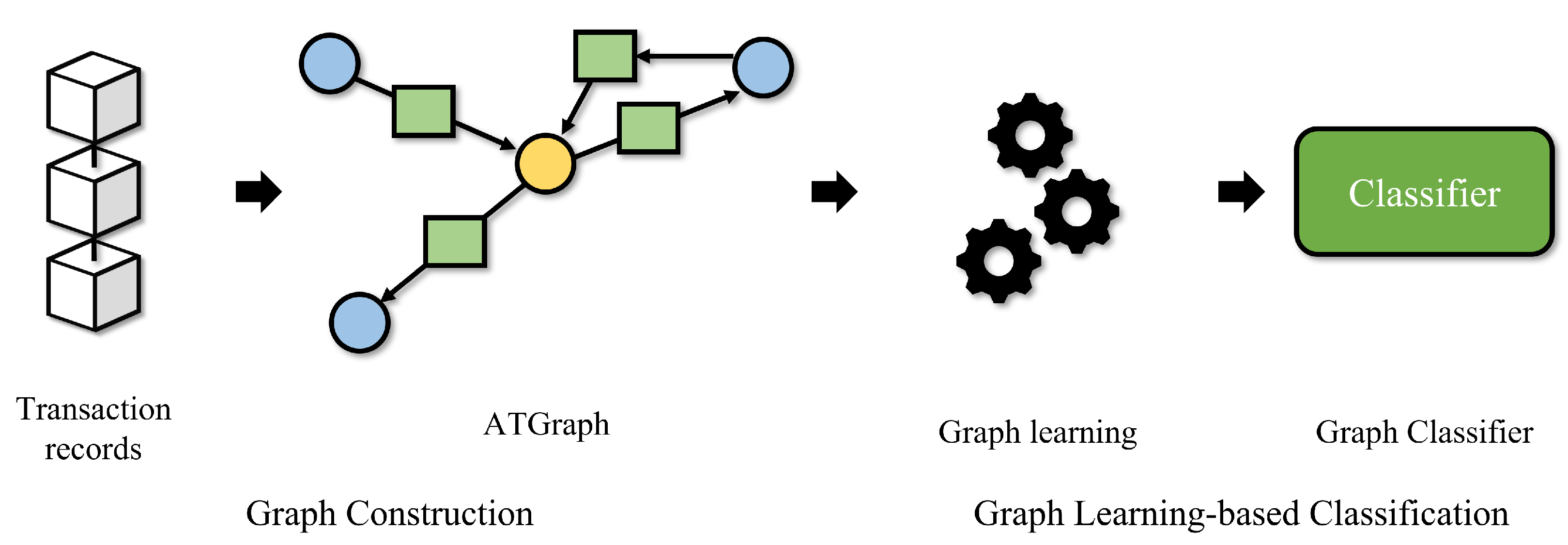
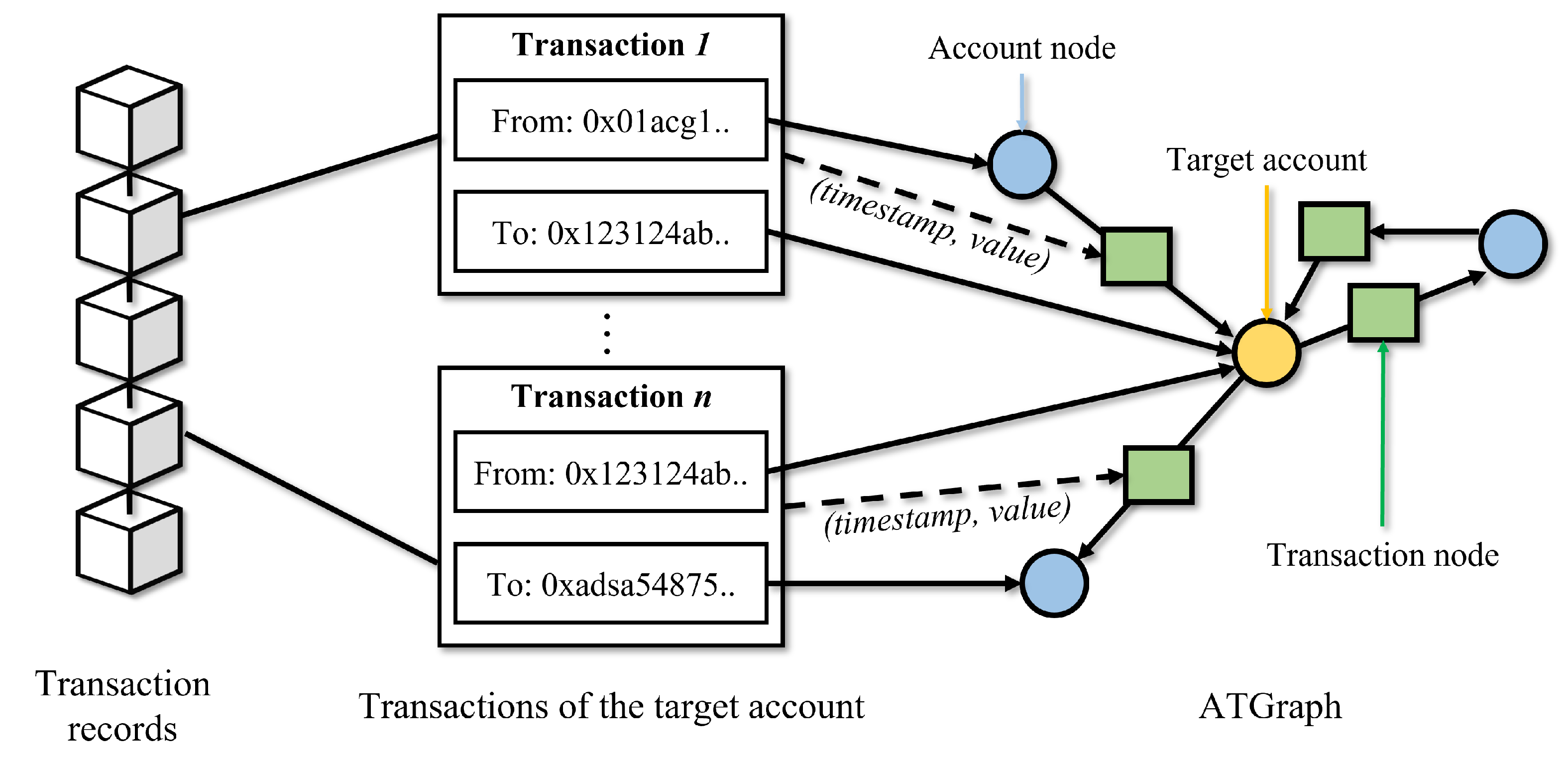
1. Introduction
Blockchain is a distributed ledger technology that facilitates the recording and managing of transactions in a decentralized manner. Participants in the blockchain network record and share ledgers by consensus. Ledgers are managed transparently without a central authority because all the participants share the same ledger. Owing to the advantages of blockchain technology, many fields such as finance, healthcare, and logistics have adopted blockchain technology [
1,
2,
3]. In particular, cryptocurrencies such as Bitcoin [
4] and Ethereum [
5] are among the most successful blockchain applications in finance. Ethereum has introduced smart contracts that enable users to draft contracts without intermediaries to support various activities such as voting and auction [
6]. With the introduction of smart contracts, Ethereum has become the most famous cryptocurrency platform. Users can transfer assets on cryptocurrency platforms without a central authority, such as a bank. Moreover, cryptocurrency platforms use pseudonymous transaction identities that allow users to trade assets without revealing their real-world identities.
However, many cybercrimes have been exploiting cryptocurrencies to hide their identities [
7]. In 2017, WannaCry, one of the largest cybercrimes, encrypted victims’ data and demanded cryptocurrencies in exchange for the decryption key. WannaCry is estimated to have caused losses worth
$4 billion and affected over 300k Windows computers in over 150 countries [
8]. In Ethereum, smart contracts have created new opportunities for cybercrimes such as Ponzi schemes [
9]. Chainanalysis, the blockchain data platform, reported that around 19,000 victims of Ethereum cybercrimes lost approximately
$8000 per person only in 2017 [
10]. Besides, the number of phishing accounts for more than 50% of all cybercrimes in Ethereum, indicating that phishing has become a critical issue in the Ethereum ecosystem [
11]. The rise of phishing accounts on Ethereum has threatened users’ assets and the network’s reliability, destabilizing the Ethereum network [
12]. Therefore, it is important to detect phishing accounts to protect users’ assets and make the Ethereum ecosystem more sustainable.
Blockchain transaction records are historical and publicly accessible data. Tracking and analyzing these records can infer the pattern of the specific accounts [
13]. Many studies have been conducted to detect blockchain cybercriminal accounts by analyzing transaction records using machine learning [
14,
15]. Moreover, blockchain transaction records can be expressed in a graph structure with accounts as nodes and transactions as edges, such as typical financial transaction graphs. The graph structure of transaction records has motivated the exploration of graph-based learning approaches [
16]. Based on this motivation, several studies have adopted graph-based learning methods such as network embedding algorithms and graph neural network (GNN) to detect cybercriminal accounts in the Ethereum network [
17,
18,
19]. These studies adopted representing transactions as a homogeneous graph with a single type of node and a single type of edge. However, the homogeneous graph is difficult to describe for the character of the transaction records because it ignores the heterogeneity of the Ethereum network [
20]. Moreover, the homogeneous transaction graph can have a multi-edge with multi-dimensional edge features between a node pair. Traditional graph learning approaches utilize one-dimensional edge features, which will limit learning the effectiveness of the multi-edge blockchain transaction graph [
21,
22].
In this paper, we propose a graph learning-based Ethereum phishing account detection framework with a heterogeneous transaction graph that has a multi-type node. First, we design a directed heterogeneous graph structure called an account-transaction graph (ATGraph), where transactions are considered nodes in the place of edges. ATGraph can effectively represent the Ethereum network’s heterogeneity. Moreover, it can reduce the complexity of Ethereum transaction graphs by representing multi-edge as single edges. According to the designed heterogeneous graph structure, we construct Ethereum transaction records into ATGraphs. Then, we extract features of nodes in ATGraphs based on their transactions. Finally, we perform graph learning-based supervised learning for graph classification to detect Ethereum phishing accounts. Our main contributions are summarized as follows:
Contributions
We propose a graph learning-based Ethereum phishing account detection framework with a heterogeneous transaction graph. Moreover, we design a novel directed heterogeneous graph structure called ATGraph to take the multi-edge into account and represent the heterogeneity of the Ethereum network.
We conduct experiments on the Ethereum phishing account detection with various graph learning algorithms. In experiments, we compare the detection performance using ATGraphs and homogeneous graphs as inputs in each graph learning algorithm. Experimental results demonstrate that ATGraphs outperform homogeneous graphs in most graph learning algorithms.
The remainder of this paper is organized as follows.
Section 2 introduces related works on the blockchain phishing account detection and graph learning approaches.
Section 3 describes the methodology of the proposed Ethereum phishing account detection framework, including ATGraph construction and graph learning-based graph classification. In
Section 4, we present the experimental results and analyses. Finally,
Section 5 concluded this paper.
4. Experiment and Results
This section describes experiments and results to evaluate the detection performance with ATGraphs. We compare the performance of ATGraph and homogeneous transaction graphs as inputs of various graph learning-based detection methods.
4.1. Data Collection
We collected labeled Ethereum accounts from authoritative sources for experiments listed in
Table 2. We collected 1,659 verified phishing accounts and 1,700 normal accounts from XBlock (
https://xblock.pro/) (accessed on 9 May 2022), Then, we crawled the transaction records of each labeled account using the API provided by
Etherscan (
https://etherscan.io/labelcloud/) (accessed on 9 May 2022). We collected 111,956 Ethereum accounts and 220,714 Ethereum transactions by parsing these transaction records.
4.2. Dataset and Evaluation Metrics
We constructed 3359 ATGraphs and homogeneous transaction graphs for each labeled Ethereum account. In the case of homogeneous transaction graphs, edge features are set to transaction node features of ATGraph. ATGraphs include 332,670 nodes and 441,428 edges and homogeneous transaction graphs include 111,956 nodes and 220,714 edges. We adopted five metrics to evaluate the performance of the ATGraph including accuracy, precision, recall, the F1 score, and the area under the receiver operating characteristic (AUROC). The precision indicates the number of accurate predictions from the perspective of the prediction results. The recall indicates the number of true positive classes that are successfully recalled. The F1 score is the harmonic mean of the precision and recall used for the imbalanced dataset. The AUROC indicates the model’s ability to discriminate between positive and negative examples. Note that higher accuracy, precision, recall, F1 score, and AUROC indicate better prediction performance.
4.3. Experimental Setup
In the experiments, we adopted four graph learning algorithms to evaluate the performance of ATGraph including SF [
31], Graph2Vec [
32], graph convolutional network (GCN) [
33], graph isomorphism network (GIN) [
34], and GraphSAGE [
35]. SF and Graph2Vec are the network embedding algorithm, and others are the GNN models. We set the parameters of Graph2Vec as the default provided by the library with
wl_iterations = 2,
dimensions = 128,
down_samplings = 0.0001, and
min_count = 5. For SF, we set the parameters as a default with
dimension = 128 and
seed = 42. We used Adam [
36] as the optimization method in GNN models. We set the parameters of GNN models with
n_layers = {2, 3, 4},
batch_size = 64, and
hidden_unit = {16, 32, 64, 128}. In the GIN, we used sum, max, and mean aggregators. For the GraphSAGE, we used mean, GCN, and pool aggregators. The candidates of the parameters are shown as
Table 3. We found a set of parameters for the best performance using the grid search with 5-fold cross-validation in all approaches, including homogeneous transaction graphs and ATGraph. The models were run in PyTorch 1.11 [
37]. We used a deep graph library (DGL) 0.8.0 [
38] for the implementation of GNN models. For graph embedding algorithms, we used a karateclub library 1.2.3 [
39] and NetworkX 2.5.1 [
40].
4.4. Experimental Results and Analysis
4.4.1. Performance Comparison Analysis
We compare the performance of phishing account detection using ATGraph and the homogeneous transaction graph as input to evaluate ATGraph. The results of phishing account detection performance with the best parameters are presented in
Table 4. The performance of phishing account detection with ATGraph outperforms the performance with homogeneous transaction graphs in all graph learning algorithms. SF and Graph2Vec show the biggest performance difference of more than about 0.2 AUROC. It is because these methods are a network embedding algorithm based on a lower-dimensional structure. The network embedding algorithm utilizes the similarity of neighbor nodes, which means that it has a limitation in embedding multi-dimension edge features. In contrast, GraphSAGE has the lowest performance gain between the ATGraph and the homogeneous transaction graph. GraphSAGE aggregates neighbor node features and edge features to generate the center node features. It indicates that the detection performance with ATGraphs is more efficient in graph learning methods that utilize edge features less, such as SF. Moreover, the average AUROC with homogeneous transaction graphs is 0.8110, and that with the ATGraph is 0.9085. ATGraph outperforms the homogeneous graph by 0.0975 AUROC. It indicates that ATGraph eliminates multi-edges, making graph learning algorithms learn graph structures more efficiently Consequently, the detection performance using ATGraph as input outperforms using homogeneous transaction graphs, especially in the network embedding algorithms.
4.4.2. Node Features Analysis
We compared node features between normal and phishing accounts to provide a better understanding of cybercriminal accounts.
Table 5 compares normal and phishing account nodes’ average value of features. There are several notable feature differences. Phishing accounts have a short lifetime than normal accounts. Normal users use the same account to transfer their assets for a long period. In contrast, phishing accounts have a short active time versus normal accounts because they only used these accounts for fraud in a short period. Moreover, the balance of phishing accounts almost converges to zero. It is because phishing accounts are only used for fraud and transfer assets to their actual activated accounts. Therefore, the balance of normal accounts is more than zero, whereas the balance of phishing accounts is almost zero. For this reason, the ratio between the average of in-value and out-value also has a notable difference. Normal accounts have more in-value than out-value, but phishing accounts have more out-value than in-value. One more notable feature difference is the average interval between transactions. Phishing accounts steal multiple users’ assets in a short period because they are active for a short period. It means that there are many transactions for a short period in the phishing account. Therefore, the average interval between transactions of phishing accounts is shorter than in normal accounts.
5. Conclusions
In this paper, we proposed graph learning-based blockchain phishing account detection with a heterogeneous transaction graph. We proposed a novel graph structure called ATGraph, which represents transactions as nodes to eliminate the multi-edge. With ATGraph as input, graph learning algorithms can embed a graph structure effectively. We conducted experiments comparing Ethereum phishing account detection performance between ATGraph and homogeneous transaction graphs. The experimental results demonstrate that the detection performance with ATGraph outperforms that of a homogeneous transaction graph by up to 0.2 AUROC. It indicates that detecting phishing accounts with ATGraph is more efficient than using homogeneous transaction graphs as input. Moreover, ATGraphs are more efficient in the network embedding algorithms, which do not utilize edge features. We expect cybercriminal account detection to make blockchain networks more sustainable by regulating or blacklisting these accounts.
This work has several issues to be improved. ATGraph has a trade-off in the size of the graph. The number of nodes and edges is more than in homogeneous transaction graphs because ATGraph represents transaction edges as transaction nodes. Therefore, the more nodes and edges, the more time consumed to learn ATGraph than homogeneous transaction graphs. Moreover, the Ethereum network has two types of accounts, such as contract accounts and externally owned accounts, but we did not consider these account types in this work. In the future, we will design a novel graph learning model suitable for ATGraph to detect phishing accounts more effectively. In addition, we will consider various node/edge types to represent the heterogeneity of the Ethereum network more.