Proof of Concept of Scalable Integration of Internet of Things and Blockchain in Healthcare
Abstract
1. Introduction
2. Related Works
2.1. Security Preliminaries
2.2. Security in IoT
- QoS-0 is no guaranteed reliable level. There is no guarantee for the packet delivery.
- QoS-1 guarantees that the message is delivered at least once.
- QoS-2 guarantees that the message is received only once. This is safest but slow in service.
2.3. Blockchain Principles
2.3.1. Hash Functions and Merkle Trees
2.3.2. Smart Contracts
2.4. Need for the Blockchain and IoT Integration
- Decentralization: Centralized systems such as cloud based IoT networks are single points of failures. Blockchain provides decentralized peer-to-peer architecture.
- Scalability: Scalability is the outcome of decentralization which improves fault tolerance.
- Identity: Every IoT device connected to the blockchain can be addressed uniquely and blockchain can provide distributed authorization and authentication to these devices.
- Autonomy: The IoT devices can interact with each other using the blockchain infrastructure without the need for centralized servers.
- Reliability: Tamper-proof and distributed record management feature of the blockchain can bring a higher degree of reliability for the data from the IoT devices.
- Security: The information from the IoT devices is stored as transactions inside the blockchain. Before storing the data inside blocks, each transaction is validated by all its peers inside the blockchain. In this way, security is guaranteed.
3. Proposed Framework
3.1. Application Layer
3.2. Business Layer
3.3. Storage Layer
4. System Evaluation
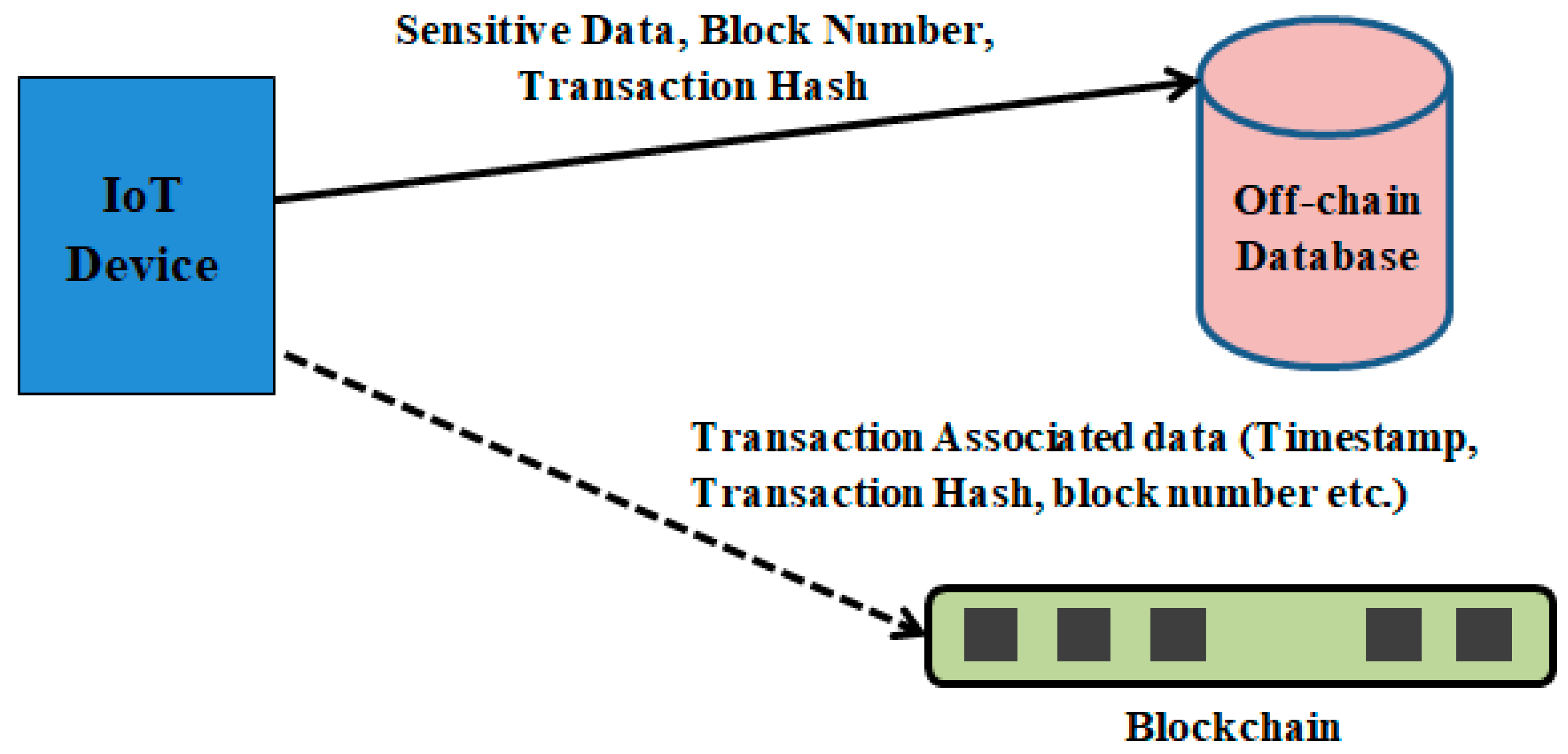
- IoT Device: This device is attached to the patient body to monitor vital parameters such as heart rate and body temperature. Sensors that read these parameters from the body are attached to the controller in the device. Processing of raw data received from the sensors, framing the data for storage purposes, communication, and networking functions will be taken care of by this device. All the interactions will go through the blockchain network, and each of these transactions are stored as immutable records inside the network. The sensitive data from the device are stored in the off-chain database.
- Off-Chain Database: This is the database in which the body vital parameters and other patient records are stored. Access to this database is controlled by the smart contract. Read or write operations on this database are based on the privileges assigned to the users by the system supervisor. There are security mechanisms employed at the database level to accommodate data privacy and integrity. Optionally, data can be hashed before being stored in the database.
- Doctor: A doctor can use a DApp to access the database to monitor the concerned patient’s body vital parameters and prescribe medicines based on the observations. Only authorized doctors are allowed to view data of a particular patient or to prescribe medication.
- Pharmacy: The pharmacist, using a DApp, can access medical prescription of a particular patient upon proving his identity. He can also access the address of the patient so that the medicines can be directly delivered at the patient’s site.
- Insurance Company: The insurance company is another component in this system who can access the services using a DApp. When a claim is made by the patient, he has the authority to verify the patient records.
- It provides real-time monitoring of patient’s critical conditions.
- It provides security to the sensitive data of the patient.
- It helps in making the insurance claiming process transparent as the records inside the blockchain are immutable and provide end-to-end traceability.
4.1. Implementation Details
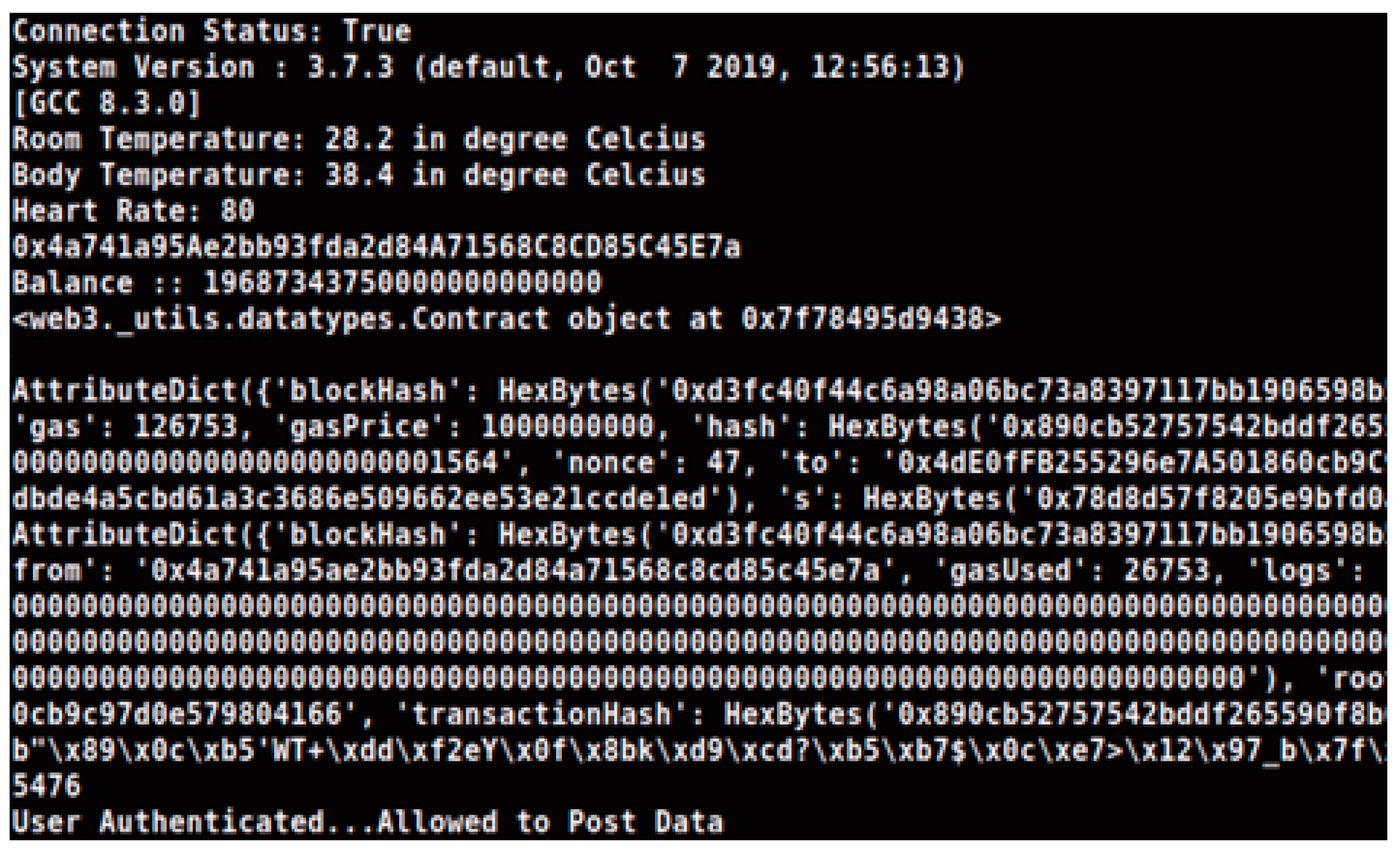
4.1.1. System Supervisor
4.1.2. Software
| Algorithm 1: Storing patient body vital parameters in the database |
| Input: patientID, patient_body_parameters Output: Body parameters are stored in the database and Transaction is recorded. pragma solidity ^0.5.12; mapping(address => bool) authorizedPatients; if( isPatientAuthorized(patientID)) store the patient body parameters in corresponding patient’s record; transaction is recorded in the blockchain; store the transaction hash and block number in the patient record; } else Revert the transaction; function public isPatientAuthorized(address patientID) public view return (bool approved) { return authorizedPatients[patientID]; } |
| Algorithm 2: Monitoring patient body vital parameters |
| Input: patientID, doctorID Output: patient_body_parameters pragma solidity ^0.5.12; mapping(address => address) authorizedDoctor; if( isDoctorAuthorized(patientID)) { Read the patient body parameters; transaction is recorded in the blockchain; } else Revert the transaction; function public isDoctorAuthorized(address patientID) public view return (bool display) { if(msg.sender == authorizedDoctor(patientID)) return true; else return false; } |
| Algorithm 3: Update patient prescription |
| Input: patientID, doctorID, prescription Output: Patient record update with new prescription pragma solidity ^0.5.12; mapping(address => address) authorizedDoctor; if( isDoctorAuthorized(patientID)) { Update the prescription in the corresponding patient’s record; transaction is recorded in the blockchain; } else Revert the transaction; function public isDoctorAuthorized(address patientID) public view return (bool display) { if(msg.sender == authorizedDoctor(patientID)) return true; else return false; } |
| Algorithm 4: Accessing patient’s prescription |
| Input: patientID, pharmaID, Output: Prescription of the patient pragma solidity ^0.5.12; mapping(address => address) authorizedPharma; if( isPharmacyAuthorized(patientID)) { Get prescription of the patient from the database transaction is recorded in the blockchain; } else Revert the transaction; function public isPharmacyAuthorized(address patientID) public view return (bool display) { if(msg.sender == authorizedPharma(patientID)) return true; else return false; } |
| Algorithm 5: Accessing patient’s medical records by the insurer |
| Input: patientID, insurerID, Output: Records of the patient pragma solidity ^0.5.12; mapping(address => address) authorizedInsurer; if( isInsurerAuthorized(patientID)) { Get patient’s record from the database; transaction is recorded in the blockchain; } else Revert the transaction; function public isInsurerAuthorized(address patientID) public view return (bool display) { if(msg.sender == authorizedInsurer(patientID)) return true; else return false; } |
4.1.3. Hardware
4.2. Analysis
- Transaction Confirmation time: A node in the chain is expected to validate each transaction of every block. Hence, transaction validation is one of the major tasks in the blockchain. The computational power of the system has an unswerving effect on the transaction confirmation time. The average transaction confirmation time of the system is 1.7 seconds.
- Block Time: The block time is defined as the amount of time it takes for the miner to generate a new block. In Ethereum, the block time is between 10–20 seconds. In the proposed use case, it is 11.21 seconds.
- Migration and Deployment Time: It is the amount of time taken by the smart contract testing framework (Truffle in this case) to compile the smart contract and push it on to the Ethereum network. It took 9.14 seconds to deploy the smart contract in this use case.
- Deployment Cost: It is the fee paid by the user to push the smart contract application on the Ethereum blockchain. The deployment cost in the proposed model is 0.00179117 ETH.
4.2.1. Discussion
- Scalability: Scalability is defined as the ability of an information system to maintain its equilibrium state with increased storage volume. Scalability is a key issue in the integration of blockchain and IoT as IoT devices are growing rapidly and their applications, in general, generate huge volumes of data. In [50,54], the scalability is achieved at the cost of increased complexity due to the clustering of nodes, and lifetime management of these clusters. In addition, the method described in [54] requires each node to store at least one local blockchain at any instance of time and hence it is not suitable for memory-constrained IoT devices. Furthermore, with off-chain data storage mechanisms, only associated data are stored in blockchain, and sensitive data are stored in the off-chain database. This reduces the transaction data size and increases the number of transactions that can be accommodated within the block. Hence, throughput and scalability of the overall system are enhanced.
- Confidentiality: As the proposed model uses permissioned blockchain, only authorized users are allowed to access the blockchain network. Since only authorized users can access on-chain as well as off-chain data, the confidentiality of the data is preserved.
- Access control and tamper-proof: Role-based access to the database is enabled by the smart contract that is deployed on the blockchain platform. The tamperproof nature of the blockchain makes it even more difficult for someone to modify the transaction data on chain.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ashton, K. That Internet of Things Thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Rajab, H.; Cinkel, T. IoT based Smart Cities. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC), Rome, Italy, 19–21 June 2018; pp. 1–4. [Google Scholar]
- Miguez, F.; Fernandez-Caranes, T.M.; Fraga-Lamas, P.; Castedo, L. Design, Implementation and Practical Evaluation of an IoT Home Automation System for Fog Computing Applications Based on MQTT and Zigbee-WiFi Sensor Nodes. Sensors 2018, 18, 2660. [Google Scholar] [CrossRef] [PubMed]
- Verma, H.; Jain, M.; Goel, K.; Vikram, A.; Verma, G. Smart home system based on Internet of Things. In Proceedings of the 3rd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 16–18 March 2016; pp. 2073–2075. [Google Scholar]
- Li, W.; Logenthiran, T.; Phan, V.; Woo, W.L. A Novel Smart Energy Theft System (SETS) for IoT-Based Smart Home. IEEE Internet Things J. 2019, 6, 5531–5539. [Google Scholar] [CrossRef]
- Satamraju, K.P.; Shaik, K.; Vellanki, N. RURAL BRIDGE: A novel system for smart and co-operative farming using IoT architecture. In Proceedings of the 2017 International Conference on Multimedia, Signal Processing and Communication Technologies (IMPACT), Aligarh, India, 24–26 November 2017; 2017; pp. 22–26. [Google Scholar]
- Agale, R.R.; Gaikwad, D.P. Automated Irrigation and Crop Security System in Agriculture Using Internet of Things. In Proceedings of the 2017 International Conference on Computing, Communication, Control and Automation (ICCUBEA), Pune, India, 17–18 August 2017; pp. 1–5. [Google Scholar]
- Herrera-Quintero, L.F.; Vega-Alfonso, J.C.; Banse, K.B.A.; Carrillo Zambrano, E. Smart ITS Sensor for the Transportation Planning Based on IoT Approaches Using Serverless and Microservices Architecture. IEEE Intelligent Transp. Sys. Magazine. 2018, 10, 17–27. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Comm. Surveys & Tutorials. 2019, 21, 2702–2733. [Google Scholar]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Forecast: IoT Security, Worldwide. 2018. Available online: https://www.gartner.com/en/newsroom/press-releases/2018-03-21-gartner-says-worldwide-iot-security-spending-will-reach-1-point-5-billion-in-2018 (accessed on 21 October 2019).
- Zhao, S.; Rengasamy, P.V.; Zhang, H.; Bhuyan, S.; Nachiappan, N.C.; Sivasubramaniam, A.; Kandemir, M.T.; Das, C. Understanding Energy Efficiency in IoT App Executions. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019; pp. 742–755. [Google Scholar]
- Liu, X.; Ansari, N. Toward Green IoT: Energy Solutions and Key Challenges. IEEE Comms. Magazine 2019, 57, 104–110. [Google Scholar] [CrossRef]
- El-hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A Survey of Internet of Things (IoT) Authentication Schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef]
- Celia, L.; Cungang, Y. (WIP) Authenticated Key Management Protocols for Internet of Things. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018; pp. 126–129. [Google Scholar]
- Roman, R.; Rios, R.; Onieva, J.A.; Lopez, J. Immune System for the Internet of Things Using Edge Technologies. IEEE Internet Things J. 2019, 6, 4774–4781. [Google Scholar] [CrossRef]
- Han, Z.; Li, X.; Huang, K.; Feng, Z. A Software Defined Network-Based Security Assessment Framework for CloudIoT. IEEE Internet Things J. 2018, 5, 1424–1434. [Google Scholar] [CrossRef]
- Mansoor, K.; Ghani, A.; Chaudhry, S.A.; Shamshirband, S.; Ghayyur, S.A.K. Securing IoT-Based RFID Systems: A Robust Authentication Protocol Using Symmetric Cryptography. Sensors 2019, 19, 4752. [Google Scholar] [CrossRef] [PubMed]
- Giaretta, A.; Dragoni, N.; Massacci, F. IoT Security Configurability with Security-by-Contract. Sensors 2019, 19, 4121. [Google Scholar] [CrossRef] [PubMed]
- Ali, B.; Awad, A.I. Cyber and Physical Security Vulnerability Assessment for IoT-Based Smart Homes. Sensors 2018, 18, 817. [Google Scholar] [CrossRef] [PubMed]
- Babaei, A.; Schiele, G. Physical Unclonable Functions in the Internet of Things: State of the Art and Open Challenges. Sensors 2019, 19, 3208. [Google Scholar] [CrossRef]
- Satamraju, K.P.; Malarkodi, B. Design and Evaluation of a Lightweight Security Framework for IoT Applications. In Proceedings of the TENCON 2019–2019 IEEE Region 10 Conference (TENCON), Kochi, India, 17–20 October 2019; pp. 522–526. [Google Scholar]
- IoTIFY, a cloud based IoT performance testing platform. Available online: https://iotify.io/ (accessed on 24 September 2019).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 24 October 2019).
- Wang, R.; He, J.; Liu, C.; Li, Q.; Tsai, W.; Deng, E. A Privacy-Aware PKI System Based on Permissioned Blockchains. In Proceedings of the 2018 IEEE 9th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 23–25 November 2018; pp. 928–931. [Google Scholar]
- Ali Syed, T.; Alzahrani, A.; Jan, S.; Siddiqui, M.S.; Nadeem, A.; Alghamdi, T. A Comparative Analysis of Blockchain Architecture and its Applications: Problems and Recommendations. IEEE Access 2019, 7, 176838–176869. [Google Scholar] [CrossRef]
- Salman, T.; Zolanvari, M.; Erbad, A.; Jain, R.; Samaka, M. Security Services Using Blockchains: A State of the Art Survey. IEEE Comm. Surveys Tutorials 2019, 21, 858–880. [Google Scholar] [CrossRef]
- Wang, W.; Hoang, D.T.; Hu, P.; Xiong, Z.; Niyato, D.; Wang, P.; Wen, Y.; Kim, D.I. A Survey on Consensus Mechanisms and Mining Strategy Management in Blockchain Networks. IEEE Access 2019, 7, 22328–22370. [Google Scholar] [CrossRef]
- Zheng, W.; Zheng, Z.; Chen, X.; Dai, K.; Li, P.; Chen, R. NutBaaS: A Blockchain-as-a-Service Platform. IEEE Access 2019, 7, 134422–134433. [Google Scholar] [CrossRef]
- Tijan, E.; Aksentijević, S.; Ivanić, K.; Jardas, M. Blockchain Technology Implementation in Logistics. Sustainability 2019, 11, 1185. [Google Scholar]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Comm. Surveys & Tutorials 2015, 17, 2347–2376. [Google Scholar]
- Wan, J.; Li, J.; Imran, M.; Li, D.; Fazal-e-Amin. A Blockchain-Based Solution for Enhancing Security and Privacy in Smart Factory. IEEE Trans. Ind. Inform. 2019, 15, 3652–3660. [Google Scholar] [CrossRef]
- Zheng, D.; Jing, C.; Guo, R.; Gao, S.; Wang, L. A Traceable Blockchain-Based Access Authentication System With Privacy Preservation in VANETs. IEEE Access 2019, 7, 117716–117726. [Google Scholar] [CrossRef]
- Sun, Y.; Zhang, L.; Feng, G.; Yang, B.; Cao, B.; Imran, M.A. Blockchain-Enabled Wireless Internet of Things: Performance Analysis and Optimal Communication Node Deployment. IEEE Internet Things J. 2019, 6, 5791–5802. [Google Scholar] [CrossRef]
- Lindsay, J. Smart Contracts for Incentivizing Sensor Based Mobile Smart City Applications. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; pp. 1–4. [Google Scholar]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2019, 6, 1594–1605. [Google Scholar] [CrossRef]
- Zhang, K.; Mao, Y.; Leng, S.; He, Y.; Maharajan, S.; Gjessing, S.; Zhang, Y.; Tsang, D.H.K. Optimal Charging Schemes for Electric Vehicles in Smart Grid: A Contract Theoretic Approach. IEEE Trans. Intell. Transp. Sys. 2018, 19, 3046–3058. [Google Scholar]
- Thomas, L.; Long, C.; Burnap, P.; Wu, J.; Jenkins, N. Automation of the supplier role in the GB power system using blockchain-based smart contracts. CIRED-Open Access Proc. J. 2017, 1, 2619–2623. [Google Scholar] [CrossRef]
- Cruz, J.P.; Kaji, Y.; Yanai, N. RBAC-SC: Role-Based Access Control Using Smart Contract. IEEE Access 2018, 6, 12240–12251. [Google Scholar] [CrossRef]
- Chain of Things. 2017. Available online: https://www.blockchainofthings.com/ (accessed on 24 October 2019).
- Ethereum: a global, open-source platform for decentralized applications. Available online: https://ethereum.org/ (accessed on 24 October 2019).
- Ozyilmaz, K.R.; Yurdakul, A. Designing a Blockchain-Based IoT with Ethereum, Swarm, and LoRa: The Software Solution to Create High Availability with Minimal Security Risks. IEEE Consumer Elec. Mag. 2019, 8, 28–34. [Google Scholar] [CrossRef]
- Ali, M.S.; Vecchio, M.; Antonelli, F. Enabling a Blockchain-Based IoT Edge. IEEE Internet Things Mag. 2018, 1, 24–29. [Google Scholar] [CrossRef]
- Lo, S.K.; Liu, Y.; Chia, S.Y.; Xu, X.; Lu, Q.; Zhu, L.; Ning, H. Analysis of Blockchain Solutions for IoT: A Systematic Literature Review. IEEE Access 2019, 7, 58822–58835. [Google Scholar] [CrossRef]
- Metamask - Brings Ethereum to your browser. Available online: https://metamask.io/ (accessed on 24 October 2019).
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: the blockchain model of cryptography and privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar]
- Hyperledger: Open Source blockchain Technologies. Available online: https://www.hyperledger.org/ (accessed on 24 October 2019).
- IBM Enterprise Blockchain Solutions and Services. Available online: https://www.ibm.com/in-en/blockchain (accessed on 24 October 2019).
- Truffle Suite: Sweet Suite for Smart Contracts. Available online: https://www.trufflesuite.com (accessed on 24 October 2019).
- Bach, L.M.; Mihaljevic, B.; Zagar, M. Comparative analysis of blockchain consensus algorithms. In Proceedings of the 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018; pp. 1545–1550. [Google Scholar]
- Raspberry Pi 3 Model B. Available online: https://www.raspberrypi.org/products/raspberry-pi-3-model-b/ (accessed on 24 October 2019).
- Raspberry Pi 3 Model B+. Available online: https://www.raspberrypi.org/products/raspberry-pi-3-model-b-plus/ (accessed on 24 October 2019).
- Aksentijević, S.; Krnjak, D.; Tijan, E. Logistics environment awareness system prototype based on modular Internet of Things platform. Pomorstvo 2015, 29, 170–179. [Google Scholar]
- Ismail, L.; Materwala, H.; Zeadally, S. Lightweight Blockchain for Healthcare. IEEE Access 2019, 7, 149935–149951. [Google Scholar] [CrossRef]
- Ren, Y.; Leng, Y.; Zhu, F.; Wang, J.; Kim, H.J. Data Storage Mechanism Based on Blockchain with Privacy Protection in Wireless Body Area Network. Sensors 2019, 19, 2395. [Google Scholar] [CrossRef]
- Hang, L.; Kim, D.H. Design and Implementation of an Integrated IoT Blockchain Platform for Sensing Data Integrity. Sensors (Basel) 2019, 19, 2228. [Google Scholar] [CrossRef] [PubMed]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. Continuous patient monitoring with a patient centric agent: A block architecture. IEEE Access 2018, 6, 32700–32726. [Google Scholar] [CrossRef]
- Shahid, A.R.; Pissinou, N.; Staier, C.; Kwan, R. Sensor-Chain: A Lightweight Scalable Blockchain Framework for Internet of Things. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Atlanta, GA, USA, 14–17 July 2019; pp. 1154–1161. [Google Scholar]






| Payload Size | No. of Nodes | Type of Service | Average Latency (mSec) | % of Packets Lost |
|---|---|---|---|---|
| 100 bytes | 100 | QoS-0 | 0.017 | 0 |
| QoS-1 | 670.713 | 0 | ||
| 200 | QoS-0 | 0.016 | 0 | |
| QoS-1 | 2029.758 | 0 | ||
| 500 | QoS-0 | 0.019 | 0 | |
| QoS-1 | 6410.813 | 0 | ||
| 750 | QoS-0 | 0.019 | 0 | |
| QoS-1 | 11592.543 | 1 | ||
| 1000 | QoS-0 | 0.017 | 0 | |
| QoS-1 | 14771.078 | 13 | ||
| 1 KB | 100 | QoS-0 | 0.029 | 0 |
| QoS-1 | 735.773 | 0 | ||
| 200 | QoS-0 | 0.017 | 0 | |
| QoS-1 | 2180.992 | 0 | ||
| 500 | QoS-0 | 0.017 | 0 | |
| QoS-1 | 5144.808 | 1 | ||
| 750 | QoS-0 | 0.017 | 19 | |
| QoS-1 | 7372.016 | 1 | ||
| 1000 | QoS-0 | 0.019 | 0 | |
| QoS-1 | 13362.244 | 27 | ||
| 10 KB | 100 | QoS-0 | 0.017 | 0 |
| QoS-1 | 687.842 | 0 | ||
| 200 | QoS-0 | 0.017 | 0 | |
| QoS-1 | 1746.986 | 0 | ||
| 500 | QoS-0 | 0.016 | 7 | |
| QoS-1 | 5490.489 | 1 | ||
| 750 | QoS-0 | 0.016 | 1 | |
| QoS-1 | 4649.574 | 1 | ||
| 1000 | QoS-0 | 0.016 | 0 | |
| QoS-1 | 7923.592 | 8 |
| Reference No. | Category | Platform | Challenge Addressed |
|---|---|---|---|
| [32] | Industrial IoT | Multiplatform | Privacy, Security |
| [33] | Smart Transportation | Ethereum | Authentication, Privacy |
| [34] | Wireless IoT Systems | Ethereum | Security, Authentication |
| [35] | Smart Cities | Ethereum | Security |
| [36] | Internet of Things | Ethereum | Access Control |
| [37] | Electric Vehicle Charging | Multiplatform | Access Control |
| [38] | Smart Meters | Ethereum | Access Control |
| [39] | Asset Management | Multiplatform | Access Control |
| [40] | Blockchain based IoT | Multiplatform | Identity, security |
| Privilege ID | User | Privileges |
|---|---|---|
| 1 | Patient | Can store body vital parameters in the off-chain server and can read doctor’s prescription. |
| 2 | Doctor | Can access patient’s data and can update prescription. |
| 3 | Pharmacist | Can access doctor’s prescription and address of the patient from the database. |
| 4 | Insurance Company | Can access patient data, prescriptions and other records during claim validations |
| Package / Library | Version |
|---|---|
| geth | 1.9.6 |
| ethereum | 1.0.8 |
| eth_abi | 2.0.0 |
| ethjsonrpc | 0.3.0 |
| Truffle | 5.0.39 |
| Solidity | 0.5.12 |
| Py_solc | 3.2.0 |
| Node | 10.15.2 |
| Web3.js | 1.2.1 |
| Python | 3.7.3 |
| go | 1.10.4 |
| Function | Input Parameters | Return Value |
|---|---|---|
| isPatientAuthorized() | patientID | true: if the patientID is legitimate false: if the patientID is not legitimate |
| isDoctorAuthorized() | patientID | true: if the doctorID is authorized to view the corresponding patient data. false: otherwise |
| isPharmacyAuthorized() | patientID | true: if the pharmacyID is authorized to view the corresponding patient data. false: otherwise |
| isInsurerAuthorized() | patientID | true: if the insurerID is authorized to view the corresponding patient records. false: otherwise |
| storePatientInfo() | patientID, patient_body_parameters | Patient’s data is stored in the database after successful authentication of the patient—else the transaction is reverted and function reports FAILED transaction. |
| monitorPatient() | patientID, doctorID | Patient’s data is retrieved and from the database after successful authentication of the doctor—else the transaction is reverted and function reports FAILED transaction. |
| prescribeMedicines() | patientID, doctorID, prescription | Prescription is stored in the database after successful authentication process—else the transaction is reverted and function reports FAILED transaction. |
| getPrescription() | patientID, pharmacyID | Retrieves prescription of the patient from the database after successful authentication of the pharmacy—else the transaction is reverted and function reports FAILED transaction. |
| getPatientRecord() | patientID, insurerID | Patient’s records are retrieved from the database after successful authentication of the insurance company—else the transaction is reverted and function reports FAILED transaction. |
| Process | Time |
|---|---|
| SHA-3 256 | 193 μS on Raspberry Pi 3 B 191 μS on Raspberry Pi 3 B+ |
| Block time | 11.21 Seconds |
| Migration and deployment of smart contract | 9.14 Seconds |
| Transaction confirmation time | 1.7 Seconds |
| Total deployment cost | 0.00179117 ETH |
| Method | Blockchain Platform | Authentication | Access Control | Authorization | Scalability | Smart Contract | Off-Chain Storage |
|---|---|---|---|---|---|---|---|
| [54] | Bitcoin | ✓ | ✓ | ✓ | ✓ | ✕ | ✕ |
| [55] | Multi Platform | ✓ | ✓ | ✓ | ✕ | ✕ | ✕ |
| [56] | Hyperledger Fabric | ✓ | ✓ | ✓ | ✕ | ✓ | ✕ |
| [57] | Ethereum | ✓ | ✓ | ✓ | ✕ | ✕ | ✕ |
| [58] | Multi Platform | ✓ | ✓ | ✓ | ✓ | ✕ | ✕ |
| Proposed Method | Ethereum | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Satamraju, K.P.; B, M. Proof of Concept of Scalable Integration of Internet of Things and Blockchain in Healthcare. Sensors 2020, 20, 1389. https://doi.org/10.3390/s20051389
Satamraju KP, B M. Proof of Concept of Scalable Integration of Internet of Things and Blockchain in Healthcare. Sensors. 2020; 20(5):1389. https://doi.org/10.3390/s20051389
Chicago/Turabian StyleSatamraju, Krishna Prasad, and Malarkodi B. 2020. "Proof of Concept of Scalable Integration of Internet of Things and Blockchain in Healthcare" Sensors 20, no. 5: 1389. https://doi.org/10.3390/s20051389
APA StyleSatamraju, K. P., & B, M. (2020). Proof of Concept of Scalable Integration of Internet of Things and Blockchain in Healthcare. Sensors, 20(5), 1389. https://doi.org/10.3390/s20051389





