Design of a Logistics System with Privacy and Lightweight Verification
Abstract
1. Introduction
Background
2. Related Works and Requirement
2.1. Related Works
| P believes X, or P would be entitled to believe X. | |
| P sees X. Someone has sent a message containing X to P, who can read and repeat X. | |
| P once said X. P at some time sent a message including X. | |
| P has jurisdiction over X. P is an authority on X and should be trusted on this matter. | |
| This represents X combined with Y. | |
| The formula X is fresh, that is, X has not been sent in a message at any time before the current run of the protocol. | |
| P and Q may use the shared key K to communicate. | |
| The formula S is a secret known only to P and Q and possibly to principals trusted by them. |
2.2. Requirements
- (1)
- (2)
- Non-repudiation: In the information transmission process, if each identity is not authenticated, the sender and the receiver are vulnerable to being sent false information by an impersonation attack. Therefore, the non-repudiation of information is crucial to effectively prevent impersonation [4,12].
- (3)
- Anonymity: It is easy for buyer and seller to disclose information in the goods delivery process. Therefore, the contents should not disclose any information about the buyer and seller [13].
- (4)
- Integrity: In an unencrypted environment, information is easily tampered with in the transmission process, resulting in the receiver being vulnerable to the information received not being that sent by the original sender’s information. Therefore, the integrity of the information must be ensured during transmission [14].
- (5)
- (1)
- Modification attack: The attacker intercepts the information of the transmitting party and the receiving party, and modifies the contents of the shopping information, resulting in the loss of the transmitting party and the receiving party. Therefore, the transmitted information must be secure against modification in order to prevent such attacks.
- (2)
- Impersonation attack: The attacker uses a fake identity to disguise themselves as a sender and sends a fake message to the receiver, causing the receiver to receive a false message.
- (3)
- Man-in-the-middle-attack: The attacker establishes independent contact with both ends of the communication and exchanges the information so that both sender and receiver of the communication think that they are talking directly with each other through a private connection. In fact, the entire conversation is completely controlled by the attacker. In a man-in-the-middle attack, an attacker can intercept calls from both parties and insert new content.
- (4)
- Clone attack: An attacker steals items by copying a label and impersonating a deliverer to deliver a non-original item.
3. The Proposed Scheme
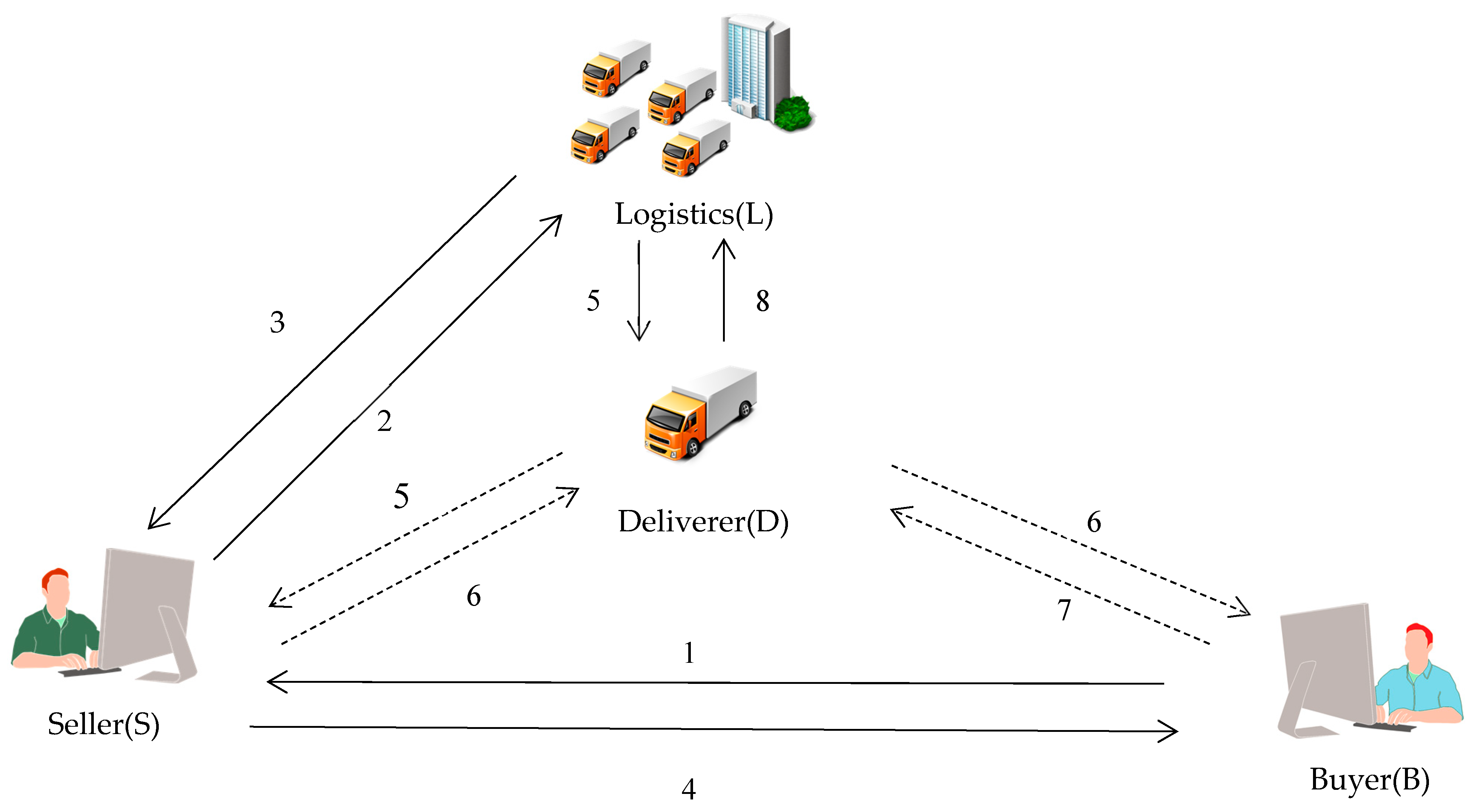
3.1. System Architecture
- (1)
- Seller: An online shopping store. People can shop there and the seller sends the goods to the buyer, who will sign for the delivered package.
- (2)
- Logistics: A company entrusted to deliver the packages to the buyer.
- (3)
- Deliverer: The logistics employee. They assist the logistics company to deliver the package to the buyer.
- (4)
- Buyer: Someone who buys something from the seller and who signs for the delivered package.
- (1)
- The buyer requests a product from the seller.
- (2)
- The seller provides the buyer and seller’s information to the logistics.
- (3)
- The logistics generates the transaction number and sends the buyer’s tag to the seller.
- (4)
- The seller sends the transaction number and the buyer’s tag to the buyer.
- (5)
- The logistics gives the tag of the seller’s information to the deliverer. The deliverer goes to the seller’s home and sends his/her identity to the seller.
- (6)
- The seller verifies the deliverer’s identity. The seller then transmits their signature and gives the goods and the buyer’s tag to the deliverer. The deliverer goes to the buyer’s house and sends his/her identity to the buyer.
- (7)
- The buyer transmits their signature to the deliverer.
- (8)
- The deliverer brings the buyer and the seller’s signature back to the logistics to verify the signature and complete the transaction.
3.2. Notations
| IDX | Identification of X |
| MX | X’s address and telephone information |
| MProduct | Product information |
| TID | Transaction number |
| TagX,Y | The tag used for X to Y |
| PukX,PrkX | The public key and private key of X, respectively |
| SigX,Y | The signature for X to Y |
| Ci | The ith ciphertext |
| P | Base point |
| SKXY | Session key between X and Y |
| (M) | Encrypt message M with session key SKXY |
| DprkX(M) | Decrypt message M with session key SKXY |
| SprkX(M) | Sign message M with X’s private key prkX |
| VpukX(M) | Verify message M with X’s public key pukX |
| EpukX(M) | Encrypt message M with X’s public key pukX |
| DprkX(M) | Decrypt message M with X’s private key prkX |
| h(M) | The message M calculated by one-way hash function |
| ⊕ | Exclusive-or operation for any two operands with same binary size |
| || | Concatenation operator |
| AB | Determine if A is equal to B |
 | A secure channel |
 | An insecure channel |
3.3. Initialization Phase
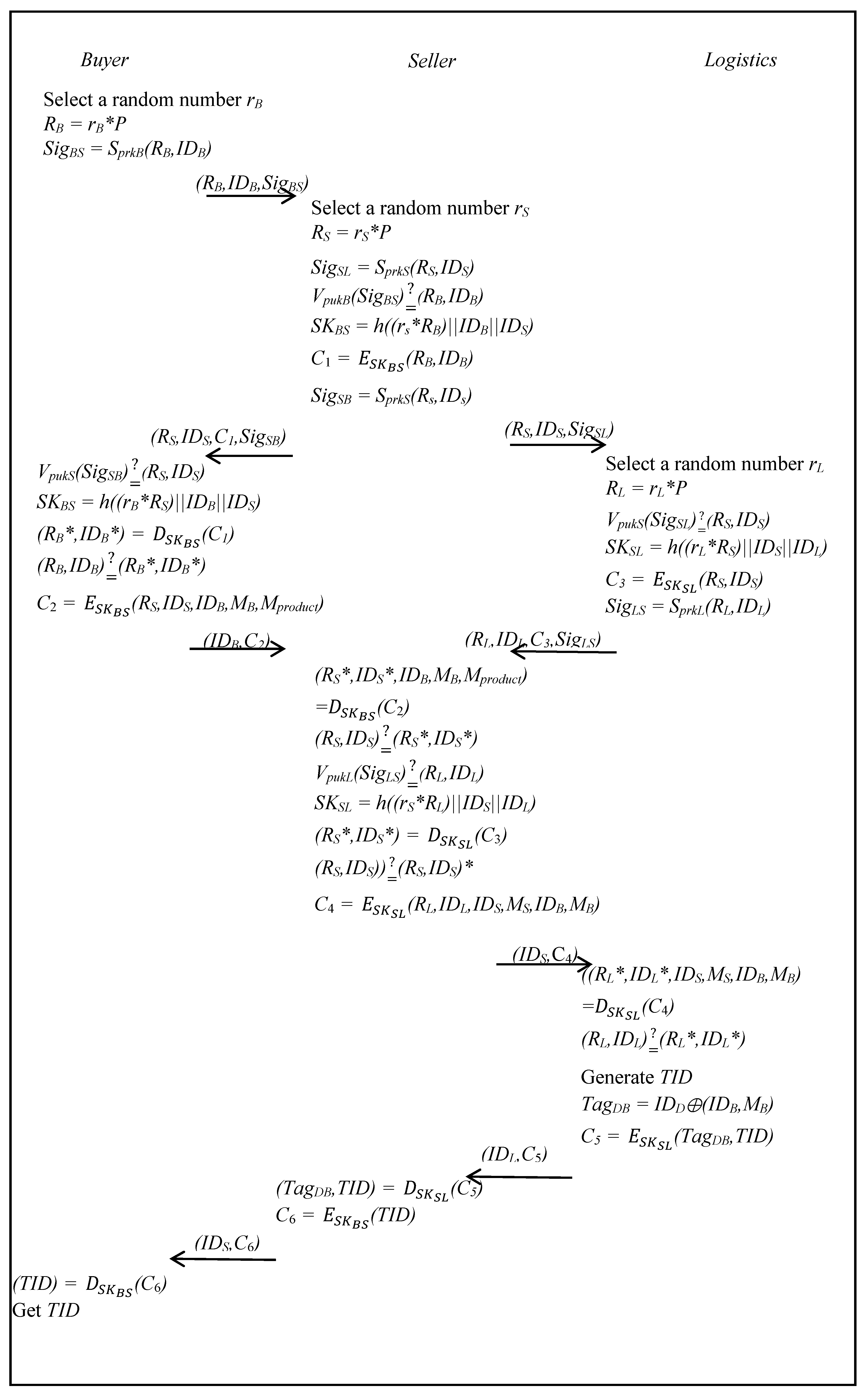
3.4. Session Key Generation Phase and Order Request Phase
- Step 1:
- The buyer selects a random rB and computes RB as follows:RB = rB*P,The buyer signs the (RB,IDB) with the private key PrkB, as follows:SigBS = SprkB(RB,IDB),The buyer then sends (RB,IDB,SigBS) to the seller.
- Step 2:
- The seller selects a random number rS and then computes RS and signs the (RS,IDS) with the private key PrkS, as follows:RS = rS*P,SigSL = SprkS(RS, IDS).The seller then sends (RS,IDS,SigSL) to logistics.The seller then verifies the SigBS with the public key PukB to determine whether the signagture is legal or not, as follows:If it passes the verification, the seller computes session key SKBS, as follows:uses the SKBS to encrypt (RB, IDB) with SKBS, as follows:SKBS = h((rs*RB)||IDB||IDS),and signs the (RS,IDS) with the private key PrkS, as follows:SigSB = SprkS(RS, IDS),The seller then sends (RS, IDS,C1,SigSB) to the buyer.
- Step 3:
- The logistics selects a random number rL, and computes RL, as follows:RL = rL*P.Logistics then verifies the SigSL with the public key PukS to determine whether the signagture is legal or not, as follows:If it holds, logistics computes session key SKSL, as follows:SKSL = h((rL*RS)||IDS||IDL).Then the logistics encrypts (RS,IDS) with SKSL, as follows:Next, logistics signs the (RL,IDL) with the private key PrkL, as follows:and sends (RL,IDL,C3,SigLS) to the seller.SigLS = SprkL(RL,IDL),
- Step 4:
- The buyer verifies the SigSB with the public key PukS to determine whether the signagture is legal or not, as follows:The buyer then computes session key SKBS, as follows:and uses the SKBS to decrypt C1, as follows:SKBS = h((rB*RS)||IDB||IDS),and determines whether (RB,IDB) is equal or not, as follows:The seller then encrypts (RS,IDS,IDB,MB,Mproduct) with SKBS, as follows:Then buyer then sends (IDB,C2) to the seller.
- Step 5:
- The seller decrypts C2 with SKBS, as follows:and then gets (RS*,IDS*), and determines whether (RS,IDS) is equal or not, as follows:The seller verifies the SigLS with the public key PukL to determine whether the signagture is legal or not, as followsIf it passes the verification, the seller computes SKSL, as follows:and decrypts C3 with SKSL, as follows:SKSL = h((rS*RL)||IDS||IDL),The seller gets (RS*,IDS*), determines whether (RS,IDS) is equal or not, as follows:If it holds, the seller encrypts (RL,IDL,IDS,MS,IDB,MB) with SKSL, as follows:and then sends (IDS,C4) to logistics.
- Step 6:
- The logistics decrypts C4 with SKSL, as follows:and then gets (RL*,IDL*) and determines whether (RL,IDL) is equal or not, as follows:Logistics generates TID and TagDB, and computes the following:and then uses the SKSL to encrypt (TagDB,TID), as follows:TagDB = IDD⊕(IDB,MB).then sends (IDL,C5) to the seller.
- Step 7:
- The seller decrypts C5 with SKSL, as follows:The seller encrypts (TID) with SKBS, as follows:then sends (IDS,C6) to the buyer.
- Step 8:
- The buyer decrypts C6 with SKBS, as follows:and then gets TID.
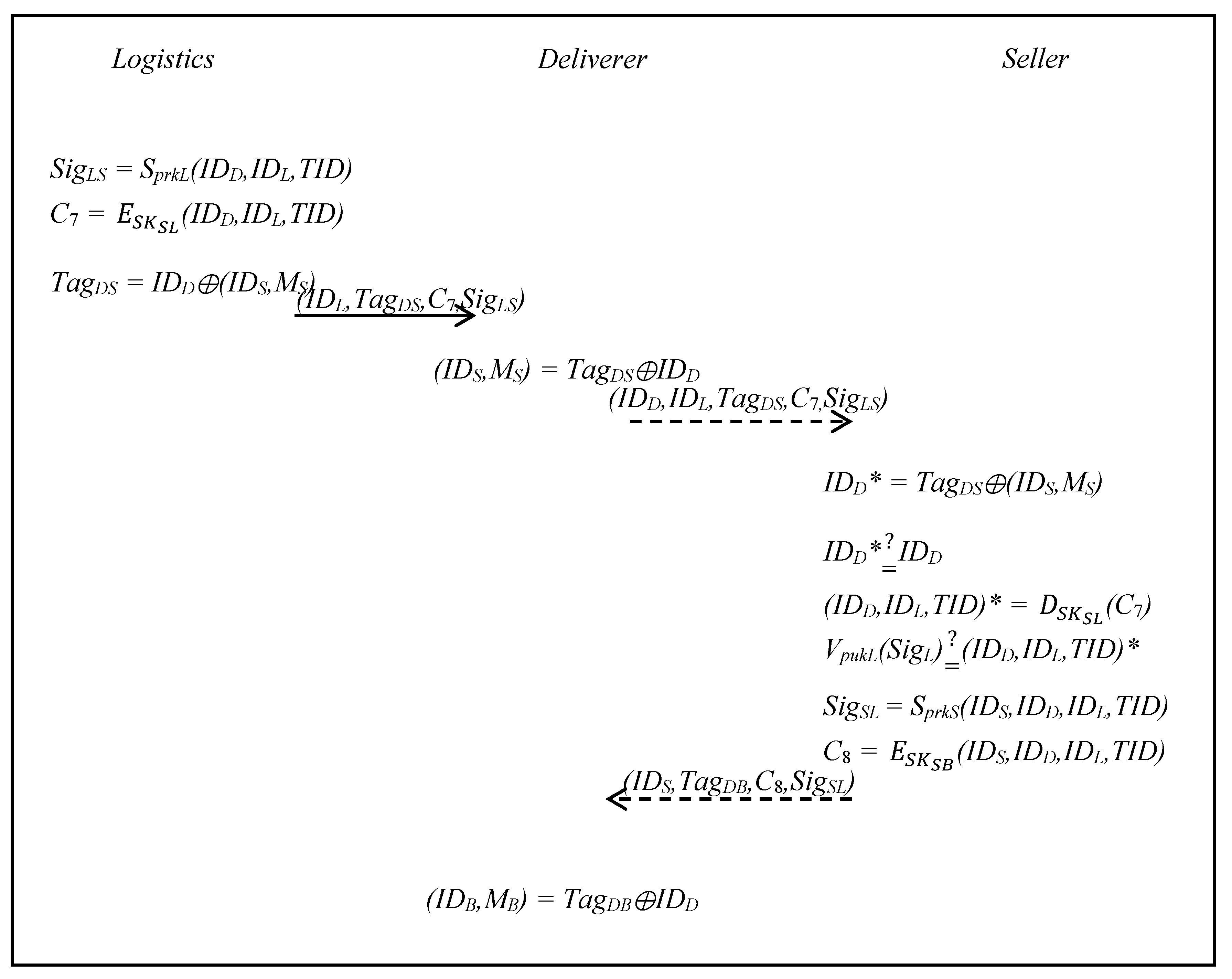
3.5. Package Collection Phase
- Step 1:
- The logistics signs (IDD,IDL,TID) with private key PrkL, as follows:SigLS = SprkL(IDD,IDL,TID),The logistics uses SKSL to encrypt (IDD,IDL,TID), as follows:then generates TagDS, as follows:and sends (IDL,TagDS,C7,SigLS) to the deliverer.TagDS = IDD⊕(IDS,MS),
- Step 2:
- The deliverer computes the following formula:and the deliverer can then get (IDS,MS).(IDS,MS) = TagDS⊕IDD,
- Step 3:
- The deliverer sends (IDD,IDL,TagDS,C7,SigLS) to the seller for verification and the seller computes IDD* as follows:and verifies whether IDD is equal or not, as follows:IDD* = TagDS⊕(IDS,MS),The seller decrypts C7 with SKSL, as follows:The seller verifies the SigLS with the public key PukL to determine whether the signagture is legal or not, as follows:If it passes the verification, the seller signs the (IDS,IDD,IDL,TID) with the private key PrkS, as follows:and uses SKSB to encrypt (IDS, DD, IDL,TID), as follows:SigSL = SprkS (IDS, IDD,IDL,TID),The seller then gives the goods and (IDS,TagDB,C8,SigSL) to the deliverer.
- Step 4:
- The deliverer computes as following formula:and gets (IDB,MB).(IDB,MB) = TagDB⊕IDD,
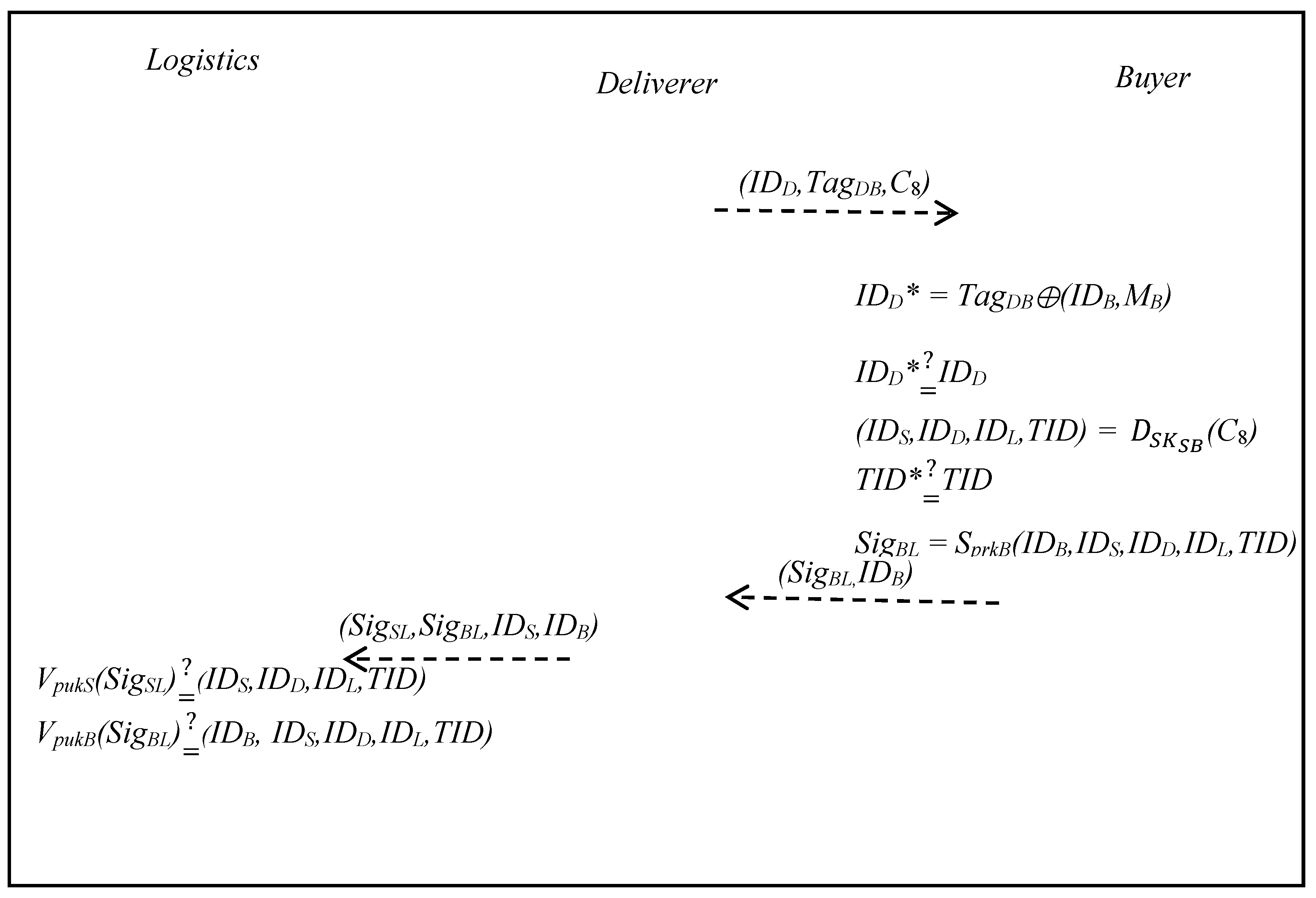
3.6. Product Transfer Phase
- Step 1:
- The deliverer sends the goods and (IDD, TagDB, C8) to the buyer to verify the identity, using the following formula:IDD* = TagDB⊕(IDB,MB),Once the deliverer has IDD*, they determine whether the IDD is equal or not, as follows:The buyer decrypts C8 with SKSB, as follows:and then gets TID* and determines whether the TID, which is stored in the session key generation and order request phase, is equal or not, as follows:The deliverer uses PrkB to sign (IDB,IDS,IDD,IDL,TID), as follows:SigBL = SprkB(IDB,IDS,IDD,IDL,TID),The buyer sends (SigBL, IDB) to the deliverer.
- Step 2:
- The deliverer returns to the logistics.Logistics verifies SigS with public key PukS, as follows:and then determines whether the signagture is legal or not.Logistics verifies SigB with public key PukB, as follows:and determines whether the signagture is legal or not.
4. Security Analysis and Discussion
4.1. Mutual Authentication Issue
| P|≡X | P believes X, or P would be entitled to believe X. |
| P⊲X | P sees X, someone has sent a message containing X to P, who can read and repeat X. |
| P|~X | P once said X. P at some time sent a message including X. |
| P|X | P has X as a public key. |
| PX | P and X may use the session key K to communicate |
| PX | P has jurisdiction over x. |
| #(X) | The formula X is fresh. |
| {X}K | The formula X encrypted by K. |
| G1 | S|≡SB |
| G2 | S|≡B|≡SB |
| G3 | B|≡SB |
| G4 | B|≡B|≡SB |
| G5 | S|≡SL |
| G6 | S|≡L|≡SL |
| G7 | L|≡SL |
| G8 | L|≡S|≡SL |
| G9 | S|≡IDB |
| G10 | S|≡B|≡IDB |
| G11 | B|≡IDS |
| G12 | B|≡S|≡IDS |
| G11 | L|≡IDS |
| G12 | L|≡S|≡IDS |
| G11 | S|≡IDL |
| G12 | S|≡L|≡IDL |
| M1 | ({RB,IDB}prkB,{RS,IDS,IDB,MB,Mproduct}SKBS), |
| M2 | ({RS,IDS}prkS,{RB,IDB}SKBS), |
| M3 | ({RS,IDS}prkS,{RL,IDL,IDS,MS,IDB,MB}SKSL), |
| M4 | ({RL,IDL}prkL,{RS,IDS}SKBS). |
| A1 | S|≡#(RB) |
| A2 | B|≡#(RB) |
| A3 | S|≡#(RS) |
| A4 | B|≡#(RS) |
| A5 | L|≡#(RS) |
| A6 | S|≡#(RS) |
| A7 | L|≡#(RL) |
| A8 | S|≡#(RL) |
| A9 | S|≡#SKBS |
| A10 | B|≡#SKBS |
| A11 | L|≡#SKSL |
| A12 | S|≡#SKSL |
| A13 | B|≡|S |
| A14 | S|≡|S |
| A15 | B|≡|B |
| A16 | S|≡|B |
| A17 | L|≡|L |
| A18 | S|≡|L |
| A19 | L|≡|S |
| A20 | S|≡|S |
| A21 | S|≡BSB |
| A22 | B|≡SSB |
| A23 | L|≡SSL |
| A24 | S|≡LSL |
| A25 | S|≡BIDB |
| A26 | B|≡SIDS |
| A27 | L|≡SIDS |
| A28 | S|≡LIDL |
- Seller S authenticates Buyer BBy M1 and the seeing rule, derive the following:S⊲ ({RB,IDB}prkB,{RS,IDS,IDB,MB,Mproduct }SKBS).By A1 and A2 and the freshness rule, derive the following:S|≡#({RB,IDB}prkB,{RS,IDS,IDB,MB,Mproduct }SKBS).By (Statement 1), A9, A13, and A14 and the message meaning rule, derive the following:S|≡B|~#({RB,IDB}pukB,{RS,IDS,IDB,MB,Mproduct }SKBS).By (Statement 2), (Statement 3), and the verification rule, derive the following:S|≡B|≡({RB,IDB}pukB,{RS,IDS,IDB,MB,Mproduct }SKBS.By (Statement 4) and the belief rule, derive the following:By (Statement 5), A21, and the jurisdiction rule, derive the following:By (Statement 6) and the belief rule, derive the following:S|≡B|≡IDB.By (Statement 7), A25, and the belief rule, derive the following:S|≡IDB.
- Buyer B authenticates Seller SBy M2 and the seeing rule, derive the following:B⊲({RS,IDS}prkS,{RB,IDB}SKBS).By A3, A4, and the freshness rule, derive the following:B |≡#({RS,IDS}prkS,{RB,IDB}SKBS).By (Statement 9), A10, A15, A16, and the message meaning rule, derive the following:B|≡S|~#({RS,IDS}pukS,{RB,IDB}SKBS).By (Statement 10), (Statement 11) and the verification rule, derive the following:B|≡S|≡({RS,IDS}prkS,{RB,IDB}SKBS).By (Statement 12) and the belief rule, derive the following:By (Statement 13), A22 and the jurisdiction rule, derive the following:By (Statement 14) and the belief rule, derive the following:B|≡S|≡IDSBy (Statement 15), A26 and the belief rule, derive the following:B|≡IDS.By (Statement 6), (Statement 8), (Statement 14), and (Statement 16), it is proved that buyer B and seller S authenticate each other in the proposed scheme. The seller authenticates the buyer by (5).If it passes the verification, the seller authenticates the legality of the buyer and then the buyer authenticates the seller by (14).
- Logistics L authenticates Seller SBy M3 and the seeing rule, derive the following:L⊲({RS,IDS}prkS, {RL,IDL,IDS,MS,IDB,MB}SKSL).By A5, A6, and the freshness rule, derive:L|≡#({RS,IDS}prkS, {RL,IDL,IDS,MS,IDB,MB}SKSL).By (Statement 17), A11, A17, A18, and the message meaning rule, derive the following:L|≡S|~#({RS,IDS}pukS, {RL,IDL,IDS,MS,IDB,MB}SKSL).By (Statement 18), (Statement 19), and the verification rule, derive the following:L|≡S|≡({RS,IDS}pukS, {RL,IDL,IDS,MS,IDB,MB}SKSL).By (Statement 20) and the belief rule, derive the following:By (Statement 21), A23, and the jurisdiction rule, derive the following:By (Statement 22) and the belief rule, derive the following:L|≡S|≡IDS.By (Statement 23), A27, and the belief rule, derive the following:L|≡IDS.
- Logistics L authenticates Seller SBy M4 and the seeing rule, derive the following:S⊲({RL,IDL}prkL, {RS,IDS}SKBS).By A7, A8, and the freshness rule, derive the following:S|≡#({RL,IDL}prkL, {RS,IDS}SKBS).By (Statement 25), A12, A19, A20 and the message meaning rule, derive the following:S|≡L|~#({RL,IDL}prkL, {RS,IDS}SKBS).By (Statement 26), (Statement 27), and the verification rule, derive the following:S|≡L|≡({RL,IDL}prkL, {RS,IDS}SKBS).By (Statement 28) and the belief rule, derive the following:By (Statement 29), A24, and the jurisdiction rule, derive the following:By (Statement 30) and the belief rule, derive the following:S|≡L|≡IDL.By (Statement 31), A28, and the belief rule, derive the following:S|≡IDL.By (Statement 22), (Statement 24), (Statement 30), and (Statement 32), it is proved that logistics L and seller S authenticate each other in the proposed scheme. The logistics authenticates the seller by (14):If it passes the verification, the logistics provider authenticates the legality of the seller and then the buyer authenticates the logistics as (21).
4.2. Non-Repudiation Issue
4.3. Anonymity Issue
4.4. Low Overhead Issue
4.5. Data Integrity Issue
4.6. Security Against Known Attacks
4.6.1. Modification Attack
- (1)
- The session key generation and order request phase is as follows:
C1 = (RB,IDB), (7) C3 = (RS,IDS), (12) C2 = (RS,IDS,IDB,MB,Mproduct), (18) C4 = (RL,IDL,IDS,MS,IDB,MB), (25) C5 = (TagDB,TID), (29) C6 = (TID). (31) - (2)
- Package collection phase:
C7 = (IDD,IDL,TID), (34) C8 = (IDS,IDD,IDL,TID). (42)
4.6.2. Impersonation Attack
- (1)
- The session key generation and order request phase is as follows:
SigBS = SprkB(RB,IDB), (2) SigSL = SprkS(RS,IDS), (4) SigSB = SprkS(RS,IDS), (8) SigLS = SprkL(RL,IDL). (13) - (2)
- Package collection phase:
SigSL = SprkS (IDS,IDD,IDL,TID). (41) - (3)
- Product transfer phase:
SigBL = SprkB(IDB,IDS,IDD,IDL,TID), (48)
4.6.3. Man-in-the-Middle Attack
4.6.4. Clone Attack
4.7. Computation Cost
| Tasy | The time required for an asymmetrical signature/verifying a signature. |
| Tsys | The time required for a symmetrical encryption/decryption operation. |
| Th | The time required for a one-way hash function. |
| Txor | The time required for an exclusive-or operation. |
| Tmul | The time required for a multiplication operation. |
4.8. Communication Cost
| Tsig | The time required to transmit a signature (1024 bits). |
| Tsys | The time required to transmit a symmetric encryption/decryption ciphertext (256 bits). |
| Txor | The time required to transmit an exclusive-or operation (80 bits). |
4.9. Storage Cost
| Tasy | The space required to storage an asymmetrical signature (1024 bits). |
| Tsys | The space required to storage a symmetrical encryption/decryption ciphertext (256 bits). |
| Th | The space required to storage a one-way hash function calculated message (256 bits). |
| Tmul | The space required to storage a multiplication calculated message (160 bits). |
| Tother | The space required to storage other messages (80 bits). |
5. Conclusions
- (1)
- The process of communication between buyers and sellers is mutual authentication.
- (2)
- The non-repudiation of the goods delivery process is achieved through the signature mechanism.
- (3)
- Personal information protection is achieved through exclusive-or operations.
- (4)
- Tags use lightweight authentication technology to reduce the computation cost, compared to related works.
Author Contributions
Funding
Conflicts of Interest
References
- Aijaz, A.; Bochow, B.; Dotzer, F.; Festag, A.; Gerlach, M.; Kroh, R.; Leinmuller, T. Attacks on inter vehicle communication systems—An analysis. In Proceedings of the 3rd International Workshop on Intelligent Transportation, Hamburg, Germany, 14–15 March 2006; pp. 189–194. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Chen, C.L.; Chiang, M.L.; Peng, C.C.; Chang, C.H.; Sui, Q.R. A Secure Mutual Authentication Scheme with Non-repudiation for Vehicular Ad Hoc Networks. Int. J. Commun. Syst. 2015, 30, e3081. [Google Scholar] [CrossRef]
- Cui, J.; She, D.; Ma, J.; Wu, Q.; Liu, J. A New Logistics Distribution Scheme Based on NFC. In Proceedings of the 2015 International Conference on Network and Information Systems for Computers, Wuhan, China, 23–25 January 2015; pp. 492–495. [Google Scholar]
- Cho, J.-S.; Jeong, Y.-S.; Park, S. Consideration on the brute-force attack cost and retrieval cost: A hash-based radio-frequency identification (RFID) tag mutual authentication protocol. Comput. Math. Appl. 2015, 69, 58–65. [Google Scholar] [CrossRef]
- Liu, S.; Wang, J. A Security-Enhanced Express Delivery System Based on NFC. In Proceedings of the 2016 13th IEEE International Conference on Solid-State and Integrated Circuit Technology, Hangzhou, China, 25–28 October 2016; pp. 1534–1536. [Google Scholar]
- Speranza, M.G. Trends in transportation and logistics. Eur. J. Oper. Res. 2018, 264, 830–836. [Google Scholar] [CrossRef]
- Gope, P.; Amin, R.; Hafizul Islam, S.K.; Kumar, N.; Bhalla, V.K. Lightweight and privacy-preserving RFID authentication scheme for distributed IoT infrastructure with secure localization services for smart city environment. Future Gener. Comput. Syst. 2018, 83, 629–637. [Google Scholar] [CrossRef]
- Liang, K.; Susilo, W. Searchable attribute-based mechanism with efficient data sharing for secure cloud storage. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1981–1992. [Google Scholar] [CrossRef]
- Das, A.K.; Goswami, A. A robust anonymous biometric-based remote user authentication scheme using smart cards. J. King Saud Univ. Comput. Inf. Sci. 2015, 27, 193–210. [Google Scholar] [CrossRef]
- Madhusudhan, R.; Hegde, M. Security bound enhancement of remote user authentication using smart card. J. Inf. Secur. Appl. 2017, 36, 59–68. [Google Scholar] [CrossRef]
- Qi, M.; Chen, J. A fresh Two-party Authentication Key Exchange Protocol for Mobile Environment. In Proceedings of the International Conference on Industrial Technology and Management Science, Tianjin, China, 27–28 March 2015; Volume 30, pp. 933–936. [Google Scholar]
- Ray, B.R.; Abawajy, J.; Chowdhury, M.; Alelaiwi, A. Universal and secure object ownership transfer protocol for the Internet of Things. Future Gener. Comput. Syst. 2017, 78, 838–849. [Google Scholar] [CrossRef]
- Rajput, U.; Abbas, F.; Eun, H.; Oh, H. A Hybrid approach for Efficient Privacy-Preserving Authentication in VANET. IEEE Access 2017, 5, 12014–12030. [Google Scholar] [CrossRef]
- Sharma, V.; Vithalkar, A.; Hashmi, M. Lightweight security protocol for chipless RFID in Internet of Things (IoT) applications. In Proceedings of the 2018 10th International Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 3–7 January 2018; pp. 468–471. [Google Scholar]
- Tu, Y.; Piramuthu, S. Lightweight non-distance-bounding means to address RFID relay attacks. Decis. Support Syst. 2017, 102, 12–21. [Google Scholar] [CrossRef]
- Whitmore, A.; Agarwal, A.; Da, X.L. The internet of things: A survey of topics and trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Wang, J.; Floerkemeier, C.; Sarma, S.E. Session-based security enhancement of RFID systems for emerging open-loop applications. Pers. Ubiquitous Comput. 2014, 18, 1881–1891. [Google Scholar] [CrossRef]
- Zhao, S.; Aggarwal, A.; Frost, R.; Bai, X. A survey of applications of identity-based cryptography in mobile ad-hoc networks. IEEE Commun. Surv. Tutor. 2012, 14, 380–400. [Google Scholar] [CrossRef]
| Party | Proof | Issuer | Holder | Verification | |
|---|---|---|---|---|---|
| Phase | |||||
| Session key generation and order request phase | (RB,IDB) | Buyer | Seller | VpukB(SigBS)(RB,IDB) | |
| (RS,IDS) | Seller | Buyer | VpukS(SigSB)(RS,IDS) | ||
| (RS,IDS) | Seller | Logistics | VpukS(SigSL)(RS,IDS) | ||
| (RL,IDL) | Logistics | Seller | VpukL(SigLS)(RL,IDL) | ||
| Package collection phase | (IDD,IDL,TID,SigL) | Logistics | Seller | VpukL(SigL)(IDD,IDL,TID) | |
| Product transfer phase | (IDS,IDD,IDL,TID,SigS) | Seller | Buyer | VpukS(SigS)(IDS,IDD,IDL,TID) | |
| (IDB,IDS,IDD,IDL,TID,SigB) | Buyer | Logistics | VpukB(SigB)(IDB,IDS,IDD,IDL,TID) | ||
| Party | Buyer | Seller | Logistics | Deliverer | |
|---|---|---|---|---|---|
| Phase | |||||
| Session key generation and order request phase | 2Tasy + 3Tsys + 1Th + 1Tmul | 4Tasy + 6Tsys + 2Th + 2Tmul | 2Tasy + 3Tsys + 1Th + 1Txor + 1Tmul | N/A | |
| Package collection phase | N/A | 2Tasy + 2Tsys + 1Txor | 1Tasy + 1Tsys + 1Txor | 2Txor | |
| Product transfer phase | 1Tasy + 1Tsys + 1Txor | N/A | 2Tasy | N/A | |
| Party | Message Length | Round | 3.5G (14 Mbps) | 4G (100 Mbps) | |
|---|---|---|---|---|---|
| Phase | |||||
| Session key generation and order request phase | 4Tsig + 6Tsys = 4 × 1024 + 6 × 256 = 5632 bits | 8 | 5632/14000 = 0.402 ms | 5632/100000 = 0.056 ms | |
| Package collection phase | 3Tsig + 3Tsys + 3Txor = 3 × 1024 + 3 × 256 + 3 × 80 = 4080 bits | 3 | 4080/14000 = 0.291 ms | 4080/100000 = 0.041 ms | |
| Product transfer phase | 3TSig + 1Tsys + 1Txor = 3 × 1024 + 1 × 256 + 1 × 80 = 3408 bits | 3 | 4432/14000 = 0.243 ms | 4432/100000 = 0.044 ms | |
| Party | Buyer | Seller | Logistics | Deliverer | |
|---|---|---|---|---|---|
| Phase | |||||
| Session key generation and order request phase | 1Tasy + 1Tsys + 1Th + 2Tmul + 4Tother = 2176 bits | 2Tasy + 3Tsys + 2Th + 3Tmul + 5Tother = 4208 bits | 1Tasy + 2Tsys + 1Th + 2Tmul + 7Tother = 2672 bits | N/A | |
| Package collection phase | N/A | 1Tasy + 1Tsys + 5Tother = 1680 bits | 1Tasy + 1Tsys + 6Tother = 1760 bits | 1Tother = 80 bits | |
| Product transfer phase | 5Tother = 400 bits | N/A | 1Tasy + 5Tother = 1424 bits | N/A | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.-L.; Lin, D.-P.; Chen, H.-C.; Deng, Y.-Y.; Lee, C.-F. Design of a Logistics System with Privacy and Lightweight Verification. Energies 2019, 12, 3061. https://doi.org/10.3390/en12163061
Chen C-L, Lin D-P, Chen H-C, Deng Y-Y, Lee C-F. Design of a Logistics System with Privacy and Lightweight Verification. Energies. 2019; 12(16):3061. https://doi.org/10.3390/en12163061
Chicago/Turabian StyleChen, Chin-Ling, Dong-Peng Lin, Hsing-Chung Chen, Yong-Yuan Deng, and Chin-Feng Lee. 2019. "Design of a Logistics System with Privacy and Lightweight Verification" Energies 12, no. 16: 3061. https://doi.org/10.3390/en12163061
APA StyleChen, C.-L., Lin, D.-P., Chen, H.-C., Deng, Y.-Y., & Lee, C.-F. (2019). Design of a Logistics System with Privacy and Lightweight Verification. Energies, 12(16), 3061. https://doi.org/10.3390/en12163061








