Washout-Filter Power-Sharing-Based Resilient Control Strategy for Microgrids Against False Data Injection Attacks
Abstract
1. Introduction
- (1)
- The removal of the attacked SC will avoid significant impacts on the PC and other DGs. The system will transition to an operating state with only the PC, and the washout-filter power sharing will replace the droop-based sharing, achieving system frequency and voltage recovery.
- (2)
- Unlike the global nature of system frequency, local voltage may still not be able to return to the rated value under the effect of washout-filter power sharing. In this case, a VCCL on the PC layer will be designed to further correct the voltage to the rated value. Moreover, the VCCL exhibits the ability to mitigate the propagation of FDIAs.
- (3)
- The proposed WFPS-RC strategy isolates the attacked SC, restoring frequency and voltage to its rated value at the PC layer. This enhances the system’s overall resilience, ensuring that, even after suffering FDIAs, the system can still maintain its original secondary control effectiveness.
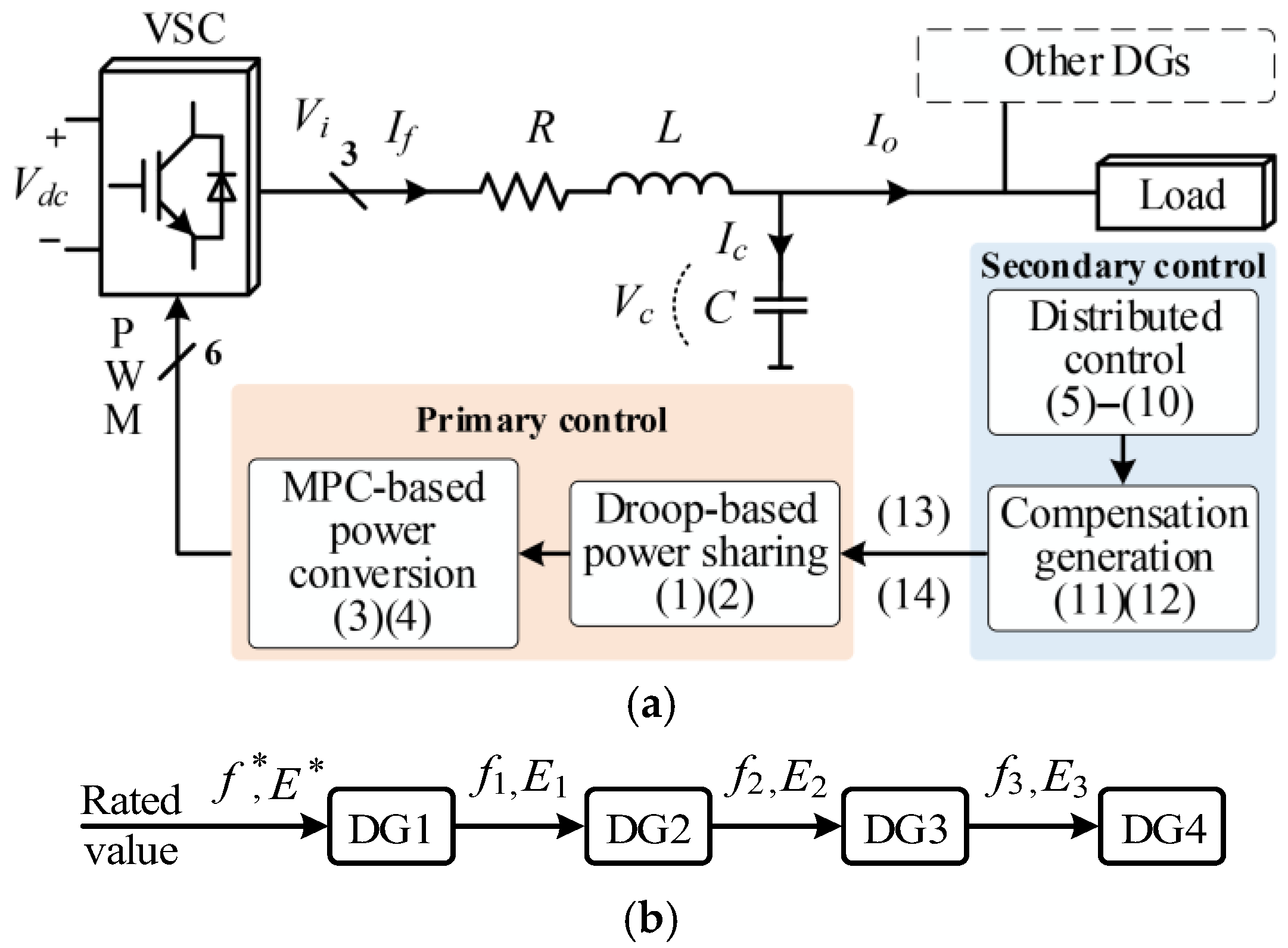
2. Primary and Secondary Controls
2.1. Droop-Based Power Sharing at the PC Level
2.2. MPC-Based Power Conversion at the PC Level
2.3. Graph-Based Distributed Cooperative Control at the SC Level
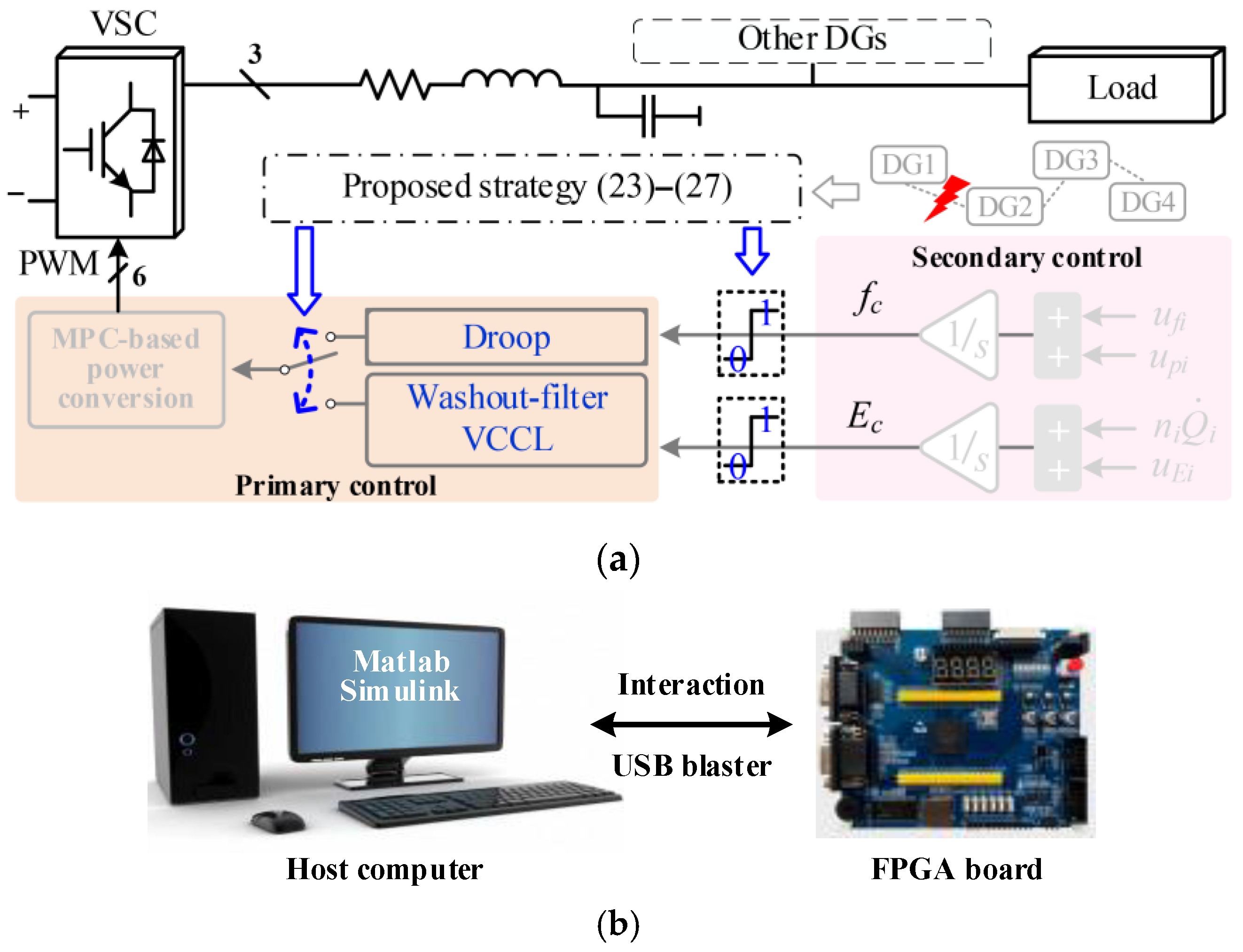
3. FDIAs and Proposed WFPS-RC Strategy
3.1. FDIAs on SC
3.2. Washout-Filter Power Sharing
3.3. VCCL
3.4. Proposed WFPS-RC Strategy
4. Verification
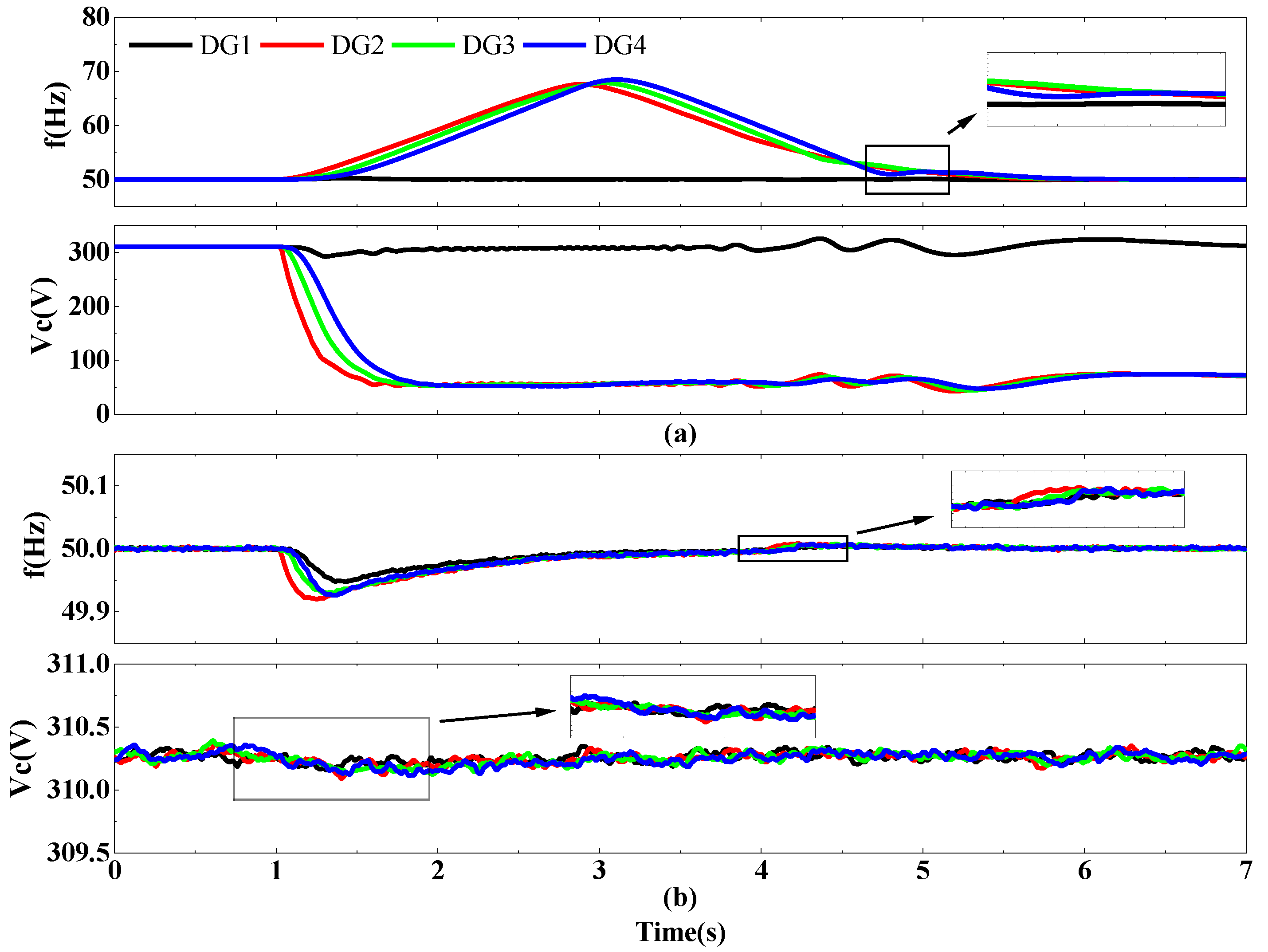
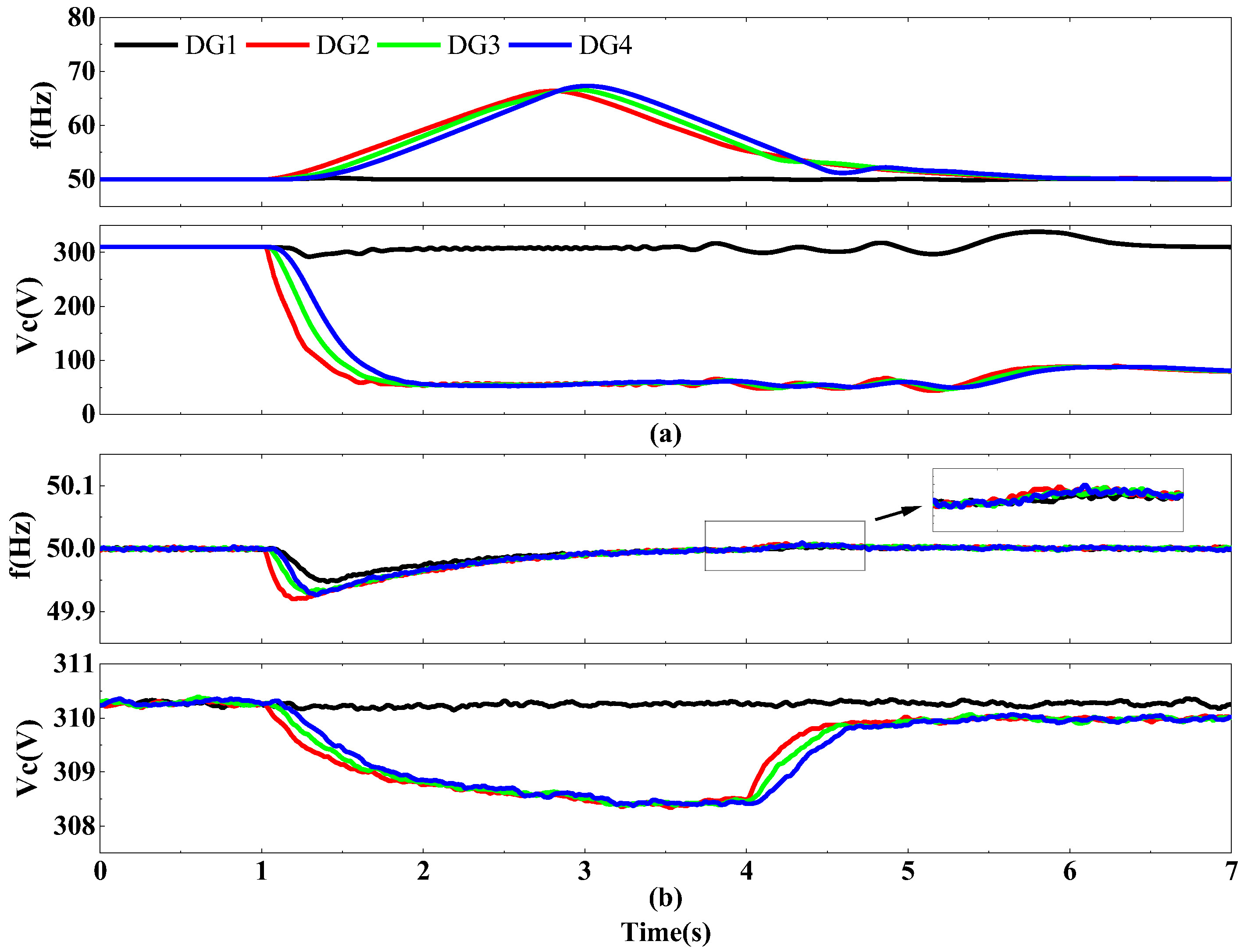
4.1. Situation of DG2 Suffering from FDIA
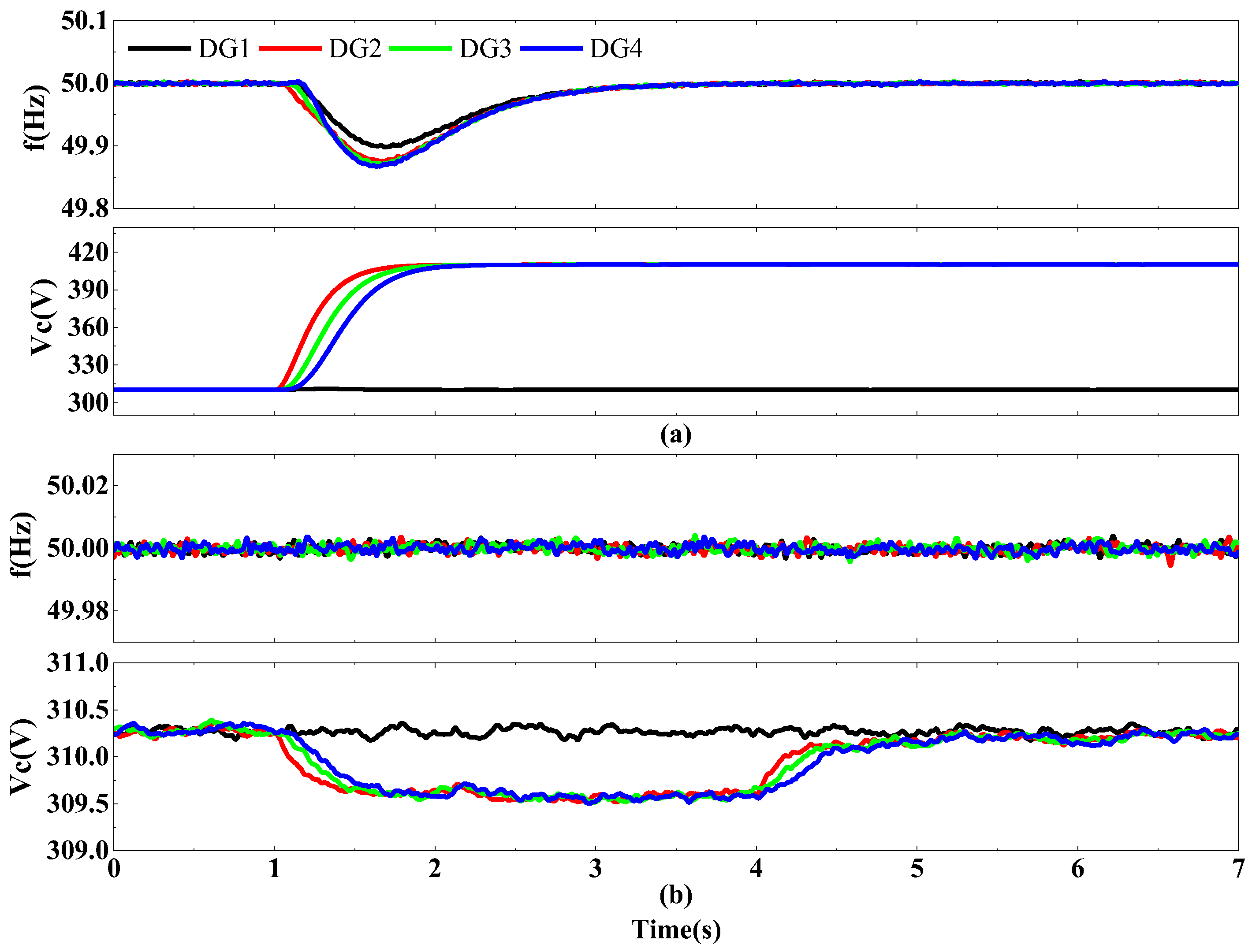
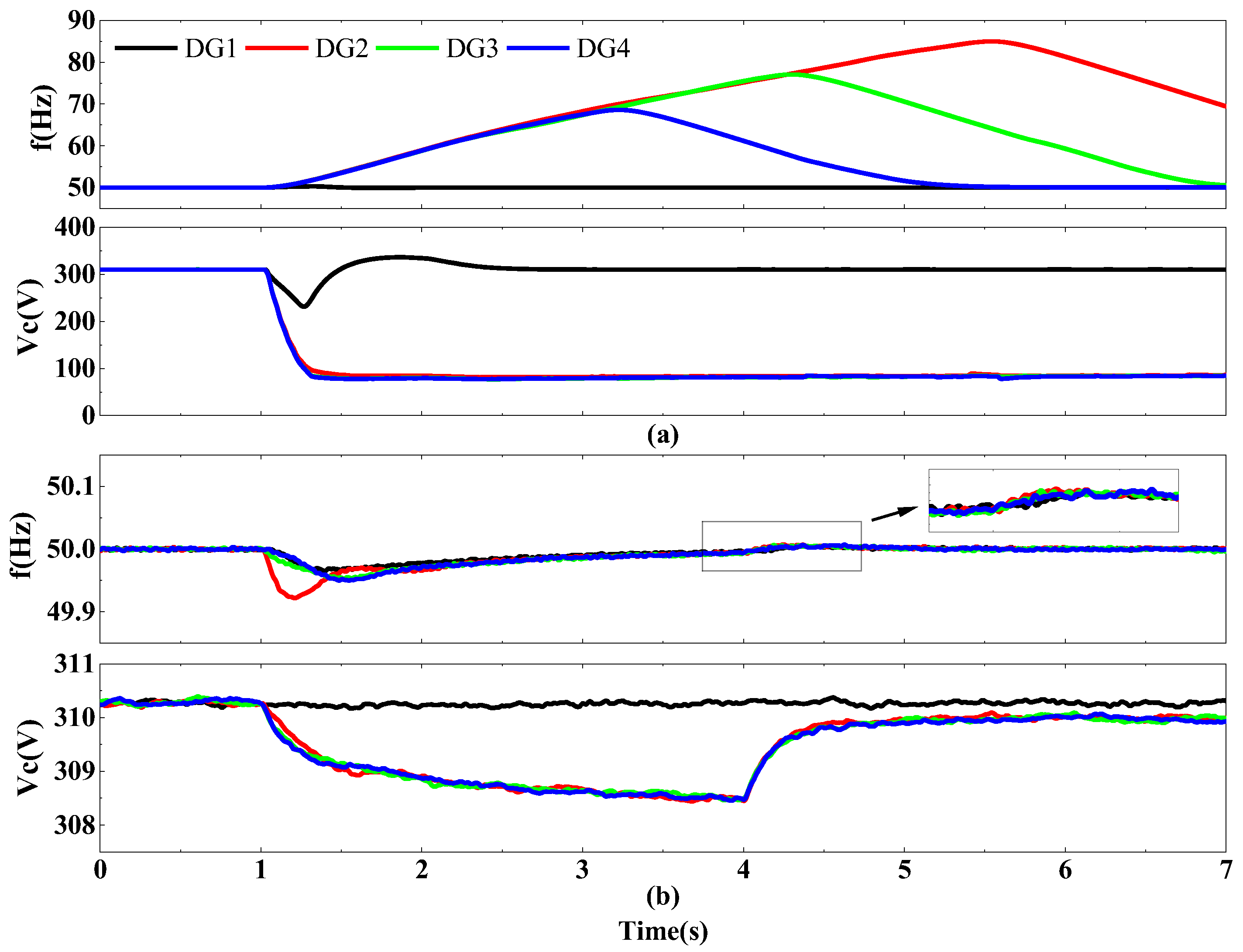
4.2. Situation of DG2 to DG4 Suffering from FDIA
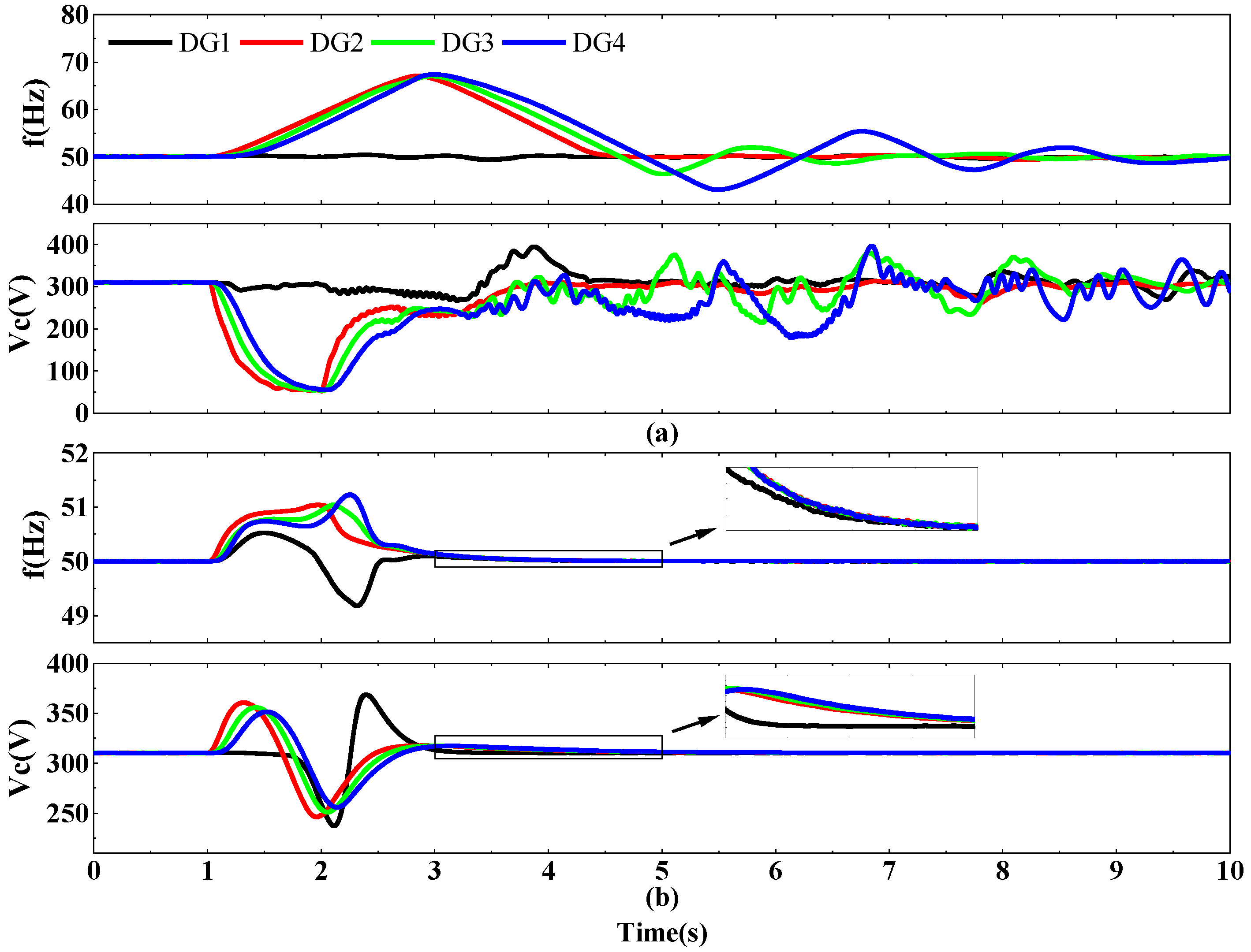
4.3. VCCL Effect
4.4. System Performance After the SC Delay Cutoff
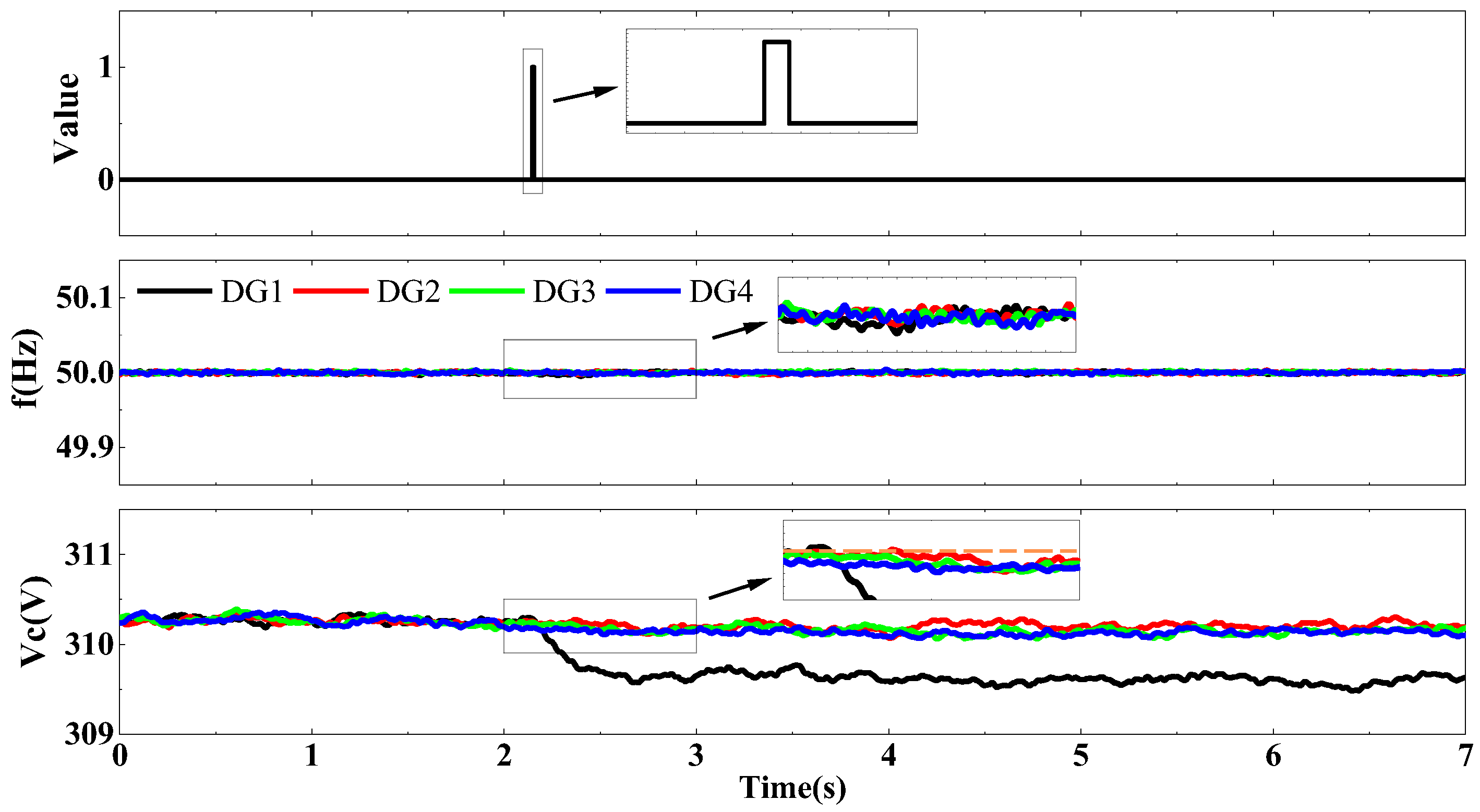
4.5. Verification of Random Attacks by FIL Experiments
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| Abbreviation/Symbol | Description |
| AC | Alternating Current |
| AI | Artificial Intelligence |
| DC | Direct Current |
| DG | Distributed Generator |
| DoS | Denial of Service |
| FDIA | False Data Injection Attack |
| FIL | FPGA-in-the-loop |
| IoT | Internet of Things |
| MPC | Model Predictive Control |
| PC | Primary Control |
| PWM | Pulse Width Modulation |
| SC | Secondary Control |
| VCCL | Voltage Compensation Control Loop |
| VPP | Virtual Power Plant |
| VSC | Voltage Source Converter |
| WFPS-RC | Washout-filter Power-sharing-based Resilient Control |
| Associated Weight of Nodes i and j | |
| Adjacency Matrix | |
| , d(t), dr(t) | Disrupted, Original, and Tampered Signals |
| df, dv, dp | Relevant Control Coefficients |
| efi, evi | Tracking Errors of Frequency and Voltage |
| E | Voltage |
| Voltage Compensation | |
| F | Frequency |
| Frequency Compensation | |
| F(‧) | Main Function for Attack Effect |
| gi | Pinning Gain |
| gs1, gs2 and gs3, gs4 | Two Sets of Control Gains of Frequency and Voltage |
| If | Filter Inductor Current |
| Identity Matrix | |
| kif, kiE | Integral Coefficients of Frequency and Voltage |
| m, n | Droop Coefficients |
| P | Active Power |
| Q | Reactive Power |
| Ts | Sampling Interval |
| T1,T2 , T3 , T4 | Time Intervals |
| Vc | Capacitor Voltage |
| * | Reference Value |
| α, β | Three-phase Variables |
| wI, wV | Weight Coefficients |
| τr | Attack Duration |
| λr | Attack Intensity Coefficient |
| Cutoff Frequency |
References
- Guerrero, J.M.; Vasquez, J.C.; Matas, J.; De Vicuña, L.G.; Castilla, M. Hierarchical Control of Droop-Controlled AC and DC Microgrids—A General Approach toward Standardization. IEEE Trans. Ind. Electron. 2011, 58, 158–172. [Google Scholar] [CrossRef]
- Hamad, B.R.; Al-Durra, A.; Al-Jaafari, K.A.; Zeineldin, H.; Mohamed, Y.A.R.I.; El-Saadany, E. Improving the Robustness of Distributed Secondary Control in Autonomous Microgrids to Mitigate the Effects of Communication Delays. Appl. Energy 2024, 364, 123167. [Google Scholar] [CrossRef]
- Shan, Y.; Hu, J.; Chan, K.W.; Fu, Q.; Guerrero, J.M. Model Predictive Control of Bidirectional DC-DC Converters and AC/DC Interlinking Converters-A New Control Method for PV-Wind-Battery Microgrids. IEEE Trans. Sustain. Energy 2019, 10, 1823–1833. [Google Scholar] [CrossRef]
- Zare, A.; Shafiyi, M.A. Virtual Power Plant Models and Market Participation: A Deep Dive into Optimization and Real-World Applications. Results Eng. 2025, 26, 105548. [Google Scholar] [CrossRef]
- Nafkha-Tayari, W.; Elghali, S.B.; Heydarian-Forushani, E.; Benbouzid, M. Virtual Power Plants Optimization Issue: A Comprehensive Review on Methods, Solutions, and Prospects. Energies 2022, 15, 3607. [Google Scholar] [CrossRef]
- Tang, X.; Wang, J. Deep Reinforcement Learning-Based Multi-Objective Optimization for Virtual Power Plants and Smart Grids: Maximizing Renewable Energy Integration and Grid Efficiency. Processes 2025, 13, 1809. [Google Scholar] [CrossRef]
- Huang, J.; Li, H.; Zhang, Z. Review of Virtual Power Plant Response Capability Assessment and Optimization Dispatch. Technologies 2025, 13, 216. [Google Scholar] [CrossRef]
- Panda, D.K.; Das, S. Smart Grid Architecture Model for Control, Optimization and Data Analytics of Future Power Networks with More Renewable Energy. J. Clean. Prod. 2021, 301, 126877. [Google Scholar] [CrossRef]
- Gopinathan, N.; Shanmugam, P.K.; Singh, M. Smart Grid Architecture Model (SGAM) for Resilience Using Energy Internet of Things (EIoT). In Proceedings of the 2022 22nd National Power Systems Conference, NPSC 2022, New Delhi, India, 17–19 December 2022; pp. 248–253. [Google Scholar]
- Taher, M.A.; Tariq, M.; Sarwat, A.I. Trust-Based Detection and Mitigation of Cyber Attacks in Distributed Cooperative Control of Islanded AC Microgrids. Electronics 2024, 13, 3692. [Google Scholar] [CrossRef]
- Zhang, S.; Zhang, K.; Hu, Z. Cooperative Control for Multi-Agent Systems with Deception Attack Based on an Attack Detection Mechanism. Energies 2025, 18, 2962. [Google Scholar] [CrossRef]
- Kutlucan, N.K.; Ucun, L.; Dasdemir, J. Event-Triggered Secure Control Design Against False Data Injection Attacks via Lyapunov-Based Neural Networks. Sensors 2025, 25, 3634. [Google Scholar] [CrossRef] [PubMed]
- Rajkumar, V.S.; Stefanov, A.; Presekal, A.; Palensky, P.; Torres, J.L.R. Cyber Attacks on Power Grids: Causes and Propagation of Cascading Failures. IEEE Access 2023, 11, 103154–103176. [Google Scholar] [CrossRef]
- Rouhani, S.H.; Su, C.L.; Mobayen, S.; Razmjooy, N.; Elsisi, M. Cyber Resilience in Renewable Microgrids: A Review of Standards, Challenges, and Solutions. Energy 2024, 309, 133081. [Google Scholar] [CrossRef]
- Calderón, D.; Folgado, F.J.; González, I.; Calderón, A.J. Implementation and Experimental Application of Industrial IoT Architecture Using Automation and IoT Hardware/Software. Sensors 2024, 24, 8074. [Google Scholar] [CrossRef]
- Jamil, N.; Qassim, Q.S.; Bohani, F.A.; Mansor, M.; Ramachandaramurthy, V.K. Cybersecurity of Microgrid: State-of-the-Art Review and Possible Directions of Future Research. Appl. Sci. 2021, 11, 9812. [Google Scholar] [CrossRef]
- Hu, W.; Shen, Y.; Yang, F.; Chang, Z.; Zhao, S. Fuzzy Resilient Control of DC Microgrids with Constant Power Loads Based on Markov Jump Models. Mathematics 2024, 12, 2656. [Google Scholar] [CrossRef]
- Mohan, A.M.; Meskin, N. Observer-Based False Data Injection Attack Resilient Event-Triggered Control of Microgrid Load Frequency Control System. ISA Trans. 2025; in press. [Google Scholar] [CrossRef]
- Zuo, S.; Zhang, Y.; Wang, Y. Adaptive Resilient Control of AC Microgrids under Unbounded Actuator Attacks. Energies 2022, 15, 7458. [Google Scholar] [CrossRef]
- Khalghani, M.R.; Verma, V.; Solanki, S.K.; Solanki, J.M. Resilient Networked Control of Inverter-Based Microgrids against False Data Injections. Electronics 2022, 11, 780. [Google Scholar] [CrossRef]
- Yuan, T.; Assilevi, K.R.; Adjallah, K.H.; Ajavon, A.S.A.; Wang, H. Microgrid Resilience Enhancement with Sensor Network-Based Monitoring and Risk Assessment Involving Uncertain Data. Energies 2024, 17, 6141. [Google Scholar] [CrossRef]
- Ji, S.; Liu, Y.; Wu, S.; Li, X. Resilience Improvement of Microgrid Cluster Systems Based on Two-Stage Robust Optimization. Energies 2024, 17, 4287. [Google Scholar] [CrossRef]
- Ma, B.; Lu, Q.; Gu, Z. Resilient Event-Based Fuzzy Fault Detection for DC Microgrids in Finite-Frequency Domain against DoS Attacks. Sensors 2024, 24, 2677. [Google Scholar] [CrossRef]
- Barzegari, Y.; Zarei, J.; Razavi-Far, R.; Saif, M.; Palade, V. Resilient Consensus Control Design for DC Microgrids against False Data Injection Attacks Using a Distributed Bank of Sliding Mode Observers. Sensors 2022, 22, 2644. [Google Scholar] [CrossRef]
- Cai, X.; Gao, B.; Nan, X. Resilient Distributed Secondary Control for Islanded AC Microgrids under FDI Attacks. Electr. Power Syst. Res. 2025, 238, 111123. [Google Scholar] [CrossRef]
- Mishra, D.K.; Ray, P.K.; Li, L.; Zhang, J.; Hossain, M.J.; Mohanty, A. Resilient Control Based Frequency Regulation Scheme of Isolated Microgrids Considering Cyber Attack and Parameter Uncertainties. Appl. Energy 2022, 306, 118054. [Google Scholar] [CrossRef]
- Yassaie, N.; Hallajiyan, M.; Sharifi, I.; Talebi, H.A. Resilient Control of Multi-Microgrids against False Data Injection Attack. ISA Trans. 2021, 110, 238–246. [Google Scholar] [CrossRef]
- He, Q.; Shah, P.; Zhao, X. Resilient Operation of DC Microgrid against FDI Attack: A GRU Based Framework. Int. J. Electr. Power Energy Syst. 2023, 145, 108586. [Google Scholar] [CrossRef]
- Huang, C.; Deng, S.; Ge, H. Resilient Load Frequency Control of Cyber–Physical Power Systems with off-the-Shelf Redundant Communication Channels under FDI Attacks. Meas. Energy 2025, 7, 100053. [Google Scholar] [CrossRef]
- Yazdanian, M.; Mehrizi-Sani, A. Washout Filter-Based Power Sharing. IEEE Trans. Smart Grid 2016, 7, 967–968. [Google Scholar] [CrossRef]
- Han, Y.; Li, H.; Xu, L.; Zhao, X.; Guerrero, J.M. Analysis of Washout Filter-Based Power Sharing Strategy-An Equivalent Secondary Controller for Islanded Microgrid Without LBC Lines. IEEE Trans. Smart Grid 2018, 9, 4061–4076. [Google Scholar] [CrossRef]
- Shan, Y.; Hu, J.; Liu, M.; Zhu, J.; Guerrero, J.M. Model Predictive Voltage and Power Control of Islanded PV-Battery Microgrids with Washout-Filter-Based Power Sharing Strategy. IEEE Trans. Power Electron. 2020, 35, 1227–1238. [Google Scholar] [CrossRef]
- Zhou, J.; Hassan, M.A.; Zhang, J.; Hou, M.; Wu, S.; Xing, G.; Chi, S. Stabilization of Constant Power Loads in Dc Microgrid Systems Using an Adaptive Continuous Control Set Model Predictive Control. Symmetry 2021, 13, 1112. [Google Scholar] [CrossRef]
- Lema, M.; Pavon, W.; Ortiz, L.; Asiedu-Asante, A.B.; Simani, S. Controller Coordination Strategy for DC Microgrid Using Distributed Predictive Control Improving Voltage Stability. Energies 2022, 15, 5442. [Google Scholar] [CrossRef]
- Cavus, M.; Allahham, A. Enhanced Microgrid Control through Genetic Predictive Control: Integrating Genetic Algorithms with Model Predictive Control for Improved Non-Linearity and Non-Convexity Handling. Energies 2024, 17, 4458. [Google Scholar] [CrossRef]
- Shan, Y.; Hu, J.; Shen, B. Distributed Secondary Frequency Control for AC Microgrids Using Load Power Forecasting Based on Artificial Neural Network. IEEE Trans. Ind. Inf. Inform. 2024, 20, 1651–1662. [Google Scholar] [CrossRef]
- Shan, Y.; Hu, J.; Liu, H. A Holistic Power Management Strategy of Microgrids Based on Model Predictive Control and Particle Swarm Optimization. IEEE Trans. Ind. Inf. Inform. 2022, 18, 5115–5126. [Google Scholar] [CrossRef]
- Ustun, T.S.; Ayyubi, S. Automated Network Topology Extraction Based on Graph Theory for Distributed Microgrid Protection in Dynamic Power Systems. Electronics 2019, 8, 655. [Google Scholar] [CrossRef]
- Zhang, B.; Liu, P.; Xie, Y.; Zhao, H.; Zhong, W.; Zhang, H.; Wang, X.; Ban, L.; Sun, M. A Novel Detection and Identification Mechanism for Malicious Injection Attacks in Power Systems. Symmetry 2023, 15, 2104. [Google Scholar] [CrossRef]
- Fu, H.; Li, W.; Qiu, L.; Ai, Y.; Liu, Z. A Communication Encryption-Based Distributed Cooperative Control for Distributed Generators in Microgrids under FDI Attacks. Energies 2023, 16, 7754. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, S.; Zhu, W.; Wang, X.; Qian, T.; Shan, Y. Washout-Filter Power-Sharing-Based Resilient Control Strategy for Microgrids Against False Data Injection Attacks. Eng 2025, 6, 198. https://doi.org/10.3390/eng6080198
Fan S, Zhu W, Wang X, Qian T, Shan Y. Washout-Filter Power-Sharing-Based Resilient Control Strategy for Microgrids Against False Data Injection Attacks. Eng. 2025; 6(8):198. https://doi.org/10.3390/eng6080198
Chicago/Turabian StyleFan, Shiwang, Wenjie Zhu, Xiaowei Wang, Tao Qian, and Yinghao Shan. 2025. "Washout-Filter Power-Sharing-Based Resilient Control Strategy for Microgrids Against False Data Injection Attacks" Eng 6, no. 8: 198. https://doi.org/10.3390/eng6080198
APA StyleFan, S., Zhu, W., Wang, X., Qian, T., & Shan, Y. (2025). Washout-Filter Power-Sharing-Based Resilient Control Strategy for Microgrids Against False Data Injection Attacks. Eng, 6(8), 198. https://doi.org/10.3390/eng6080198





