Beyond the Limits of Shannon’s Information in Quantum Key Distribution
Abstract
1. Introduction
2. Communication Model
2.1. Quantum Communication
- The states are grouped by non-orthogonal pairs or , where .
- A non-orthogonal pair is measured with the same quantum basis X or Z. Both measurements yield the same result half of the times, i.e., if measuring with X (or Z) gives i, or measuring with X (or Z) gives i or , in both cases. We call those cases double matching detection event. Then, non-compatible measurements never occur.
- It implies that the bit encoded in the X or Z basis is transmitted from Alice to Bob. This communication model defines two communication channels, channel X and channel Z, because there are two bits enclosed in a non-orthogonal quantum pair: one bit over channel X and other bit in channel Z. Bob just chooses which channel he wants to use. Provided a double matching detection event is generated, both measurements are equally useful.
2.2. Example of Error Correction
2.3. Auxiliary Frames
- To achieve reconciliation in Shannon’s model, the first step is to ensure that auxiliary zero bits are error-free. However, Shannon’s 2 × 1 frames does not allow to identify errors in two consecutive zero bits (at least in one round iteration) as indicated by the following relations:In addition, when using 2 × 1 frames, there is a unique possible matching result (MR), that is written below; therefore, no secret information can be derived from MRs in Shannon’s model.
- By contrast, using 2 × 2 frames, errors in the auxiliary frames can be easily identified. Here, we list the error-free zero frames:which can be compared, for illustrative purposes, to the erroneous cases:
- Ambiguous SS are produced in regular frames. For example, to the left, we indicate that Alice sends the frame to Bob, who measures it using MR = 11. However, when applying the Z measurement basis, the photo-detector yields an error reporting instead ; so, we have:When Alice receives the string SS = 11,11 which belongs to , she knows it implies two possibilities: either SS comes from the error-free string under MR = 10 in or an error is produced in the first measured bit that actually corresponds to the string under MR = 11 in . To disambiguate it, Alice uses the auxiliary frame . Thus, she looks at a frame where the ambiguous row is allocated. Remember that each row is combined with each other. Previously, the second row of , i.e., , was verified as a zero frame. Then, suppose Alice finds the following case:
2.4. One-Time Pad XOR Equivalency
3. Distillation Method with 3 × 2 Frames
- The 3 × 2 frames must be identified: there are binary 3 × 2 frames.
- The measurement results (MR) must be specified: in 3 × 2 frames, there are 8 MR. Those MR are illustrated in Table A2 of Appendix A.
- Frames are classified as usable and useless frames: a usable frame is a frame that produces a distinct SS under each MR. In 3 × 2 frames, there are 8 distinct SS per frame and 24 usable frames. Sifting bits are written in Table A4 of Appendix A. Remember that Sifting Strings (SS) are composed by the sifting bits and the measured bits: . The is appended to achieve discrimination, and it can be considered as a parity sifting bit.
- Auxiliary frames which are intended to catch errors produced in regular frames must be identified. In 3 × 2 frames, there are 3 auxiliary frames labeled as , , and . The frame is the zero frame and is used to verify the two (below) rows of the testing frames and . The upper row of and is the row that is being tested. In the end, Alice will include the auxiliary frames inside the set of frames that Bob must remove. Auxiliary frames are listed in Table A1 of Appendix A.
- All usable frames under each MR must be expanded to analyze all possible errors through SS, from single to multiple errors. Then, ambiguous SS that can be corrected under the auxiliary frames must be detected. In addition, all the SS that cannot be disambiguated must be identified and the corresponding frames must be removed. We show in Table A5 the cases that can be successfully disambiguated.
- At Bob’s side, each (SS, MR) pair defines a secret bit (sb). For Alice, the same secret bit results from the pair (SS, ) because she knows the frame that is behind each SS. It must be guaranteed that each SS can be produced equally by both bits. In addition, it must be ensured that each secret bit proceeds from the same number of frames, so that the bit probability of each SS is the same in order to reduce the eavesdropper’s information gain (SS are publicly transmitted over the classical channel). This action may involve removing some extra SS. Alice sends to Bob the set of SS of all the frames that must be eliminated including auxiliary frames. Table A3 of Appendix A enlists SS, MR, frames, and sb.
- Alice sends some non-orthogonal quantum pairs either or where . Although quantum non-orthogonal pairs can be mutually interleaved they are numbered, so each pair can be identified by Alice and Bob
- Bob measures each quantum pair using the same measurement basis (X or Z) which is chosen randomly (under active basis measurement). Some double detection events are produced. Bob informs Alice the tag number of such quantum pairs.
- Alice computes all usable frames including null frames and auxiliary frames. She communicates to Bob the frame arrangement information. We call this step privacy amplification.
- Bob computes the Sifting String (SS) of each frame. He returns the set of Siting Strings he obtained to Alice.
- Alice analyzes the SS received from Bob:
- She generates frames to prepare the auxiliary frames.
- Using auxiliary frames, Alice removes ambiguity. Alice gets the secret bits using the relation (SS, ) and Table A3 of Appendix A.
- Alice informs Bob of the cases that must be eliminated (because they cannot be disambiguated).
- Bob removes the frames identified by Alice to reach Alice’s secret bit string. Bob’s secret bits are derived from (SS, MR) and Table A3 of Appendix A.
4. Secret Rate
4.1. Secret Throughput
4.2. Rate Code
4.3. Secret Key Rate
4.3.1. The Intercept and Resend Attack (IR)
- —
- Alice sends the non-orthogonal pair to Bob over the quantum channel. Eve measures them using Z basis, and let us assume she obtains a double matching detection event, say .
- —
- Eve prepares and sends the quantum pair to Bob.
- —
- Suppose Eve can force both quantum pulses to arrive to Bob’s optical station. There are two quantum measurement bases (X or Z) and five possible outcomes:
- –
- due to Bob’s Z basis: .
- –
- due to Bob’s X basis: .
To match Eve’s double detection event , Bob must choose the Z basis which occurs with probability, so Eve’s final probability is .
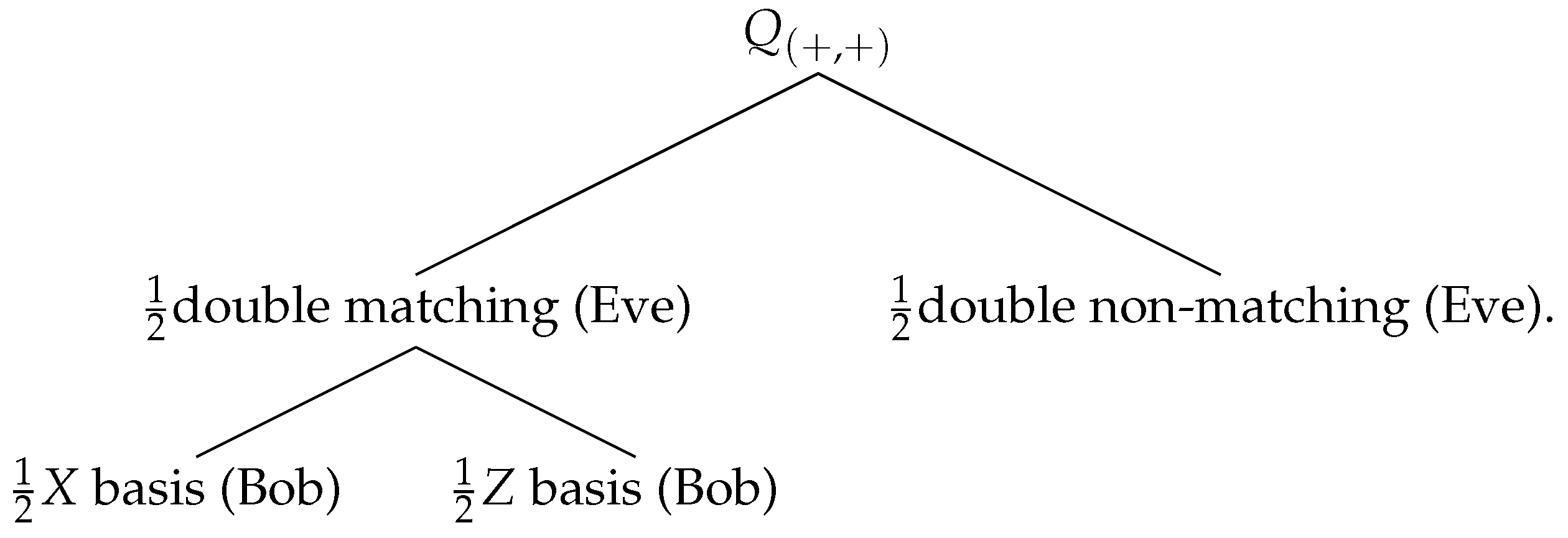
4.3.2. The Photon Number Splitting Attack (PNS)
- because of the probability to get a double matching detection event.
- due to basis matching. Eve must measure choosing between two different measurement basis (X or Z).

4.3.3. The Bases Choice Attack (BC)
5. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Useful Frames | Auxiliary Frames | ||
|---|---|---|---|
| MR = 000 | MR = 100 |
| MR = 001 | MR = 101 |
| MR = 010 | MR = 110 |
| MR = 011 | MR = 111 |
| Sifting String | Bob’s MR | Alice’s Frame | sb | Bob’s MR | sb | Alice’s Frame | |
|---|---|---|---|---|---|---|---|
| Measured | Sifting | ||||||
| 110 | 000 | 000 | , , , | 0 | 001 | 1 | , , , |
| 011 | 000 | 000 | , , , | 0 | 001 | 1 | , , , |
| 011 | 001 | 110 | , , , | 0 | 111 | 1 | , , , |
| 110 | 001 | 100 | , , , | 0 | 101 | 1 | , , , |
| 010 | 011 | 110 | , , , | 0 | 101 | 1 | , , , |
| 111 | 011 | 100 | , , , | 0 | 111 | 1 | , , , |
| 001 | 010 | 001 | , , , | 0 | 011 | 1 | , |
| 100 | 010 | 001 | , , , | 0 | 011 | 1 | , |
| 010 | 010 | 001 | , ,, | 0 | 010 | 1 | , |
| 111 | 010 | 001 | , , , | 0 | 010 | 1 | , |
| 001 | 011 | 110 | , | 0 | 100 | 1 | , |
| 100 | 011 | 101 | , | 0 | 111 | 1 | , |
| 001 | 100 | 000 | , , , | 0 | 010 | 1 | , |
| 100 | 100 | 000 | , , , | 0 | 010 | 1 | , |
| 010 | 100 | 000 | , , , | 0 | 011 | 1 | , |
| 111 | 100 | 000 | , , , | 0 | 011 | 1 | , |
| 001 | 101 | 111 | , | 0 | 101 | 1 | , |
| 100 | 101 | 100 | , | 0 | 110 | 1 | , |
| 010 | 101 | 111 | , , , | 0 | 100 | 1 | , , , |
| 111 | 101 | 101 | , , , | 0 | 110 | 1 | , , , |
| 011 | 110 | 010 | ,, ,, , | 0 | 011 | 1 | , , , , , |
| 110 | 110 | 010 | , , , , , | 0 | 011 | 1 | , , , , , |
| 011 | 111 | 101 | , , , | 0 | 100 | 1 | , , , |
| 110 | 111 | 110 | , , , | 0 | 111 | 1 | , , , |
| Alice | Bob | |||
|---|---|---|---|---|
| Frame | MR | SS | Disambiguated Bits |
|---|---|---|---|
| 010 | 011,110 | 2nd & 3rd | |
| 101 | 011,111 | ||
| 010 | 110,110 | 1st & 2nd | |
| 110 | 110,111 | ||
| 011 | 011,110 | 2nd & 3rd | |
| 100 | 011,111 | ||
| 100 | 111,011 | zero & 1st | |
| 001 | 110,000 | zero & 2nd | |
| 010 | 110,110 | ||
| 101 | 110,001 | ||
| 110 | 110,111 | ||
| 000 | 110,000 | zero & 1st | |
| 010 | 110,110 | ||
| 100 | 110,001 | ||
| 110 | 110,111 | ||
| 011 | 110,110 | 1st & 2nd | |
| 111 | 110,111 | ||
| 111 | 111,011 | 1st & 3rd | |
| 100 | 111,011 | 1st & 3rd | |
| 111 | 111,011 | zero & 3rd | |
| 001 | 110,000 | zero & 1st | |
| 011 | 110,110 | ||
| 101 | 110,001 | ||
| 111 | 110,111 | ||
| 001 | 011,000 | zero & 3rd | |
| 011 | 011,110 | ||
| 100 | 011,111 | ||
| 110 | 011,001 | ||
| 000 | 011,000 | zero & 2nd | |
| 011 | 011,110 | ||
| 100 | 011,111 | ||
| 111 | 011,001 | ||
| 000 | 110,000 | zero & 2nd | |
| 011 | 110,110 | ||
| 100 | 110,001 | ||
| 111 | 110,111 | ||
| 001 | 011,000 | zero & 2nd | |
| 010 | 011,110 | ||
| 101 | 011,111 | ||
| 110 | 011,001 | ||
| 101 | 111,101 | 1st & 3rd | |
| 101 | 111,101 | zero & 1st | |
| 000 | 011,000 | zero & 3rd | |
| 010 | 011,110 | ||
| 101 | 011,111 | ||
| 111 | 011,001 | ||
| 001 | 111,010 | zero & 1st | |
| 011 | 111,100 | ||
| 101 | 111,101 | ||
| 111 | 111,011 | ||
| 110 | 111,101 | 1st & 3rd | |
| 110 | 111,101 | zero & 3rd | |
| 001 | 111,010 | zero & 3rd | |
| 011 | 111,100 | ||
| 100 | 111,011 | ||
| 110 | 111,101 | ||
| 000 | 111,100 | zero & 1st | |
| 010 | 111,010 | ||
| 100 | 111,011 | ||
| 110 | 111,101 | ||
| 000 | 111,100 | zero & 3rd | |
| 010 | 111,010 | ||
| 101 | 111,101 | ||
| 111 | 111,011 |
References
- Kao, K.C.; Hockham, G.A. Dielectric-fibre surface waveguides for optical frequencies. In Proceedings of the Institution of Electrical Engineers; IET: London, UK, 1966; Volume 113, pp. 1151–1158. [Google Scholar]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.; Pan, J. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Mehic, M.; Niemiec, M.; Rass, S.; Ma, J.; Peev, M.; Aguado, A.; Martin, V.; Schauer, S.; Poppe, A.; Pacher, C.; et al. Quantum key distribution: A networking perspective. ACM Comput. Surv. CSUR 2020, 53, 1–41. [Google Scholar] [CrossRef]
- Lovic, V. Quantum key distribution: Advantages, challenges and policy. Camb. J. Sci. Policy 2020, 1, e8410270193. [Google Scholar] [CrossRef]
- Razavi, M.; Leverrier, A.; Ma, X.; Qi, B.; Yuan, Z. Quantum key distribution and beyond: Introduction. JOSA B 2019, 36, QKD1–QKD2. [Google Scholar] [CrossRef]
- Geihs, M.; Nikiforov, O.; Demirel, D.; Sauer, A.; Butin, D.; Günther, F.; Alber, G.; Walther, T.; Buchmann, J. The status of quantum-key-distribution-based long-term secure internet communication. IEEE Trans. Sustain. Comput. 2019. [Google Scholar] [CrossRef]
- Kong, P. A review of quantum key distribution protocols in the perspective of smart grid communication security. IEEE Syst. J. 2020. [Google Scholar] [CrossRef]
- Pearson, D. High-speed qkd reconciliation using forward error correction. In AIP Conference Proceedings; American Institute of Physics: Melville, NY, USA, 2004; Volume 734, pp. 299–302. [Google Scholar]
- Runser, R.J.; Chapuran, T.; Toliver, P.; Peters, N.A.; Goodman, M.S.; Kosloski, J.T.; Nweke, N.; McNown, S.R.; Hughes, R.J.; Rosenberg, D.; et al. Progress toward quantum communications networks: Opportunities and challenges. In Optoelectronic Integrated Circuits IX; International Society for Optics and Photonics: Red Hook, NY, USA, 2007; Volume 6476, p. 64760I. [Google Scholar]
- Lütkenhaus, N. Estimates for practical quantum cryptography. Phys. Rev. A 1999, 59, 3301. [Google Scholar] [CrossRef]
- Lizama-Pérez, L.A.; López, J.M.; Carlos-López, E.D.; Venegas-Andraca, S.E. Quantum flows for secret key distribution in the presence of the photon number splitting attack. Entropy 2014, 16, 3121–3135. [Google Scholar] [CrossRef]
- Lizama-Pérez, L.A.; López, J.M.; De Carlos López, E. Quantum key distribution in the presence of the intercept-resend with faked states attack. Entropy 2016, 19, 4. [Google Scholar] [CrossRef]
- Lizama-Pérez, L.A.; Lopez, M. Quantum key distillation using binary frames. Symmetry 2020, 12, 1053. [Google Scholar] [CrossRef]
- Fung, C.H.F.; Qi, B.; Tamaki, K.; Lo, H.K. Phase-remapping attack in practical quantum-key-distribution systems. Phys. Rev. A 2007, 75, 032314. [Google Scholar] [CrossRef]
- Xu, F.; Qi, B.; Lo, H.-K. Experimental demonstration of phase-remapping attack in a practical quantum key distribution system. New J. Phys. 2010, 12, 113026. [Google Scholar] [CrossRef]
- Makarov, V.; Hjelme, D.R. Faked states attack on quantum cryptosystems. J. Mod. Opt. 2005, 52, 691–705. [Google Scholar] [CrossRef]
- Makarov, V.; Anisimov, A.; Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 2006, 74, 022313. [Google Scholar] [CrossRef]
- Makarov, V.; Skaar, J. Faked states attack using detector efficiency mismatch on sarg04, phase-time, dpsk, and ekert protocols. Quantum Inf. Comput. 2008, 8, 622–635. [Google Scholar]
- Qi, B.; Fung, C.F.; Lo, H.; Ma, X. Time-shift attack in practical quantum cryptosystems. arXiv 2005, arXiv:quant-ph/0512080. [Google Scholar]
- Lydersen, L.; Wiechers, C.; Wittmann, C.; Elser, D.; Skaar, J.; Makarov, V. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 2010, 4, 686–689. [Google Scholar] [CrossRef]
- Gerhardt, I.; Liu, Q.; Lamas-Linares, A.; Skaar, J.; Kurtsiefer, C.; Makarov, V. Full-field implementation of a perfect eavesdropper on a quantum cryptography system. Nat. Commun. 2011, 2, 349. [Google Scholar] [CrossRef]
- Wiechers, C.; Lydersen, L.; Wittmann, C.; Elser, D.; Skaar, J.; Marquardt, C.; Makarov, V.; Leuchs, G. After-gate attack on a quantum cryptosystem. New J. Phys. 2011, 13, 013043. [Google Scholar] [CrossRef]
- Weier, H.; Krauss, H.; Rau, M.; Fuerst, M.; Nauerth, S.; Weinfurter, H. Quantum eavesdropping without interception: An attack exploiting the dead time of single-photon detectors. New J. Phys. 2011, 13, 073024. [Google Scholar] [CrossRef]
- Scarani, V.; Acin, A.; Ribordy, G.; Gisin, N. Quantum cryptography protocols robust against photon number splitting attacks for weak laser pulse implementations. Phys. Rev. Lett. 2004, 92, 057901. [Google Scholar] [CrossRef] [PubMed]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Verdu, S. Fifty years of shannon theory. IEEE Trans. Inf. Theory 1998, 44, 2057–2078. [Google Scholar] [CrossRef]
- Kuritsyn, K. Modification of error reconciliation scheme for quantum cryptography. In First International Symposium on Quantum Informatics; International Society for Optics and Photonics: Red Hook, NY, USA, 2003; Volume 5128, pp. 91–94. [Google Scholar]
- Brassard, G.; Salvail, L. Secret-key reconciliation by public discussion. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1993; pp. 410–423. [Google Scholar]
- Buttler, W.T.; Lamoreaux, S.K.; Torgerson, J.R.; Nickel, G.H.; Donahue, C.H.; Peterson, C.G. Fast, efficient error reconciliation for quantum cryptography. Phys. Rev. A 2003, 67, 052303. [Google Scholar] [CrossRef]
- Van Assche, G.; Cardinal, J.; Cerf, N.J. Reconciliation of a quantum-distributed gaussian key. IEEE Trans. Inf. Theory 2004, 50, 394–400. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G.; Crépeau, C.; Maurer, U.M. Generalized privacy amplification. IEEE Trans. Inf. Theory 1995, 41, 1915–1923. [Google Scholar] [CrossRef]
- Muramatsu, J. Transmission of messages to the efficiency limit-implementation of tractable channel code achieving the shannon limit. NTT Tech. Rev. 2019, 17, 34–39. [Google Scholar]
- Yuan, H.; Song, J.; Han, L.; Hou, K.; Shi, S. Improving the total efficiency of quantum key distribution by comparing bell states. Opt. Commun. 2008, 281, 4803–4806. [Google Scholar] [CrossRef]
- Abou Jaoude, A. The paradigm of complex probability and claude shannon’s information theory. Syst. Sci. Control Eng. 2017, 5, 380–425. [Google Scholar] [CrossRef]
- Wagner, N.R. The Laws of Cryptography with Java Code. 2003. Available online: https://www.csshl.net/sites/default/files/_downloadable/crypto/laws_of_cryptography_with_java_code.pdf (accessed on 18 December 2020).
- Grosshans, F.; Van Assche, G.; Wenger, J.; Brouri, R.; Cerf, N.J.; Grangier, P. Quantum key distribution using gaussian-modulated coherent states. Nature 2003, 421, 238–241. [Google Scholar] [CrossRef]
- Grosshans, F.; Grangier, P. Reverse reconciliation protocols for quantum cryptography with continuous variables. arXiv 2002, arXiv:quant-ph/0204127. [Google Scholar]
- Wang, X.; Zhang, Y.; Yu, S.; Guo, H. High speed error correction for continuous-variable quantum key distribution with multi-edge type ldpc code. Sci. Rep. 2018, 8, 1–7. [Google Scholar] [CrossRef] [PubMed]
- Chung, S.; Forney, G.D.; Richardson, T.J.; Urbanke, R. On the design of low-density parity-check codes within 0.0045 db of the shannon limit. IEEE Commun. Lett. 2001, 5, 58–60. [Google Scholar] [CrossRef]
- Mehic, M.; Niemiec, M.; Siljak, H.; Voznak, M. Error reconciliation in quantum key distribution protocols. Lect. Notes Comput. Sci. 2020, 12070, 222–236. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the International Conference on Computers, Systems & Signal Processing, Bangalore, India, 9–12 December 1984. [Google Scholar]
- Van Assche, G. Quantum Cryptography and Secret-Key Distillation; Cambridge University Press: Cambridge, UK, 2006. [Google Scholar]
- Hughes, R.; Nordholt, J.; Rarity, J. Summary of Implementation Schemes for Quantum Key Distribution and Quantum Cryptography—A Quantum Information Science and Technology Roadmap; United States Government: New York, NY, USA, 2004.
- Bennett, C.H.; Bessette, F.; Brassard, G.; Salvail, L.; Smolin, J. Experimental quantum cryptography. J. Cryptol. 1992, 5, 3–28. [Google Scholar] [CrossRef]
- Kumar, V.V.; Karthikeyan, T.; Praveen Sundar, P.V.; Magesh, G.; Balajee, J.M. A quantum approach in lifi security using quantum key distribution. Int. J. Adv. Sci. Technol. 2020, 29, 2345–2354. [Google Scholar]



| Alice | Bob |
|---|---|
| , , | , , |
| , , | , , |
| , , | , , |
| , , | , , |
| , , | , , |
| , , | , , |
| , , | , , |
| , , | , , |
| , | , |
| c | |
| 0 | |
| 1 | |
| c | MR | Frames | sb | |
|---|---|---|---|---|
| 00 | 10 | 0 | ||
| 11 | 1 | |||
| 00 | , | 0 | ||
| 01 | , | 1 | ||
| 01 | 01 | , | 0 | |
| 11 | 1 | |||
| 10 | 0 | |||
| 01 | , | 1 | ||
| 10 | 00 | , | 0 | |
| 10 | 1 | |||
| 00 | , | 0 | ||
| 11 | 1 | |||
| 11 | 11 | , , | 0 | |
| 10 | , , | 1 |
| n | ||||||
|---|---|---|---|---|---|---|
| 100 | 618 | 20,212 | 412 | 11,550 | 206 | 2887 |
| 500 | 15,593 | 2,588,562 | 10,395 | 1,479,178 | 5197 | 369,794 |
| 1000 | 62,437 | 20,770,875 | 41,625 | 11,869,071 | 20,812 | 2,967,267 |
| IR | PNS | BC |
|---|---|---|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lizama-Pérez, L.A.; López R., J.M.; Samperio, E.H. Beyond the Limits of Shannon’s Information in Quantum Key Distribution. Entropy 2021, 23, 229. https://doi.org/10.3390/e23020229
Lizama-Pérez LA, López R. JM, Samperio EH. Beyond the Limits of Shannon’s Information in Quantum Key Distribution. Entropy. 2021; 23(2):229. https://doi.org/10.3390/e23020229
Chicago/Turabian StyleLizama-Pérez, Luis Adrián, J. Mauricio López R., and Emmanuel H. Samperio. 2021. "Beyond the Limits of Shannon’s Information in Quantum Key Distribution" Entropy 23, no. 2: 229. https://doi.org/10.3390/e23020229
APA StyleLizama-Pérez, L. A., López R., J. M., & Samperio, E. H. (2021). Beyond the Limits of Shannon’s Information in Quantum Key Distribution. Entropy, 23(2), 229. https://doi.org/10.3390/e23020229







