Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities
Abstract
:1. Introduction
- Designed an efficient Blockchain-based authentication and trust management mechanism for smart cities;
- A practical implementation of a Blockchain-based security mechanism for secure authorization of smart city resources;
- Developed a user-friendly hybrid application to interact and control heterogeneous IoT resources.
- To mutually authenticate clients and servers and establish trust among them so that only legitimate users may access the system and the servers may become validated by the clients;
- To secure the key exchange mechanism among clients and servers;
- To authorize the users so that a resource can only be accessed by the users authorized for that resource;
- To provide monitoring and control of the smart city resources to the manager/admin of the system.
2. Related Work
3. Overview of Blockchain Technology
- A Blockchain exploits hash-based encryption algorithms for the addition or updating of transactions to the ledger. The main characteristics that belong to hashing techniques are the avalanche effect, deterministic, one-way cryptography, must withstand collisions, and faster computation. Blockchain uses the SHA-256 hashing algorithm.
- Mining: It is the process of securing and verifying transactions. It demands high computing speed to attain and acquire the reward. It requires miners to add transaction data to the ledger. In the ledgers, blocks are connected and develop a chain that is secured by Blockchain miners.
- Immutable ledger: In a Blockchain network, all transactions are recorded. An immutable ledger means recorded transactions cannot be altered or tampered with.
- Consensus protocol: It is a procedure through which all the Blockchain nodes reach a common consensus regarding the present state of the distributed ledger. It helps in achieving reliability and establishing trust between unknown nodes in the Blockchain network.
- Distributed P2P Networking: To distribute and update the data at the nodes of the Blockchain network, all transactions are broadcasted over the network.
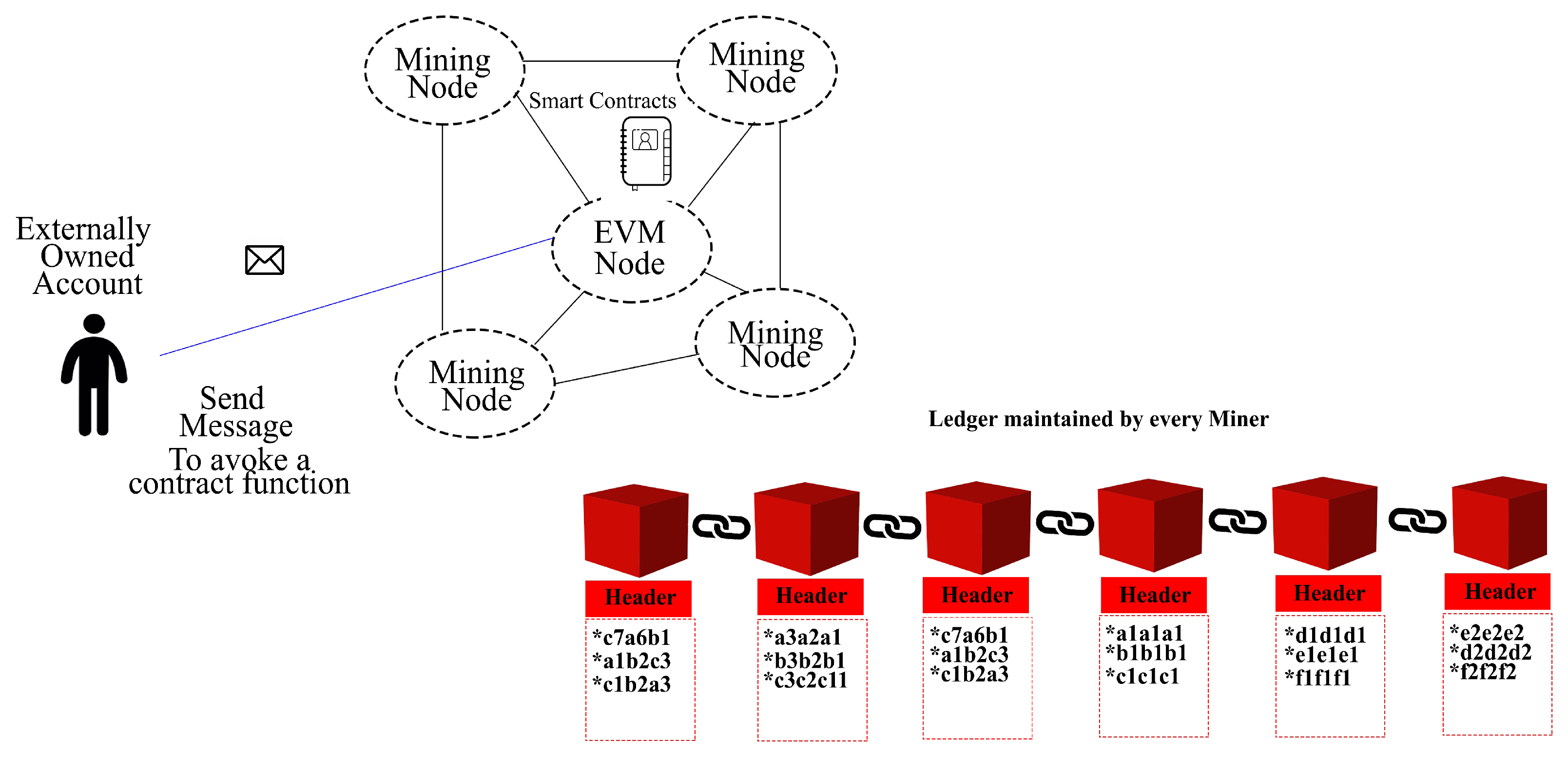
Ethereum Blockchain Architecture
4. Proposed Solution
- Authorization Servers: These are used to generate access tokens.
- Resource servers: These generate/store protected resources.
- Proxy Servers: These store protected resources and act as access interface for clients.
- Resource Publishers/Owners: These are the original owners of resource servers and their corresponding resources.
- Key Servers: These are used to generate keys for encryption/decryption of the resources.
- Client/User application: Third party that requests access to the protected resources.
4.1. Authorization Blockchain
- One of the prominent features of Ethereum is that it is programmable. All the contracts and agreements are part of the code enabling transactions to be executed automatically. With the help of its smart contracts, users can exchange anything having value, e.g., money, property, etc. These smart contracts can also invoke other contracts and may have lots of conditions and supported formats.
- Ethereum is not only confined to cryptocurrency transactions but any transactions related to supply chains, energy grids, real estate, government registries, etc.
- It is proven that Ethereum is robust in nature against security attacks.
- It is open, flexible, and supports both permissionless and permissioned implementations.
- An Ethereum network can support up to hundreds of nodes and millions of users, a number much larger than its competitors.
- Ethereum consortia are not dependent on some single vendor, rather it is interoperable.
4.2. Resource Servers
4.3. Resource Owners/Publishers
4.4. Key Servers
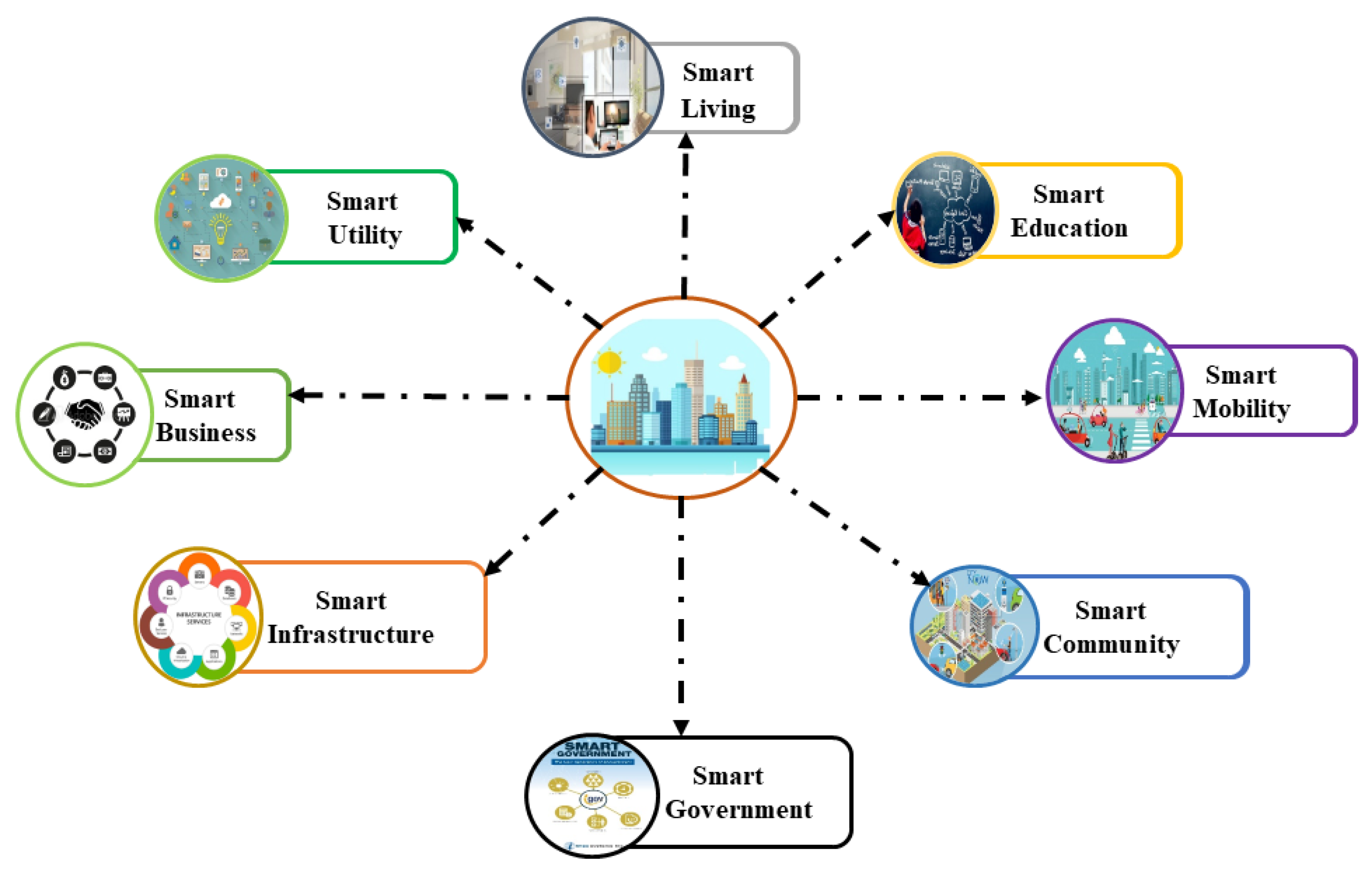
4.5. Simulation/Creation of Smart City
4.6. Integration of Smart City with Authorization Blockchain
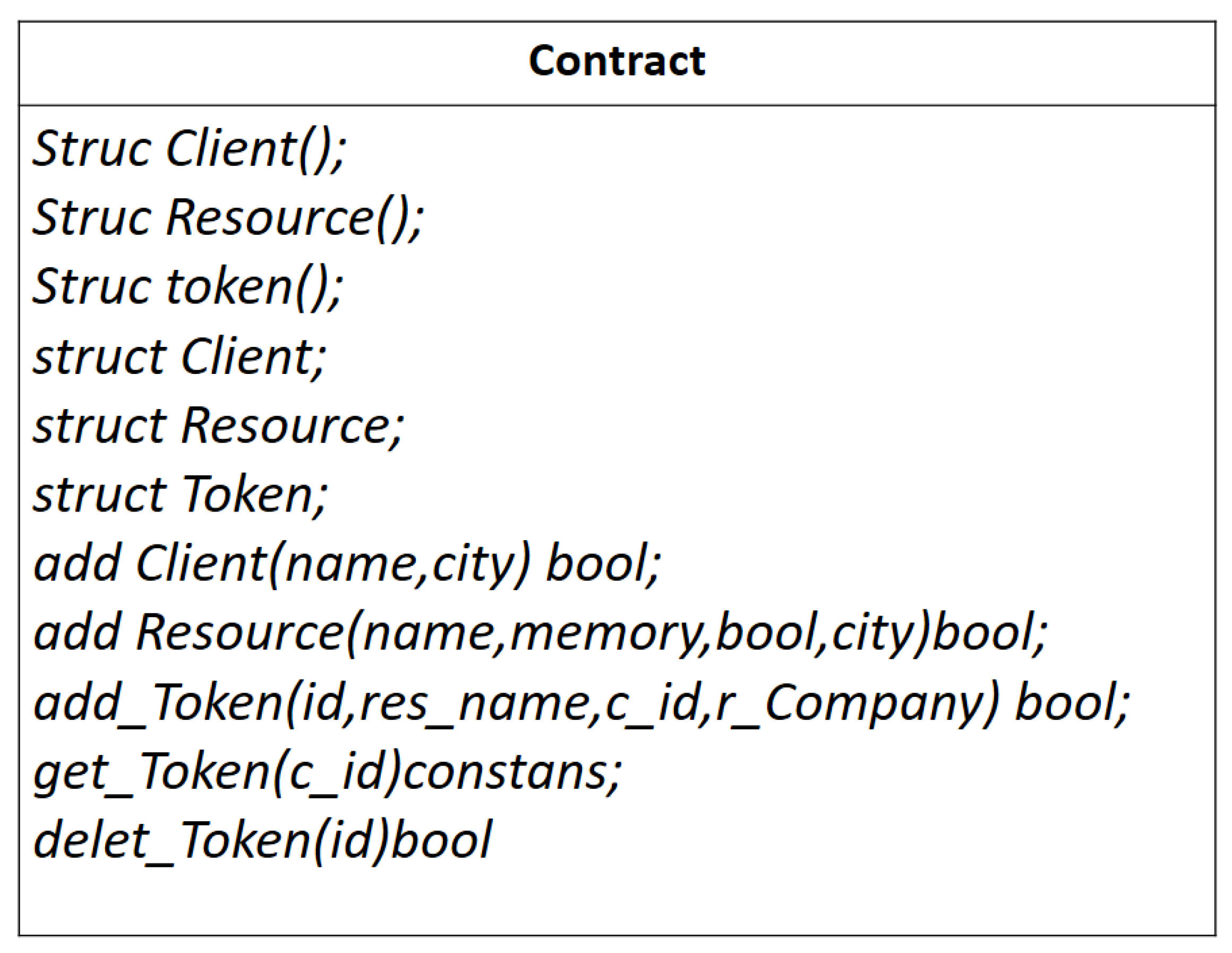
4.6.1. Smart Contract Writing
4.6.2. Migrations
4.6.3. Access Control for Blockchain at Application/Browser Level (Metamask)
4.6.4. Data Fetching from Smart Contract
4.7. User Application
- Create an Ethereum Blockchain wallet and acquire the public and private keys for wallet authentication.
- Connect wallet to metamask by providing public and private keys. The metamask provides a 14-word memic which can be used for the retrieval of the wallet in case of keys stolen.
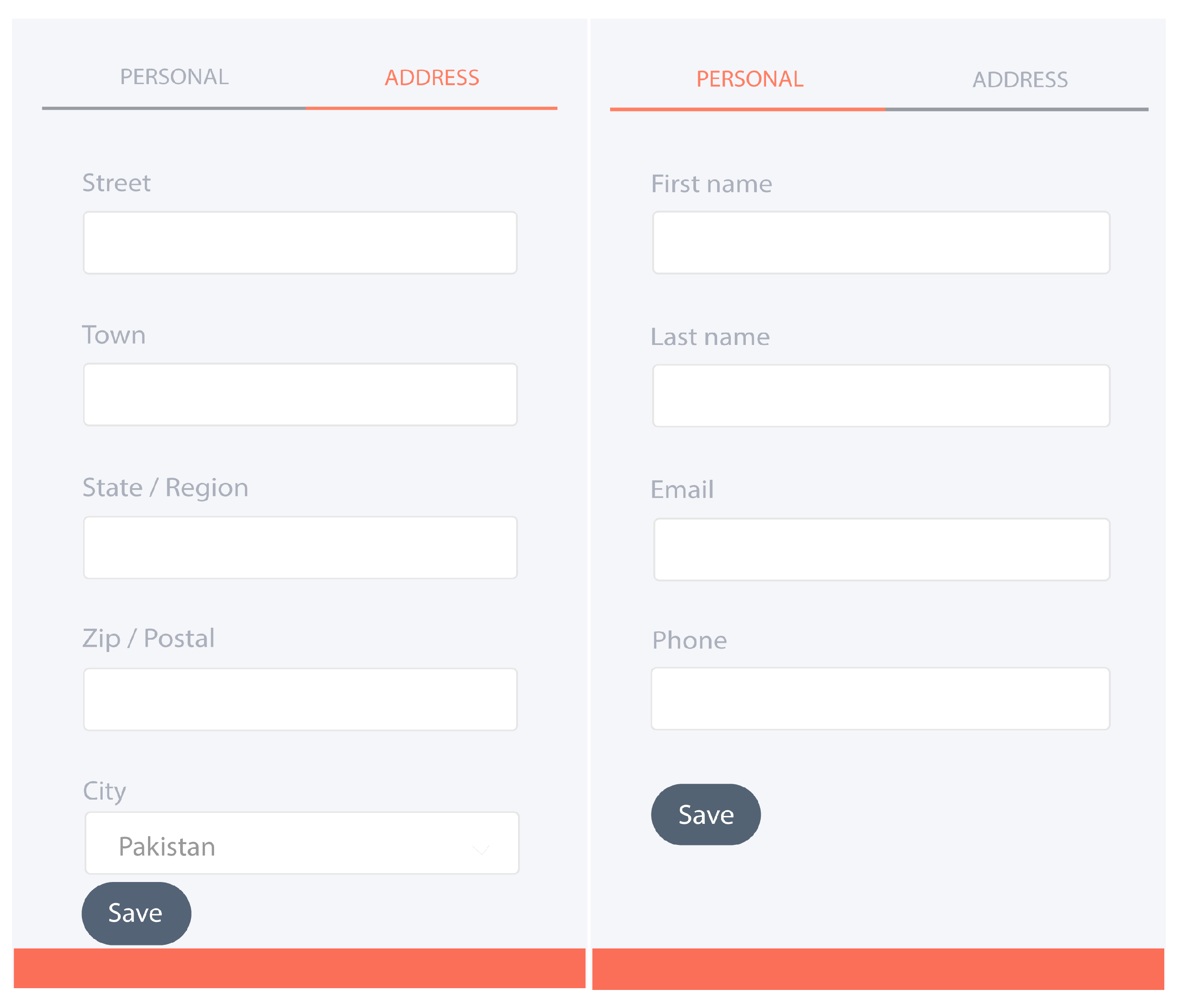
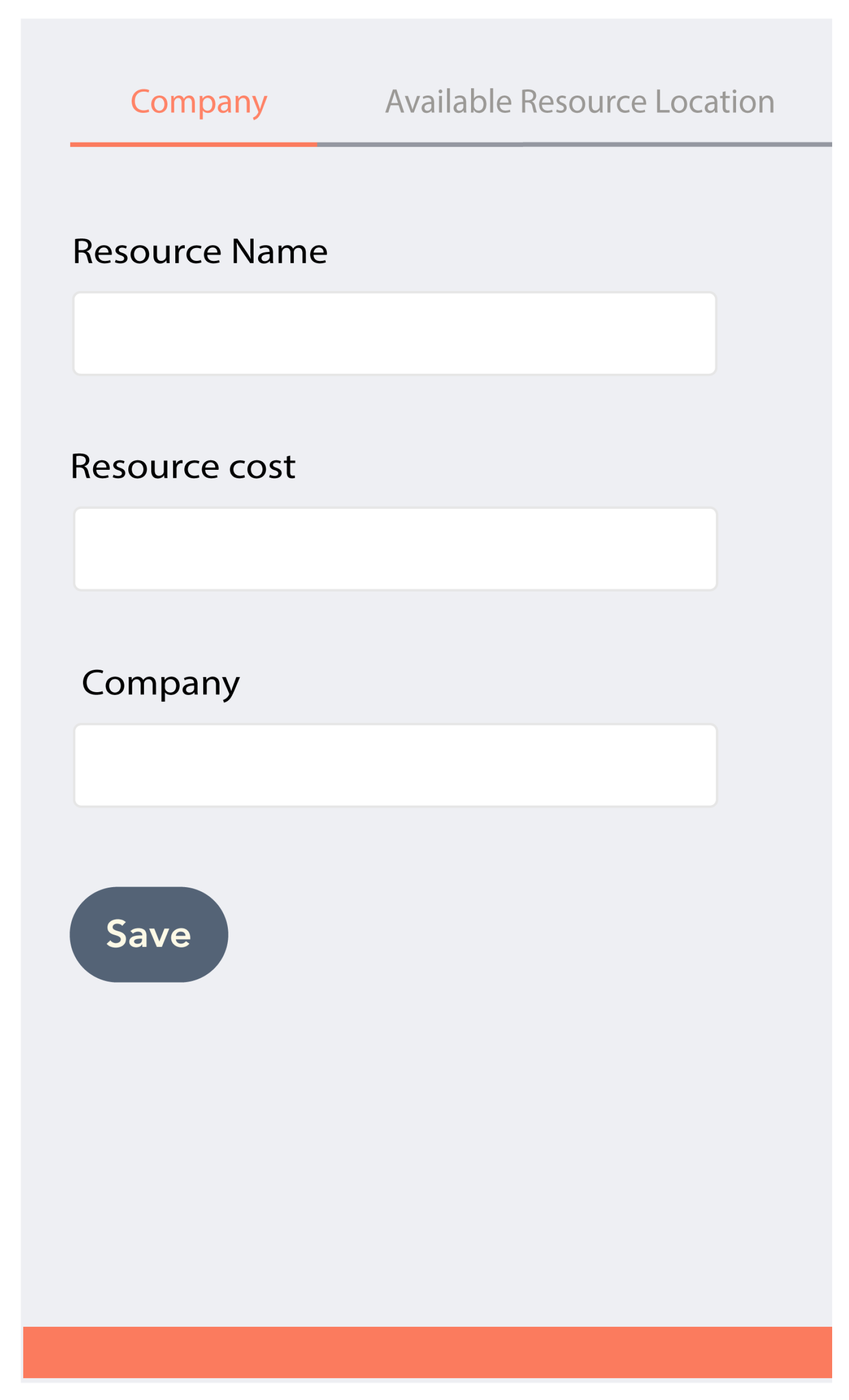
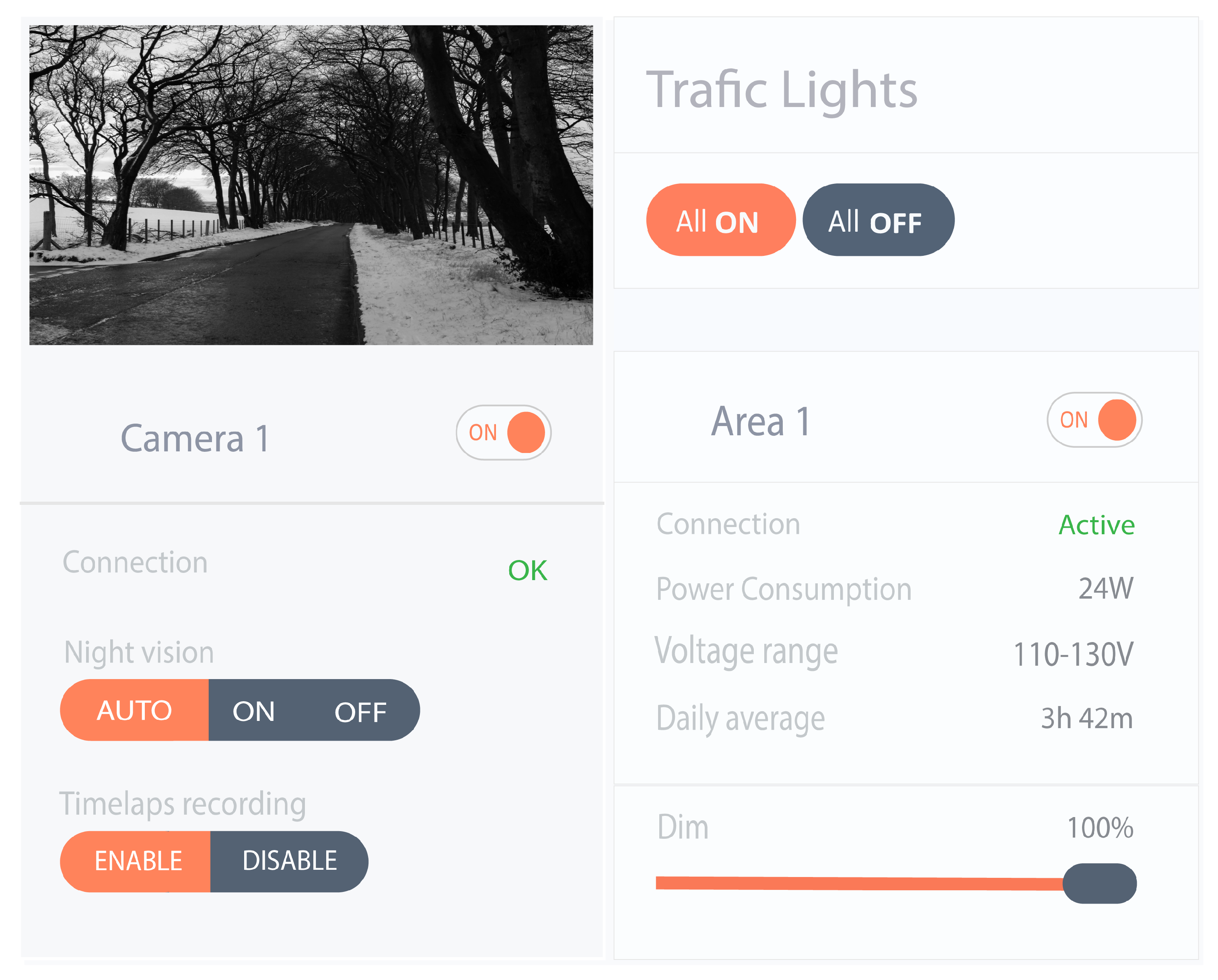
- Open the application that asks the user to provide the necessary information as shown in Figure 12. The information provided at the time of startup is used for contract and resources provision.
4.8. Overall Working Flow
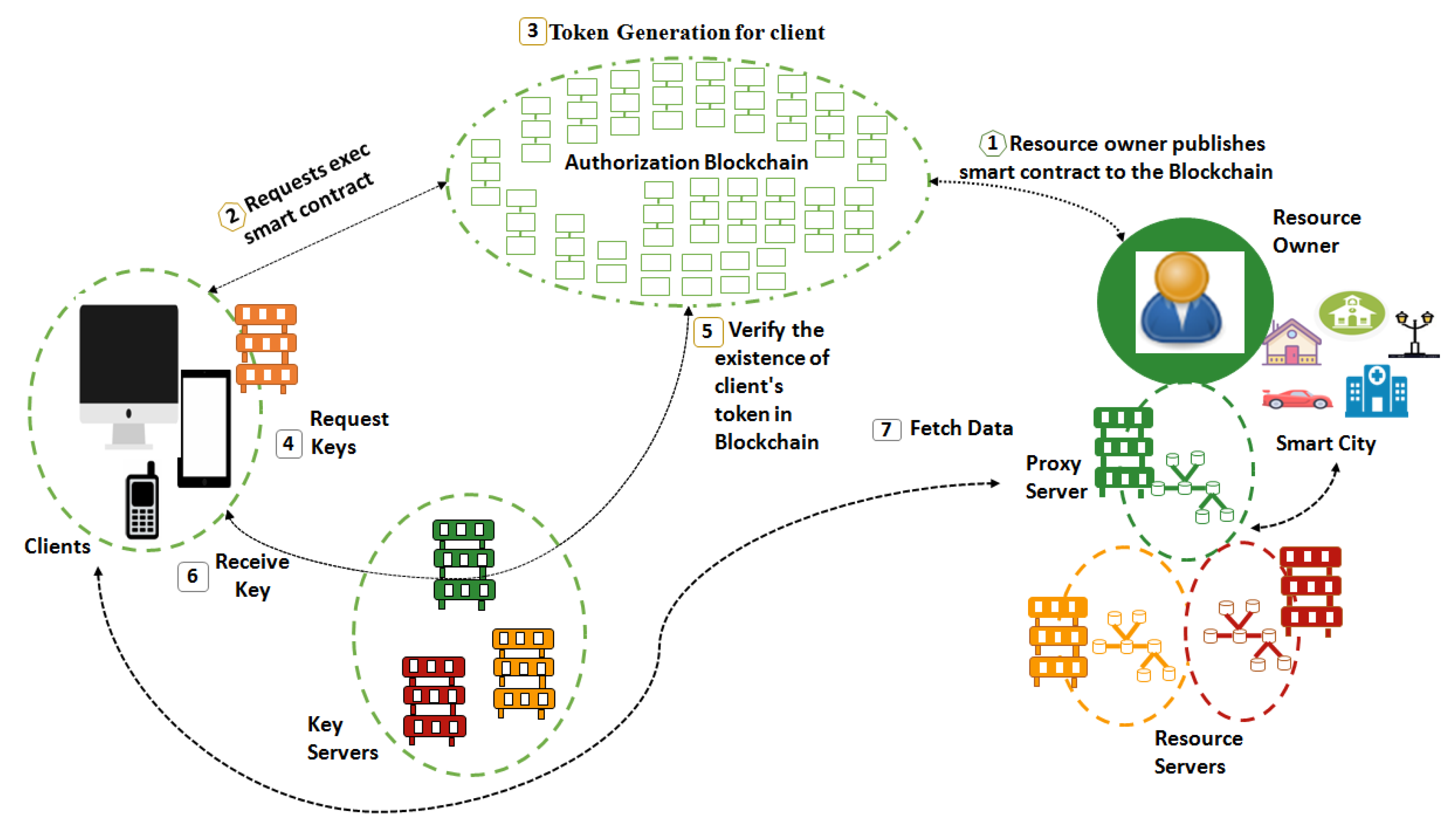
- The resource owner/provider (government institutions) creates a smart contract to publish it to the Blockchain.
- The client that wants to acquire the protected resources sends a transaction to the particular smart contract address. The transaction is broadcast to all the Blockchain network nodes. The process of validation will be started, and miners will take part in it.
- If the client meets certain requirements of the contract, then an access token will be generated. The access token describes the specific access rights (start time, expiry time, location, resource name) for the protected resources.
- After the consensus, when the transaction is confirmed, smart contracts will be executed.
- The contract transaction will be added to the contract and a token will be generated which will be the basic key for further processing.
- The client then requests the key server for the necessary decryption keys to decrypt the resources.
- The key server has a replica of the token. For the access token, the key server queries the internal storage of the responsible smart contract.
- The key server generates a challenge response based on the client address given in the token to prove the authenticity of the client. This challenge can be solved by only the legitimate client that triggered the smart contract.
- The client receives a personal key and takes part in the self-healing group key distribution process after completing the challenge.
- Finally, the encrypted resources can be downloaded by client proxy or resource server. Both of these servers offer RESTful CoAP API which enables GET, POST, and PUT resources using Uniform Resource Identifier (URI).
5. Experimental Analysis and Discussion
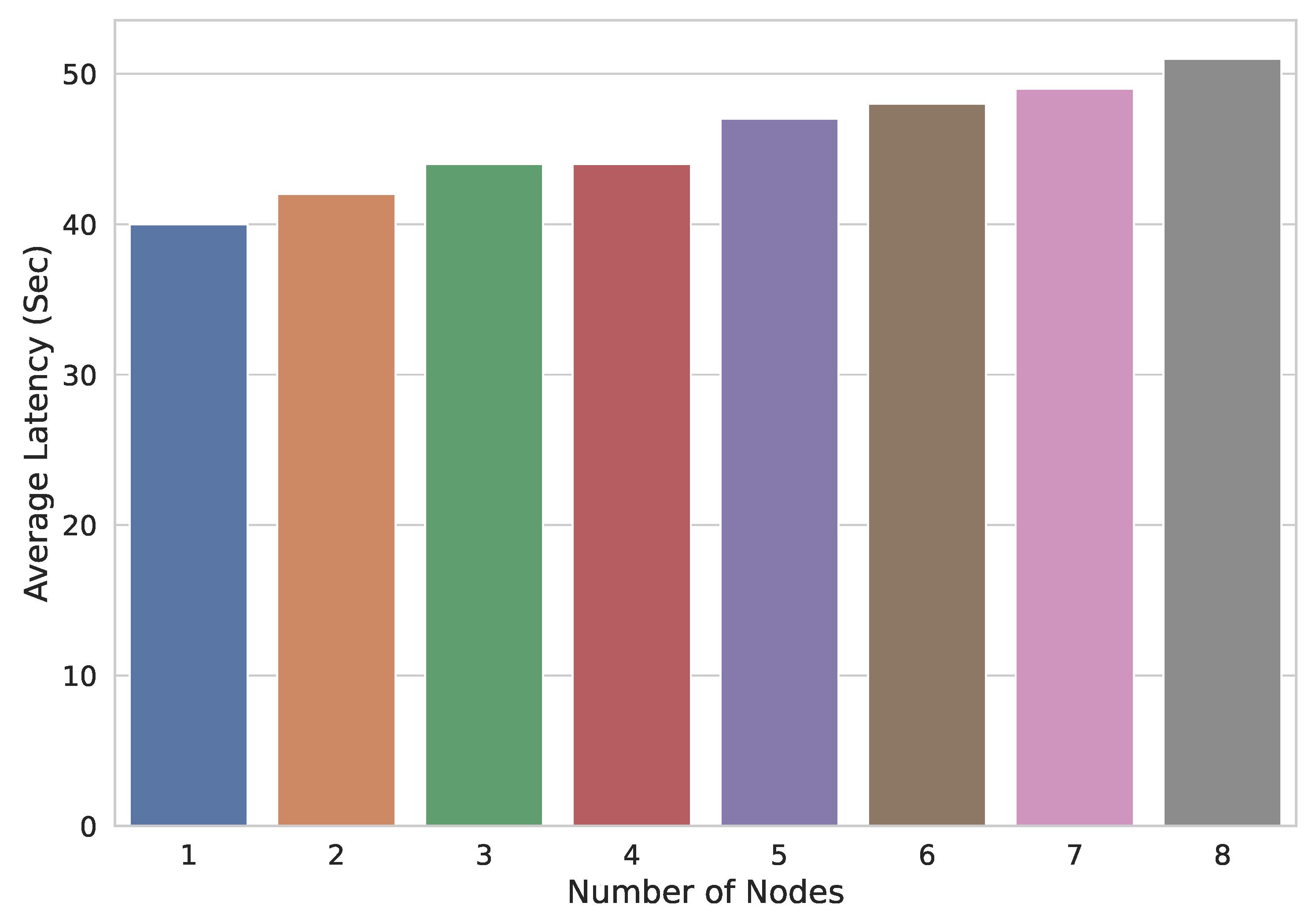
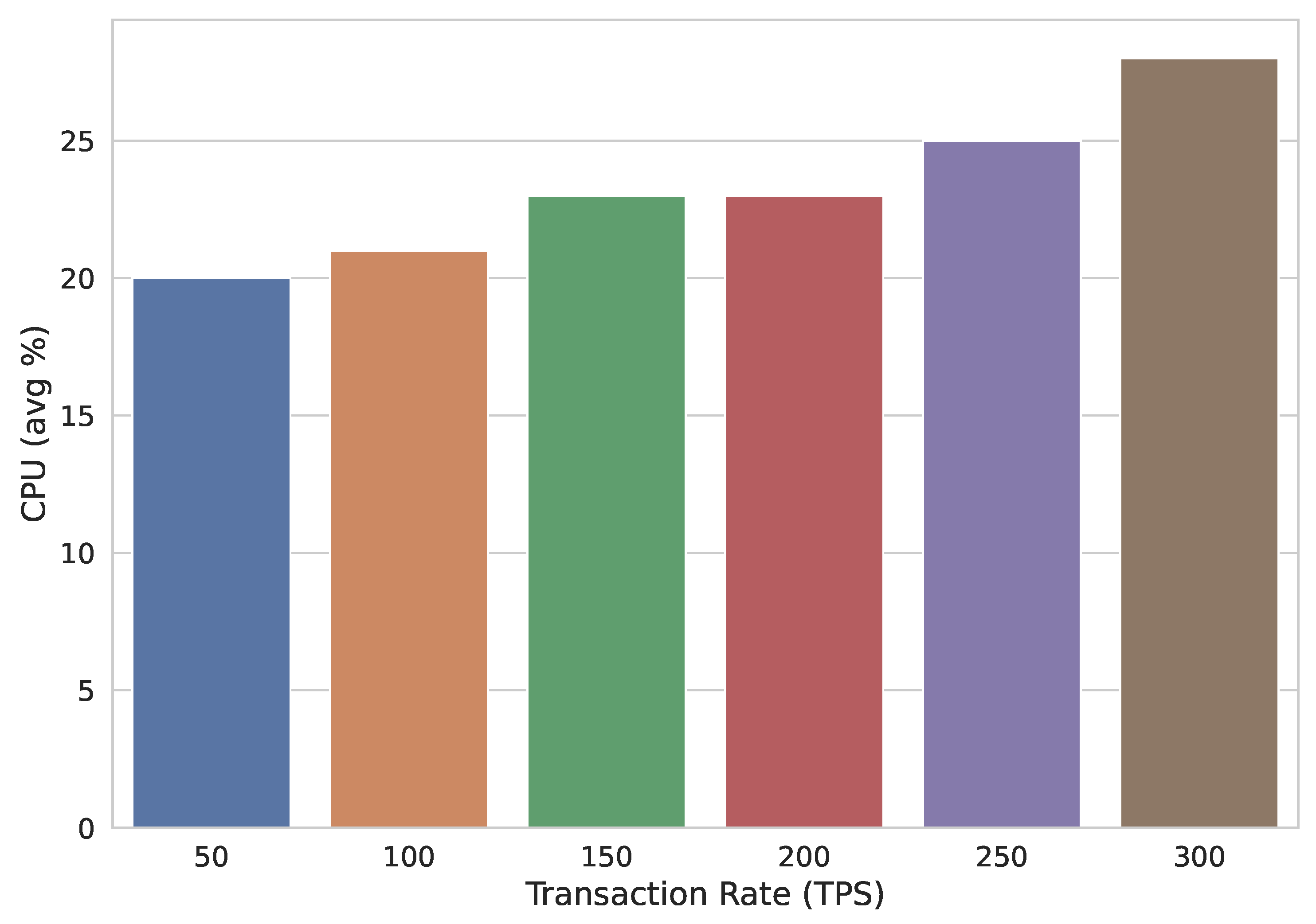
5.1. Evaluation of Key Server and Resource Server
5.2. Smart City Resource Publishing and Controlling through User Application
5.2.1. Publishing Resource
5.2.2. Accessing and Controlling of Resources
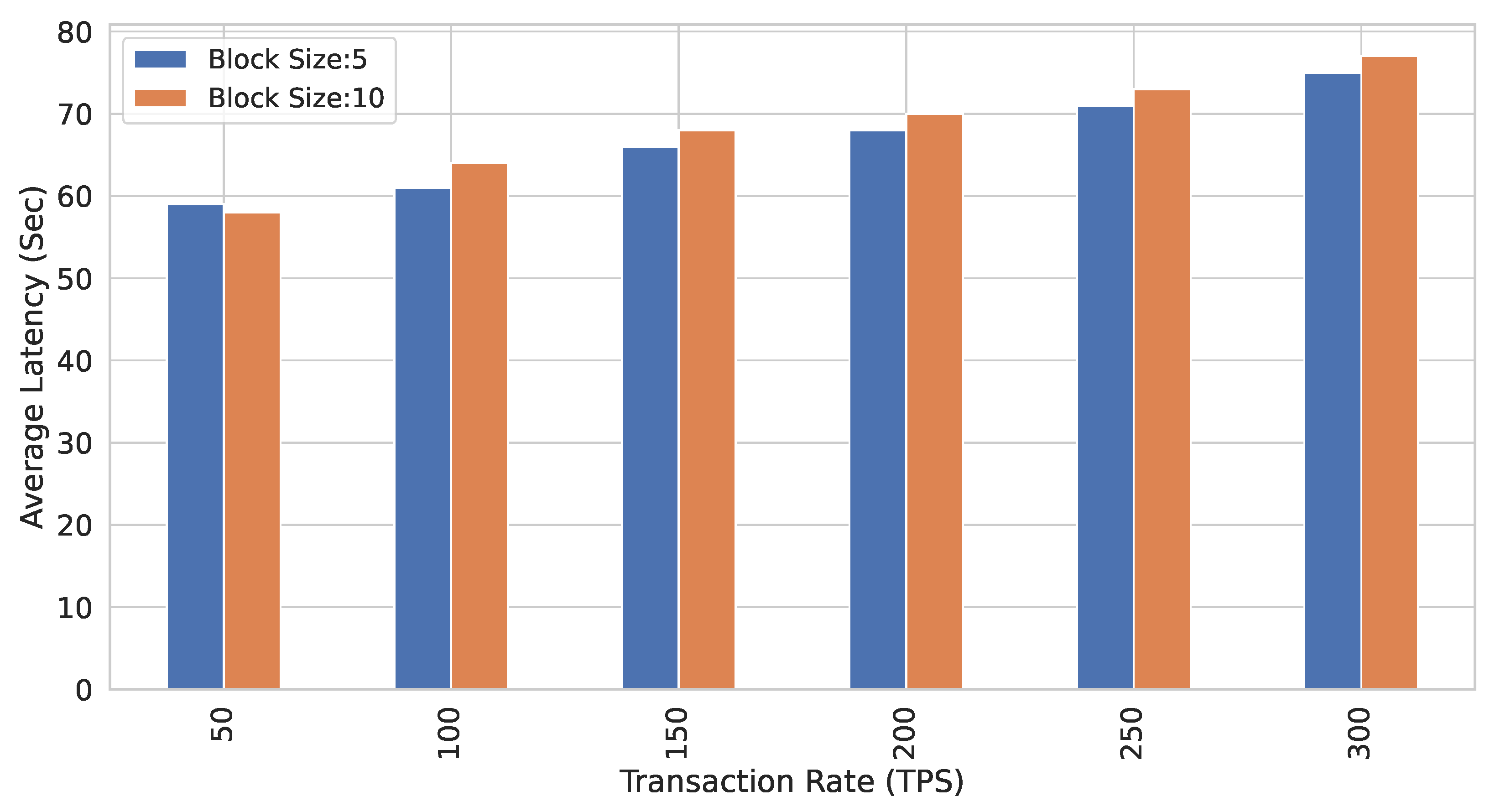
5.3. Comparative Analysis
5.4. Security Analysis
5.4.1. Formal Security Analysis
- Authorization: In the context of a Blockchain-based proposed mechanism, authorization means that an attacker should not be able to acquire or use encrypted resources accessible to some authorized clients at resource server until more than 50% of nodes of authorization Blockchain are corrupted. Formally, it can be said that is secure with respect to authorization under the following conditions: if at a point an attacker can access the encrypted resources that are accessible to some authorized client at for some resource owner , then the is corrupt or, if ≠ ⊥, it implies or at least one of the trusted of must be corrupted. As we know, if = ⊥, then the resource is accessed in the client credentials mode and is not related to a client.
- Authentication: In the context of a Blockchain-based proposed mechanism, authentication for resource server means that an attacker should not be able to acquire an access token under the identity of a valid client unless certain parties involved are corrupted. Being authenticated at means to have a valid access token from authorization server (). Formally, it can be said that is secure with respect to authentication under the following conditions: if an attacker is able to access the service token issued by a valid for a client , then either the client or one of the valid resource servers must be corrupted. In the case of the proposed Blockchain-based mechanism, the authentication and authorization are performed by authorization Blockchain nodes. Until more than 50% of nodes of are corrupted, the authorization can never fail. It is the realistic assumption adopted by the Blockchain that it would carry more honest nodes than the malicious nodes . So, in our case, unauthorized access would not be possible because > .
- Session Integrity: The session integrity from the authorization perspective is (1) a client is only authorized to access the resources of the resource server when a client has a valid access token and (2) no other client can generate the access request on the behalf of the valid client because each access request is signed by the corresponding valid client . Formally, it can be said that is secure with respect to session integrity for authorization if the following conditions are fulfilled: (1) if in an iteration for , the challenge response flow is successful for a particular client and (2), additionally, the resource server is honest to provide resources only to a client who already has successfully completed the challenge response flow. The authorization Blockchain is secure with respect to session integrity for authentication if the following conditions are fulfilled: (1) if in an iteration for , the transaction request sent by a client is successfully verified by the miners and a valid access token is granted to it as a result of the execution of the smart contract and (2), additionally, the resource server is honest to provide resources only to a client who already has successfully acquired the valid access token.
5.4.2. Informal Security Analysis
- Scenario-1: Personal keys may become compromised while sharingThe personal keys are exchanged on DTLS channels which are based on TLS. So, there is no chance of eavesdropping, tampering, or message forgery while exchanging the keys. It ensures secure exchange of personal keys among different servers and clients. So, only the authorized client/server may obtain its key.
- Scenario-2: An unauthorized client may request a resource or a fake key server may be thereCertificates are used to provide authentication between key and resource servers. The clients and key servers authenticate themselves through a challenge/response mechanism. Integrity of transactions are preserved by the use of signatures.
- Scenario-3: The access token may be captured and misused by the attackerThe proposed system is built upon ACE. In ACE, the client identity is bounded with the access token using the concept of proof of possession (PoP). Whenever a request is sent from a client for the token, the ACE server binds a key to the token. The resource server can access this key and it is known to the client that placed the request. The resource server in turn creates a challenge response based on this key to verify whether the client is the owner of the token or not. So, what the attacker needs to do is to compromise only one authorization server to capture the valid tokens. In the proposed framework, this issue was resolved by demanding a public key from the client that triggers the smart contract. This public key of the client becomes part of the access token and is saved on Blockchain. The key server creates a challenge/response with the help of this key to verify the client’s identity who is demanding decryption keys. Now, an attacker is required to compromise at-least 51% of the miners to accomplish the desired task.
- Scenario-4: DoS attack can be performed on any networkDenial of Service (DoS) attack possibility is always there and also on any infrastructure of Blockchain. Several measures are taken in the proposed framework to reduce the risk associated with such types of attacks. One possible scenario may be that a malicious user may repeatedly trigger smart contracts. This would create a huge volume of traffic in the Blockchain network as all requests need to be broadcasted and verified by the miners. It is minimized in a Blockchain-based network by presenting a client with some kind of a cryptographic puzzle before every transaction. This would flatten the attack. Furthermore, the execution time limit on the smart contracts is set on a lower side in the proposed framework. This helped in identifying the bogus requests without providing the gas value as is required in the Ethereum Blockchain. So, the smart contract would be halted in this case and all changes would be roll-backed.
5.5. Technical Challenges and Limitations
- Both smart cities and Blockchain are in their infancy so a lot of research work is still required to integrate these.
- Shifting from a conventional centralized IoT system to a decentralized Blockchain network requires technical efforts to be made in right directions.
- Conventional security and privacy architectures are inapplicable in the spectrum of smart cities due to its resource constraints. Most of the IoT devices are not designed to meet the basic security and privacy parameters which produce the security, confidentiality, privacy, authentication, data integrity, and access control issues.
- A permissionless Blockchain is hard to implement and deploy in some institutions because it lacks in trust and is uncontrollable in nature.
- There are only a limited number of accounts available (i.e., 10 in the case of Ganache) to implement and test the efficacy of any proposed solution.
6. Conclusions and Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ratasich, D.; Khalid, F.; Geissler, F.; Grosu, R.; Shafique, M.; Bartocci, E. A Roadmap Toward the Resilient Internet of Things for Cyber-Physical Systems. Access IEEE 2019, 7, 13260–13283. [Google Scholar] [CrossRef]
- Yang, C.; Li, X.; Yu, Y.; Wang, Z. Basing Diversified Services of Complex IoT Applications on Scalable Block Graph Platform. Access IEEE 2019, 7, 22966–22975. [Google Scholar] [CrossRef]
- Jindal, F.; Jamar, R.; Churi, P. Future and Challenges of Internet of Things. Int. J. Comput. Sci. Inf. Technol. (IJCSIT) 2018, 10, 13–25. [Google Scholar] [CrossRef]
- Ali, M.S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M.H. Applications of Blockchains in the Internet of Things: A Comprehensive Survey. Commun. Surv. Tutor. IEEE 2019, 21, 1676–1717. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas Security Threats and Solution Architectures. Access IEEE 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Yetis, R.; Sahingoz, O.K. Blockchain Based Secure Communication for IoT Devices in Smart Cities. In Proceedings of the 7th International Istanbul Smart Grids and Cities Congress and Fair (ICSG), Istanbul, Yurkey, 25–26 April 2019; pp. 134–138. [Google Scholar]
- Jyothi, V.; Krishna, M.G.; Raveendranadh, B.; Rupalin, D. IOT Based Smart Home System Technologies. Int. J. Eng. Res. Dev. 2017, 13, 31–37. [Google Scholar]
- Alkandari, A.; Alnasheet, M.; Alshekhly, I.F.T. Smart Cities: Survey. J. Adv. Comput. Sci. Technol. Res. 2012, 2, 79–90. [Google Scholar]
- Sun, Y.; Song, H.; Jara, A.J.; Bie, R. Internet of Things and Big Data Analytics for Smart and Connected Communities. IEEE Access 2016, 4, 766–773. [Google Scholar] [CrossRef]
- Song, H.; Srinivasan, R.; Sookoor, T.; Jeschke, S. Smart Cities: Foundations, Principles and Applications; Wiley: Hoboken, NJ, USA, 2017; pp. 1–906. ISBN 978-1-119-22639-0. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of Blockchain technology: Architecture, consensus, and future trends. In Proceedings of the IEEE International Congress on in Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017. [Google Scholar]
- Chen, J.; Lv, Z.; Song, H. Design of personnel big data management system based on blockchain. Future Gener. Comput. Syst. 2019, 101, 1122–1129. [Google Scholar] [CrossRef] [Green Version]
- Kim, S.-K. Enhanced IoV Security Network by Using Blockchain Governance Game. Mathematics 2021, 9, 109. [Google Scholar] [CrossRef]
- Kim, S.-K. Blockchain Governance Game. Comput. Ind. Eng. 2019, 136, 373–380. [Google Scholar] [CrossRef] [Green Version]
- Crosby, M.; Nachlappan; Pattanayak, P.; Verma, S.; Kalyanarman, V. Blockchain Technology; Sutardja Center for Entrepreneurship and Technology Technical Report; University of California: Berkeley, CA, USA, 2015; Available online: https://scet.berkeley.edu/wp-content/uploads/BlockchainPaper.pdf (accessed on 24 March 2022).
- Sairam, R.; SankarBhunia, S.; Thangavel, V.; Gurusamy, M. NETRA: Enhancing IoT Security Using NFV-Based Edge Traffic Analysis. Sens. J. IEEE 2019, 19, 4660–4671. [Google Scholar] [CrossRef] [Green Version]
- Sagirlar, G.; Carminati, B.; Ferrari, E.; Sheehan, J.D.; Ragnoli, E. Hybrid-IoT: Hybrid Blockchain Architecture for Internet of Things—PoW Sub-Blockchains. In Proceedings of the Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) 2018 IEEE International Conference, Halifax, NS, Canada, 30 July–3 August 2018; pp. 1007–1016. [Google Scholar]
- Paillisse, J.; Subira, J.; Lopez, A.; Rodriguez-Natal, A.; Ermagan, V.; Maino, F.; Cabellos, A. Distributed Access Control with Blockchain. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Siris, V.A.; Dimopoulos, D.; Fotiou, N.; Voulgaris, S.; Polyzos, G.C. OAuth 2.0 meets Blockchain for Authorization in Constrained IoT Environments. In Proceedings of the IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 364–367. [Google Scholar]
- Riabi, I.; Ayed, H.K.B.; Saidane, L.A. A survey on Blockchain-based access control for Internet of Things. In Proceedings of the 15th International Wireless Communications and Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 502–507. [Google Scholar]
- Siris, V.A.; Dimopoulos, D.; Fotiou, N.; Voulgaris, S.; Polyzos, G.C. Trusted D2D-Based IoT Resource Access Using Smart Contracts. In Proceedings of the IEEE 20th International Symposium on a World of Wireless Mobile and Multimedia Networks (WoWMoM), Washington, DC, USA, 10–12 June 2019; pp. 1–9. [Google Scholar]
- Dawod, A.; Kopoulos, D.G.; Jayaraman, P.P.; Nirmalathas, A. Advancements towards Global IoT Device Discovery and Integration. In Proceedings of the IEEE International Congress on Internet of Things (ICIOT), Milan, Italy, 8–13 July 2019; pp. 147–155. [Google Scholar]
- Alphand, O.; Amoretti, M.; Claeys, T.; Asta, S.D.; Duda, A.; Ferrari, G.; Rousseau, F.; Tourancheau, B.; Veltri, L.; Zanichelli, F. IoTChain: A Blockchain security architecture for the Internet of Things. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Rescorla, E.; Modadugu, N. Datagram Transport Layer Security Version 1.2. Internet Requests for Comments, RFC Editor, RFC 6347, January 2012. Available online: http://www.rfc-editor.org/rfc/rfc6347.txt (accessed on 2 February 2022).
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in Internet of Things: Challenges and Solutions. 2016. Available online: https://arxiv.org/ftp/arxiv/papers/1608/1608.05187.pdf (accessed on 2 February 2022).
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain Technologies for the Internet of Things: Research Issues and Challenges. Internet Things J. IEEE 2019, 6, 2188–2204. [Google Scholar] [CrossRef] [Green Version]
- Danzi, P.; Kalør, A.E.; Stefanović, Č.; Popovski, P. Delay and Communication Tradeoffs for Blockchain Systems with Lightweight IoT Clients. Internet Things J. IEEE 2019, 6, 2354–2365. [Google Scholar] [CrossRef] [Green Version]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Internet Things J. 2018, 8, 1184–1195. [Google Scholar] [CrossRef]
- Samaniego, M.; Deters, R. Using Blockchain to Push Software- Defined IoT Components Onto Edge Hosts. In Proceedings of the International Conference on Big Data and Advanced Wireless Technologies, Blagoevgrad, Bulgaria, 10–11 November 2016. [Google Scholar]
- Kravitz, D.W.; Cooper, J. Securing User Identity and Transactions Symbiotically: IoT meets Blockchain. In Proceedings of the 2017 Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; pp. 1–6. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Towards an Optimized Blockchain for IoT. In Proceedings of the Second International Conference on Internet-of-Things Design and Implementation, Pittsburgh, PA, USA, 18–21 April 2017; pp. 173–178. [Google Scholar]
- IOTA. Available online: https://www.iota.org/ (accessed on 2 February 2022).
- Internet of Trusted Things (IoTeX). Available online: https://www.iotex.io/ (accessed on 2 February 2022).
- Securely Connect, Manage and Analyze IoT Data with Watson IoT Platform. Available online: https://www.ibm.com/internet-of-things/solutions/iot-platform/watson-iot-platform (accessed on 2 February 2022).
- Ambrosus- Decentralized IoT Networks. Available online: https://ambrosus.com/ (accessed on 2 February 2022).
- Waltonchain-The Global Leader in Blockchain+IoT. Available online: https://www.waltonchain.org/en/ (accessed on 2 February 2022).
- Origintrail. Available online: https://origintrail.io/ (accessed on 2 February 2022).
- Atonomi-Bringing Trust and Security to IoT. Available online: https://atonomi.io/ (accessed on 2 February 2022).
- Yue, X.; Wang, H.; Jin, D.; Li, M.; Jiang, W. Healthcare data gateways: Found healthcare intelligence on blockchain with novel privacy risk control. J. Med. Syst. 2016, 40, 218. [Google Scholar] [CrossRef] [PubMed]
- Liang, X.; Zhao, J.; Shetty, S.; Liu, J.; Li, D. Integrating blockchain for data sharing and collaboration in mobile healthcare applications. In Proceedings of the IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y.; Ma, M.; He, J. Blochie: A blockchain-based platform for healthcare information exchange. In Proceedings of the IEEE International Conference on Smart Computing (SMARTCOMP), Taormina, Italy, 18–20 June 2018; pp. 49–56. [Google Scholar]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 136. [Google Scholar] [CrossRef] [PubMed]
- Tanwar, S.; Parekh, K.; Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 2020, 50, 102407. [Google Scholar] [CrossRef]
- Habibzadeh, H.; Nussbaum, B.H.; Anjomshoa, F.; Kantarci, B.; Soyata, T. A survey on cybersecurity, data privacy, and policy issues in cyber-physical system deployments in smart cities. Sustain. Cities Soc. 2019, 50, 101660. [Google Scholar] [CrossRef]
- Khan, P.W.; Byun, Y.-C.; Park, N. A Data Verification System for CCTV Surveillance Cameras Using Blockchain Technology in Smart Cities. Electronics 2020, 9, 484. [Google Scholar] [CrossRef] [Green Version]
- Malik, M.N.; Azam, M.A.; Ehatisham-Ul-Haq, M.; Ejaz, W.; Khalid, A. ADLAuth: Passive Authentication Based on Activity of Daily Living Using Heterogeneous Sensing in Smart Cities. Sensors 2019, 19, 2466. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Meshram, C.; Ibrahim, R.W.; Deng, L.; Shende, S.W.; Meshram, S.G.; Barve, S.K. A robust smart card and remote user password-based authentication protocol using extended chaotic maps under smart cities environment. Soft Comput. 2021, 25, 10037–10051. [Google Scholar] [CrossRef]
- Espositoa, C.; Ficco, M.; Gupta, B.B. Blockchain-based authentication and authorization for smart city applications. Inf. Process. Manag. 2021, 58, 102468. [Google Scholar] [CrossRef]
- Ibba, S.; Pinna, A.; Seu, M.; Pani, F.E. CitySense: Blockchain-oriented Smart Cities. In Proceedings of the XP2017 Scientific Workshops, Cologne, Germany, 22–26 May 2017; pp. 1–5. [Google Scholar]
- Suciu, G.; Nădrag, C.; Istrate, C.; Vulpe, A.; Ditu, M.; Subea, O. Comparative Analysis of Distributed Ledger Technologies. In Proceedings of the IEEE Global Wireless Summit (GWS), Chiang Rai, Thailand, 25–28 November 2018. [Google Scholar]
- Rejeb, A.; Rejeb, K.; Simske, S.J.; Keogh, J.G. Blockchain technology in the smart city: A bibliometric review. Qual. Quant. 2021, 1–32. [Google Scholar] [CrossRef]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5g-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2019, 135, 1–19. [Google Scholar] [CrossRef]
- Kabra, N.; Bhattacharya, P.; Tanwar, S.; Tyagi, S. Mudrachain: Blockchain-based framework for automated cheque clearance in financial institutions. Future Gener. Comput. Syst. 2020, 102, 574–587. [Google Scholar] [CrossRef]
- Ethereum. Available online: https://www.ethereum.org/ (accessed on 2 February 2022).
- Ganache-One Click Blockchain. Available online: https://www.trufflesuite.com/ganache (accessed on 2 February 2022).
- Rasberry. Available online: https://www.raspberrypi.org/ (accessed on 2 February 2022).
- Solidity. Available online: https://en.wikipedia.org/wiki/Solidity (accessed on 2 February 2022).
- Node.js. Available online: https://nodejs.org/ (accessed on 2 February 2022).
- Metamask. Available online: https://metamask.io/ (accessed on 2 February 2022).
- Web3.js—Ethereum JavaScript API. Available online: https://web3js.readthedocs.io/en/v1.2.1/ (accessed on 2 February 2022).
- Meteor: Build Apps with JavaScript. Available online: https://www.meteor.com/ (accessed on 2 February 2022).
- MutiChain. Available online: https://www.multichain.com/ (accessed on 2 February 2022).
- Hyperledger. Available online: https://www.hyperledger.org/ (accessed on 2 February 2022).
- Chain Core. Available online: http://fedchains.com/core/ (accessed on 2 February 2022).
- Bitcoin. Available online: https://bitcoin.org/en/ (accessed on 2 February 2022).
- Gas(Ethereum). Available online: https://www.investopedia.com/terms/g/gas-ethereum.asp (accessed on 2 February 2022).
- Eos Wallet. Available online: https://www.ledger.com/eos-wallet/ (accessed on 2 February 2022).









| Techniques | Domain | Design | Implementation | User Interface |
|---|---|---|---|---|
| Yue et al. [39] | Blockchain in Healthcare | ✓ | ✓ | ✓ |
| Liang et al. [40] | Blockchain in Healthcare | ✓ | ✗ | ✗ |
| Jiang et al. [41] | Blockchain in Healthcare | ✓ | ✓ | ✗ |
| Fan et al. [42] | Blockchain in Healthcare | ✓ | ✓ | ✗ |
| Tanwar et al. [43] | Blockchain in Healthcare | ✗ | ✗ | ✗ |
| Habibzadeh et al. [44] | Cybersecurity in smart cities | ✗ | ✗ | ✗ |
| Khan et al. [45] | Blockchain for Smart cities | ✓ | ✓ | ✗ |
| Malik et al. [46] | Blockchain for Smart cities | ✓ | ✓ | ✗ |
| Meshram et al. [47] | Authentication in Smart cities | ✓ | ✗ | ✗ |
| Espositoa et al. [48] | Blockchain for Smart cities | ✓ | ✓ | ✗ |
| Proposed | Blockchain for Smart cities | ✓ | ✓ | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Asif, M.; Aziz, Z.; Bin Ahmad, M.; Khalid, A.; Waris, H.A.; Gilani, A. Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities. Sensors 2022, 22, 2604. https://doi.org/10.3390/s22072604
Asif M, Aziz Z, Bin Ahmad M, Khalid A, Waris HA, Gilani A. Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities. Sensors. 2022; 22(7):2604. https://doi.org/10.3390/s22072604
Chicago/Turabian StyleAsif, Muhammad, Zeeshan Aziz, Maaz Bin Ahmad, Adnan Khalid, Hammad Abdul Waris, and Asfandyar Gilani. 2022. "Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities" Sensors 22, no. 7: 2604. https://doi.org/10.3390/s22072604
APA StyleAsif, M., Aziz, Z., Bin Ahmad, M., Khalid, A., Waris, H. A., & Gilani, A. (2022). Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities. Sensors, 22(7), 2604. https://doi.org/10.3390/s22072604






