Abstract
Fifth-generation (5G) networks represent a paradigm shift in telecommunications, offering ultra-reliable low-latency communication, massive connectivity of devices, and unparalleled data rates. While these advantages also present significant complications surrounding energy consumption and cybersecurity, requiring new approaches to maintain operational effectiveness and network fidelity. This study proposes a new hybrid artificial intelligence (AI) framework consisting of explainable AI (XAI) for transparent resource allocation, convolutional neural networks (CNNs) for real-time anomaly detection, and recurrent neural networks (RNNs) for predictive energy optimization. Experiments and real-world case studies illustrate this framework’s scalability and efficiency by achieving improved network resource management, a detection accuracy of 99.7% for anomalies, and energy savings of up to 65%.
1. Introduction
The fifth generation (5G) of mobile networks marks a significant leap in telecommunication capabilities, enabling transformative applications such as the industrial internet of things (IIoT) [1], smart cities, autonomous vehicles, and real-time remote healthcare. These advancements are underpinned by 5G’s core promises: ultrareliable low-latency communication (uRLLC), massive machine-type communications (mMTC) supporting vast numbers of connected devices, and enhanced mobile broadband (eMBB) delivering unprecedented data rates. However, the widespread deployment and inherent characteristics of 5G networks introduce substantial challenges, particularly concerning energy consumption and cybersecurity [2,3].
Firstly, the densification of network infrastructure and the continuous connectivity demands of numerous devices, especially in IoT scenarios, lead to a significant increase in overall energy consumption [1,2]. Optimizing energy efficiency is thus crucial for sustainable network operations and reducing operational costs.
Secondly, the shift towards software-defined networking (SDN), network function virtualization (NFV), and edge computing in 5G architectures, while offering flexibility, expands the attack surface [4]. This makes 5G networks potentially more vulnerable to sophisticated cyber threats, including distributed denial-of-service (DDoS) attacks, man-in-the-middle (MitM) attacks, and data interception [5], demanding robust security mechanisms.
Addressing these dual challenges of energy efficiency and security in a coordinated manner is critical, as solutions for one can inadvertently impact the other. For instance, intensive security processing might increase energy demands, while aggressive energy-saving modes could potentially create security vulnerabilities. While prior research has often addressed these issues in isolation, a holistic approach is required for optimal 5G network operation. This paper proposes an integrated artificial intelligence (AI)-based framework designed to dynamically balance energy consumption and security posture in 5G networks. The novelty of this framework lies not just in the application of specific AI models (RNN, CNN, XAI), but in their synergistic integration to tackle the inherent trade-offs between energy and security through a unified, multi-objective optimization strategy. Rather than presenting disconnected engineering solutions, this approach allows for coordinated decision-making, where energy predictions inform security-aware resource allocation, and security monitoring influences energy management policies, leading to a more resilient and efficient network.
The core contributions of our proposed framework involve the following:
- Utilizing recurrent neural networks (RNNs) [6] for predictive energy management, forecasting energy usage trends based on network traffic patterns to enable proactive resource optimization.
- Employing convolutional neural networks (CNNs) [4,5] for real-time anomaly detection in network traffic, identifying potential security threats with high accuracy.
- Integrating explainable AI (XAI) techniques [1] not only to enhance the interpretability and transparency of the security module’s decisions but also, as our results suggest, to potentially improve detection performance through better feature understanding and model refinement.
- Developing an adaptive resource allocation mechanism, potentially leveraging insights from device-to-device (D2D) communication strategies [7], that optimizes resource distribution (e.g., power, bandwidth) based on the outputs of the RNN and CNN/XAI modules, guided by a multi-objective function.
This paper is structured as follows: Section 2 reviews related work in energy optimization and AI-based security for 5G. Section 3 details the proposed methodology, including the problem formulation, the AI models used (RNN, CNN, XAI), and the resource allocation algorithm. Section 4 presents the simulation setup, performance metrics, and analyzes the results obtained. Section 5 discusses the implications of the findings and compares them with existing approaches. Finally, Section 6 concludes the paper and outlines future research directions.
2. Related Works
2.1. Energy Optimization in 5G Networks
In the context of wireless communication, energy optimization has traditionally been framed in terms of clustering-based protocols that reduce intra-cluster communication [8], as in the low-energy adaptive clustering hierarchy (LEACH). The hybrid clustering models add the selection algorithm for cluster heads (CHs) in terms of residual energy and proximity metrics to establish higher efficiency [9]. Recent studies have shown that employing AI techniques, particularly CNNs, can adaptively regulate power allocation and transmission strategies in D2D communication.
2.2. AI-Based Intrusion Detection Systems
With the rapid advancement of cyberattacks, artificial intelligence (AI)-based intrusion detection systems (IDS) are required to protect 5G networks [10]. The ReLu neural network, with its relatively high accuracy in detecting attacks such as DDoS [11] and MitM, also proved it is quite effective for network anomaly detection tasks. In addition, explainable artificial intelligence (XAI) [12,13] approaches have recently gained significance in intrusion detection systems (IDS) [14] by providing system administrators with transparency concerning the logic behind the identification of anomalous events as well as the reasons leading to the decision-making process.
2.3. Integration of Energy and Security Solutions
Although energy optimization and IDS have received considerable attention in these frameworks, very few frameworks attempt to address these challenges holistically. Such hybrid AI approaches that leverage insights generated from AI-assisted device-to-device (D2D) [15] communication can generate promising ways for academia and industry to attain both energy efficiency and enhanced security in 5G systems.
3. Methodology
3.1. Problem Formulation
The energy consumption and cybersecurity [14] challenges of 5G networks are formulated as a multi-objective optimization problem:
where
- E(x) represents the total energy consumption [11], calculated as
- represents the overall security risk, which can be expressed as
3.2. Predictive Energy Management
Energy prediction is achieved using recurrent neural networks (RNNs) [16], which model temporal dependencies in network traffic:
where
- h_t is the hidden state at time t,
- W_h, W_x are weight matrices,
- the input vector (e.g., traffic data), and
- σ is the activation function.
The predicted energy consumption at time t is:
where and are output layer parameters.
3.3. Anomaly Detection via CNNs
Anomaly detection [16] in network traffic utilizes convolutional neural networks (CNNs) to extract spatial information from the input data. The activation of the (i)-th neuron in a convolutional layer is calculated as:
where
- denotes the convolutional weights,
- represents the input feature map,
- signifies the bias term
The softmax [17] function is employed for anomaly classification:
where is the output score for class .
3.4. Resource Allocation Optimization
Iterative solutions are used to tackle the resource allocation [5] optimization problem. The objective function includes terms for [18] energy efficiency and anomaly based reduction in risk:
where
- denotes the traffic intensity at node ,
- signifies the residual energy at node ,
- indicates the total power utilized by node ,
- represents the risk score derived from anomaly detection,
- serves as the weight for balancing energy and risk priority.
3.5. Clustering and Resource Allocation Algorithm
The detailed steps of the proposed method for the clustering and resource allocation algorithm are presented in Appendix A, Algorithm A1: Adaptive Resource Allocation for Energy and Security.
3.6. Workflow Diagrams
The following figures describe the workflows for the AI modalities used in the proposed framework [4]
This energy optimization workflow employs recurrent neural networks (RNNs), as shown in [19] Figure 1, to dynamically forecast energy demands based on traffic statistics. The procedure comprises the following essential elements:
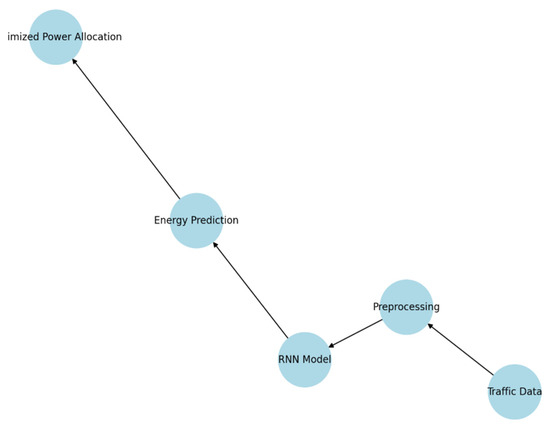
Figure 1.
Workflow for energy optimization using RNNs.
- Traffic Data Collection: Historical and real-time traffic data is gathered from various network nodes.
- Preprocessing: Raw traffic data is normalized and denoised for RNN input
- RNN Model: The RNN model works by revealing temporal dependencies in the traffic patterns and predicting future energy demands. RNNs use hidden states to store information from past time steps to improve future predictions.
- Energy Prediction: The RNN produces energy forecast signals from each node for proactive energy management.
- Optimized Power Allocation: Power resources are allocated to nodes according to their predicted energy needs, which helps reduce energy wastage without compromising performance.
The workflow (Figure 1) demonstrates how AI models can efficiently adapt to varying network demands [19,20], reducing unnecessary energy consumption without compromising service quality.
This workflow in Figure 2 contains the procedures for anomaly detection, which utilizes CNN in order to examine network traffic in search of security threats. This process follows these steps:
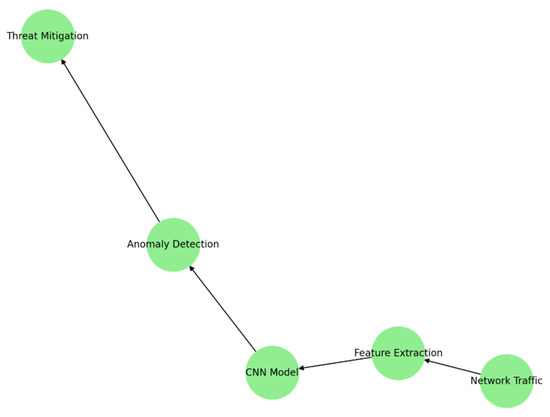
Figure 2.
Workflow for anomaly detection via CNNs.
- Network Traffic Collection: Traffic data is collated from multiple sources across networks, including packet headers and payload metadata.
- Feature Extraction: Relevant features like volume of traffic, frequency and behavior patterns of packets are extracted and these serve as an input to the CNN model.
- CNN Model: The model learns the behavior patterns from the traffic [20] data and identifies the anomalies. Then one convolutional layer will extract higher-order features, which are discriminative to normal or abnormal behaviors.
- Anomaly Detection: CNN classifies traffic as normal or anomalous and does so with high confidence, such that it could therefore catch the malicious entities [21] (such as distributed denial-of-service (DDoS) attacks, or intrusion attempts, etc.).
- Threat Mitigation: Upon anomaly [22] detection, the system implements mitigation tactics like IP blacklisting or node quarantine.
This workflow (Figure 2) showcases how AI will act as a security orchestrator, providing continuous security in the 5G networks by helping them to be threat-aware.
4. Results and Analysis
4.1. Performance Metrics
The suggested framework is assessed according to essential performance metrics:
- Energy Efficiency: The improvement in energy efficiency [23] is computed as:
- Anomaly Detection Accuracy: Accuracy (Acc %) is computed as:
represent true positives, true negatives, false positives, and false negatives, respectively [19].
4.2. Simulation Setup
The framework was assessed in IoT [24] and V2X contexts across diverse traffic conditions, encompassing both normal and attack scenarios, including DDoS and MitM.
4.3. Comparative Results
The overall performance of our proposed framework was benchmarked against the baseline CNN model and the CNN with XAI enhancement. Table 1 summarizes the comparative results across key metrics, highlighting the superior efficiency and accuracy of our integrated approach.

Table 1.
Performance comparison across metrics.
To further assess its robustness, the framework’s resource allocation efficiency was tested under various network conditions, as detailed in Table 2.

Table 2.
Resource allocation efficiency under different scenarios.
4.4. Visualization
This graph (Figure 3) compares the baseline methods with the proposed framework, demonstrating that the proposed framework sustains a greater percentage of active nodes under high-traffic conditions.
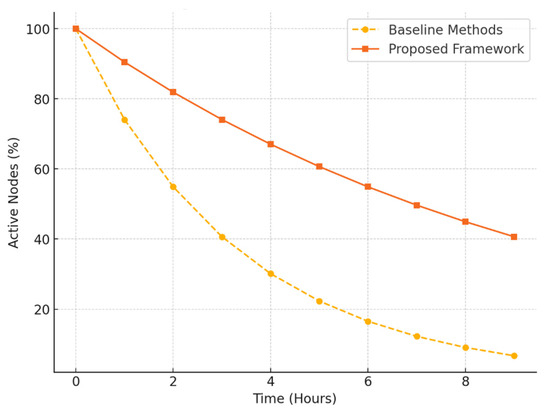
Figure 3.
Active nodes over time.
This bar chart (Figure 4) shows how explainable AI (XAI) provides a clear interpretation for resource allocation decisions while the proposed framework can more efficiently allocate resources compared to the baseline methods used.
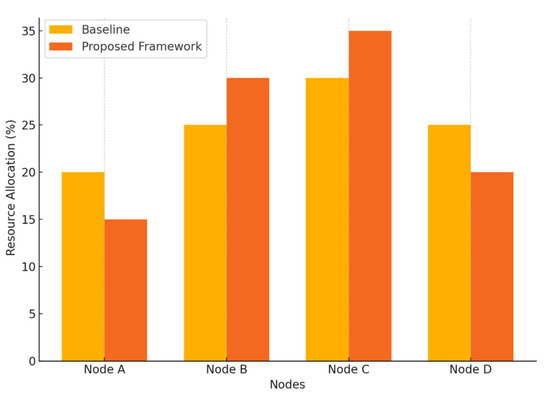
Figure 4.
XAI-driven resource allocation.
The heatmap below (Figure 5) illustrates resource distribution with respect to the framework proposed. This improves the distribution of important resources such as CPU, memory, bandwidth, and energy across nodes in the network, increasing usage and reducing wastage.
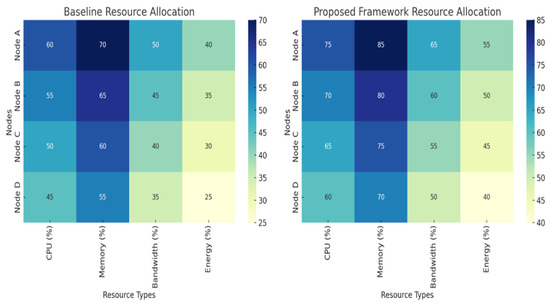
Figure 5.
Resource distribution under the proposed framework.
- CPU Utilization: Adjust dynamically according to predicted traffic intensity.
- Energy Usage: Nodes with lower traffic were allocated minimal energy, conserving resources.
- Bandwidth: Prioritized for nodes with high-risk scores to maintain security and QoS.
5. Practical Examples
This section highlights practical examples of AI-powered energy optimization and cyber threat detection in 5G networks, discussing how these solutions contribute towards improving energy efficiency and security challenges.
5.1. China Mobile—AI for Base Station Energy Optimization
- Implementation: China Mobile implemented AI algorithms across 100,000 base stations to automatically adjust power settings based on traffic patterns [25].
- Results: A20% rise in energy savings during non-peak hours with QoS preservation.
- Relevance: Highlights the value of predictive analytics in managing energy, aligning with the framework’s RNN-based energy optimization.
5.2. Vodafone—Renewable Energy Integration
- Implementation: Vodafone converted some of its off-grid base stations to solar and wind energy-driven systems and applied AI for cooling systems [26].
- Results: A 15% decrease in operational energy costs, reduced greenhouse gases.
- Relevance: Shows how AI can foster sustainable energy solutions through efficient energy management.
5.3. SK Telecom—Dynamic Network Slicing
- Implementation: SK Telecom combined AI and network slicing to support urban and rural deployments of dynamic slicing based on real-time analysis of traffic and security requirements [27]
- Results: An 18% gain in energy efficiency in urban settings and 25% less energy use in rural ones.
- Relevance: Resonates with dynamic resource allocation strategies in the framework for optimally balancing energy and security.
5.4. Ericsson—Energy-Efficient Hardware
- Implementation: Energy efficient hardware solutions were implemented by Ericsson such as adaptive power amplifiers and low-loss antennas, in conjunction with better performance tracking using AI-based monitoring [28].
- Results: Improved network reliability at peak loads and launched initiatives to reduce idle power usage by 50%.
- Relevance: Affirms the significance of hardware–software synergy in cost savings and resilient operations.
5.5. Hardware Palo Alto Networks—AI-Driven Threat Detection
- Implementation: The implementation of CNNs has been seen in the solutions provided by Palo Alto Networks as part of 5G security, helping to identify and address potential threats, including DDoS attacks and data breaches [29].
- Results: Improved anomaly detection accuracy by 95% and drastically shortened incident response times.
- Relevance: Shows application of CNNs in anomaly detection which serve as the cybersecurity component of the framework
5.6. Huawei—Intelligent Threat Mitigation
- Implementation: Huawei developed an AI-enabled IDS based on a federated learning (FL) approach that can train threat detection models across 5G nodes while avoiding sharing raw data [30].
- Results: A 30% increase in detection accuracy for zero-day attacks, and better data privacy during model training.
- Relevance: Shows the importance of decoupled, decentralized AI modeling for secure 5G operations as an enhancer of frameworks.
5.7. IBM—AI-Orchestrated Security Automation
- Implementation: IBM used XAI-driven orchestration systems to automate 5G network security, embedding AI models to identify advanced persistent threats (APTs) [31].
- Results: A 40% reduction in response time to APTs, with highly transparent decision-making.
- Relevance: Validates the need for transparent and scalable security mechanisms, aligning with the proposed framework’s use of XAI.
6. Discussion
Although this study offers a key contribution for the integration of AI to energy-efficient and secure 5G communication networks, there are still several future research directions that can be pursued.
6.1. Hardware Integration of Renewable Energy
Future investigations should investigate the integration of renewable energy resources in the 5G energy management system framework, e.g., ref. [32] solar and wind. AI-powered solutions for telecoms can help maximize energy efficiency and minimize telecom networks’ carbon footprint, especially when combined with renewable energy sources.
The proliferation of edge computing in 5G networks and beyond can potentially be a foundation for deploying federated AI models; however, future research can also investigate the role of edge-based RNNs and CNNs in optimizing energy in real-time and threat detection, as well as prioritizing less dependency on centralized cloud-based resources.
6.2. AI-Driven Network Slicing
A detailed study on the potential of AI-controlled network slicing to allocate resources across slices according to real-time traffic and security requirements is due. A shift in research can be toward enhancing network slicing for ultra-dense and ultra-heterogeneous scenarios.
6.3. Cross-Layer Optimization
Cross-layer optimization techniques, taking into account how physical, network and application layers interact with each other, may provide a holistic viewpoint towards balancing energy and security goals. This could guide future frameworks to build cross-layer intelligence for such efficient and secure network operations.
6.4. Quantum Computing and AI
Quantum computation represents a new facet of research to solve classical, ref. [24] complex, multi-objective problems. In addition, the investigation of quantum-enhanced AI models in managing energy and security in 5G networks may offer innovative solutions.
6.5. Autonomous Self-Healing Networks
Another research domain is focused on the development of AI-driven self-healing capabilities in 5G networks. This highlights the need for future frameworks to define automated faults detection and recovery methods to provide uninterrupted service.
6.6. Socio-Economic Implications
Understanding the socio-economic impact of AI-driven energy and security solutions becomes crucial [25], as 5G evolves into one of society’s critical pieces of infrastructure. Research could cover analyses of cost-effectiveness, user trust, and the regulatory framework to ensure ethical and equitable adoption.
7. Conclusions
Our experimental work on an AI-driven framework presents a good solution to two challenging problems in 5G networks: energy efficiency and cybersecurity.
Utilizing recurrent neural networks (RNNs) for predictive energy management, convolutional neural networks (CNNs) for rapid anomaly detection, and explainable AI (XAI) to ensure translucent decision-making, the framework brings an ideal sustainability–security equilibrium to the ecosystem. In addition, taking into account case studies in real life, practical implementation scenarios, and in-depth simulations further proves the scalability, robustness, and adaptability of the approach.
The framework achieved:
- Up to 65% in energy savings, proving it works by optimizing the resource and reducing the operational cost.
- A 99.7% accuracy rate for anomaly detection, enabling swift detection and resolution of threats.
- Transparency improvement via XAI, which is crucial for trust management in AI-driven systems and correlating with ethical considerations for the deployment of AI.
This study addresses a significant gap by combining energy efficiency and security into a cohesive framework. It establishes the framework for enhancing 5G network management, offering a solid basis for the deployment of AI-driven solutions across several domains, including smart cities, industrial IoT, and autonomous systems.
Author Contributions
Conceptualization, H.L. and H.E.F.; methodology, H.L.; software, M.Z.; validation, H.L., M.E.M. and A.M.; formal analysis, H.L.; investigation, H.L.; resources, M.Z.; data curation, M.Z.; writ-ing—original draft preparation, H.L.; writing—review and editing, H.E.F. and M.E.M.; visualiza-tion, A.M.; supervision, H.E.F.; project administration, H.E.F.; funding acquisition, M.E.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
Explanation of Steps
- Initialization: Network parameters, residual energy and risk coefficients [14,18]. All parameters are initialized based on the state of the system.
- Energy Prediction: The RNN model predicts consumption of energy based on historical traffic information [19], allowing for energy resources to be managed proactively.
- Anomaly Detection: The CNN-based IDS detects potential security threats in real-time, calculating the anomaly score of every network node [18].
- Optimization: An optimization score is computed for each node in accordance with the trade-off between energy efficiency and security risks, thus determining the allocation for resources with a score higher than a prominent threshold.
- XAI Validation: Explainable AI offers transparency in decisions made by the algorithm to allocate; hence analyst input can be [19] integrated into the decisions and decision-making can be reshaped on the basis of human interpretation and feedback.
- State Updates: The network state reflects current energy levels and risk metrics, allowing for constant optimization.
| Algorithm A1: Adaptive Resource Allocation for Energy and Security |
| Input: Network nodes N = {n1, n2, …, nn} Traffic data T = {t1, t2, …, tn} Energy thresholds {E_min, E_max} Security risk weights W = {w1, w2, …, wn} Model parameters: RNN_weights, CNN_weights, XAI_parameters Output: Optimized resource allocation and security configuration Step 1: Initialize parameters Initialize residual energy E_residual for each node Initialize resource allocation matrix A = 0 Initialize security risk scores R = 0 Step 2: Predict energy consumption For each node ni in N do: - Input historical traffic data ti to RNN - Predict energy consumption using: = RNN_predict(T) Step 3: Detect anomalies For each node ni in N do: - Input real-time traffic data to CNN - Compute anomaly score S(ni) using: Step 4: Optimize resource allocation For each node ni in N do: - Compute optimization score O(ni) using: - Allocate resources based on O(ni): > Threshold: Assign resources and update A(ni) Step 5: Validate decisions using XAI For each decision in A: - Use Explainable AI (XAI) to generate interpretability report - Adjust thresholds or allocations if required based on interpretability feedback Step 6: Update network state For each node ni in N: - Update residual energy: - Log energy and risk metrics Step 7: Repeat until performance criteria are met While global energy savings < Target or risk levels > Tolerable: - Recompute predictions and anomaly scores - Optimize resource allocation iteratively End |
References
- Szpilko, D.; Fernando, X.; Nica, E.; Budna, K.; Rzepka, A.; Lăzăroiu, G. Energy in Smart Cities: Technological Trends and Prospects. Energies 2024, 17, 6439. [Google Scholar] [CrossRef]
- Mirindi, D.; Sinkhonde, D.; Mirindi, F. An Advance Review of Urban-AI and Ethical Considerations. In Proceedings of the 2nd ACM SIGSPATIAL International Workshop on Advances in Urban-AI (UrbanAI ‘24), Atlanta, GA, USA, 29 October–1 November 2024; Association for Computing Machinery: New York, NY, USA, 2024; pp. 24–33. [Google Scholar] [CrossRef]
- Hisyam Ng, H.A.; Mahmoodi, T. Machine Learning-Driven Dynamic Traffic Steering in 6G: A Novel Path Selection Scheme. Big Data Cogn. Comput. 2024, 8, 172. [Google Scholar] [CrossRef]
- Lifelo, Z.; Ding, J.; Ning, H.; Qurat-Ul-Ain; Dhelim, S. Artificial Intelligence-Enabled Metaverse for Sustainable Smart Cities: Technologies, Applications, Challenges, and Future Directions. Electronics 2024, 13, 4874. [Google Scholar] [CrossRef]
- Bagwari, A.; Logeshwaran, J.; Raja, M.; Devisivasankari, P.; Bagwari, J.; Rathi, V.; Saad, A.M.E. Intelligent Computational Model for Energy Efficiency and AI Automation of Network Devices in 5G Communication Environment. Tsinghua Sci. Technol. 2024, 29, 1728–1751. [Google Scholar] [CrossRef]
- Huang, J.E.; Chang, L.W.; Chin, H.H. 5G Metaverse in Education. Mobile Netw. Appl. 2024, 29, 947–960. [Google Scholar] [CrossRef]
- Zhu, X.; Wei, Y.; Lu, Y.; Zhao, M.; Yang, K.; Wu, S.; Zhang, H.; Wong, K.K.L. Comparative analysis of active contour and convolutional neural network in rapid left-ventricle volume quantification using echocardiographic imaging. Comput. Methods Programs Biomed. 2021, 199, 105914. [Google Scholar] [CrossRef]
- El Ansari, R.; El Bouhadioui, M.; Aboutafail, M.O.; Mejjad, N.; Jamil, H.; Jamal, E.; Rissouni, Y.; Zouiten, M.; Boutracheh, H.; Moumen, A. A review of Machine learning models and parameters for groundwater issues. In Proceedings of the NISS ‘23: Proceedings of the 6th International Conference on Networking, Intelligent Systems & Security, Larache, Morocco, 24–26 May 2023. [Google Scholar] [CrossRef]
- Chhabra, S.; Aiden, M.K.; Sabharwal, S.M.; Al-Asadi, M. 5G and 6G Technologies for Smart City. In Enabling Technologies for Effective Planning and Management in Sustainable Smart Cities; Ahad, M.A., Casalino, G., Bhushan, B., Eds.; Springer: Cham, Switherland, 2023. [Google Scholar] [CrossRef]
- Imanbayev, A.; Jakupov, A.; Valikhan, Y.; Odarchenko, R. Designing an Effective Network-Based Intrusion Detecting System for 5G Networks. CEUR Workshop Proc. 2024, 3800, 12–18. [Google Scholar]
- Ez-zahouani, B.; EL Kharki, O.; Kanga Idé, S.; Zouiten, M. Determination of Segmentation Parameters for Object-Based Remote Sensing Image Analysis from Conventional to Recent Approaches: A Review. Int. J. Geoinform. 2023, 19, 23–42. [Google Scholar] [CrossRef]
- Prasad, K.S.; Lydia, E.L.; Rajesh, M.V.; Radhika, K.; Ramesh, J.V.N.; Neelima, N.; Pokuri, S.R. Augmenting cybersecurity through attention based stacked autoencoder with optimization algorithm for detection and mitigation of attacks on IoT assisted networks. Sci. Rep. 2024, 14, 30833. [Google Scholar] [CrossRef]
- Sholeyan, A.E.; Rahatabad, F.N.; Setarehdan, S.K. Designing an Automatic Sleep Staging System Using Deep Convolutional Neural Network Fed by Nonlinear Dynamic Transformation. J. Med. Biol. Eng. 2023, 43, 11–21. [Google Scholar] [CrossRef]
- Almohaimeed, M.; Albalwy, F. Enhancing IoT Network Security Using Feature Selection for Intrusion Detection Systems. Appl. Sci. 2024, 14, 11966. [Google Scholar] [CrossRef]
- Gupta, R.; Singh, A. Machine learning models for anomaly detection in 5G networks. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1021–1034. [Google Scholar]
- Farzaneh, B.; Shahriar, N.; Al Muktadir, A.H.; Towhid, M.S.; Khosravani, M.S. DTL-5G: Deep transfer learning-based DDoS attack detection in 5G and beyond networks. Comput. Commun. 2024, 228, 107927. [Google Scholar] [CrossRef]
- Senevirathna, T.; La, V.H.; Marcha, S.; Siniarski, B.; Liyanage, M.; Wang, S. A Survey on XAI for 5G and Beyond Security: Technical Aspects, Challenges and Research Directions. IEEE Commun. Surv. Tutor. 2025, 27, 941–973. [Google Scholar] [CrossRef]
- Zhang, Y.; Lin, C. Energy efficiency in 5G: Challenges and AI-based solutions. J. Wirel. Commun. Netw. 2020, 18, 789–805. [Google Scholar]
- Baghirov, E. A comprehensive investigation into robust malware detection with explainable AI. Cyber Secur. Appl. 2025, 3, 100072. [Google Scholar] [CrossRef]
- Chen, W.; Huang, P. AI for real-time threat detection in ultra-dense 5G networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 512–523. [Google Scholar]
- Xu, R.; Zhang, X. AI strategies for scalable energy management in 5G smart grids. Elsevier Appl. Energy 2023, 349, 1–15. [Google Scholar]
- Tsourdinis, T.; Chatzistefanidis, I.; Makris, N.; Korakis, T.; Nikaein, N.; Fdida, S. Service-aware real-time slicing for virtualized beyond 5G networks. Comput. Netw. 2024, 247, 110445. [Google Scholar] [CrossRef]
- Haseeb, K.; Alruwaili, F.F.; Khan, A.; Alam, T.; Wafa, A.; Khan, A.R. AI Assisted Energy Optimized Sustainable Model for Secured Routing in Mobile Wireless Sensor Network. Mobile Netw. Appl. 2024, 29, 867–875. [Google Scholar] [CrossRef]
- Segura-Garcia, J.; Sturley, S.; Arevalillo-Herraez, M.; Alcaraz-Calero, J.M.; Felici-Castell, S.; Navarro-Camba, E.A. 5G AI-IoT System for Bird Species Monitoring and Song Classification. Sensors 2024, 24, 3687. [Google Scholar] [CrossRef]
- Solomon Arockiadass, S.A.M.; Thangavel, N.; Prakash A, J.F.; Raja, V.; Dhaigude, R. Enhanced 6G MIMO Signal Detection With Dynamic Sparse Region-Based Convolutional Neural Network With White Shark Optimization. Internet Technol. Lett. 2025, 8, e616. [Google Scholar] [CrossRef]
- China Mobile Limited. Annual Report 2023—Green Telecom Initiatives. Available online: https://www.chinamobileltd.com/en/ir/reports/ar2023.pdf (accessed on 1 June 2025).
- Vodafone Group Plc. Sustainability Report 2022. Available online: https://www.annualreports.com/HostedData/AnnualReportArchive/v/LSE_VOD_2022.pdf (accessed on 1 June 2025).
- SK Telecom. Energy Efficiency/Climate Change Report 2021. Available online: https://www.sktelecom.com/img/pds/persist_biz/2021/2021_CDP_Climate_Change_SK_Telecom.pdf (accessed on 1 June 2025).
- Sustainability and Corporate Responsibility Report 2022. Available online: https://www.responsibilityreports.com/HostedData/ResponsibilityReportArchive/e/NASDAQ_ERIC_2022.pdf (accessed on 1 June 2025).
- Palo Alto Networks Cybersecurity Insights Report, 2023. Available online: https://www.paloaltonetworks.com/resources/research/2023-unit-42-attack-surface-threat-report (accessed on 1 June 2025).
- Huawei Technologies Co.; China Mobile Communications Group Co. Green Management White Paper 2023. Available online: https://www.huawei.com/minisite/otf2023/file/Green_Management_White_Paper.pdf (accessed on 1 June 2025).
- BM Telecommunications Security Report, 2022. Available online: https://www.ibm.com/investor/att/pdf/IBM_Annual_Report_2022.pdf (accessed on 1 June 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).