A Quality of Service-Aware Secured Communication Scheme for Internet of Things-Based Networks
Abstract
:1. Introduction
- We propose two algorithms; the first, a lightweight protocol for Sybil nodes detection, that is, a signalprint-based (A signalprint is created from the received signal strength information of a node to detect misbehaving nodes.) Sybil attack detection. This protocol has devised two policies for detection of Sybil nodes. The Sybil nodes are detected by high-power and mobile nodes are reported to the genuine nodes in the IoT-based network; as a result, genuine nodes do not entertain Sybil nodes.
- The second proposed algorithm is an adaptive algorithm for determining the optimal size of the CW and allocates the bandwidth to the nodes based on the current network status. This algorithm helps in maintaining a balance between per-flow fairness and fair allocation of bandwidth.
- For the QoS provisioning, the proposed QoS-IoT scheme uses a mechanism where CW size is determined based on the ratio of actual to fair bandwidth allocation. Different CW size is assigned to different flows for fairness, that is, smaller CW size to is assigned to flows having more substantial queue length.
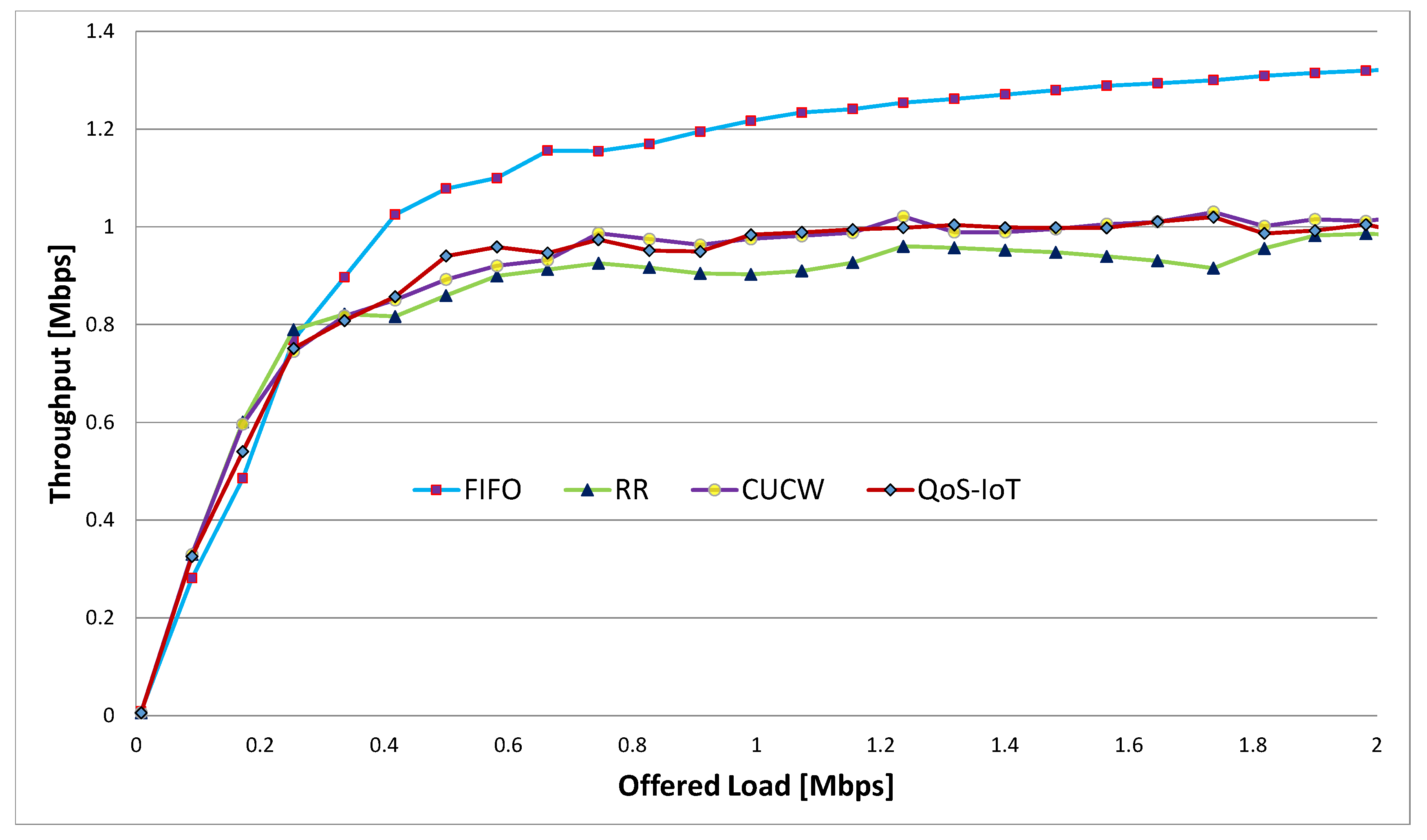
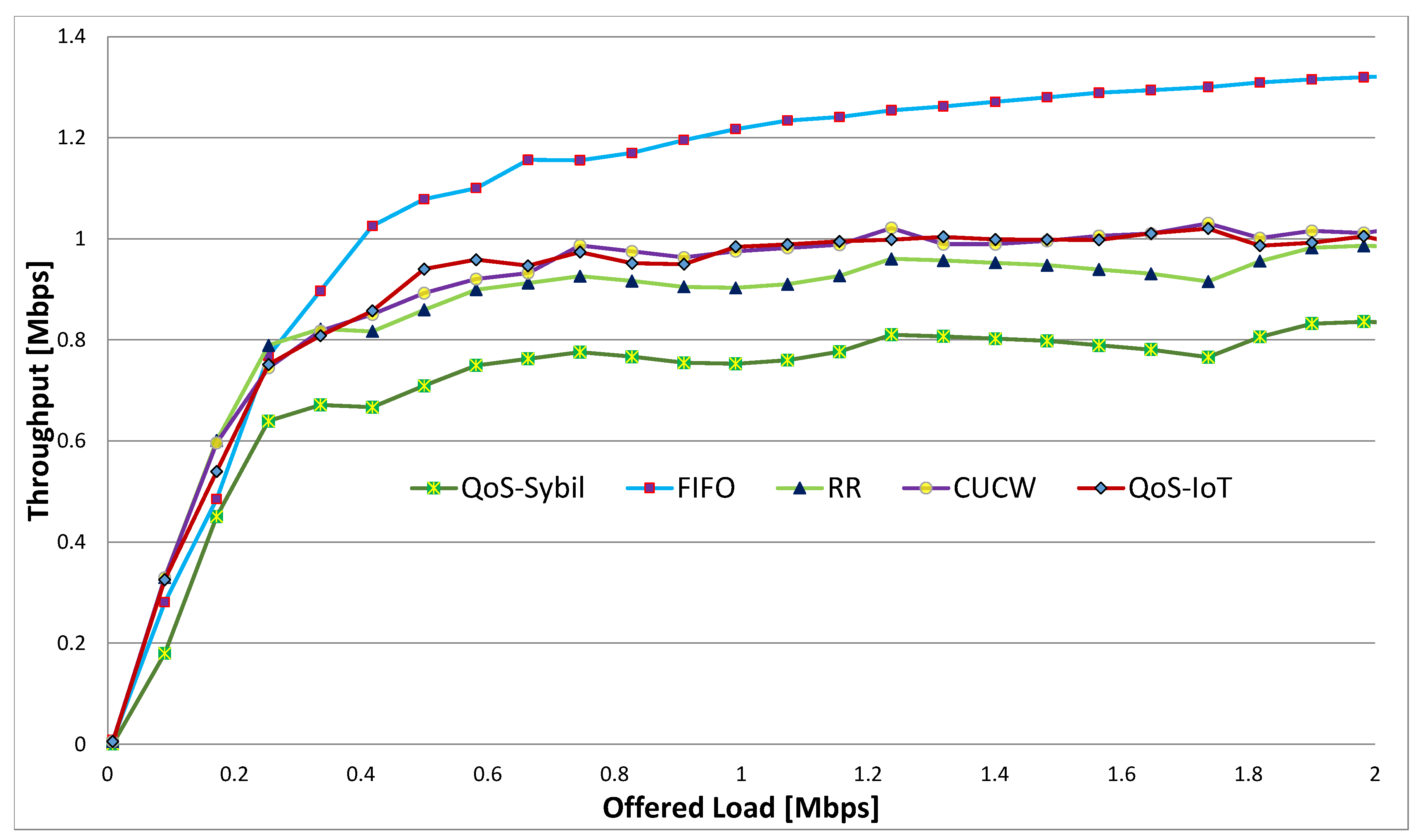
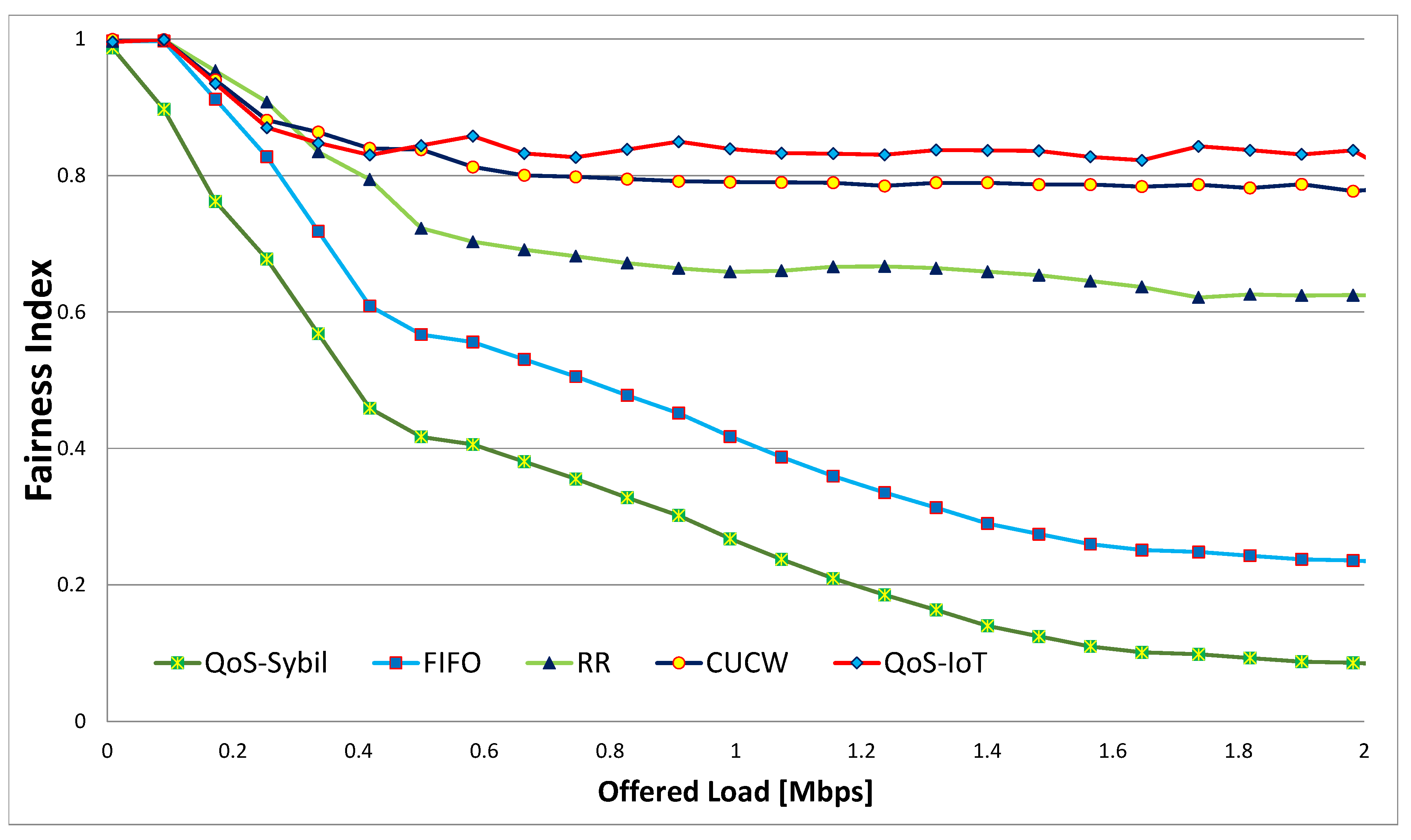
- Finally, we perform extensive simulations to prove the efficacy of the QoS-IoT in terms of fairness, throughput and link utilization. The simulation results are compared with the existing schemes.
2. Related Work
3. System Model
4. Quality of Service Degradation
4.1. Problems at the MAC Layer
4.2. Problems at the Link Layer
4.3. Malicious Node and Trust Model
5. QoS-Aware Secured Communication Scheme
5.1. Security Attack Detection and Prevention Model
5.2. Sybil Node Detection
5.3. QoS Aware Communication
| Algorithm 1 Sybil Node Detection | ||
| Initialization: K = ⌀, i = 0, = 1, = 1, = 1, = 1. | ||
| procedure | ||
| 2: | K ← K | |
| 4: | while do | ▹ is the number of nodes. |
| 6: | if K K then | |
| 8: | K = K | |
| 10: | i = i + 1 | |
| 12: | else | |
| 14: | K = K | |
| 16: | end if | |
| 18: | end while | |
| 20: | return K | |
| 22: | broadcast K to all nodes in the network. | ▹ After this broadcast, Node 0 will continue the following policy |
| 24: | (K, R) ← | |
| 26: | while R K do | |
| 28: | if R(SN) ≠ RSSI(R(SN)) then | |
| 30: | Exclude R(SN) | |
| 32: | else | |
| 34: | RR← R(SN) | |
| 36: | end if | |
| 38: | if R(GN) ≠ RSSI(R(GN)) then | |
| 40: | Exclude R(GN) | |
| 42: | = + 1 | |
| 44: | else | |
| 46: | RR← R(GN) | |
| 48: | = + 1 | |
| 50: | end if | |
| 52: | end while | |
| 54: | = 1 | |
| 56: | bool = true | |
| 58: | while bool do | |
| 60: | if SizeOf(RR(GN)) ≥ SizeOf(RR(GN) then | |
| 62: | R = RR(GN) | |
| 64: | = + 1 | |
| 66: | else | |
| 68: | R = RR(GN) | |
| 70: | bool = false | |
| 72: | end if | |
| 74: | end while | |
| 76: | return R | |
| 78: | broadcast R to all nodes in S. | |
| 80: | end procedure | |
| Algorithm 2 Optimal Contention Window Selction | ||
| Initialization: 𝚥 = 0, 𝚤 = 0, T = 0. | ||
| procedure | ||
| 2: | count 𝚤▹𝚤 is a flow sensed at the physical layer by a node, which is out of transmission range but within the sensing range | |
| 4: | count 𝚥 | ▹ 𝚥 is a flow within the transmission range |
| 6: | for each TS duration do | ▹ MAC layer is divided into Time Slots (TS) of fixed intervals |
| 8: | 𝚥’s duration = 10% × 𝚥’s time + 90% × T duration | ▹ time taken by 𝚥 flow |
| 10: | = 0 | |
| 12: | for each packet p do | |
| 14: | if p is CTS then | |
| 16: | T = T + T | |
| 18: | elseif p is ACK then | |
| 20: | T = T + T | |
| 22: | end if | |
| 24: | end for | |
| 26: | end for | |
| 28: | ▹ is real allocation of bandwidth | |
| 30: | = | ▹ is the fair allocation of bandwidth to a node |
| 32: | CW = CW | |
| 34: | CW = | ▹ if packet is marked using Equation (6) and > 1 is a delay factor. |
| 36: | CW = CW | ▹ if packet is not marked using Equation (6) |
| 38: | end procedure | |
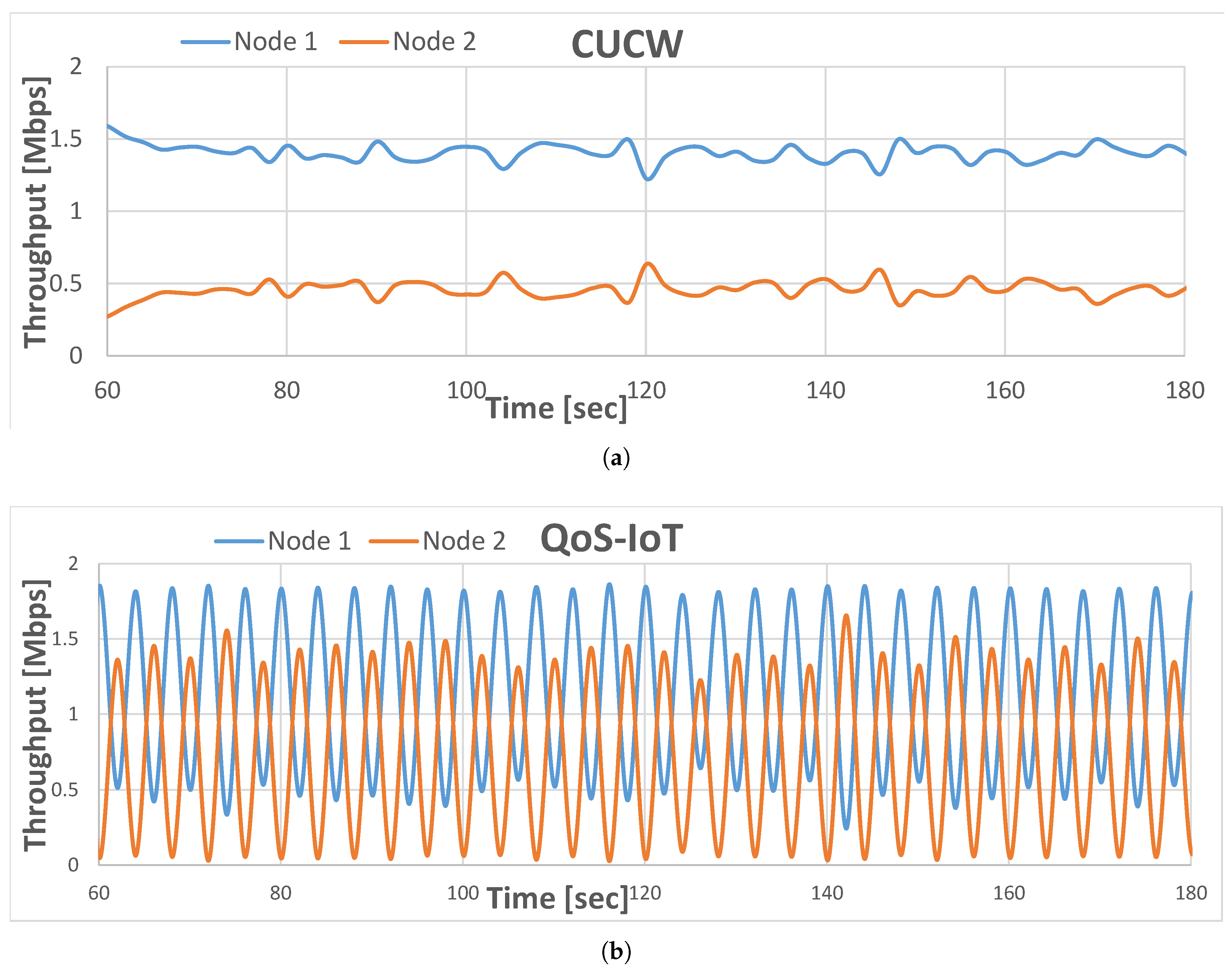
6. Results and Discussion
6.1. Fairness Index
6.2. Throughput
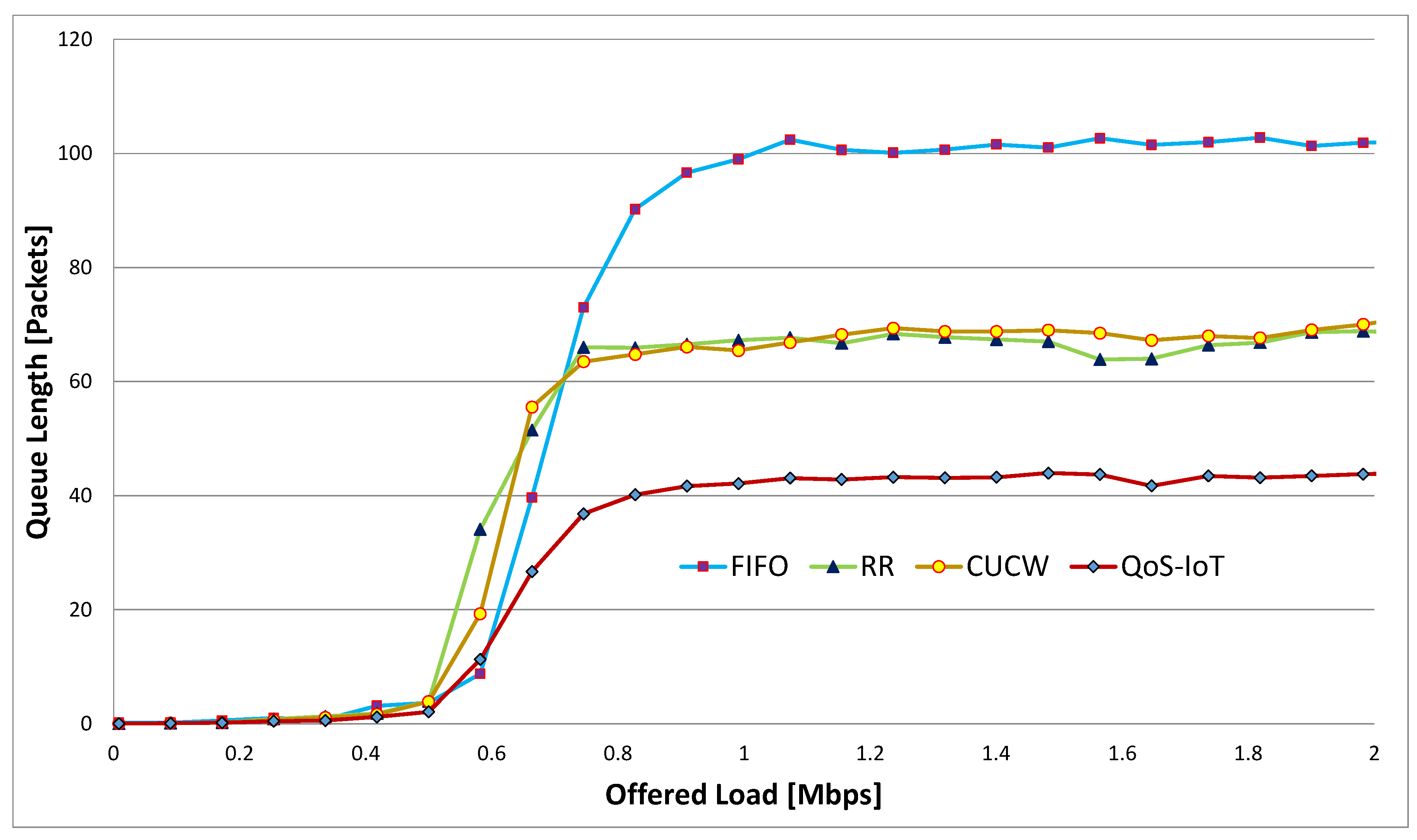
6.3. Average Queue Length
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| QoS | Quality of Service |
| CW | Contention Window |
| MAC | Medium Access Control |
| NS-2 | Network Simulator version 2 |
| DCF | Distributed Coordination Function |
| BI | Back-off Interval |
| DIFS | Distributed Inter-frame Space |
| DoS | Denial of Serves |
| MANETs | Mobile Ad hoc NETworks |
| VANETs | Vehicular Ad hoc NETworks |
| WSNs | Wireless Sensor Networks |
| SN | Sybil Node |
| GN | Genuine Node |
| FIFO | First In First Out |
| RR | Round Robbin |
| RFID | Radio Frequency Identification |
References
- Morino, Y.; Hiraguri, T.; Yoshino, H.; Nishimori, K.; Tachibana, A.; Matsuda, T. A novel contention window control scheme based on a Markov chain model in dense WLAN environment. In Proceedings of the 2015 3rd International Conference on Artificial Intelligence, Modelling and Simulation (AIMS), Kota Kinabalu, Malaysia, 2–4 December 2015; pp. 417–421. [Google Scholar]
- Liu, Q.; Leung, K.C.; Li, V.O.; Zhao, Z.; Yang, G.; Cui, L. Fairness and high-throughput scheduling for multihop wireless ad hoc networks. Ad Hoc Netw. 2016, 52, 195–206. [Google Scholar] [CrossRef]
- Stai, E.; Papavassiliou, S.; Baras, J.S. Performance-aware cross-layer design in wireless multihop networks via a weighted backpressure approach. IEEE/ACM Trans. Netw. 2016, 24, 245–258. [Google Scholar] [CrossRef]
- Wang, Q.; Jaffrès-Runser, K.; Scharbarg, J.L.; Fraboul, C.; Sun, Y.; Li, J.; Li, Z. A thorough analysis of the performance of delay distribution models for IEEE 802.11 DCF. Ad Hoc Netw. 2015, 24, 21–33. [Google Scholar] [CrossRef] [Green Version]
- IEEE 802 LAN/MAN Standards Committee. IEEE 802.11-Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications; IEEE: Piscataway, NJ, USA, 2007. [Google Scholar]
- Tuan, N.M.; Watabe, K.; Giang, P.T.; Nakagawa, K. Improving Fairness in Wireless Ad Hoc Networks by Channel Access Sensing at Link Layer and Packet Rate Control. IEICE Trans. Commun. 2017, 100, 1818–1826. [Google Scholar] [CrossRef]
- Giang, P.T.; Nakagawa, K. Cross-Layer Scheme to Control Contention Window for Per-Flow in Asymmetric Multi-Hop Networks. IEICE Trans. Commun. 2010, 93, 2326–2335. [Google Scholar] [CrossRef]
- Giang, P.T.; Nakagawa, K. Cooperation between channel access control and TCP rate adaptation in multi-hop ad hoc networks. IEICE Trans. Commun. 2015, 98, 79–87. [Google Scholar] [CrossRef]
- Jabeen, Q.; Khan, F.; Khan, S.; Jan, M.A. Performance improvement in multihop wireless mobile adhoc networks. J. Appl. Environ. Biol. Sci. (JAEBS) 2016, 6, 82–92. [Google Scholar]
- Khan, F. Fairness and throughput improvement in multihop wireless ad hoc networks. In Proceedings of the 2014 IEEE 27th Canadian Conference on Electrical and Computer Engineering (CCECE), Toronto, ON, Canada, 4–7 May 2014; pp. 1–6. [Google Scholar]
- Khan, F.; Kamal, S.A.; Arif, F. Fairness Improvement in ong chain multihop wireless ad hoc networks. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; pp. 556–561. [Google Scholar]
- Khan, F.; Rehman, A.U.; Usman, M.; Tan, Z.; Puthal, D. Performance of Cognitive Radio Sensor Networks Using Hybrid Automatic Repeat ReQuest: Stop-and-Wait. Springer Mob. Netw. Appl. 2018, 23, 479–488. [Google Scholar] [CrossRef] [Green Version]
- Zheng, J.; Li, B.; Tian, C.; Foerster, K.T.; Schmid, S.; Chen, G.; Wu, J.; Li, R. Congestion-free rerouting of multiple flows in timed sdns. IEEE J. Sel. Areas Commun. 2019, 37, 968–981. [Google Scholar] [CrossRef]
- Begin, T.; Baynat, B.; Lassous, I.G.; Abreu, T. Performance analysis of multi-hop flows in IEEE 802.11 networks: A flexible and accurate modeling framework. Perform. Eval. 2016, 96, 12–32. [Google Scholar] [CrossRef] [Green Version]
- Brogi, A.; Forti, S. QoS-aware deployment of IoT applications through the fog. IEEE Int. Things J. 2017, 4, 1185–1192. [Google Scholar] [CrossRef]
- Khan, F.; Rehman, A.U.; Zheng, J.; Jan, M.A.; Alam, M. Mobile crowdsensing: A survey on privacy-preservation, task management, assignment models, and incentives mechanisms. Future Gener. Comput. Syst. 2019, 100, 456–472. [Google Scholar] [CrossRef]
- Evangelista, D.; Mezghani, F.; Nogueira, M.; Santos, A. Evaluation of Sybil attack detection approaches in the Internet of Things content dissemination. In Proceedings of the 2016 Wireless Days (WD), Toulouse, France, 23–25 March 2016; pp. 1–6. [Google Scholar]
- Jan, M.A.; Nanda, P.; He, X.; Liu, R.P. A Sybil attack detection scheme for a forest wildfire monitoring application. Future Gener. Comput. Syst. 2018, 80, 613–626. [Google Scholar] [CrossRef] [Green Version]
- Yao, Y.; Xiao, B.; Wu, G.; Liu, X.; Yu, Z.; Zhang, K.; Zhou, X. Multi-channel based Sybil attack detection in vehicular ad hoc networks using RSSI. IEEE Trans. Mob. Comput. 2018, 18, 362–375. [Google Scholar] [CrossRef]
- Jamshidi, M.; Darwesh, A.M.; Lorenc, A.; Ranjbari, M.; Meybodi, M.R. A Precise Algorithm for Detecting Malicious Sybil Nodes in Mobile Wireless Sensor Networks. IEIE Trans. Smart Process. Comput. 2018, 7, 457–466. [Google Scholar] [CrossRef]
- Jamshidi, M.; Zangeneh, E.; Esnaashari, M.; Darwesh, A.M.; Meybodi, M.R. A Novel Model of Sybil Attack in Cluster-Based Wireless Sensor Networks and Propose a Distributed Algorithm to Defend It. Wirel. Pers. Commun. 2019, 105, 145–173. [Google Scholar] [CrossRef]
- Almas Shehni, R.; Faez, K.; Eshghi, F.; Kelarestaghi, M. A new lightweight watchdog-based algorithm for detecting Sybil nodes in mobile WSNs. Future Internet 2018, 10, 1. [Google Scholar] [CrossRef]
- Mishra, A.K.; Tripathy, A.K.; Puthal, D.; Yang, L.T. Analytical model for sybil attack phases in internet of things. IEEE Internet Things J. 2018, 6, 379–387. [Google Scholar] [CrossRef]
- Dong, W.; Liu, X. Robust and secure time-synchronization against sybil attacks for sensor networks. IEEE Trans. Ind. Inf. 2015, 11, 1482–1491. [Google Scholar] [CrossRef]
- Ning, H.; Liu, H.; Yang, L.T. Aggregated-proof based hierarchical authentication scheme for the internet of things. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 657–667. [Google Scholar] [CrossRef]
- Alsaedi, N.; Hashim, F.; Sali, A.; Rokhani, F.Z. Detecting sybil attacks in clustered wireless sensor networks based on energy trust system (ETS). Comput. Commun. 2017, 110, 75–82. [Google Scholar] [CrossRef]
- Liu, S.; Fu, L.; Xie, W. Hidden-node Problem in Full-duplex Enabled CSMA Networks. IEEE Trans. Mobile Comput. 2019. [Google Scholar] [CrossRef]
- Weyulu, E.; Hanada, M.; Kanemitsu, H.; Park, E.C.; Kim, M.W. Cross-Layer Design for Exposed Node Reduction in Ad Hoc WLANs. IEICE Trans. Commun. 2018, 101, 1575–1588. [Google Scholar] [CrossRef]
- Sarkar, S.K.; Basavaraju, T.G.; Puttamadappa, C. Ad Hoc Mobile Wireless Networks: Principles, Protocols, and Applications; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Ouni, S.; Boulila, N.; Zafar, B.A. Enhanced EDCA with Deterministic Transmission Collision Resolution for Real-Time Communication in Vehicular Ad Hoc Networks. Wirel. Pers. Commun. 2018, 98, 311–335. [Google Scholar] [CrossRef]
- NS-2. The Network Simluator Version 2. Available online: http://www.isi.edu/nsnam/ns/ (accessed on 7 April 2019).
- Jain, R.K.; Chiu, D.M.W.; Hawe, W.R. A quantitative measure of fairness and discrimination. In Eastern Research Laboratory; Digital Equipment Corporation: Hudson, MA, USA, 1984. [Google Scholar]



| Parameters | Values |
|---|---|
| Channel data rate | 2 [Mbps] |
| Antenna type | Omni direction |
| Radio Propagation | Two-ray ground |
| Transmission range | 450 [m] |
| MAC protocol | IEEE802.11b |
| Routing protocol | AODV |
| Connection type | UDP/CBR |
| Maximum Queue length | 100 [packet] |
| Distance between stations | 300 [m] |
| Number of nodes | random |
| Packet size | 1024 [Byte] |
| 2 | |
| Simulation time | 1000 [s] |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, F.; Rehman, A.u.; Yahya, A.; Jan, M.A.; Chuma, J.; Tan, Z.; Hussain, K. A Quality of Service-Aware Secured Communication Scheme for Internet of Things-Based Networks. Sensors 2019, 19, 4321. https://doi.org/10.3390/s19194321
Khan F, Rehman Au, Yahya A, Jan MA, Chuma J, Tan Z, Hussain K. A Quality of Service-Aware Secured Communication Scheme for Internet of Things-Based Networks. Sensors. 2019; 19(19):4321. https://doi.org/10.3390/s19194321
Chicago/Turabian StyleKhan, Fazlullah, Ateeq ur Rehman, Abid Yahya, Mian Ahmad Jan, Joseph Chuma, Zhiyuan Tan, and Khalid Hussain. 2019. "A Quality of Service-Aware Secured Communication Scheme for Internet of Things-Based Networks" Sensors 19, no. 19: 4321. https://doi.org/10.3390/s19194321
APA StyleKhan, F., Rehman, A. u., Yahya, A., Jan, M. A., Chuma, J., Tan, Z., & Hussain, K. (2019). A Quality of Service-Aware Secured Communication Scheme for Internet of Things-Based Networks. Sensors, 19(19), 4321. https://doi.org/10.3390/s19194321







