithms become inconsequential.
2. Problem Statement
3. Is the Quantum Threat Unassailable?
- (i)
- Scrambling the information to make it undecipherable to the intruder;
- (ii)
- Automatically making the information physically inaccessible to an unauthorized intruder.
- (1)
- As ZVC security is encryption-independent, will it be quantum-resistant by design?
- (2)
- As the ZVC architecture lacks layering, rendering it conceptually analogous to the zero-moving-parts nature of solid-state electronics, will it deliver the same advantages to computers as the solid state did to revolutionize the electronics industry in the 1960s–1970s?
4. How Does ZVC Work?
- (i)
- Comprehend how ZVC achieves zero vulnerability without using adversary-facing encryption techniques. In the state of the art, encryption is the first and, in most cases, the only defense against intruding adversaries [30], rendering the cybersecurity of a legacy victim computer vulnerable to a quantum computer’s ability to break the standard encryption algorithms;
- (ii)
- Examine how ZVC’s minimalist design can replicate, in software systems, the integrity, robustness, and energy efficiency of solid-state electronic hardware.
4.1. Encryption-Agnostic Security of ZVC
- 1.
- Banning all third-party permissions, thus completely obliterating the attack surface;
- 2.
- Creating switchable in-computer offline storage within the connected device itself.
- (i)
- Device access authentication data;
- (ii)
- Data stored on the device’s memory.
- (1)
- Device access authentication data: Quantum computers (QCs) can break today’s encryption standards remotely, but that requires online accessibility to the victim resource and freedom of unlimited decryption attempts. ZVC’s ICOS (in-computer offline storage) module automatically goes offline after three failed attempts, rendering the private data inaccessible to the QC algorithms.
- (2)
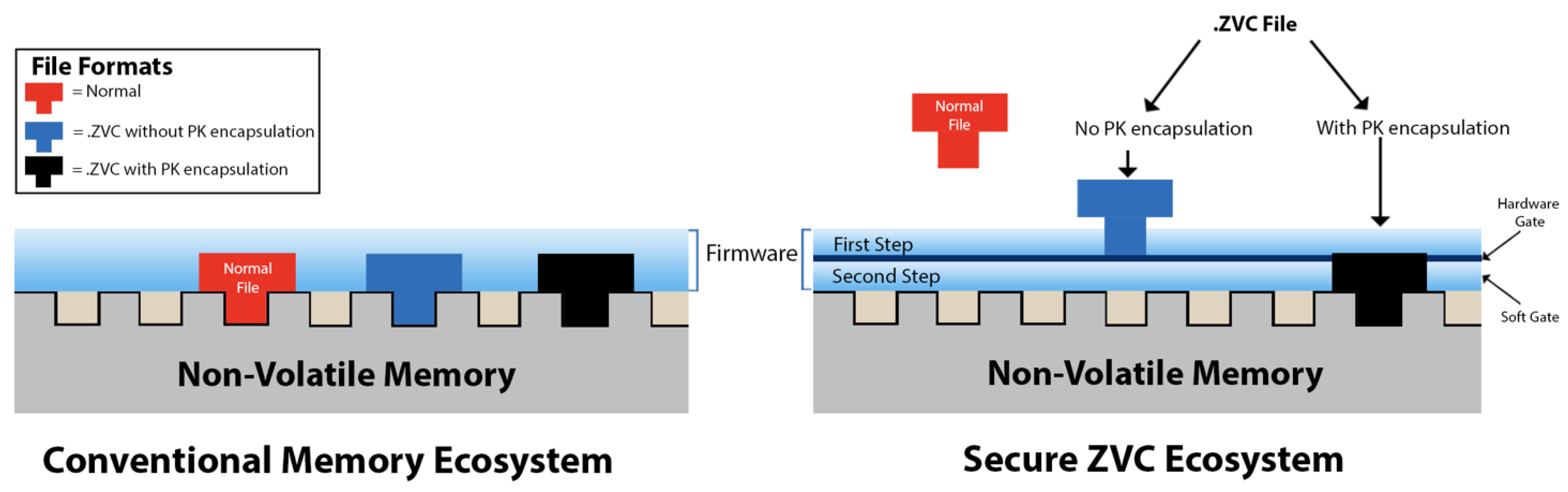
- Data stored on the device’s memory: Assuming a QC algorithm succeeds in overcoming the access authentication barrier, it will be able to access all the exposed and discoverable data. However, ZVC stores all private data on NAND memory hidden behind two security gates. To pass those gates, the remote QC must run its algorithms locally on the device in the same fashion as typical malware, i.e., it must be installed on the device, and execute its algorithm. ZVC bans all third-party permissions at the hardware level not only to run any non-native algorithm locally but also to find and recognize the data on the device targeted for breaching. A QC can run its access-breaching algorithm remotely to break the encrypted access credentials, but once the access is breached, the QC cannot transfer codes to run locally in the absence of third-party permissions. In other words, breaking the encryption for access authentication is of no avail, as no further local execution of any remote malicious code is possible for compromising the ZVC-secured data. ZVC secures the native data by setting up two gates that need to be passed before the data become accessible, as illustrated in Figure 4.
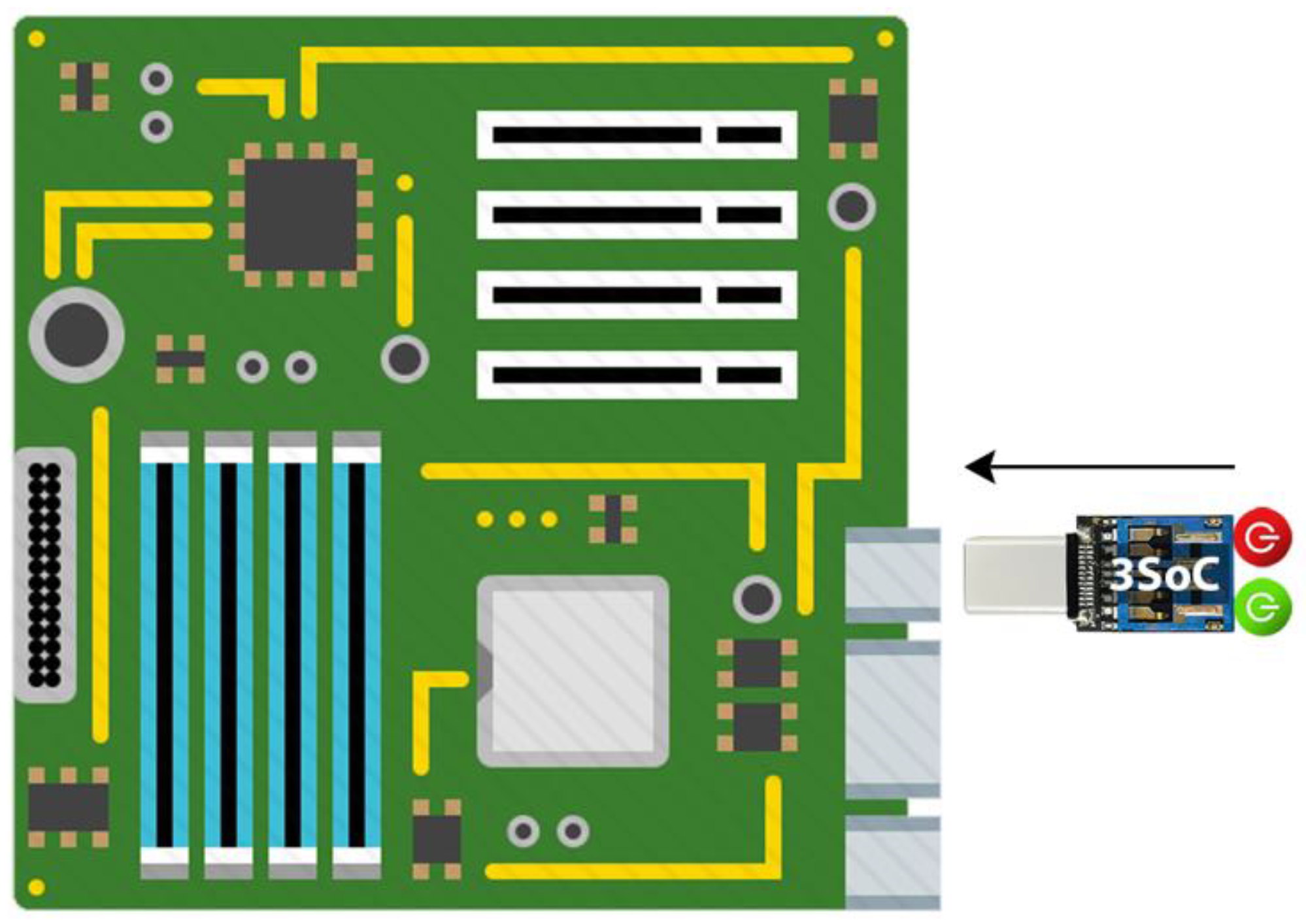
4.2. Solid-State Software on a Chip (3SoC) and Potential Quantum Resistance
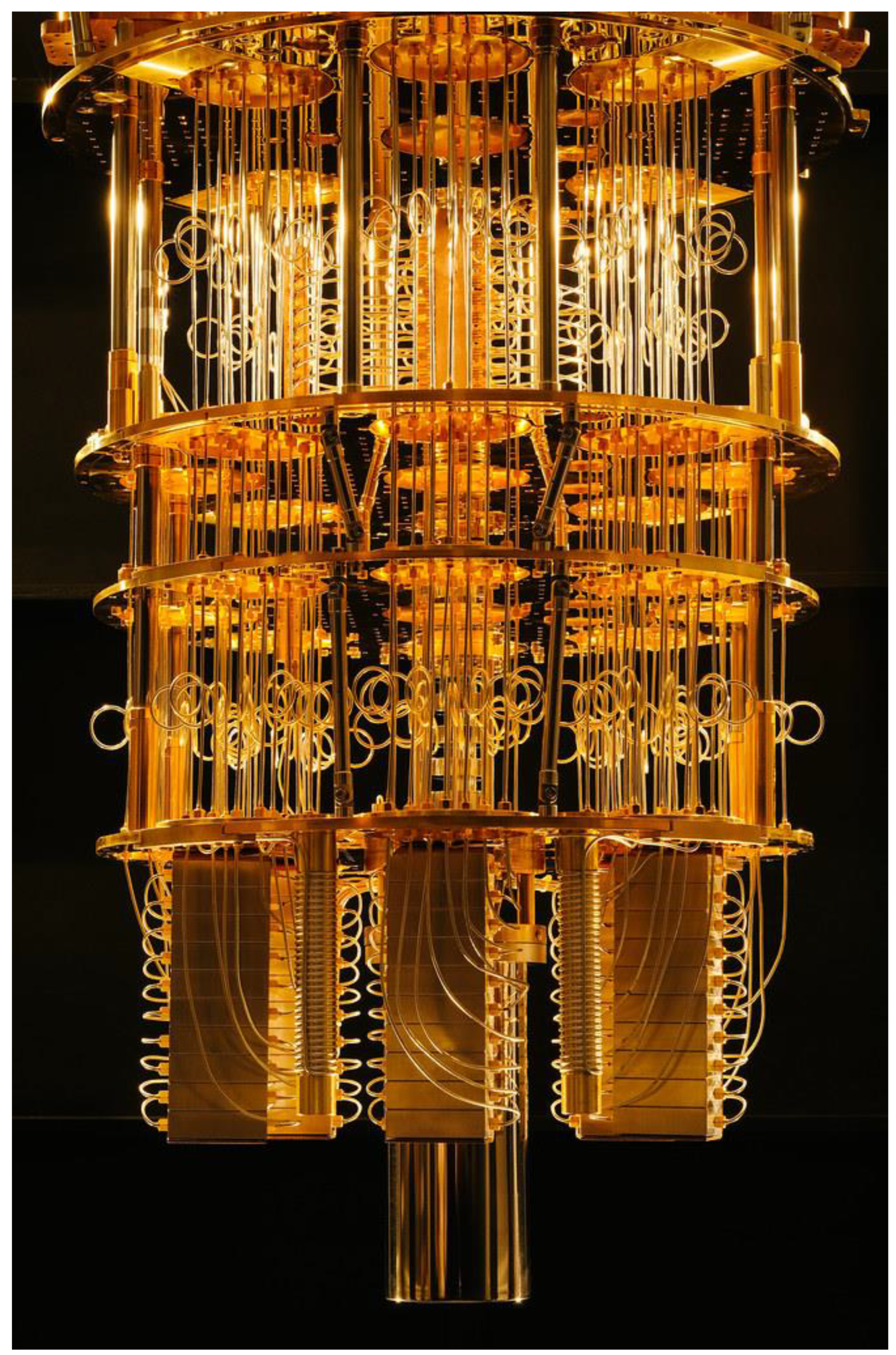
5. Quantum Supremacy and the Q-Day Threat
5.1. Potential Quantum Computing Business Model
5.2. Securing Quantum Computing Service Provider (QCSP) Network
6. Limitations and Caveats
- (i)
- These hypotheses are formulated based on empirical data from a limited-use hardware wallet experiment [14] and need to be validated in diverse mainstream computing environments before any extrapolation to more complex computing environments;
- (ii)
- The ZVC/3SoC research is ongoing, and the inferences drawn from the available data are preliminary and subject to updates as and when available;
- (iii)
- Currently, cloud services seem to be the only way quantum computing can become available to end users in the near future;
- (iv)
- Notably, 3SoC devices inherently restrict the porting of generic or non-conforming third-party peripheral devices [27];
- (v)
- Rigorous experimentation by peer researchers is warranted for testing and proving or disproving the ZVC/3SoC hypotheses and replicating the conclusions;
- (vi)
- Appropriate key performance indicators (KPIs) should be framed to justify the quantity and quality of the case studies designed to investigate the formulated hypotheses.
7. Conclusions and Future Prospects
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Preskill, J. Quantum computing 40 years later. arXiv 2021, arXiv:2106.10522. [Google Scholar]
- Arute, F.; Arya, K.; Babbush, R.; Bacon, D.; Bardin, J.C.; Barends, R.; Martinis, J.M. Quantum supremacy using a programmable superconducting processor. Nature 2019, 574, 505–510. [Google Scholar] [CrossRef] [PubMed]
- Bova, F.; Goldfarb, A.; Melko, R.G. Commercial applications of quantum computing. EPJ Quantum Technol. 2021, 8, 2. [Google Scholar] [CrossRef] [PubMed]
- Castelvecchi, D. The race to save the Internet from quantum hackers. Nature 2022, 602, 198–201. [Google Scholar] [CrossRef] [PubMed]
- Steve, M. Cybercrime to Cost the World $10.5 Trillion Annually by 2025. Cybercrime Magazine. 13 November 2020. Available online: https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021 (accessed on 8 August 2022).
- Cornea, A.A.; Obretin, A.M. Security Concerns Regarding Software Development Migrations in Quantum Computing Context; Department of Informatics and Economic Cybernetics, Bucharest University of Economic Studies: Bucharest, Romania, 2002; Volume 5, pp. 12–17. ISSN 2619-9955. [Google Scholar] [CrossRef]
- Rozell, D.J. Cash is king. Nature 2022, 16, 2022. [Google Scholar] [CrossRef] [PubMed]
- De Wolf, R. The potential impact of quantum computers on society. Ethics Inf. Technol. 2017, 19, 271. [Google Scholar] [CrossRef]
- Grimes, R.A. Cryptography Apocalypse: Preparing for the Day When Quantum Computing Breaks Today’s Crypto; John Wiley & Sons: Hoboken, NJ, USA, 2019. [Google Scholar]
- Schiffer, B.F. Quantum computers as an amplifier for existential risk. arXiv 2022, arXiv:2205.02761. [Google Scholar]
- Casati, N.M. Use of Quantum Computers in Understanding Cultures and Global Business Successes. In Culture in Global Businesses; Palgrave Macmillan: Cham, Switzerland, 2021; pp. 77–103. [Google Scholar]
- Scott, F., III. A Buyer’s Guide to Quantum as a Service: Qubits for Hire. Available online: https://www.zdnet.com/article/a-buyers-guide-to-quantum-as-a-service-qubits-for-hire/ (accessed on 21 May 2021).
- Sharma, S.K.; Khaliq, M. The role of quantum computing in software forensics and digital evidence: Issues and challenges. Limit. Future Appl. Quantum Cryptogr. 2021, 169–185. [Google Scholar]
- Raheman, F.; Bhagat, T.; Vermeulen, B.; Van Daele, P. Will Zero Vulnerability Computing (ZVC) Ever Be Possible? Testing the Hypothesis. Future Internet 2022, 14, 238. [Google Scholar] [CrossRef]
- Alagic, G.; Alagic, G.; Alperin-Sheriff, J.; Apon, D.; Cooper, D.; Dang, Q.; Smith-Tone, D. Status Report on the First Round of the NIST Post-Quantum Cryptography Standardization Process; US Department of Commerce, National Institute of Standards and Technology: Washington, DC, USA, 2019. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=927303 (accessed on 8 August 2022).
- Hoschek, M. Quantum security and 6G critical infrastructure. Serb. J. Eng. Manag. 2021, 6, 1–8. [Google Scholar] [CrossRef]
- Lennart, B.; Benjamin, K.; Niko, M.; Anika, P.; Henning, S. When—And How—To Prepare for Post-Quantum Cryptography. McKinsey Digital. 4 May 2022. Available online: https://www.mckinsey.com/business-functions/mckinsey-digital/our-insights/when-and-how-to-prepare-for-post-quantum-cryptography (accessed on 8 August 2022).
- Computer Security Research Center. Post Quantum Cryptography PQC: Workshops and Timeline. NIST; 7 July 2022. Available online: https://csrc.nist.gov/Projects/post-quantum-cryptography/workshops-and-timeline (accessed on 8 August 2022).
- Edlyn, T. The NIST Announcement on Quantum-Resistant Cryptography Standards is Out. Act Now! Cryptomathic. 6 July 2022. Available online: https://www.cryptomathic.com/news-events/blog/the-nist-announcement-on-quantum-resistant-cryptography-standards-is-out.-act-now (accessed on 8 August 2022).
- Mathew, S. Encryption Meant to Protect Against Quantum Hackers is Easily Cracked. New Scientist. 8 March 2022. Available online: https://www.newscientist.com/article/2310369-encryption-meant-to-protect-against-quantum-hackers-is-easily-cracked/ (accessed on 28 May 2022).
- Castryck, W.; Thomas., D. An efficient key recovery attack on SIDH (preliminary version). Cryptol. Eprint Arch. 2022. Available online: https://eprint.iacr.org/2022/975 (accessed on 8 August 2022).
- Laura, D. Post-Quantum Crypto Cracked in an Hour with One Core of an Ancient Xeon. The Register. 3 August 2022. Available online: https://www.theregister.com/2022/08/03/nist_quantum_resistant_crypto_cracked/ (accessed on 8 August 2022).
- Xue, W.; Wang, C.; Wang, J. Research on Cryptography as a Service Technique Based on Commercial Cryptography. In Proceedings of the 2022 IEEE 2nd International Conference on Electronic Technology, Communication and Information (ICETCI), Changchun, China, 27–29 May 2022; pp. 260–264. [Google Scholar] [CrossRef]
- Scala, N.M.; Reilly, A.C.; Goethals, P.L.; Cukier, M. Risk and the five hard problems of cybersecurity. Risk Anal. 2019, 39, 2119–2126. [Google Scholar] [CrossRef] [PubMed]
- Davis, G. 2020: Life with 50 billion connected devices. In Proceedings of the 2018 IEEE International Conference on Innovative Research and Development (ICCE), Las Vegas, NV, USA, 12–15 January 2018; p. 1. [Google Scholar]
- DrFazal. Why Computers Are Inherently Vulnerable? Medium. 3 August 2022. Available online: https://drfazal.medium.com/why-computers-are-inherently-vulnerable-fd7a34afaec6 (accessed on 8 August 2022).
- Raheman, F. Solid State Software On A Chip (3SOC) For Building Quantum Resistant Web 3.0 Computing Devices. U.S. Patent US29/842,535, 15 June 2022. [Google Scholar]
- Arikpo, I.I.; Ogban, F.U.; Eteng, I.E. Von Neumann architecture and modern computers. Glob. J. Math. Sci. 2007, 6, 97–103. [Google Scholar] [CrossRef]
- Francillon, A.; Castelluccia, C. Code injection attacks on Harvard-architecture devices. In Proceedings of the 15th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008. [Google Scholar]
- Moon, Y.H.; Kim, J.H.; Kim, D.S.; Kim, H.K. Hybrid Attack Path Enumeration System Based on Reputation Scores. In Proceedings of the 2016 IEEE International Conference on Computer and Information Technology (CIT), Nadi, Fiji, 8–10 December 2016; pp. 241–248. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Chanana, V.; Parashari, P.; Mumtaz, S.; Guizani, M. Present landscape of quantum computing. IET Quantum Commun. 2020, 1, 42–48. [Google Scholar] [CrossRef]
- Majot, A.; Yampolskiy, R. Global catastrophic risk and security implications of quantum computers. Futures 2015, 72, 17–26. [Google Scholar] [CrossRef]
- Elizabeth, G. Hello Quantum World! Google Publishes Landmark Quantum Supremacy Claim—The Company Says That Its Quantum Computer Is the First to Perform a Calculation That Would Be Practically Impossible for a Classical Machine. Nature 2019, 574, 461–463. [Google Scholar]
- Webber, M.; Elfving, V.; Weidt, S.; Hensinger, W.K. The impact of hardware specifications on reaching quantum advantage in the fault tolerant regime. AVS Quantum Sci. 2022, 4, 013801. [Google Scholar] [CrossRef]
- Chauhan, V.; Negi, S.; Jain, D.; Singh, P.; Sagar, A.K.; Sharma, A.K. Quantum Computers: A Review on How Quantum Computing Can Boom AI. In Proceedings of the 2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 28–29 April 2022. [Google Scholar]
- Aboy, M.; Timo, M.; Mauritz, K. Mapping the Patent Landscape of Quantum Technologies: Patenting Trends, Innovation and Policy Implications. IIC-Int. Rev. Intellect. Prop. Compet. Law 2022, 53, 853–882. [Google Scholar] [CrossRef]
- Ménard, A.; Ostojic, I.; Patel, M.; Volz, D. A game plan for quantum computing. McKinsey Q. 2020, 7–9. Available online: https://www.mckinsey.com/business-functions/mckinsey-digital/our-insights/a-game-plan-for-quantum-computing (accessed on 8 August 2022).
- Ding, J.A. New Proof of Work for Blockchain Based on Random Multivariate Quadratic Equations. In Applied Cryptography and Network Security Workshops; Zhou, J., Deng, R., Li, Z., Majumdar, S., Meng, W., Wang, L., Zhang, K., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 97–107. [Google Scholar]
- Schwabe, P.; Douglas, S.; Thom, W. Post-quantum TLS without handshake signatures. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 9–13 November 2020. [Google Scholar]




Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Raheman, F. The Future of Cybersecurity in the Age of Quantum Computers. Future Internet 2022, 14, 335. https://doi.org/10.3390/fi14110335
Raheman F. The Future of Cybersecurity in the Age of Quantum Computers. Future Internet. 2022; 14(11):335. https://doi.org/10.3390/fi14110335
Chicago/Turabian StyleRaheman, Fazal. 2022. "The Future of Cybersecurity in the Age of Quantum Computers" Future Internet 14, no. 11: 335. https://doi.org/10.3390/fi14110335
APA StyleRaheman, F. (2022). The Future of Cybersecurity in the Age of Quantum Computers. Future Internet, 14(11), 335. https://doi.org/10.3390/fi14110335






