A Survey on Blockchain-Based Federated Learning
Abstract
:1. Introduction
- We offer an overview encompassing the definition, architectural design, and challenges of both blockchains and FL. We also delve into the motivations driving the application of blockchains in the context of FL.
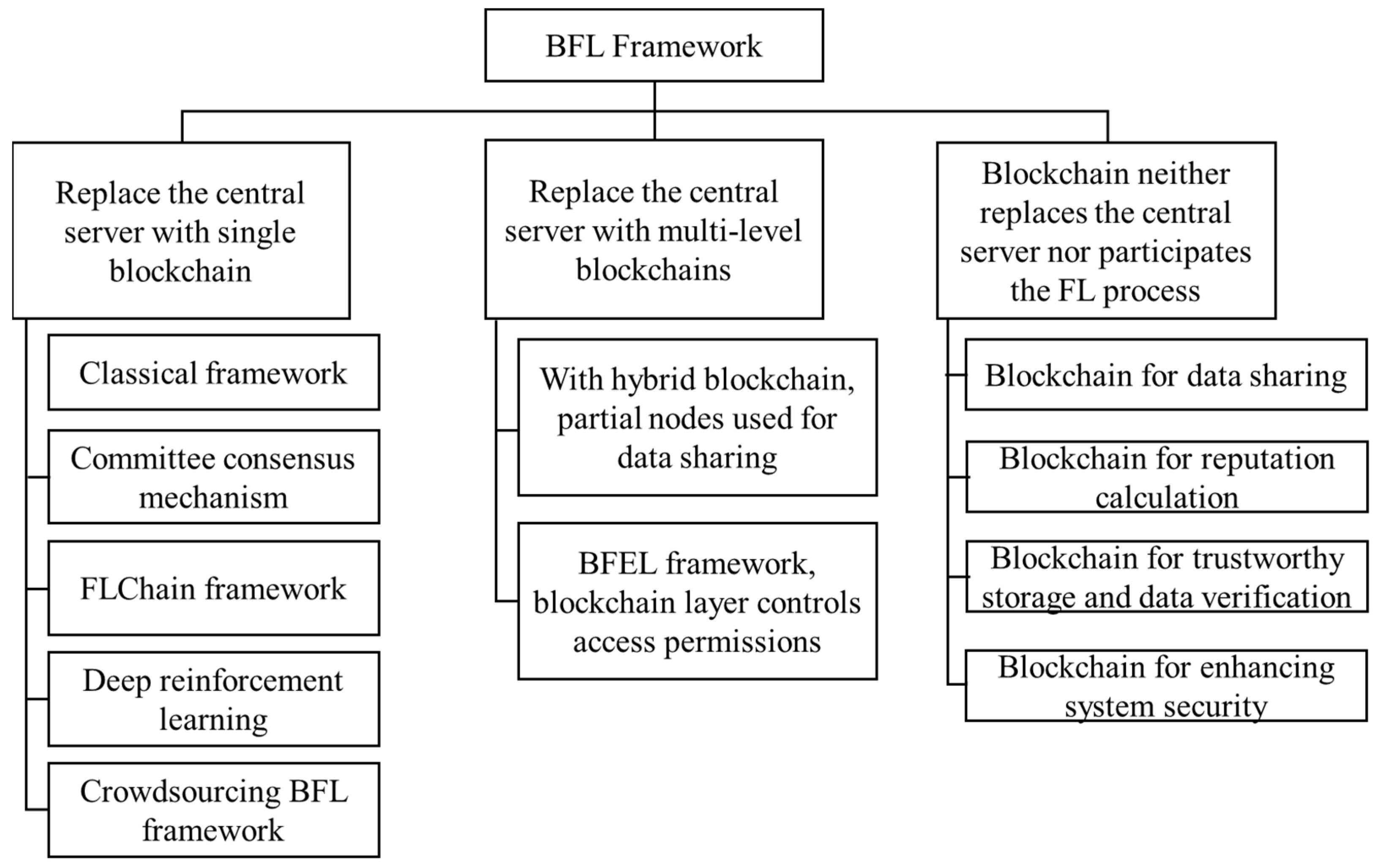
- We categorize BFL frameworks into three distinct classes based on how blockchains participated in the FL process within individual nodes.
- We elaborate on how to use blockchain technology to mitigate the challenges of FL from the perspectives of decentralization, incentive mechanisms, attack resistance, privacy protection, and efficiency enhancement.
- We compile a comprehensive list of current viable applications for BFL and engage in discussions regarding the promising future directions and unresolved issues in the field of BFL.
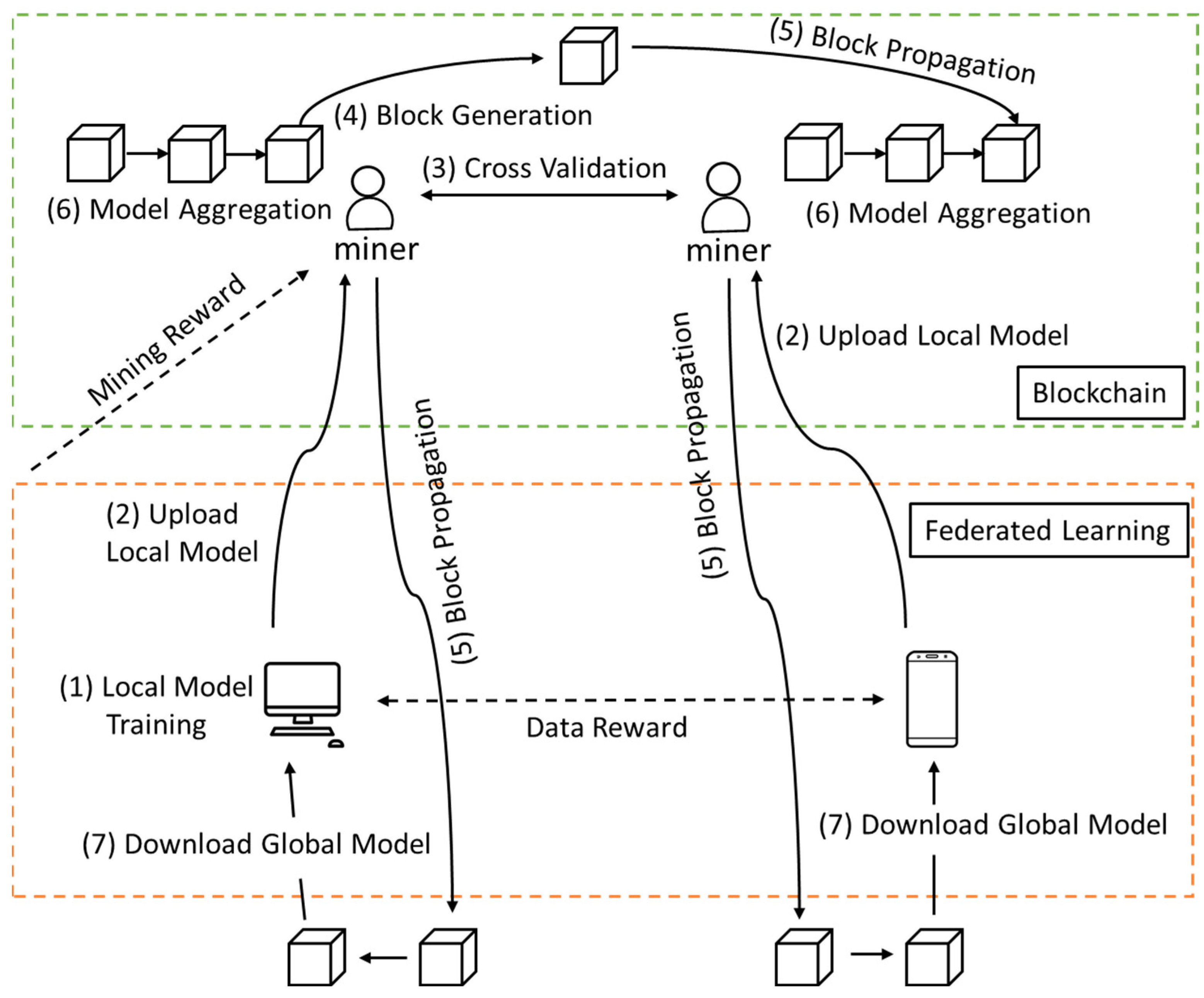
2. Preliminary
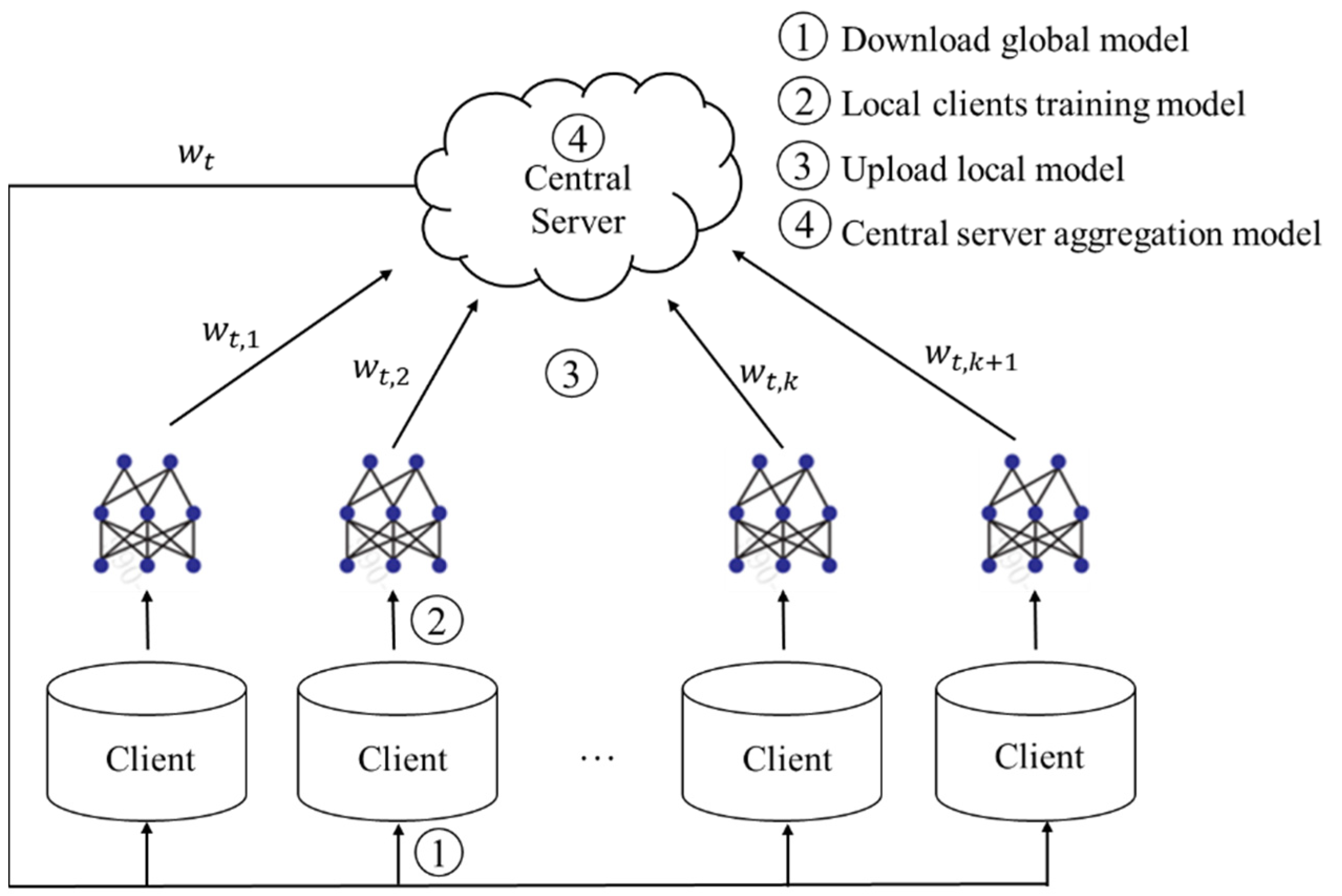
2.1. Overview of Federated Learning
- Client devices retrieve the global parameter from the server;
- Each client k trains its local data to derive its local model (signifying the local model update for the client in the communication round);
- All participating clients transmit their local model updates to the central server;
- Upon receiving updates from diverse clients, the central server executes weighted aggregation operations to formulate the global model (indicating the global model update in the communication round).
2.2. Threats and Challenges of FL
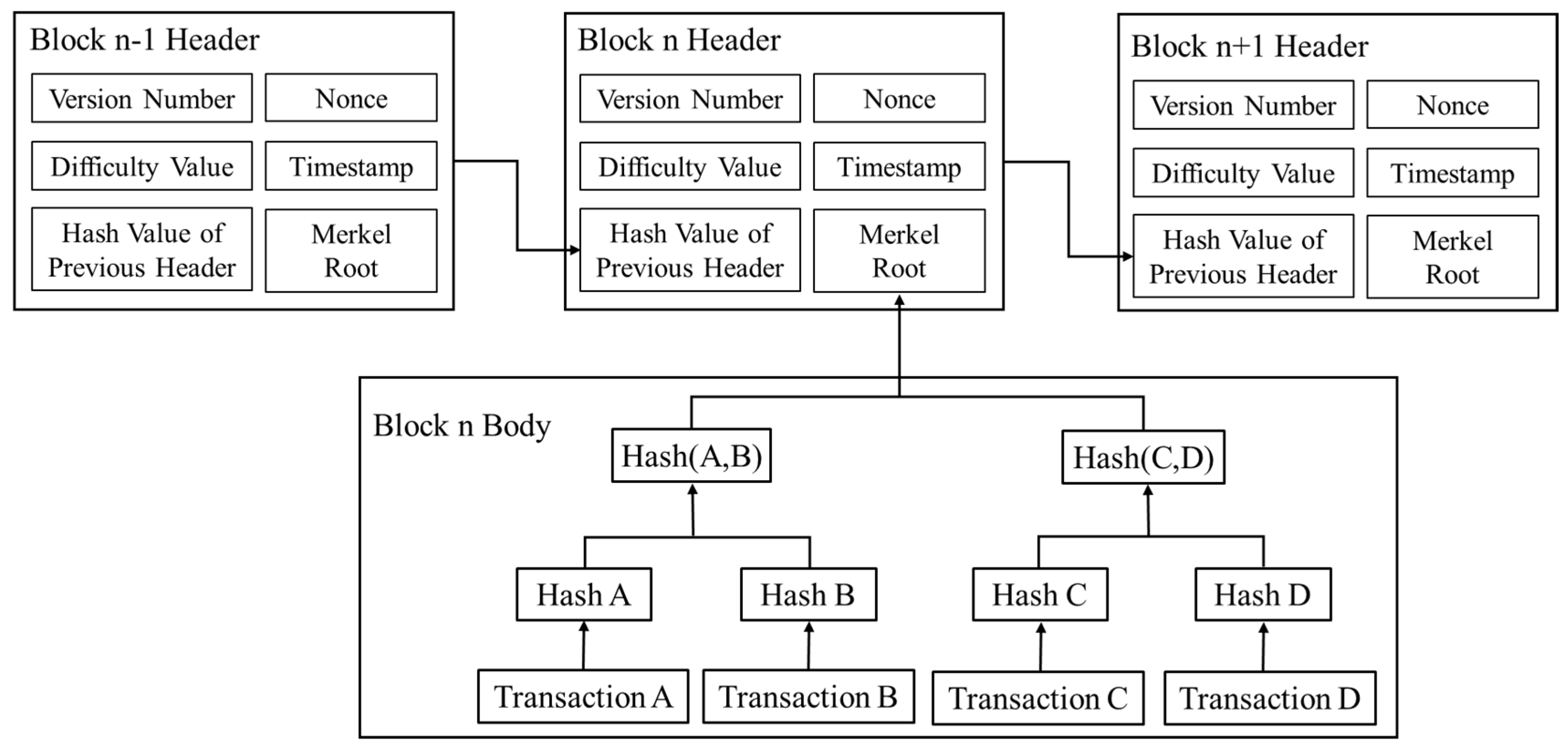
2.3. Overview of Blockchains
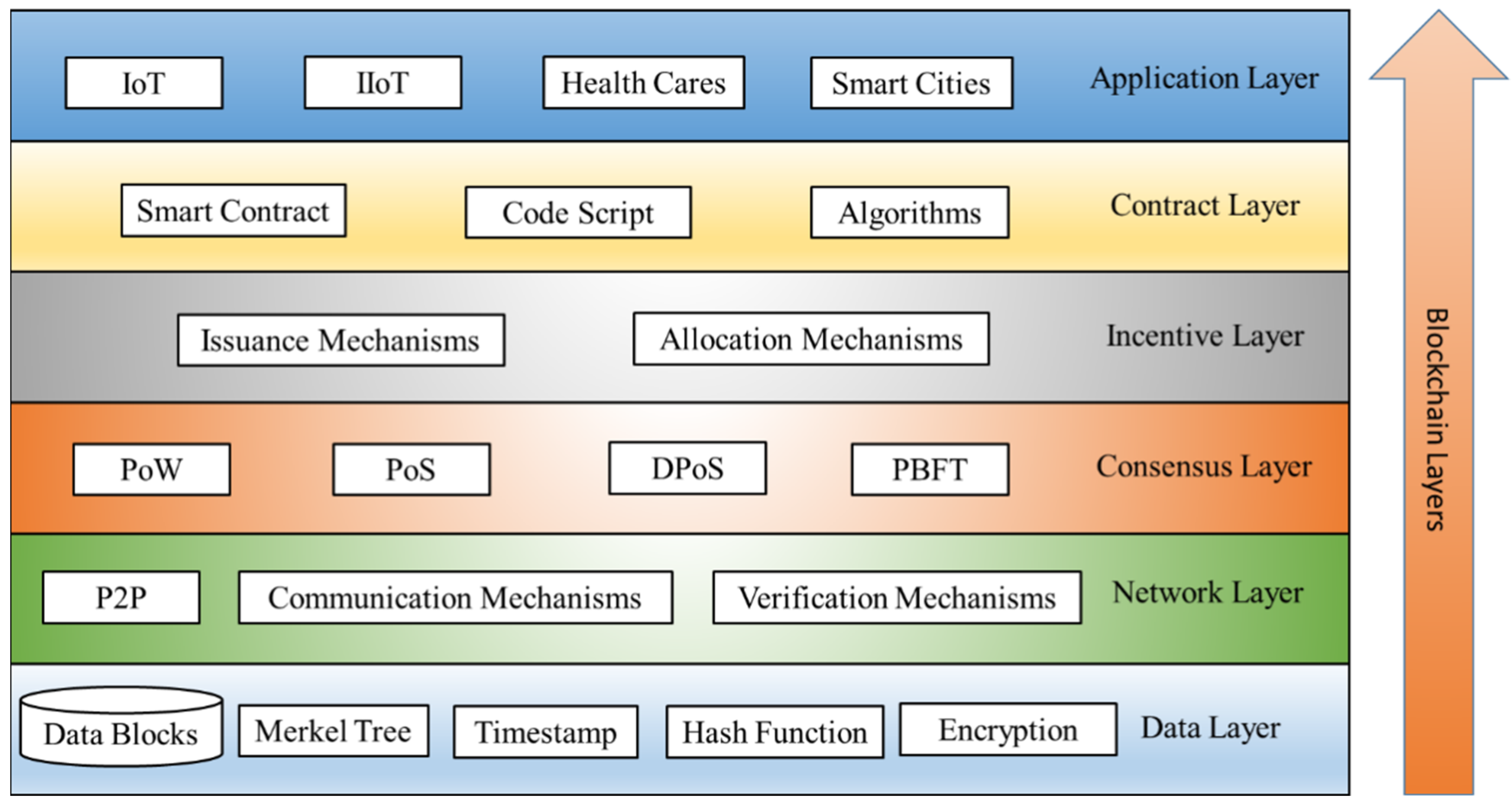
2.4. Architecture of Blockchains
- A.
- Data layer
- B.
- Network layer
- C.
- Consensus layer
- D.
- Incentive layer
- E.
- Contract layer
- F.
- Application layer
3. Blockchain-Based Federated Learning
3.1. Frameworks of BFL
3.2. Functions of BFL
3.2.1. Decentralization
3.2.2. Incentive Mechanism
3.2.3. Attack Resistance
3.2.4. Privacy Protection
3.2.5. Efficiency Enhancement
4. Applications
4.1. Internet of Things
4.2. Industrial Internet of Things
4.3. Smart Healthcare
4.4. Internet of Vehicles
5. Challenges and Future Directions
5.1. Privacy Concerns
5.2. Efficiency, Performance, Scalability
5.3. Security Concerns
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bourse, F.; Minelli, M.; Minihold, M.; Paillier, P. Fast Homomorphic Evaluation of Deep Discretized Neural Networks. In Proceedings of the Advances in Cryptology—CRYPTO 2018: 38th Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2018; Proceedings, Part III. Springer-Verlag: Berlin/Heidelberg, Germany, 2018; pp. 483–512. [Google Scholar]
- Shi, E.; Chan, T.-H.H.; Rieffel, E.; Song, D. Distributed Private Data Analysis: Lower Bounds and Practical Constructions. ACM Trans. Algorithms 2017, 13, 1–38. [Google Scholar] [CrossRef]
- Albrecht, J.P. How the GDPR Will Change the World. Eur. Data Prot. Law. Rev. 2016, 2, 287–289. [Google Scholar] [CrossRef]
- Bonawitz, K.; Eichner, H.; Grieskamp, W.; Huba, D.; Ingerman, A.; Ivanov, V.; Kiddon, C.; Konečný, J.; Mazzocchi, S.; McMahan, B.; et al. Towards Federated Learning at Scale: System Design. Proc. Mach. Learn. Syst. 2019, 1, 374–388. [Google Scholar]
- Zhao, L.; Ni, L.; Hu, S.; Chen, Y.; Zhou, P.; Xiao, F.; Wu, L. InPrivate Digging: Enabling Tree-Based Distributed Data Mining with Differential Privacy. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 2087–2095. [Google Scholar]
- Sprague, M.R.; Jalalirad, A.; Scavuzzo, M.; Capota, C.; Neun, M.; Do, L.; Kopp, M. Asynchronous Federated Learning for Geospatial Applications. In Proceedings of the ECML PKDD 2018 Workshops, Dublin, Ireland, 10–14 September 2018; Monreale, A., Alzate, C., Kamp, M., Krishnamurthy, Y., Paurat, D., Sayed-Mouchaweh, M., Bifet, A., Gama, J., Ribeiro, R.P., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 21–28. [Google Scholar]
- Li, Q.; Wen, Z.; He, B. Practical Federated Gradient Boosting Decision Trees. Proc. AAAI Conf. Artif. Intell. 2020, 34, 4642–4649. [Google Scholar] [CrossRef]
- Xie, C.; Koyejo, S.; Gupta, I. Asynchronous Federated Optimization. Available online: https://arxiv.org/abs/1903.03934v5 (accessed on 30 November 2023).
- Bhowmick, A.; Duchi, J.; Freudiger, J.; Kapoor, G.; Rogers, R. Protection against Reconstruction and Its Applications in Private Federated Learning. Available online: https://arxiv.org/abs/1812.00984v2 (accessed on 10 October 2023).
- Fredrikson, M.; Lantz, E.; Jha, S.; Lin, S.; Page, D.; Ristenpart, T. Privacy in Pharmacogenetics: An {End-to-End} Case Study of Personalized Warfarin Dosing. In Proceedings of the 23rd USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 17–32. [Google Scholar]
- Melis, L.; Song, C.; De Cristofaro, E.; Shmatikov, V. Exploiting Unintended Feature Leakage in Collaborative Learning. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 23 May 2019; pp. 691–706. [Google Scholar]
- Hitaj, B.; Ateniese, G.; Perez-Cruz, F. Deep Models Under the GAN: Information Leakage from Collaborative Deep Learning. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 3 November 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 603–618. [Google Scholar]
- Carlini, N.; Liu, C.; Erlingsson, Ú.; Kos, J.; Song, D. The Secret Sharer: Evaluating and Testing Unintended Memorization in Neural Networks. In Proceedings of the 28rd USENIX Security Symposium, Santa Clara, CA, USA, 14–16 August 2019. [Google Scholar]
- Song, M.; Wang, Z.; Zhang, Z.; Song, Y.; Wang, Q.; Ren, J.; Qi, H. Analyzing User-Level Privacy Attack Against Federated Learning. IEEE J. Sel. Areas Commun. 2020, 38, 2430–2444. [Google Scholar] [CrossRef]
- Geiping, J.; Bauermeister, H.; Dröge, H.; Moeller, M. Inverting Gradients—How Easy Is It to Break Privacy in Federated Learning? In Proceedings of the Advances in Neural Information Processing Systems, Online, 6–12 December 2020; Curran Associates, Inc.: New York, NY, USA, 2020; Volume 33, pp. 16937–16947. [Google Scholar]
- Konečný, J.; McMahan, H.B.; Yu, F.X.; Richtárik, P.; Suresh, A.T.; Bacon, D. Federated Learning: Strategies for Improving Communication Efficiency. Available online: https://arxiv.org/abs/1610.05492v2 (accessed on 10 October 2023).
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A. Communication-Efficient Learning of Deep Networks from Decentralized Data. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, PMLR, Fort Lauderdale, FL, USA, 20–22 April 2017; pp. 1273–1282. [Google Scholar]
- Wang, L.; Wang, W.; Li, B. CMFL: Mitigating Communication Overhead for Federated Learning. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–9 July 2019; pp. 954–964. [Google Scholar]
- Li, L.; Fan, Y.; Tse, M.; Lin, K.-Y. A Review of Applications in Federated Learning. Comput. Ind. Eng. 2020, 149, 106854. [Google Scholar] [CrossRef]
- Li, T.; Sahu, A.K.; Talwalkar, A.; Smith, V. Federated Learning: Challenges, Methods, and Future Directions. IEEE Signal. Process. Mag. 2020, 37, 50–60. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 30 November 2023).
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain Challenges and Opportunities: A Survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Toyoda, K.; Zhang, A.N. Mechanism Design for An Incentive-Aware Blockchain-Enabled Federated Learning Platform. In Proceedings of the 2019 IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019; pp. 395–403. [Google Scholar]
- Hou, D.; Zhang, J.; Man, K.L.; Ma, J.; Peng, Z. A Systematic Literature Review of Blockchain-Based Federated Learning: Architectures, Applications and Issues. In Proceedings of the 2021 2nd Information Communication Technologies Conference (ICTC), Nanjing, China, 7–9 May 2021; pp. 302–307. [Google Scholar]
- Wahab, O.A.; Mourad, A.; Otrok, H.; Taleb, T. Federated Machine Learning: Survey, Multi-Level Classification, Desirable Criteria and Future Directions in Communication and Networking Systems. IEEE Commun. Surv. Tutor. 2021, 23, 1342–1397. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Ding, M.; Pham, Q.-V.; Pathirana, P.N.; Le, L.B.; Seneviratne, A.; Li, J.; Niyato, D.; Poor, H.V. Federated Learning Meets Blockchain in Edge Computing: Opportunities and Challenges. IEEE Internet Things J. 2021, 8, 12806–12825. [Google Scholar] [CrossRef]
- Issa, W.; Moustafa, N.; Turnbull, B.; Sohrabi, N.; Tari, Z. Blockchain-Based Federated Learning for Securing Internet of Things: A Comprehensive Survey. ACM Comput. Surv. 2023, 55, 191. [Google Scholar] [CrossRef]
- Li, D.; Han, D.; Weng, T.-H.; Zheng, Z.; Li, H.; Liu, H.; Castiglione, A.; Li, K.-C. Blockchain for Federated Learning toward Secure Distributed Machine Learning Systems: A Systemic Survey. Soft Comput. 2022, 26, 4423–4440. [Google Scholar] [CrossRef]
- Feng, L.; Zhao, Y.; Guo, S.; Qiu, X.; Li, W.; Yu, P. BAFL: A Blockchain-Based Asynchronous Federated Learning Framework. IEEE Trans. Comput. 2022, 71, 1092–1103. [Google Scholar] [CrossRef]
- Li, Y.; Chen, C.; Liu, N.; Huang, H.; Zheng, Z.; Yan, Q. A Blockchain-Based Decentralized Federated Learning Framework with Committee Consensus. IEEE Netw. 2021, 35, 234–241. [Google Scholar] [CrossRef]
- Lyu, L.; Yu, H.; Yang, Q. Threats to Federated Learning: A Survey. arXiv 2020, preprint. arXiv:2003.02133. [Google Scholar]
- Khan, L.U.; Saad, W.; Han, Z.; Hossain, E.; Hong, C.S. Federated Learning for Internet of Things: Recent Advances, Taxonomy, and Open Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 1759–1799. [Google Scholar] [CrossRef]
- Sun, G.; Cong, Y.; Dong, J.; Wang, Q.; Lyu, L.; Liu, J. Data Poisoning Attacks on Federated Machine Learning. IEEE Internet Things J. 2022, 9, 11365–11375. [Google Scholar] [CrossRef]
- Tolpegin, V.; Truex, S.; Gursoy, M.E.; Liu, L. Data Poisoning Attacks Against Federated Learning Systems. In Proceedings of the Computer Security—ESORICS 2020, Guildford, UK, 14–18 September 2020; Chen, L., Li, N., Liang, K., Schneider, S., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 480–501. [Google Scholar]
- Chen, X.; Liu, C.; Li, B.; Lu, K.; Song, D. Targeted Backdoor Attacks on Deep Learning Systems Using Data Poisoning. arXiv 2017, preprint. arXiv:1712.05526. [Google Scholar]
- Alfeld, S.; Zhu, X.; Barford, P. Data Poisoning Attacks against Autoregressive Models. In Proceedings of the AAAI Conference on Artificial Intelligence, Phoenix, AZ, USA, 12–17 February 2016; Volume 30. [Google Scholar]
- Li, B.; Wang, Y.; Singh, A.; Vorobeychik, Y. Data Poisoning Attacks on Factorization-Based Collaborative Filtering. In Proceedings of the 30th Annual Conference on Neural Information Processing Systems 2016, Barcelona, Spain, 5–10 December 2016; Volume 29. [Google Scholar]
- Caldas, S.; Konečny, J.; McMahan, H.B.; Talwalkar, A. Expanding the Reach of Federated Learning by Reducing Client Resource Requirements. Available online: https://arxiv.org/abs/1812.07210v2 (accessed on 10 October 2023).
- Nofer, M.; Gomber, P.; Hinz, O.; Schiereck, D. Blockchain. Bus. Inf. Syst. Eng. 2017, 59, 183–187. [Google Scholar] [CrossRef]
- Zheng, W.; Zheng, Z.; Chen, X.; Dai, K.; Li, P.; Chen, R. Nutbaas: A Blockchain-as-a-Service Platform. IEEE Access 2019, 7, 134422–134433. [Google Scholar] [CrossRef]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain Technology Overview. Available online: https://arxiv.org/abs/1906.11078v1 (accessed on 10 October 2023).
- Xu, L.; Shah, N.; Chen, L.; Diallo, N.; Gao, Z.; Lu, Y.; Shi, W. Enabling the Sharing Economy: Privacy Respecting Contract Based on Public Blockchain. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts, Abu Dhabi, United Arab Emirates, 2 April 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 15–21. [Google Scholar]
- Jiao, Y.; Wang, P.; Niyato, D.; Suankaewmanee, K. Auction Mechanisms in Cloud/Fog Computing Resource Allocation for Public Blockchain Networks. IEEE Trans. Parallel Distrib. Syst. 2019, 30, 1975–1989. [Google Scholar] [CrossRef]
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain Technology: Beyond Bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-Preserving Energy Trading Using Consortium Blockchain in Smart Grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3690–3700. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Wang, P.; Ye, D.; Kim, D.I. Incentivizing Consensus Propagation in Proof-of-Stake Based Consortium Blockchain Networks. IEEE Wirel. Commun. Lett. 2019, 8, 157–160. [Google Scholar] [CrossRef]
- Xu, M.; Chen, X.; Kou, G. A Systematic Review of Blockchain. Financ. Innov. 2019, 5, 27. [Google Scholar] [CrossRef]
- Yang, M.; Zhu, T.; Liang, K.; Zhou, W.; Deng, R.H. A Blockchain-Based Location Privacy-Preserving Crowdsensing System. Future Gener. Comput. Syst. 2019, 94, 408–418. [Google Scholar] [CrossRef]
- Rouhani, S.; Deters, R. Performance Analysis of Ethereum Transactions in Private Blockchain. In Proceedings of the 2017 8th IEEE International Conference on Software Engineering and Service Science (ICSESS), Piscataway, NJ, USA, 24–26 November 2017; pp. 70–74. [Google Scholar]
- Dinh, T.T.A.; Wang, J.; Chen, G.; Liu, R.; Ooi, B.C.; Tan, K.-L. BLOCKBENCH: A Framework for Analyzing Private Blockchains. In Proceedings of the 2017 ACM International Conference on Management of Data, Chicago, IL, USA, 14–19 May 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 1085–1100. [Google Scholar]
- Iansiti, M.; Lakhani, K.R. The Truth about Blockchain. Harv. Bus. Rev. 2017, 95, 118–127. [Google Scholar]
- Wang, W.; Hoang, D.T.; Hu, P.; Xiong, Z.; Niyato, D.; Wang, P.; Wen, Y.; Kim, D.I. A Survey on Consensus Mechanisms and Mining Strategy Management in Blockchain Networks. IEEE Access 2019, 7, 22328–22370. [Google Scholar] [CrossRef]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the Security and Performance of Proof of Work Blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 3–16. [Google Scholar]
- Nguyen, C.T.; Hoang, D.T.; Nguyen, D.N.; Niyato, D.; Nguyen, H.T.; Dutkiewicz, E. Proof-of-Stake Consensus Mechanisms for Future Blockchain Networks: Fundamentals, Applications and Opportunities. IEEE Access 2019, 7, 85727–85745. [Google Scholar] [CrossRef]
- Saad, S.M.S.; Radzi, R.Z.R.M. Comparative Review of the Blockchain Consensus Algorithm between Proof of Stake (POS) and Delegated Proof of Stake (DPOS). Int. J. Innov. Comput. 2020, 10, 1273–1282. [Google Scholar] [CrossRef]
- Ailijiang, A.; Charapko, A.; Demirbas, M. Consensus in the Cloud: Paxos Systems Demystified. In Proceedings of the 2016 25th International Conference on Computer Communication and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 1–10. [Google Scholar]
- Huang, D.; Ma, X.; Zhang, S. Performance Analysis of the Raft Consensus Algorithm for Private Blockchains. IEEE Trans. Syst. Man. Cybern. Syst. 2020, 50, 172–181. [Google Scholar] [CrossRef]
- Sukhwani, H.; Martínez, J.M.; Chang, X.; Trivedi, K.S.; Rindos, A. Performance Modeling of PBFT Consensus Process for Permissioned Blockchain Network (Hyperledger Fabric). In Proceedings of the 2017 IEEE 36th Symposium on Reliable Distributed Systems (SRDS), Hong Kong, China, 26 September 2017; pp. 253–255. [Google Scholar]
- Bamakan, S.M.H.; Babaei Bondarti, A.; Babaei Bondarti, P.; Qu, Q. Blockchain Technology Forecasting by Patent Analytics and Text Mining. Blockchain Res. Appl. 2021, 2, 100019. [Google Scholar] [CrossRef]
- Dos Santos, S.; Singh, J.; Thulasiram, R.K.; Kamali, S.; Sirico, L.; Loud, L. A New Era of Blockchain-Powered Decentralized Finance (DeFi)—A Review. In Proceedings of the 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 27 June–1 July 2022; pp. 1286–1292. [Google Scholar]
- Wu, H.; Cao, J.; Yang, Y.; Tung, C.L.; Jiang, S.; Tang, B.; Liu, Y.; Wang, X.; Deng, Y. Data Management in Supply Chain Using Blockchain: Challenges and a Case Study. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–8. [Google Scholar]
- Wu, H.; Jiang, S.; Cao, J. High-Efficiency Blockchain-Based Supply Chain Traceability. IEEE Trans. Intell. Transp. Syst. 2023, 24, 3748–3758. [Google Scholar] [CrossRef]
- Yao, S.; Wang, M.; Qu, Q.; Zhang, Z.; Zhang, Y.-F.; Xu, K.; Xu, M. Blockchain-Empowered Collaborative Task Offloading for Cloud-Edge-Device Computing. IEEE J. Sel. Areas Commun. 2022, 40, 3485–3500. [Google Scholar] [CrossRef]
- Liu, Y.; Lu, Q.; Chen, S.; Qu, Q.; O’Connor, H.; Raymond Choo, K.-K.; Zhang, H. Capability-Based IoT Access Control Using Blockchain. Digit. Commun. Netw. 2021, 7, 463–469. [Google Scholar] [CrossRef]
- Lalitha, A.; Kilinc, O.C.; Javidi, T.; Koushanfar, F. Peer-to-Peer Federated Learning on Graphs. arXiv 2019, preprint. arXiv:1901.11173. [Google Scholar]
- Savazzi, S.; Nicoli, M.; Rampa, V. Federated Learning with Cooperating Devices: A Consensus Approach for Massive IoT Networks. IEEE Internet Things J. 2020, 7, 4641–4654. [Google Scholar] [CrossRef]
- Hu, C.; Jiang, J.; Wang, Z. Decentralized Federated Learning: A Segmented Gossip Approach. arXiv 2019, preprint. arXiv:1908.07782. [Google Scholar]
- Abou El Houda, Z.; Hafid, A.S.; Khoukhi, L. Mitfed: A Privacy Preserving Collaborative Network Attack Mitigation Framework Based on Federated Learning Using Sdn and Blockchain. IEEE Trans. Netw. Sci. Eng. 2023, 10, 1985–2001. [Google Scholar] [CrossRef]
- Moulahi, T.; Jabbar, R.; Alabdulatif, A.; Abbas, S.; El Khediri, S.; Zidi, S.; Rizwan, M. Privacy-preserving Federated Learning Cyber-threat Detection for Intelligent Transport Systems with Blockchain-based Security. Expert. Syst. 2023, 40, e13103. [Google Scholar] [CrossRef]
- Huang, X.; Wu, Y.; Liang, C.; Chen, Q.; Zhang, J. Distance-Aware Hierarchical Federated Learning in Blockchain-Enabled Edge Computing Network. IEEE Internet Things J. 2023, 10, 19163–19176. [Google Scholar] [CrossRef]
- Bao, X.; Su, C.; Xiong, Y.; Huang, W.; Hu, Y. Flchain: A Blockchain for Auditable Federated Learning with Trust and Incentive. In Proceedings of the 2019 5th International Conference on Big Data Computing and Communications (BIGCOM), IEEE, Qingdao, China, 9–11 August 2019; pp. 151–159. [Google Scholar]
- Baucas, M.J.; Spachos, P.; Plataniotis, K.N. Federated Learning and Blockchain-Enabled Fog-IoT Platform for Wearables in Predictive Healthcare. IEEE Trans. Comput. Soc. Syst. 2023, 10, 1732–1741. [Google Scholar] [CrossRef]
- Ullah, I.; Deng, X.; Pei, X.; Jiang, P.; Mushtaq, H. A Verifiable and Privacy-Preserving Blockchain-Based Federated Learning Approach. Peer Peer Netw. Appl. 2023, 16, 2256–2270. [Google Scholar] [CrossRef]
- Mohammed, M.A.; Lakhan, A.; Abdulkareem, K.H.; Zebari, D.A.; Nedoma, J.; Martinek, R.; Kadry, S.; Garcia-Zapirain, B. Energy-Efficient Distributed Federated Learning Offloading and Scheduling Healthcare System in Blockchain Based Networks. Internet Things 2023, 22, 100815. [Google Scholar] [CrossRef]
- Fan, M.; Zhang, Z.; Li, Z.; Sun, G.; Yu, H.; Guizani, M. Blockchain-Based Decentralized and Lightweight Anonymous Authentication for Federated Learning. IEEE Trans. Veh. Technol. 2023, 72, 12075–12086. [Google Scholar] [CrossRef]
- Zhang, J.; Liu, Y.; Qin, X.; Xu, X.; Zhang, P. Adaptive Resource Allocation for Blockchain-Based Federated Learning in Internet of Things. IEEE Internet Things J. 2023, 10, 10621–10635. [Google Scholar] [CrossRef]
- Yang, F.; Abedin, M.Z.; Hajek, P. An Explainable Federated Learning and Blockchain-Based Secure Credit Modeling Method. Eur. J. Oper. Res. 2023, in press. [Google Scholar] [CrossRef]
- Singh, S.K.; Yang, L.T.; Park, J.H. FusionFedBlock: Fusion of Blockchain and Federated Learning to Preserve Privacy in Industry 5.0. Inf. Fusion. 2023, 90, 233–240. [Google Scholar] [CrossRef]
- Kim, H.; Park, J.; Bennis, M.; Kim, S.-L. Blockchained On-Device Federated Learning. IEEE Commun. Lett. 2020, 24, 1279–1283. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J. Federated Learning with Blockchain for Autonomous Vehicles: Analysis and Design Challenges. IEEE Trans. Commun. 2020, 68, 4734–4746. [Google Scholar] [CrossRef]
- Qu, Y.; Gao, L.; Luan, T.H.; Xiang, Y.; Yu, S.; Li, B.; Zheng, G. Decentralized Privacy Using Blockchain-Enabled Federated Learning in Fog Computing. IEEE Internet Things J. 2020, 7, 5171–5183. [Google Scholar] [CrossRef]
- Awan, S.; Li, F.; Luo, B.; Liu, M. Poster: A Reliable and Accountable Privacy-Preserving Federated Learning Framework Using the Blockchain. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 2561–2563. [Google Scholar]
- Hieu, N.Q.; Anh, T.T.; Luong, N.C.; Niyato, D.; Kim, D.I.; Elmroth, E. Resource Management for Blockchain-Enabled Federated Learning: A Deep Reinforcement Learning Approach. Available online: https://arxiv.org/abs/2004.04104v2 (accessed on 10 October 2023).
- Majeed, U.; Hong, C.S. FLchain: Federated Learning via MEC-Enabled Blockchain Network. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–4. [Google Scholar]
- Li, Z.; Liu, J.; Hao, J.; Wang, H.; Xian, M. CrowdSFL: A Secure Crowd Computing Framework Based on Blockchain and Federated Learning. Electronics 2020, 9, 773. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Zhang, K.; Maharjan, S.; Zhang, Y. Blockchain Empowered Asynchronous Federated Learning for Secure Data Sharing in Internet of Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 4298–4311. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Jiang, C.; Liu, Y.; Guo, S.; Zhang, Y.; Niyato, D.; Leung, C.; Miao, C. Scalable and Communication-Efficient Decentralized Federated Edge Learning with Multi-Blockchain Framework. In Proceedings of the Blockchain and Trustworthy Systems, Dali, China, 6–7 August 2020; Zheng, Z., Dai, H.-N., Fu, X., Chen, B., Eds.; Springer: Singapore, 2020; pp. 152–165. [Google Scholar]
- Lu, Y.; Huang, X.; Dai, Y.; Maharjan, S.; Zhang, Y. Blockchain and Federated Learning for Privacy-Preserved Data Sharing in Industrial IoT (Not Survey). IEEE Trans. Ind. Inf. 2020, 16, 4177–4186. [Google Scholar] [CrossRef]
- ur Rehman, M.H.; Salah, K.; Damiani, E.; Svetinovic, D. Towards Blockchain-Based Reputation-Aware Federated Learning. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Online, 6–9 July 2020; pp. 183–188. [Google Scholar]
- Zhang, W.; Lu, Q.; Yu, Q.; Li, Z.; Liu, Y.; Lo, S.K.; Chen, S.; Xu, X.; Zhu, L. Blockchain-Based Federated Learning for Device Failure Detection in Industrial IoT. IEEE Internet Things J. 2021, 8, 5926–5937. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Zhang, K.; Maharjan, S.; Zhang, Y. Low-Latency Federated Learning and Blockchain for Edge Association in Digital Twin Empowered 6G Networks. IEEE Trans. Ind. Inform. 2021, 17, 5098–5107. [Google Scholar] [CrossRef]
- Jiang, C.; Xu, C.; Cao, C.; Chen, K. GAIN: Decentralized Privacy-Preserving Federated Learning. J. Inf. Secur. Appl. 2023, 78, 103615. [Google Scholar] [CrossRef]
- Ma, X.; Xu, D. TORR: A Lightweight Blockchain for Decentralized Federated Learning. IEEE Internet Things J. 2023, 1. [Google Scholar] [CrossRef]
- Zekiye, A.; Özkasap, Ö. Decentralized Healthcare Systems with Federated Learning and Blockchain. arXiv 2023, preprint. arXiv:2306.17188. [Google Scholar]
- Liu, S.; Wang, X.; Hui, L.; Wu, W. Blockchain-Based Decentralized Federated Learning Method in Edge Computing Environment. Appl. Sci. 2023, 13, 1677. [Google Scholar] [CrossRef]
- Sharma, P.K.; Park, J.H.; Cho, K. Blockchain and Federated Learning-Based Distributed Computing Defence Framework for Sustainable Society. Sustain. Cities Soc. 2020, 59, 102220. [Google Scholar] [CrossRef]
- Arachchige, P.C.M.; Bertok, P.; Khalil, I.; Liu, D.; Camtepe, S.; Atiquzzaman, M. A Trustworthy Privacy Preserving Framework for Machine Learning in Industrial IoT Systems. IEEE Trans. Ind. Inform. 2020, 16, 6092–6102. [Google Scholar] [CrossRef]
- Wang, Z.; Hu, Q.; Li, R.; Xu, M.; Xiong, Z. Incentive Mechanism Design for Joint Resource Allocation in Blockchain-Based Federated Learning. IEEE Trans. Parallel Distrib. Syst. 2023, 34, 1536–1547. [Google Scholar] [CrossRef]
- Park, M.; Chai, S. BTIMFL: A Blockchain-Based Trust Incentive Mechanism in Federated Learning. In Proceedings of the International Conference on Computational Science and Its Applications, Athens, Greece, 3–6 July 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 175–185. [Google Scholar]
- Kim, H.; Park, J.; Bennis, M.; Kim, S.-L. On-Device Federated Learning via Blockchain and Its Latency Analysis. arXiv 2018, arXiv:1808.03949. [Google Scholar]
- Kang, J.; Xiong, Z.; Niyato, D.; Xie, S.; Zhang, J. Incentive Mechanism for Reliable Federated Learning: A Joint Optimization Approach to Combining Reputation and Contract Theory. IEEE Internet Things J. 2019, 6, 10700–10714. [Google Scholar] [CrossRef]
- Weng, J.; Weng, J.; Zhang, J.; Li, M.; Zhang, Y.; Luo, W. DeepChain: Auditable and Privacy-Preserving Deep Learning with Blockchain-Based Incentive. IEEE Trans. Dependable Secur. Comput. 2021, 18, 2438–2455. [Google Scholar] [CrossRef]
- Kim, Y.J.; Hong, C.S. Blockchain-Based Node-Aware Dynamic Weighting Methods for Improving Federated Learning Performance. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–4. [Google Scholar]
- Zhan, Y.; Li, P.; Qu, Z.; Zeng, D.; Guo, S. A Learning-Based Incentive Mechanism for Federated Learning. IEEE Internet Things J. 2020, 7, 6360–6368. [Google Scholar] [CrossRef]
- Dong, N.; Wang, Z.; Sun, J.; Kampffmeyer, M.; Wen, Y.; Zhang, S.; Knottenbelt, W.; Xing, E. Defending Against Malicious Behaviors in Federated Learning with Blockchain. arXiv 2023, preprint. arXiv:2307.00543. [Google Scholar]
- Kalapaaking, A.P.; Khalil, I.; Yi, X. Blockchain-Based Federated Learning with SMPC Model Verification Against Poisoning Attack for Healthcare Systems. IEEE Trans. Emerg. Top. Comput. 2023, 1–11. [Google Scholar] [CrossRef]
- Prokop, K.; Połap, D.; Srivastava, G.; Lin, J.C.-W. Blockchain-Based Federated Learning with Checksums to Increase Security in Internet of Things Solutions. J. Ambient. Intell. Hum. Comput. 2023, 14, 4685–4694. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhao, J.; Jiang, L.; Tan, R.; Niyato, D.; Li, Z.; Lyu, L.; Liu, Y. Privacy-Preserving Blockchain-Based Federated Learning for IoT Devices. IEEE Internet Things J. 2021, 8, 1817–1829. [Google Scholar] [CrossRef]
- Zhang, K.; Huang, H.; Guo, S.; Zhou, X. Blockchain-Based Participant Selection for Federated Learning. In Proceedings of the Blockchain and Trustworthy Systems, Dali, China, 6–7 August 2020; Zheng, Z., Dai, H.-N., Fu, X., Chen, B., Eds.; Springer: Singapore, 2020; pp. 112–125. [Google Scholar]
- Shayan, M.; Fung, C.; Yoon, C.J.M.; Beschastnikh, I. Biscotti: A Blockchain System for Private and Secure Federated Learning. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 1513–1525. [Google Scholar] [CrossRef]
- Chen, H.; Asif, S.A.; Park, J.; Shen, C.-C.; Bennis, M. Robust Blockchained Federated Learning with Model Validation and Proof-of-Stake Inspired Consensus. Available online: https://arxiv.org/abs/2101.03300v1 (accessed on 10 October 2023).
- Ouyang, L.; Wang, F.-Y.; Tian, Y.; Jia, X.; Qi, H.; Wang, G. Artificial Identification: A Novel Privacy Framework for Federated Learning Based on Blockchain. IEEE Trans. Comput. Soc. Syst. 2023, 1–10. [Google Scholar] [CrossRef]
- Javed, L.; Anjum, A.; Yakubu, B.M.; Iqbal, M.; Moqurrab, S.A.; Srivastava, G. ShareChain: Blockchain-enabled Model for Sharing Patient Data Using Federated Learning and Differential Privacy. Expert. Syst. 2023, 40, e13131. [Google Scholar] [CrossRef]
- Guduri, M.; Chakraborty, C.; Margala, M. Blockchain-Based Federated Learning Technique for Privacy Preservation and Security of Smart Electronic Health Records. IEEE Trans. Consum. Electron. 2023, 1. [Google Scholar] [CrossRef]
- Martinez, I.; Francis, S.; Hafid, A.S. Record and Reward Federated Learning Contributions with Blockchain. In Proceedings of the 2019 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Guilin, China, 17–19 October 2019; pp. 50–57. [Google Scholar]
- Tao, R.E.N.; Ruochen, J.I.N.; Yongmei, L.U.O. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning. Netinfo Secur. 2021, 21, 27. [Google Scholar] [CrossRef]
- Qi, Y.; Hossain, M.S.; Nie, J.; Li, X. Privacy-Preserving Blockchain-Based Federated Learning for Traffic Flow Prediction. Future Gener. Comput. Syst. 2021, 117, 328–337. [Google Scholar] [CrossRef]
- Zhang, J.; Zhou, J.; Guo, J.; Sun, X. Visual Object Detection for Privacy-Preserving Federated Learning. IEEE Access 2023, 11, 33324–33335. [Google Scholar] [CrossRef]
- Mahmood, Z.; Jusas, V. Blockchain-Enabled: Multi-Layered Security Federated Learning Platform for Preserving Data Privacy. Electronics 2022, 11, 1624. [Google Scholar] [CrossRef]
- Kumar, S.; Dutta, S.; Chatturvedi, S.; Bhatia, M. Strategies for Enhancing Training and Privacy in Blockchain Enabled Federated Learning. In Proceedings of the 2020 IEEE Sixth International Conference on Multimedia Big Data (BigMM), New Delhi, India, 24–26 September 2020; pp. 333–340. [Google Scholar]
- Kalapaaking, A.P.; Khalil, I.; Rahman, M.S.; Atiquzzaman, M.; Yi, X.; Almashor, M. Blockchain-Based Federated Learning with Secure Aggregation in Trusted Execution Environment for Internet-of-Things. IEEE Trans. Ind. Inform. 2023, 19, 1703–1714. [Google Scholar] [CrossRef]
- Zhang, P.; Hong, Y.; Kumar, N.; Alazab, M.; Alshehri, M.D.; Jiang, C. BC-EdgeFL: A Defensive Transmission Model Based on Blockchain-Assisted Reinforced Federated Learning in IIoT Environment. IEEE Trans. Ind. Inform. 2021, 18, 3551–3561. [Google Scholar] [CrossRef]
- Kang, J.; Ye, D.; Nie, J.; Xiao, J.; Deng, X.; Wang, S.; Xiong, Z.; Yu, R.; Niyato, D. Blockchain-Based Federated Learning for Industrial Metaverses: Incentive Scheme with Optimal AoI. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22–25 August 2022; pp. 71–78. [Google Scholar]
- Lian, Z.; Zeng, Q.; Wang, W.; Gadekallu, T.R.; Su, C. Blockchain-Based Two-Stage Federated Learning With Non-IID Data in IoMT System. IEEE Trans. Comput. Soc. Syst. 2023, 10, 1701–1710. [Google Scholar] [CrossRef]
- Passerat-Palmbach, J.; Farnan, T.; Miller, R.; Gross, M.S.; Flannery, H.L.; Gleim, B. A Blockchain-Orchestrated Federated Learning Architecture for Healthcare Consortia. Available online: https://arxiv.org/abs/1910.12603v1 (accessed on 10 October 2023).
- El Rifai, O.; Biotteau, M.; de Boissezon, X.; Megdiche, I.; Ravat, F.; Teste, O. Blockchain-Based Federated Learning in Medicine. In Proceedings of the Artificial Intelligence in Medicine, Minneapolis, MN, USA, 25–28 August 2020; Michalowski, M., Moskovitch, R., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 214–224. [Google Scholar]
- Połap, D.; Srivastava, G.; Jolfaei, A.; Parizi, R.M. Blockchain Technology and Neural Networks for the Internet of Medical Things. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Online, 6–9 July 2020; pp. 508–513. [Google Scholar]
- Rahman, M.A.; Hossain, M.S.; Islam, M.S.; Alrajeh, N.A.; Muhammad, G. Secure and Provenance Enhanced Internet of Health Things Framework: A Blockchain Managed Federated Learning Approach. IEEE Access 2020, 8, 205071–205087. [Google Scholar] [CrossRef] [PubMed]
- Aich, S.; Sinai, N.K.; Kumar, S.; Ali, M.; Choi, Y.R.; Joo, M.-I.; Kim, H.-C. Protecting Personal Healthcare Record Using Blockchain & Federated Learning Technologies. In Proceedings of the 24th International Conference on Advanced Communication Technology (ICACT), IEEE, Pyeongchang, Republic of Korea, 13–16 February 2022; pp. 109–112. [Google Scholar]
- Kumar, R.; Khan, A.A.; Kumar, J.; Zakria; Golilarz, N.A.; Zhang, S.; Ting, Y.; Zheng, C.; Wang, W. Blockchain-Federated-Learning and Deep Learning Models for COVID-19 Detection Using CT Imaging. IEEE Sens. J. 2021, 21, 16301–16314. [Google Scholar] [CrossRef] [PubMed]
- Hua, G.; Zhu, L.; Wu, J.; Shen, C.; Zhou, L.; Lin, Q. Blockchain-Based Federated Learning for Intelligent Control in Heavy Haul Railway. IEEE Access 2020, 8, 176830–176839. [Google Scholar] [CrossRef]
- Chai, H.; Leng, S.; Chen, Y.; Zhang, K. A Hierarchical Blockchain-Enabled Federated Learning Algorithm for Knowledge Sharing in Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3975–3986. [Google Scholar] [CrossRef]
- Cui, L.; Su, X.; Ming, Z.; Chen, Z.; Yang, S.; Zhou, Y.; Xiao, W. CREAT: Blockchain-Assisted Compression Algorithm of Federated Learning for Content Caching in Edge Computing. IEEE Internet Things J. 2022, 9, 14151–14161. [Google Scholar] [CrossRef]
- Halim, S.M.; Khan, L.; Thuraisingham, B. Next—Location Prediction Using Federated Learning on a Blockchain. In Proceedings of the 2020 IEEE Second International Conference on Cognitive Machine Intelligence (CogMI), Atlanta, GA, USA, 28–31 October 2020; pp. 244–250. [Google Scholar]
- Wang, Y.; Su, Z.; Zhang, N.; Benslimane, A. Learning in the Air: Secure Federated Learning for UAV-Assisted Crowdsensing. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1055–1069. [Google Scholar] [CrossRef]
- Pokhrel, S.R. Federated Learning Meets Blockchain at 6G Edge: A Drone-Assisted Networking for Disaster Response. In Proceedings of the 2nd ACM MobiCom Workshop on Drone Assisted Wireless Communications for 5G and Beyond, London, UK, 25 September 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 49–54. [Google Scholar]
- Wang, Y.; Tian, Y.; Yin, X.; Hei, X. A Trusted Recommendation Scheme for Privacy Protection Based on Federated Learning. CCF Trans. Netw. 2020, 3, 218–228. [Google Scholar] [CrossRef]
- Singh, A.; Click, K.; Parizi, R.M.; Zhang, Q.; Dehghantanha, A.; Choo, K.-K.R. Sidechain Technologies in Blockchain Networks: An Examination and State-of-the-Art Review. J. Netw. Comput. Appl. 2020, 149, 102471. [Google Scholar] [CrossRef]
- Chen, J.; Micali, S. Algorand. Available online: https://arxiv.org/abs/1607.01341v9 (accessed on 11 October 2023).
- Silvano, W.F.; Marcelino, R. Iota Tangle: A Cryptocurrency to Communicate Internet-of-Things Data. Future Gener. Comput. Syst. 2020, 112, 307–319. [Google Scholar] [CrossRef]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A Survey on the Security of Blockchain Systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, L.; Ruan, W.; Hu, J.; He, Y. A Survey on Blockchain-Based Federated Learning. Future Internet 2023, 15, 400. https://doi.org/10.3390/fi15120400
Wu L, Ruan W, Hu J, He Y. A Survey on Blockchain-Based Federated Learning. Future Internet. 2023; 15(12):400. https://doi.org/10.3390/fi15120400
Chicago/Turabian StyleWu, Lang, Weijian Ruan, Jinhui Hu, and Yaobin He. 2023. "A Survey on Blockchain-Based Federated Learning" Future Internet 15, no. 12: 400. https://doi.org/10.3390/fi15120400
APA StyleWu, L., Ruan, W., Hu, J., & He, Y. (2023). A Survey on Blockchain-Based Federated Learning. Future Internet, 15(12), 400. https://doi.org/10.3390/fi15120400




