Entitlement-Based Access Control for Smart Cities Using Blockchain †
Abstract
:1. Introduction
- High latency: all access authorization regardless of the mode of operation (e.g., read, write) are considered as blockchain transactions that require computationally expensive mining operations before the client can access resources [17]. It not only adds significant latency but is not scalable in a large-scale IoT network [6,11].
- We propose a novel entitlement-based blockchain-enabled access control architecture for a large-scale IoT environment where resources can be shared across multiple organizations. Our proposal provides a flexible access delegation and revocation mechanism that ensures the resource owner is in full control. The proposed access control model also allows a user to have a different set of access rights on the same resource depending on the user’s profile contexts.
- We provide detailed design and implementation of the proposed scheme on the Ethereum blockchain platform. Extensive experiments are performed on a private Ethereum network with multiple instances of test client applications concurrently generating a high volume of blockchain transactions/calls and thus simulating a real-world scenario. Our feasibility study confirms that our proposal can be easily implemented using a publicly available blockchain.
- We also present a qualitative analysis of how the proposed architecture can meet the standard security and access control aspects of a complex IoT environment.
2. Background and Related Work
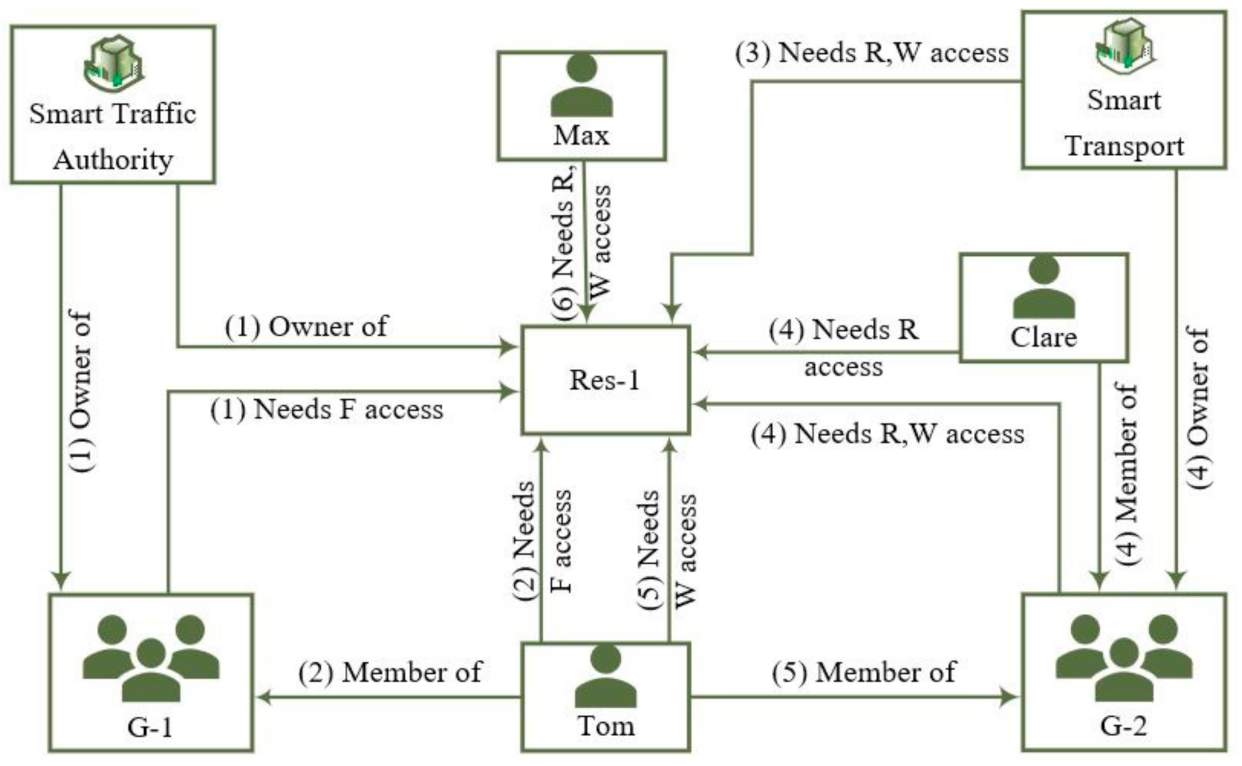
3. A Smart City Use Case
- 1.
- Smart Traffic Authority Organization has deployed an IoT resource (Res-1). They are the owner of this resource, and its own Group-1 (G-1).
- 2.
- Tom is a member of Group-1 (G-1) and needs Full (F) access on Res-1 data.
- 3.
- Smart Traffic Authority has agreed to provide Read/Write (R/W) access to the Smart Transport Organization for this resource data.
- 4.
- Smart Transport needs to further delegate its R/W access right to its Group-2 (G-2) but wants to further control access to its members Clare and Tom where Clare has a R access, but Tom has a W access.
- 5.
- Tom is a casual part-time worker and works for both Smart Traffic Authority and Smart Transport organization.
- 6.
- Smart Traffic Authority also agreed to provide a R and W access to an individual third party, Max, who provides some services.
4. Proposed Entitlement-Based Blockchain-Enabled Access Control Architecture
4.1. System Model for Entitlement-Based Access Control
4.2. Proposed Reference Architecture
- Manage internal user access: the API allows provisioning and maintaining organization’s internal user access and entitlements. This API is used by both resource owner and TP organizations.
- Manage Third-Party (TP) access: This API allows connecting to blockchain and create and manage TP Org entitlements and TP Org user entitlements. This API is used by both resource owner and TP organizations.
- Manage device: this API is used by the resource owner Org for registering the IoT devices.
- Resource access: this API is on the resource owner side and used for accessing the resources. For internal user access for a given resource, the API checks the local entitlement and profile DB before granting resource access. TP user can retrieve the TP user access token from blockchain and make call to this API with the access token and the API validates the token before allowing access.
5. Entitlement Management and Access Control
5.1. Entitlement and Access Tokens
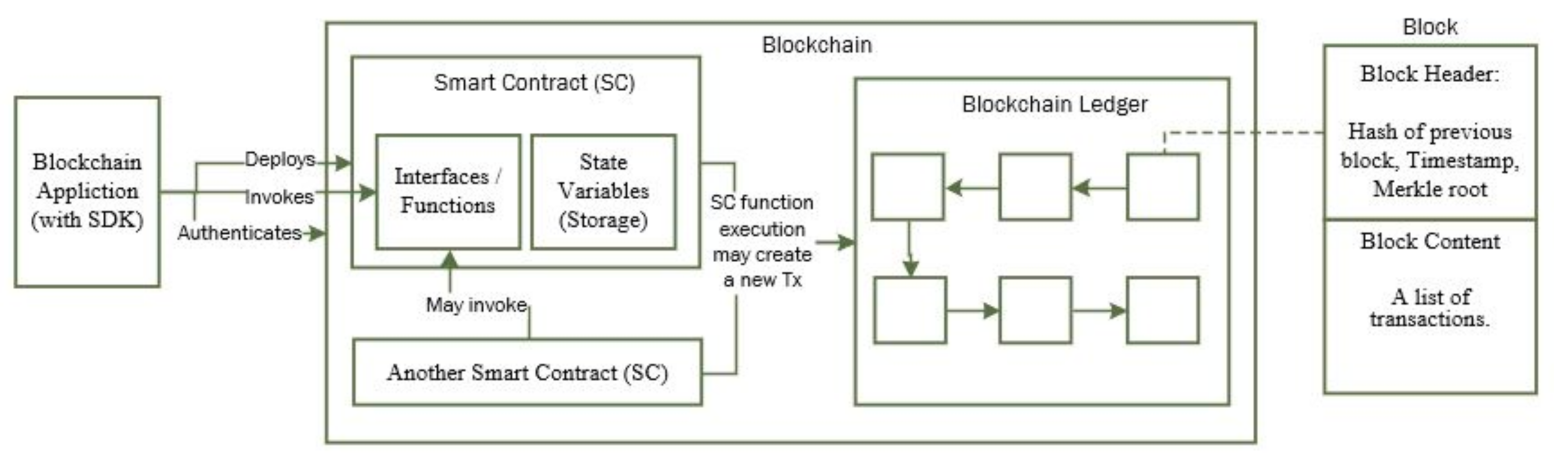
5.2. Smart Contract and Its Interfaces
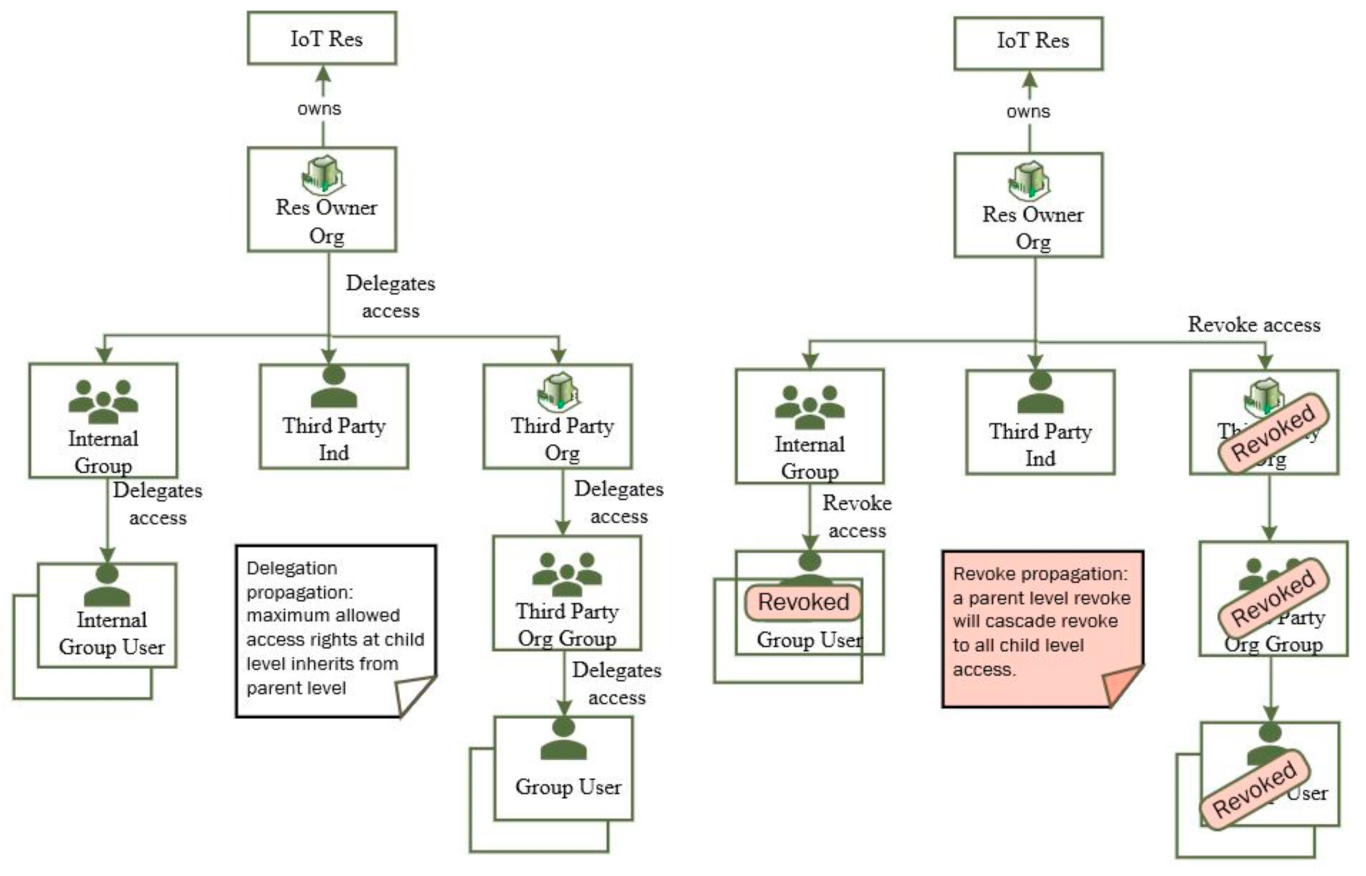
5.3. Access Control Flows
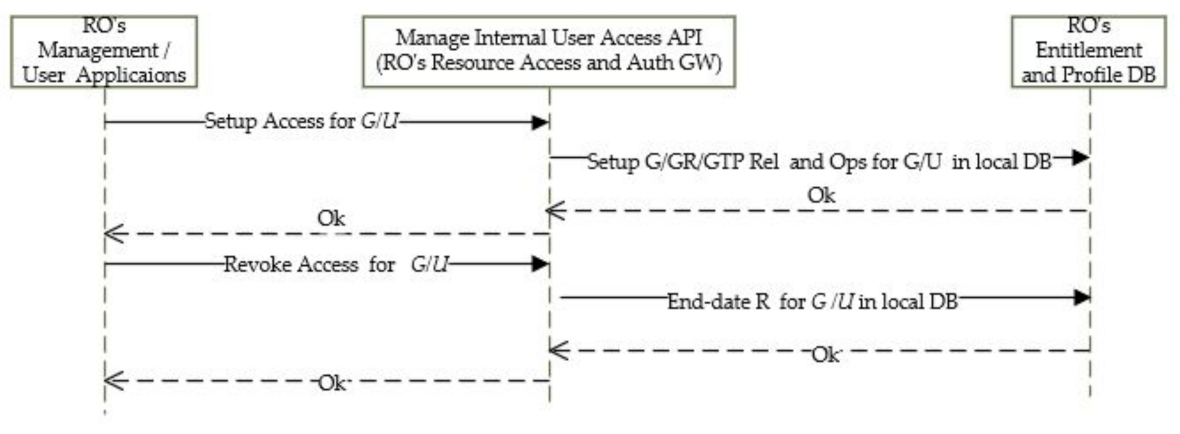
- Entitlement Setup and Revoke for Org’s Users on Local Resources
- 2.
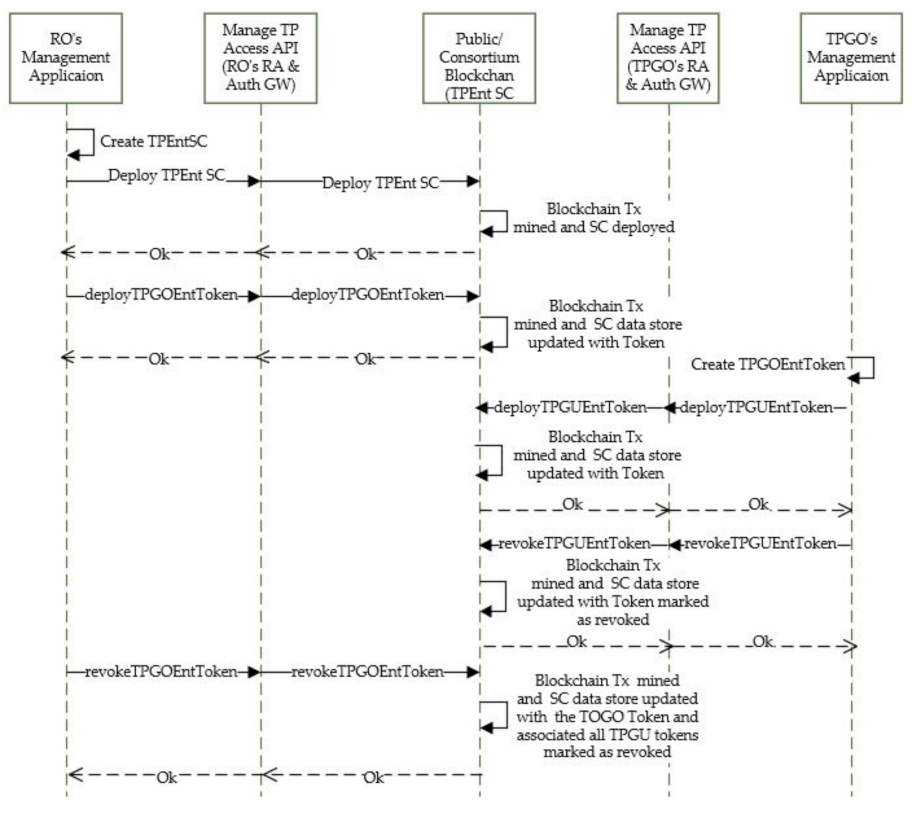
- Entitlement Set-up/Revoke for External TPGO and Their Users
- 3.
- Device (resource) Registration and Data Aggregation
- 4.
- Accessing Org Own Resources
- 5.
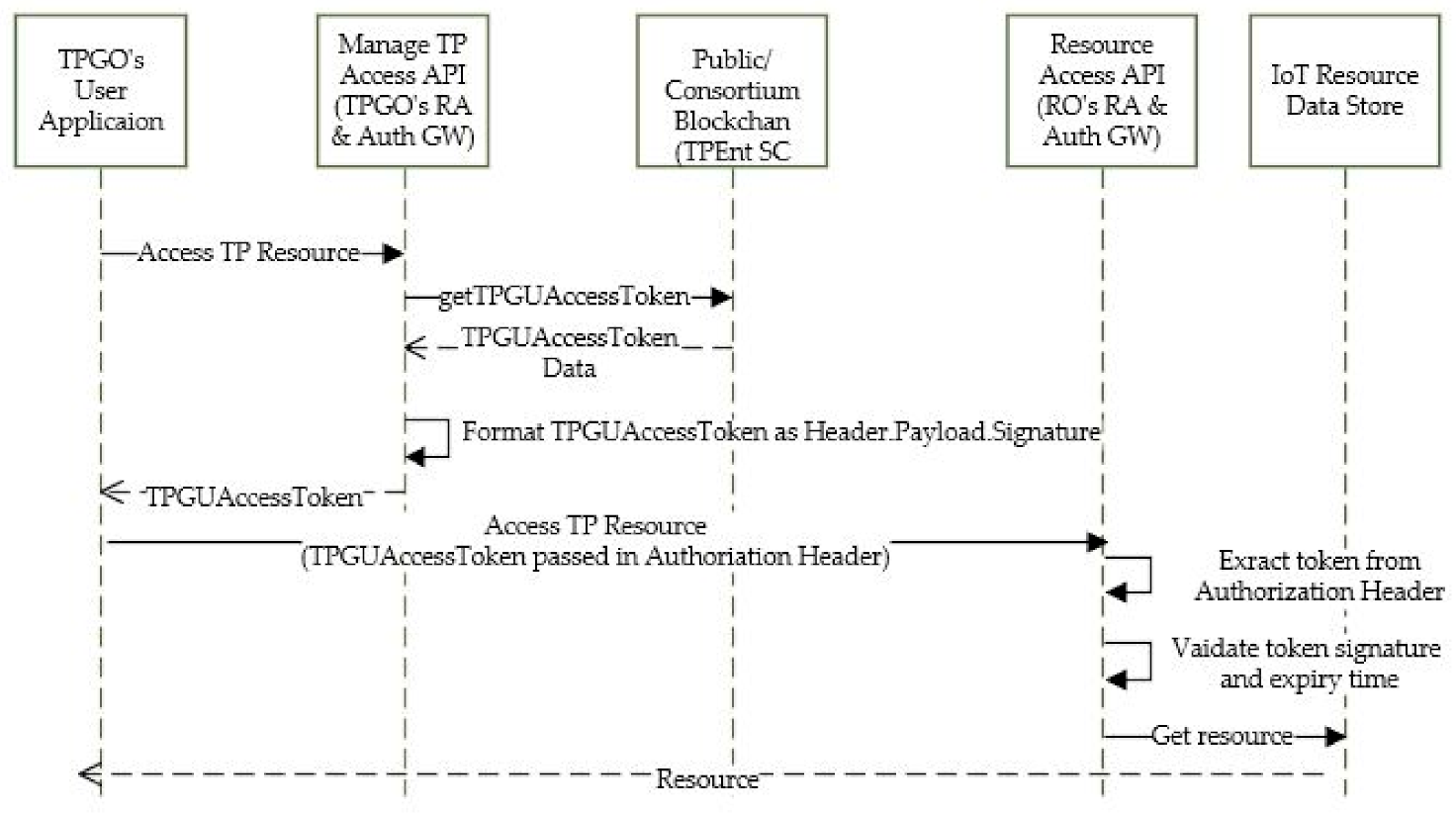
- Accessing External TP Resources
6. Smart Contract Detail Design for Ethereum Platform and Algorithms
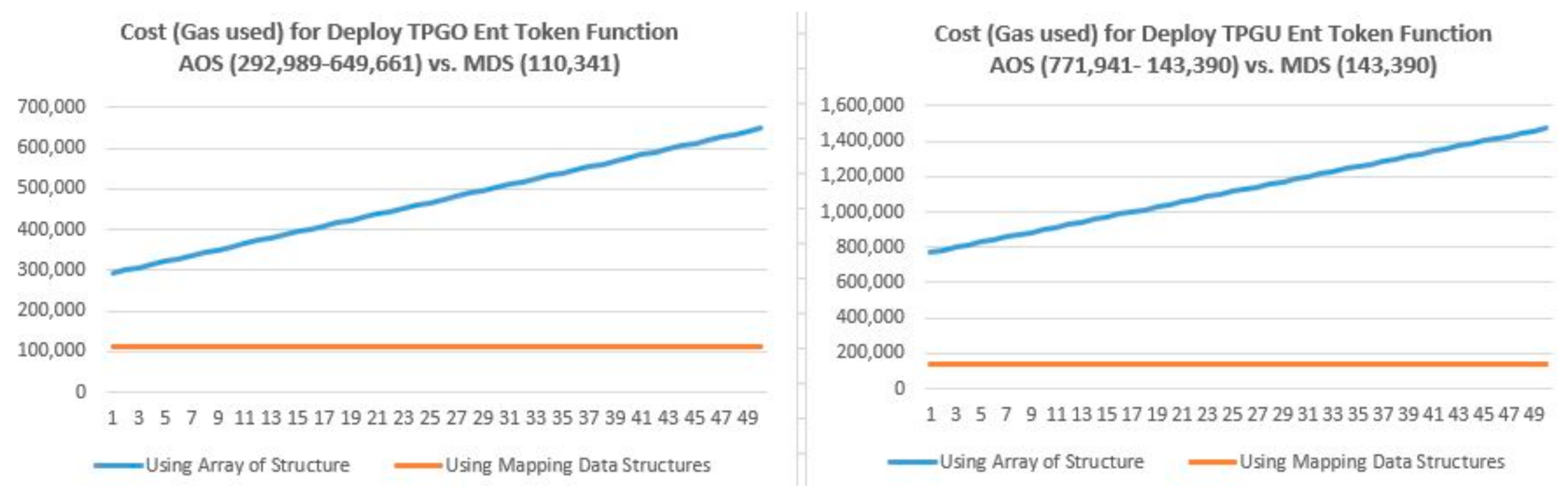
6.1. Data Structure Considerations and Complexities Analysis
6.2. Algorithms for Smart Contract Interfaces
- Smart Contract Constructor
| Algorithm 1: Algorithm to set smart contract variables from constructor function. |
| Input: nil Output: set the value of some smart contract variables in blockchain 1 roAdrKey ← msg.sender; 2 tpgoAdrKey ← TPGO blockchain account address; 3 roUID ← UID of the RO ; 4 tpgoUID ← UID of the TPGO; 5 roAddresses[roAdrKey] ← 1; 6 tpgoAddresses[tpgoAdrKey] ← 1; |
- 2.
- Deploy TPGO Entitlement Token
| Algorithm 2: Algorithm to deploy a TPGO entitlement token in blockchain. |
| Input: _roUID, _tpgoUID, _resUID, _resUrl, _ops Output: TPGO Entitlement Token is added to smart contract storage in blockchain and return success or return error 1 adrKey ← msg.sender; 2 if (roAddresses[adrKey] != 1) then return error; 3 if ((_roUID != roUID) || (_tpgoUID != tpgoUID)) then return error; 4 tpgoEntTokenKey ← keccak256 (_roUID, _tpgoUID, _resUID); 5 if ((tpgoEntTokens[tpgoEntTokenKey]._isActive) == 1) then 6 tpguCount ← (tokenKeys[tpgoEntTokenKey]).length; 7 if (tpguCount > 0) then for each tpguEntTokens[tokenKeys[tpgoEntTokenKey]]._isActive ← 0; 8 end if 9 tpgoEntTokens[tpgoEntTokenKey] ← tpgoEntRecord (_roUID, _tpgoUID, _resUID, “TP”, _resURL, _ops, 1); 10 return success; |
- 3.
- Revoke TPGO Entitlement Token
| Algorithm 3: Algorithm to revoke a TPGO entitlement token in blockchain. |
| Input: _roUID, _tpgoUID, _resUID Output: TPGO Entitlement Token and all associated TPGU Entitlement Tokens are revoked in blockchain and return success or return error 1 adrKey ← msg.sender; 2 if (roAddresses[adrKey] != 1) then return error; 3 if ((_roUID != roUID) || (_tpgoUID != tpgoUID)) then return error; 4 tpgoEntTokenKey ← keccak256 (_roUID, _tpgoUID, _resUID); 5 if ((tpgoEntTokens[tpgoEntTokenKey]._isActive) == 1) then 6 tpguCount ← (tokenKeys[tpgoEntTokenKey]).length; 7 if (tpguCount > 0) then for each tpguEntTokens[tokenKeys[tpgoEntTo- kenKey]]._isActive ← 0; 8 tpgoEntTokens[tpgoEntTokenKey]._isActive ← 0; 9 end if 10 return success; |
- 4.
- Deploy TPGU Entitlement Token
| Algorithm 4: Algorithm to deploy a TPGU entitlement token in blockchain. |
| Input: _roUID, _tpgoUID, _tpguUID, _resUID, _tpguPKUrl, _ops Output: TPGU Entitlement Token is added to smart contract storage in blockchain and return success or return error 1 adrKey ← msg.sender; 2 if (tpgoAddresses[adrKey] != 1) then return error; 3 if ((_roUID != roUID) || (_tpgoUID != tpgoUID)) then return error; 4 tpgoEntTokenKey ← keccak256 (_roUID, _tpgoUID, _resUID); 5 if ((tpgoEntTokens[tpgoEntTokenKey]._isActive) != 1) then return error; 6 tpguEntTokenKey ← keccak256 (_roUID, _tpgoUID, _tpguUID, _resUID); 7 if (_ops > (tpgoEntTokens[tpgoEntTokenKey]._ops)) then return error; 8 tpguEntTokens[tpguEntTokenKey] ← tpguEntRecord (_roUID, _tpgoUID, _tpguUID,_resUID, “GTP”, (tpgoEntTokens[tpgoEntTokenKey]._resUrl), _tpguPKUrl, _ops, 1); 9 tpguCount ← (tokenKeys[tpgoEntTokenKey]).length; 10 if (tpguCount > 0) then if any of ((tokenKeys[tpgoEntTokenKey])[ from 0 to (tpguCount-1)] == tpguEntTokenKey) then return success; 11 end If 12 tokenKeys[tpgoEntTokenKey].push (bytes32(tpguEntTokenKey)); 13 return success; |
- 5.
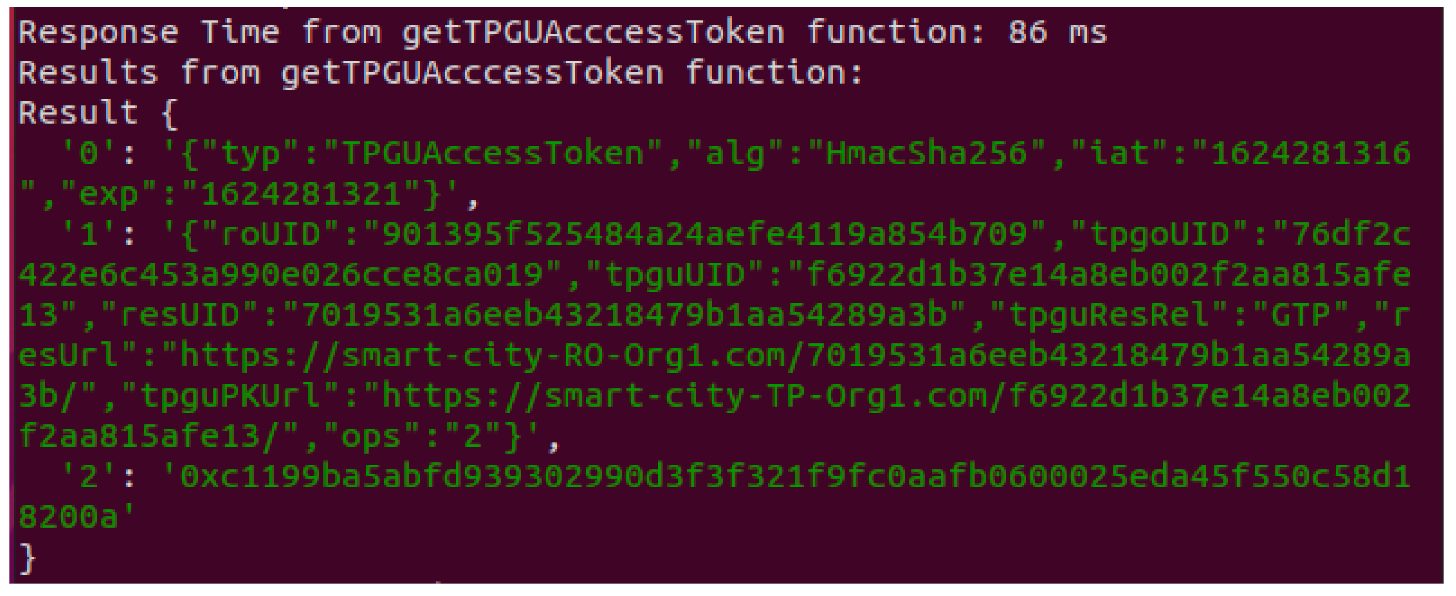
- Get TPGU Access Token
| Algorithm 5: Algorithm to create a TPGU Access Token. |
| Input: _roUID, _tpgoUID, _tpguUID, _resUID Output: returns TPGU Access Token Header, Payload and Signature 1 adrKey ← msg.sender; 2 if (tpgoAddresses[adrKey] != 1) then return error; 3 tpguEntTokenKey ← keccak256 (_roUID, _tpgoUID, _tpguUID, _resUID); 4 if ((tpguEntTokens[tpguEntTokenKey]._isActive) != 1) then return error; 5 iat ← block.timestamp; exp ← (iat + token TTL); typ ← “TPGUAccessToken”; alg ← “HmacSha256”; 6 Format Header (in JSON) including iat, exp, typ, alg; 7 Format Payload (in JSON) using data recorded in (tpguEntTokens[tpguEntTokenKey]); 8 Signature ← HmacSha256 ((Header +Payload), Secret); 9 return (Header, Payload, Signature); |
- 6.
- Add or Delete RO Address
| Algorithm 6: Algorithm to add or remove an eligible RO address. |
| Input: _address, _add Output: Add (or delete) a RO account address in (from) roAddresses list 1 adrKey ← msg.sender; 2 if (roAddresses[adrKey] != 1) then return error; 3 if ((roAddresses[_address] == 1) && (_add == false)) then roAddresses[_address] ← 0; 4 else if ((roAddresses[_address] == 1) && (_add == true)) then return error; 5 else if ((roAddresses[_address] != 1) && (_add == true)) then roAddresses[_address] ← 1; 6 else if ((roAddresses[_address] !== 1) && (_add == false)) then return error; 7 end if 8 return success |
7. Experimental Results and Evaluations
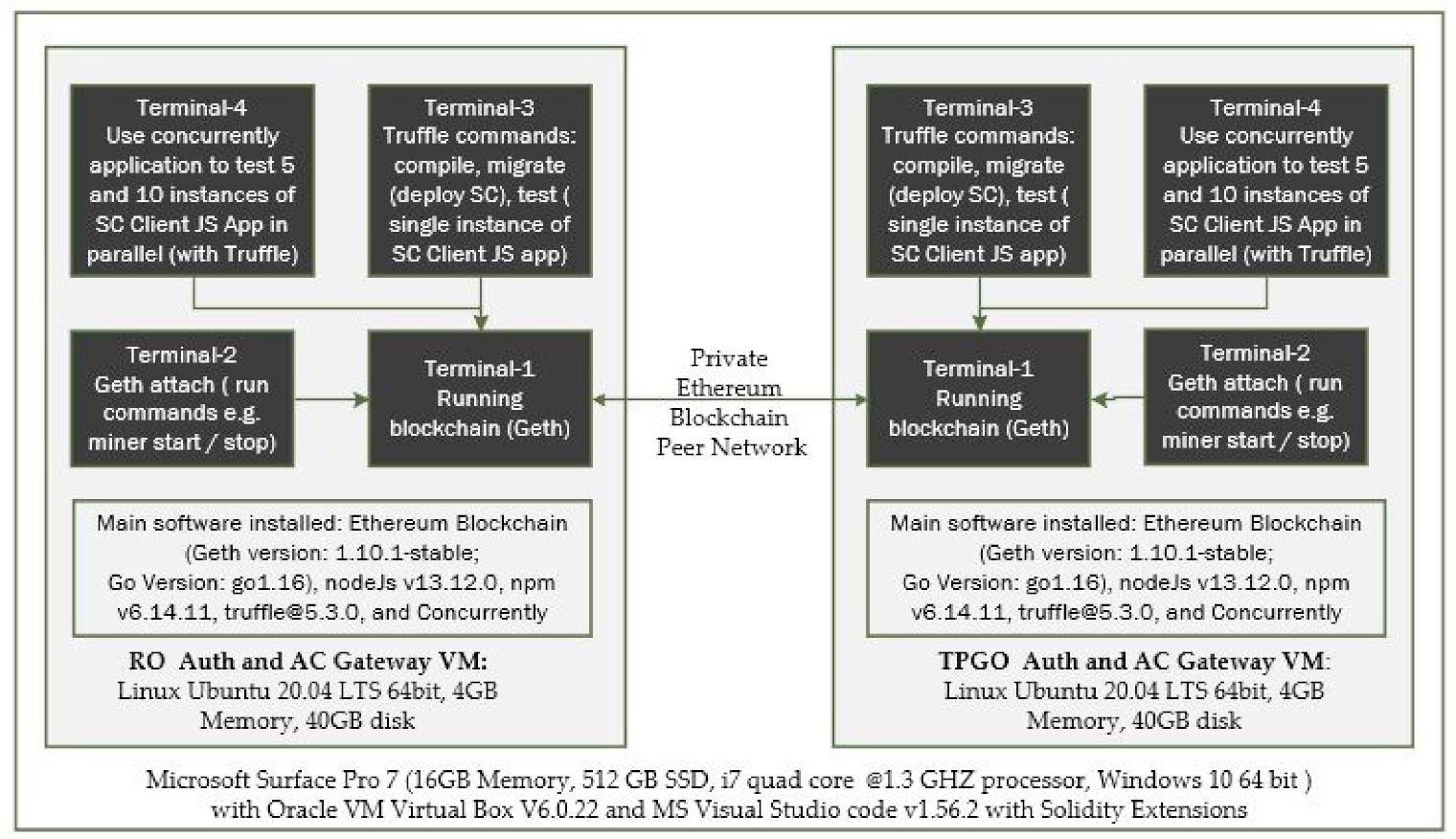
7.1. Experimental Setup
- We installed the Go version of the open source Ethereum [35] blockchain, Node.Js, NPM, Truffle, and Concurrently applications in each virtual machine and created a private blockchain network.
- We used multiple terminal windows to run the blockchain nodes and test smart construct deployment and its interfaces. From Terminal-1 we run Geth commands to initialize and start the blockchain. In Terminal-2, we run Geth attach command to connect to the running instance of blockchain and run the control commands such as start/stop miner and peering the nodes.
- Truffle is used in Terminal-3 to compile and deploy smart contract bytecodes to the blockchain network. Truffle is also used to run a single instance of our Javascript client application that makes single call or make repeated calls (e.g., making a consecutive 10,000 calls to Get TPGU Access Token interface, making a consecutive 500 calls to Deploy TPGU Entitlement Token etc.).
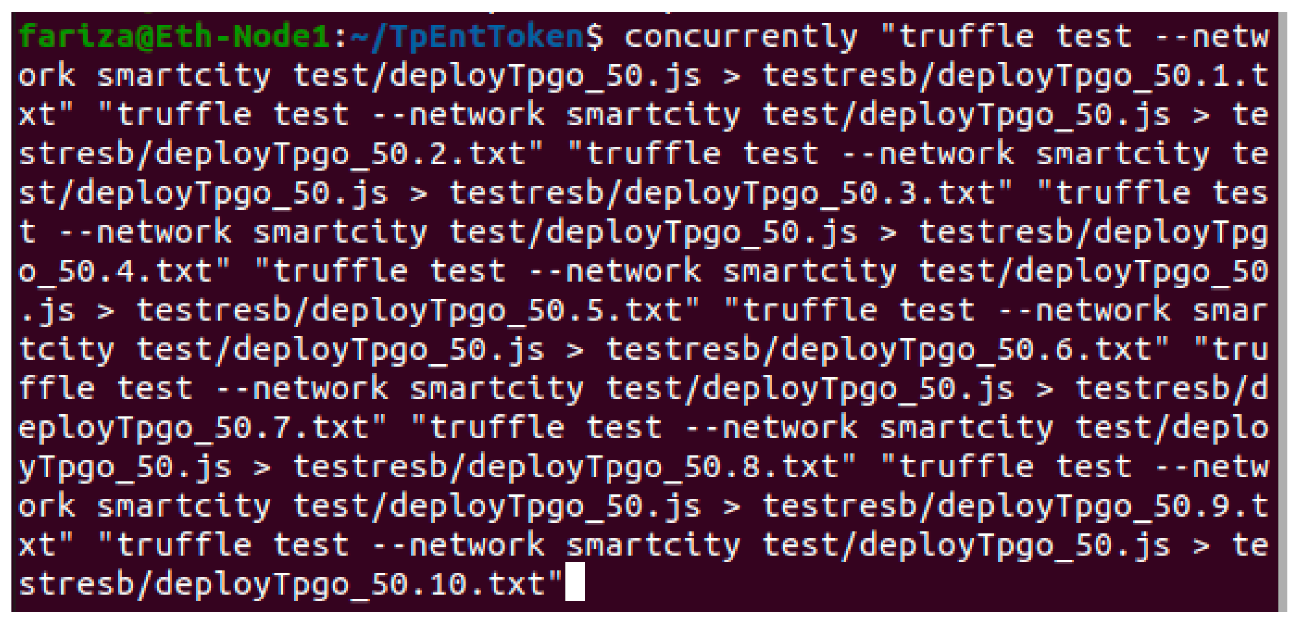
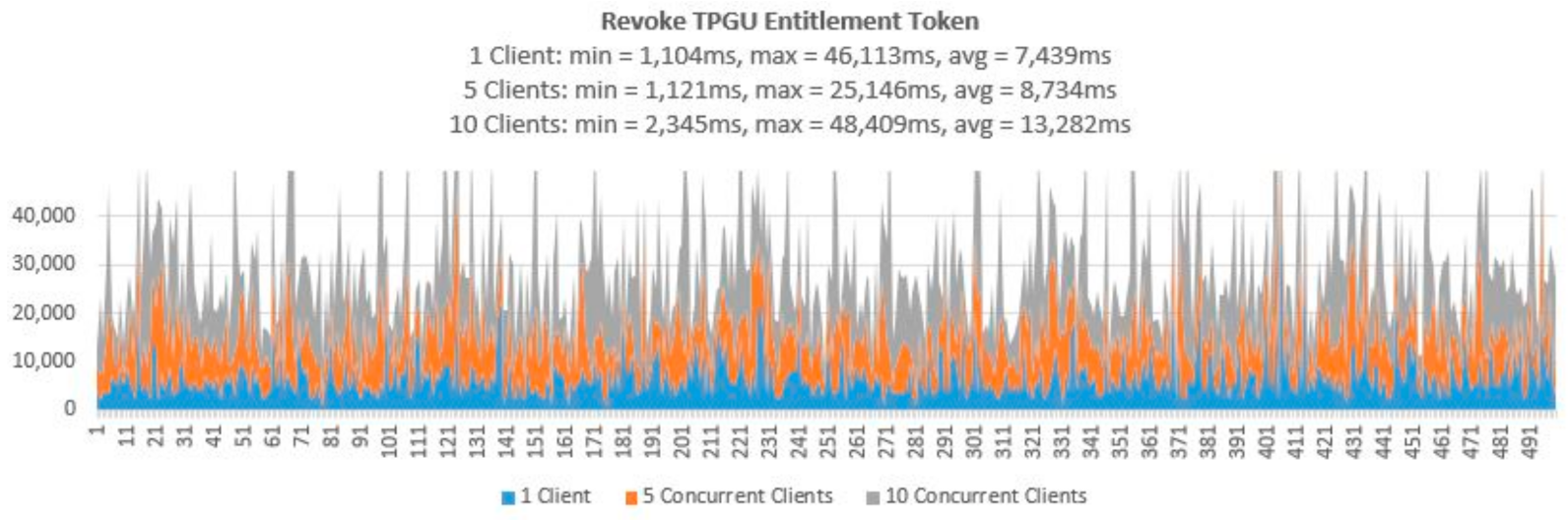
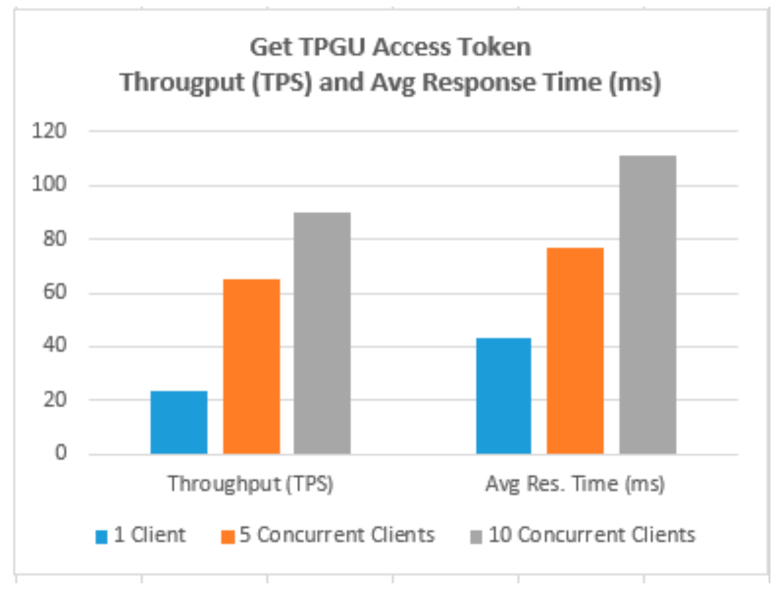
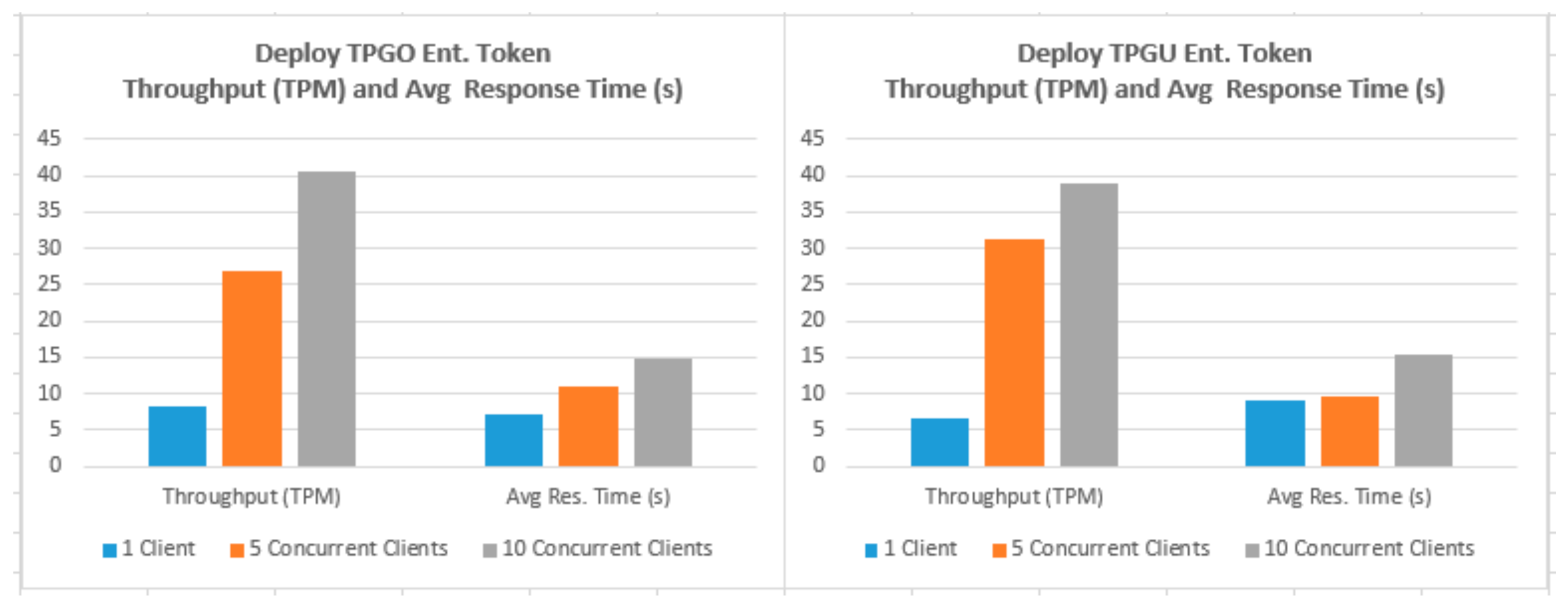
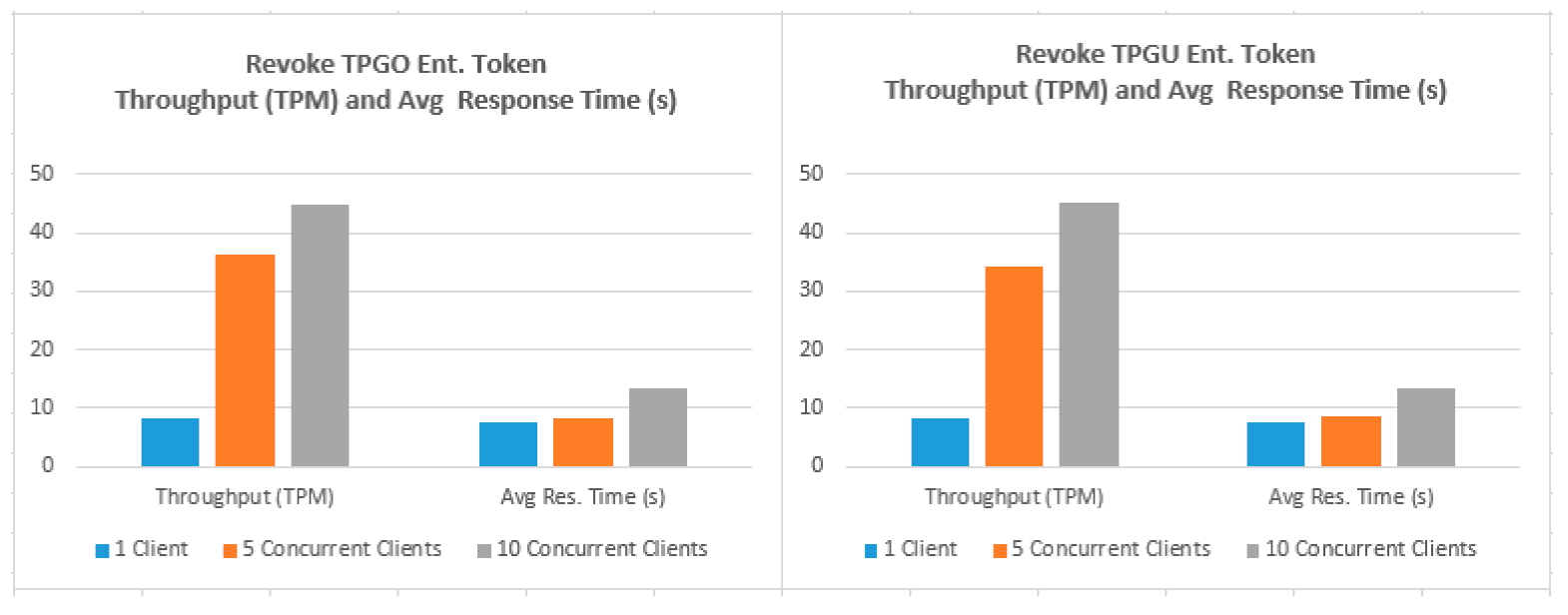
- In order to simulate and test the TP access control for a large IoT network such as smart city, we used the Concurrently application (in Terminal-4) to instantiate parallel instances (×5 and ×10) of our Javascript client application so that we can test the scalability of both deploy entitlement token functions (updating blockchain) and obtain the access token function (reading from blockchain and generating access token). We tested 10,000 read calls and 500 writes/updated calls simultaneously running from 5 and 10 instances of client application concurrently. An example of the concurrently command is shown in Figure 11.
7.2. Experimental Results
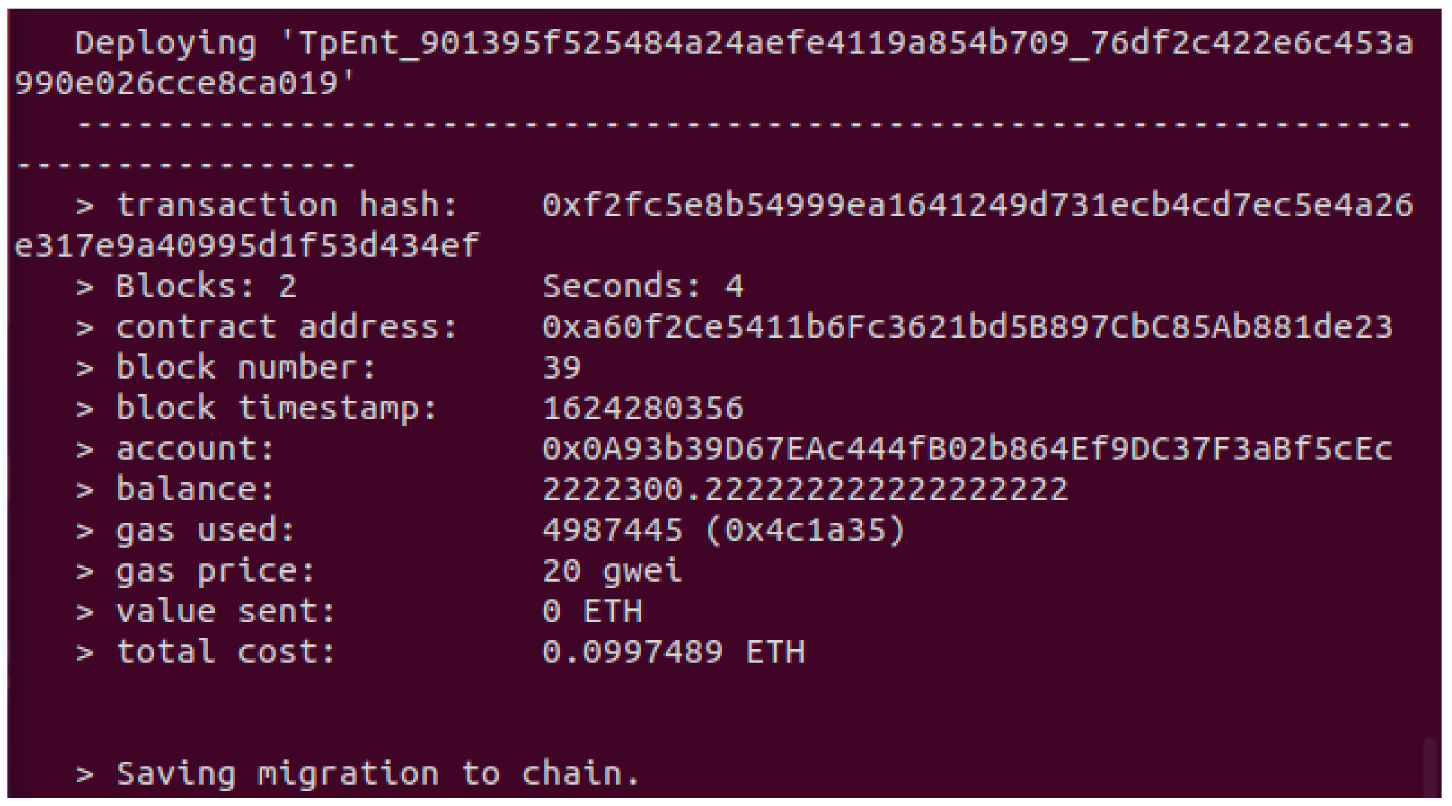
- Testing Smart Contract Deployment
- 2.
- Testing Smart Contract Interfaces—Integration Testing
- 3.
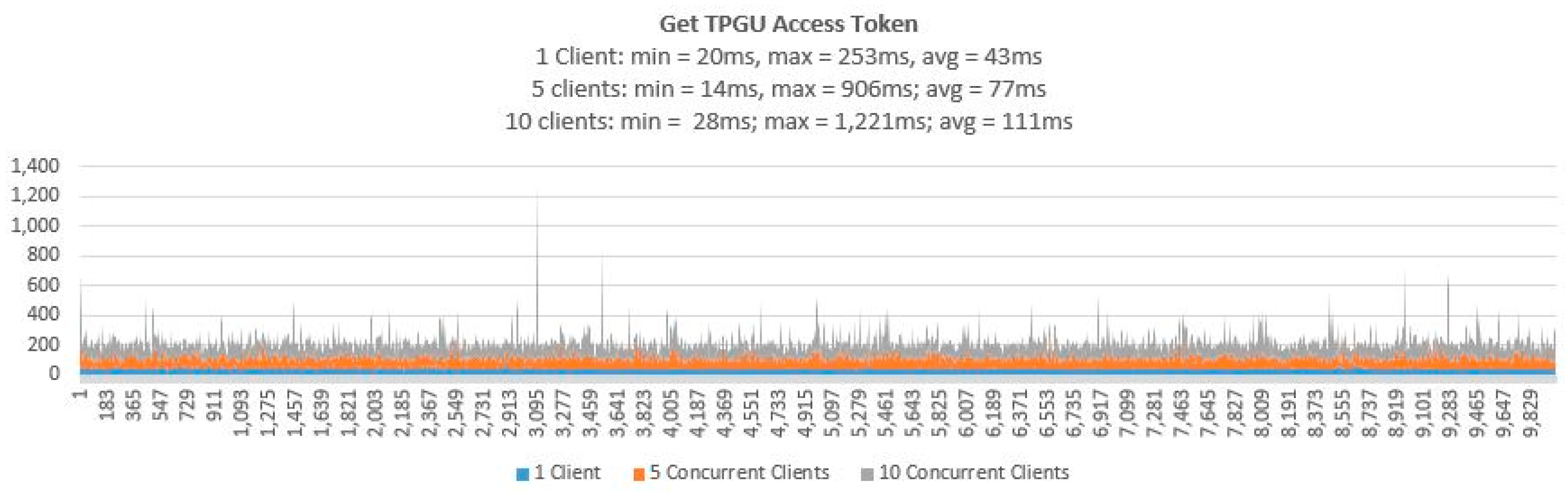
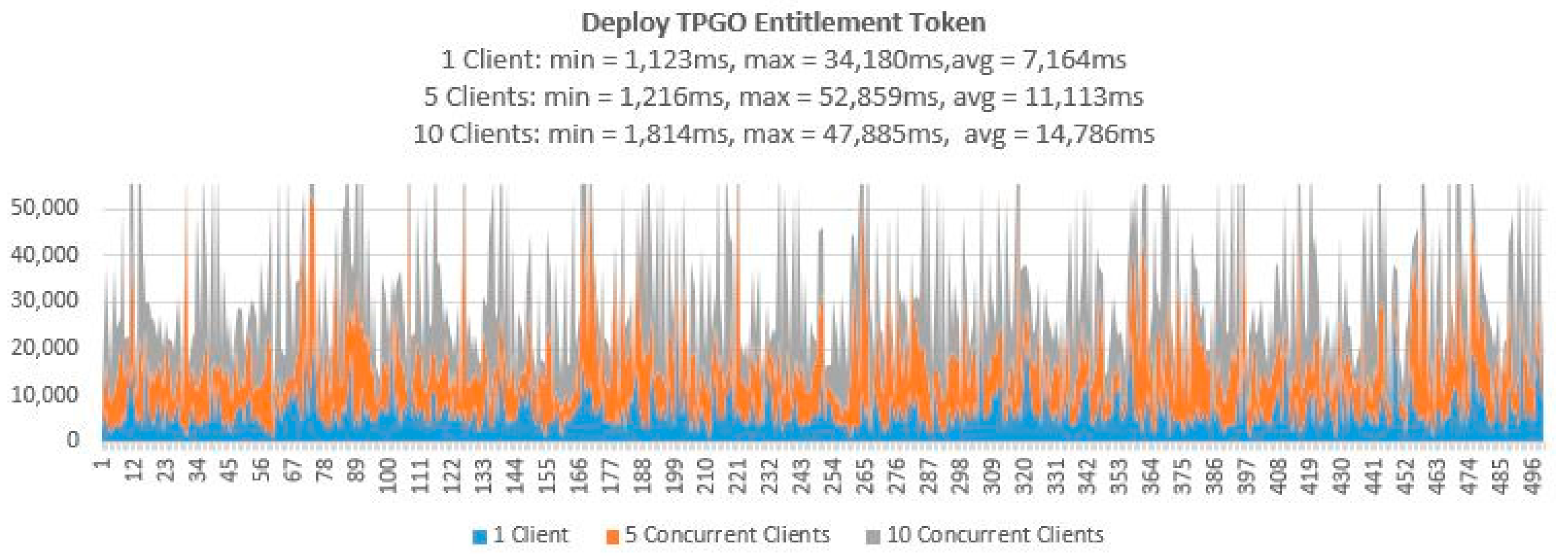
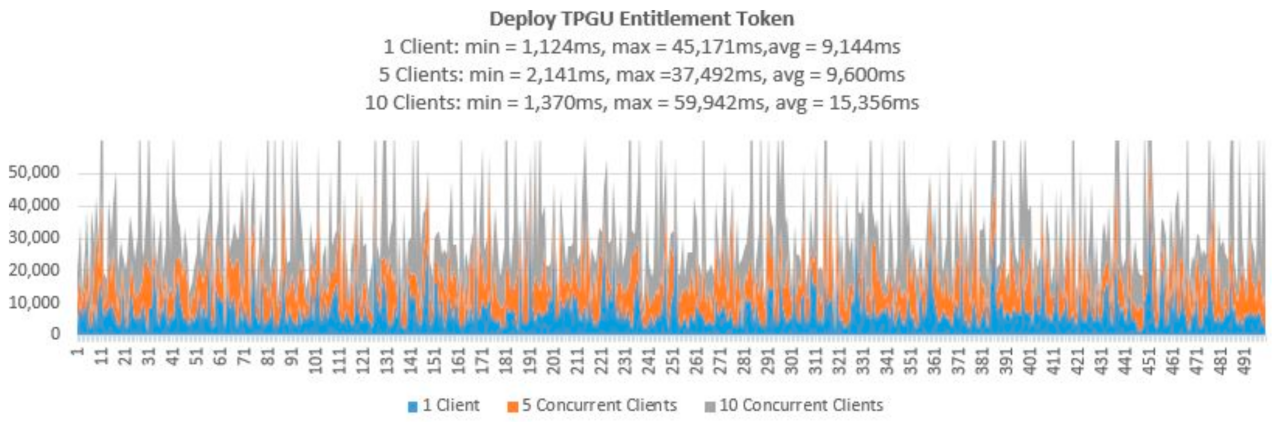
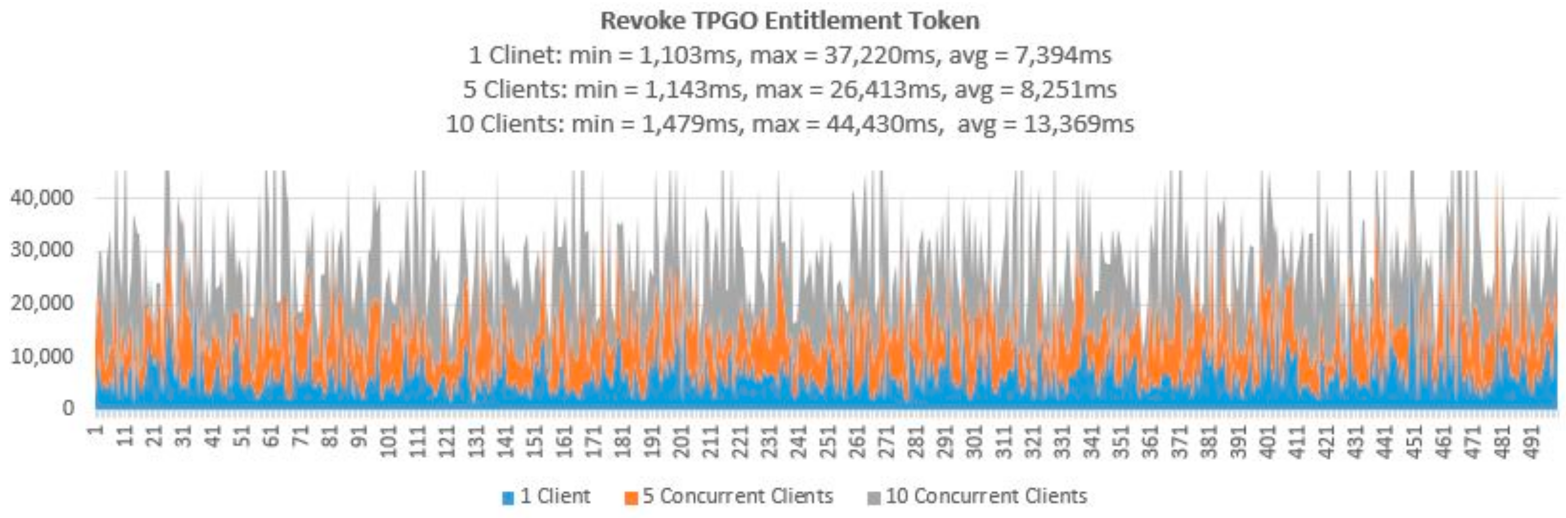
- Testing Smart Contract Interfaces—Performance
7.3. Experimental Results and Evaluation
7.4. Evaluation of Security and Privacy
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef] [Green Version]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Habibzadeh, H.; Soyata, T.; Kantarci, B.; Boukerche, A.; Kaptan, C. Sensing, communication and security planes: A new challenge for a smart city system design. Comput. Netw. 2018, 144, 163–200. [Google Scholar] [CrossRef]
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X. Security and Privacy in Smart City Applications: Challenges and Solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. BlendCAC: A BLockchain-ENabled Decentralized Capability-based Access Control for IoTs. arXiv 2018, arXiv:1804.09267v1. [Google Scholar]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2018, 6, 1594–1605. [Google Scholar] [CrossRef] [Green Version]
- Sabrina, F. A Novel Entitlement-based Blockchain-enabled Security Architecture for IoT. In Proceedings of the 2019 29th International Telecommunication Networks and Applications Conference (ITNAC), Auckland, New Zealand, 27–29 November 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A Novel Attribute-Based Access Control Scheme Using Blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Sabrina, F. Blockchain and Structural Relationship Based Access Control for IoT: A Smart City Use Case. In Proceedings of the 2019 IEEE 44th Conference on Local Computer Networks (LCN), Osnabrueck, Germany, 14–17 October 2019; pp. 137–140. [Google Scholar]
- Wang, P.; Yue, Y.; Sun, W.; Liu, J. An Attribute-Based Distributed Access Control for Blockchain-enabled IoT. In Proceedings of the 2019 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 21–23 October 2019; pp. 1–6. [Google Scholar]
- Islam, M.A.; Madria, S. A Permissioned Blockchain Based Access Control System for IOT. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 469–476. [Google Scholar]
- Sultana, T.; Almogren, A.; Akbar, M.; Zuair, M.; Ullah, I.; Javaid, N. Data Sharing System Integrating Access Control Mechanism using Blockchain-Based Smart Contracts for IoT Devices. Appl. Sci. 2020, 10, 488. [Google Scholar] [CrossRef] [Green Version]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Fairaccess: A new blockchain-based access control framework for the internet of things. Secur. Commun. Netw. 2016, 9, 5943–5964. [Google Scholar] [CrossRef]
- Alphandy, O.; Amoretti, M.; Claeys, T.; Dall’Asta, S.; Duday, A.; Ferrari, G.; Rousseauy, F.; Tourancheauy, B.; Veltri, L.; Zanichelli, F. IoTChain: A Blockchain Security Architecture for the Internet of Things. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Zhaofeng, M.; Lingyun, W.; Xiaochang, W.; Zhen, W.; Weizhe, Z. Blockchain-Enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data. IEEE Internet Things J. 2019, 7, 4000–4015. [Google Scholar] [CrossRef]
- Al-Megren, S.; Alsalamah, S.; Altoaimy, L.; Alsalamah, H.; Soltanisehat, L.; Almutairi, E.; Pentland, A.S. Blockchain Use Cases in Digital Sectors: A Review of the Literature. In Proceedings of the IEEE Conference on Blockchain (Blockchain 2018), Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar]
- Hakak, S.; Khan, W.Z.; Gilkar, G.A.; Imran, M.; Guizani, N. Securing Smart Cities through Blockchain Technology: Architecture, Requirements, and Challenges. IEEE Netw. 2020, 34, 8–14. [Google Scholar] [CrossRef]
- Abbas, S.S.; Sierra-Sosa, D.; Kumar, A.; Elmaghraby, A. IoT in smart cities: A survey of technologies, practices and challenges. Smart Cities 2021, 4, 429–475. [Google Scholar] [CrossRef]
- Majeed, U.; Khan, L.U.; Yaqoob, I.; Kazmi, S.M.A.; Salah, K.; Hong, C.S. Blockchain for IoT-based smart cities: Recent advances, requirements, and future challenges. J. Netw. Comput. Appl. 2021, 181, 103007. [Google Scholar] [CrossRef]
- Bhushan, B.; Khamparia, A.; Sagayam, M.; Sharma, S.; Ahad, M.; Debnath, N. Blockchain for Smart Cities: A review of Architectures, Integration Trends and Future Research Directions. Sustain. Cities Soc. 2020, 61, 102360. [Google Scholar] [CrossRef]
- Xu, R.; Nagothu, D.; Chen, Y. Decentralized Video Input Authentication as an Edge Service for Smart Cities. IEEE Consum. Electron. Mag. 2021, PP, 1. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E. Decentralized Access Control for IoT Based on Blockchain and Smart Contract. In Modeling and Design of Secure Internet of Things; John Wiley & Sons: Hoboken, NJ, USA, 2020; pp. 505–528. [Google Scholar]
- Yavari, A.; Panah, A.S.; Georgakopoulos, D.; Jayaraman, P.P.; Van Schyndel, R. Scalable Role-Based Data Disclosure Control for the Internet of Things. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2226–2233. [Google Scholar]
- Liu, Q.; Zhang, H.; Wan, J.; Chen, X. An Access Control Model for Resource Sharing Based on the Role-Based Access Control Intended for Multi-Domain Manufacturing Internet of Things. IEEE Access 2017, 5, 7001–7011. [Google Scholar] [CrossRef]
- Ye, N.; Zhu, Y.; Wang, R.C.; Malekian, R.; Qiao-min, L. An efficient authentication and access control scheme for perception layer of internet of things. Appl. Math. Inf. Sci. 2014, 8, 1617–1624. [Google Scholar] [CrossRef] [Green Version]
- Bhatt, S.; Patwa, F.; Sandhu, R. Access control model for aws internet of things. In International Conference on Network and System Security; Springer: Berlin/Heidelberg, Germany, 2017; pp. 721–736. [Google Scholar] [CrossRef]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-Based Access Control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Gusmeroli, S.; Piccione, S.; Rotondi, D. A capability-based security approach to manage access control in the internet of things. Math. Comput. Model. 2013, 58, 1189–1205. [Google Scholar] [CrossRef]
- Mahalle, P.N.; Anggorojati, B.; Prasad, N.R.; Prasad, R. Identity authentication and capability based access control (iacac) for the internet of things. J. Cyber Secur. Mobil. 2013, 1, 309–348. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Zeadally, S.; Huang, X.; Liu, Z. Blockchain-based Data Sharing System for Sensing-as-a-Service in Smart Cities. ACM Trans. Internet Technol. 2021, 21, 1–21. [Google Scholar]
- Saha, S.; Sutrala, A.K.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. On the Design of Blockchain-Based Access Control Protocol for IoT-Enabled Healthcare Applications. In Proceedings of the 2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Tapas, N.; Longo, F.; Merlino, G.; Puliafito, A. Experimenting with smart contracts for access control and delegation in IoT. Futur. Gener. Comput. Syst. 2020, 111, 324–338. [Google Scholar] [CrossRef]
- Zhang, Y.; Yutaka, M.; Sasabe, M.; Kasahara, S. Attribute-Based Access Control for Smart Cities: A Smart-Contract-Driven Framework. IEEE Internet Things J. 2021, 8, 6372–6384. [Google Scholar] [CrossRef]
- Go-Ethereum. Available online: https://github.com/ethereum/go-ethereum (accessed on 10 January 2021).
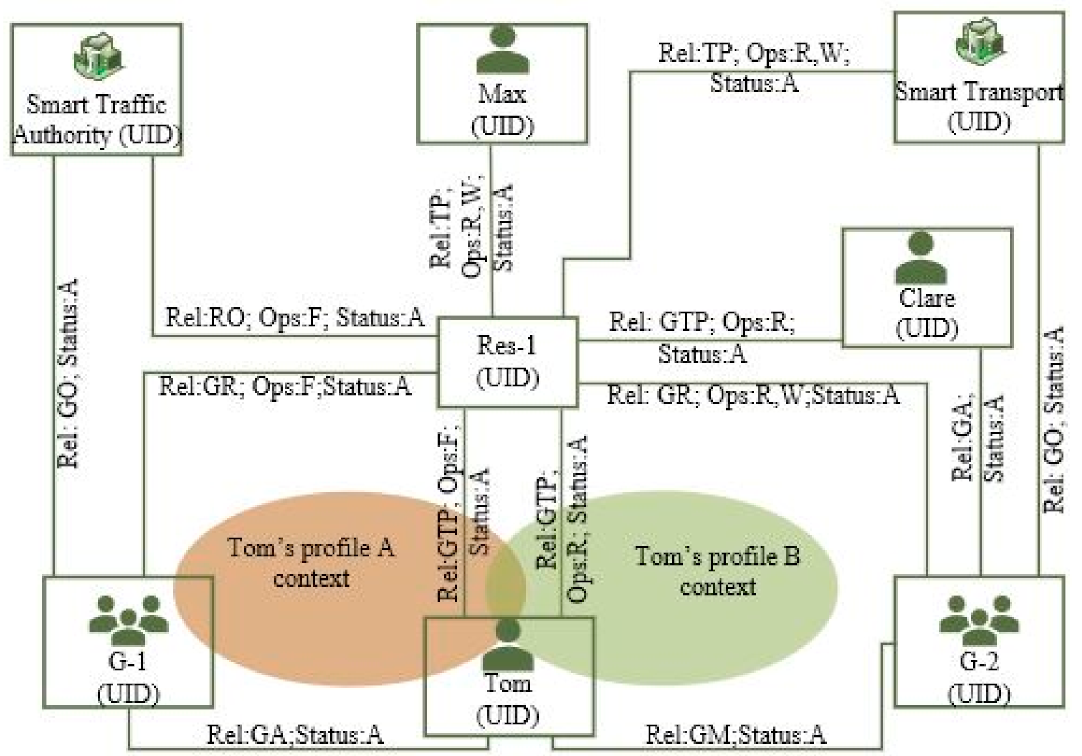

| Acronym | Description |
|---|---|
| Org | An organization entity or domain. It is the registered legal business entity that runs the organization. |
| Ind | An individual entity. |
| Res | An IoT Resource. |
| RO | Resource Owner. It could be an Org or Ind entity. |
| G | A Group (division) within an Org. |
| GO | Group Owner. It could be either RO Org or TP Org. |
| P | A party. It is an entity representing an Org, Ind, G, or U. |
| GM | A Group Member. GM represents a relationship between an Ind and G. |
| GA | A Group Admin. GA also represents a relationship between an Ind and G. (GA is a GM with admin privilege). |
| U | A User. It is an Ind. |
| TP | Third Party. An external Org or external Ind. |
| TPGO | Third-Party Group Owner. |
| TPGU | Third-Party Group User. |
| GTP | Group Third Party. A party within an Org G. |
| GR | Group Resource. It is an RS made available for a G. |
| Rel | Relationship between a P and RS or between Ps (parties). In the proposed model, Rel can be labelled as RO, GO, GR, TP, GTP, GM, or GA. |
| Ops | A set of Operations (e.g., Read (R), Write (W), F (Full)). |
| Cs | A set of constraints (e.g., Status (Active(A)/Inactive(I))). |
| Interface Name | Description |
|---|---|
| deployTPGOEntToken | This interface is called by the RO to deploy a TPGOEntToken. |
| deployTPGUEntToken | This interface is called by the TPGO to deploy a TPGUEntToken. |
| getTPGUAccessToken | This interface is be called by the TPGO network to retrieve the TPGUAccessToken (which is presented to the resource owner to gain access on the given resource). |
| revokeTPGUEntToken | This interface is called by the TPGO for revoking a TPGUEntToken. |
| revokeTPGOEntToken | This interface is called by the RO to revoke the TPGO token. The interface also carries out a cascade revoke for all the associated TPGUEntToken. |
| addDeleteTPGOAddress | This interface can be called by the TPGO for maintaining a list of valid blockchain account addresses for TPGO for accessing the smart contract. |
| addDeleteROAddress | This interface is called by the RO for maintaining a list of valid blockchain account addresses for RO for accessing the smart contract. |
| Data Storage—Using Array | Data Storage—Using Mapping |
|---|---|
| tpgoEntRecord[] private tpgoEntTokens; | mapping (bytes32 ≥ tpgoEntRecord) private tpgoEntTokens; |
| tpguEntRecord[] private tpguEntTokens; | mapping (bytes32 ≥ tpguEntRecord) private tpguEntTokens; |
| addressRecord[] private tpgoAddresses; | mapping (address ≥ uint) private tpgoValidAddresses; |
| addressRecord[] private roAddresses; | mapping (address ≥ uint) private roValidAddresses; |
| Functions | Deploy Entitlement Tokens, Add Eligible Addresses | Revoke Entitlement Tokens, Remove Eligible Addresses | Get Access Token |
|---|---|---|---|
| Time | O(1) | O(1) | O(1) |
| Space | O(N) | O(1) | O(1) |
| Interface | Test Results with Response Time and Transaction Receipt (Partial) |
|---|---|
| Deploy TPGO Ent Token | Response Time: 3210 ms; transactionHash: 0xed5412899c4129547bcd07745cec2e2bbbfb1250f3c17647aa8d1e4ab96f487;blockHash: 0xad09c089c20423c44733951a5d0a54dc92140595ca9e00a8ab5d50180c3ce95; gasUsed: 284945 |
| Revoke TPGO Ent Token | Response Time: 4172 ms; transactionHash: 0 × 4fd852805a1a33aeb97e9b50438c0d5e21e58c24a509cda919d7969dbce06ba4;blockHash: 0xd0884ca4db333629671ddb4bfc5d21c00bec704e0fb913b96bd46fa49d6943; gasUsed: 26,293 |
| Deploy TPGU Ent Token | Response Time: 4199 ms; transactionHash: 0xffd3f29cc74fd0e75eb49bb3b431ec2b1c9de769e0d5c9ab470f9f4873484347;blockHash: 0xa696ae2f8c7ca162f37bc7e4ba0b3537f6ed90246df04a7d6c89c2dffbf5505c; gasUsed: 433,140 |
| Revoke TPGU Ent Token | Response Time: 4212 ms; transactionHash: 0x43b0a1c6ccac6d2d3d6bfc649dbb6414e3247c7cff27bae639ca04c95d38135;blockHash: 0x160dbc93126c99effb103ac32f6403aaabc8261480f56143928604de50773dc; gasUsed: 29,271 |
| Add or Delete RO Address | Response Time: 5225 ms; transactionHash: 0x02cf9483a40a58ab2a5bf4e0158e144e8fc00a6c26d17874bc1b95ed187de4fa; blockHash: 0x7c664750eaf0f2c9e737e5e207d4e790eed70d2200b3af36a4bd5ad98eed79c; gasUsed: 44,485 |
| Add or Delete TPGO Address | Response Time: 4263 ms; transactionHash: 0x3f9c5f2870d8cff7765e4fe121d52699bce86f25575a47d3e5c46bf7b5e08e56; blockHash: 0xd2b8681c8b24bd2f4b8fc023939289df12da44c4e49131fbc06d5133789400c; gasUsed: 44,484 |
| Interface | Total Volume (# Calls) | One Client (# Calls) | Five Concurrent Clients (Each # Calls) | Ten Concurrent Clients (Each # Calls) |
|---|---|---|---|---|
| Get TPGU Access Token | 10,000 | 10,000 | 2000 | 1000 |
| Deploy TPGO Ent Token | 500 | 500 | 100 | 50 |
| Revoke TPGO Ent Token | 500 | 500 | 100 | 50 |
| Deploy TPGU Ent Token | 500 | 500 | 100 | 50 |
| Revoke TPGU Ent Token | 500 | 500 | 100 | 50 |
| Concerns | Definition | How It Is Addressed in The Proposed Architecture |
|---|---|---|
| Authentication | Authentication verifies user identity. | Organization-specific Authentication (Auth) mechanism will apply for resource owner and user applications. BC nodes will use their BC accounts. Standard Auth using functional logon, mutual Auth, API keys etc. to be used for system-system access. |
| Access Control | Access control ensures legitimacy of user’s access on a resource. | Entitlement-based and blockchain-enabled access control for TP access as presented in the paper above. Entitlement-based access control for organization’s internal users. The proposed architecture also provides robust revoke mechanisms with revoke propagation. Smart contract functions are designed utilizing “Secure by Design” principles. For instance, each of the function does the validations and reject the calls if the callers are not authorized and/or the invalid data are passed in. The design also allows flexibility of maintaining a RO and TPGO account address list by the legitimate users. If an account becomes compromised, the RO and TPGO can delete (i.e., make invalid) an address. |
| Privacy/Anonymity | User’s identity is not identifiable to public. | No personally identifiable information (PII) data are deployed in BC. SSL tunnel encryption applies for all communications. Access token will be included in authorization (bearer) header which will be SSL tunnel encrypted. Additionally, access token will be digitally signed (using HmacSha256 algorithm using a secret known by the RO). |
| Confidentiality | Information for a user is made unintelligible to others | In the proposed solution, user’s public key URL will be part of user’s access token and the data can be encrypted with the user’s public key by the resource access gateway before returning the data. |
| Integrity | Ensuring that data is not modified by un-authorized party. | Standard-based process and mechanisms will be applied for data at rest by the RO. Any tampering of entitlement tokens in BC is protected by validating that the caller’s blockchain account address is eligible. Additionally, any tampering of the access token is protected by digital signature. |
| Availability | Ensuring that services are available to legitimate users. | It is assumed that industry standard-based policies and security controls (including firewalls/appliances) will be used by each organization. Moreover, both gateways will validate the access rights to eliminate any Denial of Services (DoS) attacks. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sabrina, F.; Jang-Jaccard, J. Entitlement-Based Access Control for Smart Cities Using Blockchain. Sensors 2021, 21, 5264. https://doi.org/10.3390/s21165264
Sabrina F, Jang-Jaccard J. Entitlement-Based Access Control for Smart Cities Using Blockchain. Sensors. 2021; 21(16):5264. https://doi.org/10.3390/s21165264
Chicago/Turabian StyleSabrina, Fariza, and Julian Jang-Jaccard. 2021. "Entitlement-Based Access Control for Smart Cities Using Blockchain" Sensors 21, no. 16: 5264. https://doi.org/10.3390/s21165264
APA StyleSabrina, F., & Jang-Jaccard, J. (2021). Entitlement-Based Access Control for Smart Cities Using Blockchain. Sensors, 21(16), 5264. https://doi.org/10.3390/s21165264






