The Road to Accountable and Dependable Manufacturing
Abstract
:1. Introduction
- (P0)
- CPS and site-related improvements (↻) with limited external influences,
- (P1)
- Extended data sharing along the supply chain (⇄), e.g., to reduce the bullwhip effect [9], and
- (P2)
- Secure industrial collaborations across supply chains (⇅), e.g., to reduce ramp-up costs [10]. To cover P1 and P2 not only with today’s (established) long-term trust but also in settings with dynamically evolving and flexible short-term relationships, we identify a new research pillar
- (P3)
- That has to provide accountable and dependable dataflows even for stakeholders who have not yet established any (trusted) relationships (❖).
- We raise the awareness for a new research pillar (P3 ❖) evolving around dataflows between stakeholders without any trusted or previous relationship.
- We identify three main groups of scenario-driven research challenges in the context of accountable and dependable manufacturing that are accompanied by related blockchain-inherent and socio-economic challenges.
- Using blockchain technology, we propose the idea of a trustworthy information store (TrustedStore) to realize a reliable and automated production landscape.
2. Motivation and Potentials
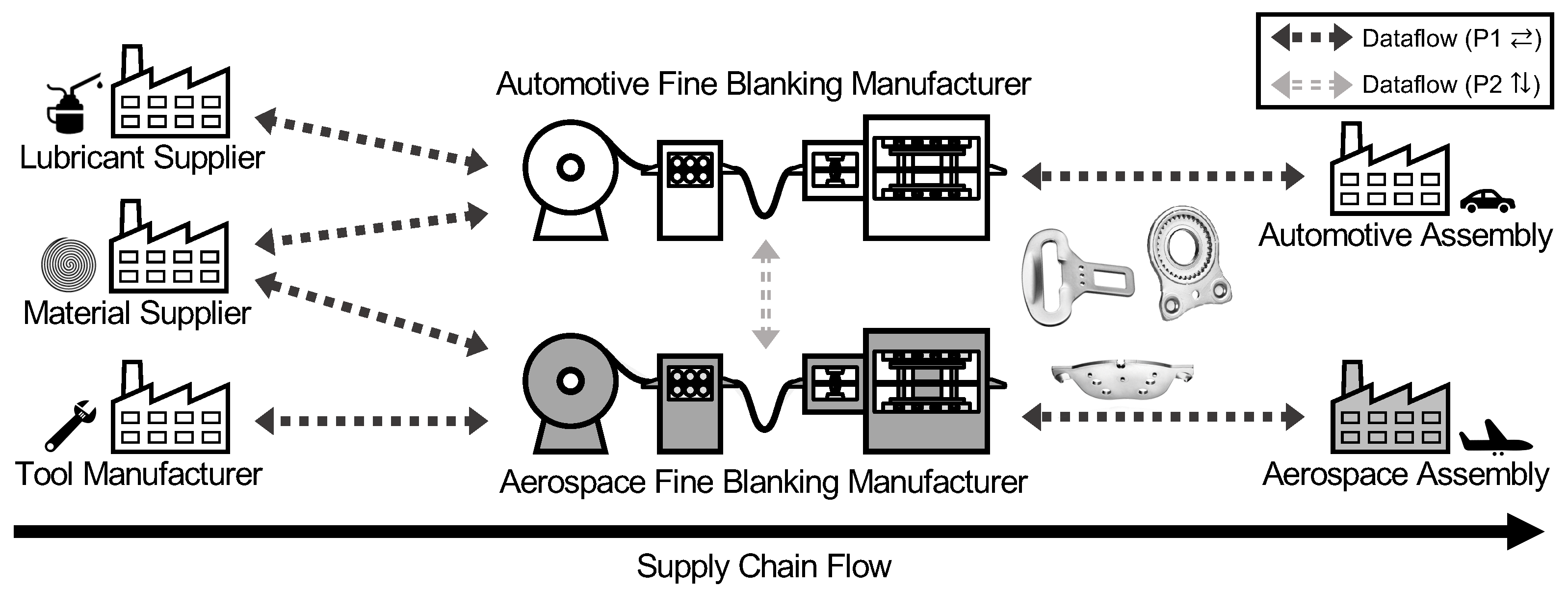
2.1. Information Sharing along Supply Chains (P1 ⇄)
2.2. Foundations for Expanding Secure Industrial Collaborations across Supply Chains (P2 ⇅)
2.3. Ad Hoc Relationships in Untrusted Environments (P3 ❖)
3. The Influence of Blockchains
3.1. The State of Industrial Blockchain Integration
3.1.1. Financial Origins
3.1.2. Digital Assets
3.1.3. Process Automation
3.1.4. Internet of Things
3.1.5. Supply Chains
3.2. Useful Properties for Diverse Applications
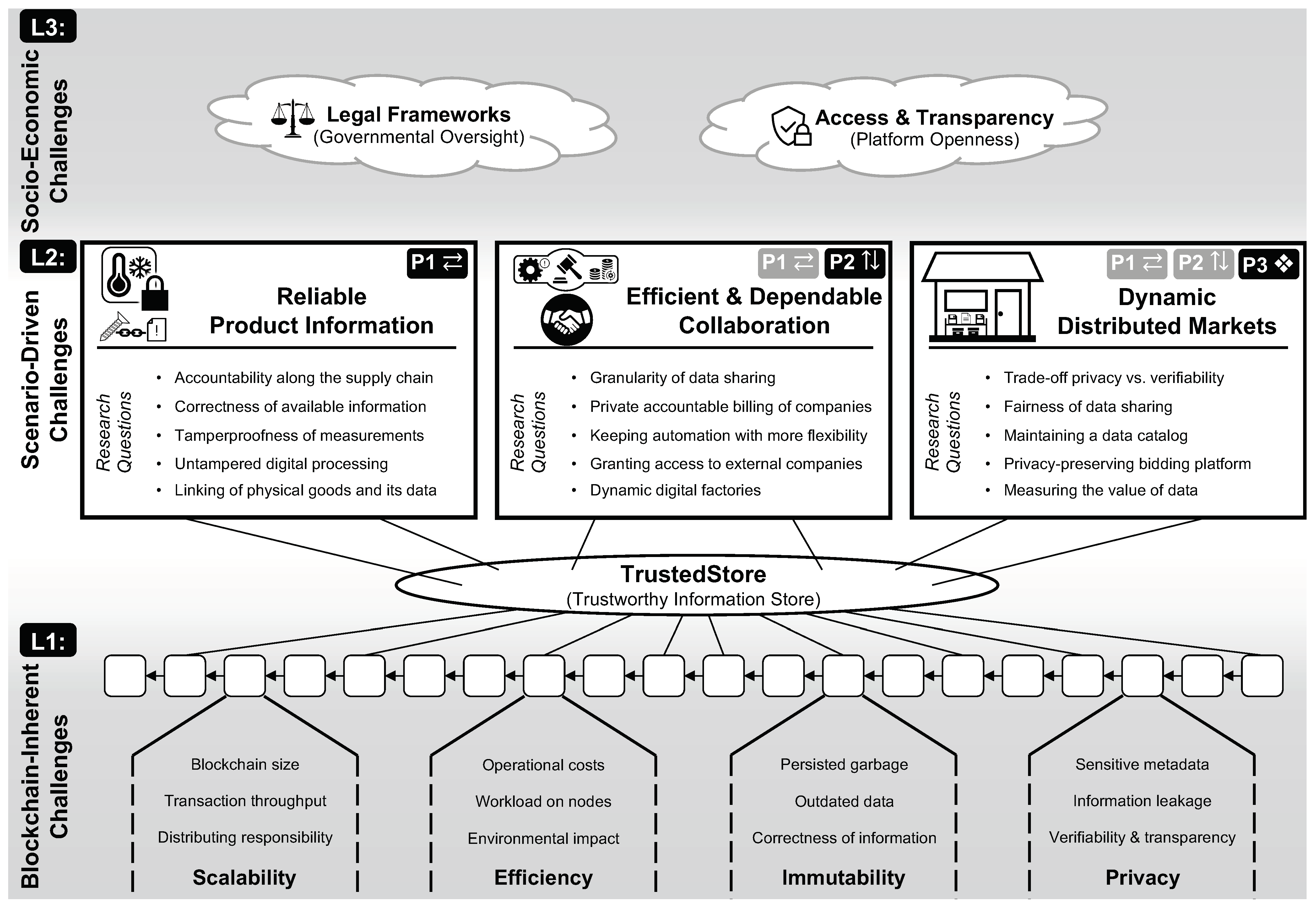
4. Open Research Areas
- (L1)
- Yet unaddressed challenges for the use of blockchain technology in manufacturing,
- (L2)
- New opportunities for a fast, versatile, accountable, and dependable manufacturing enabled by blockchains, i.e., scenario-driven challenges, and
- (L3)
- Socio-economic challenges stemming from immutably recorded production data and highly flexible cross-company collaborations.
4.1. Open Blockchain-Inherent Challenges (L1)
4.1.1. Scalability
4.1.2. Efficiency
4.1.3. Immutability
4.1.4. Privacy
4.2. Scenario-Driven Research Directions (L2)
4.2.1. Reliable Product Information
4.2.2. Efficient and Dependable Collaboration
4.2.3. Dynamic Distributed Markets
4.3. Socio-Economic Challenges (L3)
4.3.1. Legal Frameworks
4.3.2. Access and Transparency
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kusiak, A. Smart manufacturing must embrace big data. Nature 2017, 544, 23–25. [Google Scholar] [CrossRef] [PubMed]
- Coito, T.; Firme, B.; Martins, M.S.E.; Vieira, S.M.; Figueiredo, J.; Sousa, J. Intelligent Sensors for Real-Time Decision-Making. Automation 2021, 2, 62–82. [Google Scholar] [CrossRef]
- Friede, G.; Busch, T.; Bassen, A. ESG and financial performance: Aggregated evidence from more than 2000 empirical studies. J. Sustain. Financ. Invest. 2015, 5, 210–233. [Google Scholar] [CrossRef] [Green Version]
- Rosen, M.A.; Kishawy, H.A. Sustainable Manufacturing and Design: Concepts, Practices and Needs. Sustainability 2012, 4, 154–174. [Google Scholar] [CrossRef] [Green Version]
- Seuring, S.; Müller, M. From a literature review to a conceptual framework for sustainable supply chain management. J. Clean. Prod. 2008, 16, 1699–1710. [Google Scholar] [CrossRef]
- Pennekamp, J.; Glebke, R.; Henze, M.; Meisen, T.; Quix, C.; Hai, R.; Gleim, L.; Niemietz, P.; Rudack, M.; Knape, S.; et al. Towards an Infrastructure Enabling the Internet of Production. In Proceedings of the 2019 IEEE International Conference on Industrial Cyber Physical Systems (ICPS ’19), Taipei, Taiwan, 6–9 May 2019; pp. 31–37. [Google Scholar] [CrossRef]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial Internet of Things: Challenges, Opportunities, and Directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Pennekamp, J.; Henze, M.; Schmidt, S.; Niemietz, P.; Fey, M.; Trauth, D.; Bergs, T.; Brecher, C.; Wehrle, K. Dataflow Challenges in an Internet of Production: A Security & Privacy Perspective. In Proceedings of the ACM Workshop on Cyber-Physical Systems Security & Privacy (CPS-SPC’19), London, UK, 11 November 2019; ACM: New York, NY, USA; pp. 27–38. [Google Scholar] [CrossRef]
- Moyaux, T.; Chaib-draa, B.; D’Amours, S. Information Sharing as a Coordination Mechanism for Reducing the Bullwhip Effect in a Supply Chain. IEEE Trans. Syst. Man, Cybern. Part C (Appl. Rev.) 2007, 37, 396–409. [Google Scholar] [CrossRef]
- Pennekamp, J.; Buchholz, E.; Lockner, Y.; Dahlmanns, M.; Xi, T.; Fey, M.; Brecher, C.; Hopmann, C.; Wehrle, K. Privacy-Preserving Production Process Parameter Exchange. In Proceedings of the 36th Annual Computer Security Applications Conference (ACSAC ’20), Virtual Conference, 7–11 December 2020; ACM: New York, NY, USA; pp. 510–525. [Google Scholar] [CrossRef]
- Malik, S.; Kanhere, S.S.; Jurdak, R. ProductChain: Scalable Blockchain Framework to Support Provenance in Supply Chains. In Proceedings of the 2018 IEEE 17th International Symposium on Network Computing and Applications (NCA ’18), Cambridge, MA, USA, 1–3 November 2018. [Google Scholar] [CrossRef]
- Gleim, L.; Pennekamp, J.; Liebenberg, M.; Buchsbaum, M.; Niemietz, P.; Knape, S.; Epple, A.; Storms, S.; Trauth, D.; Bergs, T.; et al. FactDAG: Formalizing Data Interoperability in an Internet of Production. IEEE Internet Things J. 2020, 7, 3243–3253. [Google Scholar] [CrossRef]
- Matzutt, R.; Kalde, B.; Pennekamp, J.; Arthur, D.; Henze, M.; Bergs, T.; Wehrle, K. How to Securely Prune Bitcoin’s Blockchain. In Proceedings of the 19th IFIP Networking 2020 Conference (NETWORKING’20), Paris, France, 22–26 June 2020; pp. 298–306. [Google Scholar]
- Kouhizadeh, M.; Sarkis, J. Blockchain Practices, Potentials, and Perspectives in Greening Supply Chains. Sustainability 2018, 10, 3652. [Google Scholar] [CrossRef] [Green Version]
- Tijan, E.; Aksentijević, S.; Ivanić, K.; Jardas, M. Blockchain Technology Implementation in Logistics. Sustainability 2019, 11, 1185. [Google Scholar] [CrossRef] [Green Version]
- Varriale, V.; Cammarano, A.; Michelino, F.; Caputo, M. The Unknown Potential of Blockchain for Sustainable Supply Chains. Sustainability 2020, 12, 9400. [Google Scholar] [CrossRef]
- Tan, B.Q.; Wang, F.; Liu, J.; Kang, K.; Costa, F. A Blockchain-Based Framework for Green Logistics in Supply Chains. Sustainability 2020, 12, 4656. [Google Scholar] [CrossRef]
- Trautmann, L.; Lasch, R. Smart Contracts in the Context of Procure-to-Pay. In Smart and Sustainable Supply Chain and Logistics—Trends, Challenges, Methods and Best Practices; Springer: Cham, Switzerland, 2020; Volume 1, pp. 3–23. [Google Scholar] [CrossRef]
- Wang, M.; Wang, B.; Abareshi, A. Blockchain Technology and Its Role in Enhancing Supply Chain Integration Capability and Reducing Carbon Emission: A Conceptual Framework. Sustainability 2020, 12, 10550. [Google Scholar] [CrossRef]
- Park, A.; Li, H. The Effect of Blockchain Technology on Supply Chain Sustainability Performances. Sustainability 2021, 13, 1726. [Google Scholar] [CrossRef]
- Bekrar, A.; El Cadi, A.A.; Todosijevic, R.; Sarkis, J. Digitalizing the Closing-of-the-Loop for Supply Chains: A Transportation and Blockchain Perspective. Sustainability 2021, 13, 2895. [Google Scholar] [CrossRef]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J.; Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 2019, 57, 2117–2135. [Google Scholar] [CrossRef] [Green Version]
- Ko, T.; Lee, J.; Ryu, D. Blockchain Technology and Manufacturing Industry: Real-Time Transparency and Cost Savings. Sustainability 2018, 10, 4274. [Google Scholar] [CrossRef] [Green Version]
- Lohmer, J. Applicability of Blockchain Technology in Scheduling Resources Within Distributed Manufacturing. In Logistics Management; Springer: Cham, Switzerland, 2019; pp. 89–103. [Google Scholar] [CrossRef]
- Lohmer, J.; Lasch, R. Blockchain in operations management and manufacturing: Potential and barriers. Comput. Ind. Eng. 2020, 149, 106789. [Google Scholar] [CrossRef]
- Müller, J.M.; Kiel, D.; Voigt, K.I. What Drives the Implementation of Industry 4.0? The Role of Opportunities and Challenges in the Context of Sustainability. Sustainability 2018, 10, 247. [Google Scholar] [CrossRef] [Green Version]
- Glebke, R.; Henze, M.; Wehrle, K.; Niemietz, P.; Trauth, D.; Mattfeld, P.; Bergs, T. A Case for Integrated Data Processing in Large-Scale Cyber-Physical Systems. In Proceedings of the 52nd Hawaii International Conference on System Sciences (HICSS ’19), Wailea, HI, USA, 8–11 January 2019; AIS: Atlanta, GA, USA; pp. 7252–7261. [Google Scholar] [CrossRef] [Green Version]
- Oussous, A.; Benjelloun, F.Z.; Lahcen, A.A.; Belfkih, S. Big Data technologies: A survey. J. King Saud-Univ.-Comput. Inf. Sci. 2018, 30, 431–448. [Google Scholar] [CrossRef]
- Jagadish, H.V.; Gehrke, J.; Labrinidis, A.; Papakonstantinou, Y.; Patel, J.M.; Ramakrishnan, R.; Shahabi, C. Big Data and Its Technical Challenges. Commun. ACM 2014, 57, 86–94. [Google Scholar] [CrossRef]
- Kunze, I.; Glebke, R.; Scheiper, J.; Bodenbenner, M.; Schmitt, R.H.; Wehrle, K. Investigating the Applicability of In-Network Computing to Industrial Scenarios. In Proceedings of the 2021 4th IEEE International Conference on Industrial Cyber-Physical Systems (ICPS ’21), Victoria, BC, Canada, 10–13 May 2021; pp. 334–340. [Google Scholar] [CrossRef]
- Kunze, I.; Niemietz, P.; Tirpitz, L.; Glebke, R.; Trauth, D.; Bergs, T.; Wehrle, K. Detecting Out-Of-Control Sensor Signals in Sheet Metal Forming using In-Network Computing. In Proceedings of the 2020 IEEE 29th International Symposium on Industrial Electronics (ISIE ’21), Kyoto, Japan, 20–23 June 2021. [Google Scholar]
- Ślusarczyk, B.; Tvaronavičienė, M.; Haque, A.U.; Oláh, J. Predictors of Industry 4.0 technologies affecting logistic enterprises’ performance: International perspective from economic lens. Technol. Econ. Dev. Econ. 2020, 26, 1263–1283. [Google Scholar] [CrossRef]
- Oláh, J.; Aburumman, N.; Popp, J.; Khan, M.A.; Haddad, H.; Kitukutha, N. Impact of Industry 4.0 on environmental sustainability. Sustainability 2020, 12, 4674. [Google Scholar] [CrossRef]
- Peng, H.; Liu, C.; Zhao, D.; Ye, H.; Fang, Z.; Wang, W. Security Analysis of CPS Systems Under Different Swapping Strategies in IoT Environments. IEEE Access 2020, 8, 63567–63576. [Google Scholar] [CrossRef]
- Peng, H.; Liu, C.; Zhao, D.; Hu, Z.; Han, J. Security Evaluation under Different Exchange Strategies Based on Heterogeneous CPS Model in Interdependent Sensor Networks. Sensors 2020, 20, 6123. [Google Scholar] [CrossRef] [PubMed]
- Henze, M. The Quest for Secure and Privacy-preserving Cloud-based Industrial Cooperation. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS ’20), the 6th International Workshop on Security and Privacy in the Cloud (SPC ’20), Avignon, France, 29 June–1 July 2020. [Google Scholar] [CrossRef]
- Wang, S.; Li, D.; Zhang, Y.; Chen, J. Smart Contract-Based Product Traceability System in the Supply Chain Scenario. IEEE Access 2019, 7, 115122–115133. [Google Scholar] [CrossRef]
- Montecchi, M.; Plangger, K.; Etter, M. It’s real, trust me! Establishing supply chain provenance using blockchain. Bus. Horiz. 2019, 62, 283–293. [Google Scholar] [CrossRef] [Green Version]
- Malik, S.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. TrustChain: Trust Management in Blockchain and IoT supported Supply Chains. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain ’19), Atlanta, GA, USA, 14–17 July 2019; pp. 184–193. [Google Scholar] [CrossRef] [Green Version]
- Pennekamp, J.; Sapel, P.; Fink, I.B.; Wagner, S.; Reuter, S.; Hopmann, C.; Wehrle, K.; Henze, M. Revisiting the Privacy Needs of Real-World Applicable Company Benchmarking. In Proceedings of the 8th Workshop on Encrypted Computing & Applied Homomorphic Cryptography (WAHC ’20), Virtual Conference, 15 December 2020; HomomorphicEncryption.org: Toronto, ON, Canada; pp. 31–44. [Google Scholar] [CrossRef]
- Gleim, L.; Pennekamp, J.; Tirpitz, L.; Welten, S.; Brillowski, F.; Decker, S. FactStack: Interoperable Data Management and Preservation for the Web and Industry 4.0. In Proceedings of the 19th Symposium for Database Systems for Business, Technology and Web (BTW ’21), Virtual Conference, 19 April–21 June 2021; Gesellschaft für Informatik: Bonn, Germany; Volume P-311, pp. 371–395. [Google Scholar] [CrossRef]
- Korpela, K.; Hallikas, J.; Dahlberg, T. Digital Supply Chain Transformation toward Blockchain Integration. In Proceedings of the 50th Hawaii International Conference on System Sciences (HICSS ’17), Waikoloa, HI, USA, 4–7 January 2017; AIS: Atlanta, GA, USA; pp. 4182–4191. [Google Scholar] [CrossRef] [Green Version]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 8 September 2021).
- Giungato, P.; Rana, R.; Tarabella, A.; Tricase, C. Current Trends in Sustainability of Bitcoins and Related Blockchain Technology. Sustainability 2017, 9, 2214. [Google Scholar] [CrossRef] [Green Version]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Wüst, K.; Gervais, A. Do you need a Blockchain? In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT ’18), Zug, Switzerland, 20–22 June 2018; pp. 45–54. [Google Scholar] [CrossRef]
- Guo, Y.; Liang, C. Blockchain application and outlook in the banking industry. Financ. Innov. 2016, 2. [Google Scholar] [CrossRef] [Green Version]
- Armknecht, F.; Karame, G.O.; Mandal, A.; Youssef, F.; Zenner, E. Ripple: Overview and Outlook. In Proceedings of the 8th International Conference on Trust and Trustworthy Computing (TRUST ’15), Heraklion, Greece, 24–26 August 2015; Springer: Cham, Switzerland; Volume 9229, pp. 163–180. [Google Scholar] [CrossRef]
- Chase, B.; MacBrough, E. Analysis of the XRP Ledger Consensus Protocol. arXiv 2018, arXiv:1802.07242. [Google Scholar]
- JPMorgan Chase & Co. Liink by J.P. Morgan. 2020. Available online: https://www.jpmorgan.com/onyx/liink (accessed on 11 April 2021).
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress ’17), Honolulu, HI, USA, 25–30 June 2017. [Google Scholar] [CrossRef]
- Durham, V. Namecoin. 2011. Available online: https://namecoin.org (accessed on 11 April 2021).
- Bartoletti, M.; Pompianu, L. An analysis of Bitcoin OP_RETURN metadata. In Proceedings of the 21st International Conference on Financial Cryptography and Data Security (FC ’17), Sliema, Malta, 3–7 April 2017; Springer: Cham, Switzerland; Volume 10323, pp. 218–230. [Google Scholar] [CrossRef] [Green Version]
- Proof of Existence. 2015. Available online: https://proofofexistence.com (accessed on 11 April 2021).
- Wood, G. Ethereum: A Secure Decentralised Generalised Transaction Ledger. Available online: https://ethereum.github.io/yellowpaper/paper.pdf (accessed on 8 September 2021).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the 13th EuroSys Conference (EuroSys ’18), Porto, Portugal, 23–26 April 2018; ACM: New York, NY, USA. [Google Scholar] [CrossRef] [Green Version]
- ConsenSys. Quorum. 2016. Available online: https://consensys.net/quorum (accessed on 11 April 2021).
- Mengelkamp, E.; Gärttner, J.; Rock, K.; Kessler, S.; Orsini, L.; Weinhardt, C. Designing microgrid energy markets: A case study: The Brooklyn Microgrid. Appl. Energy 2018, 210, 870–880. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C. Blockchain-Based Decentralized Trust Management in Vehicular Networks. IEEE Internet Things J. 2019, 6, 1495–1505. [Google Scholar] [CrossRef]
- Lin, Q.; Wang, H.; Pei, X.; Wang, J. Food Safety Traceability System Based on Blockchain and EPCIS. IEEE Access 2019, 7, 20698–20707. [Google Scholar] [CrossRef]
- Bader, L.; Pennekamp, J.; Matzutt, R.; Hedderich, D.; Kowalski, M.; Lücken, V.; Wehrle, K. Blockchain-Based Privacy Preservation for Supply Chains Supporting Lightweight Multi-Hop Information Accountability. Inf. Process. Manag. 2021, 58. [Google Scholar] [CrossRef]
- Malik, S.; Dedeoglu, V.; Kanhere, S.; Jurdak, R. PrivChain: Provenance and Privacy Preservation in Blockchain enabled Supply Chains. arXiv 2021, arXiv:2104.13964. [Google Scholar]
- Malik, S.; Gupta, N.; Dedeoglu, V.; Kanhere, S.; Jurdak, R. TradeChain: Decoupling Traceability and Identity in Blockchain enabled Supply Chains. arXiv 2021, arXiv:2105.11217. [Google Scholar]
- Gonczol, P.; Katsikouli, P.; Herskind, L.; Dragoni, N. Blockchain Implementations and Use Cases for Supply Chains-A Survey. IEEE Access 2020, 8, 11856–11871. [Google Scholar] [CrossRef]
- Croman, K.; Decker, C.; Eyal, I.; Gencer, A.E.; Juels, A.; Kosba, A.; Miller, A.; Saxena, P.; Shi, E.; Gün Sirer, E.; et al. On Scaling Decentralized Blockchains. In Proceedings of the 20th International Conference on Financial Cryptography and Data Security (FC ’16), Christ Church, Barbados, 22–26 February 2016; Springer: Berlin, Germany; Volume 9604, pp. 106–125. [Google Scholar] [CrossRef]
- Barber, S.; Boyen, X.; Shi, E.; Uzun, E. Bitter to Better—How to Make Bitcoin a Better Currency. In Proceedings of the 13th International Conference on Financial Cryptography and Data Security (FC ’12), Kinabalu, Malaysia, 10–14 February 2012; Springer: Berlin, Germany; Volume 7397, pp. 399–414. [Google Scholar] [CrossRef] [Green Version]
- Cachin, C.; Vukolić, M. Blockchain Consensus Protocols in the Wild. In Proceedings of the 31st International Symposium on Distributed Computing (DISC ’17), Vienna, Austria, 16–20 October 2017; Schloss Dagstuhl: Dagstuhl, Germany; Volume 91. [Google Scholar] [CrossRef]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A Secure Sharding Protocol For Open Blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security (CCS ’16), Vienna, Austria, 24–28 October 2016; ACM: New York, NY, USA; pp. 17–30. [Google Scholar] [CrossRef]
- Zamani, M.; Movahedi, M.; Raykova, M. RapidChain: Scaling Blockchain via Full Sharding. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security (CCS ’18), Toronto, ON, Canada, 15–19 October 2018; ACM: New York, NY, USA; pp. 931–948. [Google Scholar] [CrossRef] [Green Version]
- Kokoris-Kogias, E.; Jovanovic, P.; Gasser, L.; Gailly, N.; Syta, E.; Ford, B. OmniLedger: A Secure, Scale-Out, Decentralized Ledger via Sharding. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP ’20), San Francisco, CA, USA, 21–23 May 2018; pp. 583–598. [Google Scholar] [CrossRef] [Green Version]
- Matzutt, R.; Kalde, B.; Pennekamp, J.; Drichel, A.; Henze, M.; Wehrle, K. CoinPrune: Shrinking Bitcoin’s Blockchain Retrospectively. IEEE Trans. Netw. Serv. Manag. 2021. [Google Scholar] [CrossRef]
- Matzutt, R.; Hiller, J.; Henze, M.; Ziegeldorf, J.H.; Müllmann, D.; Hohlfeld, O.; Wehrle, K. A Quantitative Analysis of the Impact of Arbitrary Blockchain Content on Bitcoin. In Proceedings of the 22th International Conference on Financial Cryptography and Data Security (FC ’18), Nieuwpoort, Curaçao, 26 February 26–2 March 2018; Springer: Berlin, Germany; Volume 10957, pp. 420–438. [Google Scholar] [CrossRef]
- Mangel, S.; Gleim, L.; Pennekamp, J.; Wehrle, K.; Decker, S. Data Reliability and Trustworthiness through Digital Transmission Contracts. In Proceedings of the 18th Extended Semantic Web Conference (ESWC ’21), Heraklion, Greece, 6–10 June 2021; Springer: Cham, Switzerland; Volume 12731, pp. 265–283. [Google Scholar] [CrossRef]
- Hohenberger, S.; Waters, B. Attribute-Based Encryption with Fast Decryption. In Proceedings of the 16th International Conference on Practice and Theory in Public Key Cryptography (PKC ’13), Nara, Japan, 26 February–1 March 2013; Springer: Berlin, Germany; Volume 7778, pp. 162–179. [Google Scholar] [CrossRef] [Green Version]
- Miller, A.; Xia, Y.; Croman, K.; Shi, E.; Song, D. The Honey Badger of BFT Protocols. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security (CCS ’16), Vienna, Austria, 24–28 October 2016; ACM: New York, NY, USA; pp. 31–42. [Google Scholar] [CrossRef] [Green Version]
- Ozdemir, A.; Wahby, R.; Whitehat, B.; Boneh, D. Scaling Verifiable Computation Using Efficient Set Accumulators. In Proceedings of the 29th USENIX Conference on Security Symposium (SEC ’20), Boston, MA, USA, 12–14 August 2020; USENIX Association: Berkeley, CA, USA; pp. 2075–2092. [Google Scholar]
- Wang, G.; Shi, Z.J.; Nixon, M.; Han, S. SoK: Sharding on Blockchain. In Proceedings of the 1st ACM Conference on Advances in Financial Technologies (AFT ’19), Zurich, Switzerland, 21–23 October 2019; ACM: New York, NY, USA; pp. 41–61. [Google Scholar] [CrossRef]
- Pennekamp, J.; Alder, F.; Matzutt, R.; Mühlberg, J.T.; Piessens, F.; Wehrle, K. Secure End-to-End Sensing in Supply Chains. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS ’20), Avignon, France, 29 June–1 July 2020. [Google Scholar] [CrossRef]
- Pennekamp, J.; Bader, L.; Matzutt, R.; Niemietz, P.; Trauth, D.; Henze, M.; Bergs, T.; Wehrle, K. Private Multi-Hop Accountability for Supply Chains. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops ’20), the 1st Workshop on Blockchain for IoT and Cyber-Physical Systems (BIoTCPS ’20), Dublin, Ireland, 7–11 June 2020. [Google Scholar] [CrossRef]
- Hu, L.; Nguyen, N.T.; Tao, W.; Leu, M.C.; Liu, X.F.; Shahriar, M.R.; Al Sunny, S.M.N. Modeling of cloud-based digital twins for smart manufacturing with MT connect. Procedia Manuf. 2018, 26, 1193–1203. [Google Scholar] [CrossRef]
- Coronado, P.D.U.; Lynn, R.; Louhichi, W.; Parto, M.; Wescoat, E.; Kurfess, T. Part data integration in the Shop Floor Digital Twin: Mobile and cloud technologies to enable a manufacturing execution system. J. Manuf. Syst. 2018, 48, 25–33. [Google Scholar] [CrossRef]
- Zambal, S.; Eitzinger, C.; Clarke, M.; Klintworth, J.; Mechin, P.Y. A digital twin for composite parts manufacturing: Effects of defects analysis based on manufacturing data. In Proceedings of the 2018 IEEE 16th International Conference on Industrial Informatics (INDIN ’18), Porto, Portugal, 18–20 July 2018; pp. 803–808. [Google Scholar] [CrossRef] [Green Version]
- Jarke, M.; Schuh, G.; Brecher, C.; Brockmann, M.; Prote, J.P. Digital Shadows in the Internet of Production. ERCIM News 2018, 115, 26–28. [Google Scholar]
- Becker, F.; Bibow, P.; Dalibor, M.; Gannouni, A.; Hahn, V.; Hopmann, C.; Jarke, M.; Kröger, M.; Lipp, J.; Maibaum, J.; et al. A Conceptual Model for Digital Shadows in Industry and its Application. In Proceedings of the 40th International Conference on Conceptual Modeling (ER’21), St. John’s, NL, Canada, 18–21 October 2021. [Google Scholar]
- Bibow, P.; Dalibor, M.; Hopmann, C.; Mainz, B.; Rumpe, B.; Schmalzing, D.; Schmitz, M.; Wortmann, A. Model-Driven Development of a Digital Twin for Injection Molding. In Proceedings of the 32nd International Conference on Advanced Information Systems Engineering (CAiSE ’20), Grenoble, France, 8–12 June 2020; Springer: Cham, Switzerland; Volume 12127, pp. 85–100. [Google Scholar] [CrossRef]
- Schuh, G.; Häfner, C.; Hopmann, C.; Rumpe, B.; Brockmann, M.; Wortmann, A.; Maibaum, J.; Dalibor, M.; Bibow, P.; Sapel, P.; et al. Effizientere Produktion mit Digitalen Schatten. ZWF Z. FüR Wirtsch. Fabr. 2020, 115, 105–107. [Google Scholar] [CrossRef]
- Tian, F. An agri-food supply chain traceability system for China based on RFID & blockchain technology. In Proceedings of the 2016 13th International Conference on Service Systems and Service Management (ICSSSM ’16), Kunming, China, 24–26 June 2016. [Google Scholar] [CrossRef]
- Rejeb, A.; Keogh, J.G.; Treiblmaier, H. Leveraging the Internet of Things and Blockchain Technology in Supply Chain Management. Future Internet 2019, 11, 161. [Google Scholar] [CrossRef] [Green Version]
- Leng, J.; Jiang, P.; Xu, K.; Liu, Q.; Zhao, J.L.; Bian, Y.; Shi, R. Makerchain: A blockchain with chemical signature for self-organizing process in social manufacturing. J. Clean. Prod. 2019, 234, 767–778. [Google Scholar] [CrossRef]
- Buckhorst, A.F.; Montavon, B.; Wolfschläger, D.; Buchsbaum, M.; Shahidi, A.; Petruck, H.; Kunze, I.; Pennekamp, J.; Brecher, C.; Hüsing, M.; et al. Holarchy for Line-less Mobile Assembly Systems Operation in the Context of the Internet of Production. Procedia CIRP 2021, 99, 448–453. [Google Scholar] [CrossRef]
- Pennekamp, J.; Henze, M.; Wehrle, K. Unlocking Secure Industrial Collaborations through Privacy-Preserving Computation. ERCIM News 2021, 126, 24–25. [Google Scholar]
- Matzutt, R.; Müllmann, D.; Zeissig, E.M.; Horst, C.; Kasugai, K.; Lidynia, S.; Wieninger, S.; Ziegeldorf, J.H.; Gudergan, G.; Spiecker gen. Döhmann, I.; et al. myneData: Towards a Trusted and User-controlled Ecosystem for Sharing Personal Data. In INFORMATIK; Gesellschaft für Informatik: Bonn, Germany, 2017; Volume 275, pp. 1073–1084. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O.; Pentland, A.S. Decentralizing Privacy: Using Blockchain to Protect Personal Data. In Proceedings of the 2015 IEEE Symposium on Security and Privacy Workshops (SPW ’15), San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pennekamp, J.; Matzutt, R.; Kanhere, S.S.; Hiller, J.; Wehrle, K. The Road to Accountable and Dependable Manufacturing. Automation 2021, 2, 202-219. https://doi.org/10.3390/automation2030013
Pennekamp J, Matzutt R, Kanhere SS, Hiller J, Wehrle K. The Road to Accountable and Dependable Manufacturing. Automation. 2021; 2(3):202-219. https://doi.org/10.3390/automation2030013
Chicago/Turabian StylePennekamp, Jan, Roman Matzutt, Salil S. Kanhere, Jens Hiller, and Klaus Wehrle. 2021. "The Road to Accountable and Dependable Manufacturing" Automation 2, no. 3: 202-219. https://doi.org/10.3390/automation2030013
APA StylePennekamp, J., Matzutt, R., Kanhere, S. S., Hiller, J., & Wehrle, K. (2021). The Road to Accountable and Dependable Manufacturing. Automation, 2(3), 202-219. https://doi.org/10.3390/automation2030013






