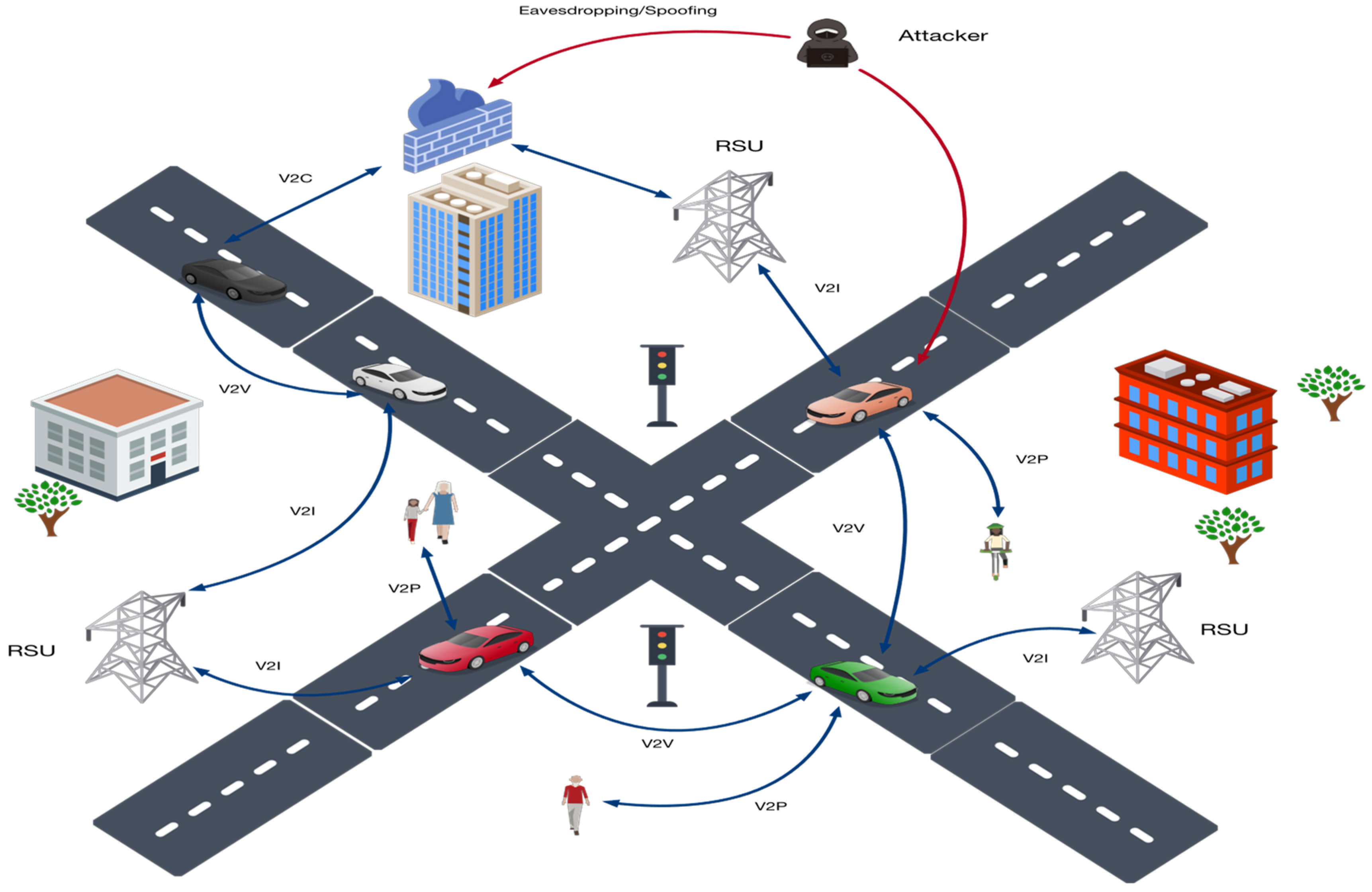
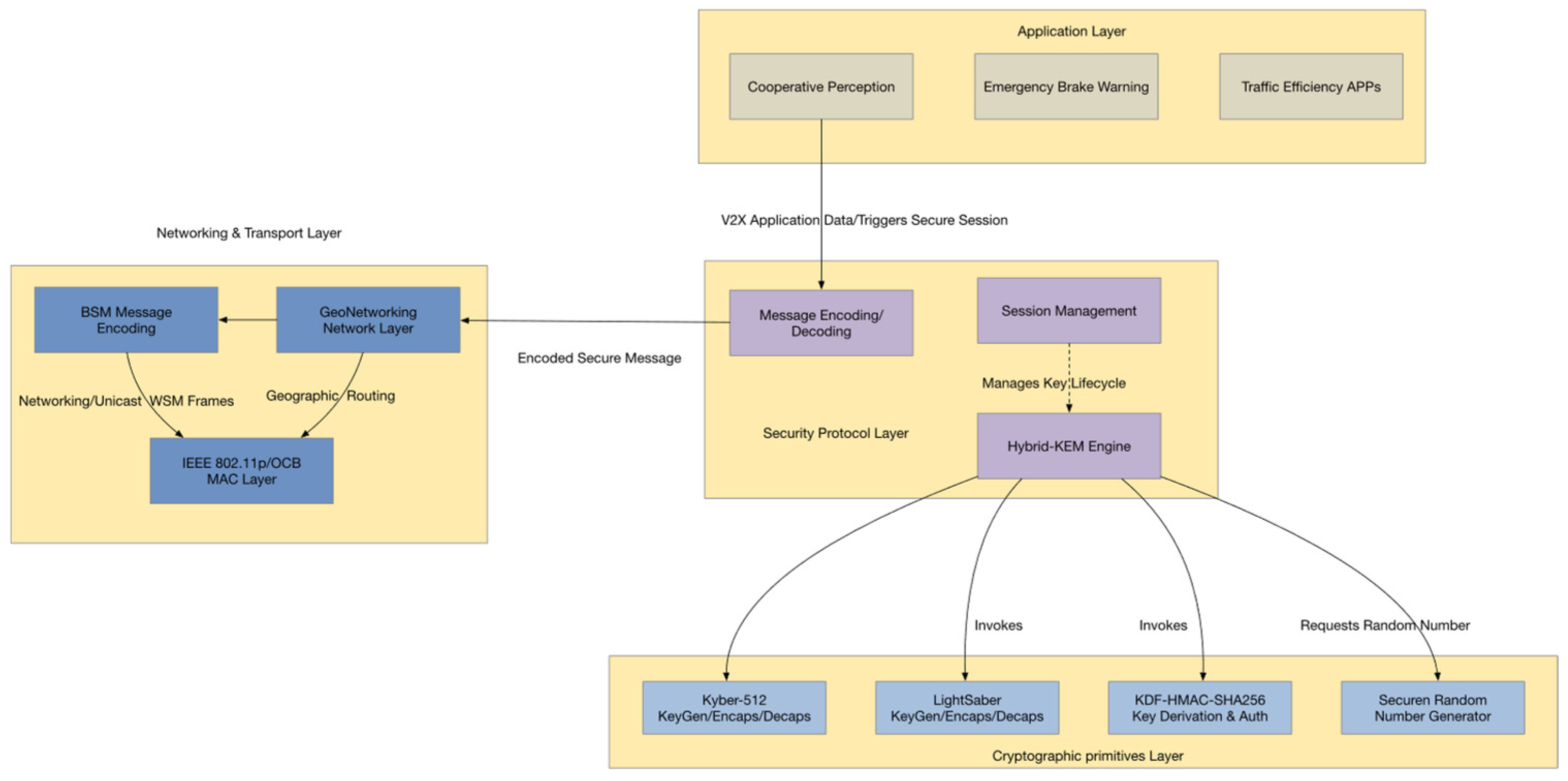
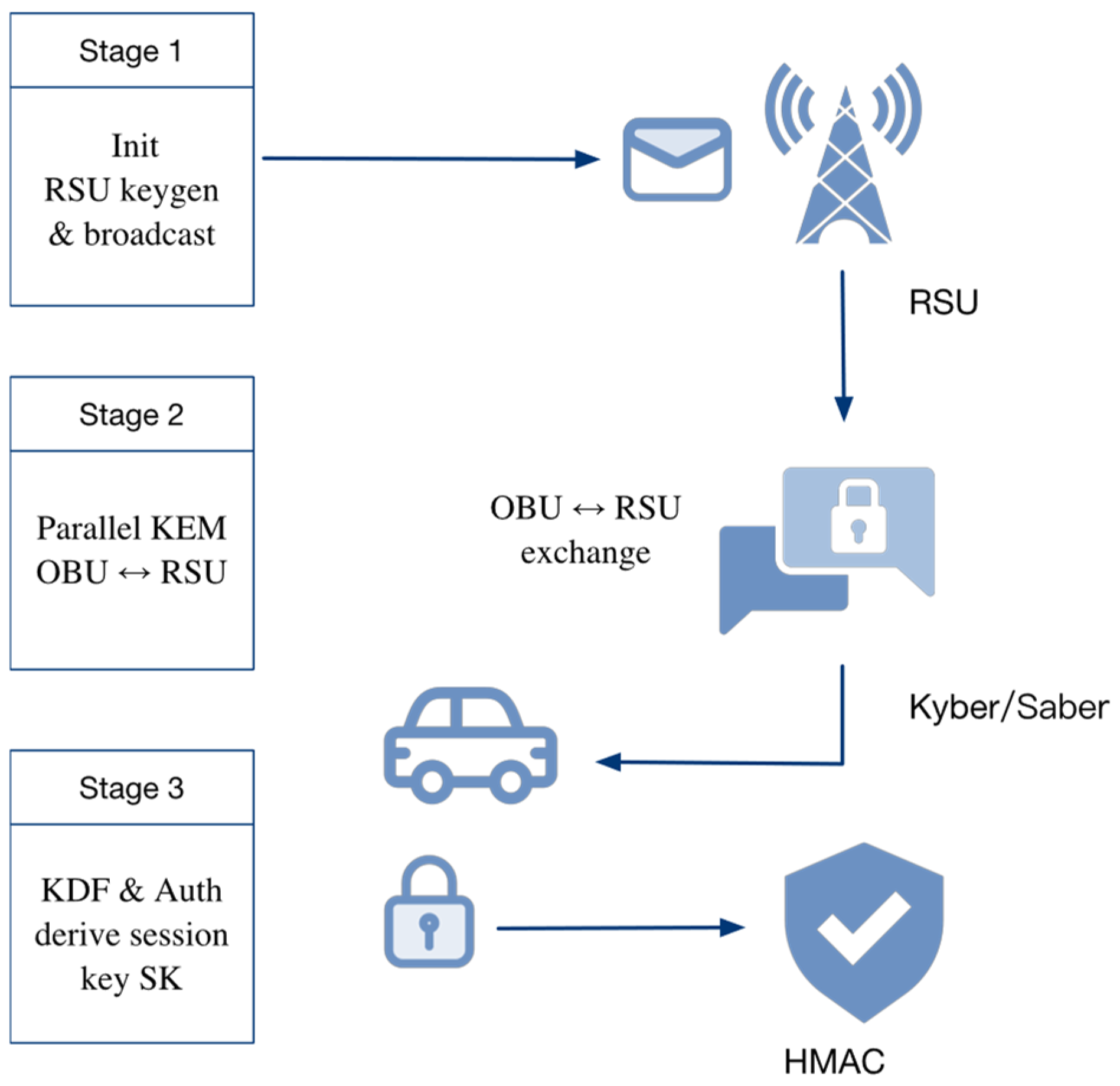
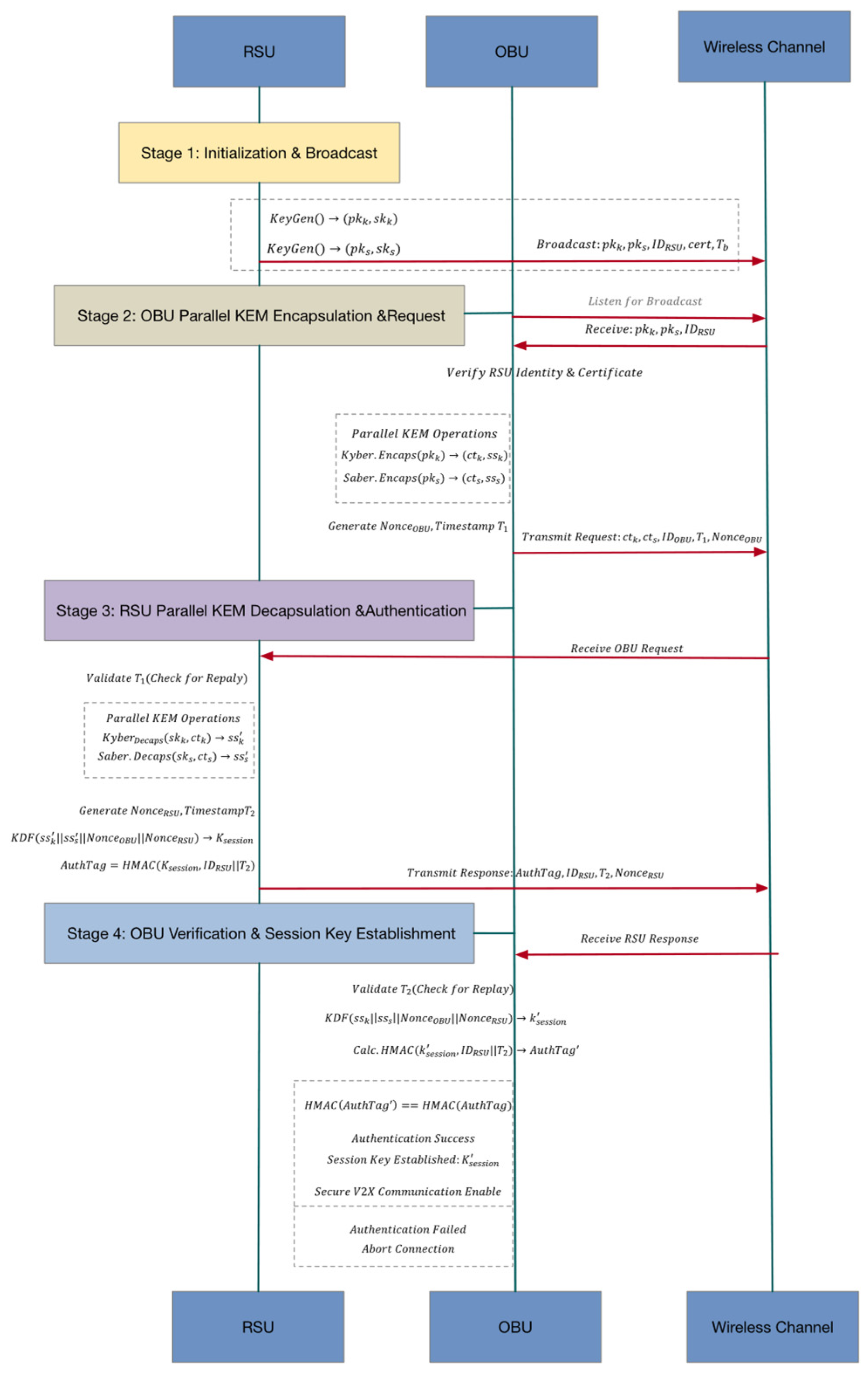
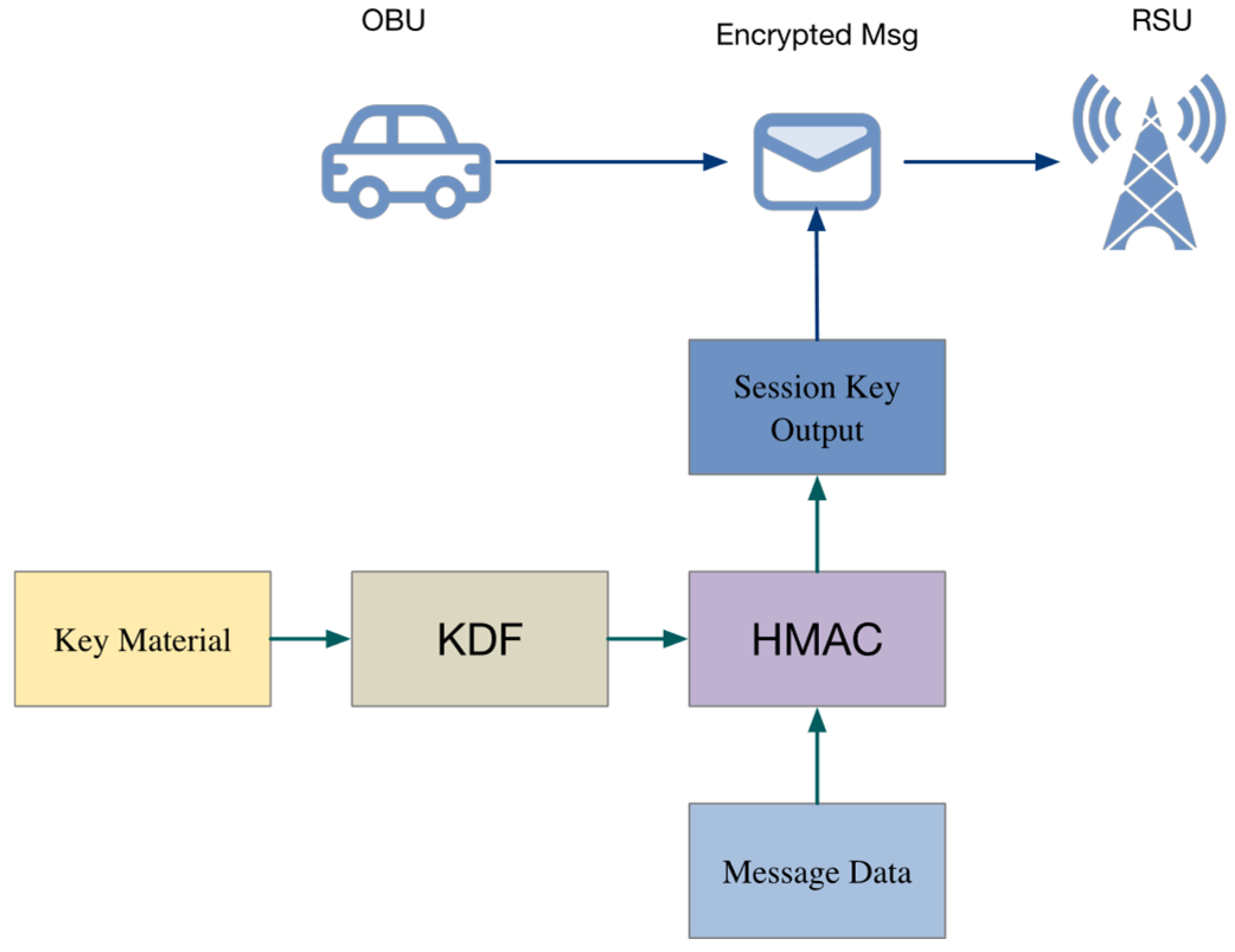
To meet the combined requirements of low latency, strong security, and lightweight computation in V2X, the proposed protocol realizes a hybrid key agreement through a carefully designed three-stage mechanism. The following sections provide a detailed description and formalization of the operations performed in each stage, including cryptographic operations, message formats, and verification procedures.
3.3.1. Algorithm Setup and Assumptions
To build a lightweight yet post-quantum secure key-agreement protocol for V2X, we unify the notation, cryptographic building blocks, and interface conventions used throughout the protocol. These definitions ensure clarity and implementability of the protocol logic.
The cryptographic primitives employed in this work are configured as follows. Kyber512 is adopted as the parameter set for the Kyber scheme, while LightSaber, the lightweight variant of Saber, is selected to improve suitability for resource-constrained embedded platforms. The hash function H() is instantiated with SHA-256, which also underpins the Key Derivation Function (KDF) (e.g., HKDF-SHA256) for deriving the final symmetric session keys. For message authentication, the protocol employs HMAC-SHA256 to ensure data integrity and authenticity. System entities are represented by unique identifiers, namely for the On-Board Unit (OBU) and for the Road-Side Unit (RSU). Furthermore, timestamps are incorporated to guarantee freshness and provide replay resistance, where denotes the handshake initiation time and represents the handshake response time.
- 2.
KEM interface definitions
We model each Key Encapsulation Mechanism (KEM) with the following standard interface that applies to both Kyber and Saber:
Key generation: —outputs a public key and a secret key .
Encapsulation: —given a recipient public key , outputs a ciphertext and a shared secret .
Decapsulation: —given a secret key and a ciphertext , recovers the shared secret .
Correctness requires for matching encapsulation/decapsulation pairs.
In the proposed protocol, both Kyber and Saber implement the above interface and are run in parallel during the encapsulation phase; their recovered shared materials are later combined (via the KDF) to form the final symmetric session key.
Security and implementation assumptions. We assume that: (i) private keys are securely stored and never exposed; (ii) a cryptographically secure random number generator is available for key generation and any nonce/entropy needs; and (iii) the underlying implementations of Kyber512 and LightSaber follow their respective specification best practices (padding, parameter choices, constant-time operations where required).
- 3.
Kyber Algorithm Workflow
Kyber is a Key Encapsulation Mechanism (KEM) based on the Module-Learning With Errors (MLWE) problem. Its core idea is that the value
computed from a public matrix
and a secret vector
, appears computationally indistinguishable from random to an adversary who does not know
. This property provides the foundation for public-key cryptographic security.
In this work, the Kyber512 parameter set is adopted as a reference, where
(modulus)
(polynomial dimension)
(module dimension)
(parameter for the centered binomial distribution used to sample secret and error vectors)
A random seed is used to deterministically generate the public matrix .
The Kyber scheme consists of Key Generation (KeyGen), Encapsulation (Encaps), and Decapsulation (Decaps), as illustrated in Algorithm 1.
| Algorithm 1. Kyber Algorithms |
| (a) Key Generation |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
| 6. |
|
| 7. | |
| 8. | |
| (b) Encapsulation |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
| 6. | |
| 7. | |
| 8. | |
| (c) Decapsulation |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
To ensure stability in the decapsulation phase, Kyber introduces an Error Checking Function to validate whether the error vector
remains within the acceptable range. Specifically, the function computes:
If the result exceeds the predefined threshold , the sample is considered invalid and the process is restarted; otherwise, the computation continues.
Moreover, Kyber’s randomness relies on the Centered Binomial Distribution (CBD). Both secret keys and error vectors are sampled using parameter . The final shared secret is derived using a Key Derivation Function (KDF), ensuring uniqueness and forward secrecy of session keys across multiple rounds of communication.
- 4.
Saber Algorithm Flow
Saber is a lightweight KEM based on the Module-Learning With Rounding (MLWR) problem. Unlike Kyber, Saber employs deterministic rounding operations instead of noise sampling in certain steps, thereby reducing computational overhead and power consumption. This makes Saber particularly suitable for deployment in resource-constrained vehicular networks (V2X terminals).
In this work, the LightSaber parameter set is adopted as a reference, with the following parameters:
(modulus)
(number of public key matrix columns)
(polynomial dimension)
random seed is used to initialize the pseudorandom generator for constructing the public matrix .
The Saber scheme includes Key Generation (KeyGen), Encapsulation (Encaps), and Decapsulation (Decaps), as shown in Algorithm 2.
| Algorithm 2. Saber Algorithms |
| (a) Key Generation |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
| 6. | |
| 7. | |
| (b) Encapsulation |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
| 5. | |
| 6. | |
| 7. | |
| 8. | |
| (c) Decapsulation |
| 1. | |
| 2. | |
| 3. | |
| 4. | |
During KeyGen, the public key matrix
is generated from the seed, and secret and error vectors are sampled from the centered binomial distribution. The public key is then computed as:
Compared with Kyber, Saber incorporates an approximate integer inner product optimization, replacing traditional floating-point multiplications. This approach enhances compatibility with embedded platforms while reducing power consumption.
During Encapsulation, given the public key and a random message , the ciphertext is generated, and the shared secret is derived via the KDF. During Decapsulation, the receiver uses the private key to recover an estimated message and recompute the shared secret .
- 5.
Error Check Function
To further guarantee correctness during the Decapsulation phase, both Kyber and Saber introduce an Error Checking Mechanism. The function CheckE(e) ensures that the sampled error vector does not exceed the predefined tolerance, thereby preventing decryption failures or incorrect key recovery.
In this work, the tolerance threshold is set to L. The function sums the absolute values of all coefficients of the error vector:
If
, the function returns False, meaning the sample is rejected and must be regenerated; otherwise, it returns True. The procedure is shown in Algorithm 3.
| Algorithm 3. Error Checking Function |
| 1. | |
| 2. | |
| 3. |
|
This mechanism is integrated into both Kyber and Saber during the key generation and decapsulation phases, thereby improving the robustness, correctness, and security of the overall system.
- 6.
Lightweight and Parallel Optimization Design
To enhance the deployability and responsiveness of the protocol on embedded platforms in vehicular networks, the following optimization strategies are introduced during key generation, encapsulation, and decapsulation processes:
Kyber Optimization Path
Introduce Number Theoretic Transform (NTT) to accelerate polynomial modular multiplication and convolution operations;
Significantly reduce key encapsulation and decapsulation times, improving overall protocol throughput.
Saber Optimization Path
Utilize the AVX2 instruction set to parallelize polynomial inner products and multiplications;
Vector Computation Optimization
Replace floating-point multiplications in Saber with integer approximate multiplications, reducing computational and energy overhead on embedded devices.
Sampling Function Optimization
Replace the original rejection sampling with Cumulative Distribution Table (CDT) table-based sampling, improving sampling efficiency and reducing entropy source consumption.
Error Term Limitation Mechanism
Integrate the checkE(e) process during key generation;
If the error exceeds the predefined threshold, resampling is performed to enhance protocol stability and ciphertext decapsulation success rate.
In summary, the core cryptographic primitives and interaction interfaces of the protocol have been fully defined. The complete key exchange procedure between OBU and RSU, including message sequence, parallel encapsulation/decapsulation operations, and authentication response mechanism, is illustrated in
Figure 4. This figure provides an overall framework for understanding the detailed operations of the three protocol stages.