An Experimental Performance Assessment of Galileo OSNMA †
Abstract
1. Introduction
2. OSNMA Overview
3. Experimental Setup
4. Results and Analysis
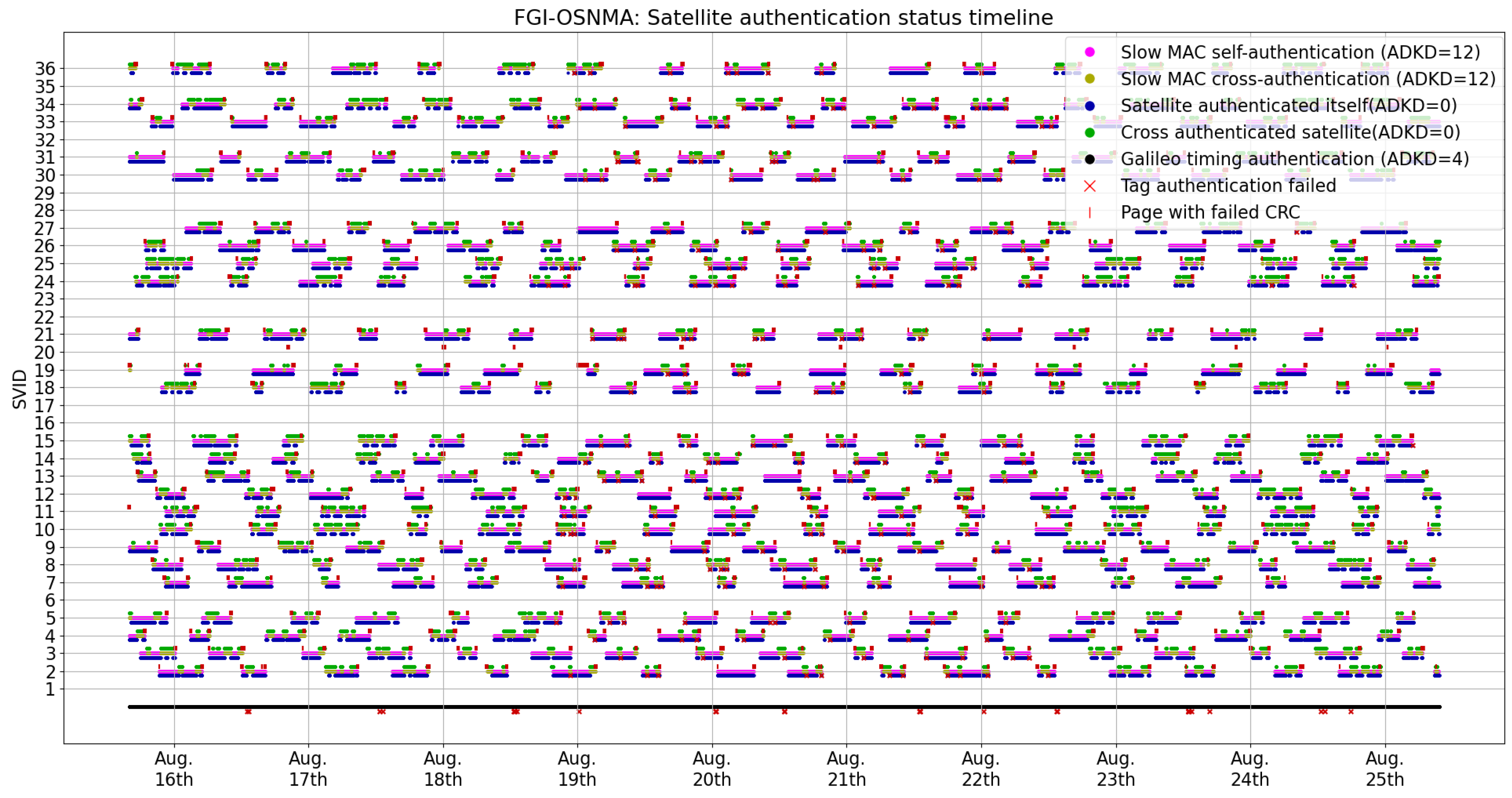
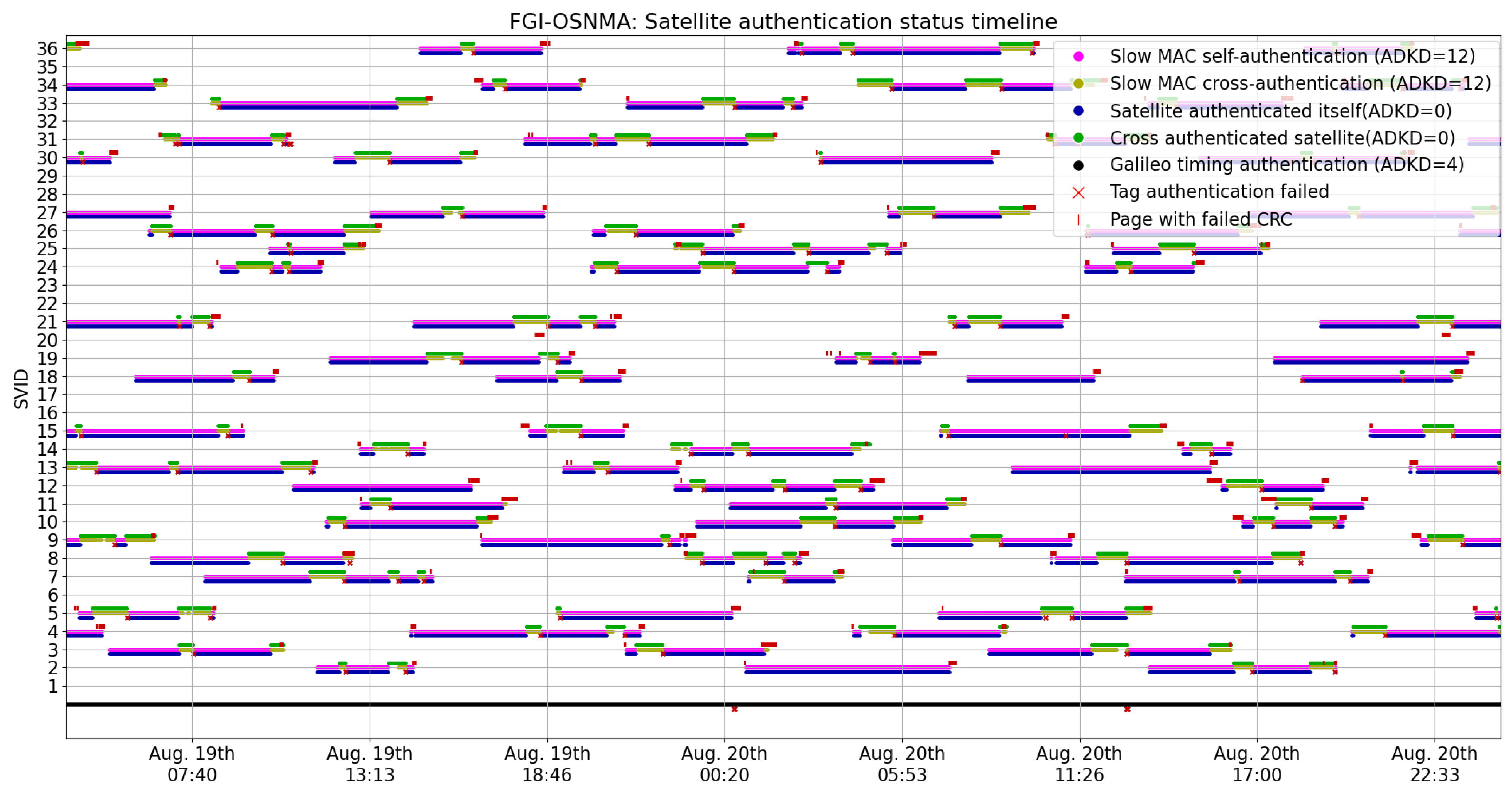
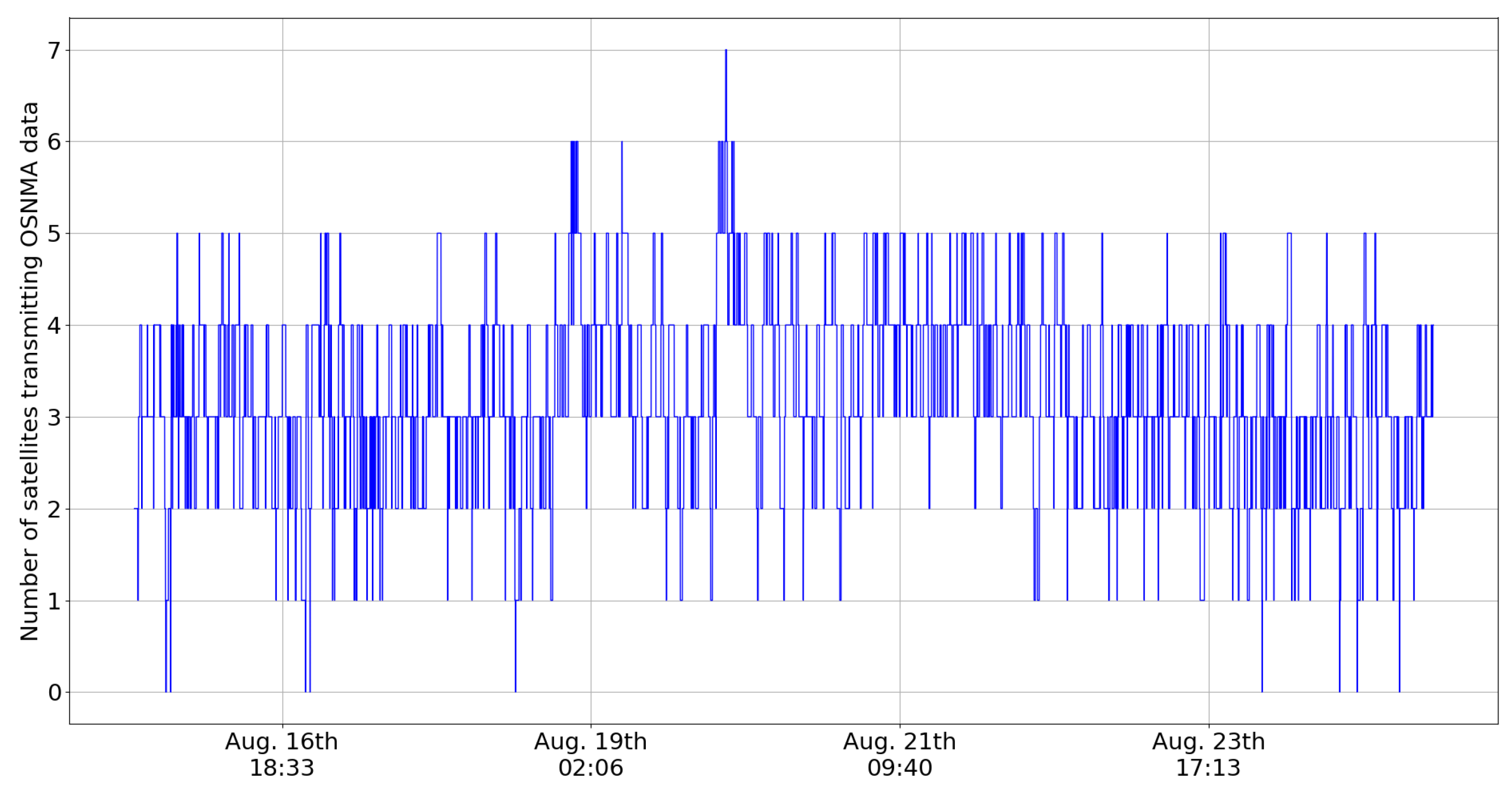
4.1. Authentication KPIs
- The Galileo constellation specific timing information (ADKD = 4) was authenticated 100% of the time. Even though there are a few ADKD = 4 tag authentication failures, because multiple satellites can transmit ADKD = 4 tags, these do not affect the overall authentication status.
- In the authentication scheme, the satellites alternate relatively frequently between self-authentication (which also implies that the satellite is transmitting OSNMA data) and cross-authentication, following a seemingly random pattern. In relation to this pattern, the specification states that it is indeed unpredictable for the user ([1]; Section 5.2).
- There are numerous cases of failed cyclic redundancy checks CRCs. These are associated with poor signal quality. In the dataset used in this study, these occurred exclusively when the satellites were rising over or disappearing below the horizon, in other words, in cases in which satellites have low elevation and therefore poor signal reception quality. It then comes as no surprise that we observed data reception problems from satellites with low elevation.
- Out of the 772,483 events related to authentication (i.e., not the CRCs failures), there are 272 instances where tag authentication failed. In these cases, the received tag consisted only of 0 bits. Given how the tags are generated by a hash function, they should be approximately uniformly distributed, making the reception of such tags in normal conditions close to impossible. This seems to be caused by data reception problems.
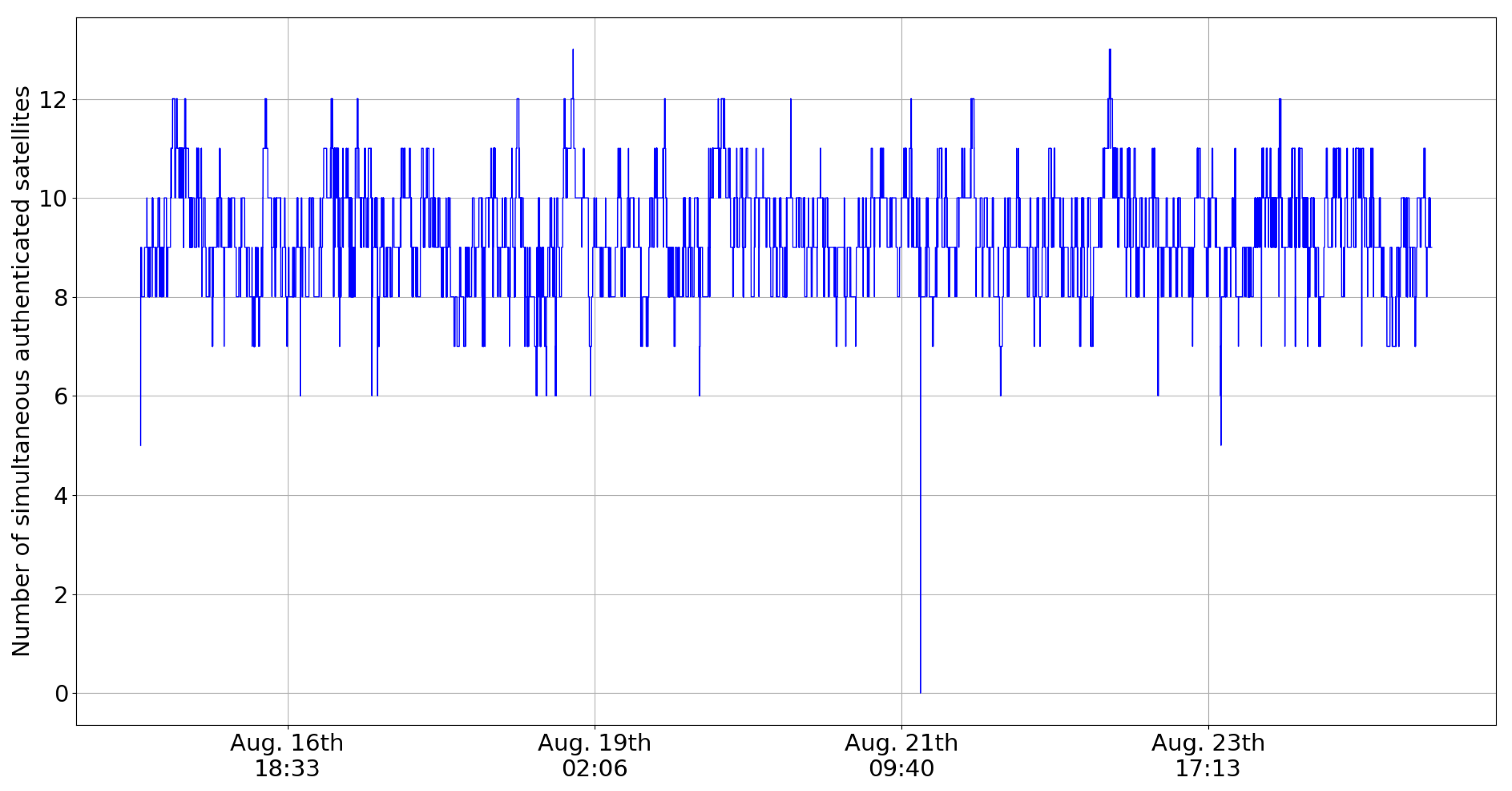
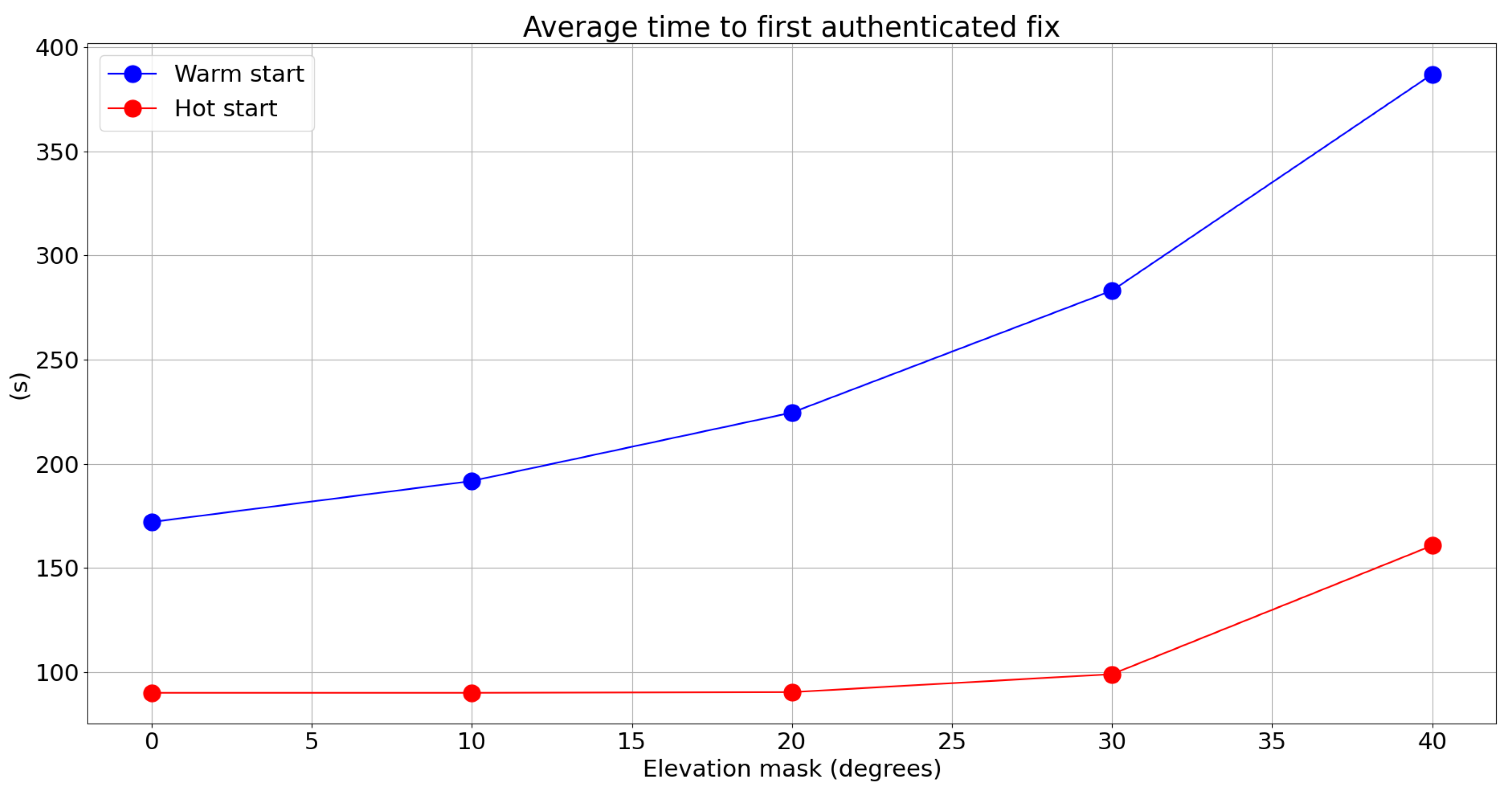
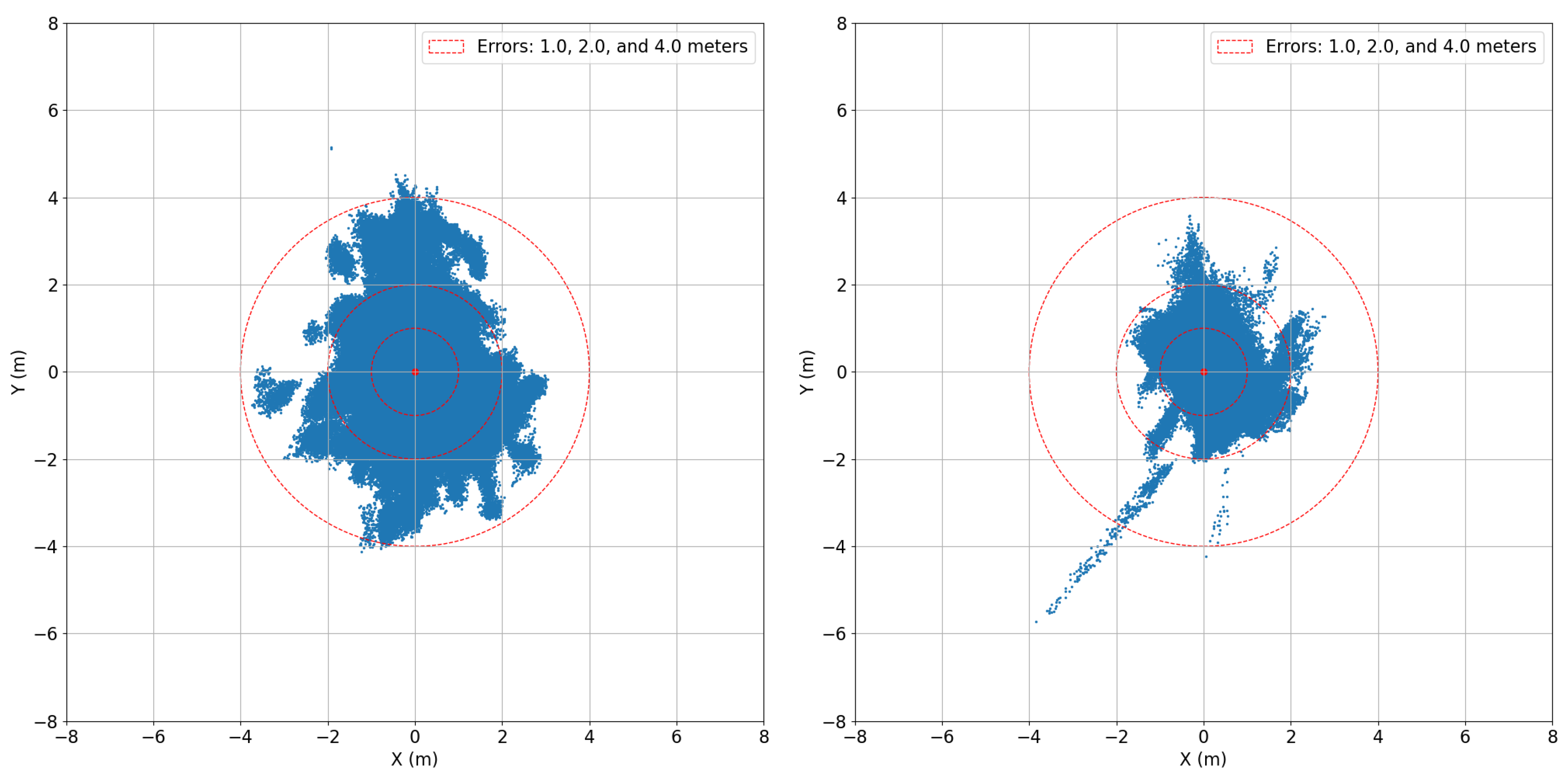
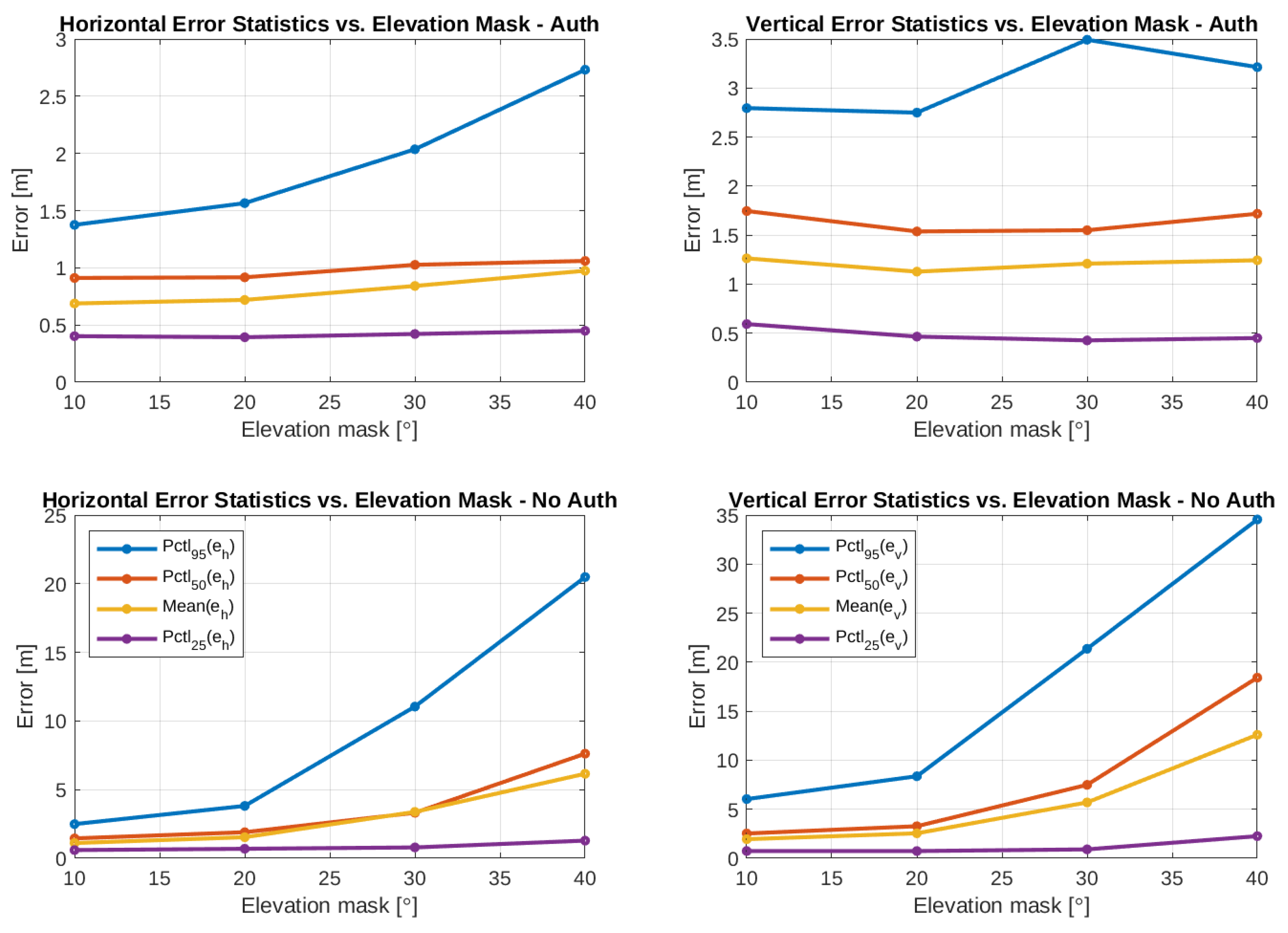
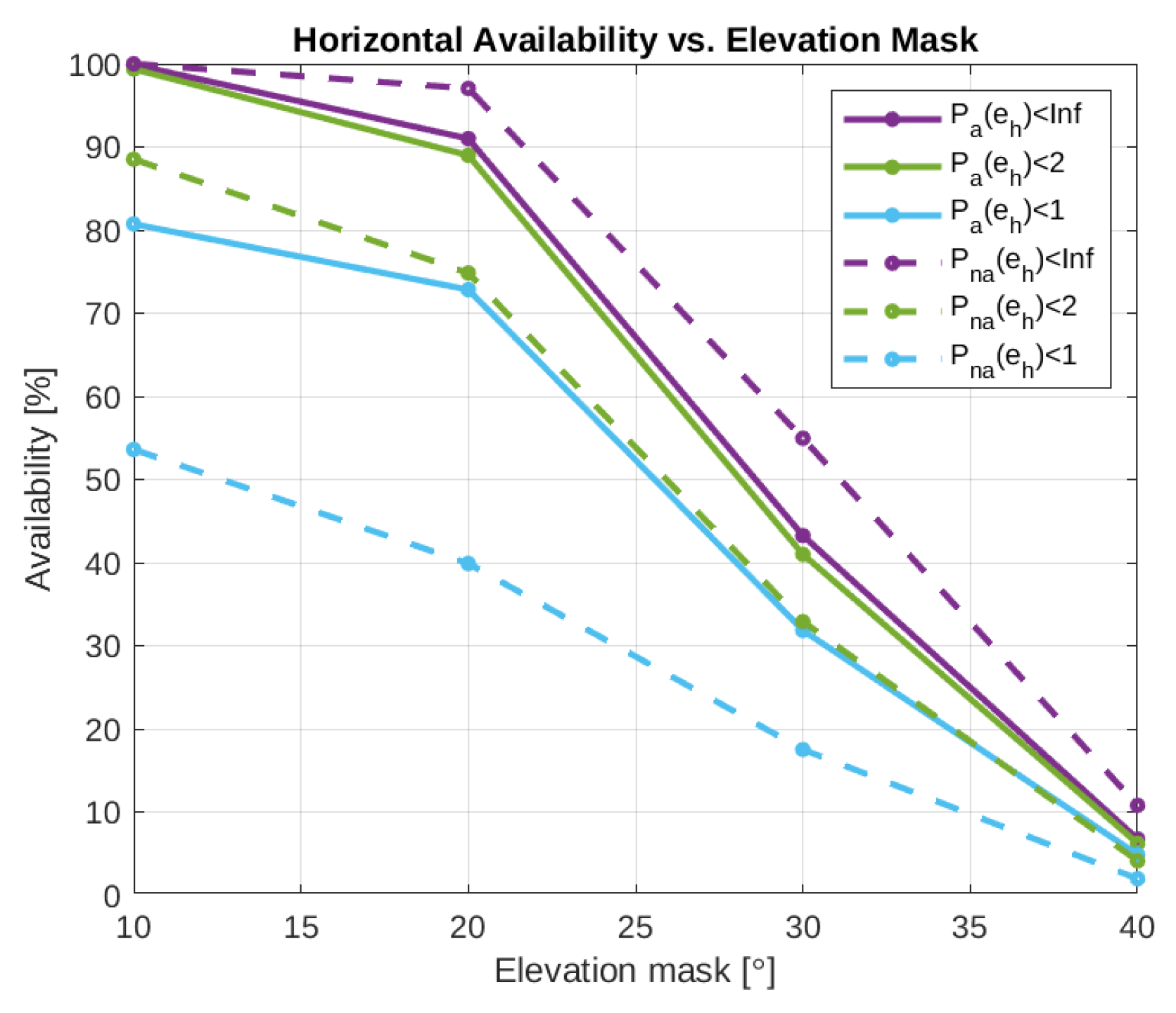
4.2. Authenticated Positioning KPIs
5. Discussion
- The data in the HKROOT message do not require fast reaction, not to mention that the root key (contained in the HKROOT) message transmission uses redundancy: all the satellites transmitting OSNMA data will transmit the same message, but they transmit the blocks in a different order. This makes the root key transmission both fast and robust. Therefore, the impact of receiving an incomplete HKROOT message from one satellite is not very significant. Some information from the HKROOT message is required to start the authentication process. Therefore, a delay in parsing the HKROOT due to an incomplete subframe will cause a delay in the first set of authentications. However, in the so-called hot-start case (which is the usual one), the receiver has stored a previous HKROOT, and, as long as the TESLA key chain does not change, the receiver can start the authentication immediately without the need to wait for the HKROOT messages. Therefore, moderate navigation page drops have little effect on the HKROOT processing.
- If the key (contained in the MACK message) in the subframe is incomplete, it is not possible to authenticate the previous set of tags immediately. However, all the satellites transmit the same key, not to mention that the receiver may wait for the next key, from which it can recover the missing key with hash iteration. Therefore, page drops affecting the key have minimal effect.
- The tags are the critical part of the transmission: they are the most important part of the authentication process and cannot be recovered later. The tags are naturally independent of each other, meaning that, even if some of the tags are missing due to dropped pages, the others can still be extracted. Also, multiple satellites may transmit a tag for the same satellite. Therefore, OSNMA offers some redundancy for protecting the data. We consider missing tags due to dropped pages to be the worst-case scenario. However, in our experiments, we found barely any problem with this.
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- European Union. Galileo Open Service Navigation Message Authentication (OSNMA) Signal-in-Space Interface Control Document (SIS ICD) Issue 1.1. 2023. Available online: https://www.gsc-europa.eu (accessed on 6 December 2023).
- European Union. Galileo Open Service Navigation Message Authentication (OSNMA) Receiver Guidelines Issue 1.1. 2023. Available online: https://www.gsc-europa.eu (accessed on 6 December 2023).
- ESRIUM Project Web Page. Available online: https://esrium.eu/ (accessed on 31 January 2023).
- Fernández-Hernández, I.; Ashur, T.; Rijmen, V.; Sarto, C.; Cancela, S.; Calle, D. Toward an Operational Navigation Message Authentication Service: Proposal and Justification of Additional OSNMA Protocol Features. In Proceedings of the 2019 European Navigation Conference (ENC), Warsaw, Poland, 9–12 April 2019. [Google Scholar] [CrossRef]
- Fernández-Hernández, I.; Rijmen, V.; Seco-Granados, G.; Simon, J.; Rodríguez, I.; Calle, J.D. A Navigation Message Authentication Proposal for the Galileo Open Service. Navigation 2016, 63, 85–102. [Google Scholar] [CrossRef]
- Margaria, D.; Marucco, G.; Nicola, M. A first-of-a-kind spoofing detection demonstrator exploiting future Galileo E1 OS authentication. In Proceedings of the 2016 IEEE/ION Position, Location and Navigation Symposium (PLANS), Savannah, GA, USA, 11–14 April 2016. [Google Scholar] [CrossRef]
- Motella, B.; Nicola, M.; Damy, S. Enhanced GNSS Authentication Based on the Joint CHIMERA/OSNMA Scheme. IEEE Access 2021, 9, 121570–121582. [Google Scholar] [CrossRef]
- Motallebighomi, M.; Sathaye, H.; Singh, M.; Ranganathan, A. Cryptography Is Not Enough: Relay Attacks on Authenticated GNSS Signals. arXiv 2022, arXiv:2204.11641. [Google Scholar]
- O’Driscoll, C.; Fernández-Hernández, I. Mapping bit to symbol unpredictability in convolutionally encoded messages with checksums, with application to galileo OSNMA. In Proceedings of the 33rd International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2020), Online, 22–25 September 2020; pp. 3751–3765. [Google Scholar]
- Nicola, M.; Motella, B.; Pini, M.; Falletti, E. Galileo OSNMA Public Observation Phase: Signal Testing and Validation. IEEE Access 2022, 10, 27960–27969. [Google Scholar] [CrossRef]
- Gamba, M.T.; Nicola, M.; Motella, B. Computational Load Analysis of a Galileo OSNMA-Ready Receiver for ARM-Based Embedded Platforms. Sensors 2021, 21, 467. [Google Scholar] [CrossRef] [PubMed]
- Motella, B.; Gamba, M.T.; Nicola, M. A Real-time OSNMA-ready Software Receiver. In Proceedings of the 2020 International Technical Meeting of the Institute of Navigation, San Diego, CA, USA, 21–24 January 2020. [Google Scholar] [CrossRef]
- Gamba, M.T.; Nicola, M.; Motella, B. Galileo OSNMA: An implementation for ARM-based embedded platforms. In Proceedings of the 2020 International Conference on Localization and GNSS (ICL-GNSS), Tampere, Finland, 2–4 June 2020. [Google Scholar] [CrossRef]
- Cucchi, L.; Damy, S.; Paonni, M.; Nicola, M.; Gamba, M.T.; Motella, B.; Fernandez-Hernandez, I. Assessing Galileo OSNMA Under Different User Environments by Means of a Multi-Purpose Test Bench, Including a Software-defined GNSS Receiver. In Proceedings of the 34th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2021), St. Louis, MO, USA, 20–24 September 2021. [Google Scholar] [CrossRef]
- Sarto, C.; Pozzobon, O.; Fantinato, S.; Montagner, S.; Fernández-Hernández, I.; Simon, J.; Calle, J.D.; Díaz, S.C.; Walker, P.; Burkey, D.; et al. Implementation and Testing of OSNMA for Galileo. In Proceedings of the 30th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2017), Portland, OR, USA, 25–29 September 2017. [Google Scholar] [CrossRef]
- Cucchi, L.; Damy, S.; Paonni, M.; Nicola, M.; Motella, B. Receiver Testing for the Galileo E1 OSNMA and I/NAV Improvements. In Proceedings of the 35th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2022), Denver, CO, USA, 19–23 September 2022; pp. 808–819. [Google Scholar]
- Damy, S.; Cucchi, L.; Paonni, M. Impact of OSNMA Configurations, Operations and User’s Strategies on Receiver Performances. In Proceedings of the 35th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2022), Denver, CO, USA, 19–23 September 2022; pp. 820–827. [Google Scholar]
- Cancela, S.; Calle, J.D.; Fernández-Hernández, I. CPU consumption analysis of TESLA-based navigation message authentication. In Proceedings of the 2019 European Navigation Conference (ENC), Warsaw, Poland, 9–12 April 2019; pp. 1–6. [Google Scholar]
- Seco-Granados, G.; Gómez-Casco, D.; López-Salcedo, J.A.; Fernández-Hernández, I. Detection of replay attacks to GNSS based on partial correlations and authentication data unpredictability. Gps Solut. 2021, 25, 33. [Google Scholar] [CrossRef]
- Cancela, S.; Navarro, J.; Calle, D.; Reithmaier, T.; Chiara, A.D.; Broi, G.D.; Fernández-Hernández, I.; Seco-Granados, G.; Simón, J. Field testing of GNSS user protection techniques. In Proceedings of the 32nd International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2019), Miami, FL, USA, 16–20 September 2019; pp. 1824–1840. [Google Scholar]
- Götzelmann, M.; Köller, E.; Viciano-Semper, I.; Oskam, D.; Gkougkas, E.; Simon, J. Galileo open service navigation message authentication: Preparation phase and drivers for future service provision. NAVIGATION J. Inst. Navig. 2023, 70. [Google Scholar] [CrossRef]
- Galan, A.; Fernandez-Hernandez, I.; Cucchi, L.; Seco-Granados, G. OSNMAlib: An Open Python Library for Galileo OSNMA. In Proceedings of the 2022 10th Workshop on Satellite Navigation Technology (NAVITEC), Online, 5–7 April 2022; pp. 1–12. [Google Scholar] [CrossRef]
- Estevez, D. Galileo-Osnma. 2022. Available online: https://github.com/daniestevez/galileo-osnma (accessed on 6 December 2023).
- osnmaPython. 2023. Available online: https://github.com/astromarc/osnmaPython (accessed on 6 December 2023).
- Hammarberg, T.; García, J.M.V.; Alanko, J.N.; Bhuiyan, M.Z.H. FGI-OSNMA: An Open Source Implementation of Galileo’s Open Service Navigation Message Authentication. In Proceedings of the 36th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2023), Denver, CO, USA, 11–15 September 2023; pp. 3774–3785. [Google Scholar]
- Septentrio. mosaic-X5 Reference Guide. 2023. Applicable to Version 4.14.0 of the Firmware. Available online: https://www.septentrio.com/resources/mosaic-X5/mosaic-X5+Firmware+v4.14.0+Reference+Guide.pdf (accessed on 31 December 2023).
- Papadimitratos, P.; Jovanovic, A. GNSS-based positioning: Attacks and countermeasures. In Proceedings of the MILCOM 2008—2008 IEEE Military Communications Conference, San Diego, CA, USA, 16–19 November 2008; pp. 1–7. [Google Scholar]
- Curran, J.T.; Bavaro, M.; Closas, P.; Navarro, M. On the threat of systematic jamming of GNSS. In Proceedings of the 29th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2016), Portland, OR, USA, 12–16 September 2016; pp. 313–321. [Google Scholar]
- Schmidt, D.; Radke, K.; Camtepe, S.; Foo, E.; Ren, M. A survey and analysis of the GNSS spoofing threat and countermeasures. ACM Comput. Surv. (CSUR) 2016, 48, 1–31. [Google Scholar] [CrossRef]
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Hammarberg, T.; García, J.M.V.; Alanko, J.N.; Bhuiyan, M.Z.H. An Experimental Performance Assessment of Galileo OSNMA. In Proceedings of the 2023 International Conference on Localization and GNSS (ICL-GNSS), Castellon, Spain, 6–8 June 2023; pp. 1–7. [Google Scholar]
- Perrig, A.; Tygar, J.; Perrig, A.; Tygar, J. TESLA broadcast authentication. In Secure Broadcast Communication: In Wired and Wireless Networks; Springer: Boston, MA, USA, 2003; pp. 29–53. [Google Scholar]
- Eledlebi, K.; Yeun, C.Y.; Damiani, E.; Al-Hammadi, Y. Empirical studies of TESLA protocol: Properties, implementations, and replacement of public cryptography using biometric authentication. IEEE Access 2022, 10, 21941–21954. [Google Scholar] [CrossRef]
- FGI. Dataset Used in the Paper. 2023. Available online: https://zenodo.org/records/10259098 (accessed on 5 December 2023).
- FGI. Repository of the FGI-OSNMA. 2023. Available online: https://github.com/nlsfi/fgi-osnma (accessed on 27 November 2023).
- Takasu, T.; Yasuda, A. Development of the low-cost RTK-GPS receiver with an open source program package RTKLIB. In Proceedings of the International Symposium on GPS/GNSS, Seogwipo-si, Republic of Korea, 4–6 November 2009; Volume 1, pp. 1–6. [Google Scholar]



| Statistic | Value |
|---|---|
| Simultaneous authenticated satellites: 5% percentile | 8 |
| Simultaneous authenticated satellites: average | 9.33 |
| Simultaneous authenticated satellites: 95% percentile | 11 |
| Percentage of authenticated fixes | 99.996% |
| Self-authentications out of all ADKD = 0 authentications | 49.2% |
| Cross-authentications out of all ADKD = 0 authentications | 50.8% |
| Elevation Mask | Number of Authenticated Fixes | Authenticated Sats. Count Percentiles: 5%, 50%, 95% |
|---|---|---|
| 0° | 99.996% | 8, 9, 11 |
| 5° | 99.993% | 7, 9, 11 |
| 10° | 99.993% | 6, 8, 10 |
| 20° | 99.319% | 4, 6, 8 |
| 30° | 72.385% | 3, 4, 6 |
| 40° | 20.280% | 1, 3, 4 |
| Elevation Mask | Warm-Start Percentiles: 10%, 50%, 90% | Hot-Start Percentiles: 10%, 50%, 90% |
|---|---|---|
| 0° | 120, 150, 240 | 90, 90, 90 |
| 10° | 120, 180, 270 | 90, 90, 90 |
| 20° | 150, 210, 330 | 90, 90, 90 |
| 30° | 150, 240, 420 | 90, 90, 120 |
| 40° | 180, 300, 690 | 90, 90, 270 |
| Number of Satellites Transmitting OSNMA Data | August 2023 | October 2022 |
|---|---|---|
| Average | 6.78 | 5.49 |
| 0.1% percentile | 3 | 1 |
| 1% percentile | 4 | 2 |
| 5% percentile | 5 | 3 |
| 95% percentile | 9 | 7 |
| Elev. Mask [°] | [m] | RMSE [m] 3D | Av. # Sats. | Horiz. Avail. (P(eh) < d) [%] | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Horiz. | Vert. | 3D | ||||||||
| Auth | 10 | 1.375 | 2.795 | 2.929 | 1.745 | 7.062 | 80.720 | 99.371 | 99.870 | 99.890 |
| 20 | 1.565 | 2.749 | 3.037 | 1.721 | 5.220 | 72.829 | 88.992 | 90.837 | 91.003 | |
| 30 | 2.036 | 3.493 | 4.073 | 2.035 | 4.321 | 31.842 | 40.987 | 42.902 | 43.245 | |
| 40 | 2.732 | 3.213 | 4.348 | 2.229 | 4.087 | 4.859 | 6.224 | 6.572 | 6.748 | |
| No Auth | 10 | 2.490 | 6.036 | 6.351 | 2.937 | 7.490 | 53.610 | 88.524 | 99.974 | 100.000 |
| 20 | 3.814 | 8.367 | 9.085 | 4.341 | 5.434 | 39.890 | 74.832 | 92.760 | 97.034 | |
| 30 | 11.049 | 21.364 | 24.564 | 12.094 | 4.430 | 17.510 | 32.898 | 43.659 | 54.949 | |
| 40 | 20.489 | 34.554 | 45.499 | 21.522 | 4.140 | 1.972 | 4.122 | 6.160 | 10.795 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hammarberg, T.; García, J.M.V.; Alanko, J.N.; Bhuiyan, M.Z.H. An Experimental Performance Assessment of Galileo OSNMA. Sensors 2024, 24, 404. https://doi.org/10.3390/s24020404
Hammarberg T, García JMV, Alanko JN, Bhuiyan MZH. An Experimental Performance Assessment of Galileo OSNMA. Sensors. 2024; 24(2):404. https://doi.org/10.3390/s24020404
Chicago/Turabian StyleHammarberg, Toni, José M. Vallet García, Jarno N. Alanko, and M. Zahidul H. Bhuiyan. 2024. "An Experimental Performance Assessment of Galileo OSNMA" Sensors 24, no. 2: 404. https://doi.org/10.3390/s24020404
APA StyleHammarberg, T., García, J. M. V., Alanko, J. N., & Bhuiyan, M. Z. H. (2024). An Experimental Performance Assessment of Galileo OSNMA. Sensors, 24(2), 404. https://doi.org/10.3390/s24020404






