PlugID: A Platform for Authenticated Energy Consumption to Enhance Accountability and Efficiency in Smart Buildings
Abstract
1. Introduction
2. The State of the Art in Smart Energy Management
2.1. Energy Monitoring Paradigms: ILM vs. NILM
2.2. IoT Platforms for Energy Management
2.3. Access Control for IoT Resources
- Discretionary Access Control (DAC): In this model, the owner of a resource defines access permissions. Its static nature and the need for manual management of access control lists (ACLs) make it unsuitable for dynamic and large-scale IoT environments.
- Role-Based Access Control (RBAC): RBAC grants permissions based on roles assigned to users. While it simplifies administration in some contexts, it faces the problem of “role explosion” in heterogeneous IoT ecosystems and has difficulty supporting the necessary dynamism.
- Attribute-Based Access Control (ABAC): ABAC is widely considered the most promising model for IoT [11]. It makes access decisions based on policies that evaluate a combination of attributes of the subject (user/device), object (resource), action, and environment (location, time of day). This flexibility allows for the creation of rich, dynamic, and context-sensitive access policies.
2.4. Security and Privacy in Smart Metering Systems
3. The PlugID Platform for Authenticated Energy Consumption
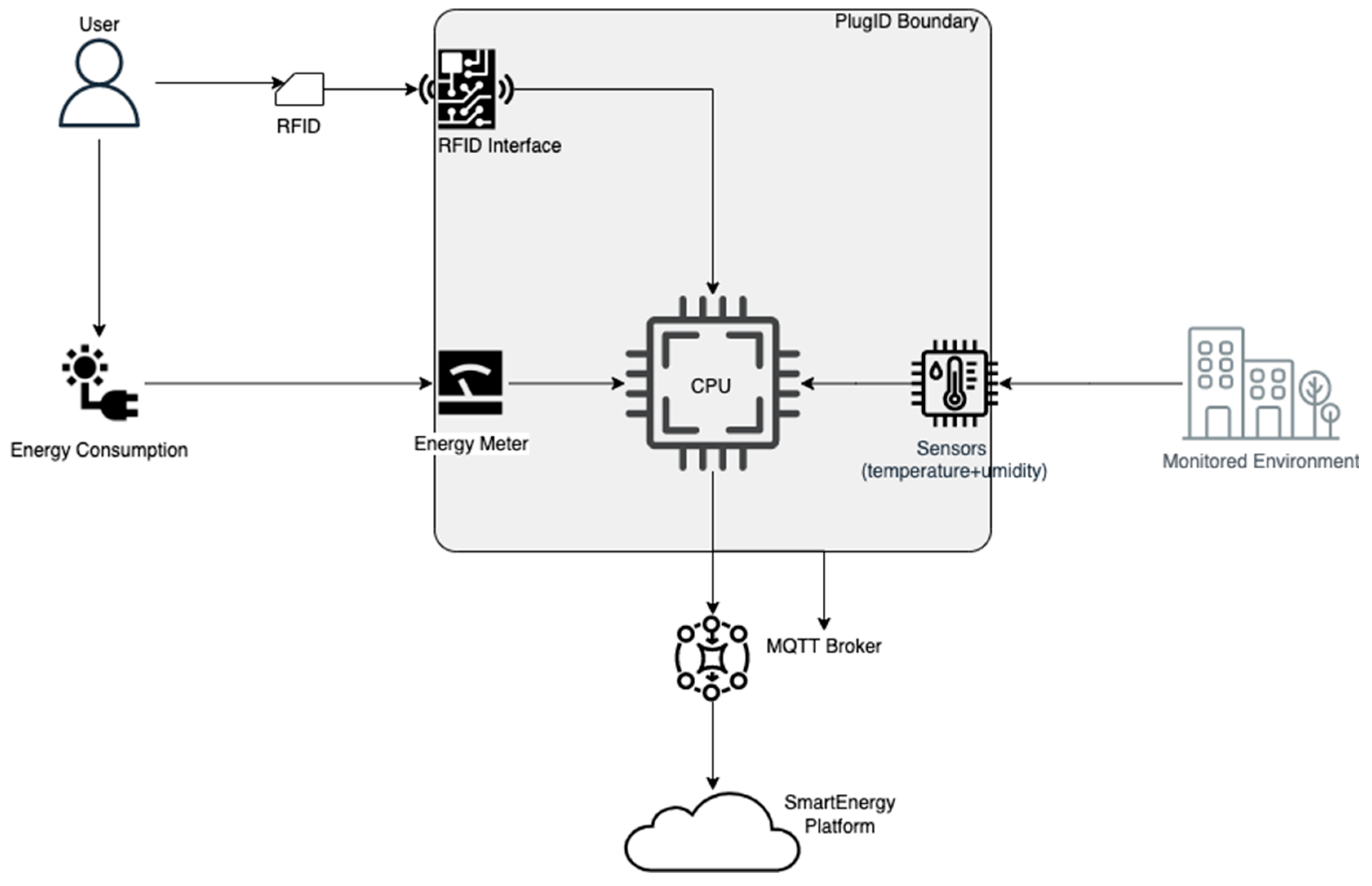
3.1. System Architecture
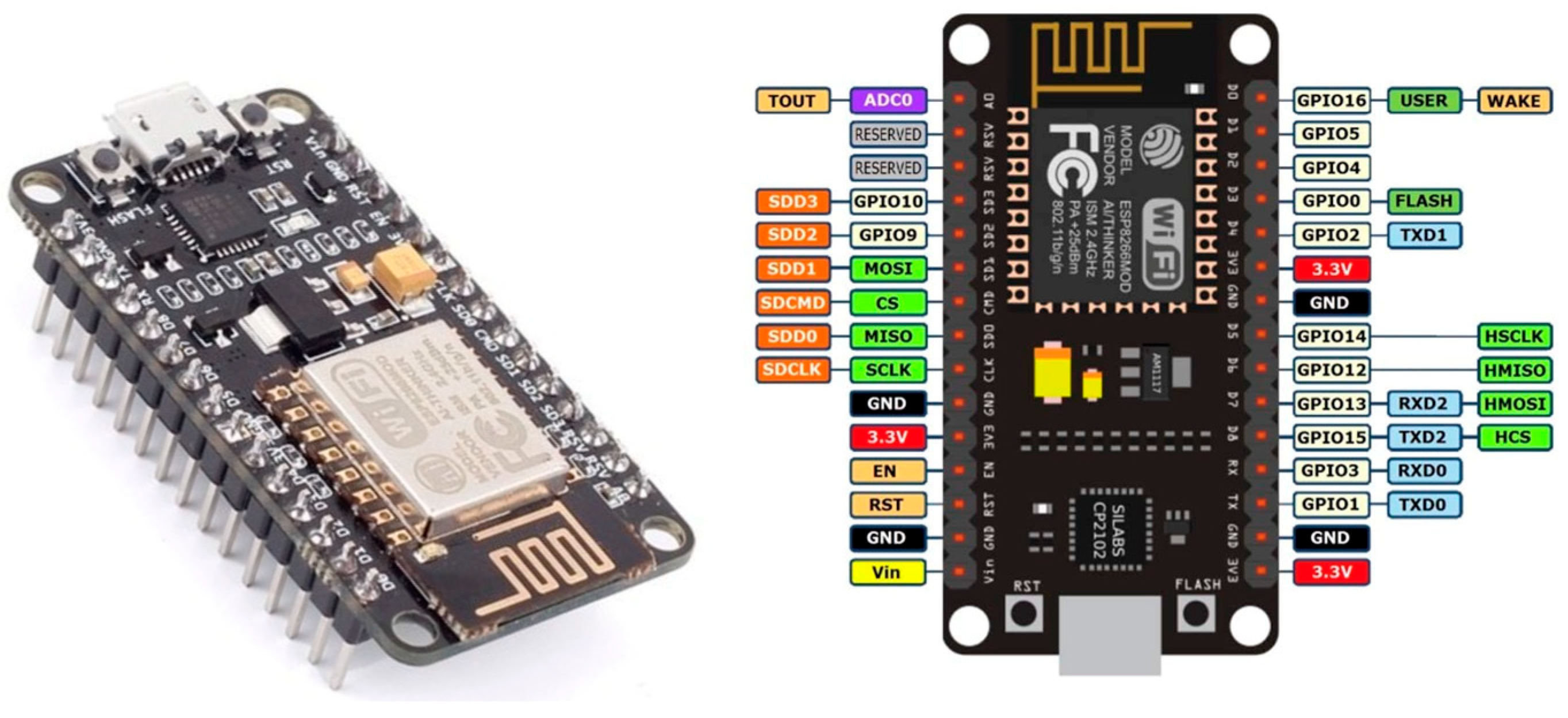
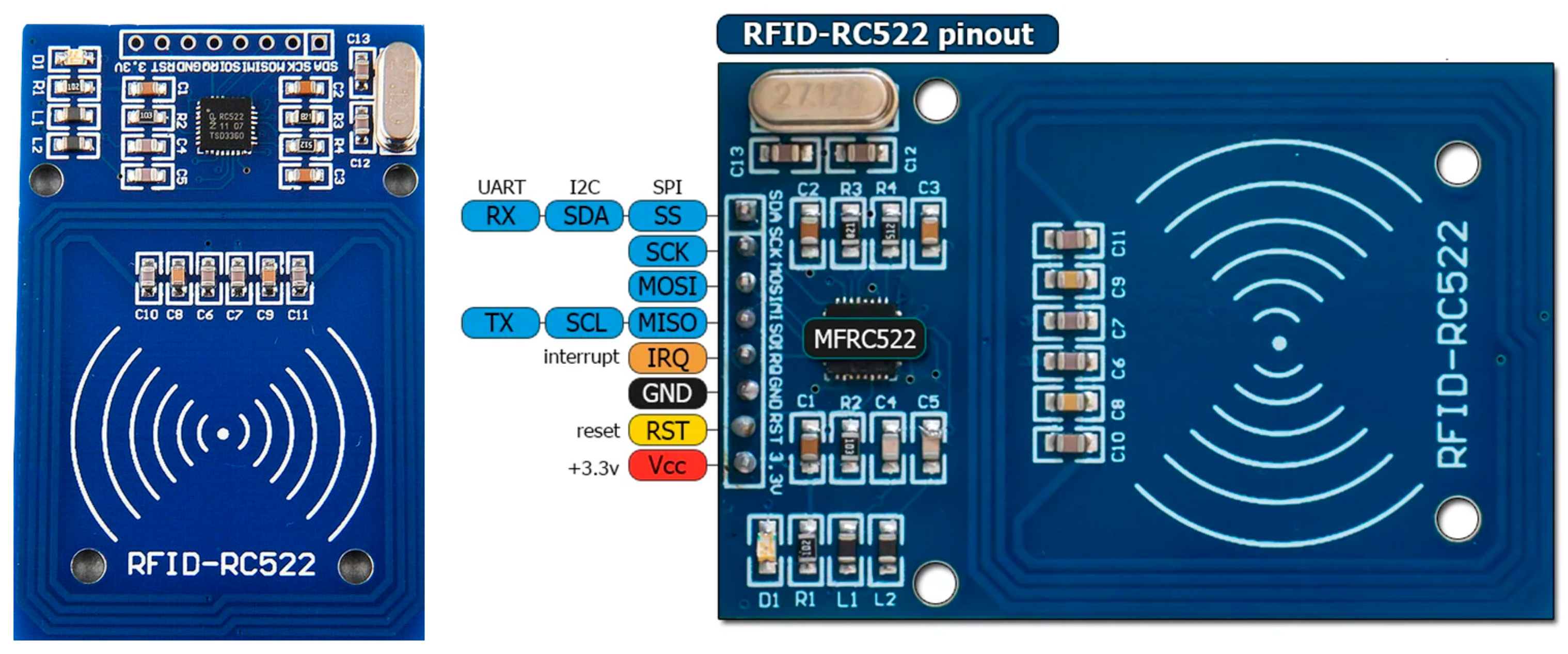
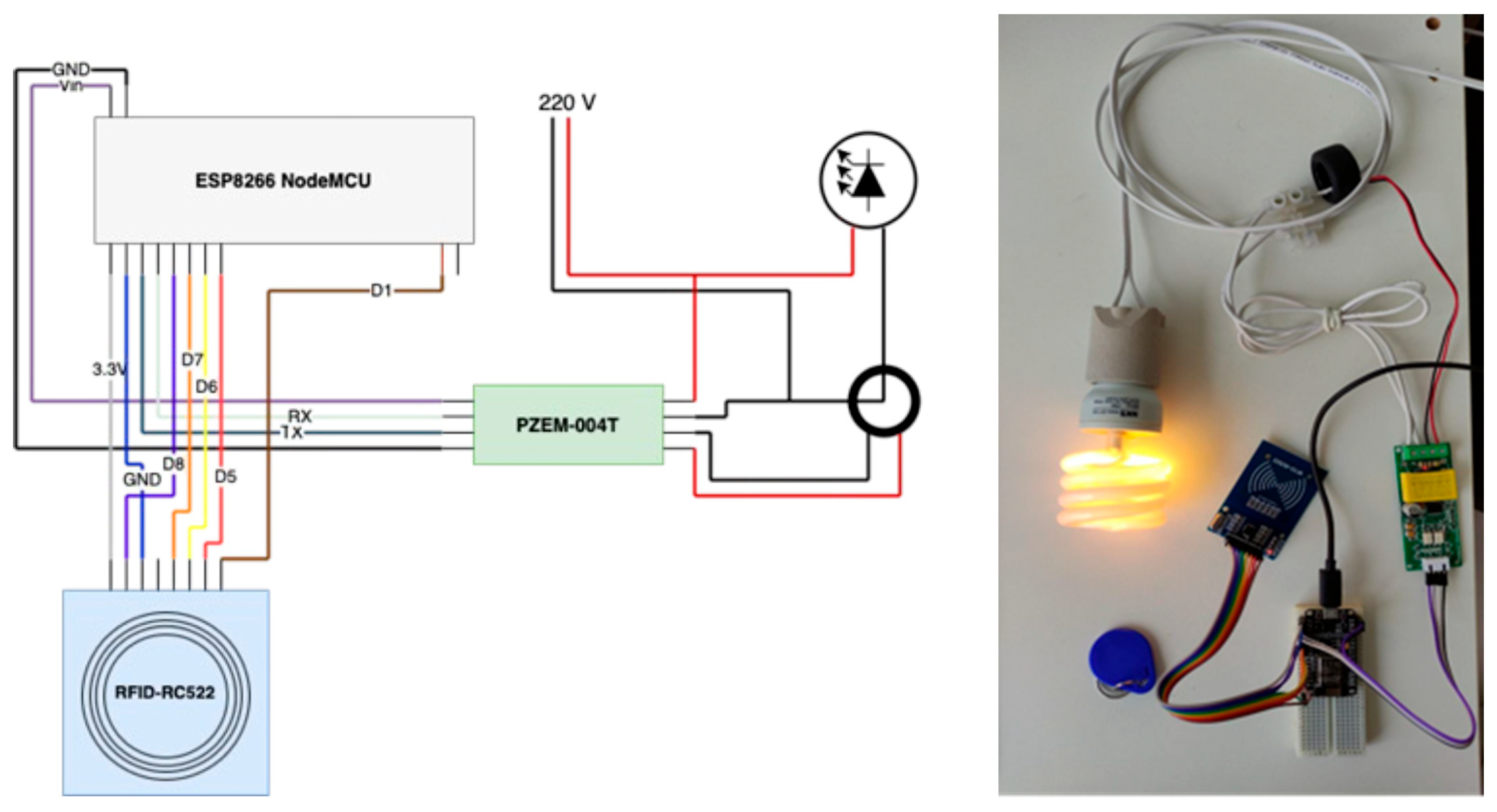
3.2. The PlugID Device: Hardware and Firmware
- Rule1: This set of rules handles periodic and initialization events. One rule is triggered on system startup to obtain and store the device’s MAC address, which serves as a unique identifier. Another rule is triggered periodically (every teleperiod) to publish a status message via MQTT—containing the MAC—an authentication capability indicator (TokenAuth), and the UID of the currently logged-in user (if any).
- Rule2: This set is dedicated to the RFID authentication logic. It is triggered by read events from the RC522 module. When a card is brought near, the rule checks if a session is already active. If not, it stores the card’s UID, starts a new session, and triggers an LED for visual feedback. If a session is already active, the rule checks if the presented card’s UID is the same as the current session’s. If so, the session is terminated. Cards with different UIDs are ignored while a session is active.
3.3. Secure Communication and Data Model
4. Case Study
4.1. Implementation of Hardware, Firmware, and Software
- Possibility of high granularity in the temporal aspect of energy consumption monitoring;
- Ease of connection to electrical outlets and circuits typical of homes and offices;
- Ability to identify the user responsible for energy consumption at each instant of time;
- Interoperability without relying on specific software applications to access consumer data.
4.2. Deployment Scenario
- PlugID-E/AT (with authentication): Installed at shared workstations, where multiple employees could use the same computer at different times. RFID authentication was necessary to attribute consumption to the correct user.
- PlugID-E (without authentication): Used at fixed workstations, assigned to a single individual, where continuous authentication was considered unnecessary for the proof of concept.
- PlugID-ETH (with environmental sensor): Positioned in key locations to collect temperature and humidity data, allowing for the correlation between environmental conditions and energy consumption, especially of the air conditioning system.
4.3. Data Collection and Visualization
- Tasmota Web Console: Each PlugID device offers a local web interface for real-time configuration and monitoring. Figure 5 shows an example of this interface, with instantaneous readings of power, voltage, current, and, in applicable models, temperature, humidity, and the UID of the last RFID session.
- MQTT Broker: On the server, raw data arrived as JSON messages, as per the examples in Table 3. This confirmed the correct data flow and proper formatting.
- SmartEnergy Platform (Kibana): The data ingested and stored in Elasticsearch was used to create interactive dashboards in Kibana. These dashboards, as exemplified in Figure 6, allowed for the visualization of energy consumption time series, the correlation of consumption peaks with authenticated user sessions, and the analysis of the impact of environmental factors on energy use.
- To analyze energy consumption data;
- To implement energy consumption policies.
4.4. Proof of Concept: Enabling Granular Energy Policies
- Accountability Scenario: An office manager observes, through the SmartEnergy dashboard, a spike in energy consumption at a shared workstation over the weekend. Traditional aggregated consumption would only flag the event. With the PlugID platform, the manager can cross-reference the timestamp of the consumption peak with the RFID session logs. The system reveals that UID “9996E8B8” was logged in at that time, allowing the manager to identify the responsible user and initiate a targeted conversation about the policy for using equipment outside of working hours. This transforms an anonymous problem into a matter of personal responsibility.
- Active Access Control Scenario: Based on the collected data, which shows a pattern of equipment being left on overnight, the company decides to implement a more active energy policy. Using the control capabilities of the PlugID (via its internal relay), a rule is configured on the SmartEnergy platform: all workstation outlets are automatically de-energized at 8:00 PM. Access after this time is only permitted if the user authenticates with an RFID token associated with a profile that has “after-hours access” privileges. This scenario demonstrates the transition from passive monitoring to active and dynamic access control, a key feature of advanced energy management systems.
5. Discussion
5.1. The Impact of Authentication on Energy-Related Behavior
5.2. Security and Privacy Analysis of the PlugID Platform
5.3. Limitations and Future Directions
- Scale: The deployment served as a functional proof of concept in a real-world office setting, but was limited in scale (seven devices in a single office) and duration. The scalability of the platform, both in terms of device management and data processing, was not tested in a large-scale deployment.
- Duration: The data collection period was relatively short, which prevents the extraction of statistically significant conclusions about long-term behavioral changes.
- Focus: The main objective of the project was the development and validation of the technological tool (the PlugID platform), rather than conducting a formal study of energy efficiency or behavior.
- Longitudinal Behavioral Study: Conduct a large-scale, long-term deployment in different types of environments (e.g., offices, university labs, co-working spaces) to quantitatively measure the impact of authenticated consumption on energy savings and behavioral change.
- Enhanced Authentication: Integrate alternative and more secure authentication factors to overcome the limitations of RFID. This could include PINs entered on an attached keypad, biometric authentication, or, more pragmatically, authentication based on smartphone apps (via Bluetooth Low Energy or Wi-Fi).
- Advanced ABAC Policies: Develop and implement more complex, attribute-based energy access control policies on the SmartEnergy platform. For example, policies that grant different energy quotas to different user roles or that dynamically adjust access based on the time of day and the cost of grid energy.
- Integration with Building Management Systems (BMS): Explore the integration of the PlugID platform with existing commercial BMS. This would allow authenticated consumption data at the outlet level to be correlated with data from centralized systems (like HVAC and lighting), providing a truly holistic view of the building’s energy use.
- Addressing Shared Loads: This study focused on attributing consumption from discrete, user-specific loads. A significant challenge remains in attributing shared loads like central lighting or refrigerators. Future work could explore hybrid models where PlugID data is combined with occupancy data or organizational policies to allocate the consumption of these shared resources, which were monitored but not attributed in this study.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ABAC | Attribute-Based Access Control |
| ACL | Access Control List |
| ADC | Analog-to-Digital Converter |
| BMS | Building Management System |
| CA | Certificate Authority |
| DAC | Discretionary Access Control |
| DoS | Denial of Service |
| ESP | Espressif Systems Platform |
| ETH | Environmental Temperature and Humidity (PlugID variant) |
| FDI | False Data Injection |
| GPIO | General-Purpose Input/Output |
| HVAC | Heating, Ventilation, and Air Conditioning |
| ILM | Intrusive Load Monitoring |
| IoT | Internet of Things |
| JSON | JavaScript Object Notation |
| MAC | Media Access Control (Address) |
| MFA | Multi-Factor Authentication |
| MQTT | Message Queuing Telemetry Transport |
| NILM | Non-Intrusive Load Monitoring |
| OTA | Over-The-Air (Firmware Update) |
| PUF | Physical Unclonable Function |
| RBAC | Role-Based Access Control |
| RFID | Radio-Frequency Identification |
| SPI | Serial Peripheral Interface |
| TLS | Transport Layer Security |
| UID | Unique Identifier |
References
- Poyyamozhi, M.; Murugesan, B.; Rajamanickam, N.; Shorfuzzaman, M.; Aboelmagd, Y. IoT—A Promising Solution to Energy Management in Smart Buildings: A Systematic Review, Applications, Barriers, and Future Scope. Buildings 2024, 14, 3446. [Google Scholar] [CrossRef]
- Pu, Z.; Huang, Y.; Weng, M.; Meng, Y.; Zhao, Y.; He, G. Enhancing non-intrusive load monitoring with weather and calendar feature integration in DAE. Front. Energy Res. 2024, 12, 1361916. [Google Scholar] [CrossRef]
- Zhao, Q.; Liu, W.; Li, K.; Wei, Y.; Han, Y. Unknown appliances detection for non-intrusive load monitoring based on vision transformer with an additional detection head. Heliyon 2024, 10, e30666. [Google Scholar] [CrossRef] [PubMed]
- Mensah, N.K.; Abdel-Fatao, H.; Yao, Y.; Ziggah, Y.Y.; Nunoo, S. An Effective Non-Intrusive Load Monitoring (NILM) for Residential Appliances using Wavelet Transform and Clustering. Int. J. Comput. Appl. 2024, 186, 975–8887. [Google Scholar]
- Shabbir, N.; Vassiljeva, K.; Nourollahi Hokmabad, H.; Husev, O.; Petlenkov, E.; Belikov, J. Comparative Analysis of Machine Learning Techniques for Non-Intrusive Load Monitoring. Electronics 2024, 13, 1420. [Google Scholar] [CrossRef]
- Condon, F.; Martínez, J.M.; Eltamaly, A.M.; Kim, Y.C.; Ahmed, M.A. Design and Implementation of a Cloud-IoT-Based Home Energy Management System. Sensors 2022, 23, 176. [Google Scholar] [CrossRef] [PubMed]
- Ahsan, M.S.; Pathan, A.-S.K. A Comprehensive Survey on the Requirements, Applications, and Future Challenges for Access Control Models in IoT: The State of the Art. IoT 2025, 6, 9. [Google Scholar] [CrossRef]
- Almarri, S.; Frikha, M. Authentication and Access Control Mechanisms to Secure IoT Environments: A comprehensive SLR. Preprints 2024, 2024050948. [Google Scholar] [CrossRef]
- Ali, S.; Sabir, S.; Ullah, Z. Internet of Things Security, Device Authentication and Access Control: A Review. Available online: https://www.researchgate.net/publication/383214250_Internet_of_Things_Security_Device_Authentication_and_Access_Control_A_Review (accessed on 22 June 2025).
- Ragothaman, K.; Wang, Y.; Rimal, B.; Lawrence, M. Access Control for IoT: A Survey of Existing Research, Dynamic Policies and Future Directions. Sensors 2023, 23, 1805. [Google Scholar] [CrossRef] [PubMed]
- Nambundo, J.M.; de Souza Martins Gomes, O.; de Souza, A.D.; Machado, R.C.S. Cybersecurity and Major Cyber Threats of Smart Meters: A Systematic Mapping Review. Energies 2025, 18, 1445. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Fouda, M.M.; Emran, A.; Fadlullah, Z.M.; Ibrahem, M.I. A Survey on Key Management and Authentication Approaches in Smart Metering Systems. Energies 2023, 16, 2355. [Google Scholar] [CrossRef]
- Tufail, S.; Parvez, I.; Batool, S.; Sarwat, A. A Survey on Cybersecurity Challenges, Detection, and Mitigation Techniques for the Smart Grid. Energies 2021, 14, 5894. [Google Scholar] [CrossRef]
- Kua, J.; Hossain, M.B.; Natgunanathan, I.; Xiang, Y. Privacy Preservation in Smart Meters: Current Status, Challenges and Future Directions. Sensors 2023, 23, 3697. [Google Scholar] [CrossRef] [PubMed]
- Zhang, X.-Y.; Kuenzel, S.; Córdoba-Pachón, J.-R.; Watkins, C. Privacy-Functionality Trade-Off: A Privacy-Preserving Multi-Channel Smart Metering System. Energies 2020, 13, 3221. [Google Scholar] [CrossRef]
- Díaz Redondo, R.P.; Fernández-Vilas, A.; Fernández dos Reis, G. Security Aspects in Smart Meters: Analysis and Prevention. Sensors 2020, 20, 3977. [Google Scholar] [CrossRef] [PubMed]





| Feature | Intrusive Load Monitoring (ILM) | Non-Intrusive Load Monitoring (NILM) | PlugID (Authenticated ILM) |
|---|---|---|---|
| Accuracy | High (>99%) | Variable (typically 80–95%) 1 | High (>99%) |
| Installation Cost | High (>USD 100 per point) | Low (<USD 10 per building) 1 | Moderate (~USD 50 per point) 2 |
| Installation Complexity | High (may require wiring changes) | Low (single meter) | Moderate (plug-and-play) |
| Maintenance | Difficult (distributed sensors) | Easy (centralized) | Easy (per device) |
| Privacy | Invasive (detailed appliance data) | Preserved (aggregated data) | Requires data governance policies |
| Granularity (Appliance Level) | Yes | Yes (inferred) | Yes |
| Granularity (User Level) | No | No | Yes (main feature) |
| Component | Model | Key Specifications | Rationale for Selection |
|---|---|---|---|
| Microcontroller | ESP8266 NodeMCU v2-ESP12 | Integrated Wi-Fi, 11 GPIO pins, analog-to-digital converter | Low cost, wide availability, active development community, sufficient processing power for the application. |
| Energy Measurement Module | PZEM-004T | AC voltage measurement, current (up to 100 A), power. Serial communication. | Indirect measurement via current coil (non-invasive), ease of integration, and simple data interface. |
| Authentication Module | MFRC522 RFID Reader | 13.56 MHz frequency, supports MIFARE cards, SPI interface. | Market standard for token-based authentication, low cost, and mature software libraries. |
| Power Supply | Mini Hi-link 5 V Power Supply | Bivolt input (100–240 VAC), 5 VDC output. | Compact and sealed, allows powering the circuit directly from the electrical outlet safely. |
| Environmental Sensor (ETH Model) | AM2302/DHT22 | Temperature and humidity measurement. | Allows correlation between energy consumption and environmental conditions, aiding in deeper efficiency analyses. |
| Model | Example JSON Data Payload |
|---|---|
| PlugID-E | {“Time”:”2021-07-27T17:35:42”, “ENERGY”:{“Total”:0.008, “Power”:12, “Voltage”:128, “Current”:0.168}} |
| PlugID-E/AT | {“Time”:”2021-07-27T18:08:29”, “ENERGY”:{“Power”:55, “Voltage”:127, “Current”:0.481}, “RC522”:{“UID”:”9996E8B8”, “Type”:”MIFARE 1KB”}} |
| PlugID-ETH | {“Time”:”2021-07-27T17:35:42”, “ENERGY”:{“Power”:45, “Voltage”:128, “Current”:0.352}, “AM2301”:{“Temperature”:29.2, “Humidity”:48.5}, “TempUnit”:”C”, “RC522”:{“UID”:”9996E8B8”, “Type”:”MIFARE 1KB”}} |
| SM-3W Lite (AC) | {“variable”:”PT”, “value”:79.33, “unit”:”W”} {“variable”:”IA”, “value”:6.92, “unit”:”A”} |
| Threat Category | Specific Threat | Platform Vulnerability | Proposed Mitigation/Future Work |
|---|---|---|---|
| Communication Channel | Eavesdropping, Man-in-the-Middle | Interception of MQTT data in transit. | Implemented: Use of TLS to encrypt the MQTT channel, protecting data confidentiality and integrity. |
| Device Authentication | Spoofing Attack | Cloning of RFID cards to gain unauthorized access [13]. | Future Mitigation: For high-security environments, implement Multi-Factor Authentication (MFA). This could include requiring an RFID token plus a PIN entered on a keypad, or using more secure smartphone-based authentication methods (e.g., via Bluetooth Low Energy) to mitigate spoofing risks. |
| Physical Security | Node Tampering, Fake Node | An attacker with physical access can alter the PlugID’s hardware/firmware or replace it with a malicious device [10]. | Mitigation: Implement cabinets with physical security seals. Future Work: Investigate the use of Physical Unclonable Functions (PUFs) for hardware attestation. |
| Availability | Denial of Service (DoS) | The centralized MQTT broker is a single point of failure and can be targeted by flooding attacks [13]. | Future Mitigation: Implement load balancing and traffic filtering mechanisms. Investigate decentralized or federated broker architectures. |
| Data Privacy | Activity Inference | Granular and authenticated consumption data can be used to monitor employee activities in detail [15]. | Mitigation: Implement strict data governance policies with access control to raw data. Future Work: Develop privacy-preserving aggregation and anonymization techniques for less granular analyses. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Machado, R.; Pinheiro, L.; Santos, V.; Salgado, B. PlugID: A Platform for Authenticated Energy Consumption to Enhance Accountability and Efficiency in Smart Buildings. Energies 2025, 18, 5466. https://doi.org/10.3390/en18205466
Machado R, Pinheiro L, Santos V, Salgado B. PlugID: A Platform for Authenticated Energy Consumption to Enhance Accountability and Efficiency in Smart Buildings. Energies. 2025; 18(20):5466. https://doi.org/10.3390/en18205466
Chicago/Turabian StyleMachado, Raphael, Leonardo Pinheiro, Victor Santos, and Bruno Salgado. 2025. "PlugID: A Platform for Authenticated Energy Consumption to Enhance Accountability and Efficiency in Smart Buildings" Energies 18, no. 20: 5466. https://doi.org/10.3390/en18205466
APA StyleMachado, R., Pinheiro, L., Santos, V., & Salgado, B. (2025). PlugID: A Platform for Authenticated Energy Consumption to Enhance Accountability and Efficiency in Smart Buildings. Energies, 18(20), 5466. https://doi.org/10.3390/en18205466






