Opportunities for Early Detection and Prediction of Ransomware Attacks against Industrial Control Systems
Abstract
1. Introduction
1.1. Recent ICS Ransomware Attacks
1.2. Objectives and Contributions
- We identify existing studies pertaining to ransomware attacks on SCADA systems and highlight the differences to establish our unique contribution;
- We discuss both technical and organizational aspects of the ransomware problem;
- We provide a generic situational-based framework that can be used to design solutions that combine the technical and environmental factors dealing with ransomware attacks on SCADA.
2. Related Works
2.1. SCADA Ransomware Surveys and Challenges
2.2. Ransomware Attacks on SCADA
2.3. Research Related to Ransomware Countermeasures
2.3.1. Ransomware Prevention
2.3.2. Ransomware Prediction and Detection
3. The Data Used for Ransomware Behavioral Analysis
- Cuckoo Sandbox: a popular open-source sandboxing platform that is widely used for malware analysis, including ransomware. It supports multiple operating systems, including Windows, Linux, and macOS, and allows researchers to monitor the behavior of malware in a virtual environment;
- Any.Run: a cloud-based sandboxing platform that allows users to analyze malware behavior in real-time. It supports a wide range of file types and provides detailed reports on the malware’s behavior, including network connections, file modifications, and registry changes;
- Hybrid Analysis: a malware analysis platform that combines sandboxing with threat intelligence to provide a comprehensive view of malware behavior. It supports multiple file types, including executables, documents, and archives, and provides detailed reports on the malware’s behavior and indicators of compromise (IOCs);
- VMRay Analyzer: a sandboxing platform that uses virtual machine introspection (VMI) to analyze malware behavior. It supports a wide range of file types and provides detailed reports on the malware’s behavior, including network connections, file modifications, and memory analysis.
- File system activity: information on which files and directories the ransomware accesses, modifies, or encrypts during an attack;
- Network activity: Data on the servers with which the ransomware communicates, the ports it uses, and the protocols it employs.;
- Registry modifications: changes made to the Windows registry by the ransomware, such as the creation or modification of registry keys;
- Process activity: information on the processes created or modified by the ransomware during an attack, as well as any child processes spawned by the malware;
- System configuration changes: changes made by the ransomware to system settings or configurations, such as changes to firewall rules or user account permissions;
- Memory analysis: the analysis of the ransomware’s behavior in memory, such as code injection, process hollowing, or other memory-based attacks;
- Behavioral indicators: specific patterns or behaviors associated with ransomware attacks, such as attempts to disable security software, or the presence of specific file types or extensions commonly targeted by ransomware.
4. Research Direction and Future Work
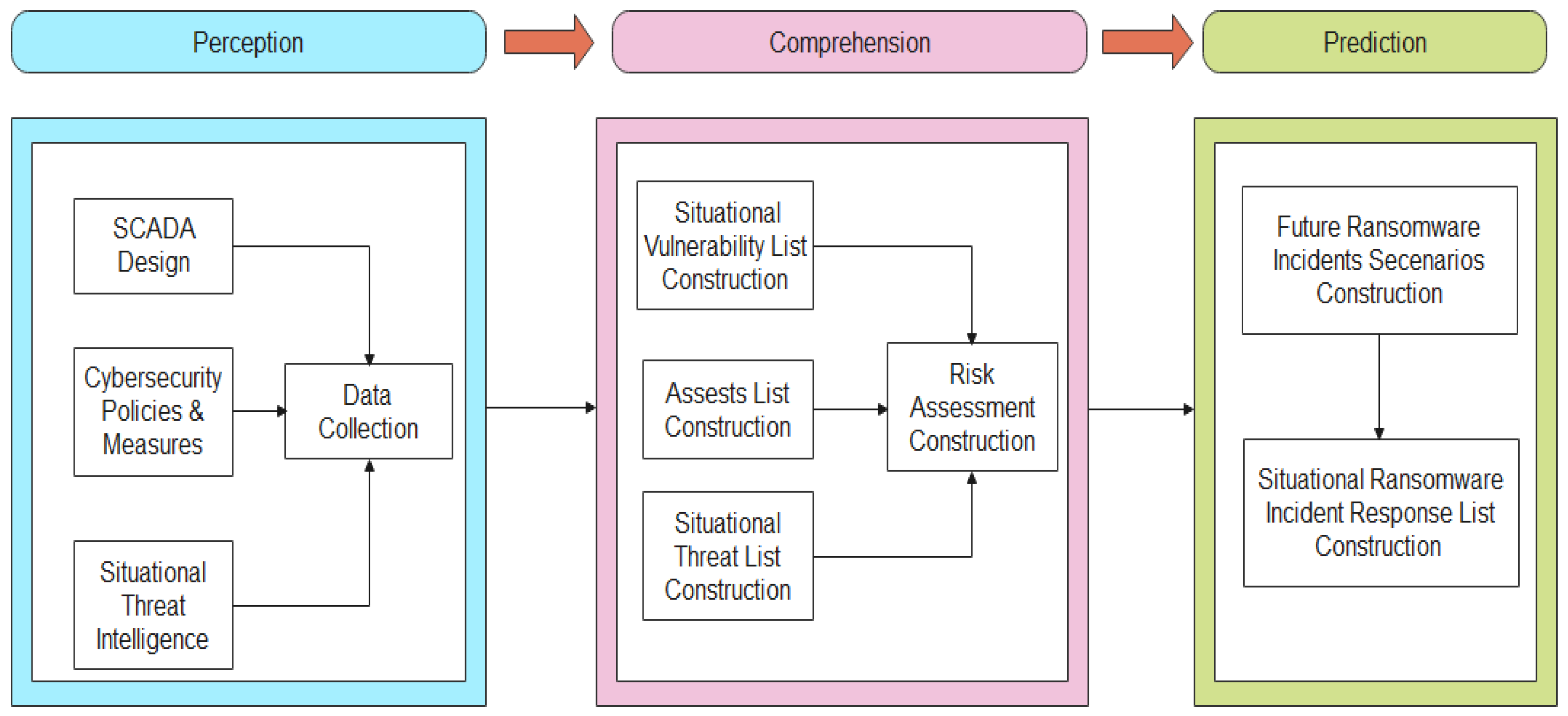
4.1. Research Direction: Situational Awareness Ransomware Prediction Framework
4.1.1. Perception Phase
4.1.2. Comprehension Phase
4.1.3. Projection Phase
4.2. Suggestions for Future Works
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Smadi, A.A.; Allehyani, M.F.; Johnson, B.K.; Lei, H. Power Quality Improvement Utilizing PV-UPQC Based on PI-SRF and PAC Controllers. In Proceedings of the 2022 IEEE Power & Energy Society General Meeting (PESGM), Denver, CO, USA, 17–21 July 2022. [Google Scholar]
- Camargo, O.A.M.; Duarte, J.C.; Dos Santos, A.F.P.; Borges, C.A. A Review of Testbeds on SCADA Systems with Malware Analysis. Rev. Inf. Teórica E Apl. 2022, 29, 84–94. [Google Scholar] [CrossRef]
- Aboaoja, F.A.; Zainal, A.; Ghaleb, F.A.; Al-Rimy, B.A.S.; Eisa, T.A.E.; Elnour, A.A.H. Malware detection issues, challenges, and future directions: A survey. Appl. Sci. 2022, 12, 8482. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; Smadi, A.A.; Allehyani, M.F. Meticulously intelligent identification system for smart grid network stability to optimize risk management. Energies 2021, 14, 6935. [Google Scholar] [CrossRef]
- Fovino, I.N.; Carcano, A.; Masera, M.; Trombetta, A. An experimental investigation of malware attacks on SCADA systems. Int. J. Crit. Infrastruct. Prot. 2009, 2, 139–145. [Google Scholar] [CrossRef]
- Nazir, S.; Patel, S.; Patel, D. Assessing and augmenting SCADA cyber security: A survey of techniques. Comput. Secur. 2017, 70, 436–454. [Google Scholar] [CrossRef]
- Mir, A.W.; Kumar, K.R. An Enhanced Implementation of Security Management System (SSMS) using UEBA in Smart Grid based SCADA Systems. In Applications of Machine Intelligence in Engineering; CRC Press: Boca Raton, FL, USA, 2022; pp. 1–11. [Google Scholar]
- Gómez, L.P.; Maimó, L.F.; Celdrán, A.H.; Clemente, F.J.G. Malware Detection in Industrial Scenarios Using Machine Learning and Deep Learning Techniques. Adv. Malware Data Driven Netw. Secur. 2022, 74–93. [Google Scholar]
- Reshmi, T. Information security breaches due to ransomware attacks-a systematic literature review. Int. J. Inf. Manag. Data Insights 2021, 1, 100013. [Google Scholar] [CrossRef]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Crypto-ransomware early detection model using novel incremental bagging with enhanced semi-random subspace selection. Future Gener. Comput. Syst. 2019, 101, 476–491. [Google Scholar] [CrossRef]
- Gazzan, M.; Alqahtani, A.; Sheldon, F.T. Key Factors Influencing the Rise of Current Ransomware Attacks on Industrial Control Systems. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021. [Google Scholar]
- Alqahtani, A.; Sheldon, F.T. A survey of crypto ransomware attack detection methodologies: An evolving outlook. Sensors 2022, 22, 1837. [Google Scholar] [CrossRef] [PubMed]
- Smadi, A.; Ajao, B.; Johnson, B.; Lei, H.; Chakhchoukh, Y.; Abu Al-Haija, Q. A Comprehensive survey on cyber-physical smart grid testbed architectures: Requirements and challenges. Electronics 2021, 10, 1043. [Google Scholar] [CrossRef]
- Alghofaili, Y.; Albattah, A.; Alrajeh, N.; Rassam, M.A.; Al-Rimy, B.A.S. Secure cloud infrastructure: A survey on issues, current solutions, and open challenges. Appl. Sci. 2021, 11, 9005. [Google Scholar] [CrossRef]
- Aboaoja, F.A.; Zainal, A.; Ghaleb, F.A.; Saleh Al-rimy, B.A. Toward an Ensemble Behavioral-Based Early Evasive Malware Detection Framework. In Proceedings of the 2021 International Conference on Data Science and Its Applications (ICoDSA), Bandung, Indonesia, 6–7 October 2021. [Google Scholar]
- Butt, U.J.; Abbod, M.; Lors, A.; Jahankhani, H.; Jamal, A.; Kumar, A. Ransomware Threat and Its Impact on SCADA. In Proceedings of the 2019 IEEE 12th International Conference on Global Security, Safety and Sustainability (ICGS3), London, UK, 16–18 January 2019. [Google Scholar]
- Basnet, M.; Poudyal, S.; Ali, M.H.; Dasgupta, D. Ransomware detection using deep learning in the SCADA system of electric vehicle charging station. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies Conference-Latin America (ISGT Latin America), Lima, Peru, 15–17 September 2021. [Google Scholar]
- Ibarra, J.; Butt, U.J.; Do, A.; Jahankhani, H.; Jamal, A. Ransomware impact to SCADA systems and its scope to critical infrastructure. In Proceedings of the 2019 IEEE 12th International Conference on Global Security, Safety and Sustainability (ICGS3), London, UK, 16–18 January 2019; pp. 1–12. [Google Scholar]
- Alanazi, M.; Mahmood, A.; Chowdhury, M.J.M. SCADA Vulnerabilities and Attacks: A Review of the State-of-the-Art and Open Issues. Comput. Secur. 2022, 125, 103028. [Google Scholar] [CrossRef]
- Oz, H.; Aris, A.; Levi, A.; Uluagac, A.S. A survey on ransomware: Evolution, taxonomy, and defense solutions. ACM Comput. Surv. CSUR 2022, 54, 1–37. [Google Scholar] [CrossRef]
- Humayun, M.; Jhanjhi, N.Z.; Alsayat, A.; Ponnusamy, V. Internet of things and ransomware: Evolution, mitigation and prevention. Egypt. Inform. J. 2021, 22, 105–117. [Google Scholar] [CrossRef]
- Beaman, C.; Barkworth, A.; Akande, T.D.; Hakak, S.; Khan, M.K. Ransomware: Recent advances, analysis, challenges and future research directions. Comput. Secur. 2021, 111, 102490. [Google Scholar] [CrossRef]
- Berrueta, E.; Morato, D.; Magaña, E.; Izal, M. A survey on detection techniques for cryptographic ransomware. IEEE Access 2019, 7, 144925–144944. [Google Scholar] [CrossRef]
- Urooj, U.; Maarof, M.A.B.; Al-rimy, B.A.S. A Proposed Adaptive Pre-Encryption Crypto-Ransomware Early Detection Model. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021. [Google Scholar]
- Olaimat, M.N.; Maarof, M.A.; Al-rimy, B.A.S. Ransomware Anti-Analysis and Evasion Techniques: A Survey and Research Directions. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021; IEEE: New York, NY, USA. [Google Scholar]
- Ahmed, Y.A.; Huda, S.; Al-Rimy, B.A.S.; Alharbi, N.; Saeed, F.; Ghaleb, F.A.; Ali, I.M. A weighted minimum redundancy maximum relevance technique for ransomware early detection in industrial IoT. Sustainability 2022, 14, 1231. [Google Scholar] [CrossRef]
- Ahmed, Y.A.; Koçer, B.; Huda, S.; Al-Rimy, B.A.S.; Hassan, M.M. A system call refinement-based enhanced Minimum Redundancy Maximum Relevance method for ransomware early detection. J. Netw. Comput. Appl. 2020, 167, 102753. [Google Scholar] [CrossRef]
- Ahmed, Y.A.; Kocer, B.; Al-rimy, B.A.S. Automated analysis approach for the detection of high survivable ransomware. KSII Trans. Internet Inf. Syst. TIIS 2020, 14, 2236–2257. [Google Scholar]
- Mierzwa, S.J.; Drylie, J.J.; Ho, C.; Bogdan, D.; Watson, K. Ransomware Incident Preparations with Ethical Considerations and Command System Framework Proposal. J. Leadersh. Account. Ethics 2022, 19. [Google Scholar]
- Connolly, L.Y.; Wall, D.S. The rise of crypto-ransomware in a changing cybercrime landscape: Taxonomising countermeasures. Comput. Secur. 2019, 87, 101568. [Google Scholar] [CrossRef]
- Brewer, R. Ransomware attacks: Detection, prevention and cure. Netw. Secur. 2016, 2016, 5–9. [Google Scholar] [CrossRef]
- Rhode, M.; Burnap, P.; Jones, K. Early-stage malware prediction using recurrent neural networks. Comput. Secur. 2018, 77, 578–594. [Google Scholar] [CrossRef]
- Adamu, U.; Awan, I. Ransomware Prediction Using Supervised Learning Algorithms. In Proceedings of the 2019 7th International Conference on Future Internet of Things and Cloud (FiCloud), Istanbul, Turkey, 26–28 August 2019. [Google Scholar]
- Bahtiyar, Ş.; Yaman, M.B.; Altıniğne, C.Y. A multi-dimensional machine learning approach to predict advanced malware. Comput. Netw. 2019, 160, 118–129. [Google Scholar] [CrossRef]
- Leguesse, Y.; Vella, M.; Ellul, J. AndroNeo: Hardening Android Malware Sandboxes by Predicting Evasion Heuristics; Springer International Publishing: Berlin/Heidelberg, Germany, 2018. [Google Scholar]
- Acosta-Maestre, H.A. The Empirical Study of the Factors that Influence Threat Avoidance Behaviour in Ransomware Security Incidents; Nova Southeastern University: Ann Arbor, MI, USA, 2021; p. 95. [Google Scholar]
- Connolly, L.Y.; Wall, D.S.; Lang, M.; Oddson, B. An empirical study of ransomware attacks on organizations: An assessment of severity and salient factors affecting vulnerability. J. Cybersecur. 2020, 6, tyaa023. [Google Scholar] [CrossRef]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Ransomware threat success factors, taxonomy, and countermeasures: A survey and research directions. Comput. Secur. 2018, 74, 144–166. [Google Scholar] [CrossRef]
- Lévesque, F.L.; Chiasson, S.; Somayaji, A.; Fernandez, J.M. Technological and human factors of malware attacks: A computer security clinical trial approach. ACM Trans. Priv. Secur. TOPS 2018, 21, 1–30. [Google Scholar] [CrossRef]
- Holt, T.J.; Bossler, A.M. Examining the Relationship Between Routine Activities and Malware Infection Indicators. J. Contemp. Crim. Justice 2013, 29, 420–436. [Google Scholar] [CrossRef]
- Moti, Z.; Hashemi, S.; Namavar, A. Discovering Future Malware Variants by Generating New Malware Samples Using Generative Adversarial Network. In Proceedings of the 2019 9th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 24–25 October 2019. [Google Scholar]
- Lu, S.; Ying, L.; Lin, W.; Wang, Y. New era of deeplearning-based malware intrusion detection: The malware detection and prediction based on deep learning. arXiv 2019, arXiv:1907.08356. [Google Scholar]
- Hu, W.; Tan, Y. Generating adversarial malware examples for black-box attacks based on GAN. arXiv 2017, arXiv:1702.05983. [Google Scholar]
- Popli, N.K.; Girdhar, A. Behavioural Analysis of Recent Ransomwares and Prediction of Future Attacks by polymorphic and Metamorphic Ransomware. In Computational Intelligence: Theories, Applications and Future Directions-Volume II; Springer: Berlin/Heidelberg, Germany, 2019; pp. 65–80. [Google Scholar]
- Yeboah-Ofori, A.; Boachie, C. Malware Attack Predictive Analytics in a Cyber Supply Chain Context Using Machine Learning. In Proceedings of the 2019 International Conference on Cyber Security and Internet of Things (ICSIoT), Accra, Ghana, 29–31 May 2019. [Google Scholar]
- Patel, V.; Choe, S.; Halabi, T. Predicting Future Malware Attacks on Cloud Systems using Machine Learning. In Proceedings of the 2020 IEEE 6th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Baltimore, MD, USA, 25–27 May 2020. [Google Scholar]
- Albulayhi, K.; Al-Haija, Q.A. Early-Stage Malware and Ransomware Forecasting in the Short-Term Future Using Regression-based Neural Network Technique. In Proceedings of the 2022 14th International Conference on Computational Intelligence and Communication Networks (CICN), Al-Khobar, Saudi Arabia, 4–6 December 2022. [Google Scholar]
- Mathane, V.; Lakshmi, P. Predictive analysis of ransomware attacks using context-aware AI in IoT systems. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 240–244. [Google Scholar] [CrossRef]
- Sadighian, S.A.; Robert, J.-M.; Sarencheh, S.; Basu, S. A Context-Aware Malware Detection Based on Low- Level Hardware Indicators as a Last Line of Defense. In Proceedings of the SECURWARE 2017: The Eleventh International Conference on Emerging Security Information, Systems and Technologies, Rome, Italy, 10–14 September 2017; pp. 10–19. [Google Scholar]
- Amer, E.; El-Sappagh, S. Robust deep learning early alarm prediction model based on the behavioral smell for android malware. Comput. Secur. 2022, 116, 102670. [Google Scholar] [CrossRef]
- Khan, M.; Naeem, M.R.; Al-Ammar, E.A.; Ko, W.; Vettikalladi, H.; Ahmad, I. Power forecasting of regional wind farms via variational auto-encoder and deep hybrid transfer learning. Electronics 2022, 11, 206. [Google Scholar] [CrossRef]
- Mehedi, S.T.; Anwar, A.; Rahman, Z.; Ahmed, K.; Islam, R. Dependable intrusion detection system for IoT: A deep transfer learning based approach. IEEE Trans. Ind. Inform. 2022, 19, 1006–1017. [Google Scholar] [CrossRef]
| Author | Problem | Solution | Method | Tools | Empirical | Limitation |
|---|---|---|---|---|---|---|
| [32] | Existing approaches to detect the malware need to collect enough data which takes more time, during which the sabotage has likely already been inflicted by the time of detection. | Predicting the behavior based on a short snapshot of behavioral data. | An ensemble RNN. The method was able to predict the attack within 5 s with an accuracy of around 94 %. | Keras, and Tensorflow | Yes | The method relies on historical data to predict the behavior. This approach is not suitable for obfuscated behavior that tries to show a major difference between past and future attacks. |
| [50] | Due to the obfuscation techniques employed by advanced malware, detection is no longer enough, and there is a need for methodologies to predict future behavior instead. | A rapid sequence snapshot analysis was used to make the prediction decisions. | A set of random snapshots were taken from the APIs and permission data and used to train an ensemble LSTM model that is used for the prediction. | Tensorflow | Yes | The LSTM was trained on historical data only, which assumes that these historical attack patterns are likely to reoccur in future attacks. This does not hold, especially with the use of obfuscation and polymorphic strategies adopted by the malware to change the attack behavior. |
| [33] | The detection of ransomware based on past attack data is not suitable to detect novel, zero-day attacks, which are common nowadays. | The behavioral patterns extracted from the dynamic analysis of ransomware during the execution time were used to train a prediction model. | Support vector machines (SVM) were used to build the prediction model based on the behavioral data. | Scikit Learn, and Pandas | Yes | This approach also uses historical behavior to predict future ones. This is not suitable for evasive ransomware that uses obfuscation and polymorphism to change its behavior from time to time. |
| [34] | Advanced malware can obfuscate much of its traces through many mechanisms, such as metamorphic engines. Therefore, the detection of such malware has become a significant challenge for malware analysis mechanisms. | A regression model to predict advanced malware based on a selected set of significant features extracted from a dataset of malware runtime data. | The dataset is created by executing real-world malware samples and capturing the behavioral data into trace files. | N/A | Yes | The model was trained using historical data of existing and known malware samples. The dataset does not contain the future behaviors necessary for accurate prediction models. |
| [35] | Sophisticated Android malware families often implement techniques aimed at avoiding detection. Split-personality malware, for example, behaves benignly when it detects that it is running on an analysis environment such as a malware sandbox, and maliciously when running on a real user’s device. | Exploiting sandbox detecting heuristic prediction to predict and automatically generate bytecode patches. | An Andronew, a heuristic approach, was used based on API calls collected during the execution time of the malware. | Sandbox | Yes | The heuristics were performed based on historical data, which limits the ability of this approach to predict the future behavior of malware |
| [41] | Zero-day malware attacks are challenging due to the polymorphic nature of the malware. | Generating synthesized malware samples based on existing malware signatures derived from the static analysis of malware payloads. | GAN algorithm to generate artificial malware samples. | Keras, and Tensorflow | Yes | The static analysis adopted by the study does not reveal the behavioral aspect of the malware as polymorphism works during the runtime. In addition, the packing and encryption techniques used by sophisticated malware prevent the static analysis from exploring the malware features. |
| [42] | Existing malware detection is not accurate enough. | A cluster-based detection engine that is trained based on artificial patterns represents the trending of malware behavior. | GAN algorithm to create malware patterns. | N/A | N/A | There was no evidence of the applicability and efficacy of the model. |
| [43] | Malware authors have the ability to reveal the features used by detection models. | MalGAN model that attacks black-box machine-learning detection models. | A substitute detector to fit the black-box malware detection system. | N/A | Yes | The data used for model training were general and limited to malware operational behavior. The context was not captured. |
| [44] | The ransomware changes its behavior which makes it difficult to detect. | The study studies data collected from the ransomware process and its interaction with the file system. | It used malware development toolkits to create ransomware samples. | ADMMutate, Clet, and Phatbot | Yes | The study is limited to the ability of the tools to manually create samples, which makes it impractical to have a diversified dataset. |
| [45] | Detecting novel malware attacks is difficult as the behavior changes continuously. | The model examines the patterns in the data and studies the evolution of the malware behavior. | It used a collection of data from previous malware infections to train a logistic regression algorithm. | N/A | Yes | Relying on the evolution of the attack behavior to forecast future attacks is not sufficient to visualize the sophisticated malware attacks. |
| [47] | The new types of malware tend to be more difficult to detect than older ones. This has made content-based, signature-based, and pattern-matching techniques less effective in detecting and preventing ransomware attacks. | Utilized the neural network algorithm to predict the future occurrences of ransomware and malware attacks over time. | Time-series regression-based neural network algorithm model. | TensorFlow, Keras, NumPy, Matplotlib, and Pandas | Yes | The model concentrates solely on data pertaining to processing operations, disregarding the context in which the process was executed. |
| [48] | Existing ransomware attack predictions are not tailored for IoT systems that are diverse and resource-constrained environments. | A technique for predicting ransomware using contextual data and utilizing a context ontology to gather information characteristics of ransomware attacks against the IoT. | An ontology approach with SVM. | N/A | Yes | Relying only on contextual data and ignoring the behavioral data is insufficient for modeling the characteristics of the evasive malware attacks. |
| [50] | Detection solutions alone are no longer enough to protect against malware due to the increasing rate of zero-day attacks. | An early prediction of malware attacks in Android devices was proposed. By capturing the implicit contextual relations between various data, the model predicts the suspicious behavior of a running process using data collected during the early stages of the attack within the same session. | LSTM and ensemble learning. | N/A | Yes | This approach is inadequate in terms of the necessary data required for an accurate prediction and is unable to anticipate the future behavior of the malware. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gazzan, M.; Sheldon, F.T. Opportunities for Early Detection and Prediction of Ransomware Attacks against Industrial Control Systems. Future Internet 2023, 15, 144. https://doi.org/10.3390/fi15040144
Gazzan M, Sheldon FT. Opportunities for Early Detection and Prediction of Ransomware Attacks against Industrial Control Systems. Future Internet. 2023; 15(4):144. https://doi.org/10.3390/fi15040144
Chicago/Turabian StyleGazzan, Mazen, and Frederick T. Sheldon. 2023. "Opportunities for Early Detection and Prediction of Ransomware Attacks against Industrial Control Systems" Future Internet 15, no. 4: 144. https://doi.org/10.3390/fi15040144
APA StyleGazzan, M., & Sheldon, F. T. (2023). Opportunities for Early Detection and Prediction of Ransomware Attacks against Industrial Control Systems. Future Internet, 15(4), 144. https://doi.org/10.3390/fi15040144







