Blockchain Based Authentication and Cluster Head Selection Using DDR-LEACH in Internet of Sensor Things
Abstract
:1. Introduction
- The identity authentication of nodes is performed to remove the external unauthenticated nodes;
- CHs are selected from ordinary nodes using the proposed minimum distance, highest degree, and highest residual energy (DDR) based LEACH protocol;
- IPFS is used to provide distributed storage for IoST;
- A payment method is proposed to motivate IPFS for long term data storage;
- A blockchain based secure service provisioning mechanism is proposed;
- An advanced symmetric encryption algorithm (AES) 128-bit is used for the integrity of data;
- Comparison of DDR-LEACH is performed with the LEACH protocol;
- Formal security analysis is performed for the smart contract to check its effectiveness;
- Man in the middle (MITM) and Sybil attacks are induced in the network, which show that our proposed system is resilient against these attacks.
2. Related Work
2.1. Nodes’ Authentication
2.2. Lack of Data Storage
2.3. Lack of Data Privacy
2.4. Lack of Resources
2.5. Malicious Nodes’ Existence
2.6. Single Point of Failure Issue
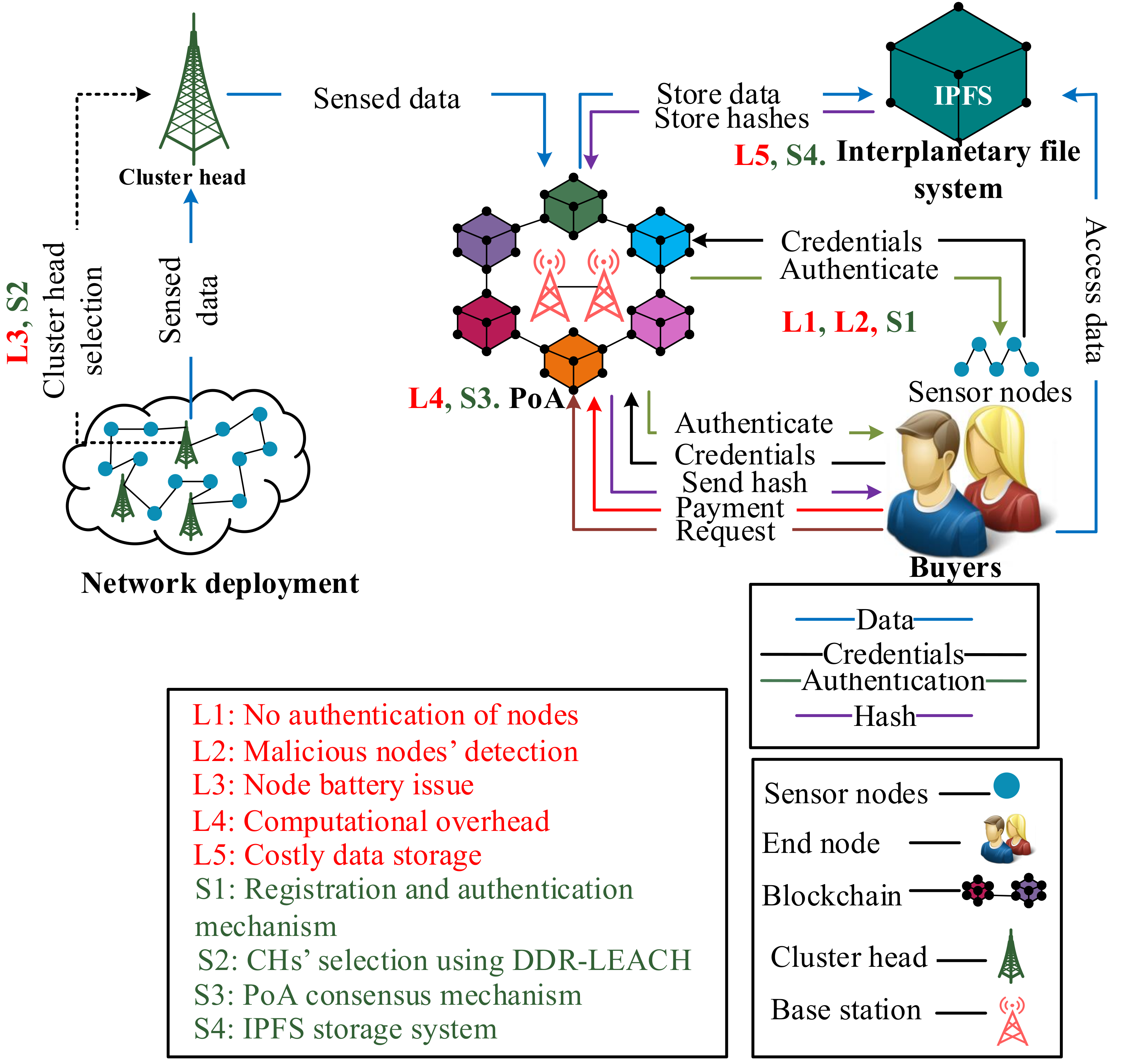
3. Proposed System Model
3.1. Assumptions
- BSs are considered legitimate. As they are peers of blockchain; therefore, they provide secure services to buyers;
- Symmetric keys are exchanged securely in the network.
3.2. System Components
3.3. Workflow of the System Model
| Algorithm 1:CH selection. |
 |
| Algorithm 2:Nodes’ authentication process. |
 |
| Algorithm 3: Service provisioning. |
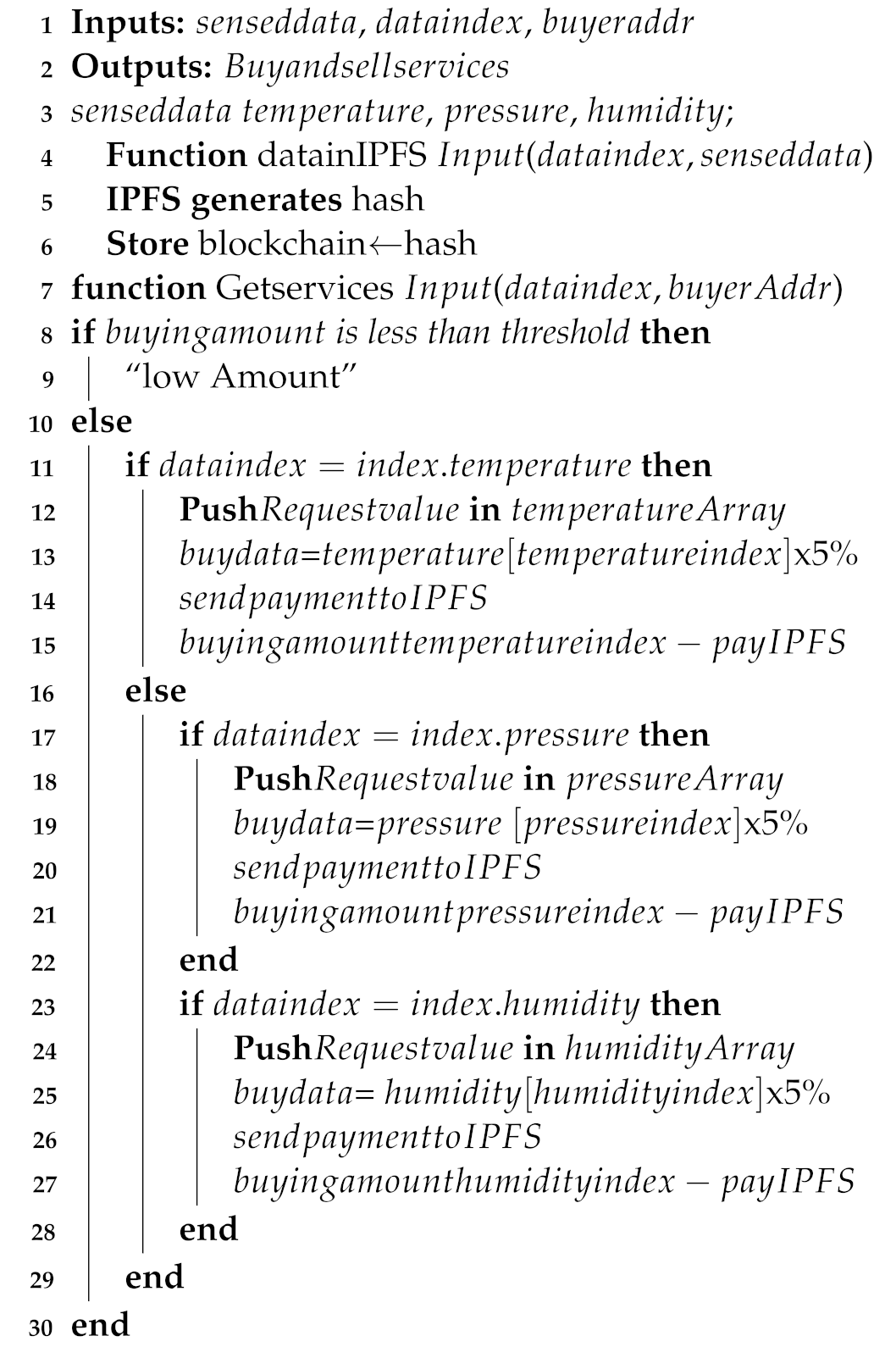 |
4. Simulation Results and Discussion
5. Formal Security Analysis
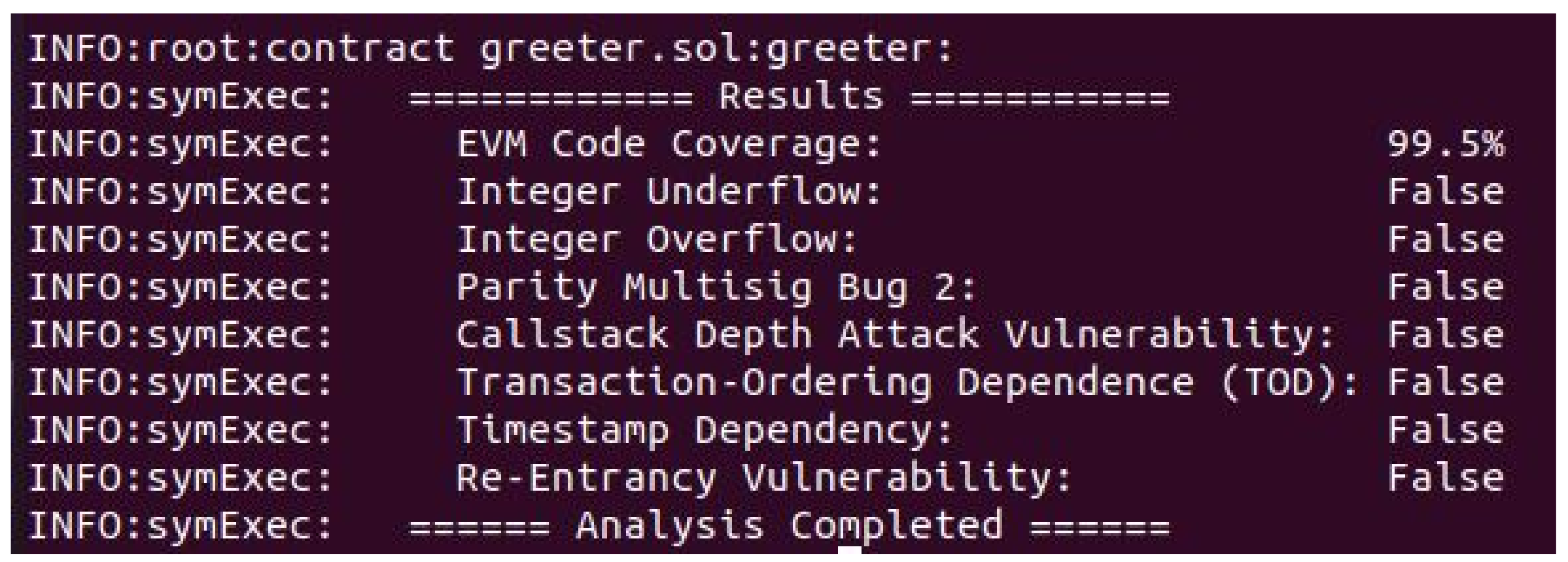
Smart Contract Analysis
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| Notation | Description |
| AES | Advance encryption standard |
| BSs | Base stations |
| CHs | Cluster heads |
| DDR | Distance degree and residual energy |
| IoT | Internet of things |
| IoST | Internet of sensor things |
| IPFS | Interplanetary file system |
| LEACH | Low energy adaptive clustering hierarchy |
| MITM | Man in the middle |
| PoA | Proof of authority |
| PoW | Proof of work |
| RSA | Rivest shamir adleman |
| SHA | Secure hashing algorithm |
| SPOF | Single point of failure |
| WSNs | Wireless sensors networks |
| Private key |
References
- Javaid, N. Integration of context awareness in Internet of Agricultural Things. ICT Express, 2021; in press. [Google Scholar] [CrossRef]
- Fu, M.H. Integrated technologies of blockchain and biometrics based on wireless sensor network for library management. Inf. Technol. Libr. 2020, 39, 3. [Google Scholar] [CrossRef]
- Kumari, S.; Om, H. Authentication protocol for wireless sensor networks applications like safety monitoring in coal mines. Comput. Netw. 2016, 104, 137–154. [Google Scholar] [CrossRef]
- Prabu, P.; Ahmed, A.N.; Venkatachalam, K.; Nalini, S.; Manikandan, R. Energy efficient data collection in sparse sensor networks using multiple mobile data patrons. Comput. Electr. Eng. 2020, 87, 106778. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Abbas, S.; Javaid, N.; Almogren, A.; Gulfam, S.M.; Ahmed, A.; Radwan, A. Securing genetic algorithm enabled SDN routing for blockchain based Internet of Things. IEEE Access 2021, 9, 139739–139754. [Google Scholar] [CrossRef]
- Javaid, N. A Secure and Efficient Trust Model for Wireless Sensor IoTs using Blockchain. IEEE Access 2022, 10, 4568–4579. [Google Scholar] [CrossRef]
- Kumar, M.; Mukherjee, P.; Verma, K.; Verma, S.; Rawat, D.B. Improved deep convolutional neural network based malicious node detection and energy-efficient data transmission in wireless sensor networks. IEEE Trans. Netw. Sci. Eng. 2021; in press. [Google Scholar] [CrossRef]
- Kar, J.; Liu, X.; Li, F. CL-ASS: An efficient and low-cost certificateless aggregate signature scheme for wireless sensor networks. J. Inf. Secur. Appl. 2021, 61, 102905. [Google Scholar] [CrossRef]
- Verma, N.; Kaushik, A.; Nayak, P. A lightweight secure authentication protocol for wireless sensor networks. In International Conference on Innovative Computing and Communications; Springer: Singapore, 2021; pp. 291–299. [Google Scholar]
- Padmavathi, U.; Rajagopalan, N. Concept of Blockchain Technology and Its Emergence. In Blockchain Applications in IoT Security; IGI Global: Raipur, India, 2021; pp. 1–20. [Google Scholar] [CrossRef]
- Abubaker, Z.; Khan, A.U.; Almogren, A.; Abbas, S.; Javaid, A.; Radwan, A.; Javaid, N. Trustful data trading through monetizing IoT data using BlockChain based review system. Concurr. Comput. Pract. Exp. 2021, 34, e6739. [Google Scholar] [CrossRef]
- Moinet, A.; Darties, B.; Baril, J.L. Blockchain based trust and authentication for decentralized sensor networks. arXiv 2017, arXiv:1706.01730. [Google Scholar]
- Goyat, R.; Kumar, G.; Saha, R.; Conti, M.; Rai, M.K.; Thomas, R.; Hoon-Kim, T. Blockchain-based Data Storage with Privacy and Authentication in Internet-of-Things. IEEE Internet Things J. 2020; in press. [Google Scholar] [CrossRef]
- Noshad, Z.; Khan, A.U.; Abbas, S.; Abubaker, Z.; Javaid, N.; Shafiq, M.; Choi, J.G. An Incentive and Reputation Mechanism Based on Blockchain for Crowd Sensing Network. J. Sens. 2021, 2021, 1798256. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the Internet of Things. J. Fintech Blockchain Smart Contract. 2018, 1, 7–12. [Google Scholar] [CrossRef]
- She, W.; Liu, Q.; Tian, Z.; Chen, J.S.; Wang, B.; Liu, W. Blockchain trust model for malicious node detection in wireless sensor networks. IEEE Access 2019, 7, 38947–38956. [Google Scholar] [CrossRef]
- Magazzeni, D.; McBurney, P.; Nash, W. Validation and verification of smart contracts: A research agenda. Computer 2017, 50, 50–57. [Google Scholar] [CrossRef] [Green Version]
- Haseeb, K.; Islam, N.; Almogren, A.; Din, I.U. Intrusion prevention framework for secure routing in WSN-based mobile Internet of Things. IEEE Access 2019, 7, 185496–185505. [Google Scholar] [CrossRef]
- Hong, S. P2P networking based internet of things (IoT) sensor node authentication by Blockchain. Peer-to-Peer Netw. Appl. 2020, 13, 579–589. [Google Scholar] [CrossRef]
- Cui, Z.; Fei, X.U.E.; Zhang, S.; Cai, X.; Cao, Y.; Zhang, W.; Chen, J. A hybrid BlockChain- based identity authentication scheme for multi-WSN. IEEE Trans. Serv. Comput. 2020, 13, 241–251. [Google Scholar] [CrossRef]
- Sharma, P.K.; Park, J.H. Blockchain based hybrid network architecture for the smart city. Future Gener. Comput. Syst. 2018, 86, 650–655. [Google Scholar] [CrossRef]
- Stack Exchange. Available online: https://ethereum.stackexchange.com/questions/872/what-is-the-cost-to-store-1kb-10kb-100kb-worth-of-data-into-the-ethereum-block (accessed on 6 March 2021).
- Amjad, S.; Aziz, U.; Gurmani, M.U.; Awan, S.; Sajid, M.B.E.; Javaid, N. Blockchain based Authentication for end-nodes and efficient Cluster Head selection in Wireless Sensor Networks. In Conference on Complex, Intelligent, and Software Intensive Systems; Springer: Cham, Switzerland, 2021; pp. 195–205. [Google Scholar]
- Ramezan, G.; Leung, C. A blockchain-based contractual routing protocol for the internet of things using smart contracts. Wirel. Commun. Mob. Comput. 2018, 2018, 4029591. [Google Scholar] [CrossRef]
- Xu, J.; Meng, X.; Liang, W.; Zhou, H.; Li, K.C. A secure mutual authentication scheme of blockchain-based in WBANs. China Commun. 2020, 17, 34–49. [Google Scholar] [CrossRef]
- Ren, Y.; Liu, Y.; Ji, S.; Sangaiah, A.K.; Wang, J. Incentive mechanism of data storage based on blockchain for wireless sensor networks. Mob. Inf. Syst. 2018, 2018, 6874158. [Google Scholar] [CrossRef] [Green Version]
- Liu, M.; Yu, F.R.; Teng, Y.; Leung, V.C.; Song, M. Computation offloading and content caching in wireless blockchain networks with mobile edge computing. IEEE Trans. Veh. Technol. 2018, 67, 11008–11021. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, K.; Lin, Y.; Xu, W. LightChain: A Lightweight Blockchain System for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2019, 15, 3571–3581. [Google Scholar] [CrossRef]
- Danzi, P.; Kalør, A.E.; Stefanović, Č.; Popovski, P. Delay and communication tradeoffs for blockchain systems with lightweight IoT clients. IEEE Internet Things J. 2019, 6, 2354–2365. [Google Scholar] [CrossRef] [Green Version]
- Rathee, G.; Balasaraswathi, M.; Chandran, K.P.; Gupta, S.D.; Boopathi, C.S. A secure IoT sensors communication in industry 4.0 using blockchain technology. J. Ambient. Intell. Humaniz. Comput. 2020, 12, 533–545. [Google Scholar] [CrossRef]
- Jia, B.; Zhou, T.; Li, W.; Liu, Z.; Zhang, J. A blockchain-based location privacy protection incentive mechanism in crowd sensing networks. Sensors 2018, 18, 3894. [Google Scholar] [CrossRef] [Green Version]
- Mori, S. Secure caching scheme by using blockchain for information-centric network-based wireless sensor networks. J. Signal Process. 2018, 22, 97–108. [Google Scholar] [CrossRef] [Green Version]
- Kim, T.H.; Goyat, R.; Rai, M.K.; Kumar, G.; Buchanan, W.J.; Saha, R.; Thomas, R. A novel trust evaluation process for secure localization using a decentralized blockchain in wireless sensor networks. IEEE Access 2019, 7, 184133–184144. [Google Scholar] [CrossRef]
- Xu, Y.; Ren, J.; Wang, G.; Zhang, C.; Yang, J.; Zhang, Y. A blockchain-based nonrepudiation network computing service scheme for industrial IoT. IEEE Trans. Ind. Inform. 2019, 15, 3632–3641. [Google Scholar] [CrossRef]
- Kumar, M.H.; Mohanraj, V.; Suresh, Y.; Senthilkumar, J.; Nagalalli, G. Trust aware localized routing and class based dynamic block chain encryption scheme for improved security in WSN. J. Ambient. Intell. Humaniz. Comput. 2020, 12, 1–9. [Google Scholar] [CrossRef]
- Guerrero-Sanchez, A.E.; Rivas-Araiza, E.A.; Gonzalez-Cordoba, J.L.; Toledano-Ayala, M.; Takacs, A. Blockchain mechanism and symmetric encryption in a wireless sensor network. Sensors 2020, 20, 2798. [Google Scholar] [CrossRef]
- Rovira-Sugranes, A.; Razi, A. Optimizing the age of information for blockchain technology with applications to IoT sensors. IEEE Commun. Lett. 2019, 24, 183–187. [Google Scholar] [CrossRef]
- Rathore, S.; Kwon, B.W.; Park, J.H. BlockSecIoTNet: Blockchain-based decentralized security architecture for IoT network. J. Netw. Comput. Appl. 2019, 143, 167–177. [Google Scholar] [CrossRef]
- Lee, Y.; Rathore, S.; Park, J.H.; Park, J.H. A blockchain-based smart home gateway architecture for preventing data forgery. Hum.-Centric Comput. Inf. Sci. 2020, 10, 1–14. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the IEEE 33rd annual Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2000. [Google Scholar] [CrossRef]
- Tian, Y.; Wang, Z.; Xiong, J.; Ma, J. A blockchain-based secure key management scheme with trustworthiness in DWSNs. IEEE Trans. Ind. Inform. 2021, 16, 6193–6202. [Google Scholar] [CrossRef]
- Cao, C.; Tang, Y.; Huang, D.; Gan, W.; Zhang, C. IIBE: An improved identity-based encryption algorithm for WSN security. Secur. Commun. Netw. 2021, 2021, 8527068. [Google Scholar] [CrossRef]
- Abdi Nasib Far, H.; Bayat, M.; Kumar Das, A.; Fotouhi, M.; Pournaghi, S.M.; Doostari, M.A. LAPTAS: Lightweight anonymous privacy-preserving three-factor authentication scheme for WSN-based IIoT. Wirel. Netw. 2021, 27, 1389–1412. [Google Scholar] [CrossRef]
- Al-Hazaimeh, O.M.A. A new approach for complex encrypting and decrypting data. Int. J. Comput. Netw. Commun. 2013, 5, 95. [Google Scholar] [CrossRef]
- Pancholi, V.R.; Patel, B.P. Enhancement of cloud computing security with secure data storage using AES. Int. J. Innov. Res. Sci. Technol. 2016, 2, 18–21. [Google Scholar]
- Ali, S.; Javaid, N.; Javeed, D.; Ahmad, I.; Ali, A.; Badamasi, U.M. A blockchain-based secure data storage and trading model for wireless sensor networks. In International Conference on Advanced Information Networking and Applications; Springer: Cham, Switzerland, 2020; pp. 499–511. [Google Scholar]
- Ghaleb, B.; Al-Dubai, A.; Ekonomou, E.; Qasem, M.; Romdhani, I.; Mackenzie, L. Addressing the DAO insider attack in RPL’s Internet of Things networks. IEEE Commun. Lett. 2018, 23, 68–71. [Google Scholar] [CrossRef] [Green Version]
- Lu, N.; Wang, B.; Zhang, Y.; Shi, W.; Esposito, C. NeuCheck: A more practical Ethereum smart contract security analysis tool. Softw. Pract. Exp. 2021, 51, 2065–2084. [Google Scholar] [CrossRef]
- Brent, L.; Jurisevic, A.; Kong, M.; Liu, E.; Gauthier, F.; Gramoli, V.; Scholz, B. Vandal: A scalable security analysis framework for smart contracts. arXiv 2018, arXiv:1809.03981. [Google Scholar]
- Praitheeshan, P.; Pan, L.; Yu, J.; Liu, J.; Doss, R. Security analysis methods on ethereum smart contract vulnerabilities: A survey. arXiv 2019, arXiv:1908.08605. [Google Scholar]



| Limitations Already Addressed | Contributions Already Provided | Validations Already Done | Limitations to be Addressed |
|---|---|---|---|
| Data security and data privacy, huge energy consumption of resources, low computation power of resources, nodes’ authentication, trust issue [13] | Decentralized blockchain, public key infrastructure for resolving trust issue, nodes’ authentication | Reputation level | Authors will evaluate all parts of authentication process |
| Malicious nodes’ detection, malicious nodes’ traceability [17] | Trust mechanism, consortium blockchain | Sensor nodes’ data input and output parameters, credit of sensors | PoW uses more computational power, no reward for sink nodes |
| Mobile nodes’ management, data protection [19] | Uncertainty principle, Voronoi cell architecture, Blockchain | Network lifetime, energy consumption, average end-to-end delay, packet delivery ratio | No storage mechanism, no registration and authentication |
| No encryption and certificate scheme, nodes’ authentication [20] | Blockchain, SHA 64-bit algorithm, crypto based authentication | Security analysis | Node battery issue, storage issue |
| Node authentication, security issue, centralized system [21] | Hybrid structure is performed, Keccak hash function, consortium blockchain | Security analysis | PoA should be used for each validation and private blockchain |
| Data latency, limited data bandwidth, data security [22] | Blockchain based SDN, PoA, Argan2 | Transactions per second, average time per block, latency | PoW consumes more computational power |
| Trust issue, central authority, gray hole and black hole attacks in an untrusted network [25] | Blockchain based routing protocol for route establishment, reward to minimize selfish behavior | Route overhead, packet delivery ratio, gray hole attack, black hole attack | Proposed solution must be used for ad-hoc network |
| Data privacy, untrusted nodes [26] | Decentralized blockchain based authentication scheme | Energy consumption | N/A |
| PoW takes more computational power [27] | Blockchain incentive mechanism, SHA-256 | Pairing is performed by the hyper elliptic curve for the finite field | Proof of retrievability is used for recovering data in less time |
| Computationally extensive PoW-based mining [28] | Computation offloading mechanism | Net revenue of computing, average delay | Try different consensus mechanisms |
| Single point of failure, data storage [29] | Block offloading filter, blockchain | Comparison of PoW and synergistic multiple proof | N/A |
| Data storage, slow information validation in blockchain [30] | Blockchain distributed ledger, Tangle based technology to minimize computational time | Age of information vs sampling interval, processing power vs sampling interval | N/A |
| Data transparency [31] | Decentralized blockchain | Probability of attack detection by system, falsification attack, authentication delay and probabilistic scenario | No routing path is defined in order to reach the manager |
| No data privacy protection [32] | Blockchain-based privacy protection mechanism, double SHA-256 | Data about noise | Scaled experimental data will be collected for better and complete judgment, algorithm will be improved for better result |
| Data privacy and data security [33] | Information centric network, public key cryptographic scheme, two-tier structure, SHA-1 | Processing time, response time | Scheme should be used as practical implementation |
| Localization, network security [34] | Decentralized blockchain-based trust management model | Energy consumption, localization error, average error ratio | Dynamic behavior of nodes |
| Nonrepudiation [35] | Nonrepudiation mechanism, homomorphic hash function | Transaction latency, throughput, gas consumption | No user authentication, double spending |
| Malicious nodes’ detection, data security [36] | Trust aware routing algorithm | Time complexity, throughput | No authentication mechanism |
| Limitations Identified | Solutions Proposed | Validations Done |
|---|---|---|
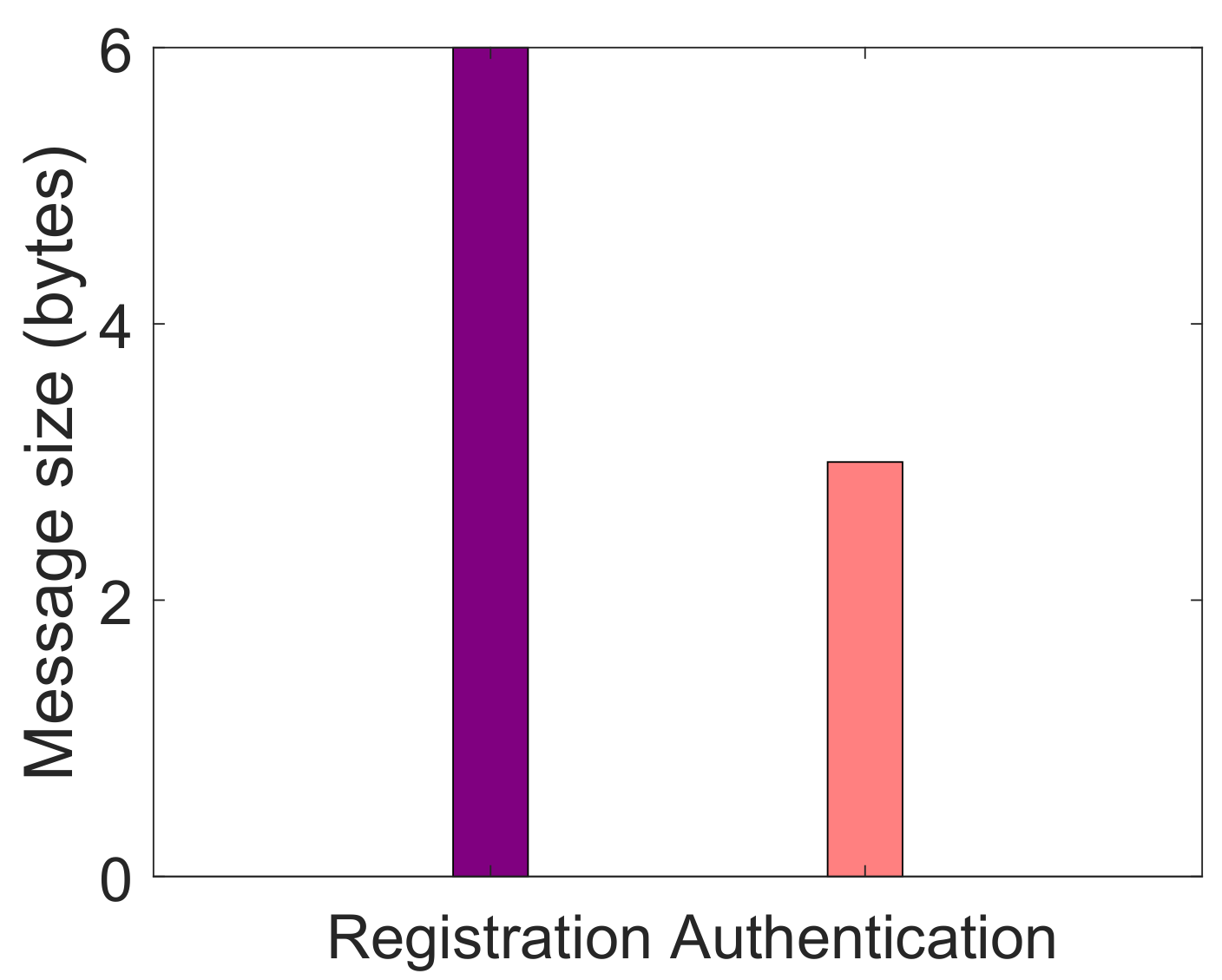
| L1. Nodes are not authenticated [19]. L2. No mechanism for malicious nodes’ detection [19] | S1. Authentication mechanism | V1. Message size, as shown in Figure 3 V2. Transaction cost, as depicted in Figure 4 |
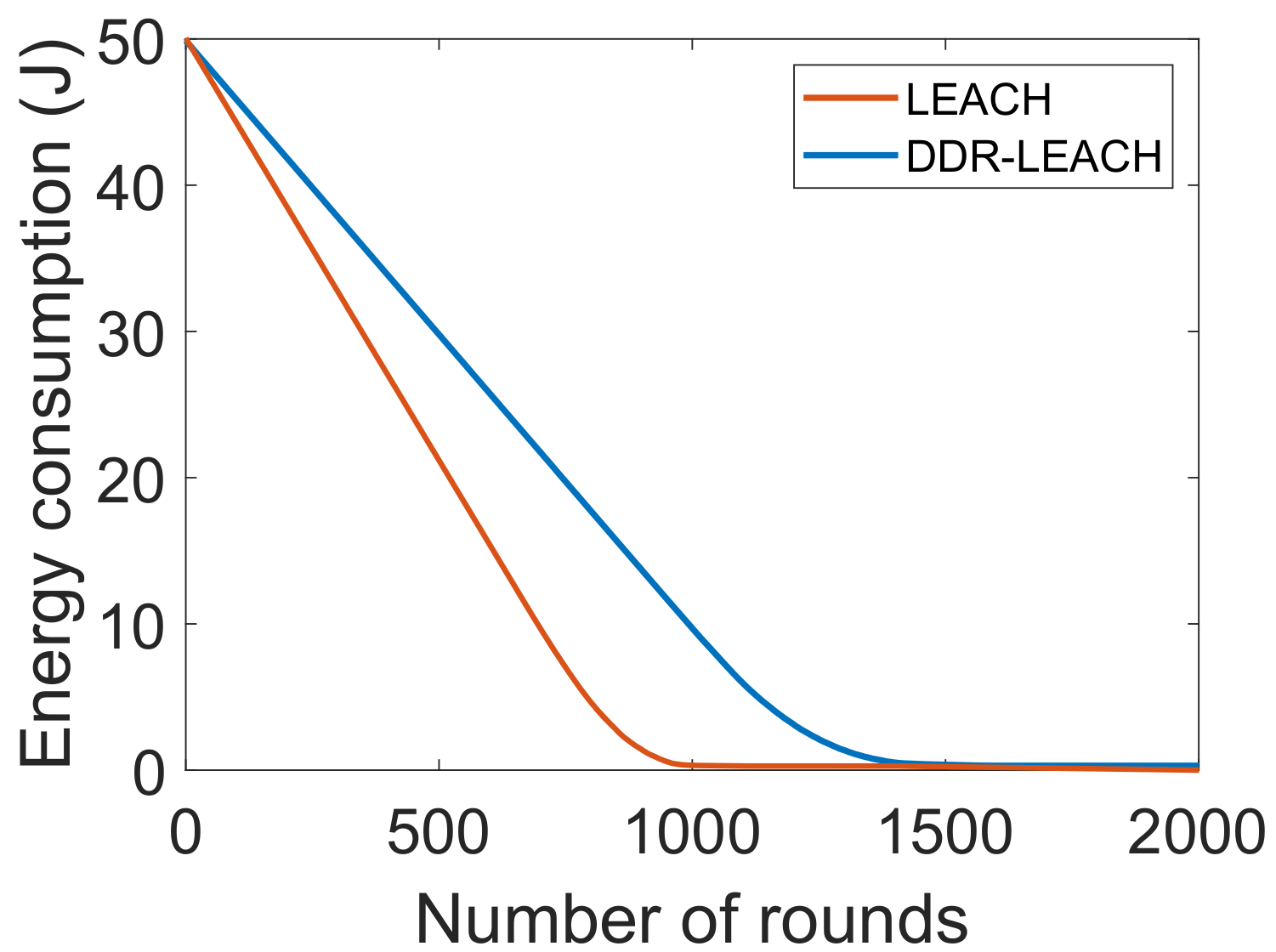
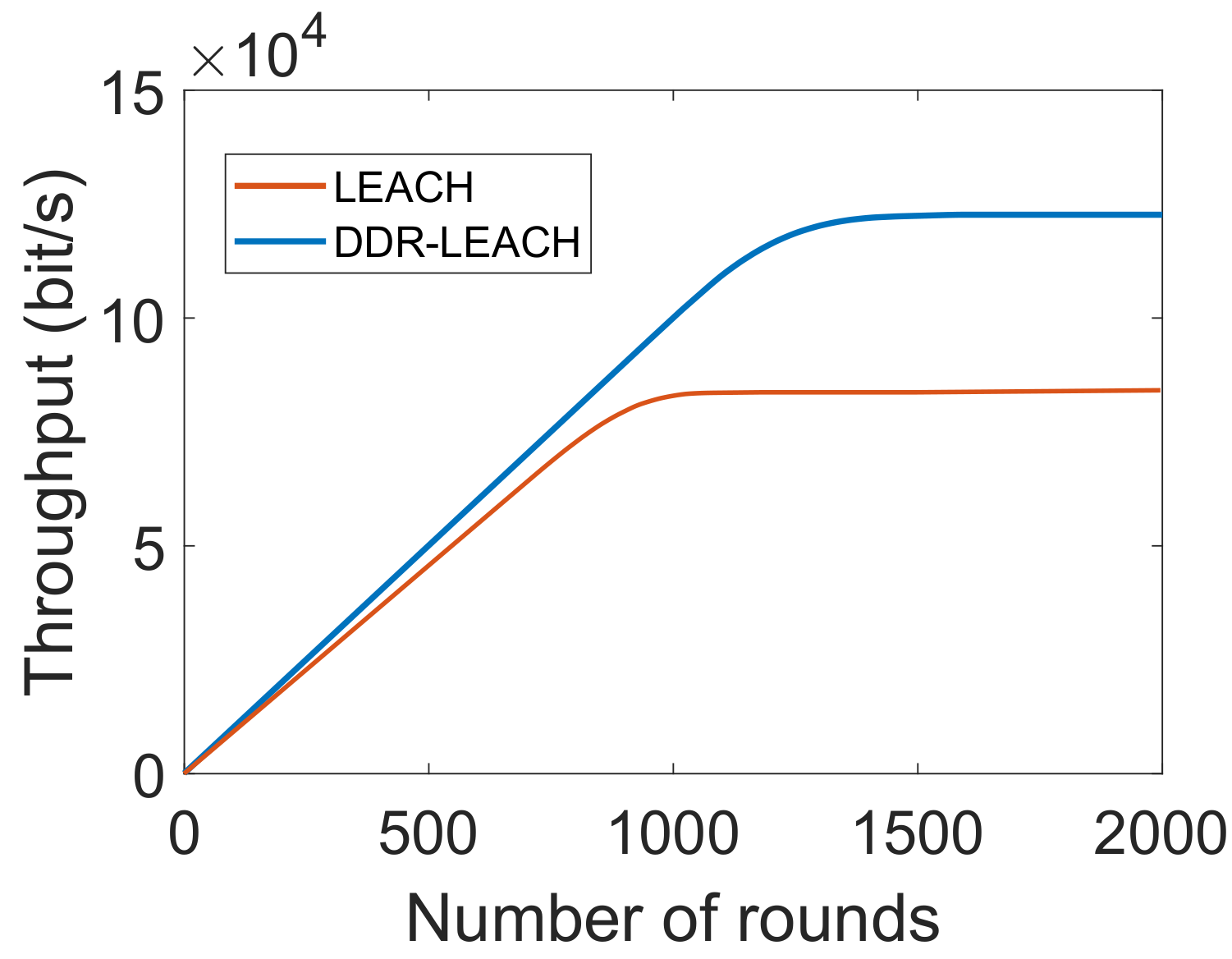
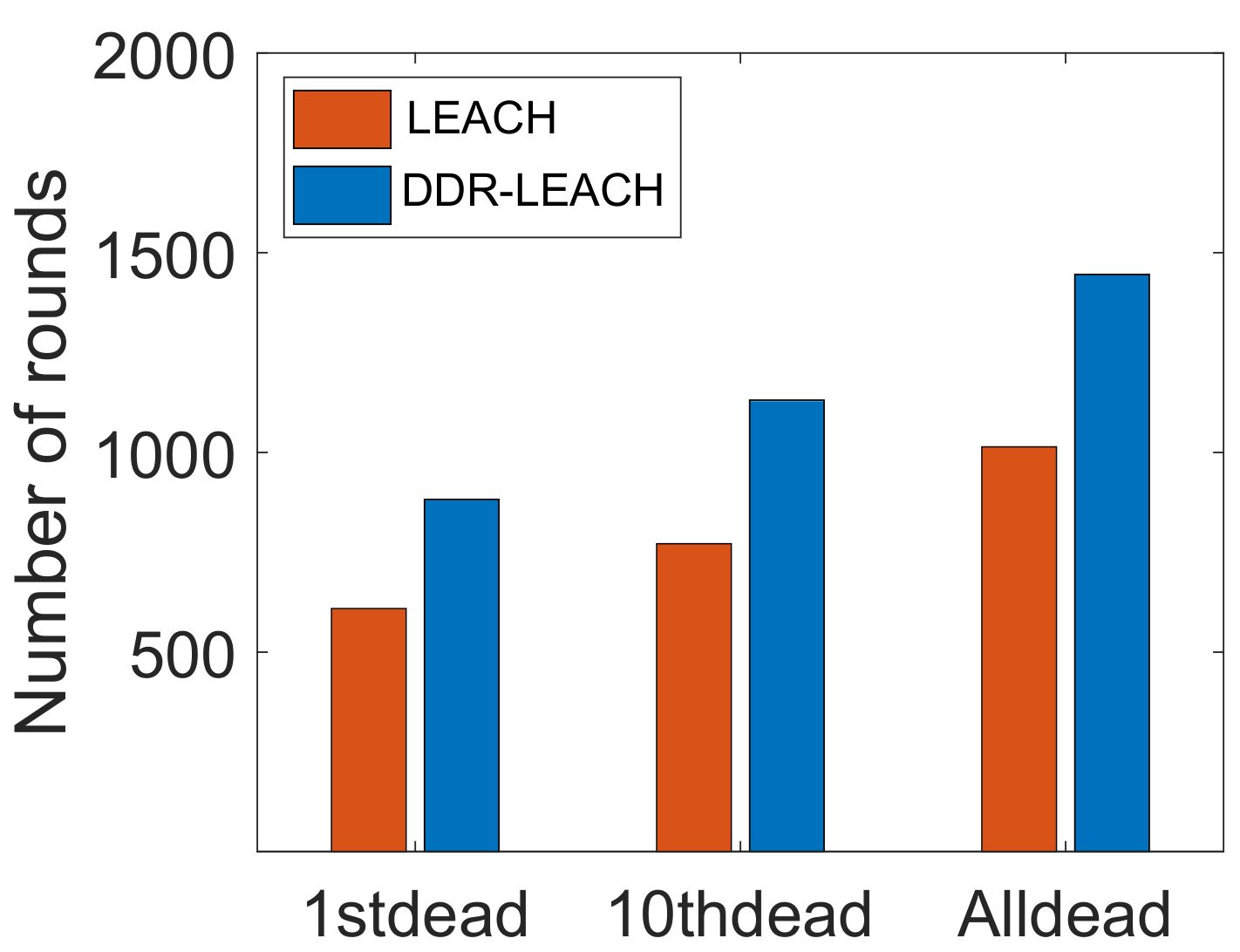
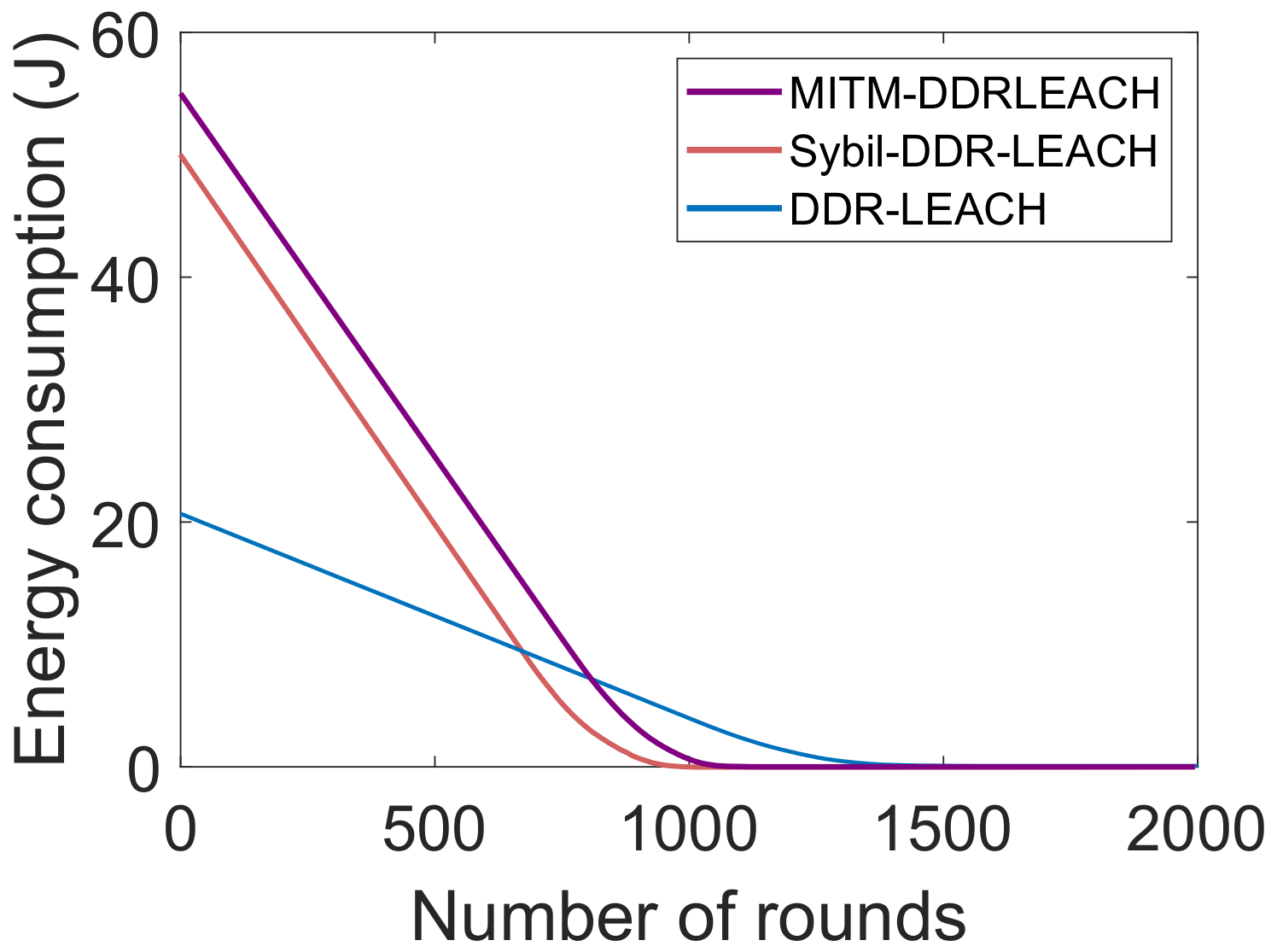
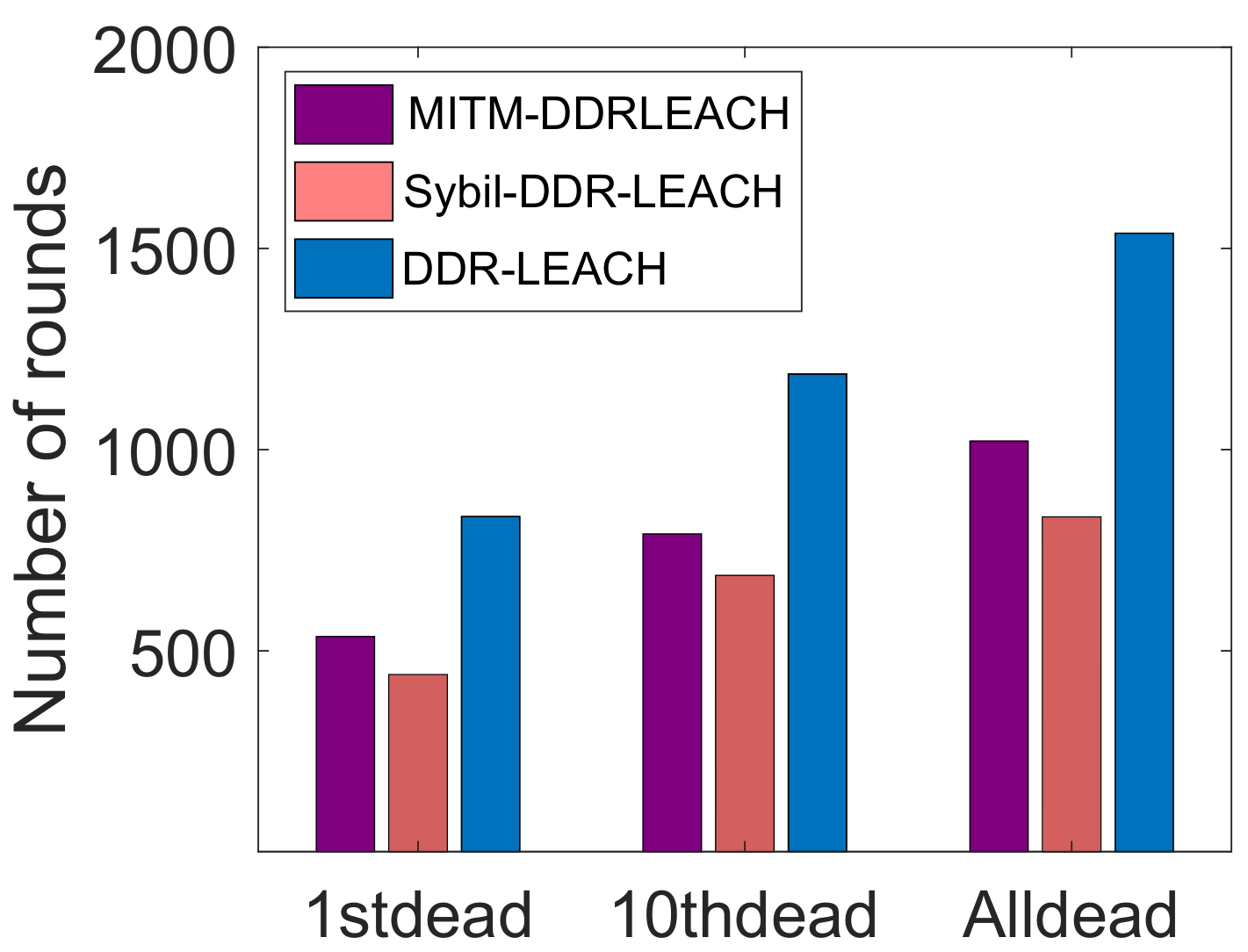
| L3. Inefficient energy consumption [21] | S2. CHs’ selection considering nodes’ residual energy, minimum distance from BS and degree | V3. Energy consumption, as depicted in Figure 5 V4. Throughput, as shown in Figure 6 V5. Network lifetime, as shown in Figure 7 |
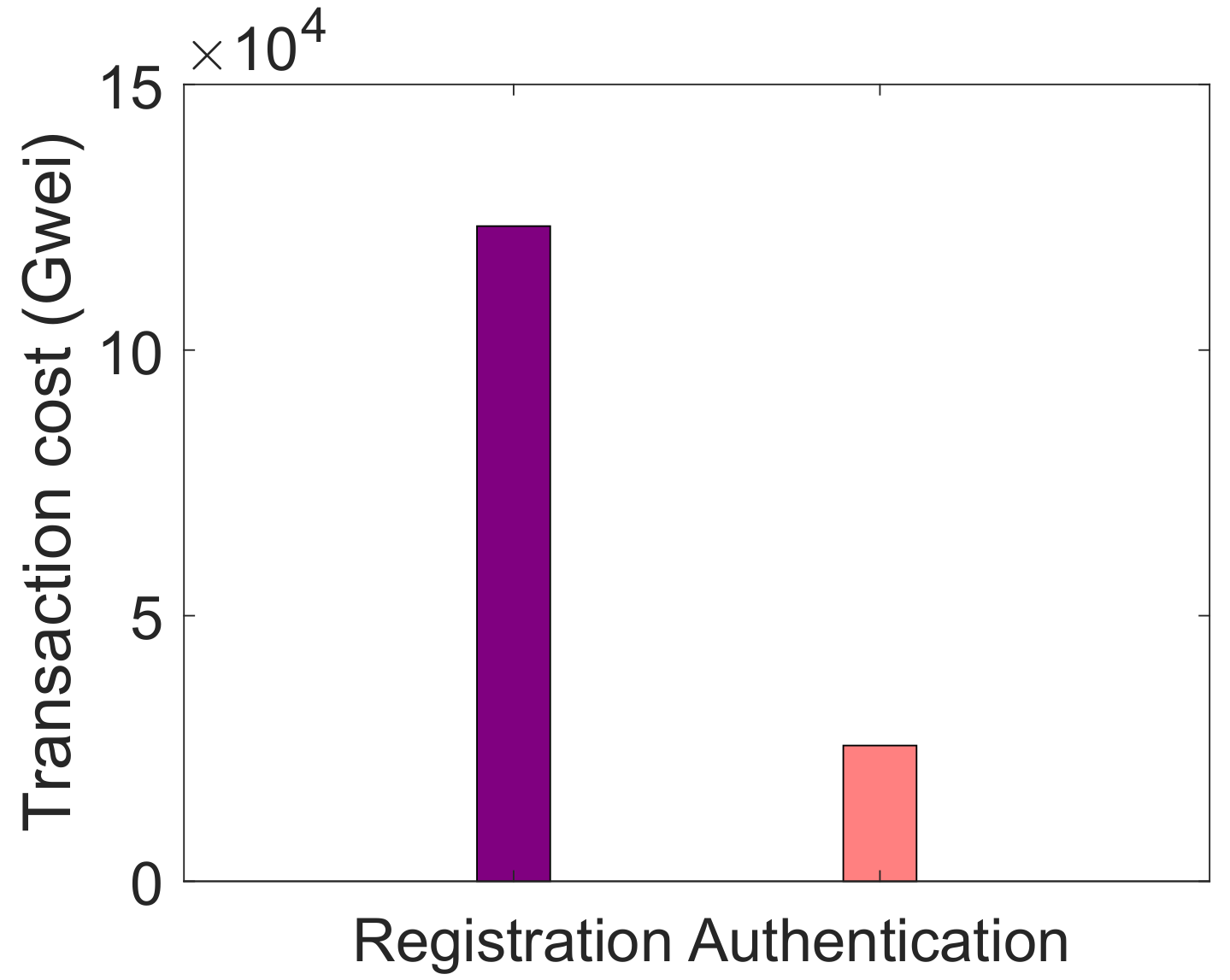
| L4. High computational cost [17,22] | S3. PoA | V6. Average transaction cost, as shown in Figure 8 |
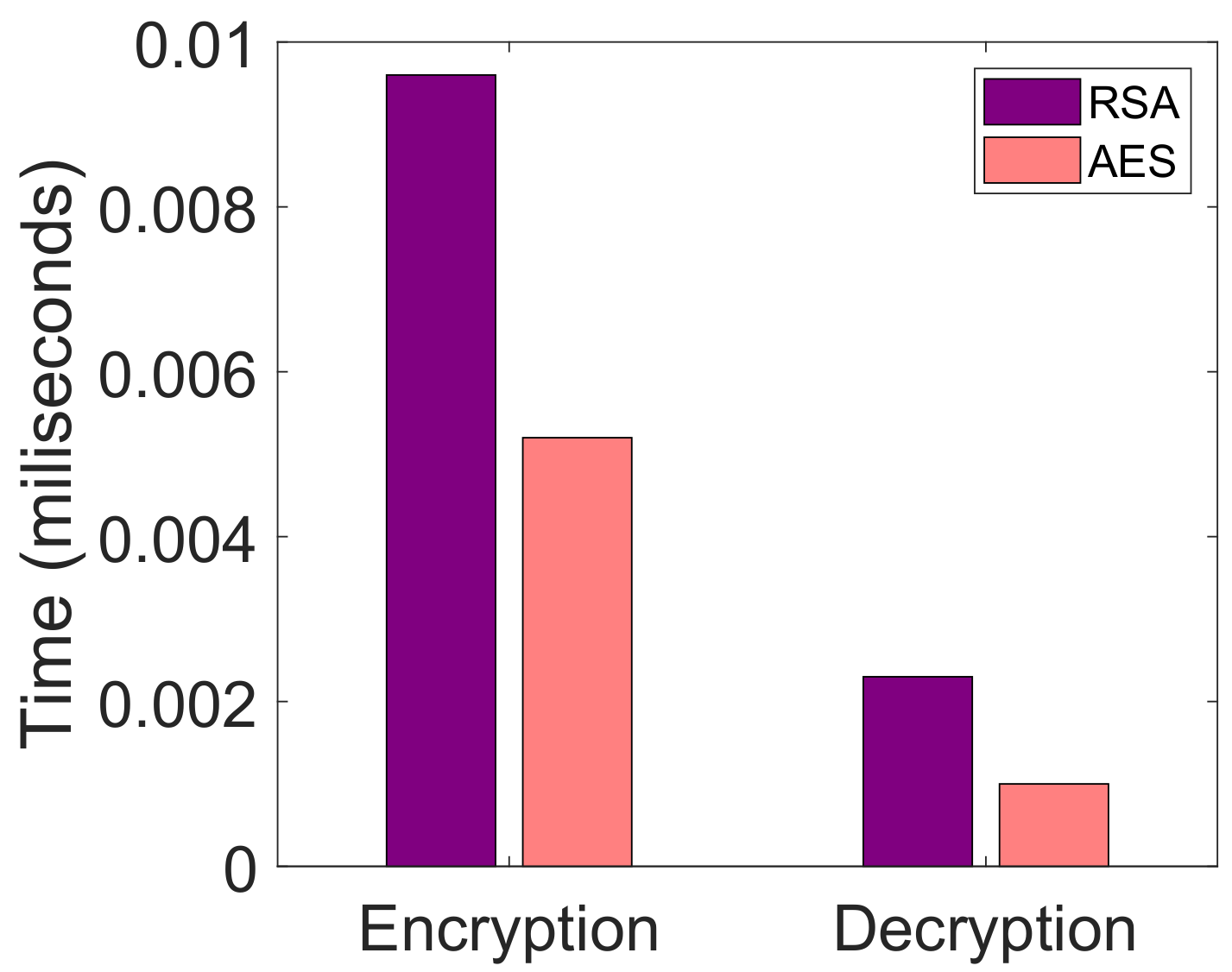
| L5. Costly data storage [19] | S4. IPFS | V7. Average transaction cost, as shown in Figure 9 V8. Encryption time, as depicted in Figure 10 |
| Parameters | Value of Parameters |
|---|---|
| Sensing area | 100 × 100 m2 |
| Deployment | Random |
| Total nodes | 100 |
| CHs | 4 |
| BSs | 2 |
| Network interface | Wireless |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amjad, S.; Abbas, S.; Abubaker, Z.; Alsharif, M.H.; Jahid, A.; Javaid, N. Blockchain Based Authentication and Cluster Head Selection Using DDR-LEACH in Internet of Sensor Things. Sensors 2022, 22, 1972. https://doi.org/10.3390/s22051972
Amjad S, Abbas S, Abubaker Z, Alsharif MH, Jahid A, Javaid N. Blockchain Based Authentication and Cluster Head Selection Using DDR-LEACH in Internet of Sensor Things. Sensors. 2022; 22(5):1972. https://doi.org/10.3390/s22051972
Chicago/Turabian StyleAmjad, Sana, Shahid Abbas, Zain Abubaker, Mohammed H. Alsharif, Abu Jahid, and Nadeem Javaid. 2022. "Blockchain Based Authentication and Cluster Head Selection Using DDR-LEACH in Internet of Sensor Things" Sensors 22, no. 5: 1972. https://doi.org/10.3390/s22051972
APA StyleAmjad, S., Abbas, S., Abubaker, Z., Alsharif, M. H., Jahid, A., & Javaid, N. (2022). Blockchain Based Authentication and Cluster Head Selection Using DDR-LEACH in Internet of Sensor Things. Sensors, 22(5), 1972. https://doi.org/10.3390/s22051972










