Security Architecture for Defining and Enforcing Security Profiles in DLT/SDN-Based IoT Systems
Abstract
:1. Introduction
- Extension of the current MUD model with MSPL to define a wide variety of security policies beyond network access control
- Integration of the MUD obtaining and enforcement processes in a lightweight bootstrapping process based on CoAP-EAP [15]
- Definition of the architecture and message exchange required to obtain and enforce MUD restrictions, improving security aspects of IoT devices’ operation
- Integration of SDN techniques with attribute-based security for the enforcement of the extended MUD restrictions
- Usage of the Distributed Ledger Technology (DLT) (e.g., blockchain) technology to ensure accountability and data provenance features for IoT devices and InterPlanetary File System (IPFS) technology to improve the scalability of the blockchain.
- Implementation and validation of the proposal in a real testbed showing its feasibility and performance to manage security profiles in IoT deployments
2. Related Work
3. Motivation, Challenges, and Proposed Solutions
- Extended network access control (filtering) policies restrict the communications from/to the device at network layer. Although the standard MUD is aimed to describe these policies, the proposed extension adds more fine-grained conditions (e.g., MAC address or interface).
- Channel protection aims to specify fine-grained security aspects of devices’ communications such as the ciphersuite to be used by a certain protocol (e.g., the Datagram Transport Layer Security (DTLS) protocol [39]).
- Data privacy is intended to specify combination of attributes to encrypt the data provided by IoT devices. Therefore, those entities that possess the necessary attributes specified in the extended MUD profile, can access to the encrypted data.
- Authorization over resources is focused on protecting the access to devices’ resources. These policies describe the authorized actions over a resource, as well as the entity that is allowed to do that.
4. Augmenting Behavioral Profiles through MUD Extensions
- rw from-device-policy
- | rw acls
- | | rw access-list* [name]
- | | rw name -> /acl:acls/acl/name
- | rw mspls
- | rw mspl-list* [name]
- | rw name -> /mspl:mspls/mspl/name
- rw to-device-policy
- rw acls
- | rw access-list* [name]
- | rw name -> /acl:acls/acl/name
- rw mspls
- rw mspl-list* [name]
- rw name -> /mspl:mspls/mspl/name
- module: umu-mspl-list
- | rw mspls
- | rw mspl* [name]
- | rw name string
- | rw configuration
- | capability string
- | configuration-rules
- | rw configuration-rule* [name]
- | | rw configuration-rule-action
- | | rw configuration-rule-condition
- | rw name
- | rw priority
- end_module
- module: umu-mspl-filtering-condition
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule:mspl:configuration-rule-condition
- | rw packet-filter-condition
- | rw application-layer-condition?
- | qos-condition?
- |
- end_module
- module: umu-mspl-packet-filter-condition
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule/mspl:umu-mspl-filtering-condition/
- mspl:packet-filter-condition
- | rw source-mac?
- | rw destination-mac?
- | rw source-address?
- | rw destination-address?
- | rw source-port?
- | rw destination-port?
- | rw direction?
- | rw interface?
- | rw protocol-type?
- end_module
- module: mspl-mspl-privacy-action
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule:mspl:configuration-rule-action
- | rw privacy-action-type string
- | rw privacy-method
- end_module
- module: umu-mspl-abprivacy-method
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule/mspl:mspl-mspl-abprivacy-action/
- mspl-privacy-method
- | rw attributes
- | rw attribute?*
- | | rw key string
- | | rw value string
- | rw attribute-chain? string
- end_module
- module: mspl-mspl-AuthorizationAction
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule:mspl:configuration-rule-action
- | rw AuthorizationActionType
- end_module
- module: umu-mspl-AuthorizationCondition
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule:mspl:umu-mspl-filtering-condition
- | rw AuthorizationSubject string
- | rw AuthorizationTarget string
- end_module
- module: umu-mspl-data-protection-action
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule/mspl:configuration-rule-action
- | +--rw technology string
- | +--rw technology-action-parameters
- | | +--rw technology-parameter*
- | | +--rw authentication-parameters
- | | +--rw authentication-parameter*
- | +--rw technology-action-security-properties
- | +--rw technology-action-security-property
- end_module
- module: umu-mspl-dtls-technology-parameter
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule/mspl:technology-action-parameters/
- mspl:technology-parameter
- | +--rw local-endpoint string
- | +--rw remote-endpoint string
- | +--rw tunel boolean
- | +--rw cipher-suite string
- | +--rw ssl-version string
- end_module
- module: umu-mspl-authentication-parameters
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule/mspl:technology-action-parameters/
- mspl:authentication-parameters
- | +--rw psk-value? string
- | +--rw psk-path? string
- | +--rw ca-id? string
- | +--rw ca-path? string
- | +--rw ca-file? string
- | +--rw cert-id? string
- | +--rw cert-file? string
- | +--rw cert-path? string
- | +--rw pub-key-path? string
- | +--rw pub-key-file? string
- | +--rw pub-key-pass? string
- end_module
- module: umu-mspl-data-protection-condition
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule:mspl:umu-mspl-filtering-condition
- end_module
- module: umu-mspl-confidentiality-technology-action-security-property
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule/mspl:technology-action-security-
- properties/mspl:technology-action-security-property
- | +--rw encryption-algorithm? string
- | +--rw key-size? string
- | +--rw mode? string
- end_module
- module: umu-mspl-integrity-technology-action-security-property
- augment /mspl:mspls/mspl:mspl/mspl:configuration/mspl:configuration-
- rules/mspl:configuration-rule/mspl:technology-action-security-
- properties/mspl:technology-action-security-property
- | +--rw integrity-algorithm? string
- | +--rw integrity-header? boolean
- | +--rw integrity-payload? boolean
- end_module
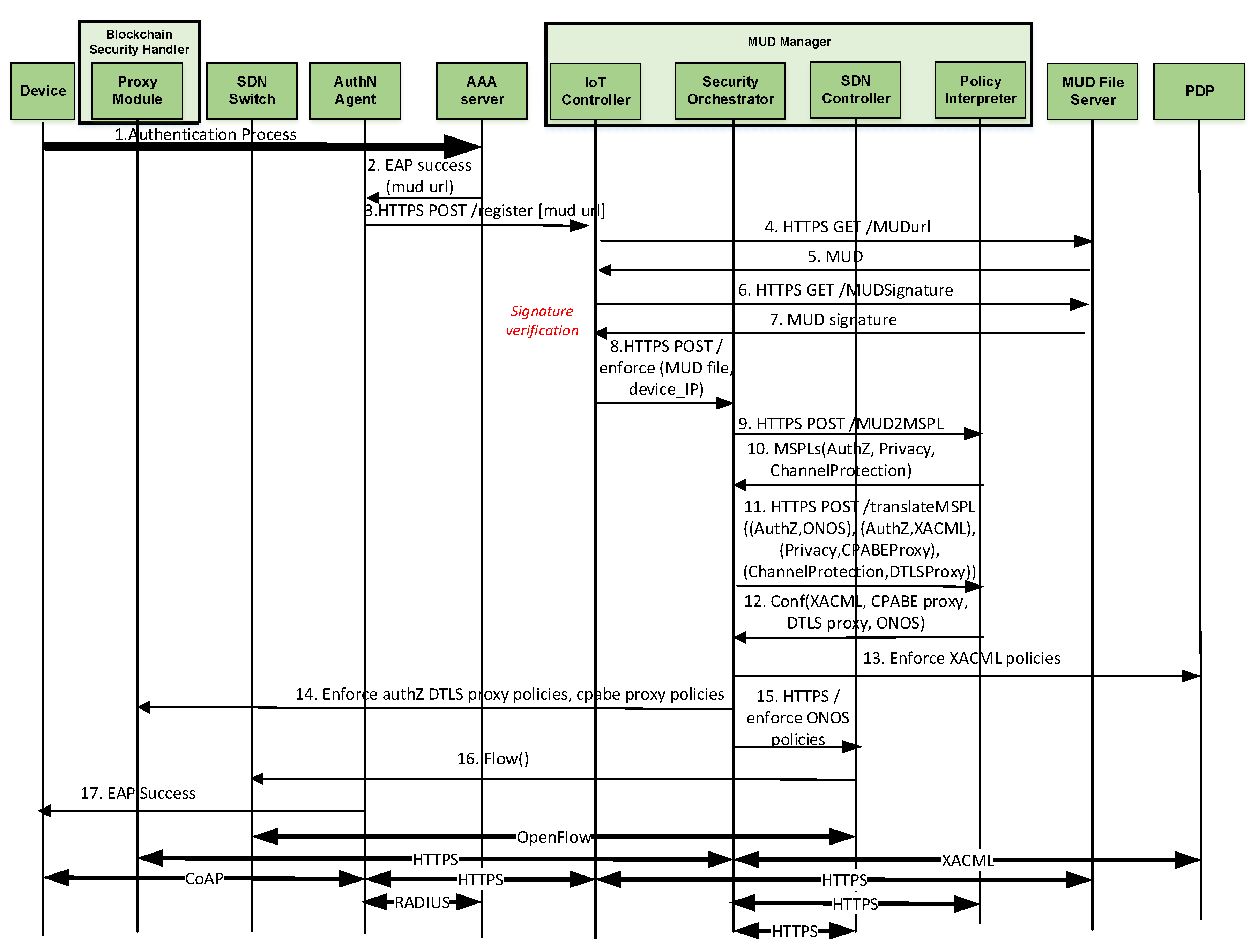
5. Architecture
- Device represents the entity joining the network through a bootstrapping process. It acts as EAP peer and establishes an EAP session with the EAP Server, with the EAP authenticator as intermediary.
- SDN Switch is the entry point of the network. It is in charge of filtering the device traffic based on the network access control policies.
- Authentication Agent, which acts as EAP Authenticator, is an intermediate entity in the EAP communication between the device and the EAP Server.
- AAA Server acts as EAP Server to establish an EAP session with the device.
- MUD Manager is the main entity to manage MUD files, including the processes required for obtaining and enforcing the different security restrictions. It comprises several roles:
- -
- IoT Controller is intended to obtain the extended MUD file from the MUD File Server.
- -
- Policy Interpreter translates the extended MUD file to MSPL policies and specific configuration.
- -
- SDN Controller is in charge of enforcing the network access control policies of the extended MUD file in the SDN switch.
- -
- Security Orchestrator coordinates the enforcement of the extended MUD policies.
- MUD File Server is located in the manufacturer domain and stores the MUD files of the different devices.
- Policy decision Point is in charge of evaluating the authorization policies after they are translated from the MUD file.
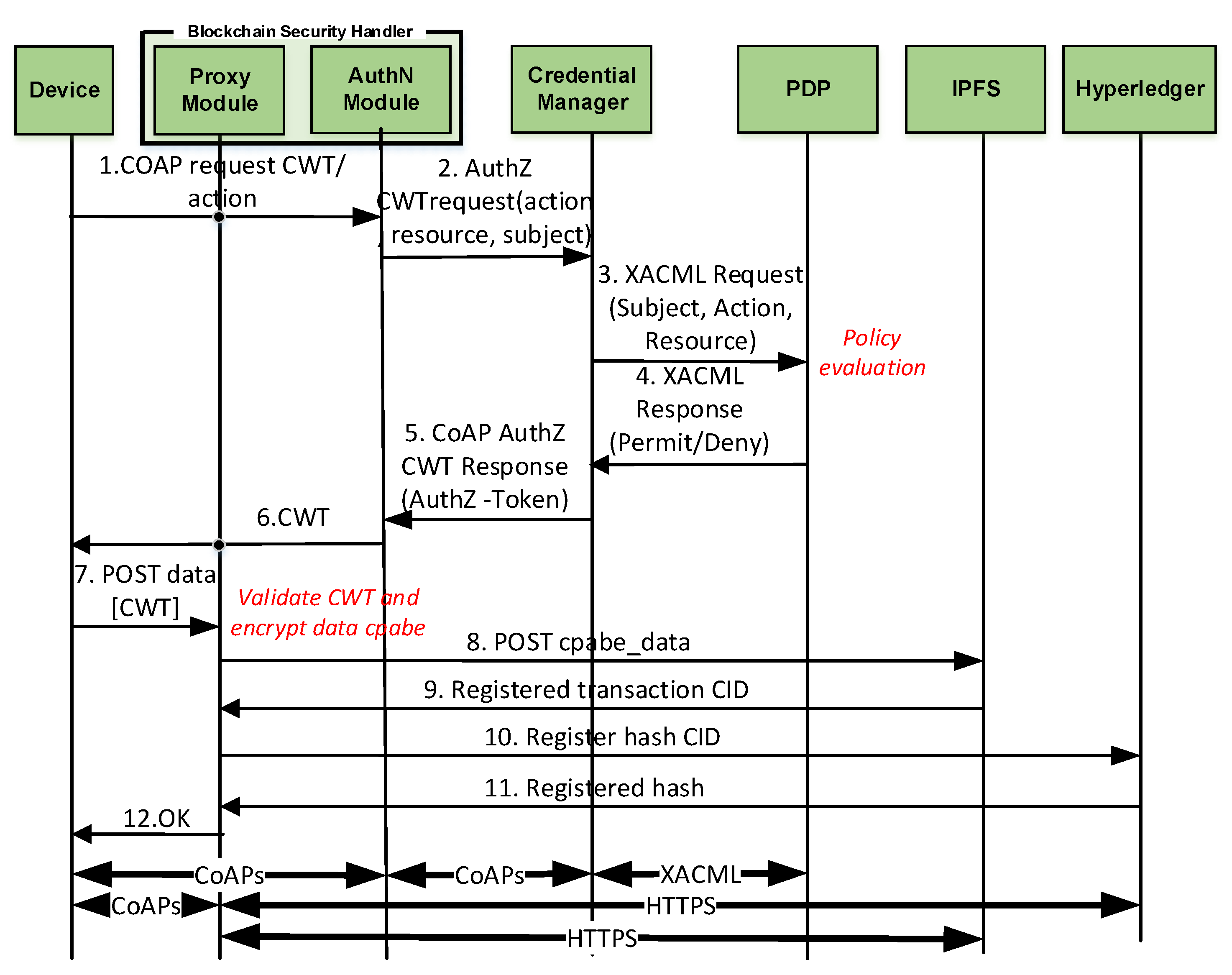
- Blockchain Security Handler is in charge of managing the access over the blockchain in a transparent way for the devices. It comprises two roles:
- -
- Proxy module is in charge of enabling the access to the blockchain, and encrypting and publishing the data generated by the devices in the blockchain. It is also responsible for validating the CWT-AIF tokens to allow or not the access to the blockchain, as well as to enforce the data privacy and channel protection policies from the extended MUD.
- -
- Authentication Module is in charge of managing the token requests device, forwarding them to the Credential Manager.
- Credential Manager is responsible for managing a CWT-AIF token request and generating the token if the device is allowed, based on the policy evaluation in the PDP.
- Distributed storage (IPFS node) is in charge of storing the published encrypted data.
- Blockchain (Hyperledger Fabric) stores the transactions of the published data.
6. Message Exchange
6.1. Bootstrapping Phase
6.1.1. Device Authentication and MUD Obtaining
6.1.2. Extended MUD Translation
6.1.3. Policy Deployment
6.2. Post-Bootstrapping Phase
6.2.1. Authorization Token Request
- COSE Header with COSE parameters following the specification in [50]. It describes the cryptographic operations applied to the token and optional properties. These parameters can be cryptographically protected or not.
- Payload, containing the claims:
- -
- Issuer (iss) identifies the entity that issued the token in a string or URI format.
- -
- Subject (sub) represents the entity that is the subject (holder) of the token in a string or URI format.
- -
- Audience (aud) indicates the recipients that the token is intended for, in a string or URI array. If the entity processing the token is not indicated in this field, the token should be rejected.
- -
- Expiration Time (exp) specifies the expiration time, after which the token will not be valid, in a Numeric Date format.
- -
- Not before (nbf) represents the time, before which the token is not valid, in a Numeric Date format.
- -
- Issued At (iat) specifies the time when the token was issued, in a Numeric Date format.
- -
- CWT ID (cti) provides a unique identifier for the token, in a string format.
- -
- Authorization Information (aif) specifies the resources and methods the token allows to, by using the AIF format
6.2.2. Data and Hash Publication
7. Performance Evaluation
7.1. Testbed
7.2. Evaluation of the Proposal
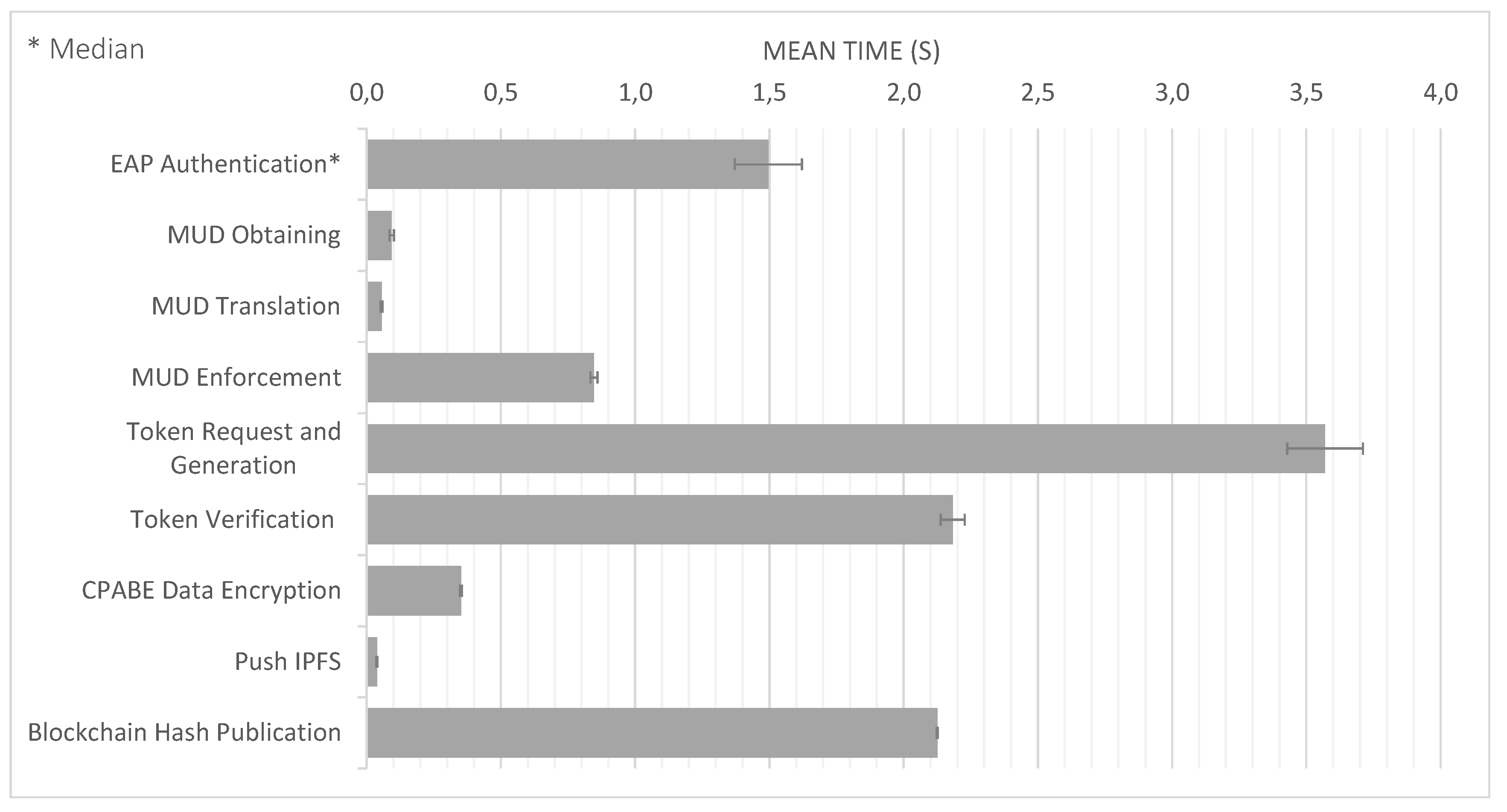
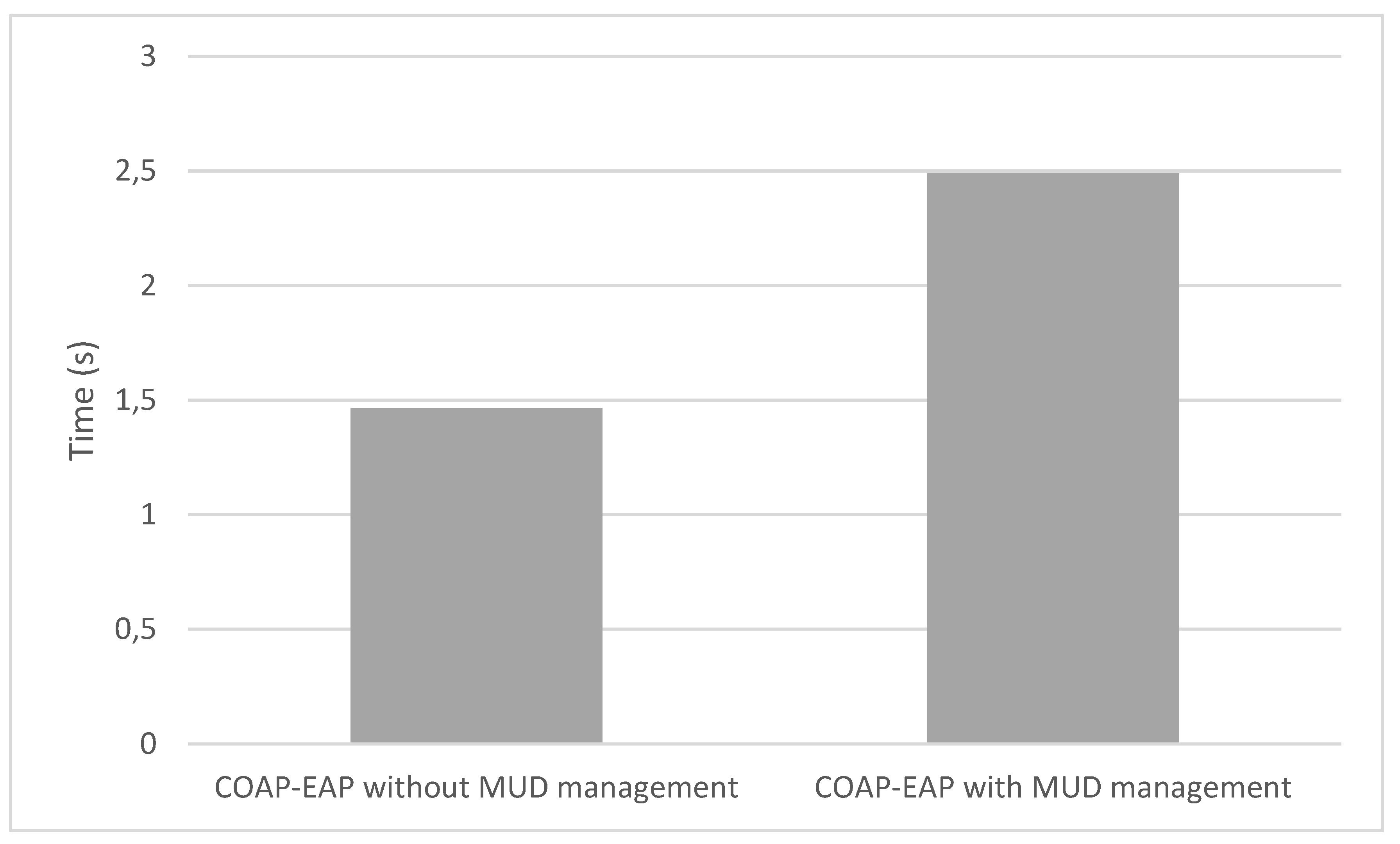
- EAP Authentication comprises Messages 1 (set of messages CoAP-EAP), 2, and 17 in Figure 2. These messages require a median value of 1496 s. The reason to use the median is to provide a more accurate time, avoiding outliers due to packet retransmission. It should be noted that, for the other results, we employ the mean value. Although the EAP authentication is time consuming, this process is performed once, when the device is authenticated to join the network. In addition, the overload of the time with respect to the CoAP-EAP with EAP-PSK exchange [15] is minimum (30.5 ms). Indeed, as the MUD URL is transferred trough a non-constrained network, the extra time is negligible.
- MUD Obtaining evaluation was performed with a MUD file of 7.58 KB (see Appendix A), containing policies of the different types considered (network access control, authorization, channel protection, and data privacy). The delay for this stage is negligible (0.093 s) since the MUD file is also transferred trough a non-constrained network. This time includes the MUD obtaining as well as the MUD signature verification (Messages 3–7 of Figure 2).
- MUD Translation comprises Messages 8–12, including the MSPL translation, as well as the translation from MSPL to a specific configuration. In particular, the network access control policies are translated to ONOS configuration, the authorization policies to XACML policies, and the channel protection policies to DTLS configuration. Finally, data privacy policies are translated to a CP-ABE policy. This CP-ABE policy is obtained by combining the required extended MUD attributes for data privacy with AND statements. We use the same MUD file previously mentioned, thus it includes different types of policies. This MUD file (included in Appendix A) shows the data privacy policy (“umu-mspl-privacy-action:privacy-action-type”: “Data-Privacy”) named “MSPL0” with four attributes specified inside the field “umu-mspl-abprivacy-method:attribute” (“es”, “um”, “iot” and “dep5”). These data privacy attributes are combined with an AND statement to generate a CP-ABE policy to encrypt the published data. MUD translation time is also negligible with respect to other phases (0.055 s).
- MUD Enforcement time includes the delay required for deploying the different types of policies in the MUD file, including the DTLS and CP-ABE configuration in the proxy, the XACML authorization policies in the PDP, and the SDN enforcement of the network access control polices (Messages 13–16 in Figure 2). As the SDN enforcement involves the enforcement of the configuration with Openflow over the SDN switches, this enforcement is the most time-consuming step of this phase. Nevertheless, the time required is less than 1 s (0.847 s), which is affordable during the bootstrapping process.
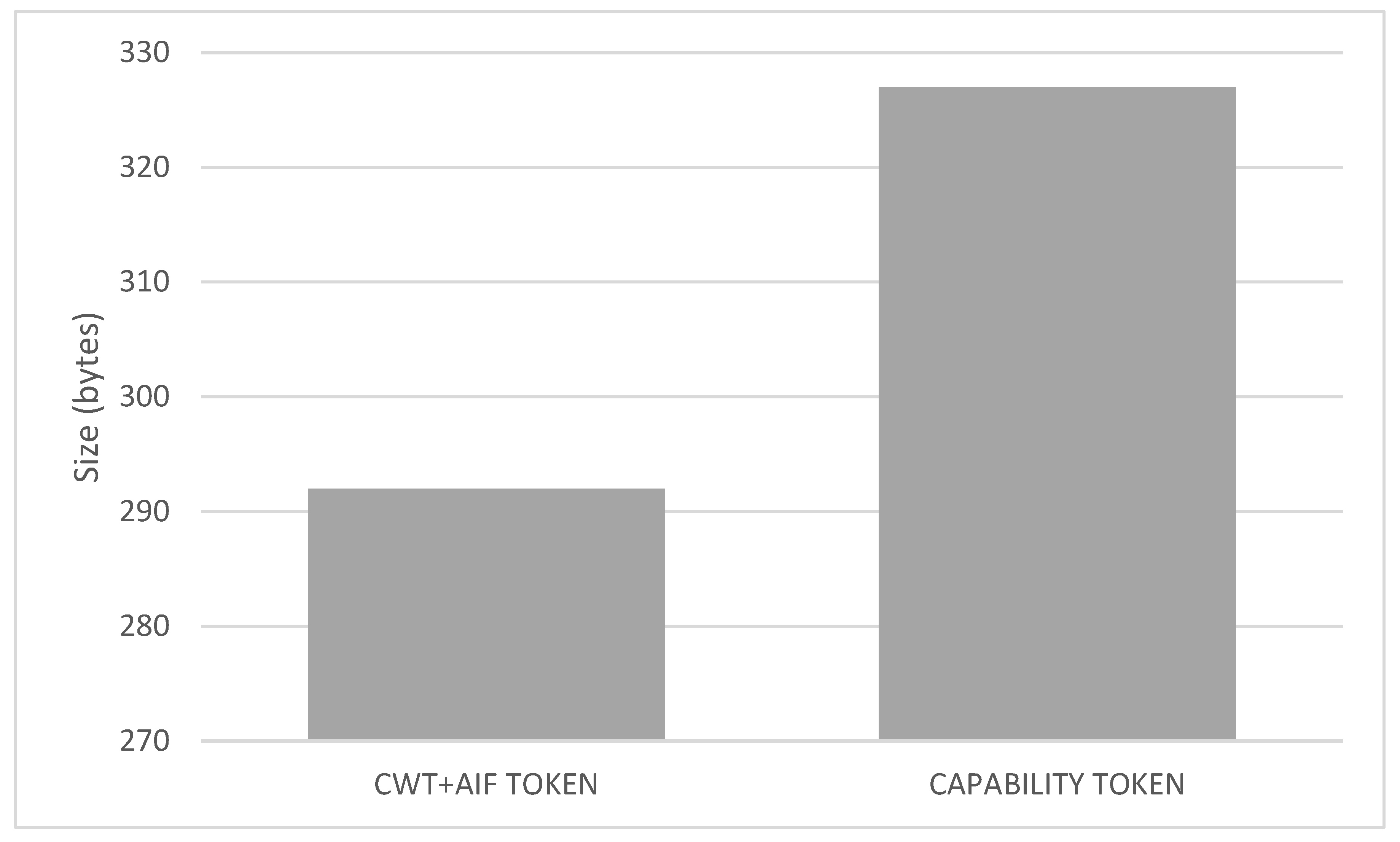
- Token request and generation comprises Messages 1–6 of Figure 3. This phase includes the device request of the CWT-AIF token, the policy evaluation of the PDP, as well as the generation of the token in case of a PERMIT decision. The token was requested for the subject bob, the audience coaps://CAFE:DCAF:8080, and the access to the resource tmp with a POST operation. This operation is allowed by the PDP, as it was specified in the extended MUD (Appendix A). The token was generated with all the claims of the CWT in addition to the AIF extension, as well as the COSE header and the 256-bits signature with the ECDSA algorithm. As shown, this is the most time consuming phase (3570 s). The main reason for this is the involvement of the device for requesting the token through a constrained network. However, it should be noted that the token is meant to be reusable during its lifetime.
- Token verification involves Message 7 and the token verification process of Figure 3. The CWT used during the evaluation (in CBOR diagnostic notation) is shown in Listing 8. This CWT allows bob to access to the resource tmp through the POST method. This process requires a delay of 2182 s, which is strongly influenced by the message sent by the device, that is, the communication between the device and the Proxy Module. Indeed, the mean time consumed only by the verification process is 3044 ms.
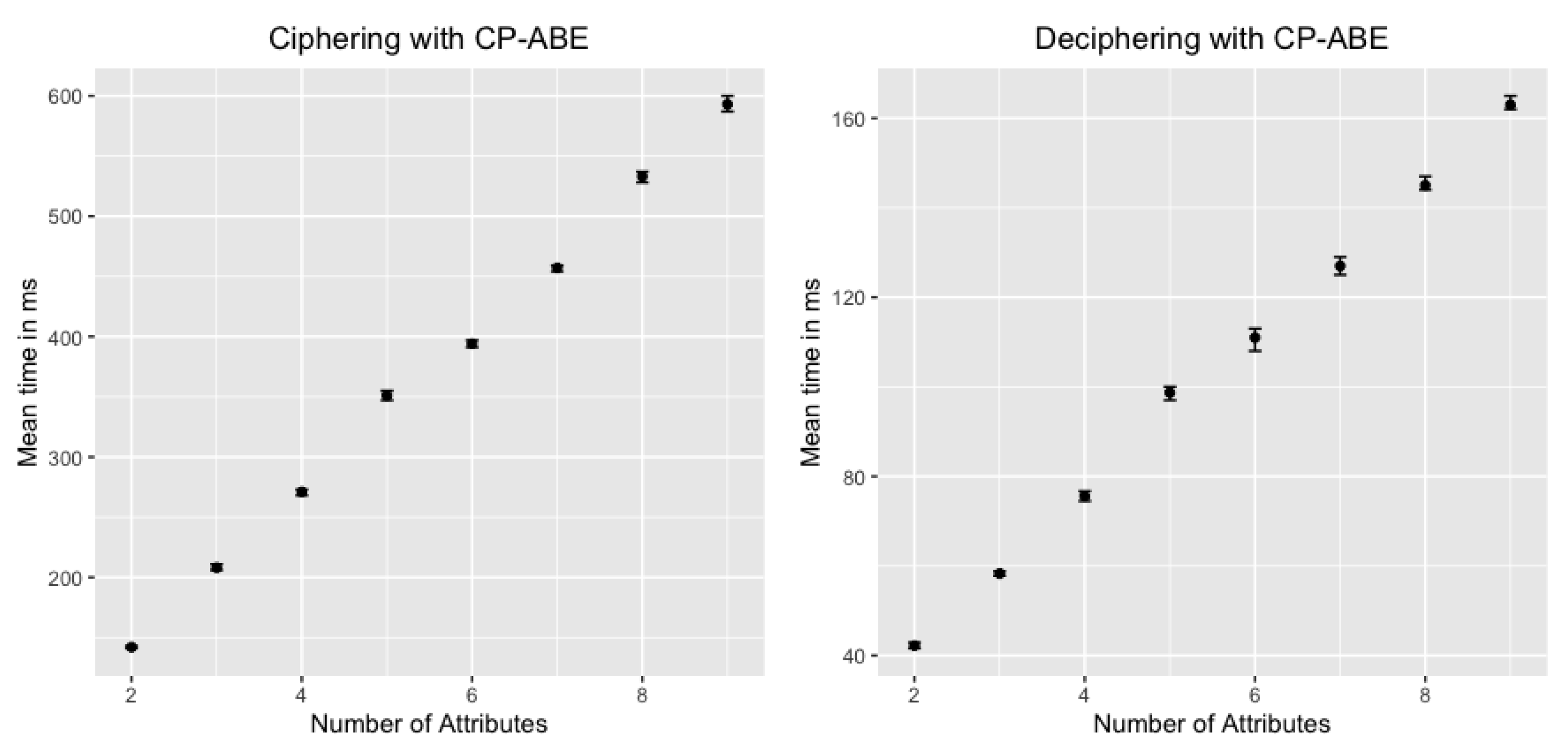
- CP-ABE data encryption is referred as the encryption process in Figure 3, after Message 6. The CP-ABE implementation is based on the curve over the field for some prime 4. The evaluation is performed by considering a 80-bit security level (i.e., , ). For the results in Figure 4, we use asix-attribute CP-ABE policy as example. However, we further analyze the CP-ABE encryption time considering different number of attributes in Figure 5.
- Push IPFS comprises Messages 8 and 9 of Figure 3. The data published were temperature s measurements encrypted with CP-ABE, with the previous configuration, and it took 0.038 s.
- Blockchain hash publication comprises Messages 10–12 of Figure 3. The hash was obtained with the SHA256 algorithm. It is worth noting that the obtained time for this phase was measured in a test environment. For a complete evaluation of the hyperledger performance, the reader can consult the analyses performed by Hyperledger [51] and Jiang et al. [52].
- 18([
- {1: −7},
- {1: “credentialmanager@odins.es”,
- 2: “bob”,
- 3: “coaps://CAFE:DCAF:5684”,
- 4: 1579637954,
- 5: 1579627954,
- 6: 1579626954,
- 7: h’64376B6B7036736E716D367430316D6E64763273676967633031’,
- 8: [[“tmp”, 2]]}, h’4D4551434943786F32346B6F7A57496B4C7056464…’
- ]).
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A. MUD File
- [{
- “ietf-mud:mud”: {
- “mud-version”: 1,
- “mud-url”: “https://iot_controller/iot_broker”,
- “last-update”: “2019-04-17T09:47:00+00:00”,
- “cache-validity”: 48,
- “is-supported”: true,
- “systeminfo”: “Wismote IoT device”,
- “mfg-name”: “Odins”,
- “documentation”: “http://doc.wismote.odins.com”,
- “model-name”: “iot_broker”,
- “from-device-policy”: {
- “access-lists”: {
- “access-list” [{
- “name”: “mud-55052-v6fr”
- }]
- },
- “mspl-list”:{
- “mspls”: [{
- “name”: “mud-55053-v6fr”
- },{
- “name”: “mud-55054-v6fr”
- }]
- }
- },
- “to-device-policy”: {
- “access-lists”: {
- “access-list”: [{
- “name”: “mud-55052-v6to”
- }]
- },
- “mspl-list”:{
- “mspls”: [{
- “name”: “mud-55054-v6to”
- }]
- }
- }
- },
- “ietf-access-control-list:acls”: {
- “acl”: [{
- “name”: “mud-55052-v6to”,
- “type”: “ipv6-acl-type”,
- “aces”: {
- “ace”: [{
- “name”: “ent0-todev”,
- “matches”: {
- “ietf-mud:mud”: {
- “my-controller”: [null]
- },
- “ipv6”: {
- “protocol”: 17
- },
- “udp”: {
- “source-port”: {
- “operator”: “eq”,
- “port”: 5683
- }
- }
- },
- “actions”: {
- “forwarding”: “accept”
- }
- }]
- }
- },
- {
- “name”: “mud-55052-v6fr”,
- “type”: “ipv6-acl-type”,
- “aces”: {
- “ace”: [{
- “name”: “ent0-frdev”,
- “matches”: {
- “ietf-mud:mud”: {
- “same-manufacturer”: [null]
- },
- “ipv6”: {
- “protocol”: 17
- },
- “udp”: {
- “destination-port”: {
- “operator”: “eq”,
- “port”: 5683
- }
- }
- },
- “actions”: {
- “forwarding”: “accept”
- }
- }]
- }
- }
- ]
- },
- “umu-mspl-list:mspls”: {
- “mspl”: [{
- “name”: “mud-55053-v6fr”,
- “type”: “ipv6-mspl-type”,
- “mspls”: {
- “mspl”: [{
- “name”: “MSPL0”,
- “configuration”: {
- “capability”: “Privacy”,
- “configuration-rules”:[{
- “configuration-rule”: {
- “configuration-rule-action”:{
- “umu-mspl-privacy-action:privacy-action-type”:
- “Data-Privacy”,
- “umu-mspl-privacy-action:privacy-method”:{
- “umu-mspl-abprivacy-method:attributes”:[
- {”umu-mspl-abprivacy-method:attribute”:{
- “umu-mspl-abprivacy-method:key”: “dc”,
- “umu-mspl-abprivacy-method:value”: “es”}
- },
- {”umu-mspl-abprivacy-method:attribute”:{
- “umu-mspl-abprivacy-method:key”: “dc”,
- “umu-mspl-abprivacy-method:value”: “um”}
- },
- {“umu-mspl-abprivacy-method:attribute”:{
- “umu-mspl-abprivacy-method:key”: “o”,
- “umu-mspl-abprivacy-method:value”: “iot”}
- },
- {“umu-mspl-abprivacy-method:attribute”:{
- “umu-mspl-abprivacy-method:key”: “ou”,
- “umu-mspl-abprivacy-method:value”: “dep5”}
- }
- ]
- }
- },
- “configuration-rule-condition”:{
- “umu-mspl-filtering-condition:packet-filter-
- condition”:{“umu-mspl-packet-filter-condition:
- destination-address”:“my-controller”}
- },
- “name”: “Rule0”,
- “priority”: 200
- }
- }]
- }
- }]
- }
- },
- {
- “name”: “mud-55054-v6from”,
- “type”: “ipv6-mspl-type”,
- “mspls”: {
- “mspl”: [{
- “name”: “MSPL0”,
- “configuration”: {
- “capability”: “Protection_confidentiality”,
- “configuration-rules”:[{
- “configuration-rule”: {
- “configuration-rule-action”:{
- “umu-mspl-data-protection-action:technology”:
- “DTLS”,
- “umu-mspl-data-protection-action:technology-
- action-parameters”:[
- {“umu-mspl-data-protection-action:technology-
- parameter”:{“umu-mspl-dtls-technology-parameter:
- remote-endpoint”: “my-controller”}
- }],
- “umu-mspl-data-protection-action:technology-action-
- security-properties”:[
- {
- “umu-mspl-data-protection-action:technology-
- action-security-property”:
- {
- “umu-mspl-confidentiality-technology-action-
- security-property:encryption-algorithm”: “AES”,
- “umu-mspl-confidentiality-technology-action-
- security-property:key-size”: 128,
- “umu-mspl-confidentiality-technology-action-
- security-property:mode”: “CCM”
- }
- }
- ]
- },
- “configuration-rule-condition”:{
- },
- “name”: “Rule0”,
- “priority”: 200
- }
- }]
- }
- }]
- }
- },
- {
- “name”: “mud-55054-v6to”,
- “type”: “ipv6-mspl-type”,
- “mspls”: {
- “mspl”: [{
- “name”: “MSPL0”,
- “configuration”: {
- “capability”: “Protection_confidentiality”,
- “configuration-rules”:[{
- “configuration-rule”: {
- “configuration-rule-action”:{
- “umu-mspl-data-protection-action:technology”:
- “DTLS”,
- “umu-mspl-data-protection-action:technology-
- action-parameters”:[
- {
- “umu-mspl-data-protection-action:technology-
- parameter”:{
- “umu-mspl-dtls-technology-parameter:
- local-endpoint”: “my-controller”
- }
- }],
- “umu-mspl-data-protection-action:technology-
- action-security-properties”:[
- { “umu-mspl-data-protection-action:technology-
- action-security-property”:
- {“umu-mspl-confidentiality-technology-action-
- security-property:encryption-algorithm”: “AES”,
- “umu-mspl-confidentiality-technology-action-
- security-property:key-size”: 128,
- “umu-mspl-confidentiality-technology-action-
- security-property:mode”: “CCM”
- }
- }
- ]
- },
- “configuration-rule-condition”:{
- },
- “name”: “Rule0”,
- “priority”: 200
- }
- }]
- }
- }]
- }
- }
- {
- “name”: “mud-55055-v6fr”,
- “type”: “ipv6-mspl-type”,
- “mspls”: {
- “mspl”: [{
- “name”: “MSPL0”,
- “configuration”: {
- “capability”: “AuthoriseAccess_resurce”,
- “configuration-rules”:[{
- “configuration-rule”: {
- “configuration-rule-action”:{
- “umu-mspl-authorization-action:AuthorizationActionType”: “ALLOW”,
- },
- “configuration-rule-condition”:{
- “umu-mspl-filtering-condition:packet-filter-condition”:{
- “umu-mspl-packet-filter-condition:source-address”:“IoT-device”,
- “umu-mspl-packet-filter-condition:destination-address”:
- “IoT-broker”,
- “umu-mspl-packet-filter-condition:destination-port”: 5684
- },
- “umu-mspl-filtering-condition:aplication-layer-condition”:{
- “umu-mspl-aplication-layer-condition:application-protocol”:
- “CoAPs”,
- “umu-mspl-aplication-layer-condition:method”:“POST”,
- “umu-mspl-aplication-layer-condition:url”:“/tmp”
- }
- },
- “name”: “Rule0”,
- “priority”: 200
- }
- }]
- }
- }]
- }
- }
- ]
- }
- }
- ]
References
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Lear, E.; Romascanu, D.; Droms, R. Manufacturer Usage Description Specification (RFC 8520), 2019. Available online: https://datatracker.ietf.org/doc/rfc8520/ (accessed on 27 March 2020).
- Jeffrey, V.; Rick, K.; Phillip, L.; Sophia, A. NISTIR 8222: Internet of Things (IoT) Trust Concerns, 2018. Available online: https://csrc.nist.gov/publications/detail/white-paper/2018/10/17/iot-trust-concerns/draft (accessed on 27 March 2020).
- Polk, T.; Souppaya, M.; Barker, W.C. Mitigating IoT-Based Automated Distributed Threats, 2017. Available online: https://csrc.nist.gov/publications/detail/white-paper/2017/10/12/mitigating-iot-based-automated-distributed-threats/draft (accessed on 27 March 2020).
- Hamza, A.; Gharakheili, H.H.; Benson, T.A.; Sivaraman, V. Detecting Volumetric Attacks on IoT Devices via SDN-Based Monitoring of MUD Activity. Symposium on SDN Research (SOSR). In Proceedings of the 2019 ACM Symposium on SDN Research, San Jose, CA, USA, 3–4 April 2019; pp. 36–48. [Google Scholar]
- Ranganathan, M. Soft MUD: Implementing Manufacturer Usage Descriptions on OpenFlow SDN Switches. In Proceedings of the International Conference on Networks (ICN), Valencia, Spain, 25–29 March 2019; pp. 49–54. [Google Scholar]
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow–enabling innovation in campus networks. Acm Sigcomm Comput. Commun. Rev. 2008, 38, 69. [Google Scholar] [CrossRef]
- Matheu, S.N.; Hernandez-Ramos, J.L.; Perez, S.; Skarmeta, A.F. Extending MUD profiles through an Automated IoT Security Testing Methodology. IEEE Access 2019, 7, 149444–149463. [Google Scholar] [CrossRef]
- Zarca, A.M.; Bernabe, J.B.; Trapero, R.; Rivera, D.; Villalobos, J.; Skarmeta, A.; Bianchi, S.; Zafeiropoulos, A.; Gouvas, P. Security Management Architecture for NFV/SDN-aware IoT Systems. IEEE Internet Things J. 2019, 6, 8005–8020. [Google Scholar] [CrossRef]
- Matheu García, S.N.; Molina Zarca, A.; Hernández-Ramos, J.L.; Bernabé, J.B.; Gómez, A.S. Enforcing Behavioral Profiles through Software-Defined Networks in the Industrial Internet of Things. Appl. Sci. 2019, 9, 4576. [Google Scholar] [CrossRef] [Green Version]
- Garcia-Carrillo, D.; Marin-Lopez, R.; Kandasamy, A.; Pelov, A. A CoAP-Based Network Access Authentication Service for Low-Power Wide Area Networks: LO-CoAP-EAP. Sensors 2017, 17, 2646. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext Policy Attribute Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef] [Green Version]
- Erdtman, S.; Wahlstroem, E.; Tschofenig, H.; Jones, M. CBOR Web Token (CWT), 2018. Available online: https://tools.ietf.org/html/rfc8392 (accessed on 27 March 2020).
- OASIS. eXtensible Access Control Markup Language Version 3.0, 2013. Available online: http://docs.oasis-open.org/xacml/3.0/xacml-3.0-core-spec-os-en.html (accessed on 27 March 2020).
- Garcia-Carrillo, D.; Marin-Lopez, R. Lightweight CoAP-Based Bootstrapping Service for the Internet of Things. Sensors 2016, 16, 358. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Habibi Gharakheili, H.; Sivanathan, A.; Hamza, A.; Sivaraman, V. Network Level Security for the Internet of Things: Opportunities and Challenges. Computer 2019, 52, 58–62. [Google Scholar] [CrossRef]
- Ellesson, E.; Strassner, J.; Moore, B.; Westerinen, A. Policy Core Information Model – Version 1 Specification, 2001. Available online: https://tools.ietf.org/html/rfc3060 (accessed on 27 March 2020).
- Molloy, I.; Huang, H. Standardizing IoT Network Security Policy Enforcement. In Proceedings of the Workshop on Decentralized IoT Security and Standards, San Diego, CA, USA, 18 February 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Barrera, D.; Molloy, I.; Huang, H. IDIoT - Securing the Internet of Things like it’s 1994. arXiv 2017, arXiv:1712.03623. [Google Scholar]
- Jethanandani, M.; Blair, D.; Huang, L.; Agarwal, S. YANG Data Model for Network Access Control Lists (RFC8519), 2019. Available online: https://tools.ietf.org/html/rfc8519 (accessed on 27 March 2020).
- Bray, T. The JavaScript Object Notation (JSON) Data Interchange Format (RFC8259), 2017. Available online: https://tools.ietf.org/html/rfc8259 (accessed on 27 March 2020).
- Hamza, A.; Gharakheili, H.H.; Sivaraman, V. Combining MUD Policies with SDN for IoT Intrusion Detection. In Proceedings of the 2018 Workshop on IoT Security and Privacy, New York, NY, USA, 20 August 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Al-Shaboti, M.; Welch, I.; Chen, A.; Mahmood, M.A. Towards Secure Smart Home IoT—Manufacturer and User Network Access Control Framework. In Proceedings of the IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 892–899. [Google Scholar] [CrossRef]
- Hernandez-Ramos, J.L.; Pawlowski, M.P.; Jara, A.J.; Skarmeta, A.F.; Ladid, L. Toward a Lightweight Authentication and Authorization Framework for Smart Objects. IEEE J. Sel. Areas Commun. 2015, 33, 690–702. [Google Scholar] [CrossRef] [Green Version]
- Hernandez-Ramos, J.L.; Moreno, M.V.; Bernabe, J.B.; Carrillo, D.G.; Skarmeta, A.F. SAFIR - Secure access framework for IoT-enabled services on smart buildings. J. Comput. Syst. Sci. 2015, 81, 1452–1463. [Google Scholar] [CrossRef]
- Hardt, D. The OAuth 2.0 Authorization Framework (RFC 6749), 2012. Available online: https://tools.ietf.org/html/rfc6749 (accessed on 27 March 2020).
- Bormann, C.; Hoffman, P. Concise Binary Object Representation (CBOR) (RFC7049), 2013. Available online: https://tools.ietf.org/html/rfc7049 (accessed on 27 March 2020).
- Carsten Bormann. An Authorization Information Format (AIF) for ACE, 2019. Available online: https://tools.ietf.org/html/draft-bormann-core-ace-aif-01 (accessed on 27 March 2020).
- Sarkar, C.; N, A.U.N.S.; Prasad, R.V.; Rahim, A.; Neisse, R.; Baldini, G. DIAT—A Scalable Distributed Architecture for IoT. IEEE Internet Things J. 2015, 2, 230–239. [Google Scholar] [CrossRef]
- Neisse, R.; Steri, G.; Fovino, I.N.; Baldini, G. SecKit—A Model-based Security Toolkit for the Internet of Things. Comput. Secur. 2015, 54, 60–76. [Google Scholar] [CrossRef]
- OASIS. Message Queue Telemetry Transport (MQTT) Version 5.0, 2019. Available online: https://docs.oasis-open.org/mqtt/mqtt/v5.0/mqtt-v5.0.html (accessed on 27 March 2020).
- Phung, P.H.; Truong, H.; Yasoju, D.T. P4SINC—An Execution Policy Framework for IoT Services in the Edge. In Proceedings of the 2017 IEEE International Congress on Internet of Things (ICIOT), Honolulu, HI, USA, 25–30 June 2017; pp. 137–142. [Google Scholar] [CrossRef]
- Uszok, A.; Bradshaw, J.; Johnson, M.; Jeffers, R.; Tate, A.; Dalton, J.; Aitken, S. KAoS policy management for semantic Web services. IEEE Intell. Syst. 2004, 19, 32–41. [Google Scholar] [CrossRef]
- Kagal, L. Rei—A Policy Language for the Me-Centric Project; Technical Report; HP Labs: Palo Alto, CA, USA, 15 September 2002. [Google Scholar]
- Valenza, F.; Lioy, A. User-oriented Network Security Policy Specification. J. Internet Serv. Inf. Secur. 2018, 8, 33–47. [Google Scholar]
- Zhang, Y.; He, D.; Choo, K.K.R. BaDS—Blockchain-Based Architecture for Data Sharing with ABS and CP-ABE in IoT. Wirel. Commun. Mob. Comput. 2018, 2018, 2783658. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetrò, A.; De Martin, J.C. Blockchain for the Internet of Things: A systematic literature review. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Bernal Bernabe, J.; Canovas, J.L.; Hernandez-Ramos, J.L.; Torres Moreno, R.; Skarmeta, A. Privacy-Preserving Solutions for Blockchain: Review and Challenges. IEEE Access 2019, 7, 164908–164940. [Google Scholar] [CrossRef]
- Rescorla, E.; Modadugu, N. Datagram Transport Layer Security Version 1.2, 2012. Available online: https://tools.ietf.org/html/rfc6347 (accessed on 27 March 2020).
- Pérez, S.; Hernández-Ramos, J.L.; Matheu-García, S.N.; Rotondi, D.; Skarmeta, A.F.; Straniero, L.; Pedone, D. A Lightweight and Flexible Encryption Scheme to Protect Sensitive Data in Smart Building Scenarios. IEEE Access 2018, 6, 11738–11750. [Google Scholar] [CrossRef]
- Garcia-Morchon, O.; Kumar, S.S.; Sethi, M. Internet of Things Security: State of the Art and Challenges (RFC 8576), 2019. Available online: https://tools.ietf.org/html/rfc8576 (accessed on 27 March 2020).
- Vollbrecht, J.R.; Aboba, B.; Blunk, L.J.; Levkowetz, H.; Carlson, J. Extensible Authentication Protocol (RFC 3748), 2004. Available online: https://tools.ietf.org/html/rfc3748 (accessed on 27 March 2020).
- Vollbrecht, J.; Holdrege, M.; Laat, C.; Calhoun, P.; Gommans, L.; Farrell, S.; Bruijn, B.D.; Gross, G.; Spence, D. AAA Authorization Framework (RFC 2904), 2000. Available online: https://tools.ietf.org/html/rfc2904 (accessed on 27 March 2020).
- Ohba, Y.; Patil, B.; Forsberg, D.; Tschofenig, H.; Yegin, A.E. Protocol for Carrying Authentication for Network Access (RFC 5191), 2008. Available online: https://tools.ietf.org/html/rfc5191 (accessed on 27 March 2020).
- Aboba, B.; Calhoun, P.R. RADIUS (Remote Authentication Dial In User Service) Support For Extensible Authentication Protocol (EAP), 2003. Available online: https://tools.ietf.org/html/rfc3579 (accessed on 27 March 2020).
- Bersani, F.; Tschofenig, H. The EAP-PSK Protocol: A Pre-Shared Key Extensible Authentication Protocol Method (RFC 4764), 2007. Available online: https://tools.ietf.org/html/rfc4764 (accessed on 27 March 2020).
- Enns, R.; Bjorklund, M.; Schoenwaelder, J. Network Configuration Protocol (RFC 6241), 2011. Available online: https://tools.ietf.org/html/rfc6241 (accessed on 27 March 2020).
- Hernandez-Ramos, J.L.; Jara, A.J.; Marin, L.; Gomez, A.F.S. DCapBAC - embedding authorization logic into smart things through ECC optimizations. Int. J. Comput. Math. 2016, 93, 345–366. [Google Scholar] [CrossRef]
- Masinter, L.; Berners-Lee, T.; Fielding, R.T. Uniform Resource Identifier (URI): Generic Syntax, 2005. Available online: https://tools.ietf.org/html/rfc3986 (accessed on 27 March 2020).
- Schaad, J. CBOR Object Signing and Encryption (COSE) (RFC8152), 2017. Available online: https://tools.ietf.org/html/rfc8152 (accessed on 27 March 2020). [CrossRef] [Green Version]
- Hyperledger. Hyperledger Blockchain Performance Metrics, 2018. Available online: https://cn.hyperledger.org/resources/publications/blockchain-performance-metrics (accessed on 27 March 2020).
- Jiang, L.; Chang, X.; Liu, Y.; Mišić, J.; Mišić, V.B. Performance analysis of Hyperledger Fabric platform: A hierarchical model approach. Peer -Peer Netw. Appl. 2020, 1–12. [Google Scholar] [CrossRef]

| Policy Type | Translation | Enforcement |
|---|---|---|
| Network access control | ONOS | SDNs |
| Channel protection | DTLS configuration | Proxy configuration |
| Data privacy | CP-ABE policies | Proxy configuration and CP-ABE encryption |
| Authorization over resources | XACML policies | XACML policy evaluation and CWT-AIF tokens |
| Name | Key | Value Type |
|---|---|---|
| iss | 1 | text string |
| sub | 2 | text string |
| aud | 3 | text string |
| exp | 4 | integer or floating-point number |
| nbf | 5 | integer or floating-point number |
| iat | 6 | integer or floating-point number |
| cti | 7 | byte string |
| aif | 8 | AIF structure |
| Component | Hardware | Role | Software |
|---|---|---|---|
| Smart Object | Zolertia Z1 with 92 kB of nominal ROM and 8 kB of RAM | EAP peer | Cooja (Contiki OS 2.7) |
| CoAP Client | cantcoap | ||
| CoAP Server | cantcoap | ||
| Authentication Agent | Linux Ubuntu VM with 2 GB of RAM, 30 GB HDD and a processor Intel(R) Core(TM) i7-8550U at 1.9 GHz, using 1 core | EAP Authenticator | FreeRadius 2.0.2. |
| CoAP Client | cantcoap | ||
| CoAP Server | cantcoap | ||
| AAA Server | Linux Ubuntu VM with 2 GB of RAM, 30 GB HDD and a processor Intel(R) Core(TM) i7-8550U at 1.9 GHz, using 1 core | AAA Server | FreeRadius 2.0.2. |
| EAP Server | C application | ||
| MUD Manager | Intel Core Processor (Haswell) at 1.5 GHz using 2vCores, 2 GB of RAM and 15 GB of HDD Intel(R) Core(TM) i7-2600 CPU at 3.4 GHz, using 3 vCores, 3.5 GB of RAM and 30 GB of HDD | IoT Controller | Python application |
| Security Orchestrator | Django 2.2.2 and Falcon 2.0 | ||
| SDN Controller | ONOS | ||
| Policy Interpreter | Django 2.2.2 and Falcon 2.0 | ||
| MUD Server | Linux Ubuntu VM with 2 GB of RAM, 30 GB HDD and a processor Intel(R) Core(TM) i7-8550U at 1.9 GHz, using 1 core | MUD Server | Apache 2.4.39 |
| Border router | Zolertia Z1 with 92 kB of nominal ROM and 8 kB of RAM | Border router | Contiki OS 2.7 |
| Blockchain Security Handler | Windows 10 Pro with processor Intel(R) Core(TM) I7-7700K at 4.2 GHz, 24GB of RAM DDR4 and SSD M.2 | Authentication Module | Jersey 1.19.1, Apache Tomcat |
| Proxy Module | Jersey 1.19.1, Apache Tomcat, CP-ABE | ||
| PDP | Windows 10 Pro with processor Intel(R) Core(TM) I7-8550U at 1.8 GHz, 8GB of RAM DDR4 and 500 GB of SSD M.2 | PDP | Apache Tomcat |
| Credential Manager | Windows 10 Pro with processor Intel(R) Core(TM) I7-8550U at 1.8 GHz, 8GB of RAM DDR4 and 500 GB of SSD M.2 | Credential Manager | Java Application, cbor-2.4.1, Californium 2.1.0 |
| Blockchain | Windows 10 Pro with processor Intel(R) Core(TM) I7-7700K at 4.2 GHz, 24GB of RAM DDR4 and SSD M.2 | Blockchain | Hyperledger Fabric 1.2, Hyperledger Composer 0.20.7 |
| IPFS | Windows 10 Pro with processor Intel(R) Core(TM) I7-7700K at 4.2 GHz, 24GB of RAM DDR4 and SSD M.2 | IPFS | IPFS version 0.4.19 |
| Publishing Mechanism | Mean Time (ms) | Confidence Interval |
|---|---|---|
| IPFS | 9.5 | 4.52 |
| Blockchain | 352.75 | 30.24 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Matheu, S.N.; Robles Enciso, A.; Molina Zarca, A.; Garcia-Carrillo, D.; Hernández-Ramos, J.L.; Bernal Bernabe, J.; Skarmeta, A.F. Security Architecture for Defining and Enforcing Security Profiles in DLT/SDN-Based IoT Systems. Sensors 2020, 20, 1882. https://doi.org/10.3390/s20071882
Matheu SN, Robles Enciso A, Molina Zarca A, Garcia-Carrillo D, Hernández-Ramos JL, Bernal Bernabe J, Skarmeta AF. Security Architecture for Defining and Enforcing Security Profiles in DLT/SDN-Based IoT Systems. Sensors. 2020; 20(7):1882. https://doi.org/10.3390/s20071882
Chicago/Turabian StyleMatheu, Sara N., Alberto Robles Enciso, Alejandro Molina Zarca, Dan Garcia-Carrillo, José Luis Hernández-Ramos, Jorge Bernal Bernabe, and Antonio F. Skarmeta. 2020. "Security Architecture for Defining and Enforcing Security Profiles in DLT/SDN-Based IoT Systems" Sensors 20, no. 7: 1882. https://doi.org/10.3390/s20071882
APA StyleMatheu, S. N., Robles Enciso, A., Molina Zarca, A., Garcia-Carrillo, D., Hernández-Ramos, J. L., Bernal Bernabe, J., & Skarmeta, A. F. (2020). Security Architecture for Defining and Enforcing Security Profiles in DLT/SDN-Based IoT Systems. Sensors, 20(7), 1882. https://doi.org/10.3390/s20071882











