Privacy-Preserving Charging Coordination Scheme for Smart Power Grids Using a Blockchain
Abstract
1. Introduction
2. Related Works
3. Network/Threat Models and Design Goals
3.1. Network Model
- The Key Management Center (KMC): The is a trusted party. It can be a governmental authority such as the Ministry of Electricity and Energy, which is the administrator of the whole system. It is responsible for the initialization of the entire system including the registration of all terminals.
- Energy Storage Units (ESUs): An can be either a home battery or EV. It is the fundamental unit in the smart grid, which is deployed in one community named group and connected to the blockchain network through the validator (local aggregator).
- The Blockchain Network: The blockchain is the heart of our proposed scheme. It is responsible for receiving and scheduling incoming charging requests without exceeding the maximum energy capacity or accessing individual charging requests. The blockchain consists of nodes named validators. Each validator acts as either an aggregator or a verifier. The local aggregator receives n masked signed charging requests from in one group. It computes the aggregated charging request . Finally, the aggregation results and proof of correct aggregation are forwarded to a verifier to start the verification process. The verifier uses the reported verification parameters to check the correctness of the aggregated result. In addition, due to the nature of the blockchain, it is a common assumption that more than of the blockchain validators are honest. In this paper, we implement our proposed scheme using a private blockchain. A private blockchain is selected because each verifier belongs to a different utility and every utility is considered a node in the blockchain network. In addition, a private blockchain provides higher throughput with more acceptable latency than a public blockchain.
3.2. Threat Model
3.3. Design Goals
- Decentralization and resiliency: Our proposed scheme should not rely on any central party to perform the charging coordination. As mentioned previously, centralized schemes are vulnerable to single-point-of-failure and other attacks and suffer from a lack of transparency. Therefore, our proposed scheme considers that no entity in the entire system has complete central authority to control the charging coordination process.
- Privacy-preserving charging scheduling: Our proposed charging scheduling scheme should compute the charging schedules without exceeding the and without disclosing any sensitive information about the clients.
- Resistance to replay attacks: Our proposed scheme should counter replay attacks, i.e., if an attacker tries to record a charging request and sends it later, it should be rejected.
- Data integrity and authenticity: Our proposed scheme should guarantee the integrity and authenticity of incoming charging requests and also the authenticity of the ESUs’ identity.
4. Preliminaries
4.1. Bilinear Pairings
- Non-degeneracy: .
- Bilinearity: and where is a finite field of order p.
- Computability: There is an efficient algorithm to compute .
- Non-degeneracy: .
- Bilinearity: and where is a finite field of order p.
- Computability: There is an efficient algorithm to compute .
4.2. Computational Diffie–Hellman (CDH) Problem
4.3. Key Agreement Protocol
- The algorithm takes the security parameter as input and produces public parameters , where is a group with a prime order p, where , and is a hash function.
- using public parameters, the terminal i could generate its private∖public key pair , in which represents the private key of terminal i and is the corresponding public key.
- Using the private key of terminal i, the public key of terminal j, and the algorithm, such as the Diffie–Hellman key agreement protocol, the two terminals could generate a shared key
4.4. The Deterministic Random Generator (DRG)
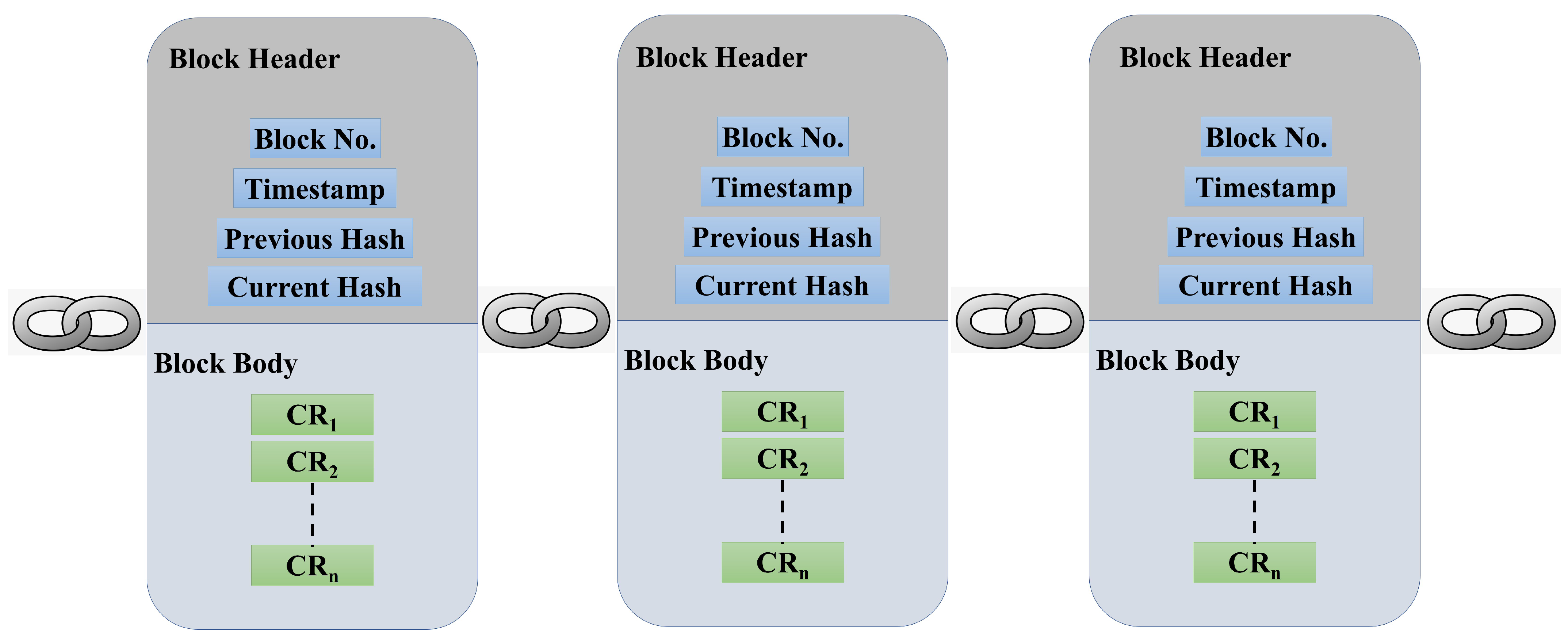
4.5. Blockchain Technology
5. The Proposed Scheme
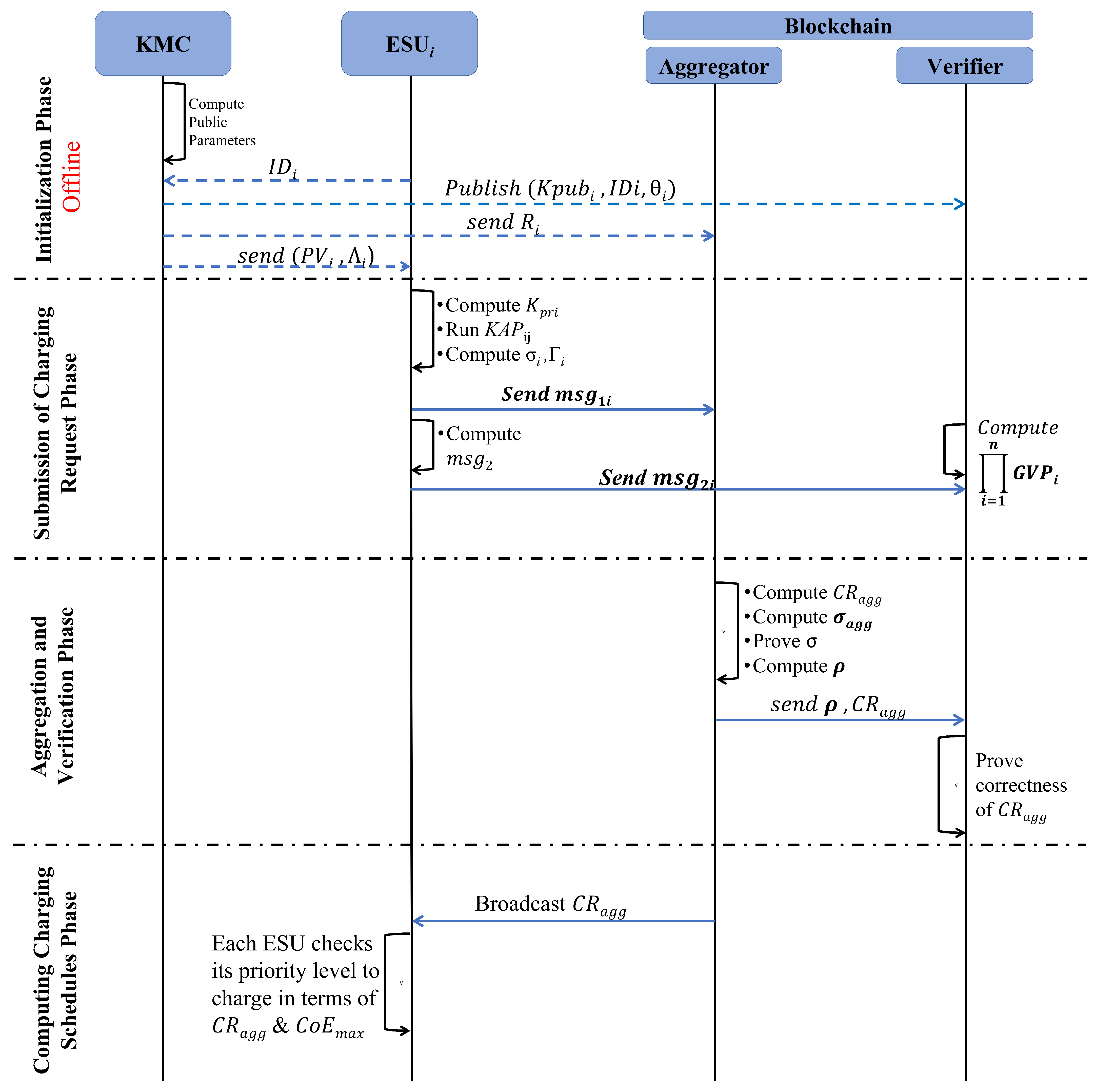
5.1. System Initialization
5.2. Submission of Charging Requests
5.2.1. Preparing Charging Requests
5.2.2. Submitting Charging Requests
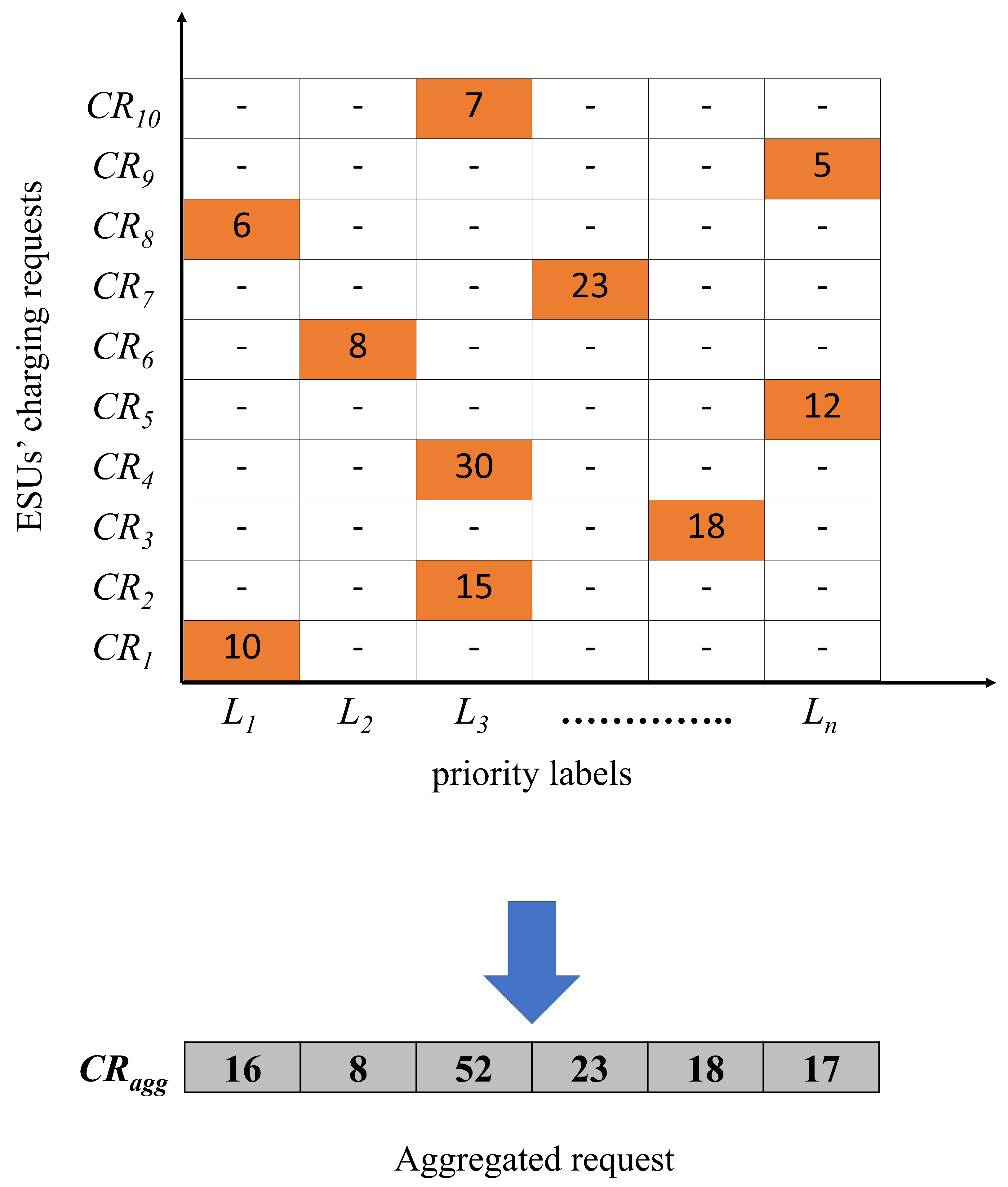
5.3. Aggregation and Verification of Charging Requests
5.4. Computing Charging Schedules
6. Security Analysis
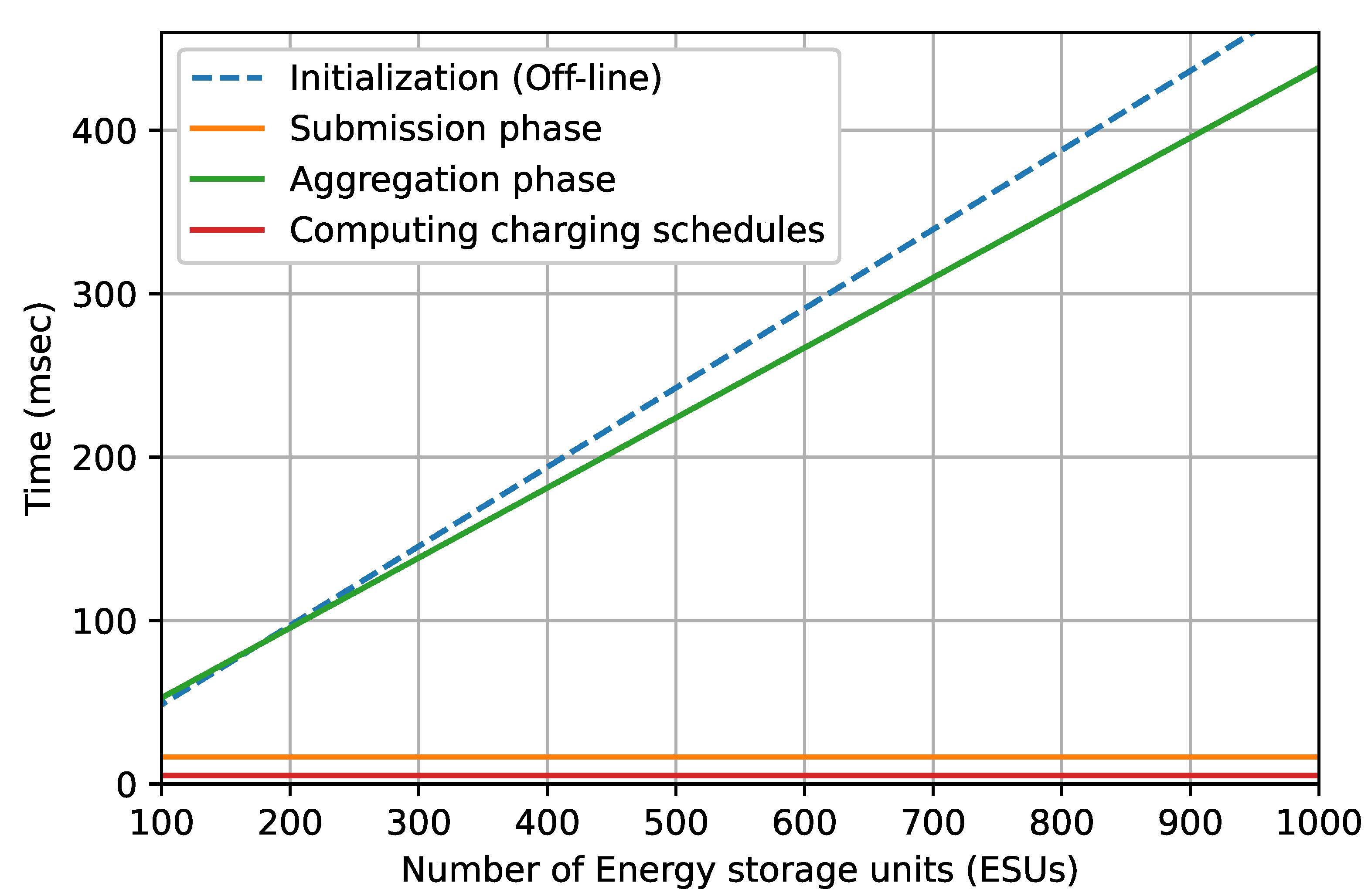
7. Performance Analysis
7.1. Off-Chain
7.1.1. Communication Overhead
7.1.2. Computation Overhead
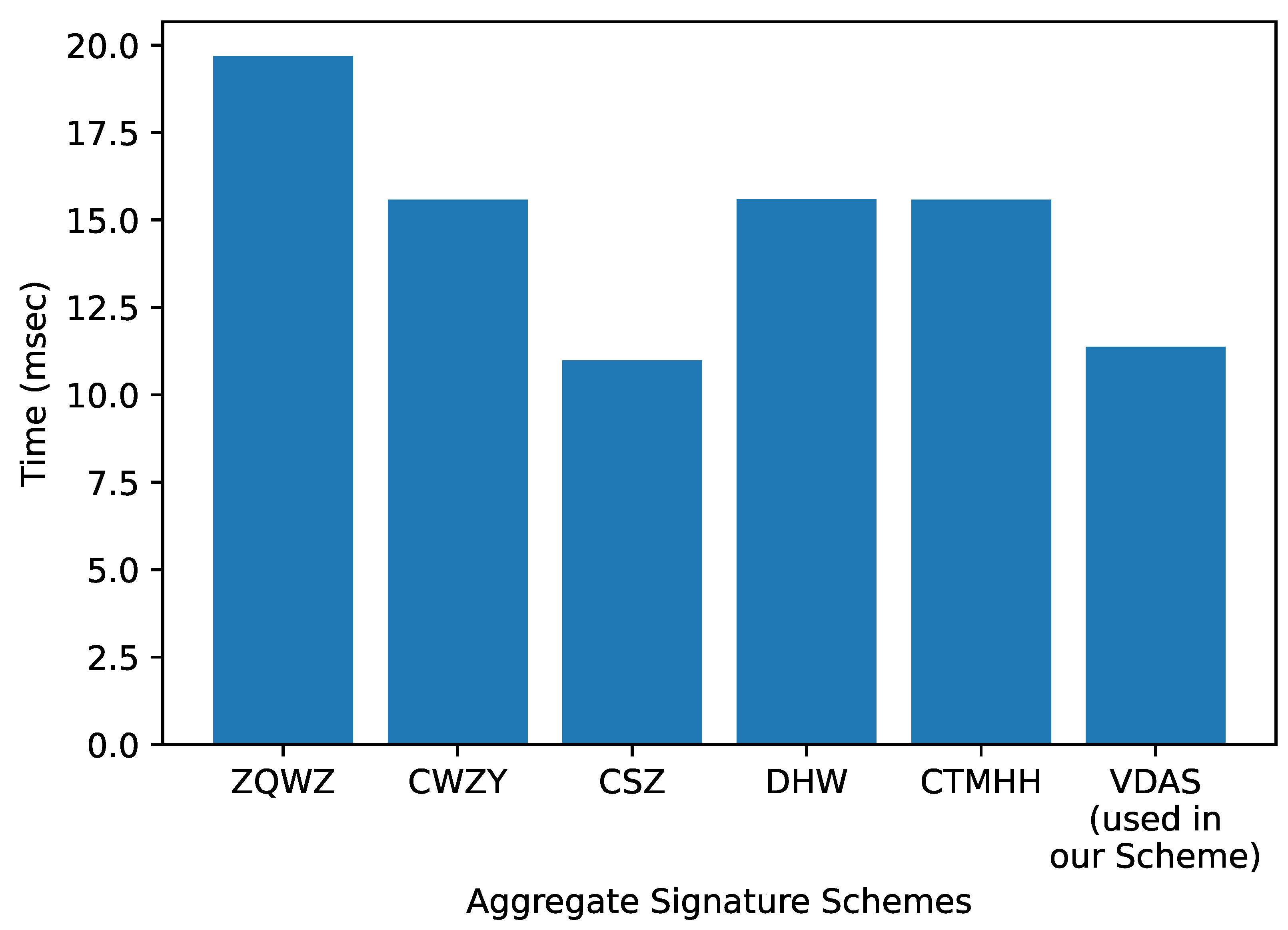
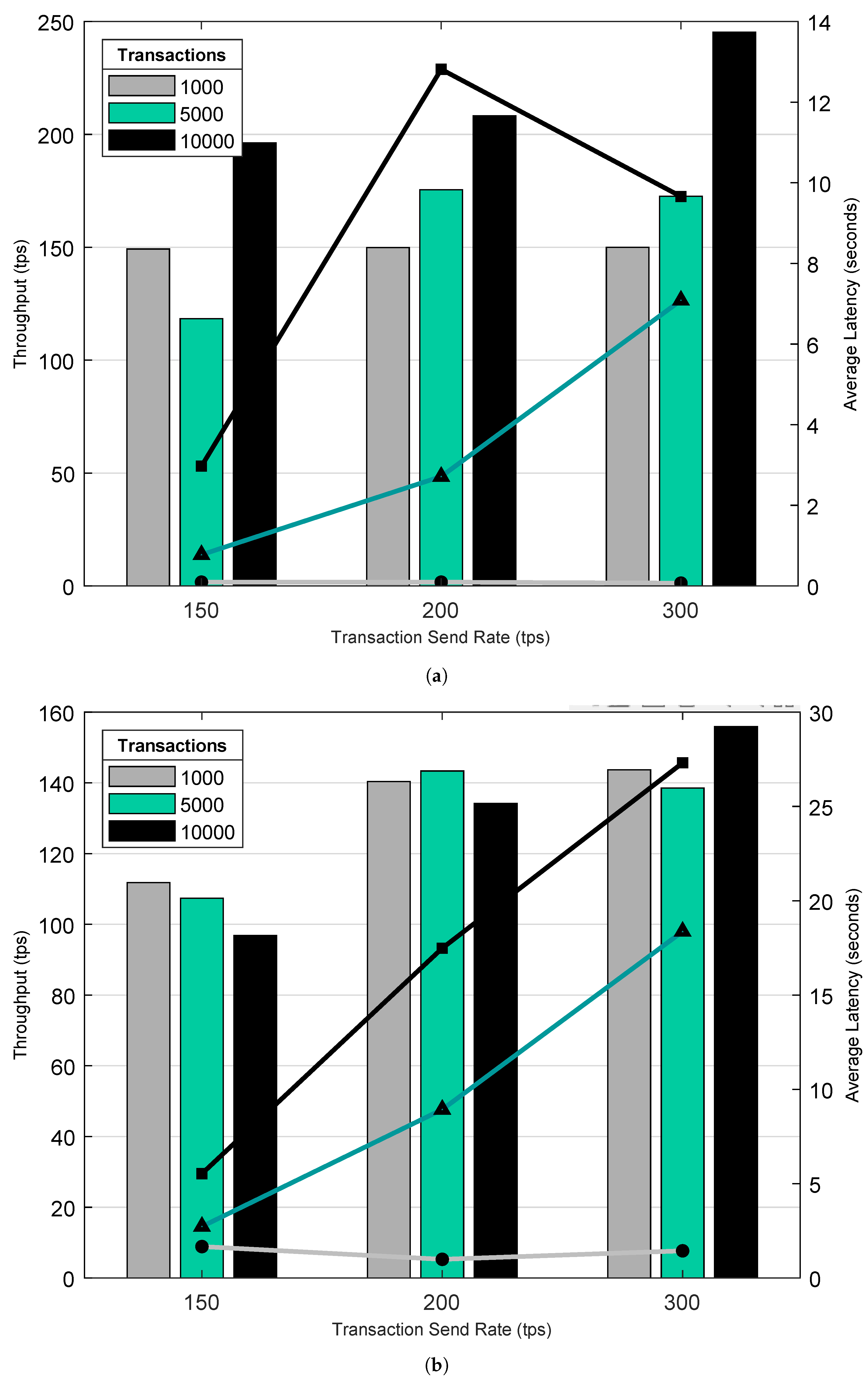
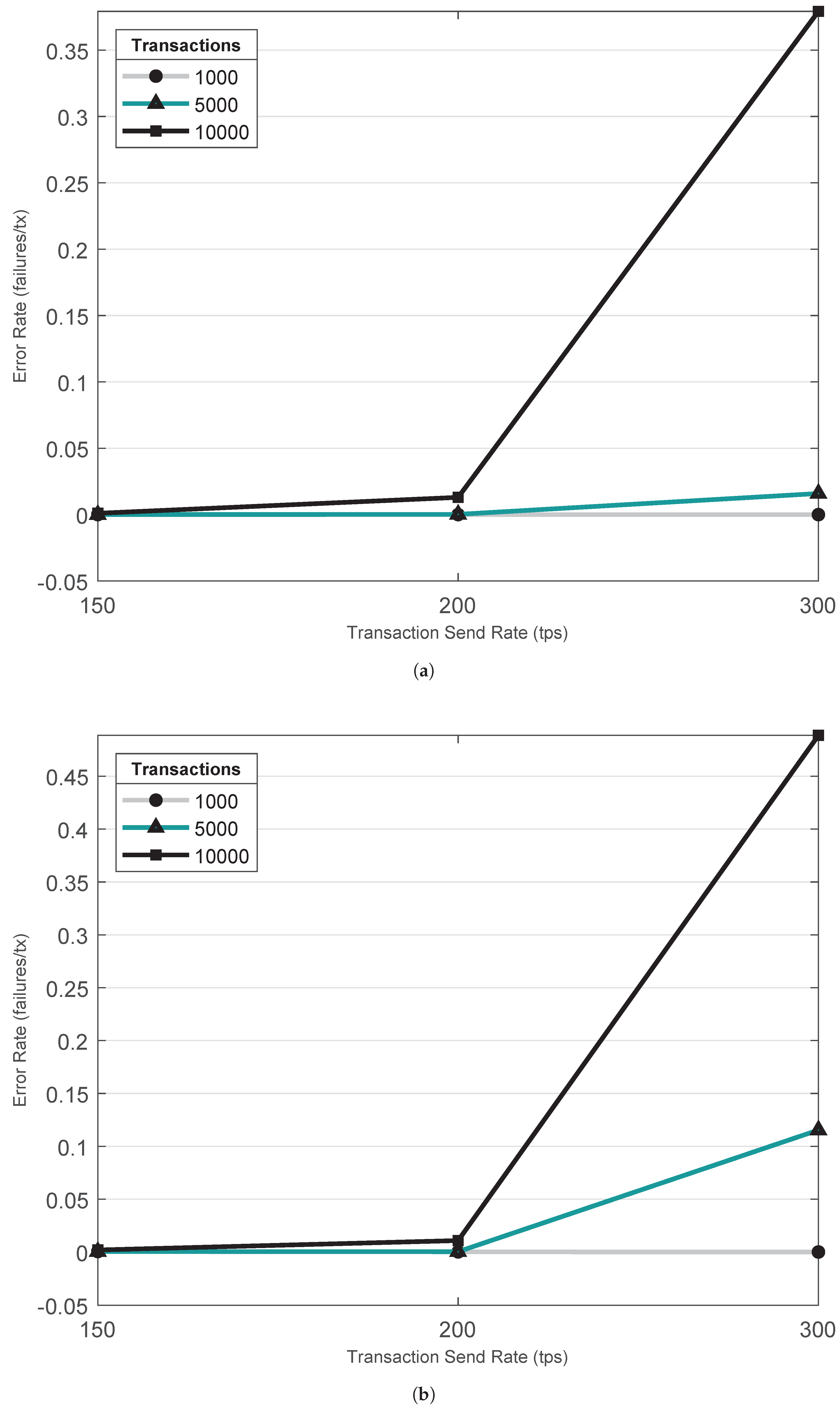
7.2. On-Chain Overheads
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Habbak, H.; Metwally, K.; Mattar, A.M. Securing Big Data: A Survey on Security Solutions. In Proceedings of the 2022 13th International Conference on Electrical Engineering (ICEENG), Cairo, Egypt, 29–31 March 2022; pp. 145–149. [Google Scholar]
- Wang, J.; Bharati, G.R.; Paudyal, S.; Ceylan, O.; Bhattarai, B.P.; Myers, K.S. Coordinated electric vehicle charging with reactive power support to distribution grids. IEEE Trans. Ind. Inform. 2019, 15, 54–63. [Google Scholar] [CrossRef]
- Mahmoud, M.; Ismail, M.; Akula, P.; Akkaya, K.; Serpedin, E.; Qaraqe, K. Privacy-aware power charging coordination in future smart grid. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Dohar, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Yang, Y.; Jia, Q.S.; Deconinck, G.; Guan, X.; Qiu, Z.; Hu, Z. Distributed Coordination of EV Charging with Renewable Energy in a Microgrid of Buildings. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019; p. 1. [Google Scholar]
- Baza, M.; Nabil, M.; Ismail, M.; Mahmoud, M.; Serpedin, E.; Rahman, M.A. Blockchain-based charging coordination mechanism for smart grid energy storage units. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 504–509. [Google Scholar]
- Liu, L.; Zhou, K. Electric vehicle charging scheduling considering urgent demand under different charging modes. Energy 2022, 249, 123714. [Google Scholar] [CrossRef]
- Yang, S.; Zhang, S.; Ye, J. A novel online scheduling algorithm and hierarchical protocol for large-scale EV charging coordination. IEEE Access 2019, 7, 101376–101387. [Google Scholar] [CrossRef]
- Koufakis, A.M.; Rigas, E.S.; Bassiliades, N.; Ramchurn, S.D. Offline and online electric vehicle charging scheduling with V2V energy transfer. IEEE Trans. Intell. Transp. Syst. 2019, 21, 2128–2138. [Google Scholar] [CrossRef]
- Baza, M.; Pazos-Revilla, M.; Sherif, A.; Nabil, M.; Aljohani, A.J.; Mahmoud, M.; Alasmary, W. Privacy-preserving and collusion-resistant charging coordination schemes for smart grids. IEEE Trans. Dependable Secur. Comput. 2021, 19, 2226–2243. [Google Scholar] [CrossRef]
- Shafee, A.; Baza, M.; Talbert, D.A.; Fouda, M.M.; Nabil, M.; Mahmoud, M. Mimic learning to generate a shareable network intrusion detection model. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; pp. 1–6. [Google Scholar]
- Yang, K.; Zhang, K.; Ren, J.; Shen, X. Security and privacy in mobile crowdsourcing networks: Challenges and opportunities. IEEE Commun. Mag. 2015, 53, 75–81. [Google Scholar] [CrossRef]
- Li, M.; Weng, J.; Yang, A.; Lu, W.; Zhang, Y.; Hou, L.; Liu, J.N.; Xiang, Y.; Deng, R.H. CrowdBC: A blockchain-based decentralized framework for crowdsourcing. IEEE Trans. Parallel Distrib. Syst. 2018, 30, 1251–1266. [Google Scholar] [CrossRef]
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.; Alshamari, M.; Cao, Y. A survey on blockchain technology: Evolution, architecture and security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Li, T.; Gao, C.; Jiang, L.; Pedrycz, W.; Shen, J. Publicly verifiable privacy-preserving aggregation and its application in IoT. J. Netw. Comput. Appl. 2019, 126, 39–44. [Google Scholar] [CrossRef]
- Liu, J.; Han, J.; Wu, L.; Sun, R.; Du, X. VDAS: Verifiable data aggregation scheme for Internet of Things. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Ota, Y.; Taniguchi, H.; Nakajima, T.; Liyanage, K.M.; Baba, J.; Yokoyama, A. Autonomous Distributed V2G (Vehicle-to-Grid) Satisfying Scheduled Charging. IEEE Trans. Smart Grid 2012, 1, 559–564. [Google Scholar] [CrossRef]
- Das, S.; Acharjee, P.; Bhattacharya, A. Charging scheduling of electric vehicle incorporating grid-to-vehicle (G2V) and vehicle-to-grid (V2G) technology in smart-grid. In Proceedings of the 2020 IEEE International Conference on Power Electronics, Smart Grid and Renewable Energy (PESGRE2020), Kerala, India, 2–4 January 2020; pp. 1–6. [Google Scholar]
- Huang, X.; Zhang, Y.; Li, D.; Han, L. An optimal scheduling algorithm for hybrid EV charging scenario using consortium blockchains. Future Gener. Comput. Syst. 2019, 91, 555–562. [Google Scholar] [CrossRef]
- Tushar, W.; Zhang, J.A.; Smith, D.B.; Poor, H.V.; Thiébaux, S. Prioritizing consumers in smart grid: A game theoretic approach. IEEE Trans. Smart Grid 2014, 5, 1429–1438. [Google Scholar] [CrossRef]
- Sortomme, E.; El-Sharkawi, M.A. Optimal scheduling of vehicle-to-grid energy and ancillary services. IEEE Trans. Smart Grid 2012, 1, 351–359. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Maharjan, S.; Zhang, Y.; Hossain, E. Enabling localized peer-to-peer electricity trading among plug-in hybrid electric vehicles using consortium blockchains. IEEE Trans. Ind. Inform. 2017, 13, 3154–3164. [Google Scholar] [CrossRef]
- Tajeddini, M.A.; Kebriaei, H. A mean-field game method for decentralized charging coordination of a large population of plug-in electric vehicles. IEEE Syst. J. 2019, 13, 854–863. [Google Scholar] [CrossRef]
- Tian, Z.; Jung, T.; Wang, Y.; Zhang, F.; Tu, L.; Xu, C.; Tian, C.; Li, X.Y. Real-time charging station recommendation system for electric-vehicle taxis. IEEE Trans. Intell. Transp. Syst. 2016, 17, 3098–3109. [Google Scholar] [CrossRef]
- Cao, Y.; Tong, W.; Omprakash, K.; Geyong, M.; Naveed, A.; Abdullah, A. An EV Charging Management System Concerning Drivers’ Trip Duration and Mobility Uncertainty. IEEE Trans. Syst. Man Cybern. Syst. 2018, 48, 596–607. [Google Scholar] [CrossRef]
- Xu, X.; Ke, D.; Li, L.; Xu, B. Optimal charging strategy for heterogeneous EVs for cyber-physical-social systems. In Proceedings of the 2018 2nd IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 20–22 October 2018; pp. 1–5. [Google Scholar]
- Akula, P.; Mahmoud, M.; Akkaya, K.; Songi, M. Privacy-preserving and secure communication scheme for power injection in smart grid. In Proceedings of the 2015 IEEE International Conference on Smart Grid Communications (SmartGridComm), Miami, FL, USA, 2–5 November 2015; pp. 37–42. [Google Scholar]
- Alsharif, A.; Nabil, M.; Tonyali, S.; Mohammed, H.; Mahmoud, M.; Akkaya, K. EPIC: Efficient privacy-preserving scheme with EtoE data integrity and authenticity for AMI networks. IEEE Internet Things J. 2019, 6, 3309–3321. [Google Scholar] [CrossRef]
- Tonyali, S.; Cakmak, O.; Akkaya, K.; Mahmoud, M.M.; Guvenc, I. Secure data obfuscation scheme to enable privacy-preserving state estimation in smart grid AMI networks. IEEE Internet Things J. 2015, 3, 709–719. [Google Scholar] [CrossRef]
- Li, H.; Dan, G.; Nahrstedt, K. Lynx: Authenticated anonymous real-Time reporting of electric vehicle information. In Proceedings of the IEEE International Conference on Smart Grid Communications, SmartGridComm 2015, Miami, FL, USA, 2–5 November 2015; pp. 599–604. [Google Scholar]
- Li, H.; Dan, G.; Nahrstedt, K. Portunes+: Privacy-Preserving Fast Authentication for Dynamic Electric Vehicle Charging. IEEE Trans. Smart Grid 2017, 8, 2305–2313. [Google Scholar] [CrossRef]
- Fan, M.; Zhang, X. Consortium blockchain based data aggregation and regulation mechanism for smart grid. IEEE Access 2019, 7, 35929–35940. [Google Scholar] [CrossRef]
- Li, H.; Han, D.; Tang, M. A privacy-preserving charging scheme for electric vehicles using blockchain and fog computing. IEEE Syst. J. 2020, 15, 3189–3200. [Google Scholar] [CrossRef]
- Wang, Z. Identity-Based Verifiable Aggregator Oblivious Encryption and Its Applications in Smart Grids. IEEE Trans. Sustain. Comput. 2021, 6, 80–89. [Google Scholar] [CrossRef]
- Baloglu, U.B.; Demir, Y. Lightweight privacy-preserving data aggregation scheme for smart grid metering infrastructure protection. Int. J. Crit. Infrastruct. Prot. 2018, 22, 16–24. [Google Scholar] [CrossRef]
- Wang, X.D.; Meng, W.Z.; Liu, Y.N. Lightweight privacy-preserving data aggregation protocol against internal attacks in smart grid. J. Inf. Secur. Appl. 2020, 55, 102628. [Google Scholar] [CrossRef]
- Badr, M.M.; Al Amiri, W.; Fouda, M.M.; Mahmoud, M.M.; Aljohani, A.J.; Alasmary, W. Smart parking system with privacy preservation and reputation management using blockchain. IEEE Access 2020, 8, 150823–150843. [Google Scholar] [CrossRef]
- Shari, N.F.M.; Malip, A. State-of-the-art solutions of blockchain technology for data dissemination in smart cities: A comprehensive review. Comput. Commun. 2022. [Google Scholar] [CrossRef]
- Xie, J.; Tang, H.; Huang, T.; Yu, F.R.; Xie, R.; Liu, J.; Liu, Y. A survey of blockchain technology applied to smart cities: Research issues and challenges. IEEE Commun. Surv. Tutor. 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Alsunaidi, S.J.; Alhaidari, F.A. A survey of consensus algorithms for blockchain technology. In Proceedings of the 2019 International Conference on Computer and Information Sciences (ICCIS), Aljouf, Saudi Arabia, 3–4 April 2019; pp. 1–6. [Google Scholar]
- Huo, R.; Zeng, S.; Wang, Z.; Shang, J.; Chen, W.; Huang, T.; Wang, S.; Yu, F.R.; Liu, Y. A Comprehensive Survey on Blockchain in Industrial Internet of Things: Motivations, Research Progresses, and Future Challenges. IEEE Commun. Surv. Tutor. 2022. [Google Scholar] [CrossRef]
- Zhao, N.; Zhang, G. Privacy-Protected Certificateless Aggregate Signature Scheme in VANET. In Proceedings of the 2019 11th International Conference on Wireless Communications and Signal Processing (WCSP), Xi’an, China, 23–25 October 2019; pp. 1–6. [Google Scholar]
- Zhang, L.; Qin, B.; Wu, Q.; Zhang, F. Efficient many-to-one authentication with certificateless aggregate signatures. Comput. Netw. 2010, 54, 2482–2491. [Google Scholar] [CrossRef]
- Chen, H.; Wei, S.M.; Zhu, C.; Yang, Y. Secure certificateless aggregate signature scheme. J. Softw. 2015, 26, 1173–1180. [Google Scholar]
- Hu, C.; Wangan, S.; Bing, Z. Certificateless aggregate signature scheme. In Proceedings of the 2010 International Conference on E-Business and E-Government, Guangzhou, China, 7–9 May 2010; pp. 3790–3793. [Google Scholar]
- Du Hong-zhen, H.M.j.; Wen, Q.y. Efficient and provably-secure certificateless aggregate signature scheme. Acta Electonica Sin. 2013, 41, 72. [Google Scholar]
- Chen, Y.C.; Tso, R.; Mambo, M.; Huang, K.; Horng, G. Certificateless aggregate signature with efficient verification. Secur. Commun. Netw. 2015, 8, 2232–2243. [Google Scholar] [CrossRef]

| Notation | Description |
|---|---|
| Energy Storage Unit | |
| ESP | Energy Service Provider |
| priority | |
| SoC | |
| TCC | |
| Public Parameters | |
| master public values, master secret key | |
| Common State Value | |
| The Identity of | |
| Public Key and Private Key Pair | |
| Private Key | |
| Charging Request | |
| Aggregated Charging Request | |
| , | The Equation Weights |
| Priority Label | |
| Temporal Charging Slot | |
| Proof Value | |
| Public Value | |
| Masked Charging Request | |
| Shared Seed Value Between and | |
| Signature Credentials | |
| Signature | |
| Correctness Proof of The Aggregated Value | |
| Aggregated V | |
| Aggregated W | |
| Aggregated | |
| Maximum Available Power | |
| The Power Assigned to The In Terms of Priority Labels |
| Data | Size “Bytes” |
|---|---|
| Charging Demand | 16 |
| Timestamp | 8 |
| Individual Signature | 112 |
| Function | Time “ms” |
|---|---|
| Pairing | 3.25 |
| Hashing | 0.04 |
| Multiplication | 0.00 |
| Exponentiation | 0.38 |
| Addition | 0.00 |
| Phase | Entity | Total Operations | Computation Overhead “ms” |
|---|---|---|---|
| System Initialization Phase | (Off-line) | ||
| Submission Phase | 0.47 | ||
| Aggregation Phase | Aggregator | ||
| Computing Charging Schedules Phase | Simple Comparison | - |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Habbak, H.; Baza, M.; Mahmoud, M.M.E.A.; Metwally, K.; Mattar, A.; Salama, G.I. Privacy-Preserving Charging Coordination Scheme for Smart Power Grids Using a Blockchain. Energies 2022, 15, 8996. https://doi.org/10.3390/en15238996
Habbak H, Baza M, Mahmoud MMEA, Metwally K, Mattar A, Salama GI. Privacy-Preserving Charging Coordination Scheme for Smart Power Grids Using a Blockchain. Energies. 2022; 15(23):8996. https://doi.org/10.3390/en15238996
Chicago/Turabian StyleHabbak, Hany, Mohamed Baza, Mohamed M. E. A. Mahmoud, Khaled Metwally, Ahmed Mattar, and Gouda I. Salama. 2022. "Privacy-Preserving Charging Coordination Scheme for Smart Power Grids Using a Blockchain" Energies 15, no. 23: 8996. https://doi.org/10.3390/en15238996
APA StyleHabbak, H., Baza, M., Mahmoud, M. M. E. A., Metwally, K., Mattar, A., & Salama, G. I. (2022). Privacy-Preserving Charging Coordination Scheme for Smart Power Grids Using a Blockchain. Energies, 15(23), 8996. https://doi.org/10.3390/en15238996







