Distributed Denial of Service Classification for Software-Defined Networking Using Grammatical Evolution
Abstract
:1. Introduction
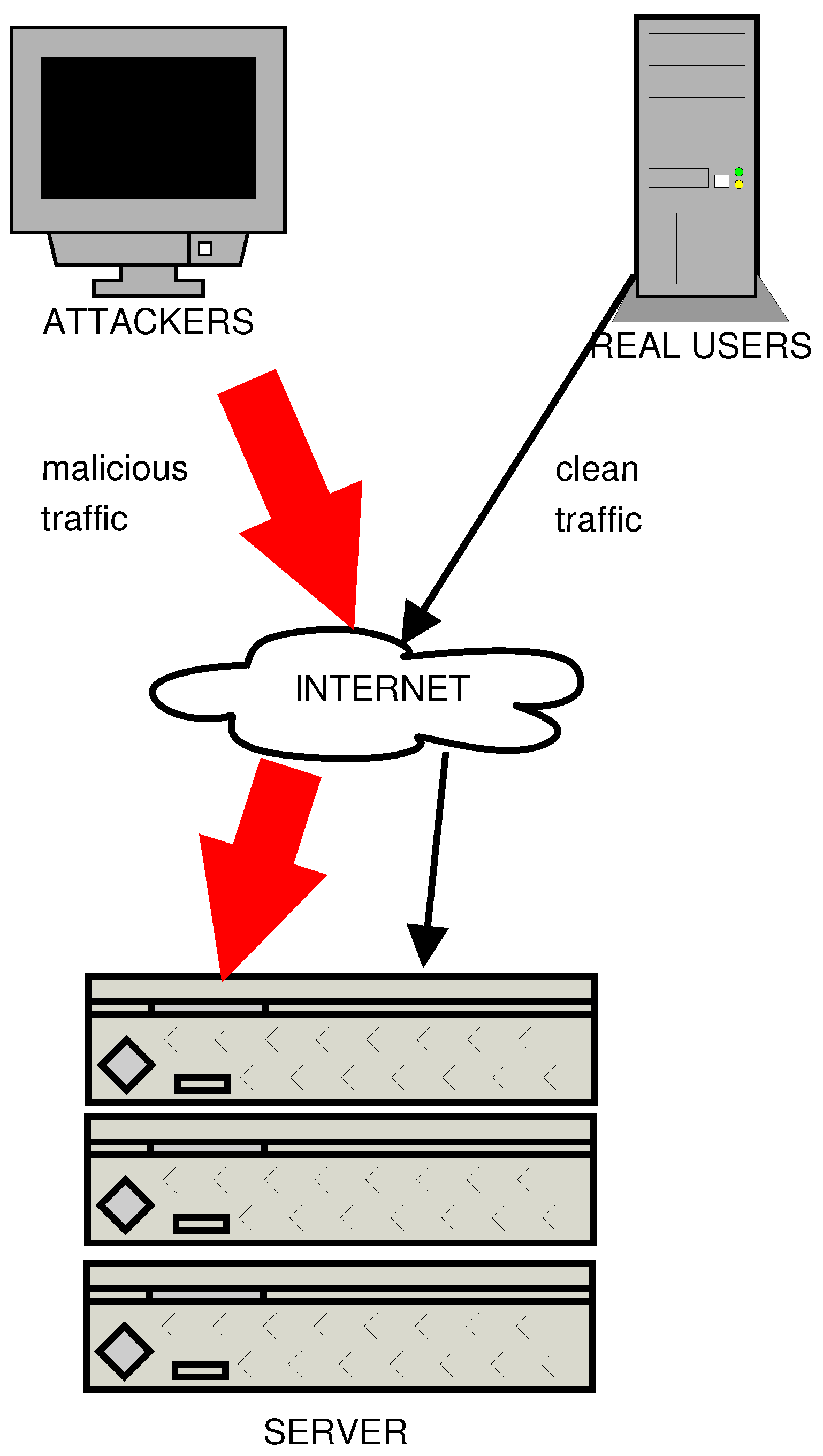
1.1. Motivation
1.2. Contributions
- Initially, we compare GenClass with three classification methods, namely the Bayes, K-Nearest Neighbors (KNN), and Random Forest methods, and demonstrate that our solution improves the average class error as opposed to the competitors.
- We encapsulate three methods based on grammatical evolution and show that GenClass exhibits a lower average class error than NNC and FC2GEN.
- We demonstrate that the three grammatical evolution methods exhibit low average class error values.
2. Related Work
Brief Comparison
3. Proposed Approach
3.1. Reference Architecture and Problem Statement
3.2. Proposed Methodologies
3.2.1. GenClass
3.2.2. Neural Network Construction (NNC)
3.2.3. FC2GEN
| Algorithm 1 GenClass algorithm |
|
| Algorithm 2 NNC algorithm |
|
| Algorithm 3 FC2GEN algorithm |
|
4. Performance Evaluation
4.1. Simulation Setup and Metrics
4.2. Experimental Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Jammal, M.; Singh, T.; Shami, A.; Asal, R.; Li, Y. Software defined networking: State of the art and research challenges. Comput. Netw. 2014, 72, 74–98. [Google Scholar] [CrossRef]
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A survey on software-defined networking. IEEE Commun. Surv. Tutor. 2014, 17, 27–51. [Google Scholar] [CrossRef]
- Chica, J.C.C.; Imbachi, J.C.; Vega, J.F.B. Security in SDN: A comprehensive survey. J. Netw. Comput. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Kanagavelu, R.; Aung, K.M.M. A survey on sdn based security in internet of things. In Advances in Information and Communication Networks, Proceedings of the 2018 Future of Information and Communication Conference (FICC), Singapore, 5–6 April 2018; Springer: Cham, Switzerland, 2019; Volume 2, pp. 563–577. [Google Scholar]
- Mirkovic, J.; Reiher, P. A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 39–53. [Google Scholar] [CrossRef]
- Galeano-Brajones, J.; Carmona-Murillo, J.; Valenzuela-Valdés, J.F.; Luna-Valero, F. Detection and mitigation of DoS and DDoS attacks in IoT-based stateful SDN: An experimental approach. Sensors 2020, 20, 816. [Google Scholar] [CrossRef]
- Shah, Z.; Ullah, I.; Li, H.; Levula, A.; Khurshid, K. Blockchain based solutions to mitigate distributed denial of service (DDoS) attacks in the Internet of Things (IoT): A survey. Sensors 2022, 22, 1094. [Google Scholar] [CrossRef] [PubMed]
- Adedeji, K.B.; Abu-Mahfouz, A.M.; Kurien, A.M. DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges. J. Sens. Actuator Netw. 2023, 12, 51. [Google Scholar] [CrossRef]
- Cui, Y.; Qian, Q.; Guo, C.; Shen, G.; Tian, Y.; Xing, H.; Yan, L. Towards DDoS detection mechanisms in software-defined networking. J. Netw. Comput. Appl. 2021, 190, 103156. [Google Scholar] [CrossRef]
- Santos, R.; Souza, D.; Santo, W.; Ribeiro, A.; Moreno, E. Machine learning algorithms to detect DDoS attacks in SDN. Concurr. Comput. Pract. Exp. 2020, 32, e5402. [Google Scholar] [CrossRef]
- Singh, M.P.; Bhandari, A. New-flow based DDoS attacks in SDN: Taxonomy, rationales, and research challenges. Comput. Commun. 2020, 154, 509–527. [Google Scholar] [CrossRef]
- Bawany, N.Z.; Shamsi, J.A.; Salah, K. DDoS attack detection and mitigation using SDN: Methods, practices, and solutions. Arab. J. Sci. Eng. 2017, 42, 425–441. [Google Scholar] [CrossRef]
- Javanmardi, S.; Shojafar, M.; Mohammadi, R.; Persico, V.; Pescapè, A. S-FoS: A secure workflow scheduling approach for performance optimization in SDN-based IoT-Fog networks. J. Inf. Secur. Appl. 2023, 72, 103404. [Google Scholar] [CrossRef]
- Javanmardi, S.; Shojafar, M.; Mohammadi, R.; Nazari, A.; Persico, V.; Pescapè, A. FUPE: A security driven task scheduling approach for SDN-based IoT–Fog networks. J. Inf. Secur. Appl. 2021, 60, 102853. [Google Scholar] [CrossRef]
- Wang, S.; Gomez, K.; Sithamparanathan, K.; Asghar, M.R.; Russello, G.; Zanna, P. Mitigating ddos attacks in sdn-based iot networks leveraging secure control and data plane algorithm. Appl. Sci. 2021, 11, 929. [Google Scholar] [CrossRef]
- Farris, I.; Taleb, T.; Khettab, Y.; Song, J. A survey on emerging SDN and NFV security mechanisms for IoT systems. IEEE Commun. Surv. Tutor. 2018, 21, 812–837. [Google Scholar] [CrossRef]
- O’Neill, M.; Ryan, C. Grammatical evolution. IEEE Trans. Evol. Comput. 2001, 5, 349–358. [Google Scholar] [CrossRef]
- O’Neill, M.; Brabazon, A.; Ryan, C.; Collins, J. Evolving market index trading rules using grammatical evolution. In Proceedings of the Applications of Evolutionary Computing: EvoWorkshops 2001: EvoCOP, EvoFlight, EvoIASP, EvoLearn, and EvoSTIM, Como, Italy, 18–20 April 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 343–352. [Google Scholar]
- Yang, L.; Zhao, H. DDoS attack identification and defense using SDN based on machine learning method. In Proceedings of the 2018 15th International Symposium on Pervasive Systems, Algorithms and Networks (I-SPAN), Yichang, China, 16–18 October 2018; pp. 174–178. [Google Scholar]
- Rahman, O.; Quraishi, M.A.G.; Lung, C.H. DDoS attacks detection and mitigation in SDN using machine learning. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; Volume 2642, pp. 184–189. [Google Scholar]
- Sahoo, K.S.; Iqbal, A.; Maiti, P.; Sahoo, B. A machine learning approach for predicting DDoS traffic in software defined networks. In Proceedings of the 2018 International Conference on Information Technology (ICIT), Bhubaneswar, India, 20–22 December 2018; pp. 199–203. [Google Scholar]
- Mohammed, S.S.; Hussain, R.; Senko, O.; Bimaganbetov, B.; Lee, J.; Hussain, F.; Kerrache, C.A.; Barka, E.; Bhuiyan, M.Z.A. A new machine learning-based collaborative DDoS mitigation mechanism in software-defined network. In Proceedings of the 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Limassol, Cyprus, 15–17 October 2018; pp. 1–8. [Google Scholar]
- Alhijawi, B.; Almajali, S.; Elgala, H.; Salameh, H.B.; Ayyash, M. A survey on DoS/DDoS mitigation techniques in SDNs: Classification, comparison, solutions, testing tools and datasets. Comput. Electr. Eng. 2022, 99, 107706. [Google Scholar] [CrossRef]
- Singh, J.; Behal, S. Detection and mitigation of DDoS attacks in SDN: A comprehensive review, research challenges and future directions. Comput. Sci. Rev. 2020, 37, 100279. [Google Scholar] [CrossRef]
- Mousavi, S.M.; St-Hilaire, M. Early detection of DDoS attacks against SDN controllers. In Proceedings of the 2015 International Conference on Computing, Networking and Communications (ICNC), Anaheim, CA, USA, 16–19 February 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 77–81. [Google Scholar]
- Banitalebi Dehkordi, A.; Soltanaghaei, M.; Boroujeni, F.Z. The DDoS attacks detection through machine learning and statistical methods in SDN. J. Supercomput. 2021, 77, 2383–2415. [Google Scholar] [CrossRef]
- Ali, T.E.; Chong, Y.W.; Manickam, S. Machine Learning Techniques to Detect a DDoS Attack in SDN: A Systematic Review. Appl. Sci. 2023, 13, 3183. [Google Scholar] [CrossRef]
- Cui, J.; Wang, M.; Luo, Y.; Zhong, H. DDoS detection and defense mechanism based on cognitive-inspired computing in SDN. Future Gener. Comput. Syst. 2019, 97, 275–283. [Google Scholar] [CrossRef]
- Tonkal, Ö.; Polat, H.; Başaran, E.; Cömert, Z.; Kocaoğlu, R. Machine learning approach equipped with neighbourhood component analysis for DDoS attack detection in software-defined networking. Electronics 2021, 10, 1227. [Google Scholar] [CrossRef]
- Tsoulos, I.G. Creating classification rules using grammatical evolution. Int. J. Comput. Intell. Stud. 2020, 9, 161–171. [Google Scholar]
- Anastasopoulos, N.; Tsoulos, I.G.; Tzallas, A. GenClass: A parallel tool for data classification based on Grammatical Evolution. SoftwareX 2021, 16, 100830. [Google Scholar] [CrossRef]
- Tsoulos, I.; Gavrilis, D.; Glavas, E. Neural network construction and training using grammatical evolution. Neurocomputing 2008, 72, 269–277. [Google Scholar] [CrossRef]
- Gavrilis, D.; Tsoulos, I.G.; Dermatas, E. Selecting and constructing features using grammatical evolution. Pattern Recognit. Lett. 2008, 29, 1358–1365. [Google Scholar] [CrossRef]
- Ahuja, N.; Singal, G.; Mukhopadhyay, D. DDOS attack SDN Dataset. J. Netw. Comput. Appl. 2020. [Google Scholar] [CrossRef]
- Ramadhan, I.; Sukarno, P.; Nugroho, M.A. Comparative analysis of K-nearest neighbor and decision tree in detecting distributed denial of service. In Proceedings of the 2020 8th International Conference on Information and Communication Technology (ICoICT), Yogyakarta, Indonesia, 24–26 June 2020; Volume 1–4. [Google Scholar]
- Kachavimath, A.V.; Nazare, S.V.; Akki, S.S. Distributed denial of service attack detection using naïve bayes and k-nearest neighbor for network forensics. In Proceedings of the 2020 2nd International conference on innovative mechanisms for industry applications (ICIMIA), Bangalore, India, 5–7 March 2020; pp. 711–717. [Google Scholar]
- Dong, S.; Sarem, M. DDoS attack detection method based on improved KNN with the degree of DDoS attack in software-defined networks. IEEE Access 2019, 8, 5039–5048. [Google Scholar] [CrossRef]
- Idhammad, M.; Afdel, K.; Belouch, M. Detection system of HTTP DDoS attacks in a cloud environment based on information theoretic entropy and random forest. Secur. Commun. Netw. 2018, 2018, 1263123. [Google Scholar] [CrossRef]
- Chen, Y.; Hou, J.; Li, Q.; Long, H. DDoS attack detection based on random forest. In Proceedings of the 2020 IEEE International Conference on Progress in Informatics and Computing (PIC), Shanghai, China, 18–20 December 2020; pp. 328–334. [Google Scholar]
- Najar, A.A.; Manohar Naik, S. DDoS attack detection using MLP and Random Forest Algorithms. Int. J. Inf. Technol. 2022, 14, 2317–2327. [Google Scholar] [CrossRef]
- López, J.; Maña, A.; Muñoz, A. A secure and auto-configurable environment for mobile agents in ubiquitous computing scenarios. In Proceedings of the International Conference on Ubiquitous Intelligence and Computing, Wuhan, China, 3–6 September 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 977–987. [Google Scholar]
- Sánchez-Cid, F.; Mana, A.; Spanoudakis, G.; Kloukinas, C.; Serrano, D.; Munoz, A. Representation of security and dependability solutions. In Security and Dependability for Ambient Intelligence; Springer: Boston, MA, USA, 2009; pp. 69–95. [Google Scholar]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Spyrou, E.D.; Tsoulos, I.; Stylios, C. Distributed Denial of Service Classification for Software-Defined Networking Using Grammatical Evolution. Future Internet 2023, 15, 401. https://doi.org/10.3390/fi15120401
Spyrou ED, Tsoulos I, Stylios C. Distributed Denial of Service Classification for Software-Defined Networking Using Grammatical Evolution. Future Internet. 2023; 15(12):401. https://doi.org/10.3390/fi15120401
Chicago/Turabian StyleSpyrou, Evangelos D., Ioannis Tsoulos, and Chrysostomos Stylios. 2023. "Distributed Denial of Service Classification for Software-Defined Networking Using Grammatical Evolution" Future Internet 15, no. 12: 401. https://doi.org/10.3390/fi15120401
APA StyleSpyrou, E. D., Tsoulos, I., & Stylios, C. (2023). Distributed Denial of Service Classification for Software-Defined Networking Using Grammatical Evolution. Future Internet, 15(12), 401. https://doi.org/10.3390/fi15120401







