1. Introduction
Global Navigation Satellite Systems (GNSS) are vital for civilian applications like navigation, power grids and communications. Disruptions can threaten safety and critical operations. GNSS signals are particularly vulnerable to jamming and spoofing due to their low reception power and known structure. Recent advances in software-defined radio technology have intensified concerns about spoofing. Various spoofing attack types and the corresponding countermeasure techniques are presented and discussed in the literature, a sample of which can be found in [
1]. A basic approach uses a GNSS repeater to create a meaconing attack by capturing, amplifying and retransmitting GNSS signals to overwhelm authentic ones. More complex attacks involve a GNSS receiver paired with a spoofing transmitter that synchronizes with real signals to create counterfeit ones, complicating detection efforts [
1,
2]. Detection techniques have been proposed, utilizing features of counterfeit signals in single- [
2,
3,
4] and multi-antenna systems [
5,
6]. Single-antenna metrics are effective in the presence of both authentic and spoofed signals, using pre-despreading techniques to detect excessive power in GNSS bands [
7] and post-despreading methods to identify abnormal behaviors in the signals [
8,
9,
10]. In [
11], various spoofing scenarios and detection metrics for single-antenna GNSS receivers are outlined, with tests conducted to assess detection accuracy and false alarms. This paper expands on those detection capabilities to a multi-frequency, multi-constellation approach and discusses cryptologic protections, including a prototype for the Galileo E1B Open Service Navigation Message Authentication (OSNMA) [
12,
13].
2. GNSS Resilience and Integrity Technology (GRIT)
Ensuring the security and resiliency of the position, navigation and timing solutions is a top priority at NovAtel. It is aimed to assist and educate customers on various defense mechanisms against malicious attacks tailored to specific applications. GNSS Resilience and Integrity Technology (GRIT) is a NovAtel OEM7 firmware suite that provides situational awareness and interference mitigation tools, including interference detection and characterization, spoofing detection, time-tagged digital snapshots, spatial processing and null-steering.
Interference Toolkit (ITK): NovAtel receivers track signals on several frequencies to achieve the precision and performance they are known for. In general, electronic devices operating in the increasingly crowded radio frequency spectrum can cause unintentional interference within the GNSS signal bands, addressing which NovAtel has developed the Interference Toolkit (ITK) for its OEM7 receivers. ITK is used to measure the RF spectrum levels and apply mitigation tools to protect the GNSS measurement quality, maintaining a high-quality multi-frequency multi-constellation positioning performance even under challenging RF environments. ITK identifies interference occurrence and characterizes the detected jammer in time and frequency domains. Mitigation options include implementing notch filters at detected frequencies and High Dynamic Range (HDR) mode for wideband interference.
Spoofing Detection: A real-time Spoofing Detection Toolkit (SK), available in the OEM7 generation of NovAtel’s receivers, employs a selection of the most effective spoofing detection metrics. In the testing, the detection unit monitors GPS L1/L5, Galileo E1/E5a/E5b and BDS B1C/B2a observations with a detection rate of 0.5 Hz. The outputs are fed to an onboard central spoofing detection unit, where the ultimate decision is made whether the receiver is under a spoofing attack or not. The main intention is to reduce the probability of false alarms in the presence of jamming and multipath signals while detecting the spoofing attack with high confidence. The implemented spoofing detection was successful in almost all spoofing scenarios performed in Jammertest 2023, detailed information of which can be found in [
14].
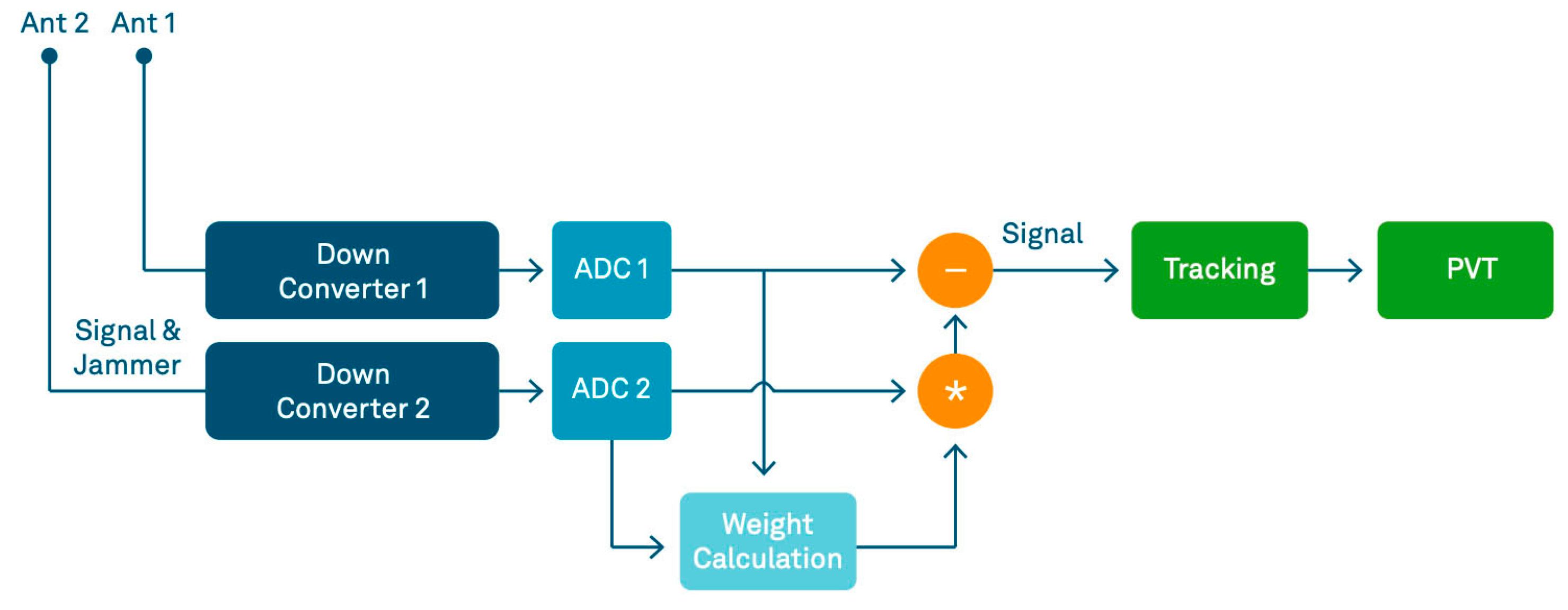
Robust Dual-Antenna Receiver (RoDAR) is an active anti-jamming tool that uses spatial processing to protect against different types of interference scenarios and spoofing signals. The operation of RoDAR is shown in
Figure 1. The RF signals from two antennas are passed to the null-steering weight calculation unit after down conversion and digitization. Then, the second antenna signal undergoes phase rotation and gain compensation based on the calculated array weights and is removed from the first antenna signal. The resultant samples are jammer- and spoofer-free. The cleaned signals are then passed on to the tracking and position, velocity and time (PVT) solution module for a resilient solution. RoDAR offers up to 30 dB of nominal protection compared to a non-protected receiver and is classified as a commercial good for export control purposes. OEM7’s multi-constellation and multi-frequency capabilities offer resiliency through frequency diversity. In the event of heightened hostility, RoDAR steps in, providing active anti-jamming across two GNSS bands.
3. Galileo Open Service Navigation Message Authentication (OSNMA)
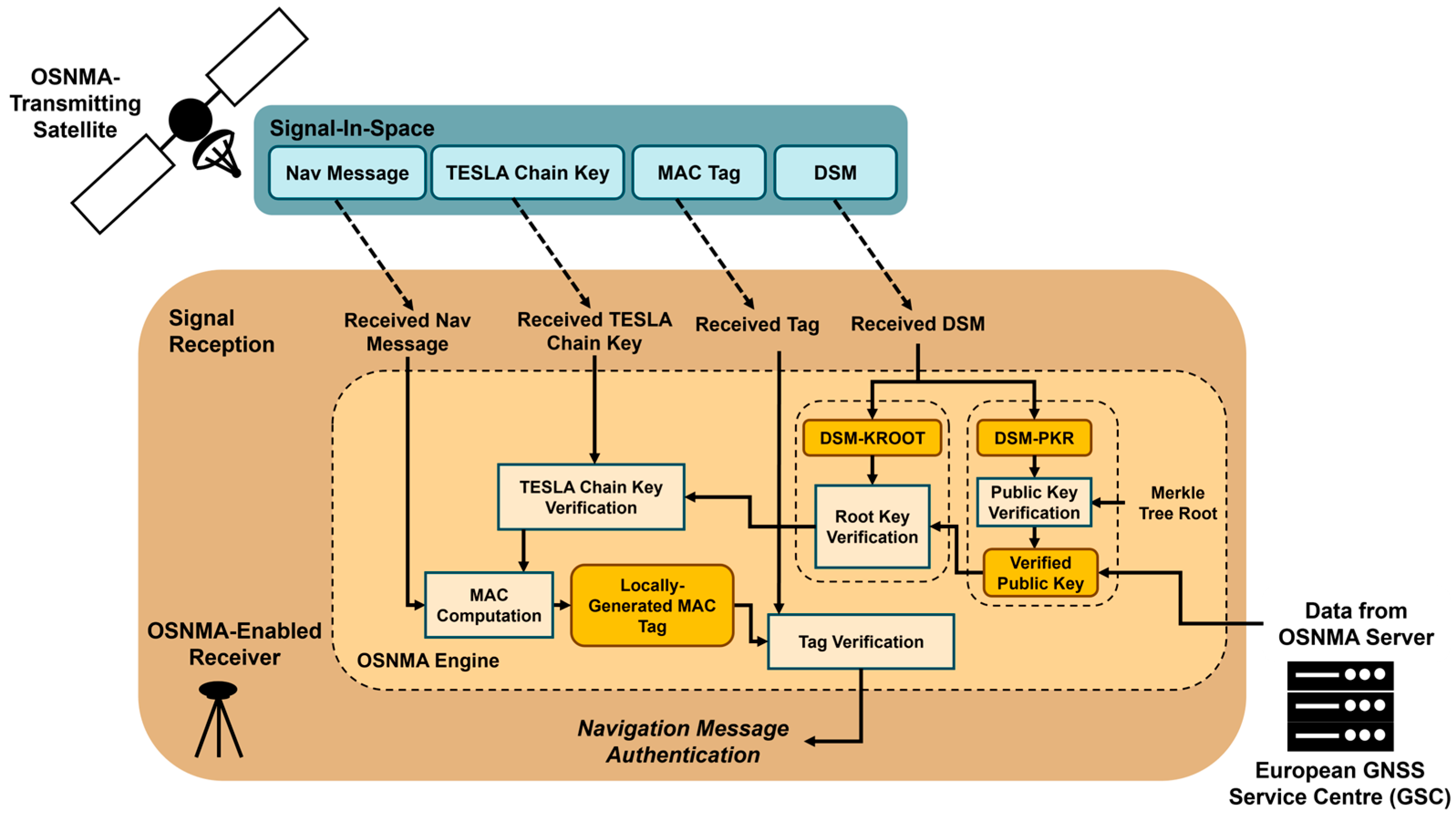
OSNMA provides Galileo users with cryptologic protection by ensuring that the navigation data received is from the system itself and has not been altered. The process is based on the Timed Efficient Stream Loss-tolerant Authentication (TESLA) protocol, where the authenticating key is broadcast with delays for all satellites, enabling auto- and cross-authentication of data from different satellites. The OSNMA data is broadcast within the reserved bits embedded in the odd page parts of a nominal Galileo E1B I/NAV message, consisting of an 8-bit Header and Root Key (KROOT) or HKROOT, and a 32-bit Message Authentication Code (MAC) and Key or MACK. During a nominal sub-frame, 15 pages are transmitted every 30 s to build up a set of 120-bit HKROOT and 480-bit MACK messages. HKROOT provides a Digital Signature Message (DSM) over a sequence of blocks comprising the Public Key Renewal (PKR) and Root Key (KROOT) information. MACK includes the chain key and authentication tags used to verify the authenticity of the navigation data [
12,
13]. An overview of the OSNMA process is shown in
Figure 2. The process is initialized by retrieving and verifying the public key and root key, depending on the stored information available at the receiver’s start. Once the root key is verified, the TESLA chain key and navigation message authentication stage is set, commencing by bootstrapping the TESLA chain key verification by the root key, leading to a steady state where the chain key is authenticated by its predecessor verified in the preceding subframe. The verified key takes the navigation data and replicates the authentication tags to be matched with those received from space and decides about the authenticity of the navigation message.
4. Jammertest 2023
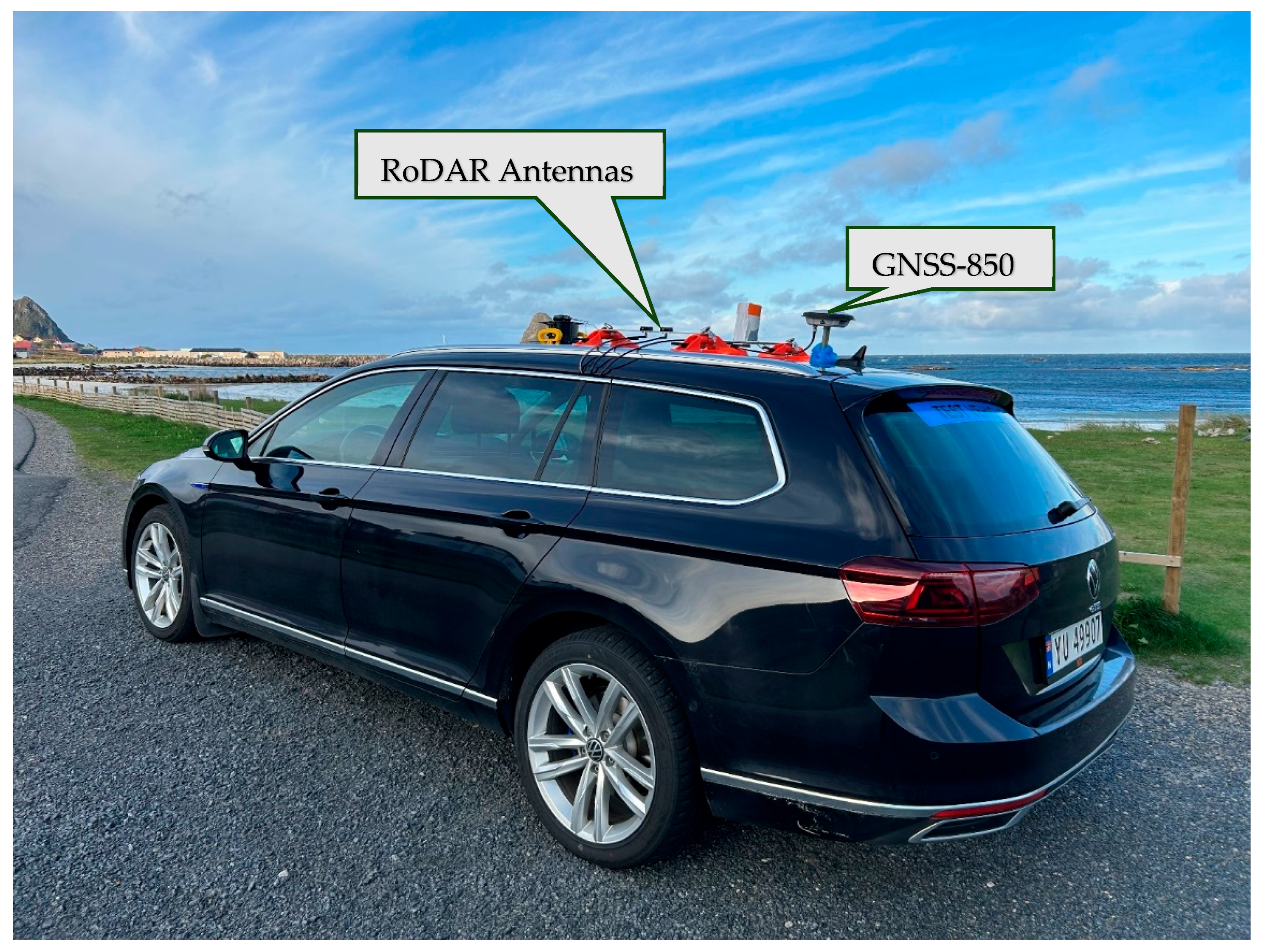
This section presents results from Jammertest 2023, a 5-day jamming and spoofing event held in September 2023 in Bleik, Norway. During the test, NovAtel OEM7 receiver cards embedded in PwrPak7 enclosures were investigated. RoDAR receivers, coupled to Hexagon|Antcom antennas, were mounted to a test vehicle as shown in
Figure 3. The PwrPak7 receiver connected to a geodetic-grade GNSS-850 antenna was used for spectrum monitoring and situational awareness, including jamming and spoofing detection. NovAtel’s ITK and SK logs were collected to analyze jamming and spoofing data sets in real-time and in post-processing. The receiver was configured for multi-frequency and multi-constellation operation. During the test, the PwrPak7 receiver tracked all available GNSS signals. The following sections present the test outcomes and receiver behavior under selected jamming and spoofing events, with detailed results from days 2-5 available in [
14]. This paper demonstrates jamming and spoofing detection and mitigation using GRIT in selected scenarios.
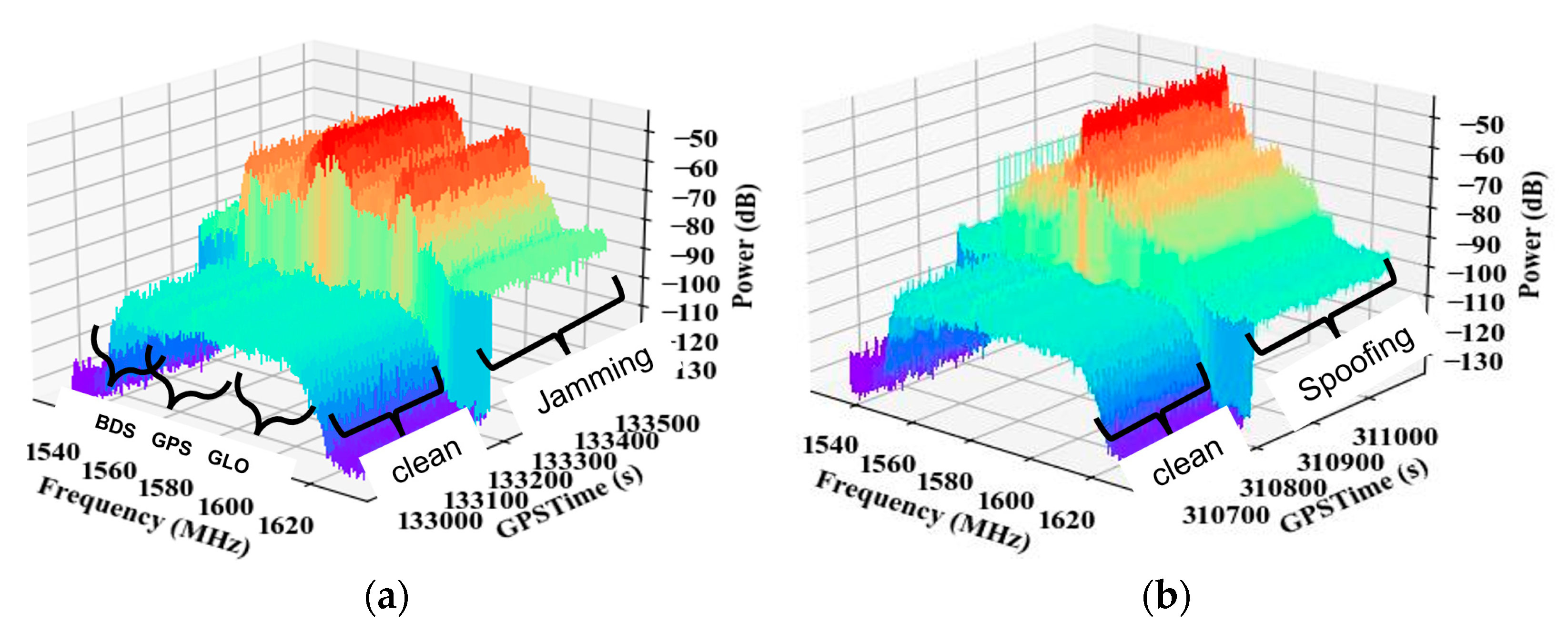
During the test, ITK logs were utilized to characterize interference, including jamming and spoofing attacks.
Figure 4a displays power spectral plots of the upper GNSS bands, including BDS B1, GPS L1 and GLONASS L1, illustrating a benign period followed by a jamming attack across all frequency bands.
Figure 4b shows power spectral plots of the upper GNSS bands under spoofing attack at the GPS L1 band.
4.1. RoDAR Performance
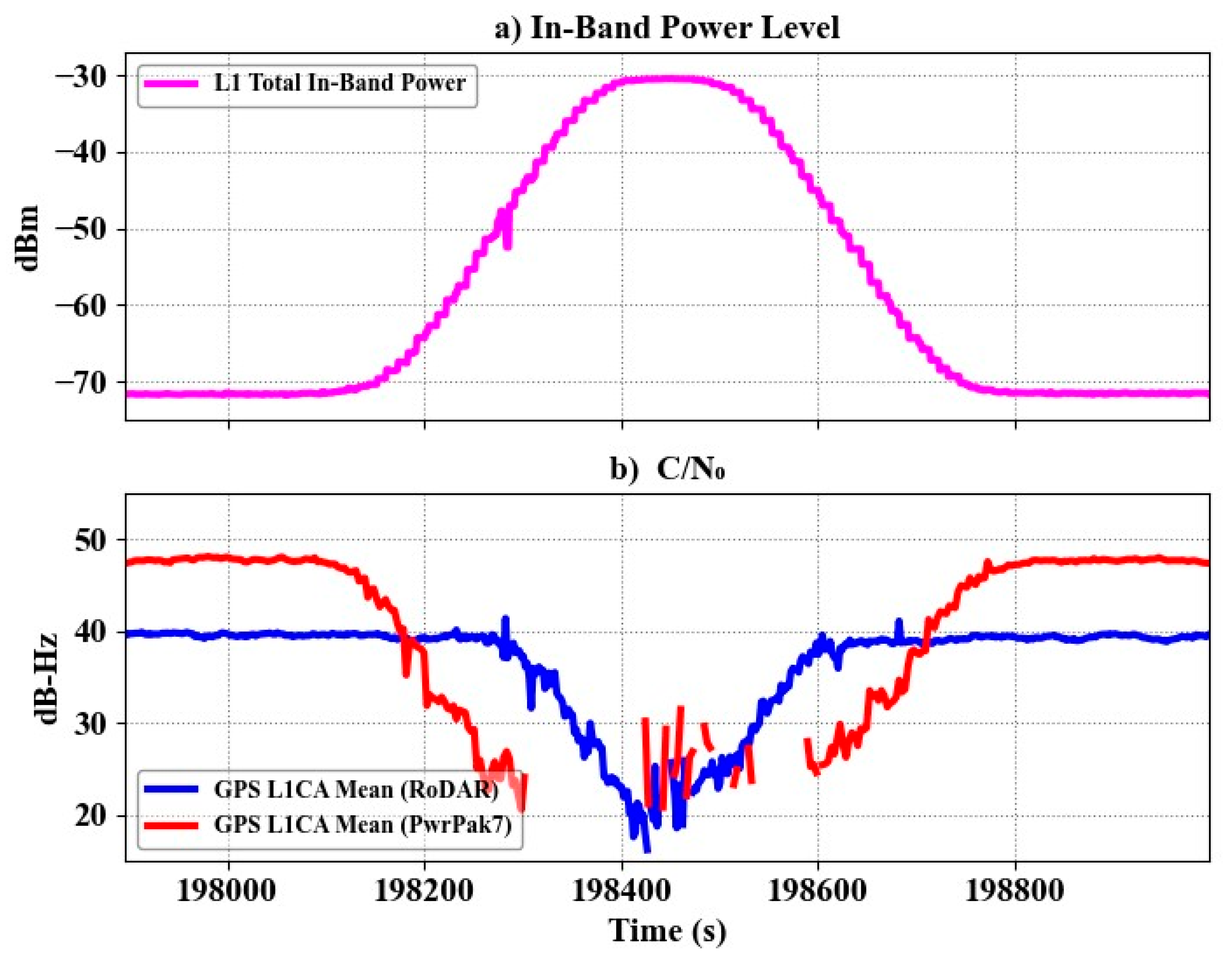
Figure 5a shows the total in-band power as a function of time at L1, L2 and L5 during day 2 events, as measured by the OEM7 receiver itself during the high-power ramp test. On day 2, the transmission plan included a high-power ramp jamming test in the morning and meaconing in the afternoon. As shown in
Figure 5a, the jammer power gradually increased and then decreased in a ramping power test on all GNSS bands. In the case of L1, the noise level is at −70 dBm when no jamming is present.
Figure 5b shows mean Carrier-to-Noise-density ratio (C/N
0) values of GPS L1CA for the PwrPak7 and RoDAR units. GPS L1CA and L5 are protected by RoDAR with active null-forming. The initial average C/N
0 of PwrPak7 is higher than RoDAR, because the GNSS-850 antenna paired with the PwrPak7 has a higher gain than the 1.2G antenna used with the RoDAR unit. By introducing the jammer, the PwrPak7 C/N
0 values fell about 20 dB and, eventually, the receiver dropped the signals, while RoDAR maintained continuous tracking.
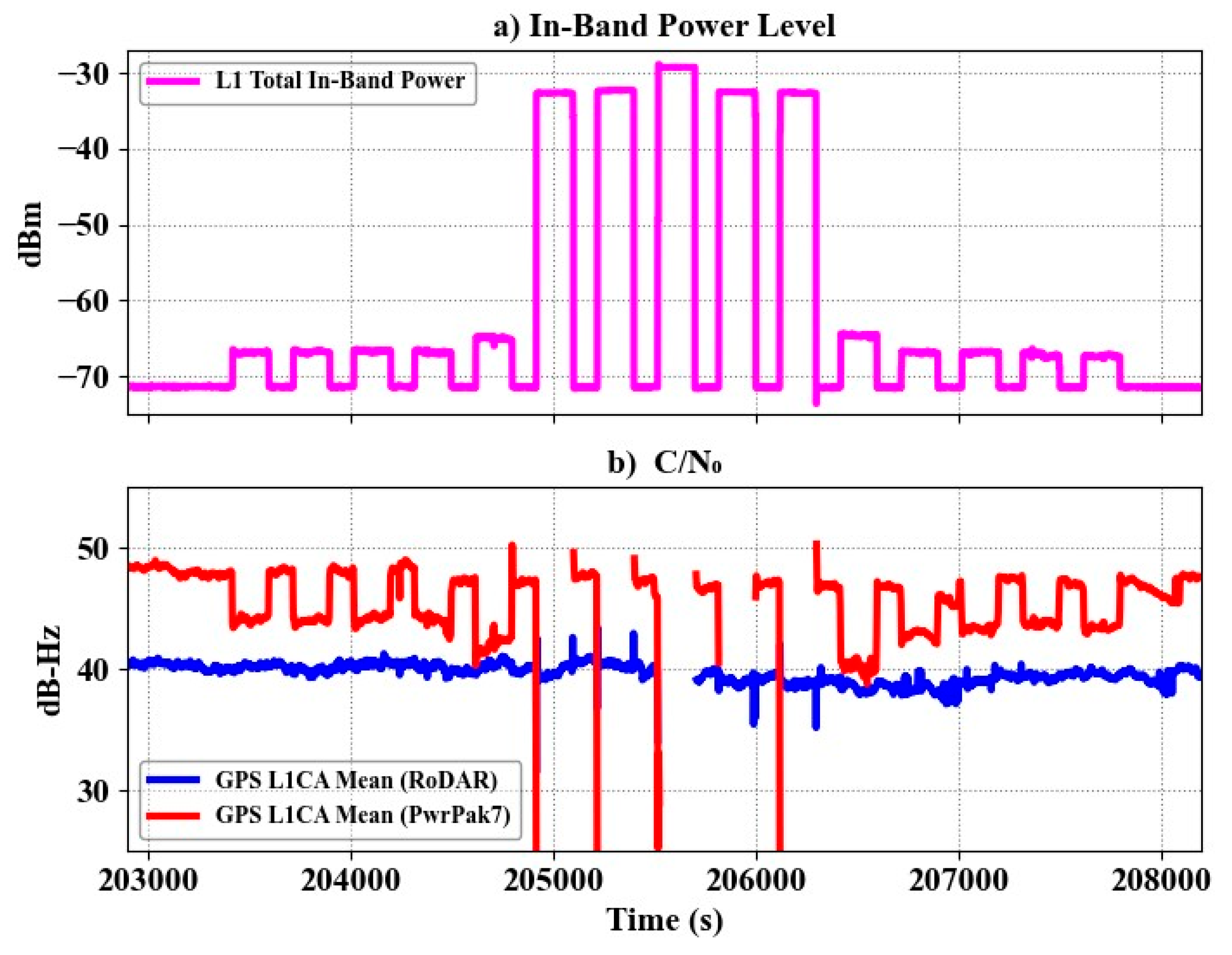
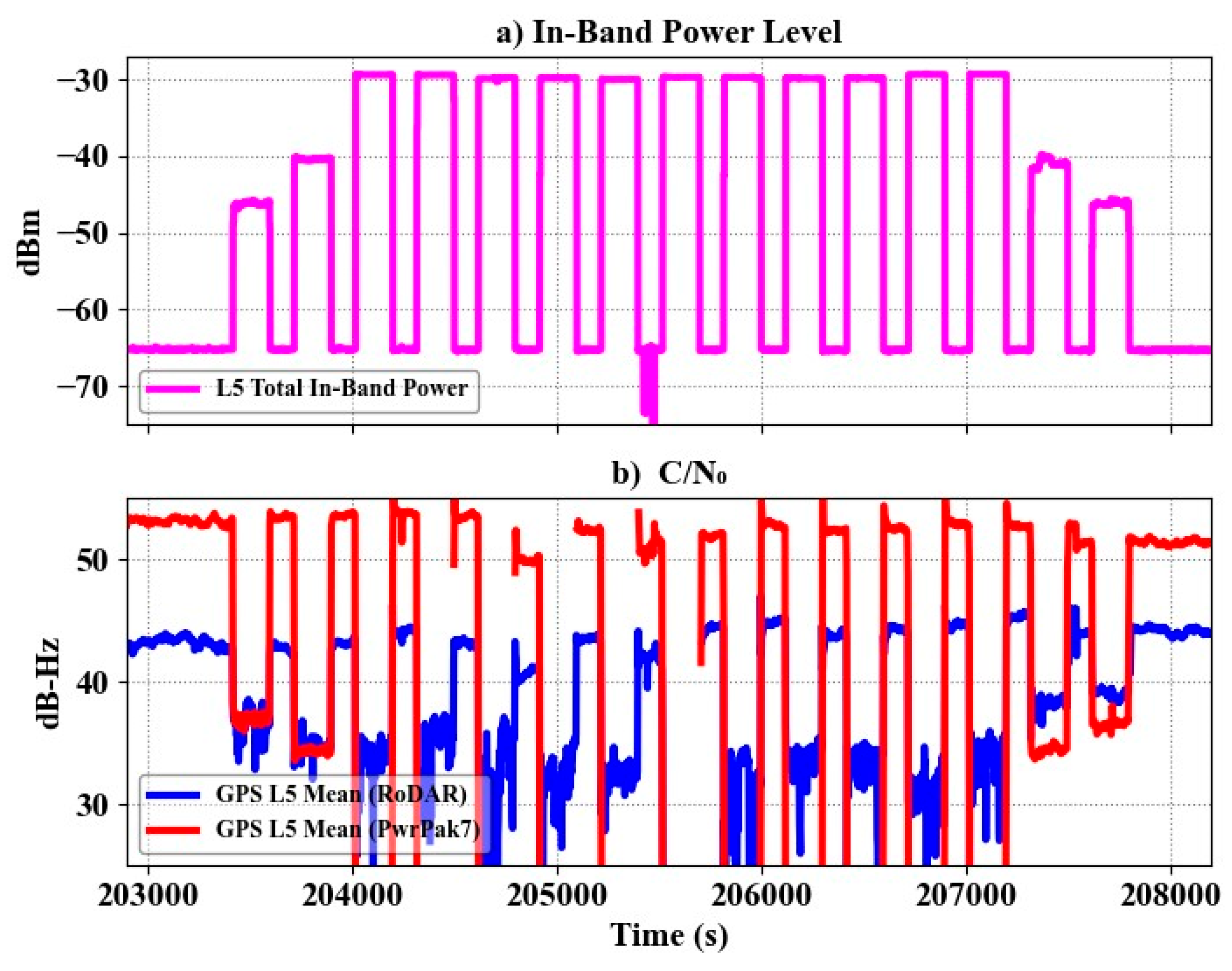
Figure 6 and
Figure 7 demonstrate the performance of RoDAR under several step-wideband jamming at the GPS L1 and L5 bands, respectively. As shown, the signal availability using RoDAR units is higher than that of the single-antenna PwrPak7 receiver.
4.2. Spoofing Detection and OSNMA Results
This section presents the results of the meaconing attack tests, which involved stationary meaconing with varying power and time exposure. The scenarios involved GNSS retransmission of real live-sky signals, resulting in a GNSS environment with incorrect positioning based on real satellite data, slightly time-delayed.
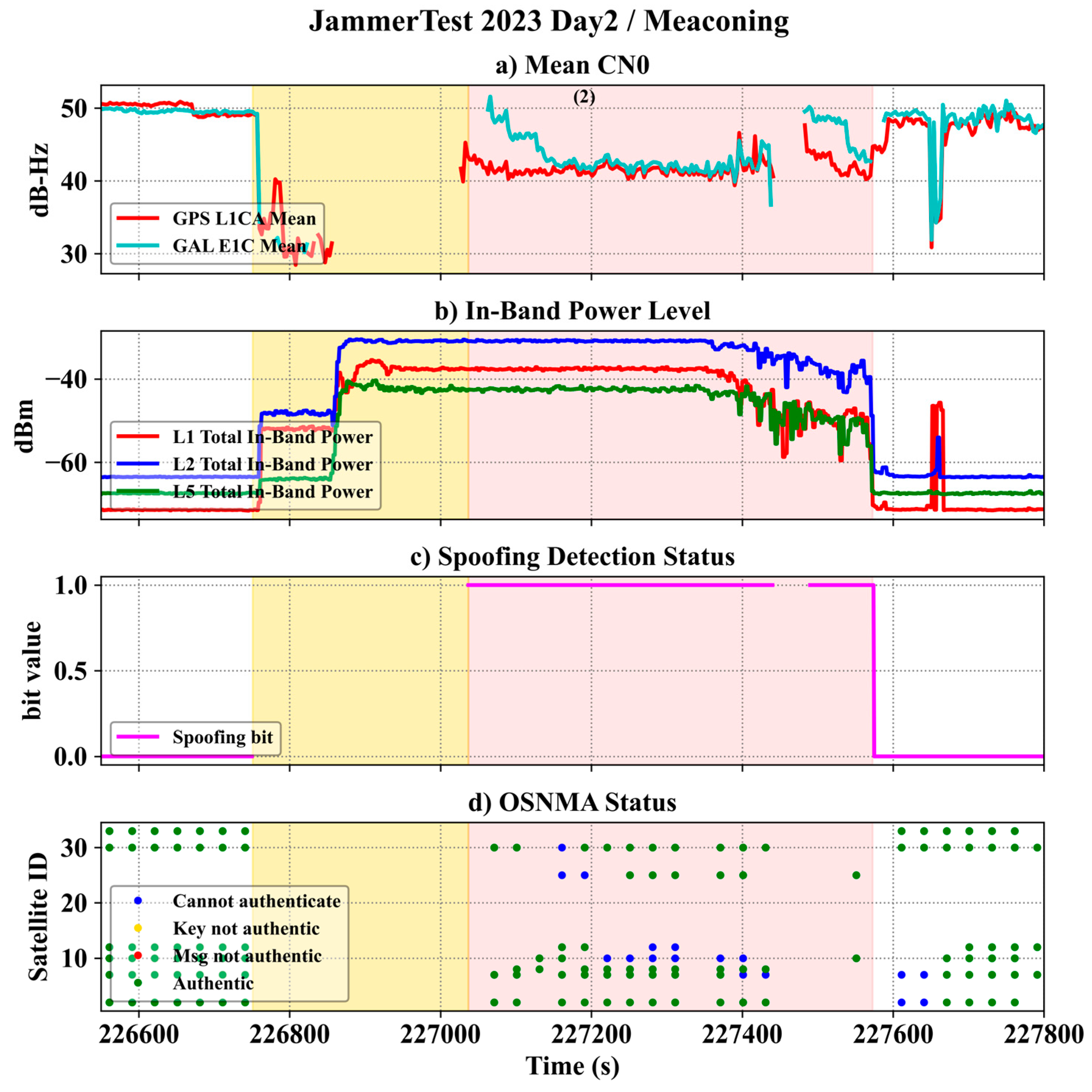
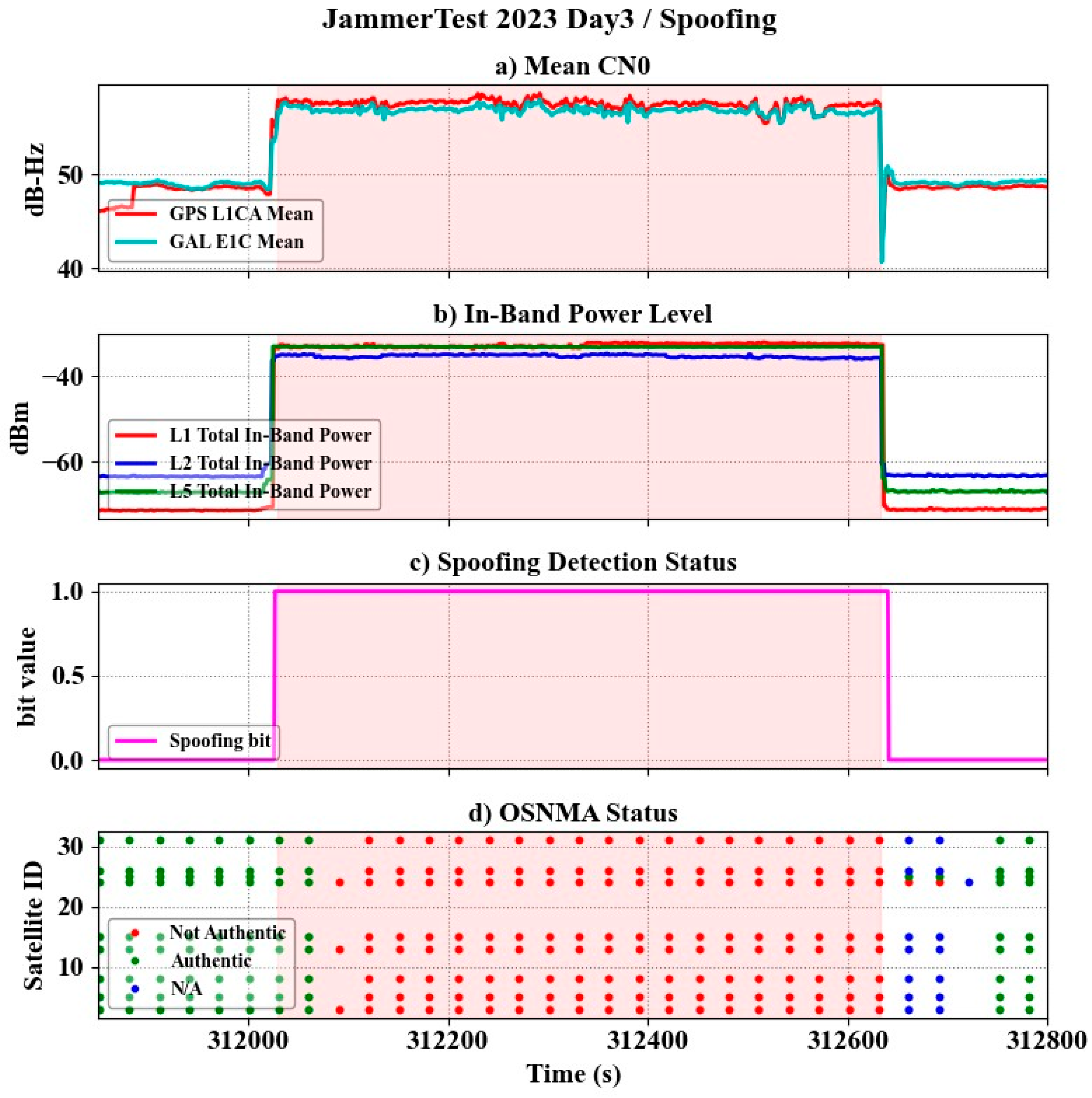
Figure 8 shows (a) average C/N
0 values (average of all tracked PRNs at a given epoch) of GPS L1CA and Galileo E1, (b) in-band power measured by ITK, (c) spoofing detection bit measured by SK and (d) Galileo E1 OSNMA detection results per pseudo-random noise (PRN).
The yellow and red shaded areas in the plots refer to the jamming and spoofing scenarios. The OSNMA results are color-coded. The blue dots refer to the epochs where authentication cannot be performed due to the lack of valid data required for OSNMA verification. This is usually the case in a cold start when the receiver is still waiting to receive data and set the crypto parameters. This can also be the case when OSNMA data reception is interrupted and does not include all authentication-required information. The red dots indicate that all data required for OSNMA (authenticating data and that to be authenticated) is available, but verification failed. This may happen when the navigation message is corrupted and cannot be corrected due to propagation environment or interference, or an unauthorized signal, with either an invalid navigation message or invalid OSNMA data, or both, is being received by the receiver. The green dots refer to the situation when all data required for OSNMA is available, and authentication is verified. The meaconing scenario started with a high-power jammer at all three GNSS bands. This is shown with the yellow area in
Figure 8 when the receiver was overwhelmed and could not track any signals at the L1 band. This is observable by comparing the results of
Figure 8a,b under the jamming event. After the jamming event, the meaconing attack was initiated, and the receiver started tracking replayed GNSS signals. As shown in
Figure 8b, the meaconing power gradually decreased at all bands. The SK spoofing detection module detected this attack as soon as there were enough tracking channels to provide position solutions (
Figure 8c).
Figure 8d shows the OSNMA results for this scenario. The receiver tracked seven Galileo E1 signals where navigation messages were reported authentic, except for the epochs where spoofing interference disrupted the reception of OSNMA-required data; thus, the receiver raised the blue flags. Although not designed for it, this exposed OSNMA’s vulnerability to meaconing attacks.
On day 3, a stationary spoofing attack generated a static false position or false route. Simulated signals were transmitted from the Bleik community house. This spoofing scenario included incoherent spoofing from a stationary spoofer using synthetic ephemerides. Incoherent spoofing is defined as the reception of transmitted simulated GNSS signals that are not code-phase aligned with live-sky signals. Generated spoofing scenarios used satellite ephemerides different from live-sky satellites. Simulated signals used one or more constellations and one or more signal bands.
Figure 9 shows different metrics and detection results from the spoofing scenario. The scenario started with a high-power spoofing attack. The high-power spoofer increased the input power by about 30 dB at all GNSS bands. The average C/N
0, as shown in
Figure 9a, was increased by about 8 dB. The SK spoofing detection module immediately detected this attack as soon as the receiver tracked GNSS signals. In this scenario, the OSNMA data field was filled by an artificial pattern of repeated “0” and “1” bits; therefore, the TESLA chain keys were not verified, and, consequently, the OSNMA classified this attack as not authentic (
Figure 9d). As expected, under the nominal operation of OSNMA, there is a lag of two subframes (or 60 s) in navigation message authentication [
12], as the receiver needs to wait for the authentication key embedded in the upcoming subframe to authenticate navigation data from the preceding epoch, which should be fine in most positioning applications given the validity of navigation messages over time. At the end of this scenario, OSNMA restarted authenticating the navigation message and the SK-based spoofing detection flag was set to zero, indicating that the spoofing was not present anymore.
5. Summary and Conclusions
NovAtel’s GRIT features were investigated during the Norwegian Jammertest 2023, across a variety of jamming and spoofing scenarios. GRIT included interference monitoring and characterization (i.e., ITK), receiver-based spoofing detection (i.e., SK) modules and a Robust dual-antenna receiver (RoDAR). Galileo navigation message authentication using the OSNMA prototype implementation was also investigated. The spoofing attacks included meaconing, matched-power and high-power scenarios. Actual and synthesized navigation data were generated, which enabled testing and verification of the OSNMA unit. These tests revealed accurate spoofing detection results using SK in real-world, over-the-air conditions. The onboard spoofing detection unit detected all the spoofing scenarios, including meaconing, matched-power and high-power spoofing attacks at single and multiple bands. The experimental results in this trial demonstrated RoDAR’s interference mitigation capabilities compared to the single-antenna PwrPak7 receiver under jamming and spoofing attacks. In the case of jamming, RoDAR was able to withstand 15–25 dB more jamming power than the single-antenna receiver in terms of position availability and accuracy. This evaluation highlights the effectiveness of a multi-layer protection strategy, where the integration of NovAtel’s ITK, SK and RoDAR solutions, along with the OSNMA feature, collectively enhances GNSS resilience against a diverse range of threats.
Author Contributions
A.B., A.P., I.T. and S.K. processed the data and contributed to the writing of the manuscript. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
Authors Ali Broumandan, Ali Pirsiavash, Isabelle Tremblay and Sandy Kennedy were employed by Hexagon | NovAtel. The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Jafarnia-Jahromi, A.; Broumandan, A.; Nielsen, J.; Lachapelle, G. GPS vulnerability to spoofing threats and a review of antispoofing techniques. Int. J. Navig. Obs. 2012, 2012, 127072. [Google Scholar] [CrossRef]
- Pirsiavash, A.; Broumandan, A.; Lachapelle, G. Two-dimensional signal quality monitoring for spoofing detection. In Proceedings of the ESA/ESTEC NAVITEC 2016 Conference, Noordwijk, The Netherlands, 14–16 December 2016; 12p. [Google Scholar]
- Pirsiavash, A. Receiver-Level Signal and Measurement Quality Monitoring for Reliable GNSS-Based Navigation. Ph.D. Thesis, Department of Geomatics Engineering, University of Calgary, Calgary, AB, Canada, 2019. [Google Scholar]
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Borio, D.; Gioia, C. A Dual-antenna spoofing detection system using GNSS commercial receivers. In Proceedings of the ION GNSS+ 2015, Tampa, FL, USA, 14–18 September, 2015. [Google Scholar]
- Vagle, N.; Broumandan, A.; Lachapelle, G. Multiantenna GNSS and inertial sensors/odometer coupling for robust vehicular navigation. IEEE Internet Things J. 2018, 5, 4816–4828. [Google Scholar] [CrossRef]
- Jafarnia-Jahromi, A.; Broumandan, A.; Nielsen, J.; Lachapelle, G. Pre-despreading authenticity verification for GPS L1 C/A signals. J. Inst. Navig. 2014, 61, 1–11. [Google Scholar] [CrossRef]
- Broumandan, A.; Curran, J.T. GNSS spoofing detection in covered spoofing attack using antenna array. In Proceedings of the International Technical Symposium on Navigation and Timing (ITSNT), Toulouse, France, 14–17 November 2017. [Google Scholar]
- Pirsiavash, A.; Broumandan, A.; Lachapelle, G.; O’Keefe, K. Detection and classification of GNSS structural interference based on monitoring the quality of signals at the tracking level. In Proceedings of the 6th ESA International colloquium of Scientific and Fundamental Aspects of Galileo, Valencia, Spain, 25–27 October 2017. [Google Scholar]
- Wesson, K.D.; Gross, J.N.; Humphreys, T.E.; Evans, B.L. GNSS signal authentication via power and distortion monitoring. IEEE Trans. Aerosp. Electron. Syst. 2017, 54, 739–754. [Google Scholar] [CrossRef]
- Broumandan, A.; Kennedy, S.; Schleppe, J. Demonstration of a multi-layer spoofing detection implemented in a high precision GNSS receiver. In Proceedings of the 2020 IEEE/ION Position, Location and Navigation Symposium (PLANS), Portland, OR, USA, 20–23 April 2020. [Google Scholar]
- Galileo Open Service Navigation Message Authentication (OSNMA) Receiver Guidelines. Available online: https://www.gsc-europa.eu/sites/default/files/sites/all/files/Galileo_OSNMA_Receiver_Guidelines_v1.3.pdf (accessed on 11 December 2025).
- Galileo Open Service Navigation Message Authentication (OSNMA) Signal-In-Space Interface Control Document (SIS ICD). Available online: https://www.gsc-europa.eu/sites/default/files/sites/all/files/Galileo_OSNMA_SIS_ICD_v1.1.pdf (accessed on 11 December 2025).
- Broumandan, A.; Pirsiavash, A.; Trembley, I.; Kennedy, S. Hexagon │ NovAtel’s jamming and spoofing detection and classification performance during the Norwegian JammerTest 2023. In Proceedings of the ION ITM Conference 2024, Long Beach, CA, USA, 22–25 January 2024. [Google Scholar]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).