1. Introduction
The traditional distribution grid is shifting from a unidirectional electricity flow model to an active distribution grid with bidirectional electricity flow capabilities. This transition is driven by the imperative to address environmental, socioeconomic, and sustainability goals, resulting in a distribution grid with high penetration of the distributed energy resources (DERs) at the edge. These DERs facilitate the incorporation of diverse renewable energy sources into the primary grid through interfaces like synchronous generators, induction generators, and inverter-based resources. Notably, inverter-based DERs have gained considerable traction due to specific attributes, including improved power quality by minimizing harmonics, control of reactive power and voltage across a wide power factor range, and rapid responses for tasks like high-frequency regulation, quick switching, and fault isolation.
Inverter-based DERs present challenges despite their advantages [
1]. The first challenge involves system reliability, primarily stemming from the inherent uncertainty in renewable energy sources. Despite employing multiple forecasting methods to estimate inverter output, accurately predicting the variance between forecasted and actual values remains elusive. In networks with high penetration of DERs, this cumulative forecasting error can lead to significant reliability issues, particularly when reserve capacity is insufficient [
2]. The second challenge pertains to system stability. Inverter-based DERs have low inertia [
3], which can diminish the system stability margin. Consequently, disturbances that are typically manageable in traditional synchronous machine-dominated grids, such as load switches, system reconfiguration, and short-term faults, may provoke stability concerns in DER-dominated grids. This will sometimes result in large-scale blackouts. The third challenge revolves around system protection. Existing protection devices are primarily designed to respond to high-amplitude fault currents, a characteristic common in synchronized machines. However, fault currents in inverters are typically of smaller magnitude, potentially failing to activate protection devices promptly [
4]. Consequently, faults in inverters may not be promptly isolated, leading to voltage or frequency violations and potentially triggering cascade failures.
To overcome these challenges, an efficient communication network is essential for real-time monitoring and control of DERs. This network enables bidirectional data exchange, handles increased sensors and actuators, adapts to the complex topology of dispersed DERs, and allows third-party involvement for collaborative efforts among stakeholders, such as DER owners, manufacturers, and aggregators [
5].
Distribution grids incorporating a communication network for DER management and control manifest a cyberphysical system (CPS), which has significantly expanded the potential cyberattack surfaces [
6,
7,
8]. Slower safety mechanisms and protection devices behind the expanded cyber networks have made vulnerabilities easier to exploit. Moreover, the requirement to involve DER manufacturers, owners, and third parties can lead to incomplete or underdeveloped authorization and access protocols, posing a substantial risk to distribution network stability and reliability. Therefore, an extensive risk assessment framework becomes crucial for ensuring the cyberphysical security of distribution grids with grid-edge DERs.
A detailed CPS model embedded with the interdependency of cyber and physical elements is crucial for risk assessment, ensuring precise evaluation of the potential attacks’ impact [
9]. Simultaneously, calculating the likelihood of these attacks is equally important. Given the defense resources constraints, identifying the most frequent attacks becomes imperative. An accurate attack probability model guarantees the optimal selection of defensive strategies, thereby fortifying CPS resilience.
Several CPS risk assessment methods have been proposed. Some of them deploy conventional probability evaluation methods. For instance, [
10] introduced a cyber risk strategy focused on protection systems. This approach uses Monte Carlo methods to simulate compromised protection components, identifying cascade failures and load-shedding effects. Ref. [
11] introduced an attack graph-based method to evaluate the cyber risk of the cyberphysical power system. In [
12], authors used the stochastic game theory to model attacker and defender behaviors in order to assess cybersecurity risks. The works from [
13,
14] employed the Bayesian network to address CPS cyberphysical risks related to system vulnerabilities. Additionally, emerging learning-based methodologies have gained popularity in recent years. These methods, compared to conventional approaches, are more suited for large-scale system analysis. For instance, [
15] utilized deep reinforcement learning to find optimal network transition policies from the attacker’s perspective, evaluating potential attack impacts. Ref. [
16] presented a rank algorithm based on learning methods to achieve real-time risk evaluation. However, they typically necessitate large amounts of data for the training set, which can be challenging to collect in real-world scenarios, posing feasibility issues.
Nevertheless, these works in the literature are generally based on the steady-state model, which typically treats DER behavior as PV or PQ buses and overlooks crucial DER functionalities outlined in the IEEE 1547-2018 standard [
17], such as Volt-Var support and ride-through capabilities. Consequently, these works fail to capture the dynamic behavior of DERs, potentially leading to inaccurate results. Therefore, a comprehensive cyberphysical system (CPS) model incorporating dynamic DER behavior is essential for accurately assessing the potential impact of cyberattacks on DERs.
Moreover, current frameworks often oversimplify the communication layer by employing time-static models or treating potential cyberattacks merely as contingencies, assessing their impacts through contingency analysis. However, with the integration of inverter-based DERs, communication latency can significantly reduce the system stability region, especially in scenarios with high DER penetration [
18,
19]. This emphasizes the need to consider communication system latency for precise cyber risk assessment within such systems.
Furthermore, within the impact quantification, it is crucial to link the attack probability to both the “cost” (vulnerability) and “reward” (criticality) of a component. Previous studies have often focused on one of these aspects or assumed a fixed probability distribution for attack likelihood, which might not accurately reflect current attack patterns.
To address the aforementioned limitations, this work introduces a novel cyber risk assessment framework for active distribution grids with inverter-based DERs. The innovative steps within the proposed framework are as follows:
A DER-explicit distribution grid model accounting for dynamic attributes of inverter-based DERs.
A high-fidelity DER communication layer model with communication latency to facilitate the precise execution of cyber layer attacks.
A cyberattack risk quantification method based on an attack probability model that accounts for both cyber component vulnerability and criticality.
The paper structure is as follows:
Section 2 outlines the proposed risk assessment framework.
Section 3 describes the DER-explicit CPS model.
Section 4 delineates cybersystem vulnerabilities and cyberattack models.
Section 5 introduces the method for risk quantification. Simulation results and conclusions are discussed in
Section 6 and
Section 7.
2. Proposed Risk Assessment Framework
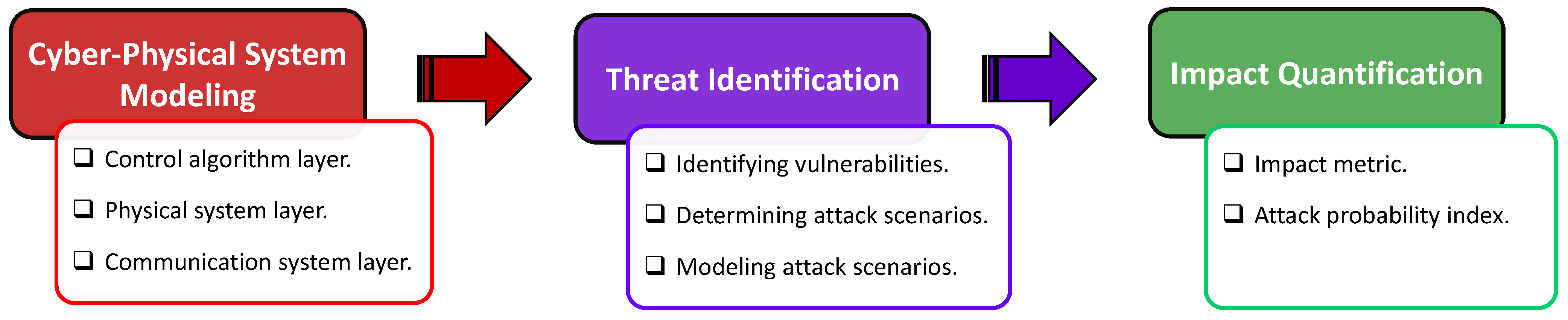
The proposed risk assessment framework comprises three main sections, as shown in
Figure 1: (i) cyberphysical system modeling, (ii) threat identification with cyberattack models, and (iii) impact quantification. This framework enables rapid snapshot analysis, focusing on steady-state evaluation. Moreover, due to the integration of the inverter dynamic model, it also facilitates accurate simulation of dynamic behavior, allowing for a detailed exploration of the potential impact of cyberattacks on the physical system. This framework has a modular structure, offering scalability and flexibility to incorporate other modules. Once the system configuration is collected, this framework can be tailored accordingly. It enables the assessment of risks posed by specific attacks and identifies the most vulnerable components in the cyber layer. Consequently, it provides valuable insights for crafting effective defense policies.
2.1. Cyberphysical System Modeling
The first and foremost important section is the CPS model of a distribution grid with inverter-based DERs. The proposed cyberphysical distribution system (CPDS) includes three layers: (i) the control layer, (ii) the physical system layer that embodies a DER-explicit distribution grid, and (iii) a communication layer manifesting interaction among the control and physical layers.
The optimal power flow (OPF) and load-sharing control represent examples of control algorithms tailored to achieve specific control objectives in physical system operation. It is important to recognize that various other DER control algorithms can also be deployed within this framework. However, different algorithms operate on distinct time scales and may necessitate different data exchange patterns. Given the low inertia of inverter-based distributed energy resources (DERs), these nuances are critical for accurately assessing risk, underscoring the necessity of specifying them prior to conducting risk assessment.
A DER-explicit unbalanced distribution system constitutes the physical layer of CPDS. With a focus on a distribution grid characterized by high DER penetration, the power-flow (PF) equations for the unbalanced distribution grid are utilized for steady-state analysis, complemented by the virtual oscillator controller (VOC)-based dynamic inverter model for dynamic analysis.
Finally, the communication layer within the CPDS employs a graph-based mapping function that captures the data exchange patterns between the control and physical system layers. This model also integrates time-stamp data for dynamic modeling and introduces communication system latency, which is essential for accurately representing the system’s dynamic characteristics.
2.2. Threat Identification
This section identifies potential threats to the DER communication network and assesses their probable impacts. In this section, the first step is to collect the cyber layer configuration, such as gateway info (manufacturer, software version) communication protocols, and so on. Based on the given information, the system vulnerability can be identified according to the vulnerability database. In this framework, the National Vulnerability Database (NVD) is utilized for vulnerability identification. Given the variety of threats, some could pose a risk to data confidentiality, potentially resulting in financial losses for utilities or customers, and others have the capacity to disrupt grid operations significantly, giving rise to concerns about public safety. This work primarily focuses on the latter category of attacks. To analyze the impact of cyberattacks, a suitable attack model is developed that aligns with the CPDS cyber model. This model can be integrated into the previously proposed cyberphysical interdependency model, capturing the atypical cyber component behaviors when attackers exploit vulnerabilities, leading to the execution of an attack. Through simulation of the CPDS model, the propagation of such attacks can be identified, thereby enabling determination of their potential impact on the physical layer.
2.3. Impact Quantification
To quantify impact, let
i denote the cyber component index. The risk for the
ith cyber component being attacked is defined as follows:
Here, represents the degree of impact, specifically the financial repercussions in this work, which is caused by the ith component being compromised. This assessment is facilitated by integrating the attack model with the proposed CPDS model, as discussed earlier. The parameter denotes the attack probability index, indicating the likelihood of the ith node being targeted. This is grounded in a cost–reward decision-making model. The associated “cost” reflects the “difficulty” of compromising a cyber node, established based on a Bayesian network using vulnerabilities identified in the preceding section. The “reward” is determined by the criticality of components, modeled as sensitivity in this study, i.e., the extent of change in physical state variables when the cyber variable transmitted in the component deviates from its desired value. This sensitivity is derived from analyzing the cyberphysical model for a given attack type. The overall attack probability index is calculated using the expected utility function, which amalgamates the “cost” and “reward” from the attackers’ perspective.
In the subsequent sections, each topic will be introduced in detail.
3. Cyberphysical System Modeling
Figure 2 provides an overview of the CPS model. The proposed model comprises three layers: (i) the control layer, (ii) the physical system layer representing a DER-explicit distribution grid, and (iii) a communication layer illustrating the interaction between the control and physical layers. These layers are depicted as time-dependent functional modules. These modules interconnect through a closed-loop data flow, where data serve as inputs and outputs for each module. Initially based on the static cyberphysical model proposed in [
20], we adapted it into a time-variant model to suit our low-inertia inverter-dominant CPS. Let
t denote time and
represent the measurement data collected at time
t, encompassing voltage, power information, etc., thus serving as the output of the physical system layer at time
t. Similarly,
denotes the control command reflecting the output of the control layer at time
t, encompassing operational commands generated for the inverter, such as real and reactive setpoints. The communication system layer further divides into two submodules: the measurement data path module
and the control command path module
. These modules delineate the data flow pattern and time latency. Consequently, for the
module, the output is denoted as
, which becomes the input of the control layer. Similarly,
refers to the output of
module. At the same time, it also refers to the input of the physical layer. Thus, by properly modeling the attacks, their propagation pattern and the potential impact can be derived from this CPS model. More details about each layer are elaborated in subsequent sections.
3.1. Control Layer
In this work, two control algorithms will be analyzed based on the desired control objective for the physical system operation.
3.1.1. Algorithm 1
The first control algorithm is the optimal power flow (OPF) [
21], with updates every 15 to 30 min. The objective of this algorithm is to regulate DER output, thus minimizing transmission-side power consumption costs and minimizing voltage deviations. Within this control, the control command carries the information of active and reactive power setpoints and is dispatched to each DER through the communication network. Let us consider a three-phase unbalanced distribution grid with
buses and
lines, and a set of
inverter-based DERs. The OPF problem can be formulated as follows:
In (
2),
and
are weight coefficients,
refers to the complex voltage phasor of each bus, and
indicate the real and reactive power of each line. The equality equations set
refers to the power flow equation, where
and
denote real and reactive power from the substation and DER, respectively. The
indicates the nominal voltage value. Additionally, the superscripts “min” and “max” correspond to the lower and upper limits of the respective variables and parameters.
3.1.2. Algorithm 2
In the second algorithm, the scenario assumes that the distribution-level OPF algorithm is unavailable. Consequently, we treat the distribution grid as a single bus and execute the OPF algorithm at the upstream or transmission control center. Control variables are defined as real and reactive power at the point of common coupling (PCC) on the distribution side. DERs are capable of load sharing [
22] and regulating real and reactive power at the substation level by exchanging output real and reactive power information with neighboring units. At steady state, the real and reactive power at the PCC achieves desired values, while the power ratio of each DER remains constant, as expressed in the following equation:
3.2. Physical System Layer
A general mathematical model for an unbalanced distribution grid with inverter-based DERs is presented here.
3.2.1. System Dynamic Model
The dynamic model of three-phase unbalanced distribution with inverter-based DERs can be described by a set of differential-algebraic equations (DAEs) [
23]:
Here, denotes a set of differential equations representing the dynamics of inverted-based DER generators, and represents PF equations. The vectors and denote dynamic state variables (e.g., system frequency) and physical algebraic variables (e.g., voltage magnitudes and phase angles), respectively. Finally, represents a vector of physical control variables (e.g., droop coefficients), and is a vector of system parameters, e.g., nodal injections including setpoints, i.e., .
The DERs are modeled as virtual oscillator controller (VOC)–based inverters, with multiple advantages compared to other control algorithms, such as droop or VSM [
21]. The control framework is based on [
24]. By leveraging a phase-decouple technology, this framework is able to be employed in a highly unbalanced network.
Figure 3 illustrates the hierarchical inverter control framework (using phase
a as an example). The inverter is first operated in the synchronization mode. When the voltage and phase differences between the grid and inverter are small enough, the inverter can be connected to the grid and start working in GFL mode, where
are the active and reactive power set points from the control layer. When operating in the load-sharing mode,
are replaced by the neighbor’s power ratio.
The VOC dynamics can be represented as follows:
where
is the averaged terminal-voltage magnitude, and
denotes the averaged phase offset.
and
are the averaged active and reactive output power of the inverter, respectively.
and
are preselected design parameters. The regulation of the inverter is achieved by continuously tuning two parameters, the voltage scaling factor
and the virtual capacitor
c, based on the control objective from the secondary control layer.
3.2.2. Steady-State Model
Consider the three-phase unbalanced distribution grid introduced previously in the section. A general expression for the
ith bus complex voltages
can be written as a function of nodal power injections
and complex voltage phasors
of all buses in the network as follows:
where
is a dense matrix with complex entries. The structure of
is defined through grid topology and line parameters [
25,
26]. The (
6) refers to the algebraic equation set depicting load flows in the unbalanced distribution grid.
For the steady-state analysis, the power system model in (
4) operates around its equilibrium, which is defined by the solutions of the algebraic set by equating the derivatives of dynamic state variables to zeros. Under normal operation, the slack bus (substation) is treated as an infinite bus. However, because of the potential cyberattacks, the power extracted from the substation may severely exceed the normal range and therefore lead to a voltage drop. Thus, in order to pull voltages back to the normal range, some load shedding may be required [
27].
3.3. Communication System Layer
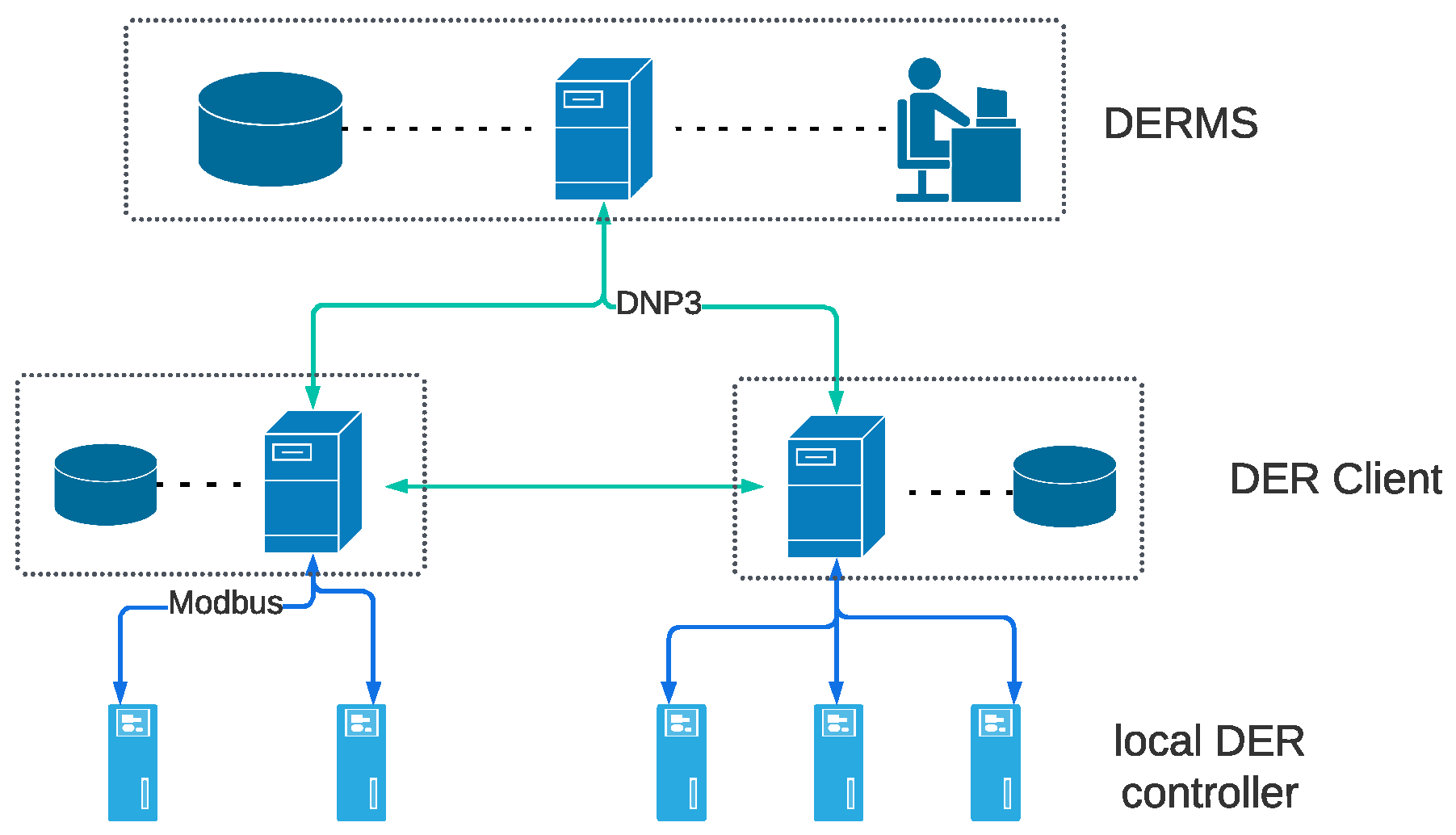
3.3.1. DER Communication Network Overview
A typical DER communication network [
28] is provided in
Figure 4. It is a three-layer hierarchical communication network analogous to an SCADA system. The first layer is the DERMS located at the utility control center. The DERMS is responsible for the operational control of all DERs. The second layer consists of DER clients enabling communication with DERMS, as well as the communication among clients for data exchange to enable distributed control. The local controller is the third layer, responsible for collecting field device measurement data and regulating DER output. Generally, this layer only supports local communication.
3.3.2. Cyber Component Model
The cyber components can be divided into two groups, nodes and links. The nodes refer to packet senders or receivers, which are capable of packet processing, including DERMS, DER client, and local controller. The links refer to communication channels.
For a single server node, the arriving data packets will queue in the server’s buffer and wait for the server to process. As a result, the time delay of cyber nodes includes the processing and queuing delay. Assuming the server processing rate is
and the packet arrival rate is
v, the average processing delay
and queuing delay
can be expressed as follows [
29]:
In the case of transmission-only nodes, the processing rate is much greater than the arrival rate, i.e.,
. Thus, the time delay is determined mainly by the processing delay. For the processing nodes, as the server needs to decode packets and modify payload, the processing rate
is comparable to
v. The dominant delay will be the queuing delay [
30]. Therefore, assuming
refers to any cyber variable processed in cyber nodes, and
indicates the payload modification function with respect to
, where
t refers to time, the nodes model
can be expressed as follows:
For long-distance communication, the main delay of communication links is the propagation delay, denoted as
, which depends on the distance between sender and receiver, as well as the links’ propagation speed, which can be modeled as follows:
Similarly, the link model
can be defined as follows:
3.3.3. Communication Network Model
In the earlier work cited as [
20], the communication network was thoroughly characterized using a time-invariant graph-based mapping function model. Recognizing the pivotal impact of latency, this study progresses by formulating an advanced time-dependent mapping function model, as depicted in the subsequent equation:
where
refers to the node function matrix,
denotes the path function matrix, and
indicates the starting node incidence matrix. Assuming the communication network is modeled as a connected graph
, where
represents vertices (nodes) and
denotes edges (links), the number of input and output streams are
L and
K, respectively. Therefore,
will be a
matrix depicting the functional list, and can be defined as follows:
where each row has the same elements, with each entry
defined through (
9). For a multiple-input multiple-output (MIMO) node, it may contain multiple functions, which can be described as follows:
where
n refers to the node index, and
indicates the number of node functions.
Take
Figure 5 as an example to illustrate the modeling process. This communication network comprises six nodes and five links with two input and output streams, respectively. For node 3, the target nodes are nodes 5 and 6, with the node function map as
and
. Similarly, for node 6,
and
denote the function corresponding to inputs from node 3 and node 4, respectively. The node function matrix
in this system is
is an
matrix, indicating the transmission path for each data packet, which can be modeled as follows:
where the superscripts and subscripts refer to the network input and output data streams, respectively. Let
be a
vector indicating the path from an input
l to an output
k, then the vector sequence is consistent with columns of
F(t).
is determined by the following steps:
Create a null vector representing all the nodes. In this example, the initial is a null vector, as there are two MIMO nodes.
Trace the transmission paths from the “In-1” to “Out-1”. Then, replace the “In-1” starting node with 1, resulting in .
Next, replace the following arrival node with the corresponding path function
. In this case, the next arrival node is node 3 through the “link-1” path, which corresponds to a function of
. Thus, the path vector becomes
, where
is defined through (
11).
Repeat step 3 until the end node is reached. in this example.
The transmission path matrix
in this example will become
Finally, we define the starting node incidence matrix
, which indicates the input starting node configuration for each output, as follows:
where
is an
matrix with
. Calculating
involves the following steps:
Generate the initial as a null matrix.
Columns of correspond to inputs. The first and second columns refer to “In-1” and “In-2”, respectively.
Rows of refer to the input starting nodes. The first and two rows outline node 1 and node 2, respectively.
Replace the exact starting node for each input with 1. Hence, the will become
Then,
for the model in
Figure 5 becomes
where the operators ⊙ and ⊕ can be referred to in [
20].
4. Cyber Threat Identification
In this section, the common vulnerabilities of the typical DER cyber layer are identified, followed by attack modeling.
4.1. Cyber Vulnerabilities in CPS
A comprehensive overview of cyber vulnerabilities within the CPS with high DER penetration is summarized in
Figure 6 [
6,
31,
32]. Cyberattacks might target either nodes or links. Among the cyber nodes, DERMS and DER clients usually perform strict security policies as the compromised data server may impact multiple devices within the network. However, due to software vulnerabilities or improper security configurations, the possibility of the potential threat still exists. The most common attacks include jamming or denial-of-service (DoS) attacks in order to disable accessibility and replay attacks or false data injection (FDI) attacks aiming to destroy data integrity.
For local controllers, the accessibility policy only allows local communication, and the most common attack is unauthorized access, including control parameters modification, set-point modification, DER disconnection, etc., which is easy to accomplish and may lead to severe consequences.
The most common attack on communication channels is the man-in-the-middle (MITM) attack. Due to existing protocol vulnerability, the attackers may intercept data packets transferred in the channel, which can delay or even drop the packets. Attackers can modify the payload data if there is no or weak cryptographic policy.
The possible consequences of these attacks in the physical layer include increased grid distribution losses, branch overflow, voltage or frequency violation, and stability issues. Note that the latter three may trigger protection devices and lead to load shedding or even blackouts.
Compared to compromising a cyber node, the impact of attacking the channel appears to be limited. Therefore, attacks on nodes are more prevalent. In this study, we primarily focus on node-based attacks.
4.2. Cyberattack Models
To incorporate the CPDS model for impact assessment, the attacks can be portrayed as either the fundamental attacks listed below or through various combinations of these attacks.
4.2.1. Jamming Attack
A jamming attack is implemented by flooding the server buffer with junk packets (i.e., increasing the packet arrival rate
v). If
v remains below the server processing rate
, the server will function, albeit with extended time delays. In contrast, if
v surpasses
, the superfluous junk packets will rapidly congest the server buffer, leading to the rejection of subsequent incoming packets, thus transforming the jamming attack into a denial-of-service (DoS) attack. Let
denote the original cyber variable, as presented before, and
denotes the compromised value. The jamming attack can be modeled as
4.2.2. Replay Attack
Replay attacks encompass the retransmission of outdated data packets. Attackers capture data packets previously sent by legitimate sources and subsequently resend these obsolete packets to the intended recipients. Detecting such attacks proves difficult since the outdated data often fall within normal ranges. Consequently, replay attacks can inflict significant disruptions on power grid operations. This type of attack can be depicted using the following equation:
where
refers to the time stamp of replacing data packets, which is determined by attackers.
4.2.3. FDI Attack
False data injection (FDI) attacks involve attackers directly altering captured data packet payloads to desired values. This manipulation is usually kept within a feasible range to avoid bad data detection. However, executing an FDI attack requires a more comprehensive understanding of system configuration and background knowledge. The FDI attack can be represented as follows:
The attack signal
is usually generated by an external system devised by attackers. This system aims to maximize the impact of the attack while avoiding detection by the bad data detection algorithm, enabling stealthy attacks. Various example systems are discussed in [
33,
34,
35]. Once
is established, for linear systems, the compromised node function can be reformulated as follows:
Therefore, by substituting with the original , the FDI attack manifests in the mapping function, and its impact can be estimated by simulating the integrated CPS model. However, pinpointing at a specific time t poses challenges. For risk analysis, a practical approach involves considering the worst-case scenario by assessing the range of . A commonly utilized method entails using the threshold value of the bad data detection algorithm to approximate this range. Nevertheless, it is crucial to acknowledge that this approximation might not comprehensively capture FDI attack characteristics. In FDI-specific research, a more precise model of should be developed.
FDI attacks can impact DER operations in various ways. When FDI targets real or reactive power measurements, it alters the power flow within the system, potentially leading to branch overflow or even necessitating load shedding. However, if the attack targets voltage or frequency measurements, DERs may erroneously adjust terminal voltage or frequency regulation, thereby introducing significant stability issues.
Once the attack type is selected and the corresponding parameters representing the attack capability are determined, the attack model is established and can be integrated into the cyber layer mapping function for impact prediction.
6. Case Study
6.1. IEEE 13-Node Test Case
In the modified IEEE 13-node test feeder, two DERs are integrated at node 680, with capacities of 500 kW and 800 kW, respectively. An additional DER is located at node 692 with a 1000 kW capacity. The DER penetration is about 66%. It is assumed that the power limit of the substation is 500 kW per phase. In normal operations, the substation can be modeled as a traditional slack bus with constant voltage. However, when the power exceeds the limit, the substation voltage will slightly decrease by kW.
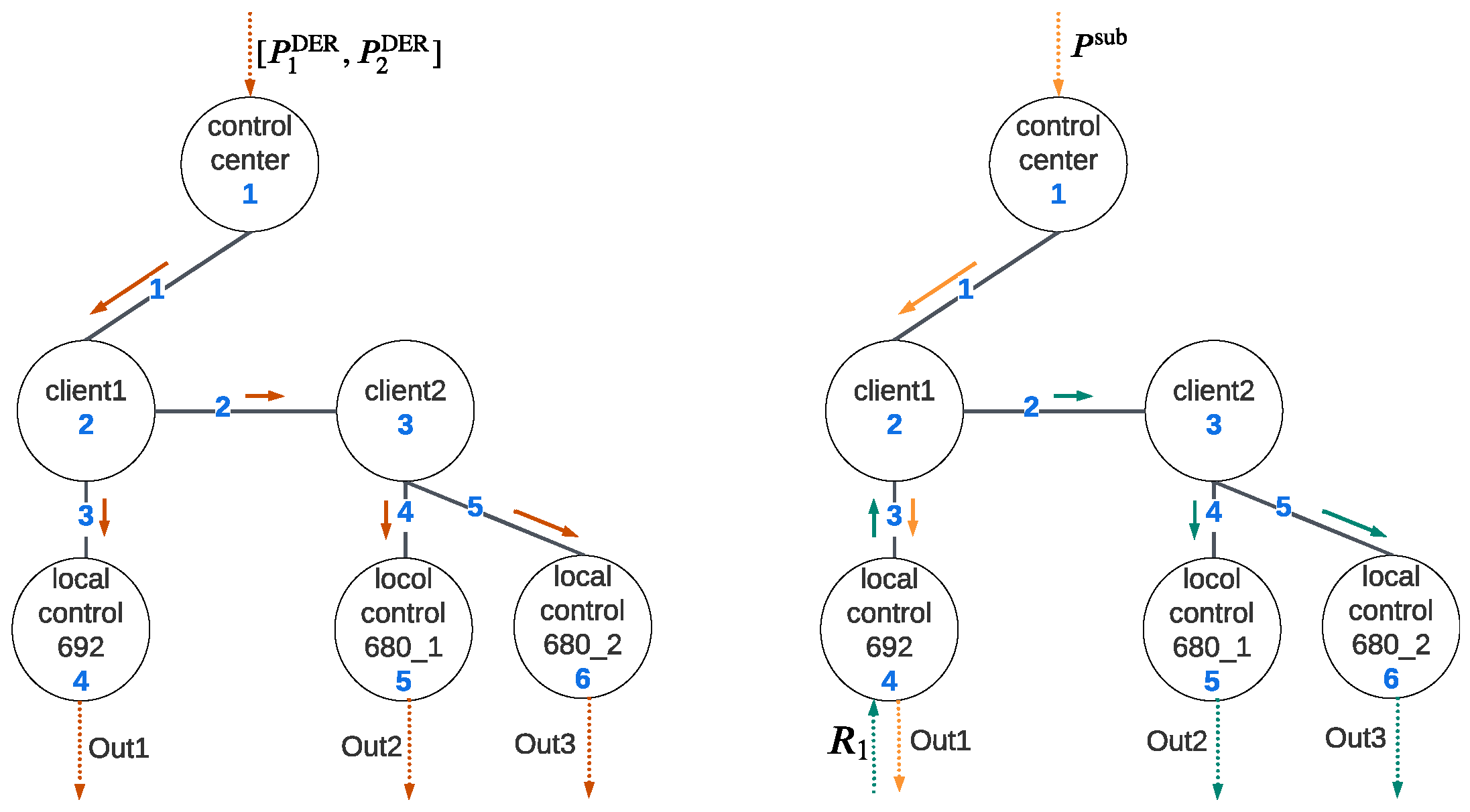
Figure 7 illustrates the data flow in the communication layer. In Algorithm 1, the control center calculates the real and reactive setpoints and sends them to each DER, while in Algorithm 2, DER at node 692 adjusts its power injection to control real and reactive power at PCC, and DERs at node 680 use the power ratio of DER at node 692 as input to achieve load sharing. In the following simulation, cases 1, 2, and 3 deploy Algorithm 1, and Algorithm 2 is implemented in case 4. The system dynamic model is implemented in MATLAB 2022, utilizing a machine with the following configuration: an Intel i7 processor with 16 GB of RAM running at 2.8 GHz.
Integrating the VOC-based inverter into the IEEE 13-node test feeder demanded careful consideration due to its low inertia, with minor disturbances risking system instability. Our exploration of inverter operation strategy highlighted potential stability challenges, underscoring the need for real-time monitoring and protection mechanisms to maintain system stability.
6.1.1. Case 1: Modification of Setpoints in OPF Mode
The control command
is issued for adjusting the setpoints of DERs. The two DERs at node 680 are considered a unified single unit during the OPF control level. Based on their respective capacities, DER client2 divides
and transmits the information to two local controllers, as depicted in
Figure 7. Considering the high data processing rate at the control center, the delay time can be disregarded. The communication network parameters are detailed in
Table 1, with
and
representing the processing rate and forwarding rate, respectively. The node function can be characterized as follows:
The functions
and
correspond to the outputs directed towards nodes 4 and 3, while
and
represent the outputs to nodes 5 and 6, respectively. As detailed in
Section 3, the communication layer outputs, specifically the setpoints of the three DERs, can be described as follows:
Table 2 provides an overview of recent vulnerabilities from NVD that could potentially result in malicious modifications. The probability index for each node is outlined in
Table 3. The control center exhibits the lowest vulnerabilities due to its stringent security policy. Comparatively, client1, functioning as a subcenter, employs a more robust security mechanism than client2, resulting in a lower vulnerability. Local controllers, being primarily restricted to local communication, maintain the weakest security policy, rendering them the most vulnerable. Meanwhile, parameter
signifies the attacker’s preference. Given the values of
found in
Table 3,
can be determined as follows:
It can be observed that nodes 5 and 6 have the highest probability index, as they are the easiest to compromise and may cause significant voltage variation. Node 2 also has a high probability index, as it can impact all DER setpoints. It is worth noting that the probability index may vary depending on the definition of and .
The impact degree is determined by the worst-case scenario. Taking node 3 as an example, in the worst case, the setpoints were modified to 0 (standby mode), i.e.,
. The simulation results from the MATLAB model are shown in
Figure 8, illustrating the impact of the DER power output attack on voltage variations across all buses. The corresponding DERs are connected to the grid at 3 s (DER 692) and 3.5 s (DER 680_1, DER 680_2), initially staying in the standby state after connection to the primary grid. We observe a minor disturbance in the voltage profile during this stage, attributed to the slight voltage gap between the inverter terminal and grid at the connecting moment. Upon connection to the grid, the DER output power (real/reactive) remains zero while the voltage profile remains unchanged. At 4 s, the control center executes OPF and dispatches real and reactive setpoints to field devices. The DERs’ output ramps up and reaches the desired value at around 5 s, operating at full capacity. Consequently, this also causes a slight elevation in the voltage profile.
Around 7 s, attackers compromise node 3 and reset the setpoints to 0. Consequently, the power output of DER 680_1 and DER 680_2 drops to 0, while DER 692 maintains its output. As a result, to meet the load demand, the power drawn from the substation increases significantly, exceeding the substation’s power limit and causing a voltage decline. Some bus voltages fall below 0.95 p.u., potentially triggering protection mechanisms necessitating load shedding. To maintain voltages within the acceptable range, an optimal load-shedding plan is formulated. This plan involves cutting loads 646, 692, 675a, 611, and 670c, resulting in a total loss of 1172 kW. Assuming that load shedding is initiated at 11 s, the bus voltages subsequently return to the normal range, as illustrated in the figure.
In this paper, we assume
and
is 24 h [
38]. In this case, the risk of node 3 (DER client2) is
The risks associated with each cyber node are presented in
Table 4. The result reveals that node 2 carries the highest risk, closely followed by node 1. These nodes can impact all DER units located at bus 680 and 692 simultaneously according to cyberphysical interdependency, thus holding the most significant criticality. Among them, as node 1 is the control center and deploys the strictest security policy, this node is not easy to compromise, making the attack probability of node 1 much lower than node 2. However, considering their high risks, implementing advanced security measures becomes imperative to fortify these specific nodes. Nodes 4, 5, and 6 are local controllers. Their vulnerable levels are comparable. Among them, node 6 holds the highest risk, even higher than node 3. This is due to the high sensitivity (especially the physical layer sensitivity) of this node. Node 4 reveals the lowest risk, as its vulnerability, although noteworthy, is counterbalanced by a less impactful outcome, rendering it less appealing to potential attackers.
6.1.2. Case 2: FDI Attack on Local Controllers
In this case, attackers try to compromise the local controllers and implement an FDI attack. Assuming the DER operation schedule is the same as in Case 1, attackers compromise node 6 at the beginning and start modifying the local voltage measurement data to 1.2 times the original value, i.e.,
. This will impact the DER synchronization process. Specifically, as the measurement data are altered, maintaining the same control algorithm, the actual voltage of the inverter tends to be approximately 0.83 times that of the voltage on the grid side. Consequently, at 3.5 s, when the inverter connects to the grid, the significant voltage differential, combined with the low inertia of the inverter, induces an inrush current from the grid into the inverter. This results in a substantial voltage drop on the grid side, as depicted in
Figure 9. Following the transition to GFL mode, the inverter aligns with the grid-side voltage, restoring the voltage profile to within normal ranges. However, in practical scenarios, this inrush current may surpass the maximum current limit, triggering protective mechanisms and causing a DER trip.
6.1.3. Case 3: Modification of Local Controller Parameters
In this scenario, the attackers’ aim is to compromise local controllers by manipulating control parameters. Assuming the DER operation schedule remains consistent with previous cases, node 6 is compromised, leading to modifications in the PI controller parameters at the GFL side at 3 s. At this time, the inverter operates in synchronization mode, keeping its performance unaffected and ensuring stable terminal voltage regulation. However, when the DER switches to GFL mode at 4 s, the inverter starts to adjust its output accordingly. Referring to
Figure 3, with the inverter initial output at 0, the deviations between the real and reactive power and their setpoints (
) are notably high. Upon malicious modification of the PI controller, specifically by enlarging its parameters, this disturbance pushes the system out of its stability zone, resulting in detrimental oscillations, as depicted in
Figure 9. In practice, this scenario may trigger inverter undervoltage (UV) protection, leading to a DER trip. If not promptly isolated, these significant voltage oscillations may cause further DER trips and potentially lead to load shedding.
6.1.4. Case 4: Jamming Attack in Load-Sharing Mode
In this case, the distribution system operates following Algorithm 2, i.e., the load-sharing algorithm, with the upper-level OPF dictating a setpoint of 1000 kW at the grid-side PCC. In contrast to Case 1, the roles of nodes 2 and 3 were altered as follows:
Here,
and
refer to the function forwarding to nodes 4 and 3;
and
refer to the function sending packets to nodes 5 and 6, respectively. The cyber layer outputs become
where
refers to the power ratio of DER_1, as depicted in
Figure 7. Let us assume that attackers can send junk packets to jam node 6. As a result, whenever the packet arrival rate is comparable to the processing rate, time latency will increase significantly. Assuming that the arrival rate of node 6 becomes 1800/s due to junk packets, the
latency becomes approximately 0.01 s.
Figure 10 shows the attack consequence. The top and bottom plots indicate an attacked scenario without and with consideration of latency, respectively. It is noted that when considering latency, the jamming attack may lead to an unstable system. However, when the communication latency is ignored, the same jamming attack does not cause system instability. This may lead operators to ignore possible grid oscillations and cause large-scale cascade failure.
6.2. IEEE 123-Node Test Case
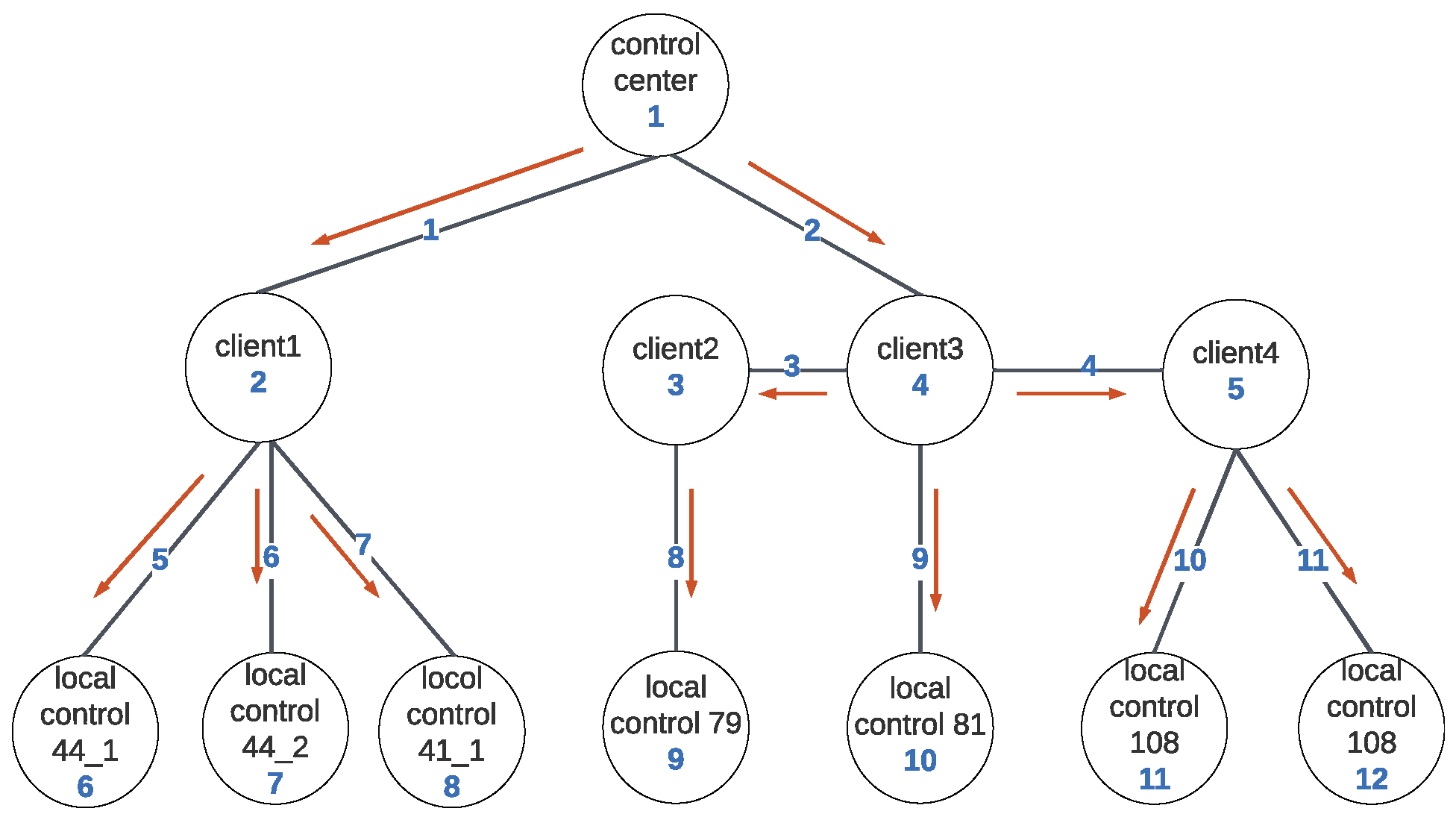
The IEEE 123-node test feeder was modified to incorporate DER units according to the configuration shown in
Table 5. The DER penetration level was 80%. We tested the attack scenario involving the modification of real and reactive power setpoints in the control layer when deploying the OPF algorithm. The data flow for this scenario is illustrated in
Figure 11. The cyber node risk associated with this test feeder is shown in
Table 6.
In this test system, the control center (node 1) presents the highest risk due to its critical role. While not easily compromised, its compromise could impact all DER units, potentially leading to severe load shedding, thus presenting the overall highest risk. While client nodes generally offer higher utility outcomes, they are less vulnerable compared to local controllers. Simulation results exhibit an interspersed pattern among these two types of nodes, as illustrated in the table. Among client nodes, node 4 exhibits the highest criticality as a transfer node, with access to data transmitted to nodes 3 and 5. Despite having the highest probability of attack among all cyber nodes, its impact degree is much lower compared to node 1, positioning it as the second-highest risk if compromised. Node 3 carries the lowest risk among all cyber nodes. It can only affect one DER unit and provides similar outcome utility to the local controller node 9. However, its higher level of security compared to node 9 makes it less attractive from an attacker’s perspective.
It is noteworthy that in comparison to the IEEE 13 node test system, compromising the control center in this highly distributed test feeder yields a similar impact. However, compromising a DER client or a local controller in this system may only affect limited DER capacities, resulting in a significantly lower impact compared to the IEEE 13 node test system. Overall, this distributed system demonstrates greater resilience against cyberattacks than the IEEE 13 node test feeder.
7. Conclusions
The integration of grid-edge inverter-based DERs into distribution grids highlights the necessity for real-time control and monitoring through efficient communication systems. However, this integration of communication networks increases the vulnerabilities susceptible to cyberattackers. As a result, the development of a comprehensive CPS risk assessment framework becomes imperative. In light of limitations in the literature work, this research presents a novel risk assessment framework tailored for distribution grids with substantial penetration of inverter-based DERs. The framework encompasses (i) a detailed distribution grid model that explicitly incorporates the dynamic attributes of inverter-based DERs, (ii) a high-fidelity DER communication layer model that considers communication latency, enabling precise execution of cyber layer attacks, and (iii) a cyberattack risk quantification approach using an attack probability model that factors in both cyber component vulnerability and criticality. Furthermore, the impact of cyberattacks is quantified in terms of economic losses resulting from load shedding. The numerical studies consider various cyberattack scenarios on standard IEEE distribution feeders with grid-edge DERs to validate the framework’s efficacy, affirming its ability to identify high-risk components and guide security policy improvements, thereby contributing to the reinforced system’s reliability and resilience.
Based on the previous discussion, we identified several potential steps to mitigate the cyber risks within the system: (i) Given that high-critical nodes can engender more severe consequences, it is imperative to enhance their security mechanisms to minimize cyber risks. (ii) Recognizing that the degree of impact is assessed based on economic losses incurred from load shedding, it is essential to implement measures such as demand response or augmenting reserve capacity. These actions aim to reduce lost load, particularly during peak hours when electricity prices are relatively high. (iii) Developing a cyber layer restoration strategy is crucial to minimizing post-attack restoration time and mitigating overall risks. (iv) Based on our previous discussion, implementing a high-distributed DER placement strategy enhances system robustness, thereby mitigating system risks.
We observed an increase in emerging cyberphysical coordinated attacks and multistage, multiwave attacks, which are more challenging to detect but can result in more severe consequences. In our future research, we aim to analyze the characteristics of these attacks and develop risk assessment platforms for them. This will enable us to provide guidelines for implementing corresponding defensive strategies and enhancing power system security.