1. Introduction
After a major disaster, it is very likely that access to some areas can be extremely difficult due to the damage caused by the disaster itself, road congestion or blockages, or even the contamination of dangerous products. This was the case of the Beirut port explosion in Lebanon in 2020 that caused several causalities, more than 7000 injured people, and left about 30,000 homeless [
1]. In this context, an alternative strategy to circumvent the aforementioned accessibility difficulties is to use drones to perform tasks such as the distribution of drugs and food, the detection of ground conditions, and to search for victims. They can also quickly access hard-to-reach areas. An extensive study in [
2] demonstrates the capabilities, performance outcomes and barriers of using drones in the context of humanitarian logistics.
In such a context, the search for victims is a crucial operation and must be well-planned and carried out with extreme efficiency to save lives. The search for victims can be supported by the use of drones. Moreover, the search can be boosted by using a fleet of drones equipped with optical and thermal cameras, flying in a coordinate swarm. This allows them to share updated information about the area, to be more efficient in scanning the area, and also to save energy using a special flight organization. As shown in [
3], energy consumption can be reduced by applying a V-shaped formation with leader replacements, which is inspired by bird flight.
The search for victims using drone swarms involves not only solving a path planning problem [
4], but also solving an optimization problem for finding the route that minimizes/maximizes a given criterion, which is the main focus of this study. More specifically, this study proposes the Drone Swarms Routing Problem (DSRP) and consists of defining routes for drone swarms in order to maximize the number of victims identified. The novelties of the DSRP are the consideration of the cooperative and decentralized flight of drone swarms, where they decide on the fly if they scan a location together or not. The interest of using such a strategy is to cover faster an area and to save energy, by means of an appropriate swarm organization. Civil drones still have low autonomy, which makes scanning large areas difficult. Moreover, the hydrogen technology for drones is not yet operational. This study extends the work of [
5], in which, drones fly independently of each other with routes predefined by a control center.
A computational model to solve the DSRP is proposed here, using the concept of Multi-Agents Systems (MAS), where drones are agents able to analyze information about the post-disaster area, and smartly select the next search location to perform the search for victims. For such a purpose, a Drone Swarm Heuristic (DSH) is applied to carry out the decision step of the drones. The proposed method is tested over a case study inspired by the Beirut port explosion in 2020. Numerical experiments considering offline and online versions of the method are presented. In the former, the input data are predefined, while in the latter, data changes during the execution of the model. The DSRP solutions produced by the proposed method are also observed in the robot simulator CoppeliaSim [
6] to simulate their execution step-by-step.
This study makes several contributions, in particular, we propose:
the new DSRP to search for victims in post-disaster scenarios;
a computational model based on multi-agent systems;
an offline and online heuristics for the DSRP;
solutions are tested using the CoppeliaSim simulator;
an adaptation of instances proposed in [
5] for DSRP.
The remainder of this paper is organized as follows. The Drone Swarms Routing Problem is defined in
Section 2. In
Section 3, closely related studies are presented. The proposed DSRP computational model and heuristic method are detailed in
Section 4. Numerical experiments, concluding remarks and future works are, respectively, given in
Section 5 and
Section 6.
2. The Drone Swarms Routing Problem
The Drone Swarms Routing Problem (DSRP) is defined on a complete and simple graph built over a post-disaster area. Each search area is a vertex which has an expected number of victims and a victim identification probability . The set of edges is , where is the shortest path between i and j. Moreover, each edge is weighted by a related cost that represents the battery consumption of a single-drone flight starting from vertex i to j. Let be a homogeneous fleet of m drones, in which each drone has a range limit A according to its battery capacity, a battery recharge time R and an associated base to perform the take-off, land and recharge operations. A specific drone searches for victims on a search location during a period of time . The identification operation follows a binomial distribution . As a consequence of the binomial distribution, search areas may be visited more than once and this visit can also be performed by the same drone. Another characteristic of the searches is that, at the same period of time, more than one drone (drone swarm) can scan for victims over the same search area. This latter characteristic is actually a relaxation of the problem that, on one hand, can improve the effectiveness of victim identification, but, on the other hand, it increases the search space of solutions to the problem, making the problem even more complex.
The DSRP considers a trajectory as a direct flight from a vertex i to another vertex j, consuming of the battery. Trajectories can be performed by a drone swarm flying in a V-shaped formation with leader replacements. A “trip” in the DSRP is a circuit of a drone that departs from its base, flies to search areas, performs victim detection, and returns to the base. In the DSRP the whole operation of a drone may include multiple trips and there is a maximum time T allowed for this operation. The objective of the DSRP is to define routes for a fleet of drones in order to maximize the expected number of detected victims.
The DSRP involves some assumptions to facilitate the modeling and analysis of the problem. The first relies on the drone movements which are constrained to two dimensions, assuming a flat surface or environment. This simplifies the spatial representation and allows efficient route planning within a 2D space. The second assumption is the communication between drones which is always considered available. This second assumption enables information sharing and real-time coordination, which facilitates efficient swarm behavior and collaboration during routing tasks. On the other hand, a more realistic communication model could be taken into account as a constraint in our model. In summary, the focus is on the decision optimization problem, and this first approach does not consider speed and altitude variation. However, since the speed and altitude are constant, the solutions generated belong to the set of feasible ones.
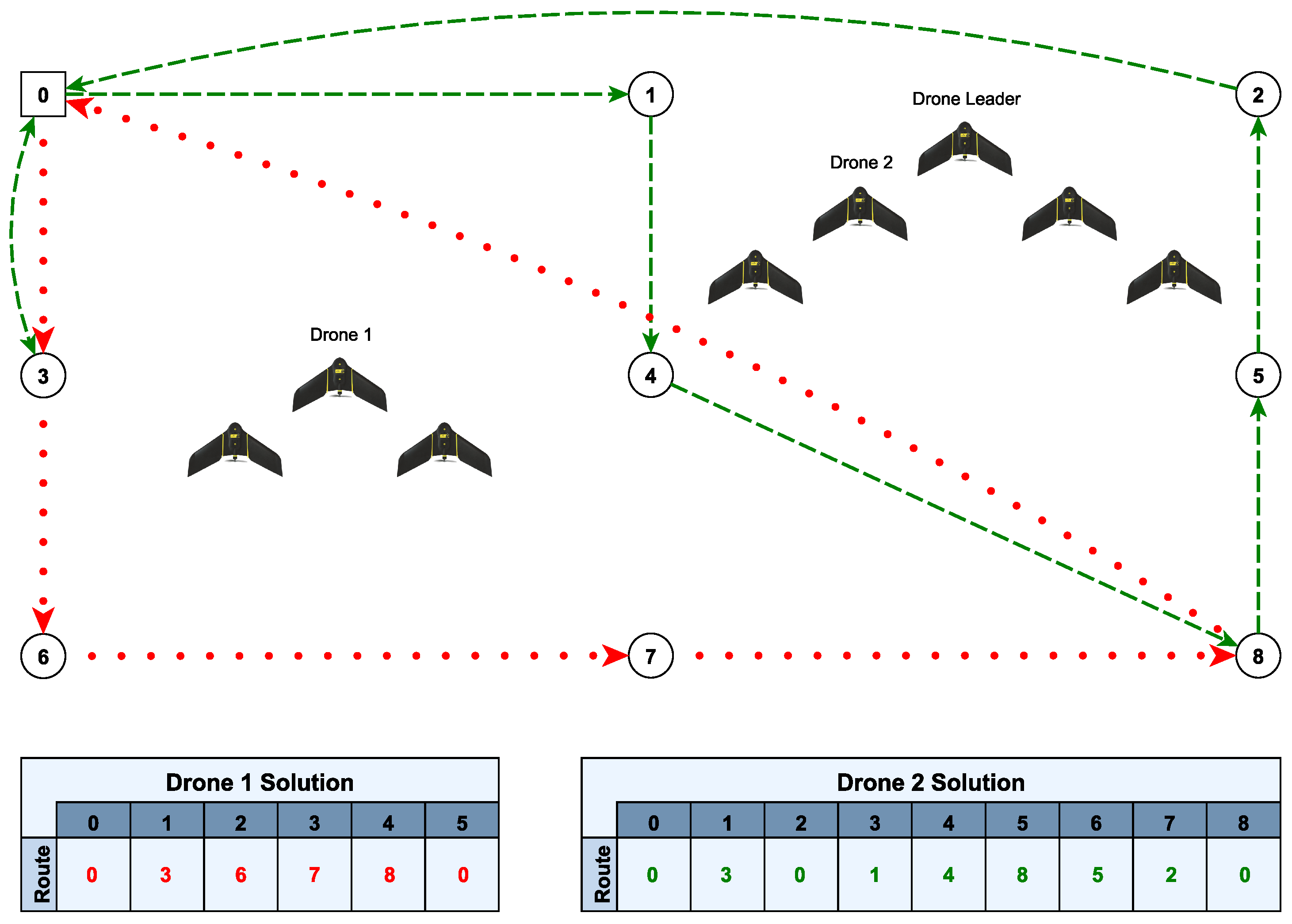
Figure 1 shows an example of a DSRP in a graph with nine vertices, eight drones and one base. It also contains two examples of routes performed by drones 1 and 2. Drone 1 starts the route by being the leader of the V-shaped formation, while drone 2, in turn, initiates the route by following another leader in another V-shaped formation. It can be seen that drone 2 performs two trips, as it returns to the base to be recharged.
Clearly, the DSRP is an NP-hard problem, as it originally comes from the Vehicle Routing Problem (VRP) [
7], a well-known NP-hard problem. In this way, the time needed to find an optimal solution for the offline version of the DSRP can be impractical. Considering that the main focus here is to find a solution for the online version of the DSRP, the need for an efficient algorithm is even greater. This has motivated us to develop a heuristic to solve the DSRP problem.
4. DSRP Computational Model and Methods
In the DSRP multi-agent decentralized approach, each drone is modeled as an agent able to compute its route based on real-time information. The drones can decide when it is appropriate (or not) to work cooperatively in a swarm of drones, considering a V-shaped formation with leader replacements. This decision is addressed by means of a heuristic proposed here. It should be noted that two versions of this model have been developed. The first is the offline version, whose main feature is the fact that when a drone searches for victims at a search location, the number of victims identified will always be equal to the expected number. As for the other version, the online version, the number of victims identified will be obtained at the instant of identification, and may be greater or less than the expected number.
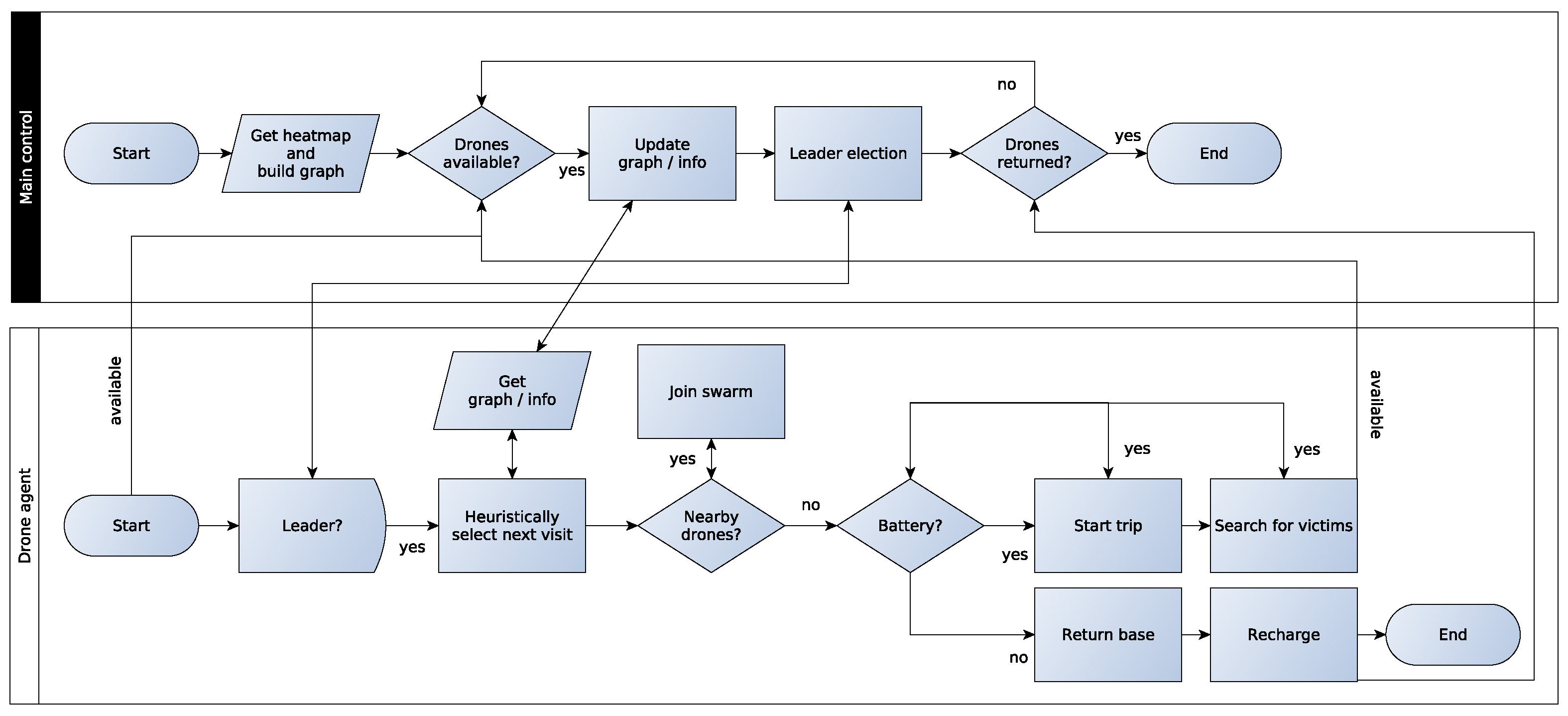
Figure 2 shows a flowchart of the proposed decentralized model. This algorithm contains two main modules: the Main Control (MC) and the Drone Agent (DA). The MC is responsible for building the heatmap of the post-disaster area containing all the information about possible victim locations. In the sequel, a graph based on this heatmap is built. Then, the algorithm checks which drones are available, updates the graph by getting their new information and sends it to the available drones. In the following, the MC performs a leader election to choose a leader. Finally, the MC controls the return of the drones to the base, considering the start of a new operation or the end of the whole operation.
The DA starts its work by becoming available and communicating with the MC. Thus, it waits for the leader election and when the answer from MC is positive the Drone Swarm Heuristic algorithm is executed to choose the next node to visit in the next trip. This decision is made by obtaining the updated graph and information about the other operations from the MC. In this module, it also decides about the drone swarms’ V-shaped formation, by making the DA able to join a nearby drone swarm, and the leader replacements during the flight. In order to perform any operation, the DA must check whether it will have enough battery power to reach the next node, search for victims and return to the base. Thus, the DA performs its operation, which may be to start the trip to the next node and then search for victims at this node; otherwise, it stops and returns to the base station. Finally, after finishing its operation, the DA reports to the MC if it will be available for the next operation or if it has finished all its work.
By employing an auction-based algorithm, for example, the Consensus-Based Bundle Algorithm (CBBA) [
21], decentralized coordination can be achieved, enabling agents to effectively exchange information between themselves. Such an approach fosters distributed decision-making, increased autonomy and robustness in the face of uncertainties or disruptions. With regard to the architecture of the data communication network, we can cite some recent works that address interesting architectures in which our model can be easily incorporated, making it possible to deploy it in real disasters. In [
22] we are introduced to a communication network architecture for a squadron of drones to be used in the scanning rocket impact area of Barreira do Inferno Launch Center in Rio Grande do Norte, Brazil to detect intruder boats. The system uses Wireless Sensor Networks, specifically employing XBee Pro 900HP S3B modules, for information transmission within a range of 5 km.
The remainder of this section describes in more detail both modules of the algorithm, Main Control (
Section 4.1) and Drone Agent (
Section 4.2). It is important to note that both modules contain simple and reproducible algorithms.
4.1. Main Control
The main control module contains five sub-modules: Get heatmap and Build a graph, Drones available, Update graph/info, Leader election and Drones returned. These sub-modules are detailed next.
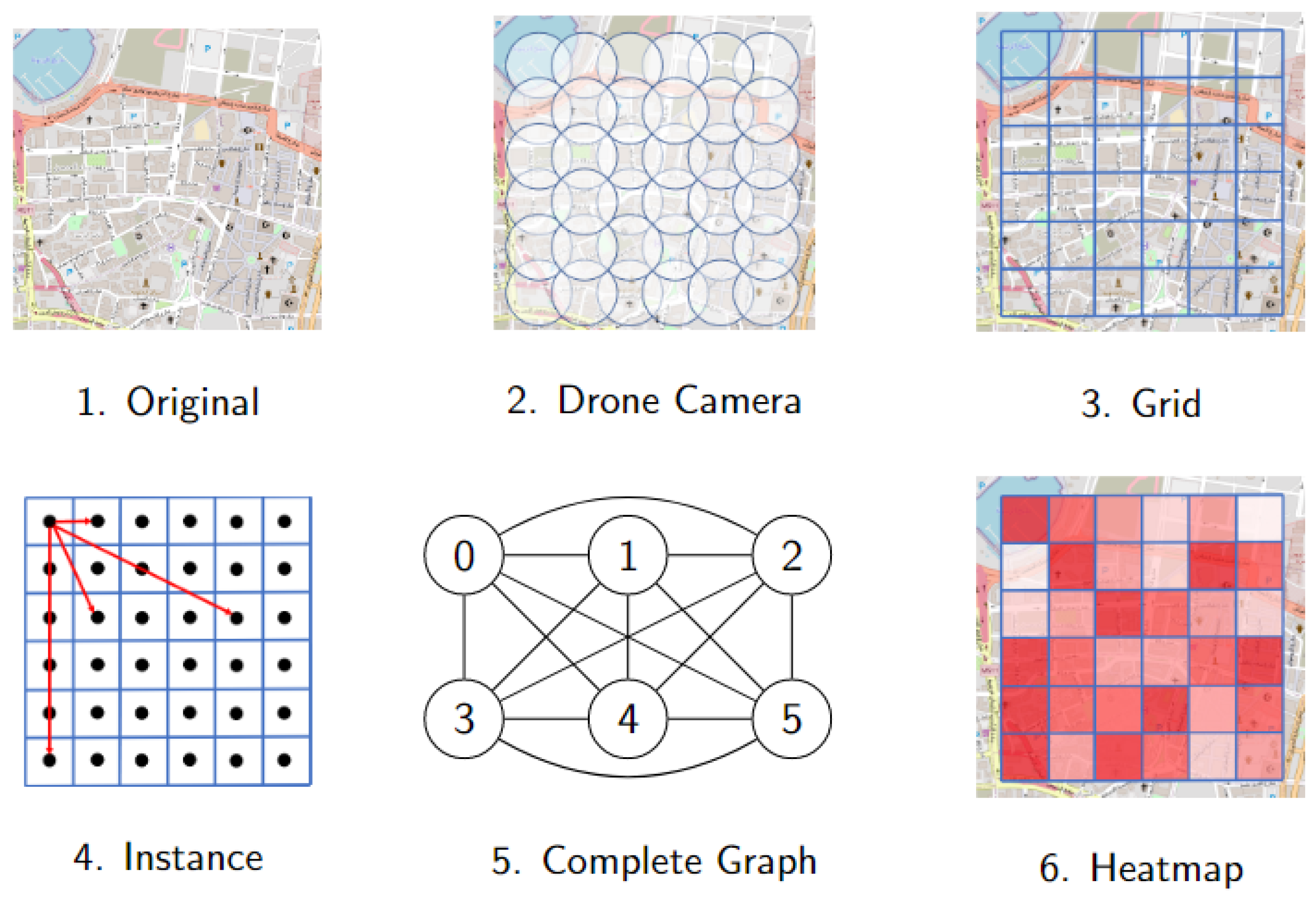
Get heatmap and build graph. The heatmap is essential information to start the search for a solution to the DSRP. The procedure on how to build the heatmap and transform it into a complete graph is illustrated in
Figure 3. This procedure consists of five steps.
The first step consists of obtaining the map of the post-disaster search area through some data source, for instance, the open data source OpenStreetMap (OSM). Then, the second step consists of defining all possible search locations for the drones, and setting the radius of action according to the range detection of the drones. The goals are to identify victims and cover the entire search area using this information.
The third step looks for the data related to the expected number of victims (
) and the victim identification probability (
) in each possible search location. Such information can be obtained from official government data, as well as through unofficial data from other sources (ground teams, Non-governmental organizations, etc.) The
number can be deduced, for example, from the number of buildings existing before the disaster. The probability
is defined by taking into account the difficulty of identifying victims in each search area after the disaster has occurred. The more buildings there are, the higher the expected number of victims, and the lower the probability of identifying them.
Figure 2 shows each search area colored in tints of red, in which the deeper the tint, the higher the estimation of the number of victims.
In the fourth step, the conversion of the heatmap into a complete graph is initiated, by first building a grid graph. This transformation is made as follows. Each search area of the grid represents a vertex of the graph, and the edges connect adjacent search areas. The edges are weighted by the battery consumption related to the path of a single drone. Once again, the number of buildings can help to define these weights.
In the last step, the complete graph is built, by solving the All Pairs Shortest Path Problem and then connecting all pairs of vertices with edges weighted by the minimum battery consumption between them, i.e., the one that corresponds to the shortest path between such vertices in the previous graph.
This step allows the drone availability to be checked. At this stage, there are three possibilities for receiving messages concerning the availability of drones. Two of them are treated in trivial ways, i.e., as soon as the message is received the process continues its flow directly to the next step. The third possibility requires synchronization as well as consistency of the graph information. The two trivial possibilities are when the DA module starts its processing and after the drone finishes its battery recharge. In the latter case, the message is only sent if there is still enough time to visit at least one search location. The last one is when the drone just ends up performing a search for victims operation. In order to avoid exchanging too many messages with the MC module, it is considered that at the end of the search, the current leader will control the availability of his swarm and he will be responsible for sending the message to the MC, notifying the swarm availability and also containing new information about the number of victims identified by the swarm.
Update graph/info. In the Update graph/info step, the information obtained by the leaders regarding the number of victims identified by the drones is updated in the graph. In addition, information related to the current allocation of drones to search locations is also updated. Considering this information, it is important to limit the number of drones that are on their way to the same search location.
Leader election. This step performs the choice of an available drone to be the next leader. This choice is performed according to a very simple rule: the next leader will be the one with the largest amount of available battery. In case of a tie, the next leader will be chosen randomly among those with sufficient battery.
Drones returned. Drones returned is the last sub-module of MC and is responsible for controlling the return of drones to the base. Basically, it is performed as a check on the remaining time of the whole operation, considering the maximum time available T. If there is still enough time for the drone to visit at least one search location and still return to the base, then the drone becomes available and this message is transmitted to the DA sub-module. Otherwise, the DA module of such a drone is concluded. In this way, the MC must wait until all the drones have no more time left for the operation to stop the algorithm.
4.2. Drone Agent
As mentioned before, the DA module starts by sending a message indicating its availability to the MC. Then, the processing continues following the flow of its eight sub-modules detailed next: Leader, Get graph/info, Drone swarm heuristic, Join swarm, Battery check, Start trip/Return base, Search for victims and Recharge.
Leader. In this step, the agent waits for the leader’s election. Once it is defined, the agent immediately moves on to the next step, the heuristic choice based on updated information.
Get graph/info. Before choosing the next search location to visit, the agent updates the information regarding the graph, as well as the operations that other agents are performing at the moment. These data are essential to make the best decisions considering the current configuration of the environment. Hence, the DA requests, and obtains, from the MC the current information which, more specifically, corresponds not only to the expected number of victims remaining at each search location but also to what are the trips that other agents are performing at that moment.
Drone swarm heuristic. The Drone Swarm Heuristic (DSH) will build iteratively a complete solution for the DSRP based on two criteria: the expected number of victims and operation cost. The choice to define only the next visit at each moment is necessary to guarantee the applicability of the model. Thus, the drones make this decision promptly, avoiding a bottleneck in the model and consuming less energy. Initially, DSH uses the data obtained from the previous sub-module to know the possible search locations available to be visited by the agent, this information is referred to here as the candidate list (CL). It means that if a search location has a positive remaining number of expected victims, then it will be included in the CL. Otherwise, if this number is close to zero, it means that all expected victims were identified. Then, DSH will rank each search location
v according to the
function (
1):
which is responsible for obtaining, given a start location
i and a search location
v, the ratio of the expected number of remaining victims (
) over the operation cost (the trip cost
may be reduced according to the number of drones in the swarm). The objective is to maximize
g in CL, the
. In other words, the
represents the search location that provides the highest victim identification while also taking into account the cost of this operation.
It is noteworthy that the DA can only choose feasible search locations to visit, taking into account enough battery to fly to the location, detect and return to the base station.
Join swarm. Once the decision on the node to be visited is made, the agent has the possibility of joining up with another agent or a swarm that is making a common trip. Even though they may have different final destinations, agents can group together to make an intermediate trip and split up afterward.
In [
3], the authors presented some possible scenarios of savings when using a drone swarm performing flights in a V-shaped formation. Among all of them, in this work, we adopted the one that the authors consider the closest to real applications, i.e., reducing to 10%, 15%, 19% and 21% of energy consumption by using two, three, four and five drones. In addition, in [
3] the possibility of reducing to 20% of extra savings by adopting the V-shaped formation with leader replacements in each case is also presented.
Table 2 presents the savings of this realistic scenario, considering the V-shaped formation and leader replacements according to the number of drones. In the last row (Total savings) we present the combined savings adopted by our computational model. To clarify, in our model, if the energy consumption between two locations is 100 and there is a swarm of two drones flying between them, this means that we will have a final consumption of 72 (28%) because of the reduction in total consumption, being 90 (10%) because of the flight in a V-shaped formation and finally 72 (20% extra) because of the replacement of leaders. It is noticeable from the table that drone swarms are limited to a maximum of five drones. This means that during the whole operation at most five drones are allowed to be in the same V-shaped formation. If more than five drones fly to the same search location, then the model will allow at least two different swarms to coexist.
The swarm function used by Equation (
1) works as follows. According to a search location
v, the swarm function returns the corresponding saving value related to the number of drones that visit
v.
Battery check. The agent must check its remaining battery during the whole operation to prevent the drone from dropping during its flight. The Battery check sub-module periodically performs such a check, considering that the agent must always have enough battery to return to its base. If, for any reason, the remaining battery is not enough to continue the current operation, this sub-module triggers the immediate return of the agent to the base.
Start trip/return base. The Start trip/return base sub-module is responsible for conducting the trip for the agent. An agent can perform the trip by itself or in a swarm of drones, in the latter case the trip cost will be lower for all drones involved in this cooperation. When the agent is running out of battery, it will perform a return to base, which is also conducted as a normal trip, alone or in a cooperative flight.
Search for victims. The search for victims is an action of an agent that demands a fixed time. If this action is carried out by more than one drone the time required will be similar for each. However, the more agents there are, the greater the probability of identifying victims. At the end of this sub-module, the DA leader sends a message to the Drones available sub-module reporting not only on the number of victims identified but also on drone availability for future operations.
Recharge. The recharge of an agent requires a fixed time, which must be respected until the end for the recharge to take place, i.e., it is not possible to recharge an agent partially. Once the recharge is complete, the DA notifies the Drones returned sub-module of the MC that the battery is full and whether there is still enough time to perform any further operations. If there is not enough time, in addition to notifying the MC, the agent terminates its activity.
5. Computational Experiments
All the algorithms were implemented in C++, using the Windows/GNU g++ compiler (version 8.1.0). All tests with the proposed algorithms were executed on an Intel(R) Core(TM) i5-9300H @ 2.40 GHz processor with 16 GB RAM on Windows 10.
The solutions produced by the proposed methods were adapted to be visualized using the simulator CoppeliaSim [
6]. This allows the execution of the solutions to be followed dynamically.
The goals of the numerical experiments are to check the performance and the impact of the proposed offline and online methods using the realistic case study. For such a purpose, several indicators are used such as:
O→ total number of operations achieved by all drones;
→ the number of operations achieved in cooperation;
T→ the total number of trips;
→ the total number of trips in a V-shaped formation;
S→ the total number of scans;
→ the total number of scans in cooperation;
R→ the total number of recharges;
→ the time the last drone returns to base;
→ the average time the drones return to base;
C→ the total cost in time units to conclude all operations: to take off from the base, arrive at search locations, identify victims, return to a base and recharge;
→ the total cost in time units to conclude all operations without considering savings from the V-shaped formation flight;
→ the percentage gain obtained by considering the savings;
E→ the total number of expected victims;
V→ the total number of victims identified by the drones;
→ the percentage related to the number of victims found.
In the following sections, the case study, the development and settings and results considering both offline and online approaches, together with sensitivity analysis are detailed in the next sections.
5.1. Case Study: Beirut Port Explosion
The Beirut Port scenarios were generated with the instance generator coming from the study [
5], using additional features for the DSRP. The process was described in
Section 4.1. A fleet of drones able to communicate with each other is defined. The complete graph is obtained by All Pairs Shortest Path Problem.
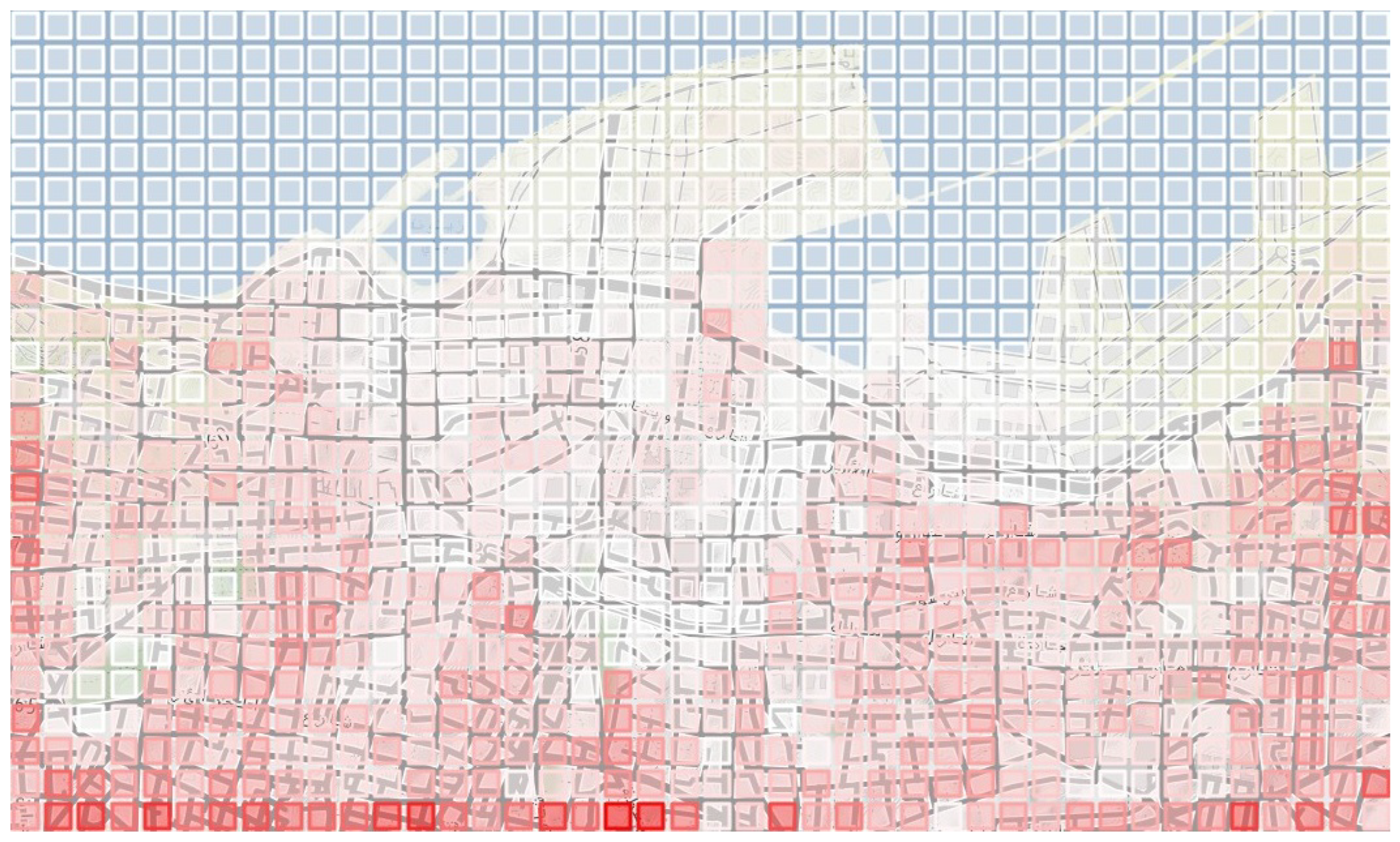
Figure 4 shows the selected area divided into squares of 100 m
, colored in tints of red to illustrate the expected number of victims. The dimension of the grid graph constructed is 42 × 25, thus resulting in a complete graph of 1050 vertices.
Scenarios
Three scenarios, referred here as Scenario 1, 2 and 3, were generated with 1050 vertices, 2 recharge base stations, and 8 drones. Each drone has a range limit of 3540, a recharging time of 2400, and the time spent detecting victims equals one. These values are based on the eBee senseFly drone [
23], which was also set and used by [
3]. The maximum time for the whole operation is 7200. The differences between the three scenarios are the variation in the expected number of victims in each search area (totaling 29,349, 30,599, and 31,711, respectively). They also differ in the identification probability for each search area.
5.2. Development and Settings
The MC module makes use of a main thread, while the DA uses more than one thread, working in parallel. This distinguishes our development from that of [
18], who employ only one thread.
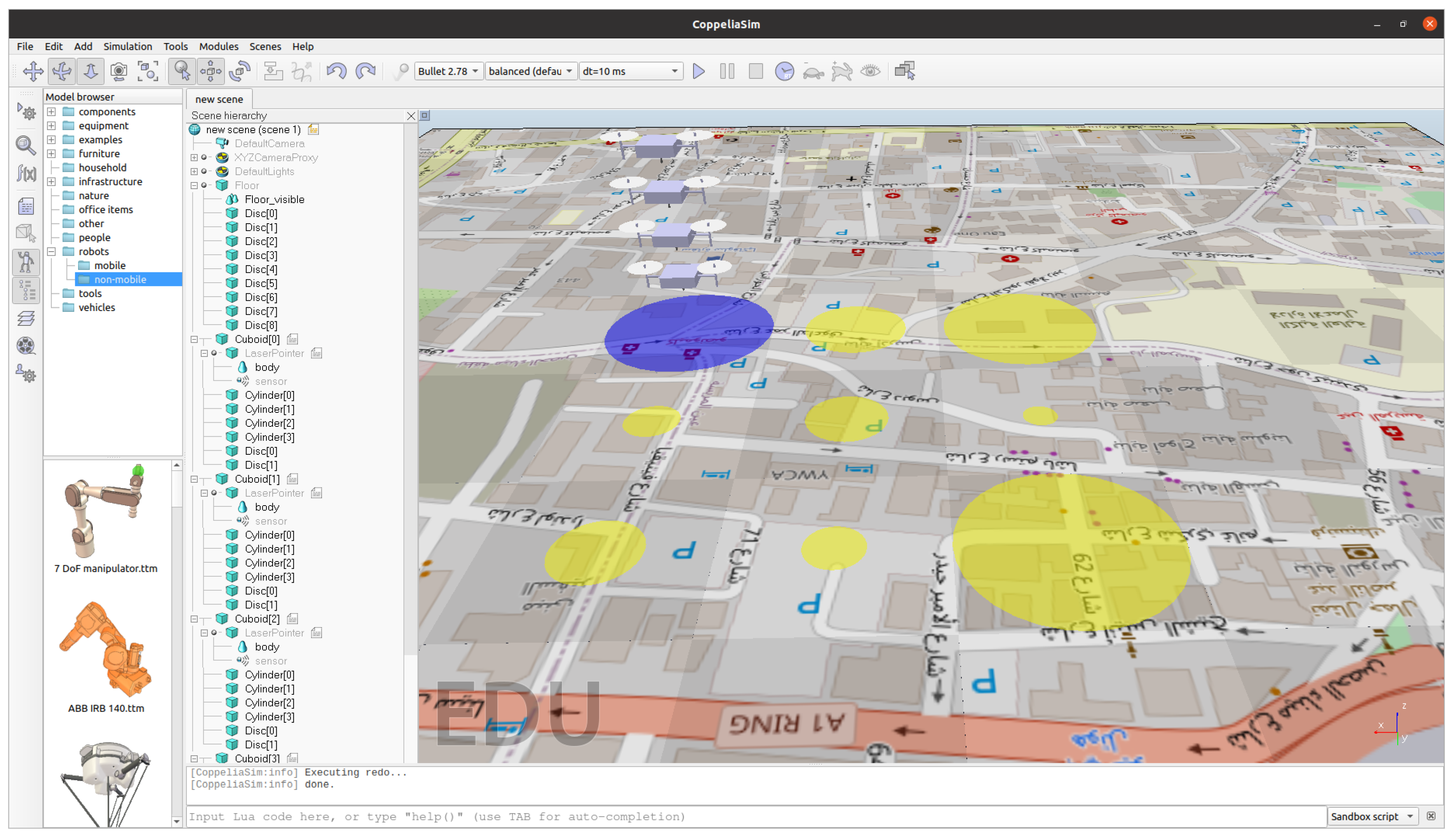
Figure 5 shows the interface of CoppeliaSim as well as an example of a loaded solution for the DSRP, containing four drones and nine vertices (one base and eight search areas). Each drone is positioned at a certain height in order to facilitate viewing, even if they are in a V-shaped formation. This has been conducted to simplify the simulation. A code color is used to identify the leaders, the drones following the leader, drone recharging, for example, the yellow and blue vertices that represent, respectively, the base stations, and the potential nodes with victims. The size of each yellow circle is proportional to the expected number of victims in the corresponding area.
5.3. Results Using an Offline Approach
The performance of the proposed algorithm is also evaluated in an offline approach based on the Beirut Port explosion. In the offline version, the number of victims obtained in each search location will always be equal to the expected number. For instance, if it is expected that there are 100 victims in a search location and the identification probability is 60%, then for each victim search operation, 60% of the remaining victims will be identified, i.e., 60, 24, 9.6, 3.84, etc.
5.3.1. Sensitivity Analysis on the Number of Drones
In this experiment, the number of drones varies (4, 8, 16, 32 and 64), while the other parameters remain similar along the optimization.
Table 3,
Table 4 and
Table 5 present results using the aforementioned indicators.
Obviously, the more the number of drones increases, the higher the percentage of identified expected victims is. It is noteworthy that with only four drones it is possible to reach more than 91% of identified victims. When increasing to eight drones, this percentage reaches more than 99% of the expected victims. Finally, with 16, 32 and 64 drones, practically all victims are expected to be identified. Taking into account the modest savings model applied, it is considered that reasonable gains can be achieved through the use of V-shaped formation flight, reaching values above 3%.
Results using 32 and 64 drones show that the final time spent concluding all operations is less than the maximum time allowed. Due to that, the maximum time limit used in the simulation was removed, in order to check the impact of using each number of drones.
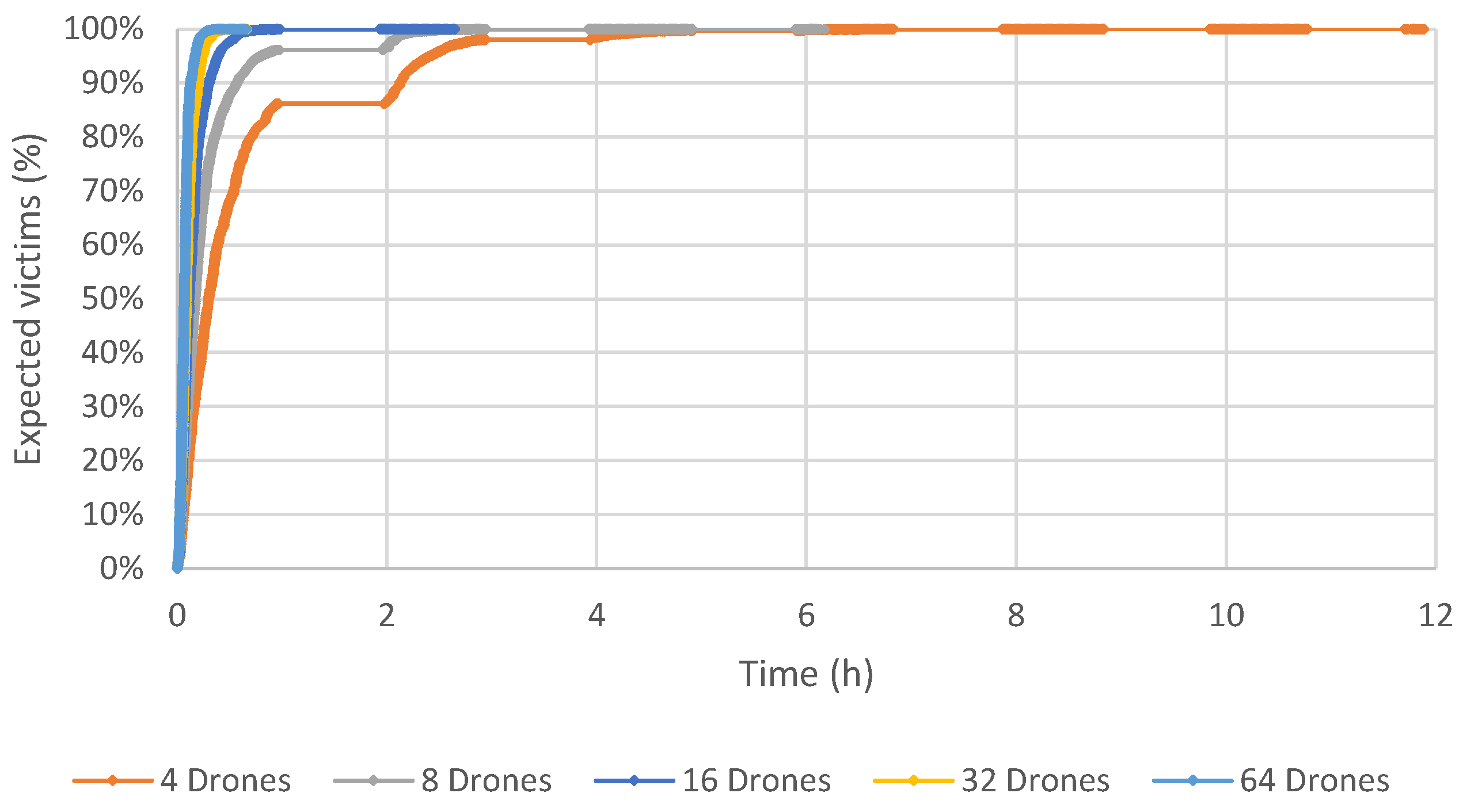
Figure 6,
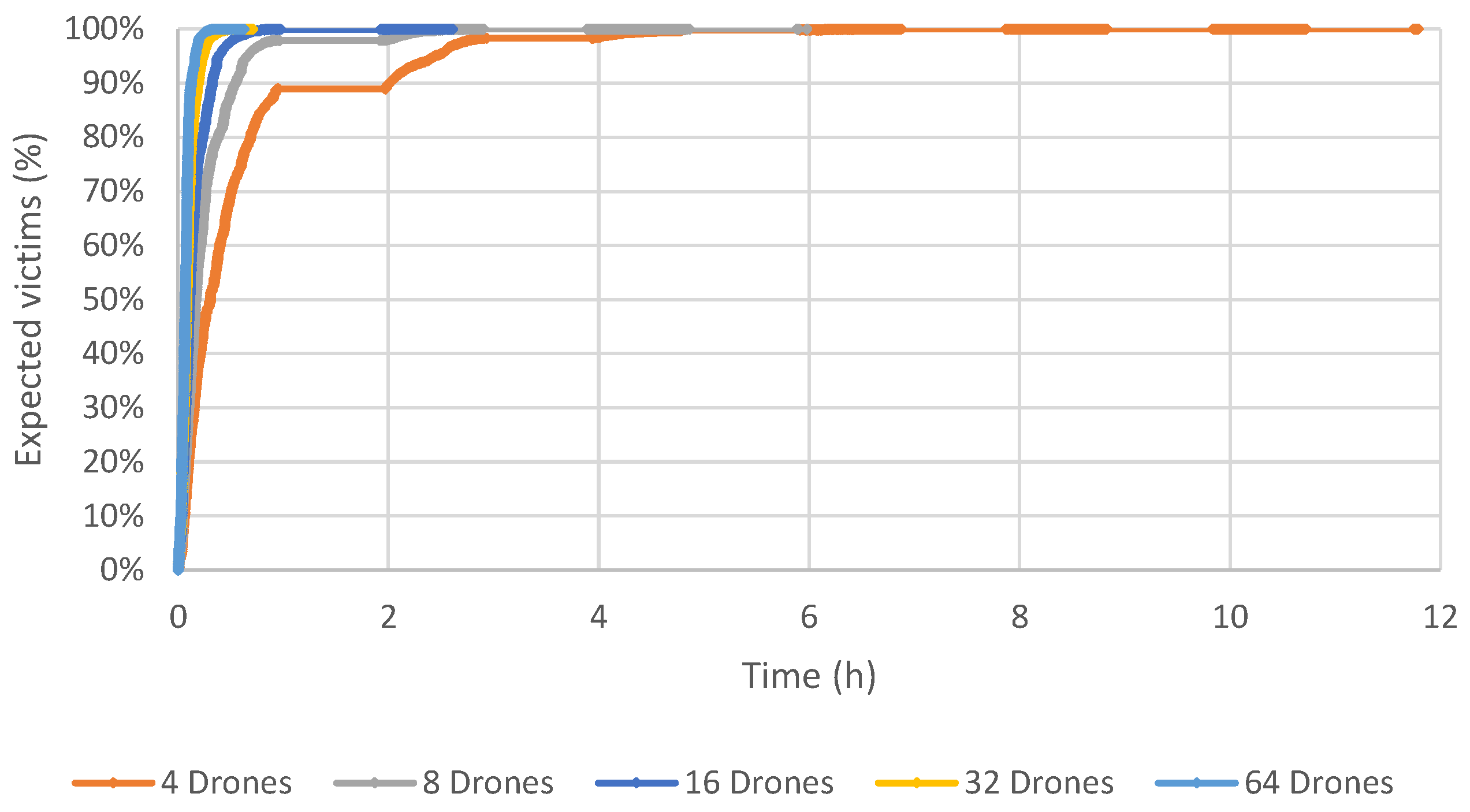
Figure 7 and
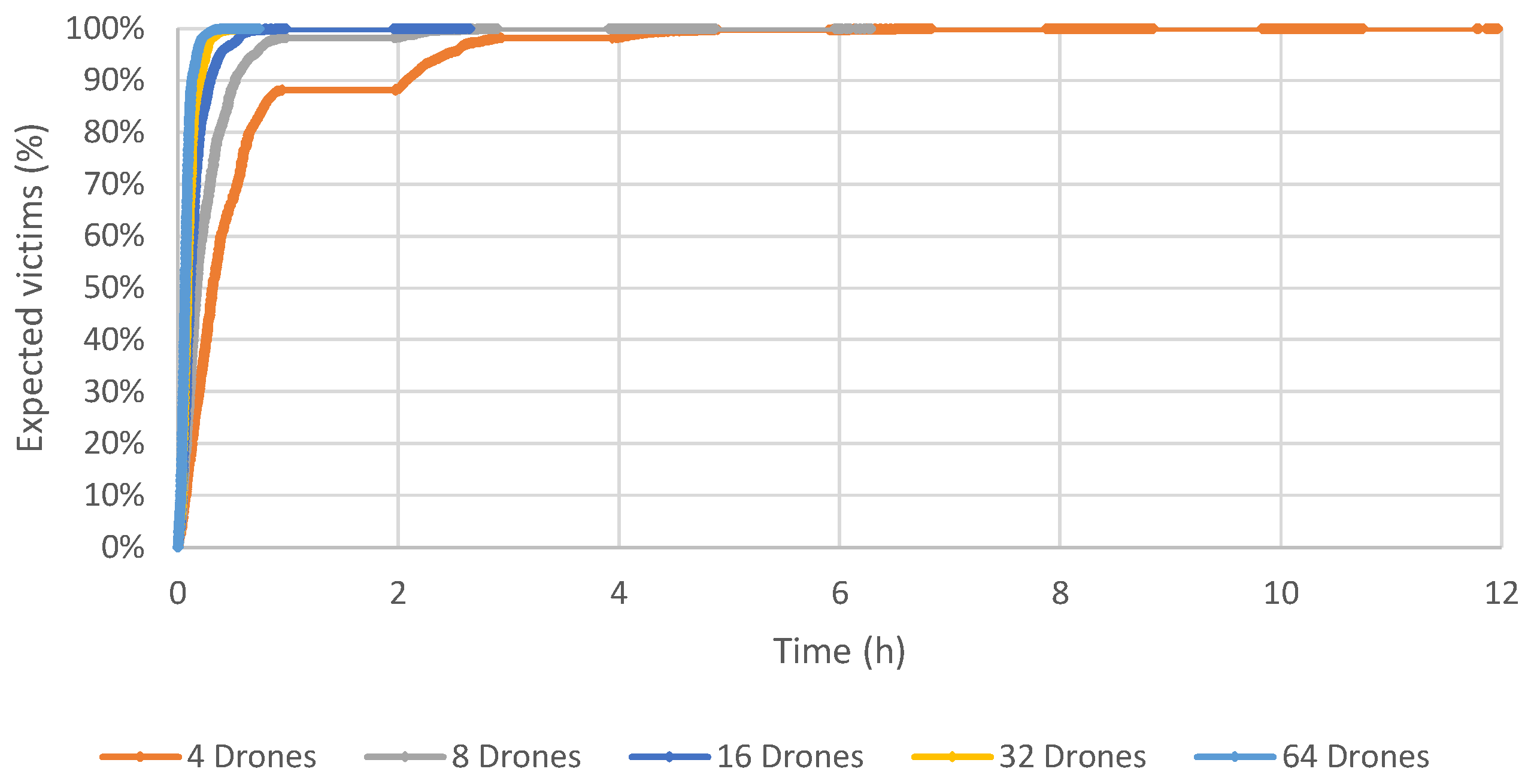
Figure 8 depict a graph that contains the percentage of expected victims identified by our computational model over time and according to the number of drones for Scenarios 1, 2 and 3.
These results show that the proposed method obtains a good coverage of the post-disaster area of Beirut in a very acceptable time. Using 64 drones, the time required to reach all expected victims is about 40 min. If the number of drones equals 32, this time increases to one hour. All the expected victims were found using 16 drones and about 2.5 h. Six hours are necessary to identify all the expected victims using eight drones. Not surprisingly, the longest time to identify all the victims is when there are only four drones, taking slightly less than 12 h.
5.3.2. Sensitivity Analysis of the V-Shaped Formation with Leader Replacements
Table 6,
Table 7 and
Table 8 present the results obtained without using a V-shaped formation with leader replacements, respectively, for Scenario 1, 2 and 3, using 4, 8, 16, 32 and 64 drones. Moreover,
Figure 9 and
Figure 10 consider, respectively, the additional cost and number of victims found, whenever not considering the savings related to the V-shaped formation flight with leader replacements.
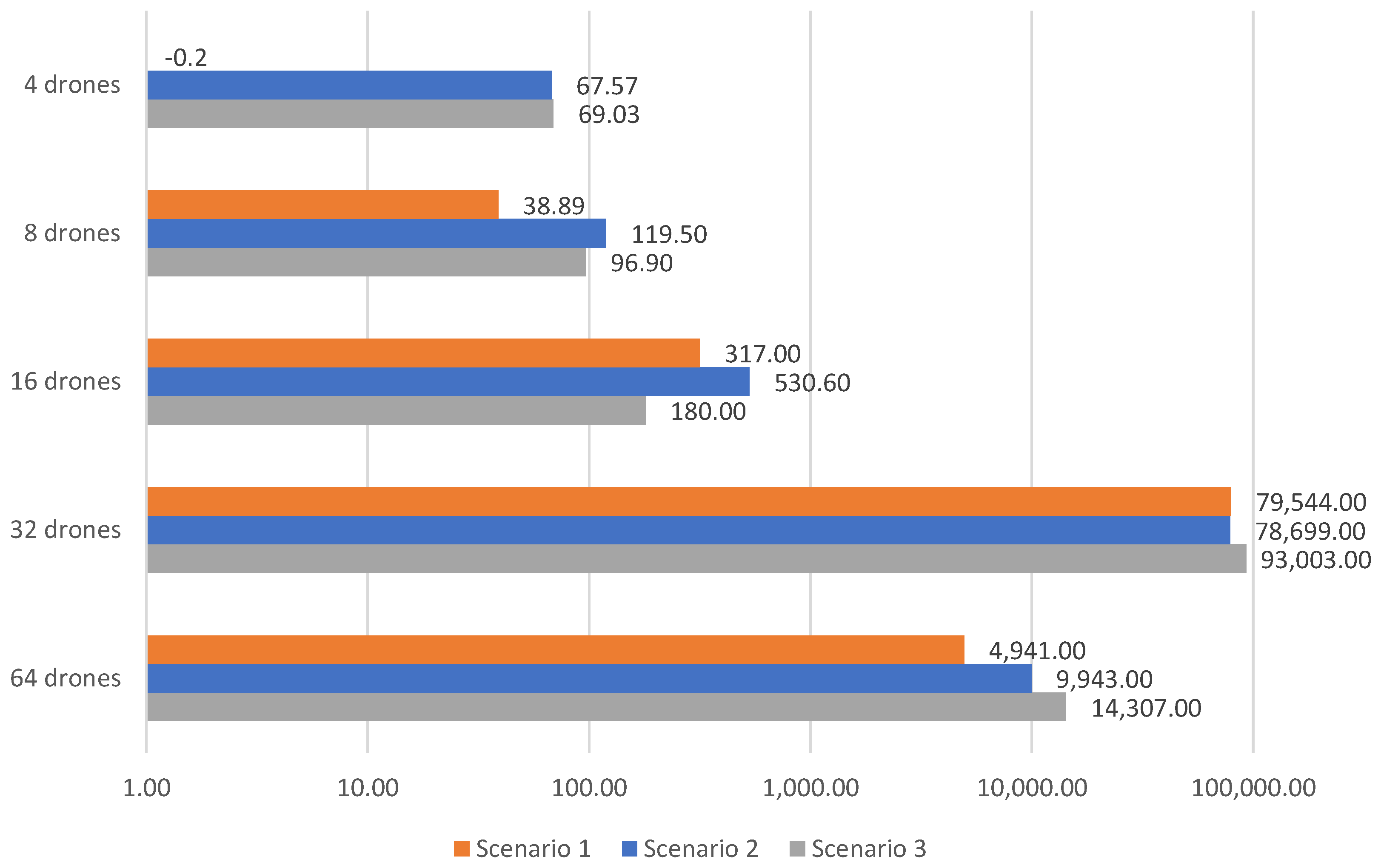
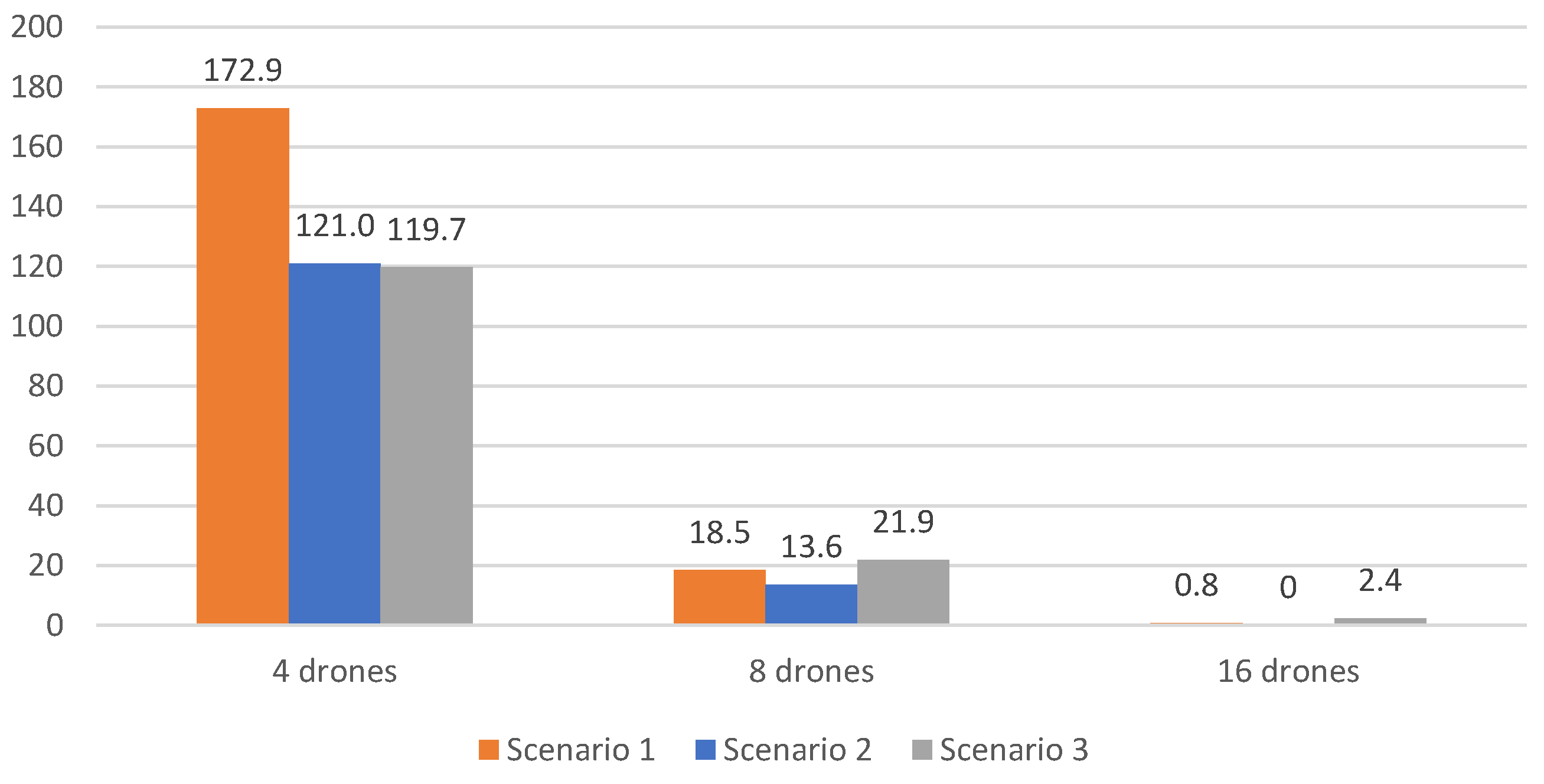
Results clearly indicate that not using V-shaped formations with leader replacements led to a smaller number of victim detection and a higher cost, compared to the previous results. The cost is increased in up to 80%, and the victim detection is decreased up to 1% It is worth noting that the number of recharges also increases for 32 and 64 drones.
Figure 9 illustrates higher cost, except with four drones in scenario 1, which was slightly lower, −0.20. Using more drones, 32 and 64 drones results in a higher cost, especially using a V-shaped formation. This is due to the additional recharges required. On the contrary, the number of victims identified increases, as depicted in
Figure 10. Using 32 and 64 all victims are identified, while the improvement using fewer drones (4, 8 and 16) is noticeable. On average, 137 extra victims could be identified with 4 drones, 18 extra victims with 8 drones and 1 extra victim with 16 drones. Such results demonstrate the importance of adopting the savings related to the V-shaped formation strategy.
5.3.3. Sensitivity Analysis on the Detection Probability
In these experiments, we evaluated the impact of using a detection probability associated with the search locations. For this purpose, three levels of detection probabilities, defined by means of intervals, were used: low (
), medium (
), and high (
). Values were randomly generated within these ranges for each search location of each scenario. The results obtained for scenarios 1, 2 and 3 using eight drones are shown, respectively, in
Table 9,
Table 10 and
Table 11.
It is remarkable for the three Scenarios, that even with low identification probabilities, the proposed computational model was able to find a high percentage of expected victims, more than 87%. Another interesting observation is that in these more "adverse" situations, the method makes use of more flights in a V-shaped formation. This can be seen when observing the highest gains in savings and, of course, the number of squad operations. Whenever the probabilities were applied at the medium level, more than 98.7% of victims were identified in all Scenarios, obtaining savings of more than 1.3% with V-shaped formation flight. By using the level with a high identification probability, the percentage of identified victims was greater than 99.6% and the savings gain was about 1%. This happens since the use of V-shaped formation flight is not as necessary as in the low detection probability level.
5.3.4. Sensitivity Analysis on the Number of Expected Victims
The goal of these numerical experiments is to evaluate the impact of the method when the expected number of victims at each search location is underestimated or overestimated. Therefore, the Scenarios were adapted to this case. In an underestimated case, each search location has the number of victims decreased to a random value between 50% to 75%, 25% to 50%, and 0% to 25%, considering the initial number of victims. In the overestimated case, the number of victims was increased in each location as a random value between 0% to 25%, 25% to 50% and 50% to 75%, considering the initial number of victims. Results are depicted in
Table 12,
Table 13 and
Table 14, using eight drones. The previous results obtained in
Table 3,
Table 4 and
Table 5 are presented in line “Initial Scenario” to allow comparison.
Results remain stable for underestimated and overestimated cases, i.e., more than 99% of the expected victims are found, with gains in savings with flights in V-shaped formation between 1% and 2%. These results allow the robustness of the proposed method to be evaluated and, as a consequence, its applicability in real situations.
5.4. Results Using an Online Approach
In post-disasters, the probability of detecting victims in a search location may vary in every scanning situation. Thus, at each location, the number of victims identified is not always equal to the expected number. To address this context, an online version of the proposed method is tested, using the underestimate and overestimate cases, considering the variation of the detection probability. Both have the following intervals: [0–5%], [5–10%], [10–15%] and [15–20%]. For instance, whenever applying an underestimated case related to the interval [0–5%] over a search location where identification probability equals 60%, the underestimated case varies from 55% to 60%.
Table 15,
Table 16 and
Table 17 present the results obtained for the online approach, using the three Scenarios 1, 2, and 3. The proposed method seems robust for the Scenarios used, even in the most adverse situationwhere the probabilities decrease between <15% and 20%, the model was able to locate more than 97% of victims. Applying the overestimated case and the interval >15% and 20%, the method is able to identify almost all the victims. In summary, for these Scenarios, the approach deals very well with uncertainties related to the identifications.
6. Conclusions
In this article, the Drones Swarm Routing Problem (DSRP) is proposed, motivated by the application of finding victims after a disaster. The main novelty of the DSRP is to address a cooperation issue between drones. Both online and offline strategies are tested using drone cooperation. This is conducted with multiple drones and using a V-shaped formation with leader replacements that lead to less energy consumption.
A computational model that applies the Drone Swarm Heuristic and uses multi-agents in a decentralized approach is proposed. It has decision features allowing a drone to operate alone or in a swarm. It relies on the hypothesis that drones are able to correctly fly within a group without collisions, considering both path planning and detection. This assumption is used since we are focusing on the decision optimization problem. The proposed computational model was developed using threads. Solutions obtained were also tested using the robot simulator CoppeliaSim, in order to visualize the operations of drones over time.
A case study was conducted based on the Beirut port explosion, thereby generating three test Scenarios. They were tested using an online and an offline approach. Extensive numerical experiments were run for the off-line version: varying the number of drones; enabling and disabling a flight-related V-shaped formation with leader replacements; varying the identification probability, and the number of expected victims. In the sequel, the online version was studied, where the identification probability was randomly modified along the test.
For the Scenarios used in this study, the proposed heuristic methods are robust. Moreover, using eight drones, results indicate that more than 99% of victims can be found within 2 h. Using 16, 32 and 64 drones, a slight improvement is obtained, despite a higher running time. The V-shaped formation with leader replacements gives very interesting results, making it possible to find extra numbers of victims at a lower cost. In general, the proposed heuristic method has good coverage.
This study opens several avenues of research. The communication issue, which in practice consumes a large part of the energy consumption can be investigated together with other types of topologies for drones, for example, the work of [
24] presents an architecture including aerial base stations that must provide network services to ground users who can move around. Other methods, such as 3D search space with Reinforcement Learning [
25] or even artificial potential fields [
26], can be investigated in order to carry out the path planning and also guarantee the permanence of the V-shaped formation. In addition, the detection is not explicitly integrated in this study. In fact, it is possible to accomplish that using thermal cameras, or even artificial intelligence using images of the areas. This step is an area for forthcoming study. Moreover, it is noticeable that observations at a higher altitude allow larger areas to be scanned at once, in spite of lower precision. On the contrary, a lower altitude allows more local and precise observations. Analyzing the trade-off between higher and lower altitudes is left for future work.